Cybersecurity Risk Assessment Report: Threats and Vulnerabilities
VerifiedAdded on 2022/08/31
|11
|1091
|30
Report
AI Summary
This report presents a risk assessment of an organization's network infrastructure and IT assets, focusing on potential threats and vulnerabilities. It identifies threats such as IP spoofing attacks, SQL injection, and cross-site scripting, detailing their impact and likelihood. The assessment includes a system characterization, outlining technology components, data utilized, and user roles. The report analyzes the potential vulnerabilities, like weak passwords and the absence of a disaster recovery plan, and offers recommendations for remediation and mitigation. The risk assessment results provide observations, threat sources, and vulnerability assessments. The report emphasizes the need for strong passwords, a robust disaster recovery plan, and validation of all inputs to prevent SQL injection and cross-site scripting attacks. The report concludes with a call for proactive security measures to safeguard the organization's data and systems. The report is contributed by a student to be published on the website Desklib. Desklib is a platform which provides all the necessary AI based study tools for students.

Risk Assessment Report
Table of Conten
1
Table of Conten
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

t
1. Introduction..................................................................................................................3
2. Approach for the Risk Assessment..............................................................................4
3. System Characterization..............................................................................................5
4. Threats.........................................................................................................................6
5. Vulnerability Statement...............................................................................................7
6. Statement for Threat....................................................................................................8
7. Risk Assessment Result...............................................................................................8
References.........................................................................................................................11
2
1. Introduction..................................................................................................................3
2. Approach for the Risk Assessment..............................................................................4
3. System Characterization..............................................................................................5
4. Threats.........................................................................................................................6
5. Vulnerability Statement...............................................................................................7
6. Statement for Threat....................................................................................................8
7. Risk Assessment Result...............................................................................................8
References.........................................................................................................................11
2

Risk Assessment Report
1. Introduction
1.1 Purpose
The purpose includes determining various known threats to the organization’s network
infrastructure and IT assets. The identification of various threats includes the following tasks
such as,
Identify the threat attack potential hackers on vulnerability in organization’s
information system and networks.
Identify the type of remediation and mitigation techniques.
Identify the function and purpose of firewalls for the organization’s network
infrastructure.
Discuss the value of using firewall log files, database transaction and access
control.
Identify the function and purpose of encryption.
At last, provide the recommendation for methods to remediate and mitigate the
identified vulnerabilities ("Spoofing Attack: IP, DNS & ARP", 2020).
1.2 Risk Assessment’s Scope
RAR lists the threats, vulnerabilities and pairwise comparisons for each vulnerability and
threats. It also determines the likelihood of each event occurring and impact level on the
organization.
3
1. Introduction
1.1 Purpose
The purpose includes determining various known threats to the organization’s network
infrastructure and IT assets. The identification of various threats includes the following tasks
such as,
Identify the threat attack potential hackers on vulnerability in organization’s
information system and networks.
Identify the type of remediation and mitigation techniques.
Identify the function and purpose of firewalls for the organization’s network
infrastructure.
Discuss the value of using firewall log files, database transaction and access
control.
Identify the function and purpose of encryption.
At last, provide the recommendation for methods to remediate and mitigate the
identified vulnerabilities ("Spoofing Attack: IP, DNS & ARP", 2020).
1.2 Risk Assessment’s Scope
RAR lists the threats, vulnerabilities and pairwise comparisons for each vulnerability and
threats. It also determines the likelihood of each event occurring and impact level on the
organization.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Approach for the Risk Assessment
2.1 Participants
The participants are:
Team of Risk assessment
Network Manager
Network Security Manager
Security Administrator
Database Administrator
System Owner
System Custodian
2.2 Techniques Used
The used techniques are:
Risk assessment related questionnaire
Vulnerability sources
Assessment Tools such as Wire shark, firewalls, encryption, and auditing.
Transaction Walkthrough
Documentation Review
Site visit
2.3 Risk Model
In risk determination, the below provided model is used for risk classification,
4
2.1 Participants
The participants are:
Team of Risk assessment
Network Manager
Network Security Manager
Security Administrator
Database Administrator
System Owner
System Custodian
2.2 Techniques Used
The used techniques are:
Risk assessment related questionnaire
Vulnerability sources
Assessment Tools such as Wire shark, firewalls, encryption, and auditing.
