Cybersecurity Risk Assessment Report: Identifying Critical Assets
VerifiedAdded on 2022/09/26
|9
|1875
|36
Report
AI Summary
This report presents a cybersecurity risk assessment, addressing key aspects of information security within an educational institution. It begins by emphasizing the importance of risk assessment as a critical step in developing and managing cybersecurity, while also acknowledging the limitations of current risk assessment methods. The report then focuses on the identification of critical information assets, explaining their value and importance, and provides a template for ranking these assets. A significant portion of the report is dedicated to identifying and analyzing various threats, including ransomware, social engineering, and denial-of-service attacks, and their potential impact on the organization. The report further examines the threat landscape for the organization's website, highlighting vulnerabilities and potential attack vectors. Finally, the report emphasizes the need for robust security controls, including data backups, and cloud computing to mitigate the identified risks. The report includes references to relevant cybersecurity literature.

Running head: CYBER SECURITY
CYBER SECURITY
Name of the Student
Name of the Organization
Author Note
CYBER SECURITY
Name of the Student
Name of the Organization
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER SECURITY
Table of Contents
Importance of the assessment of risk.........................................................................................2
Identification of the Critical asset..............................................................................................2
Template.....................................................................................................................................3
Identification of threat................................................................................................................4
Threat Landscape for the Website..............................................................................................5
References..................................................................................................................................7
CYBER SECURITY
Table of Contents
Importance of the assessment of risk.........................................................................................2
Identification of the Critical asset..............................................................................................2
Template.....................................................................................................................................3
Identification of threat................................................................................................................4
Threat Landscape for the Website..............................................................................................5
References..................................................................................................................................7

2
CYBER SECURITY
Importance of the assessment of risk
Assessment of risk is considered to be a particular term that can be utilised for
describing the entire overall procedure or rather the method where all the several hazards and
also the factors of risks can be identified that possess with the huge potential of causing harm.
It can be said that a cyber-security assessment will be basically a procedure of the
identification, analysis and also the evaluation of the risk (Arachchilage and Love 2014). This
is considered to be the only way of ensuring about the fact that all the several controls of
cyber security which will be chosen must be proper to all the several risks which the
educational institution will be facing. A cyber security assessment of risk will be identifying
all the several assets of information that be highly affected by a kind of cyber-attack like that
of several hardware, software, computer systems and the data of the students. It may be
becoming slight difficult to give a proper training to the team that will be handling with the
risk associated activities or rather the assessment of risk (Conteh and Schmick 2016). Both
the estimation as well as the evaluation of risk is very much essential to be well performed
which will be followed by the process of selecting controls for treating all the risks which
will be identified. It is essential to both review as well as monitor the specific environment of
the educational institute concerned of a various kinds of risks for detecting any kinds of
alternations within the organization and also for maintaining an overview of the entire
procedure of the management of risk (Hartmann and Steup 2013). It is to be well remembered
that the specific feasibility of utilising the assessment of risk acts as a beautiful aid to the
particular procedure of the decision making.
Identification of the Critical asset
An asset of information can be defined as a particular body of the knowledge that will
be both managed as well as organized as a singular entity (Shamala, Ahmad and Yusoff
CYBER SECURITY
Importance of the assessment of risk
Assessment of risk is considered to be a particular term that can be utilised for
describing the entire overall procedure or rather the method where all the several hazards and
also the factors of risks can be identified that possess with the huge potential of causing harm.
It can be said that a cyber-security assessment will be basically a procedure of the
identification, analysis and also the evaluation of the risk (Arachchilage and Love 2014). This
is considered to be the only way of ensuring about the fact that all the several controls of
cyber security which will be chosen must be proper to all the several risks which the
educational institution will be facing. A cyber security assessment of risk will be identifying
all the several assets of information that be highly affected by a kind of cyber-attack like that
of several hardware, software, computer systems and the data of the students. It may be
becoming slight difficult to give a proper training to the team that will be handling with the
risk associated activities or rather the assessment of risk (Conteh and Schmick 2016). Both
the estimation as well as the evaluation of risk is very much essential to be well performed
which will be followed by the process of selecting controls for treating all the risks which
will be identified. It is essential to both review as well as monitor the specific environment of
the educational institute concerned of a various kinds of risks for detecting any kinds of
alternations within the organization and also for maintaining an overview of the entire
procedure of the management of risk (Hartmann and Steup 2013). It is to be well remembered
that the specific feasibility of utilising the assessment of risk acts as a beautiful aid to the
particular procedure of the decision making.
