Cyber Security Attacks and Techniques - Threat Analysis and Trends
VerifiedAdded on 2023/06/15
|14
|1105
|277
Report
AI Summary
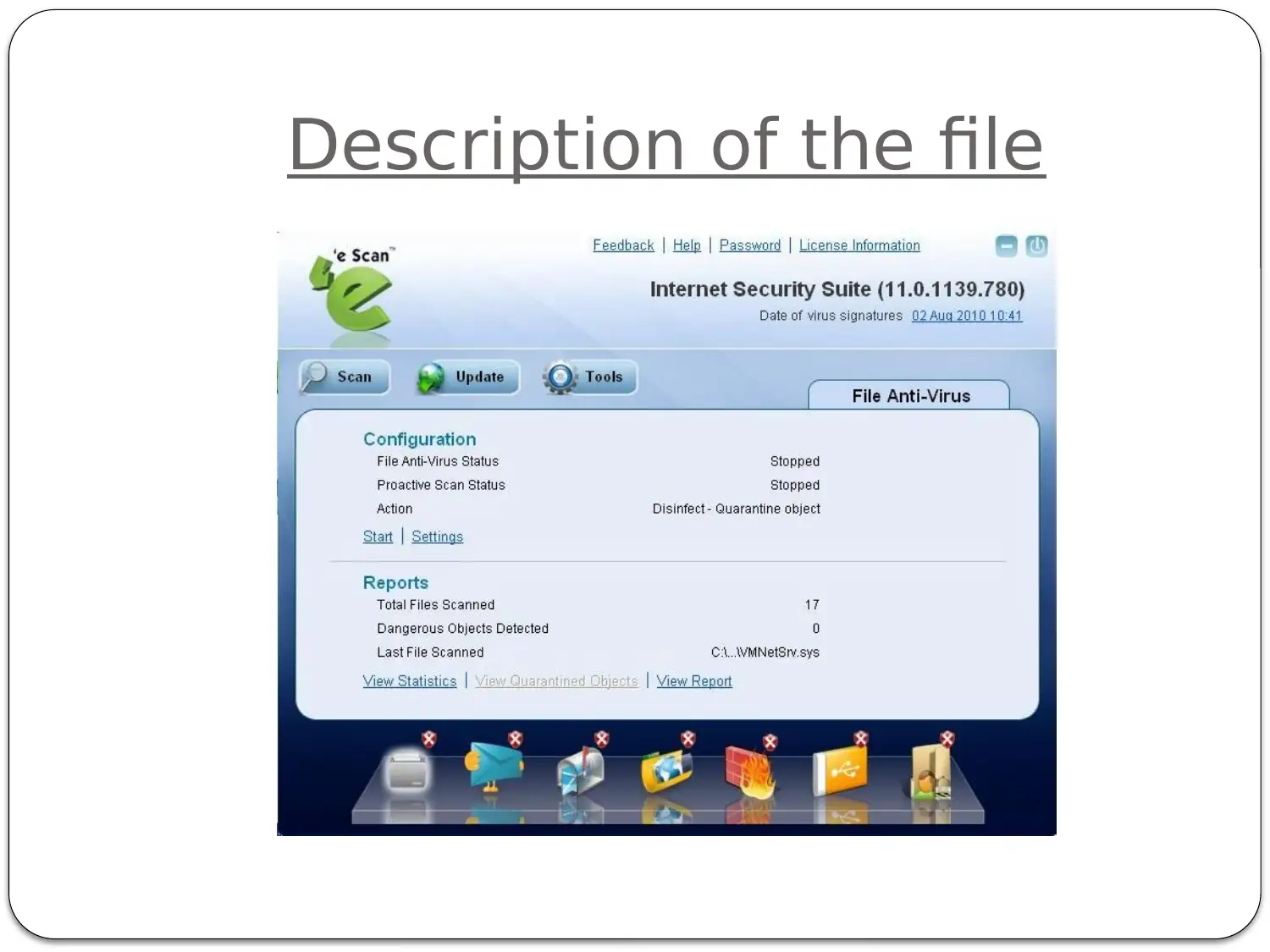
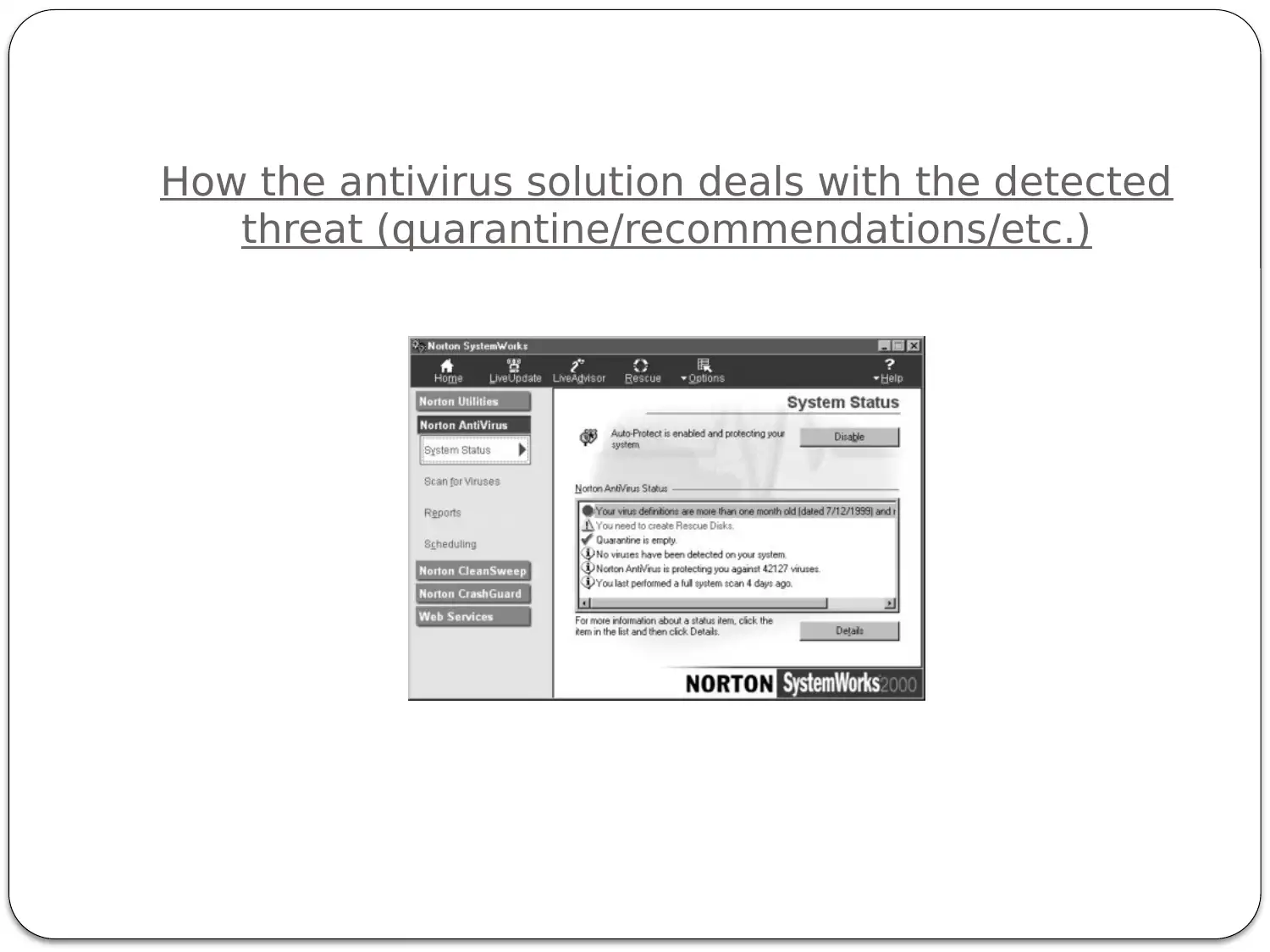
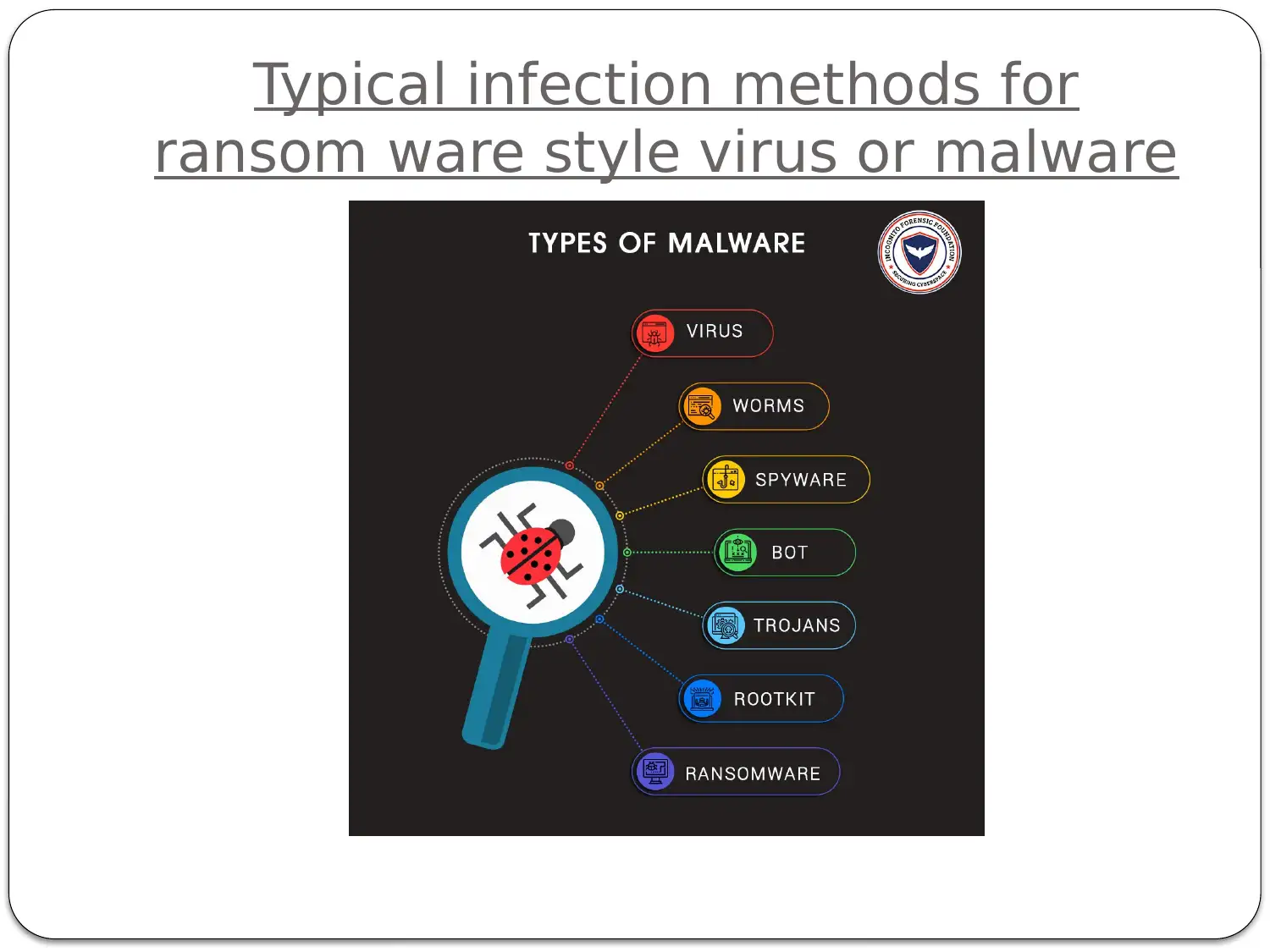
This report provides a comprehensive analysis of cyber security attacks and techniques, focusing on threat actors, current trends, and vulnerabilities. It begins by defining different threat actors, such as state-sponsored actors, organized cybercrime groups, and hacktivists, outlining their motivations and defense strategies. The report identifies and describes current trends in cyber attacks, including the impact of various cyber threat vectors like malware, phishing, and denial-of-service attacks. It differentiates between untargeted and targeted attacks, providing examples of vulnerabilities exploited in each category, with a focus on malware and its exploitation of unpatched systems. The report also describes techniques used by attackers to infiltrate systems and escalate privileges, including attacks against network perimeters and end-users, as well as vulnerabilities in wireless WPA2 networks. Furthermore, it addresses Internet of Things (IoT) security issues, defining IoT and providing examples of IoT devices and their associated security concerns. The report concludes with a list of references used in the analysis.
1 out of 14






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)