MIS607 Cybersecurity Threat Model Report: Analysis of B&C Insurance
VerifiedAdded on 2023/06/18
|10
|1987
|460
Report
AI Summary
This report presents a cybersecurity threat model analysis based on the case study of The Business & Communication Insurance (B&C Insurance), which experienced a ransomware attack and potential data breach. The report outlines the purpose and context of the research, defining key cybersecurity concepts and the objectives of threat modeling. It details the requirements of the case study, including the ransom email received and the validation of the data breach. A data flow diagram illustrates the system's vulnerabilities, followed by the identification of ransomware as the primary threat, with further classification into locker and crypto ransomware. The report concludes with findings, recommendations for mitigating such threats (such as caution with email attachments, software updates, and robust antivirus software), and a summary of the topics covered. This analysis aims to provide a structured approach to understanding and addressing cybersecurity risks within the organization. Desklib provides students with access to similar solved assignments and past papers.

Cybersecurity Threat
Model Report
Model Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
Purpose of report.........................................................................................................................1
Area of research..........................................................................................................................1
Context of research.....................................................................................................................1
Concepts of cybersecurity...........................................................................................................2
Purpose of drawing the threat
model..........................................................................................................................................2
MAIN BODY...................................................................................................................................3
Requirements of the case study...................................................................................................3
Data flow diagram.......................................................................................................................3
Identifying threats to the system.................................................................................................5
Understanding the threats............................................................................................................5
CONCLUSION................................................................................................................................6
Findings.......................................................................................................................................6
Recommendations.......................................................................................................................6
Covered in the report...................................................................................................................7
References:.......................................................................................................................................8
INTRODUCTION...........................................................................................................................1
Purpose of report.........................................................................................................................1
Area of research..........................................................................................................................1
Context of research.....................................................................................................................1
Concepts of cybersecurity...........................................................................................................2
Purpose of drawing the threat
model..........................................................................................................................................2
MAIN BODY...................................................................................................................................3
Requirements of the case study...................................................................................................3
Data flow diagram.......................................................................................................................3
Identifying threats to the system.................................................................................................5
Understanding the threats............................................................................................................5
CONCLUSION................................................................................................................................6
Findings.......................................................................................................................................6
Recommendations.......................................................................................................................6
Covered in the report...................................................................................................................7
References:.......................................................................................................................................8

INTRODUCTION
Purpose of report
The following discussion is made on the given case study of The Business &
Communication Insurance company in terms of cyber thefts and cyber security. This is a type of
research report which is studied as per the given scenario and generated accordingly. Discussion
is based on the area of research and context of research along with the concepts of cyber security
and purpose of drawing the threat model. Moreover, a proper review is conducted on the case
study given and therefore, requirements of the case study is mentioned and data flow diagram as
well along with the identification of threats to the system and understanding the threats with an
appropriate discussion is also done. Discussion is also made on the conclusion part which
includes the findings and recommendations along with the things covered in the report.
Area of research
Area of research is based on the cyber security threat model which is defined as the
procedure in order to identify and enumerate along with the mitigation process of potential
threats like structural vulnerabilities and absence of proper safeguards or protections on a prior
basis. In other words, threat model is a methodology of preparing security of network with the
help of locating the vulnerabilities and identification of the goals and objectives along with the
development of the counter measures in order to prevent and mitigate the negative impacts of the
cyber attacks which can harm the systems. It has a process which mainly includes five
components such as threat intelligence and asset identification along with the mitigating
capabilities and risk assessment which is followed by the threat mapping. All such elements of
threat modelling renders the assorted and various types of visibility and insights into the
perimeter of the security implemented.
Context of research
Context of research is base on the entire process of the cyber security threat model as per
the given case study such as this process includes mainly four steps which is applied in resolving
out the issues given as per the scenario given. First step states the diagram which describes the
what exactly is required to get build with help of diagram specifying all the requirements.
Second step states the identification of threats which describes the the estimation or the current
situation which can go wrong or currently it is going wrong. Third step states the mitigation
1
Purpose of report
The following discussion is made on the given case study of The Business &
Communication Insurance company in terms of cyber thefts and cyber security. This is a type of
research report which is studied as per the given scenario and generated accordingly. Discussion
is based on the area of research and context of research along with the concepts of cyber security
and purpose of drawing the threat model. Moreover, a proper review is conducted on the case
study given and therefore, requirements of the case study is mentioned and data flow diagram as
well along with the identification of threats to the system and understanding the threats with an
appropriate discussion is also done. Discussion is also made on the conclusion part which
includes the findings and recommendations along with the things covered in the report.