Identification of the Critical asset
An asset of information can be defined as a particular body of the knowledge that will
be both managed as well as organized as a singular entity (Shamala, Ahmad and Yusoff
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CYBER SECURITY
2013). It can be managed as a unit in such a way that it can be well understood, protected as
well as shared. It is to be well known that assets of information possess the value that will be
manageable, content as well as risk. It can be said the information assets are actually the
particular assets of the University that possess financial as well as some other value like some
kinds of the assets which will be physical. Hence, it is very much essential for identifying
them wherever they have been kept and who will be entirely responsible for all of them
(Cartwright EDIFICE TECHNOLOGIES Inc 2014). It must be remembered that the
University must develop a register of the asset of information for helping a lot in both
tracking as well as managing the information assets. Information asset is really considered to
be very much critical as the university or rather any kind of educational institution has to
keep a database, a full collection of a number of contracts as well as agreements or even some
samples of research very much carefully (Cherdantseva et al. 2016). Maintaining that will be
really very much essential but very much tough at the same time. Hence, Register of
Information Asset is really very much important (Safa et al. 2015).
Some of the questions for identifying all of the highly critical assets of information of the
educational organization are:
Is there any kind of risks which are seen to be well associated with the information
which is not at all accurate?
Does the information possess a lifecycle which will be manageable?
Does the asset of information possess a value to the organization and will it be costing
a lot of money for reacquiring the information?
Is there any kind of effect upon the particular efficiency of the operation if anyone
will not be accessing the information with an ease?
CYBER SECURITY
2013). It can be managed as a unit in such a way that it can be well understood, protected as
well as shared. It is to be well known that assets of information possess the value that will be
manageable, content as well as risk. It can be said the information assets are actually the
particular assets of the University that possess financial as well as some other value like some
kinds of the assets which will be physical. Hence, it is very much essential for identifying
them wherever they have been kept and who will be entirely responsible for all of them
(Cartwright EDIFICE TECHNOLOGIES Inc 2014). It must be remembered that the
University must develop a register of the asset of information for helping a lot in both
tracking as well as managing the information assets. Information asset is really considered to
be very much critical as the university or rather any kind of educational institution has to
keep a database, a full collection of a number of contracts as well as agreements or even some
samples of research very much carefully (Cherdantseva et al. 2016). Maintaining that will be
really very much essential but very much tough at the same time. Hence, Register of
Information Asset is really very much important (Safa et al. 2015).
Some of the questions for identifying all of the highly critical assets of information of the
educational organization are:
Is there any kind of risks which are seen to be well associated with the information
which is not at all accurate?
Does the information possess a lifecycle which will be manageable?
Does the asset of information possess a value to the organization and will it be costing
a lot of money for reacquiring the information?
