Cybersecurity Research Report: Threats, Measures, and Analysis
VerifiedAdded on 2019/11/08
|12
|2755
|166
Report
AI Summary
This report presents a comprehensive analysis of cybersecurity, focusing on the threats, prevention measures, and research methodologies employed in the field. The study begins with an introduction to cybersecurity, highlighting its importance in safeguarding digital environments from cyber-attacks. It outlines the project objective, which is to research cybersecurity parameters and prevention methods to mitigate data loss. The research scope encompasses analyzing cyber-crimes, their impact, and the countermeasures used to secure systems. A thorough literature review examines various research papers and articles on cyber-security. The report formulates primary and secondary research questions to guide the study and establishes research hypotheses regarding preventive measures and their impact on cybersecurity. The research design incorporates both qualitative and quantitative methodologies, including observation, interviews, document reviews, and the use of honeypots. The report also acknowledges research limitations, such as the scope of participant users and communication with IT experts. A detailed time schedule outlines the research plan, from topic selection to report completion. The conclusion summarizes the key findings and emphasizes the importance of proactive cybersecurity measures. The report aims to provide insights into cybersecurity challenges and offer recommendations for enhancing digital security.
Assignment on Business Research
2017
2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
1. Introduction.........................................................................................................................2
2. Project Objective.................................................................................................................2
3. Project Scope......................................................................................................................2
4. Literature Review...............................................................................................................2
5. Research question:..............................................................................................................3
Primary question:....................................................................................................................3
Secondary Question................................................................................................................3
6. Research Hypothesis...........................................................................................................4
7. Research Design ad methodology.......................................................................................6
Qualitative Research...............................................................................................................6
Quantitative Research.............................................................................................................7
8. Research Limitation............................................................................................................7
9. Time Schedule of the research plan....................................................................................8
10. Conclusion.......................................................................................................................9
11. References.......................................................................................................................9
1
1. Introduction.........................................................................................................................2
2. Project Objective.................................................................................................................2
3. Project Scope......................................................................................................................2
4. Literature Review...............................................................................................................2
5. Research question:..............................................................................................................3
Primary question:....................................................................................................................3
Secondary Question................................................................................................................3
6. Research Hypothesis...........................................................................................................4
7. Research Design ad methodology.......................................................................................6
Qualitative Research...............................................................................................................6
Quantitative Research.............................................................................................................7
8. Research Limitation............................................................................................................7
9. Time Schedule of the research plan....................................................................................8
10. Conclusion.......................................................................................................................9
11. References.......................................................................................................................9
1

1. Introduction
The cyber-security is the set of standards and principles used for securing digital
environment. It helps in safeguarding the digital infrastructure from cyber-attack. The cyber-
criminal activities are mainly associated with the fetching of the confidential information of
the user, manipulation and modification in the information available on the internet,
controlling of business activities, and many other (Tong, 2013). The step should be taken to
provide prevention control mechanism for overcoming and resolving the issues associated
with the digital activities performed on the internet. The cyber security strategies should be
built for getting best quality result of resolving security issues. The technological devices
should be placed with the international standards for preventing the system for cyber-criminal
activities.
2. Project Objective
The objective of the project is to research on the need of cyber security parameters. The
increasing rate of cyber-crime affects the working of the organization. The research should be
organized which helps in developing the key parameters of security for preventing loss of
data due to the occurrence of cyber-crime activity. The research helps in determining the
prevention methods which plays an important role in providing solution to the security
problems.
3. Project Scope
The research scope is to analyse the cyber-security system and the prevention methods which
should be taken to make secure the system with the deployment of vulnerabilities and other
associated attacks. The focus should be given on analysing the cyber-crimes occurrence and
the impact, countermeasures used for securing the system, and cyber threats associated with
the security infrastructure.
4. Literature Review
The analysis of various research papers and articles has been done to carry over the research
study on determining the facts and figures associated with the cyber-security (Faris, 2010).
The online and offline resources are used for collecting data on cyber –crimes and proactive
action plan which should be taken by the experts. The cyber-crime can be conducted at
2
The cyber-security is the set of standards and principles used for securing digital
environment. It helps in safeguarding the digital infrastructure from cyber-attack. The cyber-
criminal activities are mainly associated with the fetching of the confidential information of
the user, manipulation and modification in the information available on the internet,
controlling of business activities, and many other (Tong, 2013). The step should be taken to
provide prevention control mechanism for overcoming and resolving the issues associated
with the digital activities performed on the internet. The cyber security strategies should be
built for getting best quality result of resolving security issues. The technological devices
should be placed with the international standards for preventing the system for cyber-criminal
activities.
2. Project Objective
The objective of the project is to research on the need of cyber security parameters. The
increasing rate of cyber-crime affects the working of the organization. The research should be
organized which helps in developing the key parameters of security for preventing loss of
data due to the occurrence of cyber-crime activity. The research helps in determining the
prevention methods which plays an important role in providing solution to the security
problems.
3. Project Scope
The research scope is to analyse the cyber-security system and the prevention methods which
should be taken to make secure the system with the deployment of vulnerabilities and other
associated attacks. The focus should be given on analysing the cyber-crimes occurrence and
the impact, countermeasures used for securing the system, and cyber threats associated with
the security infrastructure.
4. Literature Review
The analysis of various research papers and articles has been done to carry over the research
study on determining the facts and figures associated with the cyber-security (Faris, 2010).
The online and offline resources are used for collecting data on cyber –crimes and proactive
action plan which should be taken by the experts. The cyber-crime can be conducted at
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

international level by the cyber-criminals. The innovation in the field of digital life increases
the activity of cyber-crime. Hacking and phishing are the major attacks which are associated
with digital world. The cyber-criminal activities are mainly associated with the fetching of
the confidential information of the user, manipulation and modification in the information
available on the internet, controlling of business activities, and many other (Edgar, 2010).
