Analyzing Cybersecurity Challenges and Solutions for Business Orgs
VerifiedAdded on 2023/06/12
|13
|2983
|68
Report
AI Summary
This report investigates the cybersecurity challenges encountered by business organizations in today's digital landscape. It begins by outlining the increasing reliance on internet technologies and the consequent rise in cyber threats. The project objective is to determine the security measures implemented by organizations to counter these threats, providing insights into cybersecurity techniques and threat management strategies. The scope of the report encompasses the significance of cybersecurity in modern business, reviewing literature on cyber-attacks, ransomware, AI expansion, IoT threats, blockchain revolution, serverless application vulnerabilities, drone jacking, social engineering, insider threats, machine learning, mobile malware, false advertisements, firewall absence, cloud configuration monitoring, and high-impact attacks. Research questions focus on identifying the cybersecurity challenges faced by businesses and the security measures they should adopt. The research methodology employs both primary (interviews and surveys) and secondary data collection methods, utilizing qualitative and quantitative techniques to gather comprehensive data. The report acknowledges limitations such as time constraints and concludes with a discussion of findings and recommendations.

Business Research Proposal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................3
Project Objective.............................................................................................................................3
Project Scope...................................................................................................................................4
Literature Review............................................................................................................................4
Research Questions/Hypotheses......................................................................................................8
Research Design and Methodology.................................................................................................8
Research Approach......................................................................................................................9
Research Limitations.....................................................................................................................10
Time Schedule (Research plan) Gantt chart..................................................................................10
Conclusion.....................................................................................................................................11
References......................................................................................................................................11
Introduction......................................................................................................................................3
Project Objective.............................................................................................................................3
Project Scope...................................................................................................................................4
Literature Review............................................................................................................................4
Research Questions/Hypotheses......................................................................................................8
Research Design and Methodology.................................................................................................8
Research Approach......................................................................................................................9
Research Limitations.....................................................................................................................10
Time Schedule (Research plan) Gantt chart..................................................................................10
Conclusion.....................................................................................................................................11
References......................................................................................................................................11

Introduction
In the modern world, the use of internet is increasing day by day and business organizations are
not exceptions. The excessive use of ultra-modern technology has changed the approach of
business organizations towards the customers. Cyber-security includes different technologies
designed to protect the systems, data, and information from various types of cyber-attacks (The
Economic Times, 2018). Majority of organizations are implementing technological tools to
perform business operations. Thus, the main challenge in front of the management of business
organizations is to protect the systems from being infected through various types of potential
online threats. The report discussed about the determination of challenges being faced by the
business organizations through cyber-security.
Project Objective
The objective of the research is to determine various types of security measures implemented by
the organizations in order to counter the threats posed by various types of cyber-attacks. It will
provide knowledge regarding the cyber-security techniques to be implemented by the business
organizations and the ways through which, such threats are handled (IT Governance, 2018). In
addition, the objective of the research is to provide insights into the cyber-security world and the
challenges being faced by the business organizations due to cyber-threats. It will provide
significant information related to the cyber-security and the ways of implementing cyber-security
in the business organizations.
In the modern world, the use of internet is increasing day by day and business organizations are
not exceptions. The excessive use of ultra-modern technology has changed the approach of
business organizations towards the customers. Cyber-security includes different technologies
designed to protect the systems, data, and information from various types of cyber-attacks (The
Economic Times, 2018). Majority of organizations are implementing technological tools to
perform business operations. Thus, the main challenge in front of the management of business
organizations is to protect the systems from being infected through various types of potential
online threats. The report discussed about the determination of challenges being faced by the
business organizations through cyber-security.
Project Objective
The objective of the research is to determine various types of security measures implemented by
the organizations in order to counter the threats posed by various types of cyber-attacks. It will
provide knowledge regarding the cyber-security techniques to be implemented by the business
organizations and the ways through which, such threats are handled (IT Governance, 2018). In
addition, the objective of the research is to provide insights into the cyber-security world and the
challenges being faced by the business organizations due to cyber-threats. It will provide
significant information related to the cyber-security and the ways of implementing cyber-security
in the business organizations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Scope
Cyber-security is a significant topic in the present scenario for the business organizations (Cisco,
2018). Most of the organizations implementing computer technologies for business purposes face
issues related to cyber-security. The report provides information related to the cyber-security and
cyber-threats because of which, the scope of the report is highly significant.