Area of research
Area of research is based on the cyber security threat model which is defined as the
procedure in order to identify and enumerate along with the mitigation process of potential
threats like structural vulnerabilities and absence of proper safeguards or protections on a prior
basis. In other words, threat model is a methodology of preparing security of network with the
help of locating the vulnerabilities and identification of the goals and objectives along with the
development of the counter measures in order to prevent and mitigate the negative impacts of the
cyber attacks which can harm the systems. It has a process which mainly includes five
components such as threat intelligence and asset identification along with the mitigating
capabilities and risk assessment which is followed by the threat mapping. All such elements of
threat modelling renders the assorted and various types of visibility and insights into the
perimeter of the security implemented.
Context of research
Context of research is base on the entire process of the cyber security threat model as per
the given case study such as this process includes mainly four steps which is applied in resolving
out the issues given as per the scenario given. First step states the diagram which describes the
what exactly is required to get build with help of diagram specifying all the requirements.
Second step states the identification of threats which describes the the estimation or the current
situation which can go wrong or currently it is going wrong. Third step states the mitigation
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

process which describes the measures in order to defend the systems against threats which were
identifies in a previous step. Fourth step states the validation process which describes the
function of validating the previous steps and make some action on it in order to execute the
whole process. This is the context of the whole research and review conducted as per the given
case study (Bodeau and McCollum, 2018).
Concepts of cybersecurity
Cyber security can be defined as the computer security or information technology
security which describes the protection of networks and technical systems from information
breach or disclosure because they can damage and can be a reason of theft of hardware and
software along with the electronic data. So therefore, cyber security safeguards the computer
systems from disruption and misdirection of the services they rendering. Hence, it basically
refers to the combination of various technologies and processes along with the practices designed
in order to protect the devices and programs along with the networks and data from attack and
unauthorised access. They are of many types such as malware, emotet, denial of services attack,
man in the middle attack, phishing, SQL injection, password attacks, Zero day exploit, DNS
tunnelling and many more (Gupta, Tanwar, Tyagi and Kumar, 2020).
Purpose of drawing the threat
model
Purpose of drawing the threat model is that it is one of the most structured process with
various objectives which are required to get fulfilled and also completes the purpose of the threat
model. Such objectives includes the identification of the requirements for security, pinpointing
the threats for the security and vulnerabilities as well, quantification of the threats for security
and vulnerabilities criticality along with the prioritizing the methods of different remedies
associated with the threats. Threat model basically creates the an abstraction of the system.
Moreover, its another purpose is to provide the risk based approach in order to design and
develop the secure systems. It also creates the awareness to the organization of increasing cyber
security risks in terms of liabilities and software development teams as well so that they make
efficient and effective methods to develop the security in the software (Ramon and Zajac, 2018).
2
identifies in a previous step. Fourth step states the validation process which describes the
function of validating the previous steps and make some action on it in order to execute the
whole process. This is the context of the whole research and review conducted as per the given
case study (Bodeau and McCollum, 2018).
Concepts of cybersecurity
Cyber security can be defined as the computer security or information technology
security which describes the protection of networks and technical systems from information
breach or disclosure because they can damage and can be a reason of theft of hardware and
software along with the electronic data. So therefore, cyber security safeguards the computer
systems from disruption and misdirection of the services they rendering. Hence, it basically
refers to the combination of various technologies and processes along with the practices designed
in order to protect the devices and programs along with the networks and data from attack and
unauthorised access. They are of many types such as malware, emotet, denial of services attack,
man in the middle attack, phishing, SQL injection, password attacks, Zero day exploit, DNS
tunnelling and many more (Gupta, Tanwar, Tyagi and Kumar, 2020).
Purpose of drawing the threat
model
Purpose of drawing the threat model is that it is one of the most structured process with
various objectives which are required to get fulfilled and also completes the purpose of the threat
model. Such objectives includes the identification of the requirements for security, pinpointing
the threats for the security and vulnerabilities as well, quantification of the threats for security
and vulnerabilities criticality along with the prioritizing the methods of different remedies
associated with the threats. Threat model basically creates the an abstraction of the system.