The contamination of the system can be resolved with the use of cyber security system. The
capacity of the system can be enhanced with the use digital security method. The one time
password generation is the effective technique used for securing the system. The cyber
security guidelines and principles should be used for expanding the security policies of the
organization. The innovation in the cyber-security helps in resolving the issues of cyber-
crime. The risks management plan helps in identifying the threats and risks associated with
the digital network. The cyber-security is the set of standards and principles used for securing
digital environment. It helps in safeguarding the digital infrastructure from cyber-attack. The
subsequent risks mitigation plans should be developed according to the identified risks. The
expertise in cyber security helps in managing the security issues of the digital tools and
technologies. The cyber security strategies should be built for getting best quality result of
resolving security issues. The cyber security challenges which come forth are categorised as
hacking, phishing attack, virus and malware attack, and other. The intrusion detection and
prevention method should be used for developing the security framework for the
organization. The loss of the data can be minimized with the use of intrusion detection and
prevention method and other security measures within the curriculum of the organization
5. Research question:
The research questions helps in taking the research in right direction. The research questions
which are undertaken to perform the research activities are depicted below:
Primary question:
What are the preventive and control measures taken to overcome the situation of
security threats?
Secondary Question
What are the devices and activities which should be protected against the occurrence
of cyber-criminal offence?
What is the reason behind the success of the intrusion?
3
the activity of cyber-crime. Hacking and phishing are the major attacks which are associated
with digital world. The cyber-criminal activities are mainly associated with the fetching of
the confidential information of the user, manipulation and modification in the information
available on the internet, controlling of business activities, and many other (Edgar, 2010).
The contamination of the system can be resolved with the use of cyber security system. The
capacity of the system can be enhanced with the use digital security method. The one time
password generation is the effective technique used for securing the system. The cyber
security guidelines and principles should be used for expanding the security policies of the
organization. The innovation in the cyber-security helps in resolving the issues of cyber-
crime. The risks management plan helps in identifying the threats and risks associated with
the digital network. The cyber-security is the set of standards and principles used for securing
digital environment. It helps in safeguarding the digital infrastructure from cyber-attack. The
subsequent risks mitigation plans should be developed according to the identified risks. The
expertise in cyber security helps in managing the security issues of the digital tools and
technologies. The cyber security strategies should be built for getting best quality result of
resolving security issues. The cyber security challenges which come forth are categorised as
hacking, phishing attack, virus and malware attack, and other. The intrusion detection and
prevention method should be used for developing the security framework for the
organization. The loss of the data can be minimized with the use of intrusion detection and
prevention method and other security measures within the curriculum of the organization
5. Research question:
The research questions helps in taking the research in right direction. The research questions
which are undertaken to perform the research activities are depicted below:
Primary question:
What are the preventive and control measures taken to overcome the situation of
security threats?
Secondary Question
What are the devices and activities which should be protected against the occurrence
of cyber-criminal offence?
What is the reason behind the success of the intrusion?
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