Literature Review
Cyber Security refers to the technologies and practices constructed to protect various networks,
programs and devices from cyber-attacks by virus, spam and various online attacks (Fielder,
Panaousis, Malacaria, Hankin, & Smeraldi, 2016). Cyber-security has become the need of
business organizations as they have to store, collect, and analyze information on computers. The
leakage of sensitive data and information could harm the business operations as well as its
reputation (Secureworks, 2017). The increasing cyber-attacks have become a serious issue as
majority of business organizations have become highly vulnerable to different types of cyber-
attacks (Graham, Olson, & Howard, 2016). It requires effective defense mechanisms to be
implemented by the organizations from the point of view of internet and computer technologies.
The rate of cybercrimes is increasing and such an alarming increase will be a great source of
problem for business organizations due to which, they are investing a lot in hiring number of IT
professionals in order to prevent their businesses from such crimes (Robert, 2018). In 2017 only,
number of business organizations had spent around $86.4 billion over cyber-security measures
and numbers of challenges still exist such as;
Evolution of Ransomware- Ransomware viruses disrupt the operations of business
organizations and are aimed by the attackers with an intention to demand as per their
Cyber-security is a significant topic in the present scenario for the business organizations (Cisco,
2018). Most of the organizations implementing computer technologies for business purposes face
issues related to cyber-security. The report provides information related to the cyber-security and
cyber-threats because of which, the scope of the report is highly significant.
Literature Review
Cyber Security refers to the technologies and practices constructed to protect various networks,
programs and devices from cyber-attacks by virus, spam and various online attacks (Fielder,
Panaousis, Malacaria, Hankin, & Smeraldi, 2016). Cyber-security has become the need of
business organizations as they have to store, collect, and analyze information on computers. The
leakage of sensitive data and information could harm the business operations as well as its
reputation (Secureworks, 2017). The increasing cyber-attacks have become a serious issue as
majority of business organizations have become highly vulnerable to different types of cyber-
attacks (Graham, Olson, & Howard, 2016). It requires effective defense mechanisms to be
implemented by the organizations from the point of view of internet and computer technologies.
The rate of cybercrimes is increasing and such an alarming increase will be a great source of
problem for business organizations due to which, they are investing a lot in hiring number of IT
professionals in order to prevent their businesses from such crimes (Robert, 2018). In 2017 only,
number of business organizations had spent around $86.4 billion over cyber-security measures
and numbers of challenges still exist such as;
Evolution of Ransomware- Ransomware viruses disrupt the operations of business
organizations and are aimed by the attackers with an intention to demand as per their
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

choice from the victims. Once the demands of the attackers, which are generally
financial, are fulfilled, such viruses can be removed by the systems. It has been found that
more than 77% of the malicious items on internet are malwares and a single mistake by
the business organizations could destroy their operating systems and servers completely.
Despite knowing this, majority of organizations do not take it seriously which provides
easy target to the hackers and they loot huge amount of ransoms form business persons
by infecting their systems with such viruses (Giles, 2018).
Al Expansion- Artificial intelligence is well-known for fighting against all types of
cyber-attacks. Business organizations all over the world are spending artificial
intelligence in order to measure the risks of cyber-attacks to their businesses. The
development in the field of robotics is advantageous for business sector as it does not
require any expenses except on their maintenance and it functions 24X7 as well. The
robotics is beneficial because it works hand in hand with the IT experts to counter threats
posed by variety of malicious software (Ashenden & Lawrence, 2016).
IoT threats- Majority of business organizations rely on internet for marketing and
advertisements to approach maximum number of customers. On one hand, where Internet
of Things (IoT) has eased the process, on the other hand, it has increased probability of
cyber-threats. The increasing interconnections in the complex web of internet make the
organizations susceptible to threats because of insecure web interfaces, data transfers,
inadequate communication methods and lack of effective security measures (Carr, 2016).
Thus, it is essential for the business organizations to adopt security measures such as
secured password, user verification codes, two factor authentication and other complex
security measures to avoid such risks (Doell, 2012).
financial, are fulfilled, such viruses can be removed by the systems. It has been found that
more than 77% of the malicious items on internet are malwares and a single mistake by
the business organizations could destroy their operating systems and servers completely.
Despite knowing this, majority of organizations do not take it seriously which provides
easy target to the hackers and they loot huge amount of ransoms form business persons
by infecting their systems with such viruses (Giles, 2018).