Moreover, its another purpose is to provide the risk based approach in order to design and
develop the secure systems. It also creates the awareness to the organization of increasing cyber
security risks in terms of liabilities and software development teams as well so that they make
efficient and effective methods to develop the security in the software (Ramon and Zajac, 2018).
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MAIN BODY
Requirements of the case study
Case study is based on the company “The Business & Communication Insurance” which
provides services as private health insurer. The case reviews that the company had received the
ransom email of personal details of the company's clients. This was a matter of concern because
some unknown company cannot access the strategic plans of the organization. So the company
decided to validate the threat and started the forensic investigation for the same. Therefore,
requirements of the case study is to generate the report which contains the information from
identification of threats to the mitigation of it so that decision making and implementation of
cybersecurity can be done potentially.
Data flow diagram
3
Requirements of the case study
Case study is based on the company “The Business & Communication Insurance” which
provides services as private health insurer. The case reviews that the company had received the
ransom email of personal details of the company's clients. This was a matter of concern because
some unknown company cannot access the strategic plans of the organization. So the company
decided to validate the threat and started the forensic investigation for the same. Therefore,
requirements of the case study is to generate the report which contains the information from
identification of threats to the mitigation of it so that decision making and implementation of
cybersecurity can be done potentially.
Data flow diagram
3
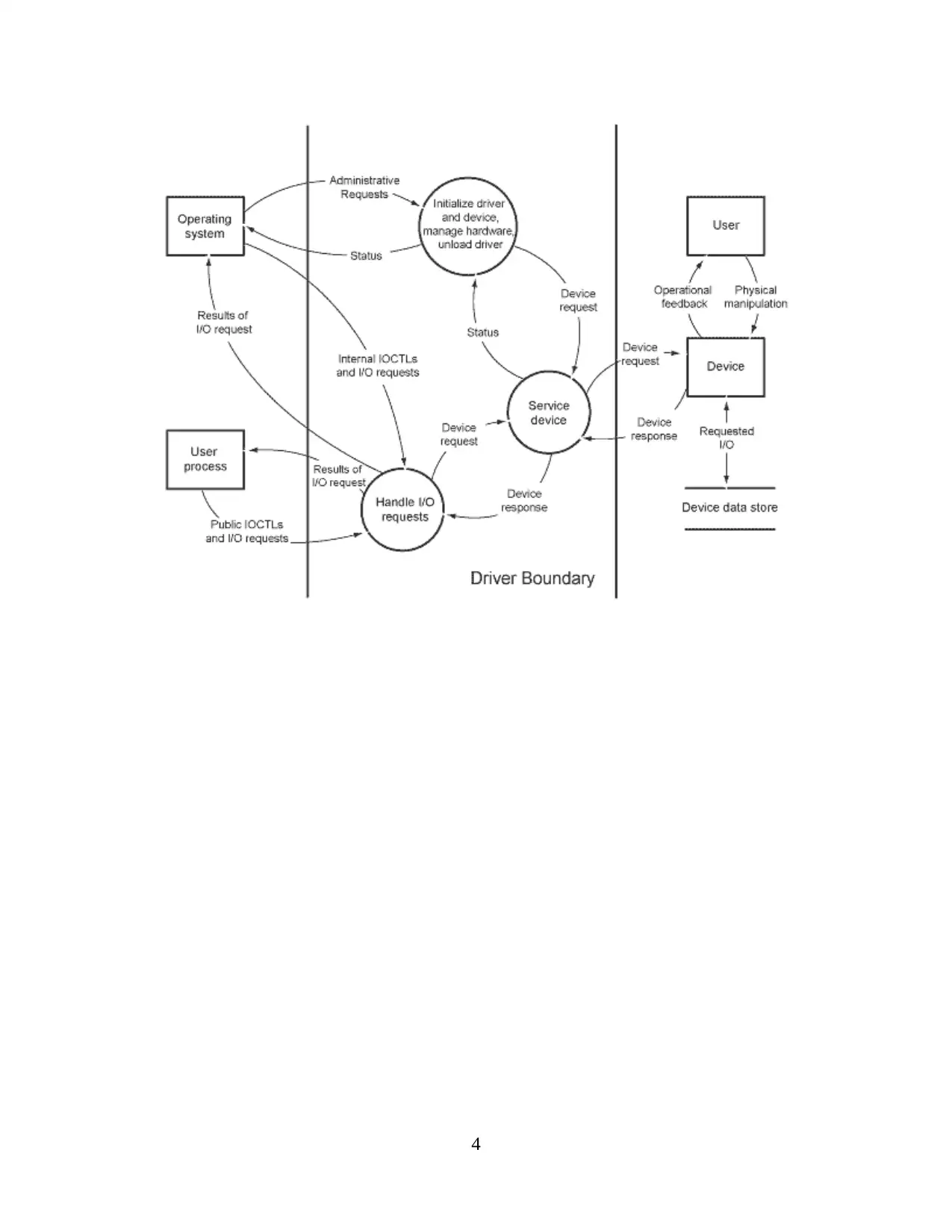
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
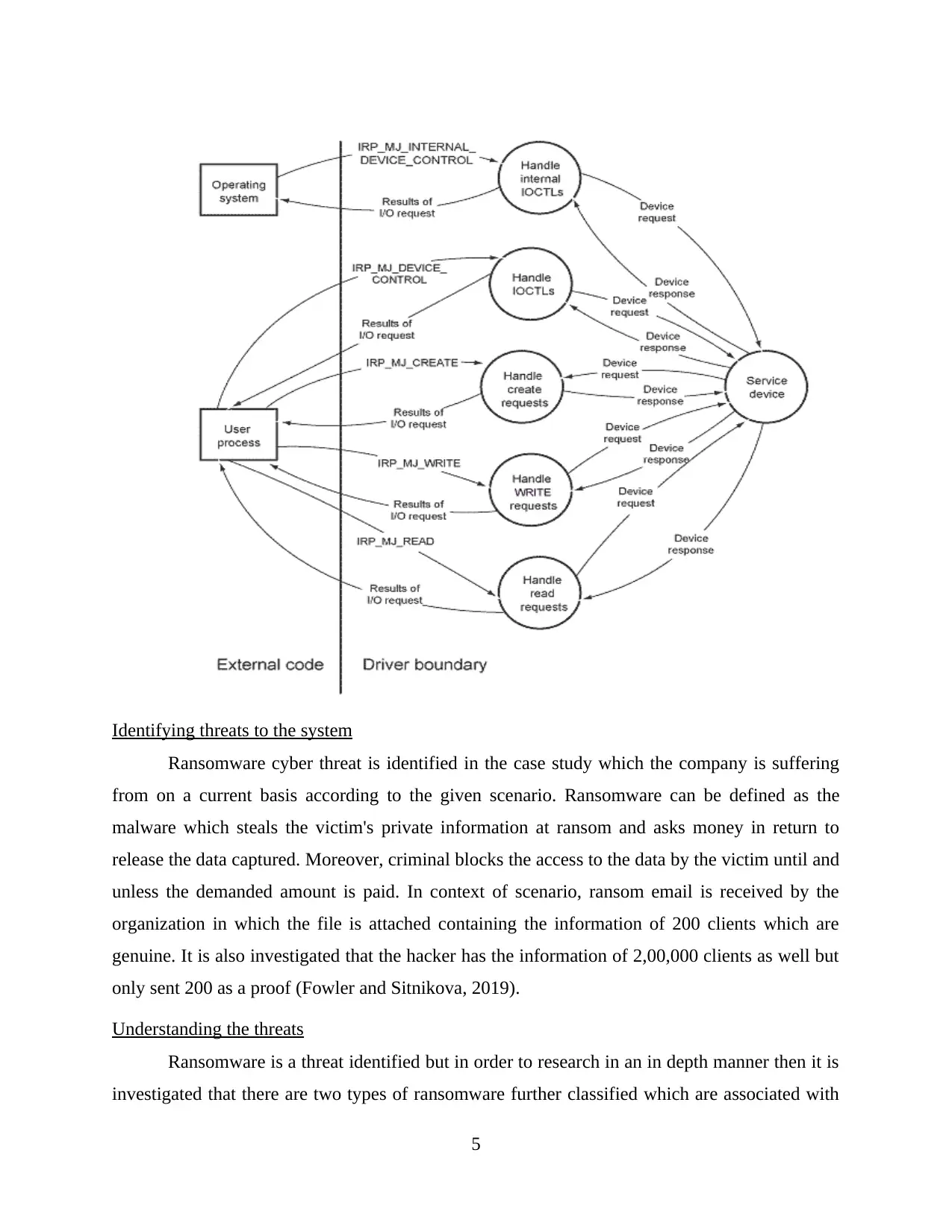
Identifying threats to the system
Ransomware cyber threat is identified in the case study which the company is suffering
from on a current basis according to the given scenario. Ransomware can be defined as the
malware which steals the victim's private information at ransom and asks money in return to
release the data captured. Moreover, criminal blocks the access to the data by the victim until and
unless the demanded amount is paid. In context of scenario, ransom email is received by the
organization in which the file is attached containing the information of 200 clients which are
genuine. It is also investigated that the hacker has the information of 2,00,000 clients as well but
only sent 200 as a proof (Fowler and Sitnikova, 2019).