What the issues rose by the cyber threats?
Why the security threats are not detected proactively?
What are the punishment standards for the digital offence?
What are the risks associated with the security of the digital information?
6. Research Hypothesis
The progress and completion of the research helps in developing security credentials to
overcome the problem of threats and vulnerabilities which are associated with the system.
The use of innovative thinking helps in bringing significant changes in the security
infrastructure of the organization (Caesar, 2012).
The hypothesis which is undertaken is that the preventive measure taken by the expert to
overcome the situation of cyber threats. The innovation in the cyber-security helps in
resolving the issues of cyber-crime. The risks management plan helps in identifying the
threats and risks associated with the digital network. The test matrix should be prepared for
analysing the precaution method taken for securing the system (Brown, 2010). The following
is the analysis matrix related with the inclusion of threats and security measures taken:
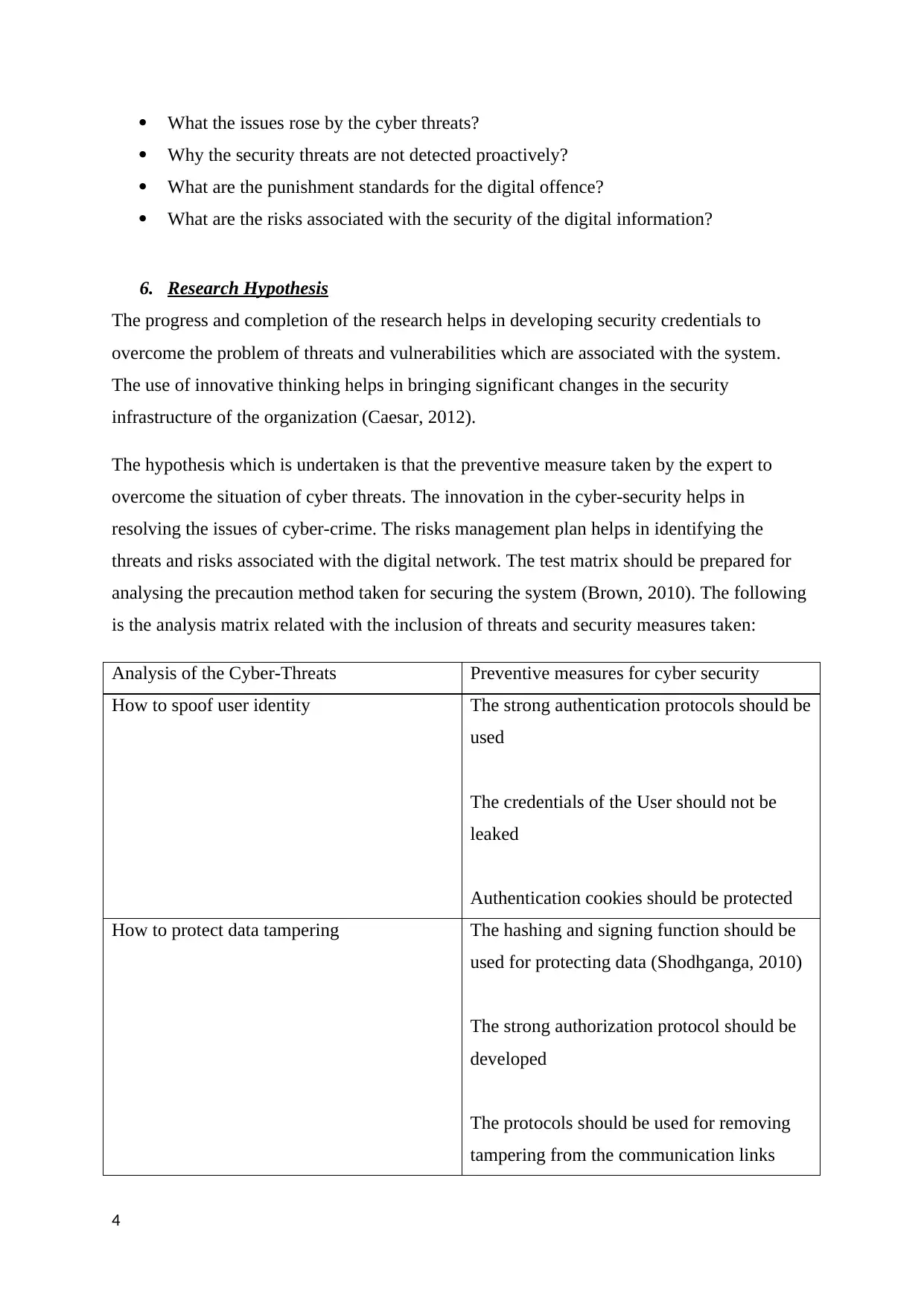
Analysis of the Cyber-Threats Preventive measures for cyber security
How to spoof user identity The strong authentication protocols should be
used
The credentials of the User should not be
leaked
Authentication cookies should be protected
How to protect data tampering The hashing and signing function should be
used for protecting data (Shodhganga, 2010)
The strong authorization protocol should be
developed
The protocols should be used for removing
tampering from the communication links
4
Why the security threats are not detected proactively?
What are the punishment standards for the digital offence?
What are the risks associated with the security of the digital information?
6. Research Hypothesis
The progress and completion of the research helps in developing security credentials to
overcome the problem of threats and vulnerabilities which are associated with the system.
The use of innovative thinking helps in bringing significant changes in the security
infrastructure of the organization (Caesar, 2012).
The hypothesis which is undertaken is that the preventive measure taken by the expert to
overcome the situation of cyber threats. The innovation in the cyber-security helps in
resolving the issues of cyber-crime. The risks management plan helps in identifying the
threats and risks associated with the digital network. The test matrix should be prepared for
analysing the precaution method taken for securing the system (Brown, 2010). The following
is the analysis matrix related with the inclusion of threats and security measures taken:
Analysis of the Cyber-Threats Preventive measures for cyber security
How to spoof user identity The strong authentication protocols should be
used
The credentials of the User should not be
leaked
Authentication cookies should be protected
How to protect data tampering The hashing and signing function should be
used for protecting data (Shodhganga, 2010)
The strong authorization protocol should be
developed
The protocols should be used for removing
tampering from the communication links
4
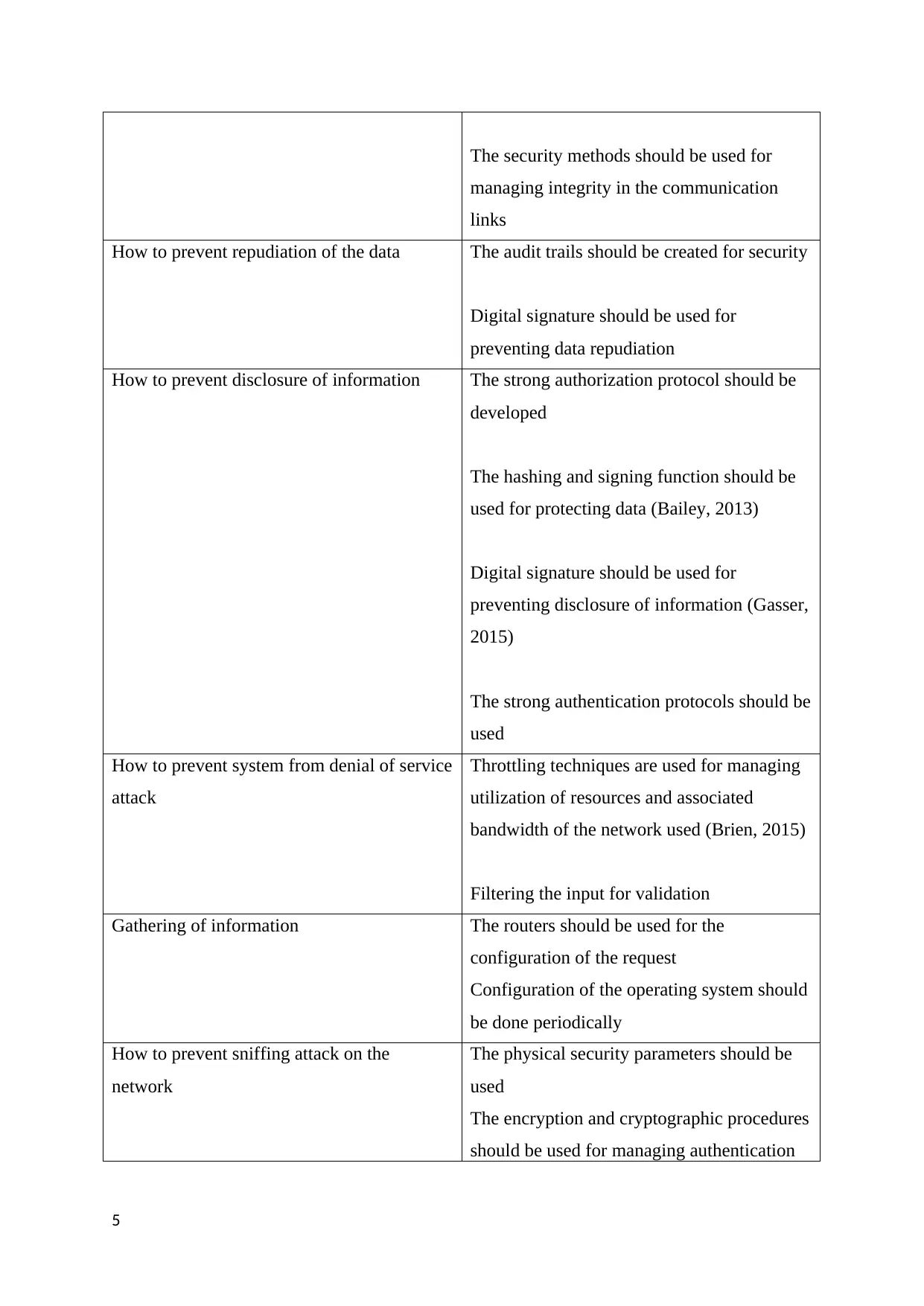
The security methods should be used for
managing integrity in the communication
links
How to prevent repudiation of the data The audit trails should be created for security
Digital signature should be used for
preventing data repudiation
How to prevent disclosure of information The strong authorization protocol should be
developed
The hashing and signing function should be
used for protecting data (Bailey, 2013)
Digital signature should be used for
preventing disclosure of information (Gasser,
2015)
The strong authentication protocols should be
used
How to prevent system from denial of service
attack
Throttling techniques are used for managing
utilization of resources and associated
bandwidth of the network used (Brien, 2015)
Filtering the input for validation
Gathering of information The routers should be used for the
configuration of the request
Configuration of the operating system should
be done periodically
How to prevent sniffing attack on the
network
The physical security parameters should be
used
The encryption and cryptographic procedures