Al Expansion- Artificial intelligence is well-known for fighting against all types of
cyber-attacks. Business organizations all over the world are spending artificial
intelligence in order to measure the risks of cyber-attacks to their businesses. The
development in the field of robotics is advantageous for business sector as it does not
require any expenses except on their maintenance and it functions 24X7 as well. The
robotics is beneficial because it works hand in hand with the IT experts to counter threats
posed by variety of malicious software (Ashenden & Lawrence, 2016).
IoT threats- Majority of business organizations rely on internet for marketing and
advertisements to approach maximum number of customers. On one hand, where Internet
of Things (IoT) has eased the process, on the other hand, it has increased probability of
cyber-threats. The increasing interconnections in the complex web of internet make the
organizations susceptible to threats because of insecure web interfaces, data transfers,
inadequate communication methods and lack of effective security measures (Carr, 2016).
Thus, it is essential for the business organizations to adopt security measures such as
secured password, user verification codes, two factor authentication and other complex
security measures to avoid such risks (Doell, 2012).

Block chain Revolution- Crypto-currencies such as Bit coin are developed upon block
chains and is a technical innovation along with a decentralized and secure record of
transactions. Business organizations are focusing on block chain enabling various forms
of decentralized access control (Xu, et al., 2015).
Vulnerability of server less applications- The data and information about the customers
in business organizations are at high risk because server less applications could easily
invite cyber-attacks. The information in generally stored in cloud servers can easily be
accessed by all the devices and are vulnerable to cyber-attacks (Nibusinessinfo, 2018).
Drone jacking- With the increasing use of drones for business purposes by business
organizations, cyber-attackers utilize the opportunity to hijack the drones.
Social Engineering- The social engineering has made it possible for the attackers to hack
the systems such as phishing technology deceive important data and information and
utilize them to hack systems easily. It requires installing anti-phishing technology to
secure the systems from hackers (Knowles, Prince, Hutchison, Disso, & Jones, 2015).
Insider threats- Internal threats are also considered as harmful and data breaches caused
due to malicious intent of workforce provide attackers with the opportunity to get
benefited out of it (Kohler, 2017).
Machine learning- The machine learning algorithms are used to determine various
frauds and determine success rate of various types of marketing campaigns as well as
various other innovative applications.
Mobile Malware- Mobiles are also under cyber-threats because viruses spread through
various applications. Through antivirus software, various types of mobile malwares can
be countered (Shackleford, 2015).
chains and is a technical innovation along with a decentralized and secure record of
transactions. Business organizations are focusing on block chain enabling various forms
of decentralized access control (Xu, et al., 2015).
Vulnerability of server less applications- The data and information about the customers
in business organizations are at high risk because server less applications could easily
invite cyber-attacks. The information in generally stored in cloud servers can easily be
accessed by all the devices and are vulnerable to cyber-attacks (Nibusinessinfo, 2018).
Drone jacking- With the increasing use of drones for business purposes by business
organizations, cyber-attackers utilize the opportunity to hijack the drones.
Social Engineering- The social engineering has made it possible for the attackers to hack
the systems such as phishing technology deceive important data and information and
utilize them to hack systems easily. It requires installing anti-phishing technology to
secure the systems from hackers (Knowles, Prince, Hutchison, Disso, & Jones, 2015).
Insider threats- Internal threats are also considered as harmful and data breaches caused
due to malicious intent of workforce provide attackers with the opportunity to get
benefited out of it (Kohler, 2017).
Machine learning- The machine learning algorithms are used to determine various
frauds and determine success rate of various types of marketing campaigns as well as
various other innovative applications.
Mobile Malware- Mobiles are also under cyber-threats because viruses spread through
various applications. Through antivirus software, various types of mobile malwares can
be countered (Shackleford, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

False advertisements and different feedbacks- Customers often fall in the trap of
attackers because of false advertisements of business organizations on social sites which
affect the operations and reputation of the organizations (Davis, 2014).
Absence of firewall- The absence of firewall in majority of servers in business
organizations or because of existence of outmoded ones is a threat to business
organizations and beneficial for hackers. The implementation of new firewall system can
be beneficial.
Monitoring Cloud Configuration and Security- The cloud monitoring software and
security checks are essential for business organizations to ensure safety and integrity
(Alton, 2018). The security procedures should be updated in order to get protected from
the attacks by new hacking technologies.
High Impact Attacks- The attack of viruses such as Wannacry and Shamoon v2 disturb
the overall performance of the organization and it is essential for the organizations to
remain updated with effective security measures.