Is there any kind of effect upon the particular efficiency of the operation if anyone
will not be accessing the information with an ease?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CYBER SECURITY
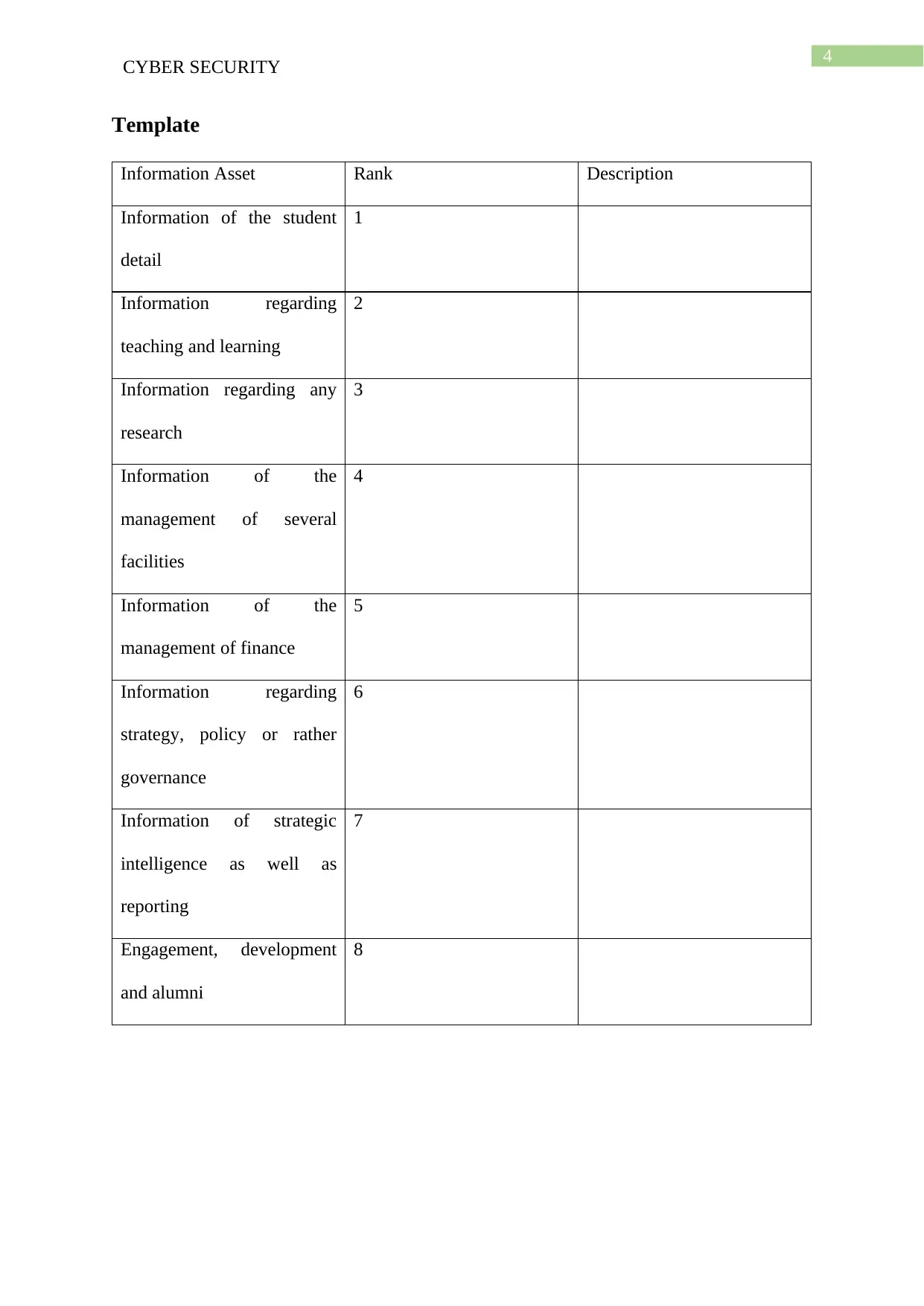
Template
Information Asset Rank Description
Information of the student
detail
1
Information regarding
teaching and learning
2
Information regarding any
research
3
Information of the
management of several
facilities
4
Information of the
management of finance
5
Information regarding
strategy, policy or rather
governance
6
Information of strategic
intelligence as well as
reporting
7
Engagement, development
and alumni
8
CYBER SECURITY
Template
Information Asset Rank Description
Information of the student
detail
1
Information regarding
teaching and learning
2
Information regarding any
research
3
Information of the
management of several
facilities
4
Information of the
management of finance
5
Information regarding
strategy, policy or rather
governance
6
Information of strategic
intelligence as well as
reporting
7
Engagement, development
and alumni
8

5
CYBER SECURITY
Identification of threat
There are a number of threats to the information of the educational organization
which will be involving some kinds of software attacks or rather any kind of malware (Love
et al. 2014). The five threats that can be very much harmful for the educational organization
will be involving ransomware, social engineering, DoS attacks or rather the denial of service
attacks, lack of appropriate controls of security and full outdated policies of security.