should be used for managing authentication
5
managing integrity in the communication
links
How to prevent repudiation of the data The audit trails should be created for security
Digital signature should be used for
preventing data repudiation
How to prevent disclosure of information The strong authorization protocol should be
developed
The hashing and signing function should be
used for protecting data (Bailey, 2013)
Digital signature should be used for
preventing disclosure of information (Gasser,
2015)
The strong authentication protocols should be
used
How to prevent system from denial of service
attack
Throttling techniques are used for managing
utilization of resources and associated
bandwidth of the network used (Brien, 2015)
Filtering the input for validation
Gathering of information The routers should be used for the
configuration of the request
Configuration of the operating system should
be done periodically
How to prevent sniffing attack on the
network
The physical security parameters should be
used
The encryption and cryptographic procedures
should be used for managing authentication
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

credential
How to prevent hijacking of the complete
session
The session should be made in the encrypted
format
Communication channels should be used in
the encrypted format
How to secure system from viruses and
malware attack
The ports of the firewall should be blocked
Anti-malware and anti-virus should be
installed in the system
7. Research Design ad methodology
Qualitative Research
The qualitative research was undertaken by using the methods like observation, arrangement
of in-depth interviews, document review system, formulation of theory, analysis of the text
based documents, and others which are summarised below:
Observation: The observation of activities in the working of the organization helps in
analysing the flow of work and the possibility of data leakages from where the cyber-
attacker get a chance to attack on the system. There is no direct face to face interview
is required with the experts.
Arrangement of In-depth interview: The descriptive data can be collected associated
with the flaws and gaps of the security methods.
Document Review: The literature review helps in analysing the different views of the
author on the research undertaken by them.
Theory formulation: The analysis of the literature view should be created in the
standard format and structure which gives the clear idea about the result and
evaluation.
Analysis of the text based document: The document should be prepared of the
information gathered from the different offline and online sources.
Organization of conferences and seminars: The question and answer set up is
developed by sending invitation to ethical hackers, policy makers, digital forensic
6
How to prevent hijacking of the complete
session
The session should be made in the encrypted
format
Communication channels should be used in
the encrypted format
How to secure system from viruses and
malware attack
The ports of the firewall should be blocked
Anti-malware and anti-virus should be
installed in the system
7. Research Design ad methodology
Qualitative Research
The qualitative research was undertaken by using the methods like observation, arrangement
of in-depth interviews, document review system, formulation of theory, analysis of the text
based documents, and others which are summarised below:
Observation: The observation of activities in the working of the organization helps in
analysing the flow of work and the possibility of data leakages from where the cyber-
attacker get a chance to attack on the system. There is no direct face to face interview
is required with the experts.
Arrangement of In-depth interview: The descriptive data can be collected associated
with the flaws and gaps of the security methods.
Document Review: The literature review helps in analysing the different views of the
author on the research undertaken by them.
Theory formulation: The analysis of the literature view should be created in the
standard format and structure which gives the clear idea about the result and
evaluation.
Analysis of the text based document: The document should be prepared of the
information gathered from the different offline and online sources.