Transaction Walkthrough
Documentation Review
Site visit
2.3 Risk Model
In risk determination, the below provided model is used for risk classification,
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. System Characterization
3.1 Components of the Technology
The technology components are,
Protocols - SSL and Web server
Networks - Cisco Firewall, Cisco Routers, Cisco Switches
Database - MySQL
Application - Microsoft IIS
Interconnections – Pay link Interfaces
3.2 Data Utilized by the Systems
All the systems contain the following data,
Financial information
Customer Information
Employee Information
Tax Information
Organization Information
Application related information
3.3 Users
The users are,
Owners
IT Personnel
Offices
Operations
IT security Personnel
5
3.1 Components of the Technology
The technology components are,
Protocols - SSL and Web server
Networks - Cisco Firewall, Cisco Routers, Cisco Switches
Database - MySQL
Application - Microsoft IIS
Interconnections – Pay link Interfaces
3.2 Data Utilized by the Systems
All the systems contain the following data,
Financial information
Customer Information
Employee Information
Tax Information
Organization Information
Application related information
3.3 Users
The users are,
Owners
IT Personnel
Offices
Operations
IT security Personnel
5
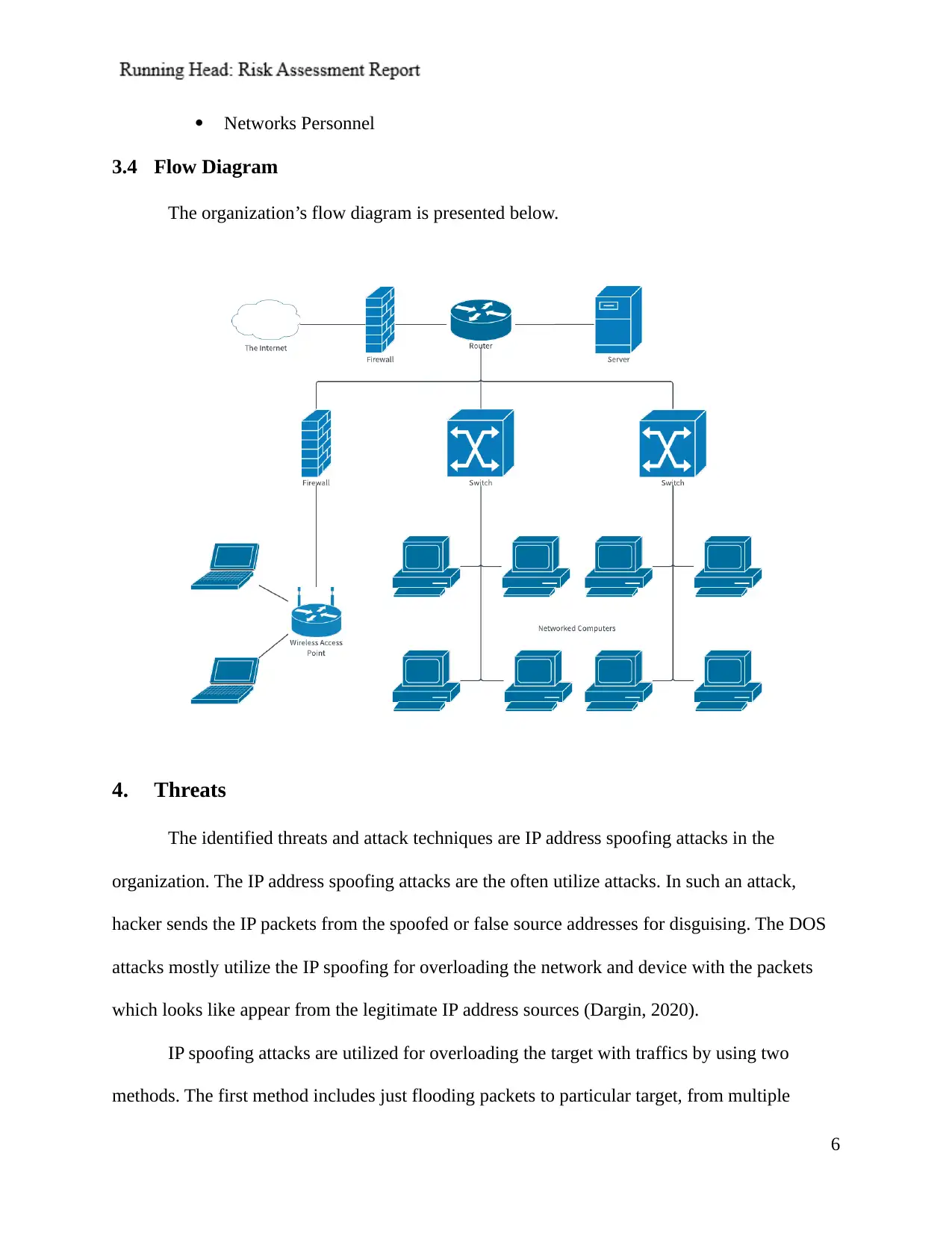
Networks Personnel
3.4 Flow Diagram
The organization’s flow diagram is presented below.