Therefore, it has been revealed that there are various types of cyber-threats challenging for the
business organizations as almost all the business organizations utilize computing devices and
internet for business purposes. There is requirement of advanced expertise along with effective
security measures to get rid of such issues arising now and then in the organizations (WaterISAC
Security Information Center, 2015). The information related to cyber-threats have been
explained in previous researches but the information regarding what measures should be taken to
prevent or combat such attacks, have not been discussed in majority of the research studies. So,
this report will provide information related to the security measures along with various types of
cyber-attacks in trend for the business organizations.
attackers because of false advertisements of business organizations on social sites which
affect the operations and reputation of the organizations (Davis, 2014).
Absence of firewall- The absence of firewall in majority of servers in business
organizations or because of existence of outmoded ones is a threat to business
organizations and beneficial for hackers. The implementation of new firewall system can
be beneficial.
Monitoring Cloud Configuration and Security- The cloud monitoring software and
security checks are essential for business organizations to ensure safety and integrity
(Alton, 2018). The security procedures should be updated in order to get protected from
the attacks by new hacking technologies.
High Impact Attacks- The attack of viruses such as Wannacry and Shamoon v2 disturb
the overall performance of the organization and it is essential for the organizations to
remain updated with effective security measures.
Therefore, it has been revealed that there are various types of cyber-threats challenging for the
business organizations as almost all the business organizations utilize computing devices and
internet for business purposes. There is requirement of advanced expertise along with effective
security measures to get rid of such issues arising now and then in the organizations (WaterISAC
Security Information Center, 2015). The information related to cyber-threats have been
explained in previous researches but the information regarding what measures should be taken to
prevent or combat such attacks, have not been discussed in majority of the research studies. So,
this report will provide information related to the security measures along with various types of
cyber-attacks in trend for the business organizations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research Questions/Hypotheses
The report discusses about the cyber-security issues being faced by the business organizations as
well as appropriate security measures to be taken by them to overcome such issues. In this
context, the report will answer the following research question and the sub-questions;
What are the challenges being faced by business organizations with regard to cyber-
security?
i. Which are those cyber-threats that influence the performance and reputation of business
organizations?
ii. What type of security measures should be adopted by the business organizations to
combat such threats?
Research Design and Methodology
The research methodology is considered as a methodical or systematic way to solve a problem. It
is known as a science of studying how to carry out a research (Rajasekar, Philominathan, &
Chinnathambi, 2013). To gather information for the purpose of answering research question, the
report will utilize both the methods of data collection i.e. primary as well as secondary. The
secondary data will be gathered from the previous researches conducted by proficient researchers
along with reports, books and various other online resources to assist in the research purpose.
The primary mode of data collection will include interviews and surveys in order to collect first-
hand data which will provide information related to the opinion of people regarding the research
issue.
The report discusses about the cyber-security issues being faced by the business organizations as
well as appropriate security measures to be taken by them to overcome such issues. In this
context, the report will answer the following research question and the sub-questions;
What are the challenges being faced by business organizations with regard to cyber-
security?
i. Which are those cyber-threats that influence the performance and reputation of business
organizations?
ii. What type of security measures should be adopted by the business organizations to
combat such threats?
Research Design and Methodology
The research methodology is considered as a methodical or systematic way to solve a problem. It
is known as a science of studying how to carry out a research (Rajasekar, Philominathan, &
Chinnathambi, 2013). To gather information for the purpose of answering research question, the
report will utilize both the methods of data collection i.e. primary as well as secondary. The
secondary data will be gathered from the previous researches conducted by proficient researchers
along with reports, books and various other online resources to assist in the research purpose.
The primary mode of data collection will include interviews and surveys in order to collect first-
hand data which will provide information related to the opinion of people regarding the research
issue.

Research Approach
For qualitative technique of data collection, interviews will be conducted with the computer
experts of the business organizations, which will provide information related to the issues being
faced by the organizations regarding cyber-security and the measures in place to fight against
such problems. The convenient non-probability sampling technique will be utilized for the
selection of participants to be interviewed and the sample size would be 3. The mode of data
collection will be structured questionnaire which will contain 10 open-ended questions to be
asked from the interview participants. The face-to-face interviews will be taken on the
convenience of the participants and responses will then be analyzed comprehensively.