Organization of conferences and seminars: The question and answer set up is
developed by sending invitation to ethical hackers, policy makers, digital forensic
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

investigators, testers, and others to generate the flow of ideas which are relevant to the
research study.
Online communication: The online portal opens the door for establishing online
research forum to circulate new ideas, discussions, opinions, and thoughts on the
research topic of cyber security prevention methods (Hoeks, 2009). The analysis of
the discussions helps in generating new tools and technologies or security methods for
securing the current infrastructure with the occurrence of cyber threats and
vulnerabilities.
Surveys: The online and offline surveys are organized with the professionals for
analysing the situation of cyber threats in the organization and what are the proactive
action taken by the professionals (Effiong, 2010)
Questionnaire: The online and offline Questionnaire are organized with the
professionals for analysing the situation of cyber threats in the organization and what
are the proactive action taken by the professionals.
Interview: The face to face interviews are organized with the professionals for
analysing the situation of cyber threats in the organization and what are the proactive
actions taken by the professionals (Levy, 2014).
Quantitative Research
The quantitative research was undertaken by using the methods like honey pots, numerical
analysis statistical testing, and others.
Arrangement of Honeypots: The honeypot helps in creating the simulation of the
cyber-attack which helps in analysing the gaps and flaws of the current security
architecture (Meushaw, 2012)).
Sampling: The adequate amount of population should be chosen for testing the effects
of cyber vulnerabilities on the security architecture.
Statistical testing: It is the quantitative approach of research methodology which is
based on hypothetical testing of the relevant data.
8. Research Limitation
The research study on cyber security has the following limitation:
The research scope: The development of the research scope is limited to the
participant users on carrying over the research on cyber security.
7
research study.
Online communication: The online portal opens the door for establishing online
research forum to circulate new ideas, discussions, opinions, and thoughts on the
research topic of cyber security prevention methods (Hoeks, 2009). The analysis of
the discussions helps in generating new tools and technologies or security methods for
securing the current infrastructure with the occurrence of cyber threats and
vulnerabilities.
Surveys: The online and offline surveys are organized with the professionals for
analysing the situation of cyber threats in the organization and what are the proactive
action taken by the professionals (Effiong, 2010)
Questionnaire: The online and offline Questionnaire are organized with the
professionals for analysing the situation of cyber threats in the organization and what
are the proactive action taken by the professionals.
Interview: The face to face interviews are organized with the professionals for
analysing the situation of cyber threats in the organization and what are the proactive
actions taken by the professionals (Levy, 2014).
Quantitative Research
The quantitative research was undertaken by using the methods like honey pots, numerical
analysis statistical testing, and others.
Arrangement of Honeypots: The honeypot helps in creating the simulation of the
cyber-attack which helps in analysing the gaps and flaws of the current security
architecture (Meushaw, 2012)).