4. Threats
The identified threats and attack techniques are IP address spoofing attacks in the
organization. The IP address spoofing attacks are the often utilize attacks. In such an attack,
hacker sends the IP packets from the spoofed or false source addresses for disguising. The DOS
attacks mostly utilize the IP spoofing for overloading the network and device with the packets
which looks like appear from the legitimate IP address sources (Dargin, 2020).
IP spoofing attacks are utilized for overloading the target with traffics by using two
methods. The first method includes just flooding packets to particular target, from multiple
6
3.4 Flow Diagram
The organization’s flow diagram is presented below.
4. Threats
The identified threats and attack techniques are IP address spoofing attacks in the
organization. The IP address spoofing attacks are the often utilize attacks. In such an attack,
hacker sends the IP packets from the spoofed or false source addresses for disguising. The DOS
attacks mostly utilize the IP spoofing for overloading the network and device with the packets
which looks like appear from the legitimate IP address sources (Dargin, 2020).
IP spoofing attacks are utilized for overloading the target with traffics by using two
methods. The first method includes just flooding packets to particular target, from multiple
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

spoofed addresses and such a method is works by directly sending maximum data to a victim,
which can increase the data managing difficulty. Second method includes spoofing the targeted
IP address and the packets are sent from this address to various the network’s different recipients.
These attacks could even be utilize for bypassing the IP address-based authentications, but
this method is extremely challenging. Moreover, it is mostly utilize while the trust relationships
are ready among the machines on the internal and network system. It allows the malicious parties
to utilize the spoofing attack for impersonating the machine with the access permissions.
5. Vulnerability Statement
The identified potential vulnerabilities are as follows ("DETAILED RISK
ASSESSMENT REPORT", 2020),
Password Strength
The passwords are inappropriately formulated, the hackers easily predict user’s
password for gaining their system’s access.
SQL Injection
In web request, the information isn’t validated prior to the usage by the web
application. So, the hackers utilize such faults for attacking the backend components
via the web application.
Cross Site Scripting
Web application is utilized as a tool for transporting the attack to an end-user
browser, and the good attack could disclose session tokens of the end user, and the users
are fooled by spoofing the content.
Disaster Recovery
7
which can increase the data managing difficulty. Second method includes spoofing the targeted
IP address and the packets are sent from this address to various the network’s different recipients.
These attacks could even be utilize for bypassing the IP address-based authentications, but
this method is extremely challenging. Moreover, it is mostly utilize while the trust relationships
are ready among the machines on the internal and network system. It allows the malicious parties
to utilize the spoofing attack for impersonating the machine with the access permissions.
5. Vulnerability Statement
The identified potential vulnerabilities are as follows ("DETAILED RISK
ASSESSMENT REPORT", 2020),
Password Strength
The passwords are inappropriately formulated, the hackers easily predict user’s
password for gaining their system’s access.
SQL Injection
In web request, the information isn’t validated prior to the usage by the web
application. So, the hackers utilize such faults for attacking the backend components
via the web application.
Cross Site Scripting
Web application is utilized as a tool for transporting the attack to an end-user
browser, and the good attack could disclose session tokens of the end user, and the users
are fooled by spoofing the content.
Disaster Recovery
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
In this organization, there is no procedures for ensuring the system’s ongoing
operations in the event of important business disaster/interruption ("Types of DNS
Attacks and Tactics for Security - GeeksforGeeks", 2020).
6. Statement for Threat
The recognized potential threat sources, including the related threat actions are listed
below.
Environment - Natural disaster
Hacker - Systems accessed by unauthorized access
Social engineering
Web defacement
System break-ins
System intrusion
Insiders - Systems accessed by unauthorized access
Malicious code
System bugs and more.