For quantitative technique of data collection, surveys will be conducted with the computer users
of the business organizations to gather the information regarding the issues faced by them in
cases of systems getting affected with the viruses and the challenges they have to face because of
loss of data and information due to cyber-attacks. The random probability sampling methods will
be used to select the survey participants and the sample size will be 30. The survey will be
conducted by preparing online questionnaire to the survey participants. The questionnaire will be
uploaded on survey monkey and mailed to the participants to be filled by them on their
convenience. The number of questions will be 25, out of which, 5 will be demographic
questions. The respondents will have to answer the questions on the scale of 1 to 5 wherein, 5
stand for ‘Strongly agree’ and 1 stand for ‘Strongly Disagree’. The data collected through survey
will be compiled by the utilization of MS-Excel. For the purpose of visualizing the data, pie
charts will be used which will assist in analysis of data. The reliability of the data instrument will
be tested using Cronbach’s alpha coefficient. If the value of Cronbach’s alpha coefficient is
For qualitative technique of data collection, interviews will be conducted with the computer
experts of the business organizations, which will provide information related to the issues being
faced by the organizations regarding cyber-security and the measures in place to fight against
such problems. The convenient non-probability sampling technique will be utilized for the
selection of participants to be interviewed and the sample size would be 3. The mode of data
collection will be structured questionnaire which will contain 10 open-ended questions to be
asked from the interview participants. The face-to-face interviews will be taken on the
convenience of the participants and responses will then be analyzed comprehensively.
For quantitative technique of data collection, surveys will be conducted with the computer users
of the business organizations to gather the information regarding the issues faced by them in
cases of systems getting affected with the viruses and the challenges they have to face because of
loss of data and information due to cyber-attacks. The random probability sampling methods will
be used to select the survey participants and the sample size will be 30. The survey will be
conducted by preparing online questionnaire to the survey participants. The questionnaire will be
uploaded on survey monkey and mailed to the participants to be filled by them on their
convenience. The number of questions will be 25, out of which, 5 will be demographic
questions. The respondents will have to answer the questions on the scale of 1 to 5 wherein, 5
stand for ‘Strongly agree’ and 1 stand for ‘Strongly Disagree’. The data collected through survey
will be compiled by the utilization of MS-Excel. For the purpose of visualizing the data, pie
charts will be used which will assist in analysis of data. The reliability of the data instrument will
be tested using Cronbach’s alpha coefficient. If the value of Cronbach’s alpha coefficient is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
greater than 0.7, instrument is reliable. The validity of instrument will be ensured by getting
questionnaires review from experts related to research area.
Research Limitations
The limitations of this research might be time constraints as more time will be required to collect