Sampling: The adequate amount of population should be chosen for testing the effects
of cyber vulnerabilities on the security architecture.
Statistical testing: It is the quantitative approach of research methodology which is
based on hypothetical testing of the relevant data.
8. Research Limitation
The research study on cyber security has the following limitation:
The research scope: The development of the research scope is limited to the
participant users on carrying over the research on cyber security.
7
Communication with the IT experts: The analysis of the thoughts and opinion of the
expert is not correctly done due to the use of professional language.
The technical information is not provided for the research on cyber security (Salem,
2011)
The company does not allow observing their working tactics.
9. Time Schedule of the research plan
The following table shows the timetable of the research proposal:
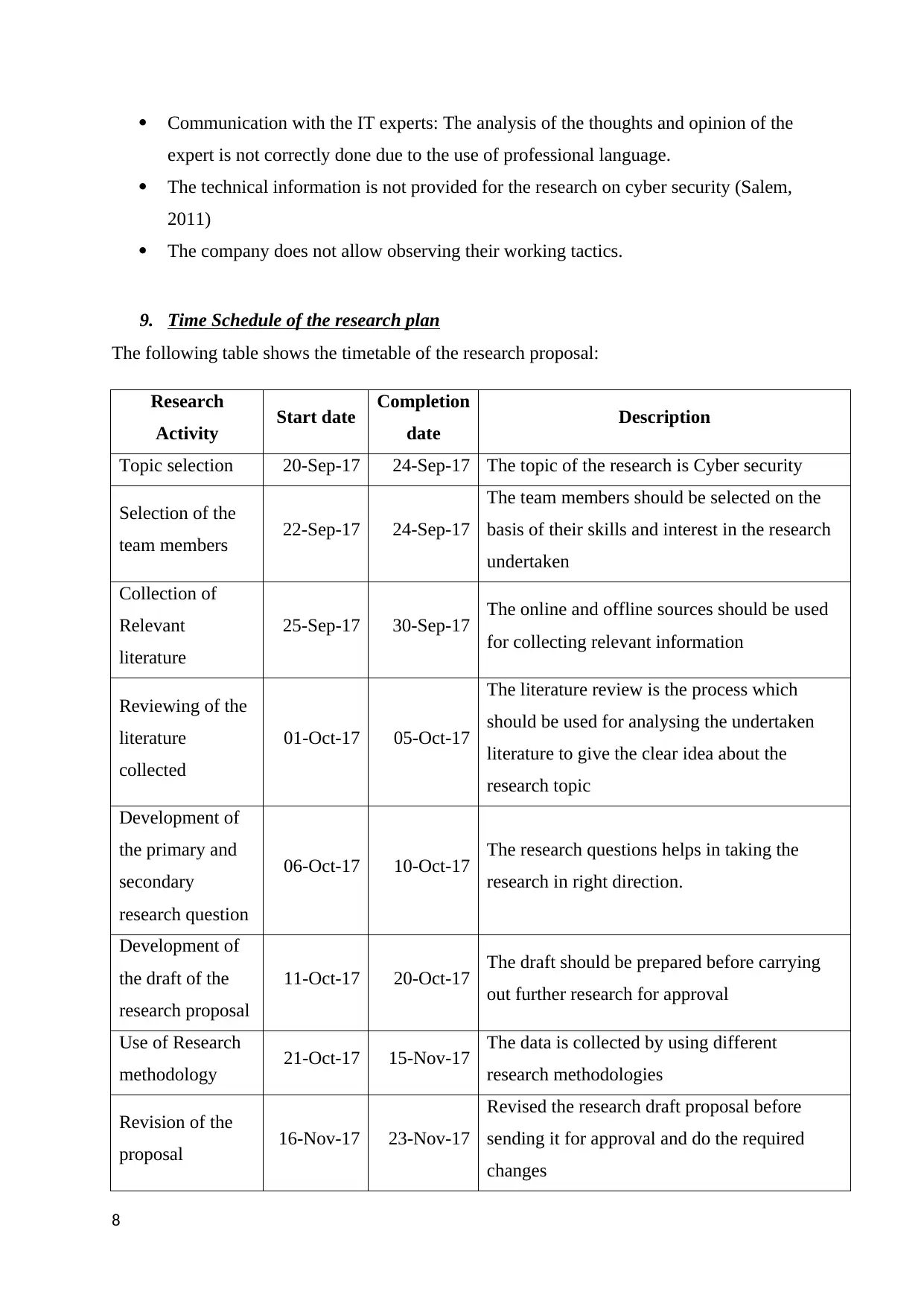
Research
Activity Start date Completion
date Description
Topic selection 20-Sep-17 24-Sep-17 The topic of the research is Cyber security
Selection of the
team members 22-Sep-17 24-Sep-17
The team members should be selected on the
basis of their skills and interest in the research
undertaken
Collection of
Relevant
literature
25-Sep-17 30-Sep-17 The online and offline sources should be used
for collecting relevant information
Reviewing of the
literature
collected
01-Oct-17 05-Oct-17
The literature review is the process which
should be used for analysing the undertaken
literature to give the clear idea about the
research topic
Development of
the primary and
secondary
research question
06-Oct-17 10-Oct-17 The research questions helps in taking the
research in right direction.
Development of
the draft of the
research proposal
11-Oct-17 20-Oct-17 The draft should be prepared before carrying
out further research for approval
Use of Research
methodology 21-Oct-17 15-Nov-17 The data is collected by using different
research methodologies
Revision of the
proposal 16-Nov-17 23-Nov-17
Revised the research draft proposal before
sending it for approval and do the required
changes
8
expert is not correctly done due to the use of professional language.
The technical information is not provided for the research on cyber security (Salem,
2011)
The company does not allow observing their working tactics.
9. Time Schedule of the research plan
The following table shows the timetable of the research proposal:
Research
Activity Start date Completion
date Description
Topic selection 20-Sep-17 24-Sep-17 The topic of the research is Cyber security
Selection of the
team members 22-Sep-17 24-Sep-17
The team members should be selected on the
basis of their skills and interest in the research
undertaken
Collection of
Relevant
literature
25-Sep-17 30-Sep-17 The online and offline sources should be used
for collecting relevant information
Reviewing of the
literature
collected
01-Oct-17 05-Oct-17
The literature review is the process which
should be used for analysing the undertaken
literature to give the clear idea about the
research topic
Development of
the primary and
secondary
research question
06-Oct-17 10-Oct-17 The research questions helps in taking the
research in right direction.
Development of
the draft of the
research proposal
11-Oct-17 20-Oct-17 The draft should be prepared before carrying
out further research for approval
Use of Research
methodology 21-Oct-17 15-Nov-17 The data is collected by using different
research methodologies
Revision of the
proposal 16-Nov-17 23-Nov-17
Revised the research draft proposal before
sending it for approval and do the required
changes
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