Threat can be considered to be anything that can be very much advantageous of a
specific vulnerability for particularly breaching the security and alter or rather harm any
object in a negative manner. It has been observed that the kind of threats which are
considered to be harmful for the organization.
Security threats Rank depending upon the impact
Ransomware 2
Phishing 3
Attacks of denial of service 1
Lack of appropriate controls of security 4
Outdated policies of security 5
Threat Landscape for the Website
The educational institute has been generally utilising a kind of website. But the main
thing which is to be remembered is that there is a huge threat landscape for the website. The
particular ransomware attack has been known to have made with the help of the website only.
For keeping the organization safe, it is very much required for protect the entire system
appropriately (Öğütçü, Testik and Chouseinoglou 2016). Sometimes the attacks are seen to
have been occurring with the help of email. Cyber security is really very much required for
CYBER SECURITY
Identification of threat
There are a number of threats to the information of the educational organization
which will be involving some kinds of software attacks or rather any kind of malware (Love
et al. 2014). The five threats that can be very much harmful for the educational organization
will be involving ransomware, social engineering, DoS attacks or rather the denial of service
attacks, lack of appropriate controls of security and full outdated policies of security.
Threat can be considered to be anything that can be very much advantageous of a
specific vulnerability for particularly breaching the security and alter or rather harm any
object in a negative manner. It has been observed that the kind of threats which are
considered to be harmful for the organization.
Security threats Rank depending upon the impact
Ransomware 2
Phishing 3
Attacks of denial of service 1
Lack of appropriate controls of security 4
Outdated policies of security 5
Threat Landscape for the Website
The educational institute has been generally utilising a kind of website. But the main
thing which is to be remembered is that there is a huge threat landscape for the website. The
particular ransomware attack has been known to have made with the help of the website only.
For keeping the organization safe, it is very much required for protect the entire system
appropriately (Öğütçü, Testik and Chouseinoglou 2016). Sometimes the attacks are seen to
have been occurring with the help of email. Cyber security is really very much required for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER SECURITY
any kind of organization. Ransomware may be totally collapsing the entire system and in
return any hacker may ask for a huge amount of money for the particular key of decryption
for opening the system (Peltier 2016). The attack upon the email can be made via the specific
phishing attack and in such a case of attack, hackers may be trying to steal the password of
the website or rather some other kind of important and confidential data. The mail will be
totally corrupting the system for an important purpose. The DoS attack can be attacking the
website of the educational institute for a number of various notes and the entire system will
be permanently collapsing for this specific attack. This particular attack may be occurring via
the dark web which can be costing about five dollars. The specific tactics of the attack can be
even done by directly receiving a call from the hacker. It is to be known that the website of
the educational institute will be comprising of all the several essential as well as sensitive
documents. The lack of appropriate controls of security and the outdated policies of security
may be leading to a crashing of the website. There is also a high chance that if the hackers do
not obtain the demanded amount of money, the website may be totally crashed for ever and
also the entire document may be lost totally. This is reason a backup of data must always be
kept.
A copy of the data must be stored in a database and the educational organization must
be utilising the computing of cloud and the thereby the data will be stored as the specific
cluster. If any of the cluster or rather data will be totally lost, then a particular copy of the
data must be directly fetched with the help of cloud or rather any kind of secondary device of
storage. It must be said that each and every organization must have their own limit of storing
data from the starting to that of the recent date and hence the problem of big data is also
arising. Storing of data and also the securing of data must be done properly with the help of
the computing of cloud.