relevant information from survey and interview respondents. To collect data on the convenience
of the respondents will require more time consumption and the research is required to be
conducted within predefined duration. It might hamper the results of the research within
restricted time-period.
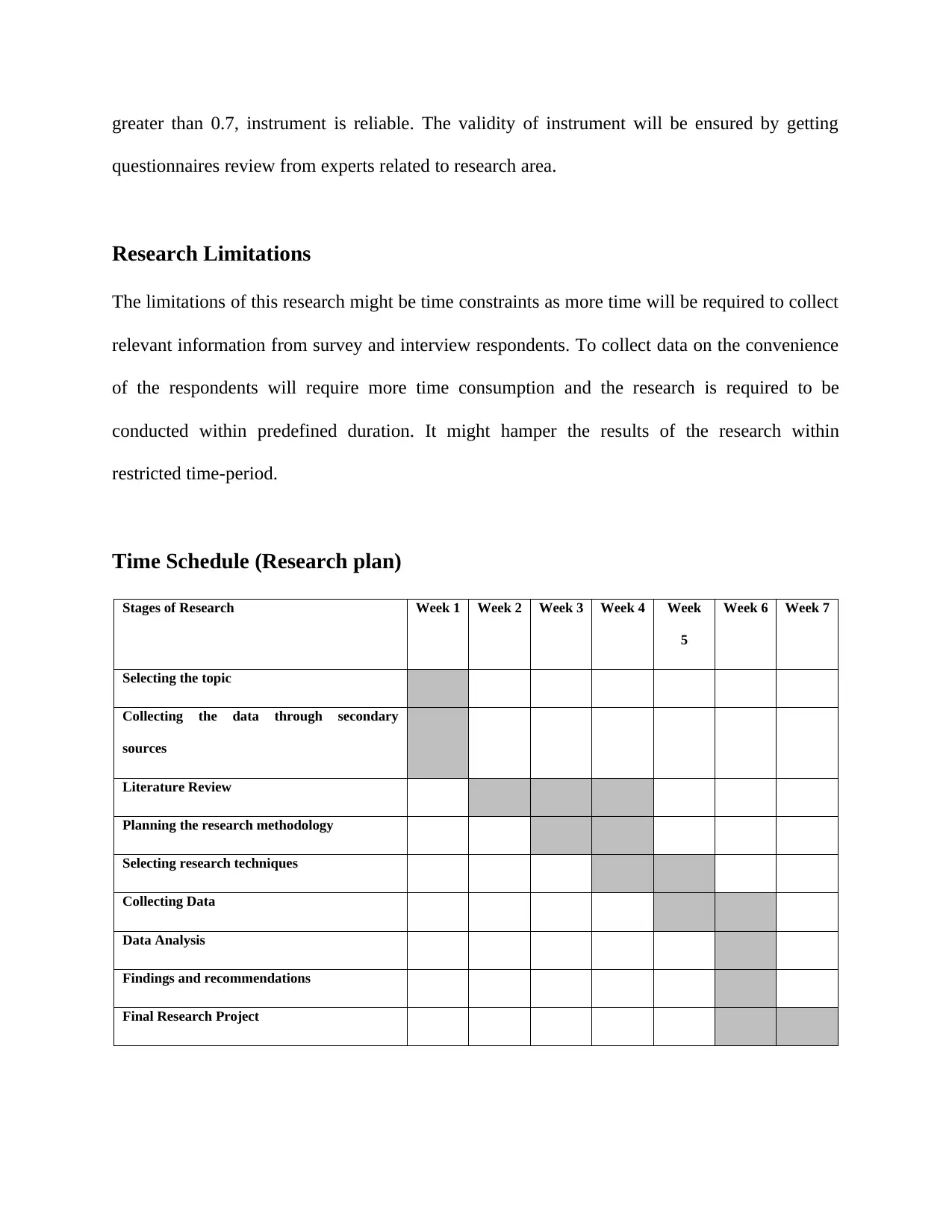
Time Schedule (Research plan)
Stages of Research Week 1 Week 2 Week 3 Week 4 Week
5
Week 6 Week 7
Selecting the topic
Collecting the data through secondary
sources
Literature Review
Planning the research methodology
Selecting research techniques
Collecting Data
Data Analysis
Findings and recommendations
Final Research Project
questionnaires review from experts related to research area.
Research Limitations
The limitations of this research might be time constraints as more time will be required to collect
relevant information from survey and interview respondents. To collect data on the convenience
of the respondents will require more time consumption and the research is required to be
conducted within predefined duration. It might hamper the results of the research within
restricted time-period.
Time Schedule (Research plan)
Stages of Research Week 1 Week 2 Week 3 Week 4 Week
5
Week 6 Week 7
Selecting the topic
Collecting the data through secondary
sources
Literature Review
Planning the research methodology
Selecting research techniques
Collecting Data
Data Analysis
Findings and recommendations
Final Research Project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
The proposal of the research will assist in conducting the research as per the demands and
requirements of the research. Through it, proper guidelines will be followed for achieving the
research purpose. It will be beneficial for conducting the research within specific time-period as
well as to obtain desired outcomes. All the procedures to be included while conducting the
research are already predetermined which will ease the process and delays will also be avoided.
The research relates to the modern world requirements as almost all the business organizations
utilize internet services and computing devices for achieving business purposes. The following
research will focus on the challenges faced by the business organizations regarding
cybersecurity. The research is significant as it will find solutions to such cyber-security threats
which would be beneficial for the business organizations.
References
WaterISAC Security Information Center. (2015). 10 Basic Cybersecurity Measures Best
Practices to Reduce Exploitable Weaknesses and Attacks. Retrieved May 24, 2018, from
Ics-cert.us-cert.gov:
https://ics-cert.us-cert.gov/sites/default/files/documents/10_Basic_Cybersecurity_Measur
es-WaterISAC_June2015_S508C.pdf
Alton, L. (2018). 5 Cybersecurity Measures Every Small Business Should Take This Year.
Retrieved May 24, 2018, from Allbusiness.com:
https://www.allbusiness.com/countdown-to-2016-4-reasons-you-must-update-your-
business-software-102555-1.html
The proposal of the research will assist in conducting the research as per the demands and
requirements of the research. Through it, proper guidelines will be followed for achieving the
research purpose. It will be beneficial for conducting the research within specific time-period as
well as to obtain desired outcomes. All the procedures to be included while conducting the
research are already predetermined which will ease the process and delays will also be avoided.