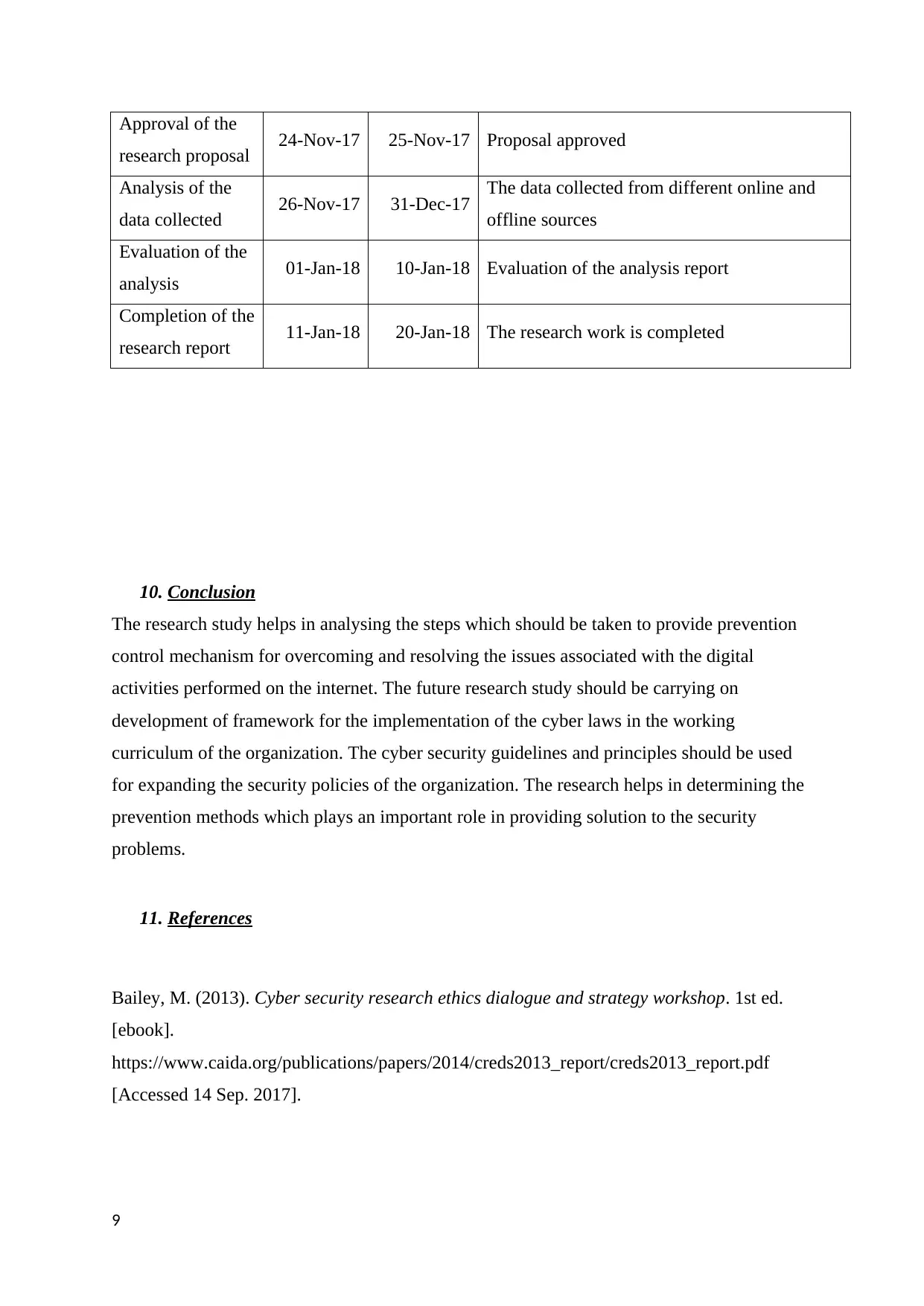
Approval of the
research proposal 24-Nov-17 25-Nov-17 Proposal approved
Analysis of the
data collected 26-Nov-17 31-Dec-17 The data collected from different online and
offline sources
Evaluation of the
analysis 01-Jan-18 10-Jan-18 Evaluation of the analysis report
Completion of the
research report 11-Jan-18 20-Jan-18 The research work is completed
10. Conclusion
The research study helps in analysing the steps which should be taken to provide prevention
control mechanism for overcoming and resolving the issues associated with the digital
activities performed on the internet. The future research study should be carrying on
development of framework for the implementation of the cyber laws in the working
curriculum of the organization. The cyber security guidelines and principles should be used
for expanding the security policies of the organization. The research helps in determining the
prevention methods which plays an important role in providing solution to the security
problems.
11. References
Bailey, M. (2013). Cyber security research ethics dialogue and strategy workshop. 1st ed.
[ebook].
https://www.caida.org/publications/papers/2014/creds2013_report/creds2013_report.pdf
[Accessed 14 Sep. 2017].
9
research proposal 24-Nov-17 25-Nov-17 Proposal approved
Analysis of the
data collected 26-Nov-17 31-Dec-17 The data collected from different online and
offline sources
Evaluation of the
analysis 01-Jan-18 10-Jan-18 Evaluation of the analysis report
Completion of the
research report 11-Jan-18 20-Jan-18 The research work is completed
10. Conclusion
The research study helps in analysing the steps which should be taken to provide prevention
control mechanism for overcoming and resolving the issues associated with the digital
activities performed on the internet. The future research study should be carrying on
development of framework for the implementation of the cyber laws in the working
curriculum of the organization. The cyber security guidelines and principles should be used
for expanding the security policies of the organization. The research helps in determining the
prevention methods which plays an important role in providing solution to the security
problems.
11. References
Bailey, M. (2013). Cyber security research ethics dialogue and strategy workshop. 1st ed.
[ebook].
https://www.caida.org/publications/papers/2014/creds2013_report/creds2013_report.pdf
[Accessed 14 Sep. 2017].
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Brien, O. (2015). Privacy and cybersecuriy. 1st ed. [ebook].
https://dash.harvard.edu/bitstream/handle/1/28552575/02Cybersecurity.pdf?sequence=1
[Accessed 14 Sep. 2017].
Brown, R. (2010). The state of cyber-security. 1st ed. [ebook].
https://www.bbb.org/globalassets/shared/media/state-of-cybersecurity/cybersecurity-
research-report.pdf [Accessed 14 Sep. 2017].
Caesar, M. (2012). Hypothesis Testing for network security. 1st ed. [ebook].
http://publish.illinois.edu/science-of-security-lablet/files/2014/05/022015-Bi-weekly-
Presentation-Godfrey.pdf [Accessed 14 Sep. 2017].
Edgar, T. (2010). Research method for cyber security. 1st ed. [ebook].
https://books.google.co.in/books?
id=aRl2DQAAQBAJ&pg=PA248&lpg=PA248&dq=Research+paper+pdf+on+research+hyp
othesis+on+cyber+security+system&source=bl&ots=SkSRWCQCH_&sig=GO13BMyV1G
mAdOHFrNRokFiSTDw&hl=en&sa=X&ved=0ahUKEwjWqoPb_6PWAhXEM48KHYOD
DJY4ChDoAQhWMAY#v=onepage&q=Research%20paper%20pdf%20on%20research
%20hypothesis%20on%20cyber%20security%20system&f=false [Accessed 14 Sep. 2017].
Effiong, E. (2010). Cyber-crime control, prevention, and investigation. 1st ed. [ebook].
http://www.academia.edu/4259163/Cyber_Crime_Research_Proposal [Accessed 14 Sep.