Understanding the threats
Ransomware is a threat identified but in order to research in an in depth manner then it is
investigated that there are two types of ransomware further classified which are associated with
5
Ransomware cyber threat is identified in the case study which the company is suffering
from on a current basis according to the given scenario. Ransomware can be defined as the
malware which steals the victim's private information at ransom and asks money in return to
release the data captured. Moreover, criminal blocks the access to the data by the victim until and
unless the demanded amount is paid. In context of scenario, ransom email is received by the
organization in which the file is attached containing the information of 200 clients which are
genuine. It is also investigated that the hacker has the information of 2,00,000 clients as well but
only sent 200 as a proof (Fowler and Sitnikova, 2019).
Understanding the threats
Ransomware is a threat identified but in order to research in an in depth manner then it is
investigated that there are two types of ransomware further classified which are associated with
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the case study scenario such as first is locker ransomware which a malware that mainly block the
fundamental functioning of the computers. People in the organization are unable to access their
basic personal computers and their working or features as well. But positivity is that this type
cannot destroy the data and not target the important files, it just keeps the employees out of the
computer access. Second is crypto ransomware which directly attacks the important files or
folders of the systems but not interfere the fundamental functions of the computers. This type is
not implemented by the hacker. They only have the access and demand ransom money in return
(Leander, Čaušević and Hansson, 2019).
CONCLUSION
Findings
In the above report, investigation about the case study is conducted along with the review
so therefore, findings includes an important and essential analysing and examining of the
purpose of the report, area and context of research made, concepts of cyber security and purpose
of drawing the threat model. Also necessary and significant determining and assessing of the
requirements of the case study, data flow diagram and identification and understanding of the
threats involved to the system. Moreover, vital, imperative and crucial investigating and studying
about the recommendations and solutions along with the mitigations of threats as per the case
scenario (Goel, Haddow and Kumar, 2018).
Recommendations
It is recommended that the organization must be very careful with email attachments so
that none of the staff should click on any link that appears in an email body because that might
invite the cyber threat. It is also recommended that organisation must also be careful with amu
unknown sources such as external drives and any USB sticks and it is important for the
company to use their social networks in a safe and clever manner. Most essential
recommendation is the frequent updates of the software for strong security purpose because
software loose security if not updated timely. Company must implement the good antivirus and
firewall software along with the timely backing up the systems helps in gaining the tight security
and reduce the chances of cyber threat (Bitton, Maman, Singh and Shabtai, 2021).
6
fundamental functioning of the computers. People in the organization are unable to access their
basic personal computers and their working or features as well. But positivity is that this type
cannot destroy the data and not target the important files, it just keeps the employees out of the
computer access. Second is crypto ransomware which directly attacks the important files or
folders of the systems but not interfere the fundamental functions of the computers. This type is
not implemented by the hacker. They only have the access and demand ransom money in return
(Leander, Čaušević and Hansson, 2019).
CONCLUSION
Findings
In the above report, investigation about the case study is conducted along with the review
so therefore, findings includes an important and essential analysing and examining of the
purpose of the report, area and context of research made, concepts of cyber security and purpose
of drawing the threat model. Also necessary and significant determining and assessing of the
requirements of the case study, data flow diagram and identification and understanding of the
threats involved to the system. Moreover, vital, imperative and crucial investigating and studying
about the recommendations and solutions along with the mitigations of threats as per the case
scenario (Goel, Haddow and Kumar, 2018).