The research relates to the modern world requirements as almost all the business organizations
utilize internet services and computing devices for achieving business purposes. The following
research will focus on the challenges faced by the business organizations regarding
cybersecurity. The research is significant as it will find solutions to such cyber-security threats
which would be beneficial for the business organizations.
References
WaterISAC Security Information Center. (2015). 10 Basic Cybersecurity Measures Best
Practices to Reduce Exploitable Weaknesses and Attacks. Retrieved May 24, 2018, from
Ics-cert.us-cert.gov:
https://ics-cert.us-cert.gov/sites/default/files/documents/10_Basic_Cybersecurity_Measur
es-WaterISAC_June2015_S508C.pdf
Alton, L. (2018). 5 Cybersecurity Measures Every Small Business Should Take This Year.
Retrieved May 24, 2018, from Allbusiness.com:
https://www.allbusiness.com/countdown-to-2016-4-reasons-you-must-update-your-
business-software-102555-1.html

Ashenden, D., & Lawrence, D. (2016). Security dialogues: Building better relationships between
security and business. IEEE Security & Privacy, 14(3), 82-87.
Carr, M. (2016). Public–private partnerships in national cyber‐security strategies. International
Affairs, 92(1), 43-62.
Cisco. (2018). What Is Cybersecurity? Retrieved May 24, 2018, from cisco.com:
https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html
Davis, R. (2014). 10 Cyber Security Measures That Every Small Business Must Take. Retrieved
May 24, 2018, from Tech.co: https://tech.co/10-cyber-security-measures-every-small-
business-must-take-2014-11
Doell, L. (2012). 10 essential cybersecurity measures. Retrieved May 24, 2018, from
Americanexpress.com:
https://www.americanexpress.com/us/small-business/openforum/articles/10-essential-
cybersecurity-measures/
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C., & Smeraldi, F. (2016). Decision support
approaches for cyber security investment. Decision Support Systems, 86, 13-23.
Giles, M. (2018). Six Cyber Threats to Really Worry About in 2018. Retrieved May 24, 2018,
from Technologyreview.com: https://www.technologyreview.com/s/609641/six-cyber-
threats-to-really-worry-about-in-2018/
Graham, J., Olson, R., & Howard, R. (2016). Cyber security essentials. CRC Press.
IT Governance. (2018). What is cyber security? Retrieved May 24, 2018, from
itgovernance.co.uk: https://www.itgovernance.co.uk/what-is-cybersecurity
Knowles, W., Prince, D., Hutchison, D., Disso, J. F., & Jones, K. (2015). A survey of cyber
security management in industrial control systems. International journal of critical
security and business. IEEE Security & Privacy, 14(3), 82-87.
Carr, M. (2016). Public–private partnerships in national cyber‐security strategies. International
Affairs, 92(1), 43-62.
Cisco. (2018). What Is Cybersecurity? Retrieved May 24, 2018, from cisco.com:
https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html
Davis, R. (2014). 10 Cyber Security Measures That Every Small Business Must Take. Retrieved
May 24, 2018, from Tech.co: https://tech.co/10-cyber-security-measures-every-small-
business-must-take-2014-11
Doell, L. (2012). 10 essential cybersecurity measures. Retrieved May 24, 2018, from
Americanexpress.com:
https://www.americanexpress.com/us/small-business/openforum/articles/10-essential-
cybersecurity-measures/
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C., & Smeraldi, F. (2016). Decision support
approaches for cyber security investment. Decision Support Systems, 86, 13-23.
Giles, M. (2018). Six Cyber Threats to Really Worry About in 2018. Retrieved May 24, 2018,
from Technologyreview.com: https://www.technologyreview.com/s/609641/six-cyber-
threats-to-really-worry-about-in-2018/
Graham, J., Olson, R., & Howard, R. (2016). Cyber security essentials. CRC Press.
IT Governance. (2018). What is cyber security? Retrieved May 24, 2018, from
itgovernance.co.uk: https://www.itgovernance.co.uk/what-is-cybersecurity
Knowles, W., Prince, D., Hutchison, D., Disso, J. F., & Jones, K. (2015). A survey of cyber
security management in industrial control systems. International journal of critical
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