2017].
Faris, R. (2010). Progress and research in cyber-security. 1st ed. [ebook].
https://royalsociety.org/~/media/policy/projects/cybersecurity-research/cybersecurity-
research-report.pdf [Accessed 14 Sep. 2017].
Gasser, U. (2015). HPE Security Research. 1st ed. [ebook].
http://h20195.www2.hpe.com/V4/getpdf.aspx/4aa5-0858enn [Accessed 14 Sep. 2017].
Hoek, R. (2009). A roadmap for cyber-security research. 1st ed. [ebook].
https://www.dhs.gov/sites/default/files/publications/CSD-DHS-Cybersecurity-Roadmap.pdf
[Accessed 14 Sep. 2017].
Levy, Y. (2014). An empirical study on the role of cyber-security skills on perceived need for
action to migrate cyber misuse. 1st ed. [ebook].
10
https://dash.harvard.edu/bitstream/handle/1/28552575/02Cybersecurity.pdf?sequence=1
[Accessed 14 Sep. 2017].
Brown, R. (2010). The state of cyber-security. 1st ed. [ebook].
https://www.bbb.org/globalassets/shared/media/state-of-cybersecurity/cybersecurity-
research-report.pdf [Accessed 14 Sep. 2017].
Caesar, M. (2012). Hypothesis Testing for network security. 1st ed. [ebook].
http://publish.illinois.edu/science-of-security-lablet/files/2014/05/022015-Bi-weekly-
Presentation-Godfrey.pdf [Accessed 14 Sep. 2017].
Edgar, T. (2010). Research method for cyber security. 1st ed. [ebook].
https://books.google.co.in/books?
id=aRl2DQAAQBAJ&pg=PA248&lpg=PA248&dq=Research+paper+pdf+on+research+hyp
othesis+on+cyber+security+system&source=bl&ots=SkSRWCQCH_&sig=GO13BMyV1G
mAdOHFrNRokFiSTDw&hl=en&sa=X&ved=0ahUKEwjWqoPb_6PWAhXEM48KHYOD
DJY4ChDoAQhWMAY#v=onepage&q=Research%20paper%20pdf%20on%20research
%20hypothesis%20on%20cyber%20security%20system&f=false [Accessed 14 Sep. 2017].
Effiong, E. (2010). Cyber-crime control, prevention, and investigation. 1st ed. [ebook].
http://www.academia.edu/4259163/Cyber_Crime_Research_Proposal [Accessed 14 Sep.
2017].
Faris, R. (2010). Progress and research in cyber-security. 1st ed. [ebook].
https://royalsociety.org/~/media/policy/projects/cybersecurity-research/cybersecurity-
research-report.pdf [Accessed 14 Sep. 2017].
Gasser, U. (2015). HPE Security Research. 1st ed. [ebook].
http://h20195.www2.hpe.com/V4/getpdf.aspx/4aa5-0858enn [Accessed 14 Sep. 2017].
Hoek, R. (2009). A roadmap for cyber-security research. 1st ed. [ebook].
https://www.dhs.gov/sites/default/files/publications/CSD-DHS-Cybersecurity-Roadmap.pdf
[Accessed 14 Sep. 2017].
Levy, Y. (2014). An empirical study on the role of cyber-security skills on perceived need for
action to migrate cyber misuse. 1st ed. [ebook].
10

http://cec.nova.edu/research/winter_2014_poster_session/documents/Anita%20Girton.pdf
[Accessed 14 Sep. 2017].
Meushaw, R. (2012). Developing a blueprint for the science of cybersecurity. 1st ed. [ebook].
https://www.nsa.gov/resources/everyone/digital-media-center/publications/the-next-wave/
assets/files/TNW-19-2.pdf [Accessed 14 Sep. 2017].
Salem, M. (2011). On the design and execution of cyber security user studies: Methodology,
challenges, and lesson learned. 1st ed. [ebook].
http://ids.cs.columbia.edu/sites/default/files/CSET_2011_0.pdf [Accessed 14 Sep. 2017].
Shodhganga, S. (2010). Research Design and methodology. 1st ed. [ebook].
http://shodhganga.inflibnet.ac.in/bitstream/10603/40658/8/08_chapter%203.pdf [Accessed 14
Sep. 2017].
Tonge, A. (2013). Cyber security: challenges for cyber security: A literature review. 1st ed.
[ebook]. http://www.iosrjournals.org/iosr-jce/papers/Vol12-issue2/K01226775.pdf?id=15
[Accessed 14 Sep. 2017].
11
[Accessed 14 Sep. 2017].
Meushaw, R. (2012). Developing a blueprint for the science of cybersecurity. 1st ed. [ebook].
https://www.nsa.gov/resources/everyone/digital-media-center/publications/the-next-wave/
assets/files/TNW-19-2.pdf [Accessed 14 Sep. 2017].
Salem, M. (2011). On the design and execution of cyber security user studies: Methodology,
challenges, and lesson learned. 1st ed. [ebook].
http://ids.cs.columbia.edu/sites/default/files/CSET_2011_0.pdf [Accessed 14 Sep. 2017].
Shodhganga, S. (2010). Research Design and methodology. 1st ed. [ebook].
http://shodhganga.inflibnet.ac.in/bitstream/10603/40658/8/08_chapter%203.pdf [Accessed 14
Sep. 2017].
Tonge, A. (2013). Cyber security: challenges for cyber security: A literature review. 1st ed.
[ebook]. http://www.iosrjournals.org/iosr-jce/papers/Vol12-issue2/K01226775.pdf?id=15
[Accessed 14 Sep. 2017].
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