CYBER SECURITY
any kind of organization. Ransomware may be totally collapsing the entire system and in
return any hacker may ask for a huge amount of money for the particular key of decryption
for opening the system (Peltier 2016). The attack upon the email can be made via the specific
phishing attack and in such a case of attack, hackers may be trying to steal the password of
the website or rather some other kind of important and confidential data. The mail will be
totally corrupting the system for an important purpose. The DoS attack can be attacking the
website of the educational institute for a number of various notes and the entire system will
be permanently collapsing for this specific attack. This particular attack may be occurring via
the dark web which can be costing about five dollars. The specific tactics of the attack can be
even done by directly receiving a call from the hacker. It is to be known that the website of
the educational institute will be comprising of all the several essential as well as sensitive
documents. The lack of appropriate controls of security and the outdated policies of security
may be leading to a crashing of the website. There is also a high chance that if the hackers do
not obtain the demanded amount of money, the website may be totally crashed for ever and
also the entire document may be lost totally. This is reason a backup of data must always be
kept.
A copy of the data must be stored in a database and the educational organization must
be utilising the computing of cloud and the thereby the data will be stored as the specific
cluster. If any of the cluster or rather data will be totally lost, then a particular copy of the
data must be directly fetched with the help of cloud or rather any kind of secondary device of
storage. It must be said that each and every organization must have their own limit of storing
data from the starting to that of the recent date and hence the problem of big data is also
arising. Storing of data and also the securing of data must be done properly with the help of
the computing of cloud.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CYBER SECURITY
References
Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing
threat avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
Cartwright, K., EDIFICE TECHNOLOGIES Inc, 2014. Systems and methods for capturing,
managing, sharing, and visualising asset information of an organization. U.S. Patent
Application 14/270,196.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K.,
2016. A review of cyber security risk assessment methods for SCADA systems. Computers
& security, 56, pp.1-27.
Conteh, N.Y. and Schmick, P.J., 2016. Cybersecurity: risks, vulnerabilities and
countermeasures to prevent social engineering attacks. International Journal of Advanced
Computer Research, 6(23), p.31.
Hartmann, K. and Steup, C., 2013, June. The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In 2013 5th international conference on cyber conflict
(CYCON 2013) (pp. 1-23). IEEE.
Love, P.E., Matthews, J., Simpson, I., Hill, A. and Olatunji, O.A., 2014. A benefits
realization management building information modeling framework for asset
owners. Automation in construction, 37, pp.1-10.
Öğütçü, G., Testik, Ö.M. and Chouseinoglou, O., 2016. Analysis of personal information
security behavior and awareness. Computers & Security, 56, pp.83-93.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
CYBER SECURITY
References
Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing
threat avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
Cartwright, K., EDIFICE TECHNOLOGIES Inc, 2014. Systems and methods for capturing,
managing, sharing, and visualising asset information of an organization. U.S. Patent
Application 14/270,196.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K.,
2016. A review of cyber security risk assessment methods for SCADA systems. Computers
& security, 56, pp.1-27.
Conteh, N.Y. and Schmick, P.J., 2016. Cybersecurity: risks, vulnerabilities and
countermeasures to prevent social engineering attacks. International Journal of Advanced
Computer Research, 6(23), p.31.
Hartmann, K. and Steup, C., 2013, June. The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In 2013 5th international conference on cyber conflict
(CYCON 2013) (pp. 1-23). IEEE.
Love, P.E., Matthews, J., Simpson, I., Hill, A. and Olatunji, O.A., 2014. A benefits
realization management building information modeling framework for asset
owners. Automation in construction, 37, pp.1-10.
Öğütçü, G., Testik, Ö.M. and Chouseinoglou, O., 2016. Analysis of personal information
security behavior and awareness. Computers & Security, 56, pp.83-93.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.

8
CYBER SECURITY
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015.
Information security conscious care behaviour formation in organizations. Computers &
Security, 53, pp.65-78.
Shamala, P., Ahmad, R. and Yusoff, M., 2013. A conceptual framework of info structure for
information security risk assessment (ISRA). Journal of Information Security and
Applications, 18(1), pp.45-52.
CYBER SECURITY
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015.
Information security conscious care behaviour formation in organizations. Computers &
Security, 53, pp.65-78.
Shamala, P., Ahmad, R. and Yusoff, M., 2013. A conceptual framework of info structure for
information security risk assessment (ISRA). Journal of Information Security and
Applications, 18(1), pp.45-52.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