Computer Criminal - Spoofing, identify theft, system intrusion
7. Risk Assessment Result
S.N
o
Observations Threat
source/vuln
erability
Likelih
ood
Impacts Risk-
Rating
Recommendatio
ns
1 Hackers easily
crack or guess the
user’s system
Hackers/
Effectivene
ss of
Mediu
m
Medium Medium Need to use
strong passwords
by using special
8
operations in the event of important business disaster/interruption ("Types of DNS
Attacks and Tactics for Security - GeeksforGeeks", 2020).
6. Statement for Threat
The recognized potential threat sources, including the related threat actions are listed
below.
Environment - Natural disaster
Hacker - Systems accessed by unauthorized access
Social engineering
Web defacement
System break-ins
System intrusion
Insiders - Systems accessed by unauthorized access
Malicious code
System bugs and more.
Computer Criminal - Spoofing, identify theft, system intrusion
7. Risk Assessment Result
S.N
o
Observations Threat
source/vuln
erability
Likelih
ood
Impacts Risk-
Rating
Recommendatio
ns
1 Hackers easily
crack or guess the
user’s system
Hackers/
Effectivene
ss of
Mediu
m
Medium Medium Need to use
strong passwords
by using special
8
passwords Password characters.
2 Does not establish
the disaster
recovery plan.
Environmen
t/ Disaster
Recovery
Mediu
m
High Medium Need to develop
and test the
disaster recovery
plan.
3 The data is
inappropriately
modified and
extracted from the
database by typing
the SQL command
into the input
fields.
Criminals+
Hackers/
SQL
Injection
High Medium Medium Need to ensure
that all the
entered
parameters are
authenticated
before they are
used and
effectively use the
centralized library
and component.
Lastly, check each
parameter that
should be in
correct format
because it is used
to specify what
input will be
allowed.
9
2 Does not establish
the disaster
recovery plan.
Environmen
t/ Disaster
Recovery
Mediu
m
High Medium Need to develop
and test the
disaster recovery
plan.
3 The data is
inappropriately
modified and
extracted from the
database by typing
the SQL command
into the input
fields.
Criminals+
Hackers/
SQL
Injection
High Medium Medium Need to ensure
that all the
entered
parameters are
authenticated
before they are
used and
effectively use the
centralized library
and component.
Lastly, check each
parameter that
should be in
correct format
because it is used
to specify what
input will be
allowed.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4 Cross site
Scripting
Hackers/
Cross site
Scripting
Mediu
m
Medium Medium Need to do the
validation of all
the hidden fields,
headers, form
fields, query
string, and
cookies.
10
Scripting
Hackers/
Cross site
Scripting
Mediu
m
Medium Medium Need to do the
validation of all
the hidden fields,
headers, form
fields, query
string, and
cookies.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Dargin, M. (2020). How to protect your infrastructure from DNS cache poisoning. Retrieved 10
January 2020, from https://www.networkworld.com/article/3298160/how-to-protect-your-
infrastructure-from-dns-cache-poisoning.html
DETAILED RISK ASSESSMENT REPORT. (2020). Retrieved 10 January 2020, from
https://itsecurity.uiowa.edu/sites/itsecurity.uiowa.edu/files/sampleriskassessmentreport.pdf
Spoofing Attack: IP, DNS & ARP. (2020). Retrieved 10 January 2020, from
https://www.veracode.com/security/spoofing-attack
Types of DNS Attacks and Tactics for Security - GeeksforGeeks. (2020). Retrieved 10 January
2020, from https://www.geeksforgeeks.org/types-of-dns-attacks-and-tactics-for-security/
11
Dargin, M. (2020). How to protect your infrastructure from DNS cache poisoning. Retrieved 10
January 2020, from https://www.networkworld.com/article/3298160/how-to-protect-your-
infrastructure-from-dns-cache-poisoning.html
DETAILED RISK ASSESSMENT REPORT. (2020). Retrieved 10 January 2020, from
https://itsecurity.uiowa.edu/sites/itsecurity.uiowa.edu/files/sampleriskassessmentreport.pdf
Spoofing Attack: IP, DNS & ARP. (2020). Retrieved 10 January 2020, from
https://www.veracode.com/security/spoofing-attack
Types of DNS Attacks and Tactics for Security - GeeksforGeeks. (2020). Retrieved 10 January
2020, from https://www.geeksforgeeks.org/types-of-dns-attacks-and-tactics-for-security/
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