Recommendations
It is recommended that the organization must be very careful with email attachments so
that none of the staff should click on any link that appears in an email body because that might
invite the cyber threat. It is also recommended that organisation must also be careful with amu
unknown sources such as external drives and any USB sticks and it is important for the
company to use their social networks in a safe and clever manner. Most essential
recommendation is the frequent updates of the software for strong security purpose because
software loose security if not updated timely. Company must implement the good antivirus and
firewall software along with the timely backing up the systems helps in gaining the tight security
and reduce the chances of cyber threat (Bitton, Maman, Singh and Shabtai, 2021).
6

Covered in the report
This report covers the investigation about the case study given on cyber threats and cyber
security which includes the introduction containing the purpose of report and area of research
along with the context of research and concepts of cyber security which is followed by the
purpose of drawing the threat model. Report also covers the main body containing the
information about the case study which includes the requirements of the case study and data flow
diagrams along with the identification of the threats to the systems and understanding of the
threats in detail. Moreover, conclusion covers the information related to the findings and
recommendations by analysing the whole report so that proper decision making can be done by
the organization and also to better understand the concepts of cybersecurity threat model.
7
This report covers the investigation about the case study given on cyber threats and cyber
security which includes the introduction containing the purpose of report and area of research
along with the context of research and concepts of cyber security which is followed by the
purpose of drawing the threat model. Report also covers the main body containing the
information about the case study which includes the requirements of the case study and data flow
diagrams along with the identification of the threats to the systems and understanding of the
threats in detail. Moreover, conclusion covers the information related to the findings and
recommendations by analysing the whole report so that proper decision making can be done by
the organization and also to better understand the concepts of cybersecurity threat model.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References:
Books and Journals
Bitton, R., Maman, N., Singh, I. and Shabtai, A., 2021. A Framework for Evaluating the
Cybersecurity Risk of Real World, Machine Learning Production Systems. arXiv preprint
arXiv:2107.01806.
Bodeau, D.J. and McCollum, C.D., 2018. System-of-systems threat model. MITRE CORP
MCLEAN VA MCLEAN.
Fowler, S. and Sitnikova, E., 2019, November. Toward a framework for assessing the cyber-
worthiness of complex mission critical systems. In 2019 Military Communications and
Information Systems Conference (MilCIS) (pp. 1-6). IEEE.
Goel, R., Haddow, J. and Kumar, A., 2018. Managing cybersecurity risk in government: an
implementation model. Report from IBM Center for The Business of Government.
Gupta, R., Tanwar, S., Tyagi, S. and Kumar, N., 2020. Machine learning models for secure data
analytics: A taxonomy and threat model. Computer Communications, 153, pp.406-440.
Leander, B., Čaušević, A. and Hansson, H., 2019, September. Cybersecurity Challenges in Large
Industrial IoT Systems. In 2019 24th IEEE International Conference on Emerging
Technologies and Factory Automation (ETFA) (pp. 1035-1042). IEEE.
Ramon, M.C. and Zajac, D.A., 2018. Cybersecurity Literature Review and Efforts
Report. Prepared for NCHRP Project, pp.03-127.
8
Books and Journals
Bitton, R., Maman, N., Singh, I. and Shabtai, A., 2021. A Framework for Evaluating the
Cybersecurity Risk of Real World, Machine Learning Production Systems. arXiv preprint
arXiv:2107.01806.
Bodeau, D.J. and McCollum, C.D., 2018. System-of-systems threat model. MITRE CORP
MCLEAN VA MCLEAN.
Fowler, S. and Sitnikova, E., 2019, November. Toward a framework for assessing the cyber-
worthiness of complex mission critical systems. In 2019 Military Communications and
Information Systems Conference (MilCIS) (pp. 1-6). IEEE.
Goel, R., Haddow, J. and Kumar, A., 2018. Managing cybersecurity risk in government: an
implementation model. Report from IBM Center for The Business of Government.
Gupta, R., Tanwar, S., Tyagi, S. and Kumar, N., 2020. Machine learning models for secure data
analytics: A taxonomy and threat model. Computer Communications, 153, pp.406-440.
Leander, B., Čaušević, A. and Hansson, H., 2019, September. Cybersecurity Challenges in Large
Industrial IoT Systems. In 2019 24th IEEE International Conference on Emerging
Technologies and Factory Automation (ETFA) (pp. 1035-1042). IEEE.
Ramon, M.C. and Zajac, D.A., 2018. Cybersecurity Literature Review and Efforts
Report. Prepared for NCHRP Project, pp.03-127.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



