The Impact of EU and UK Cybersecurity Laws: A Research Project
VerifiedAdded on 2023/06/10
|10
|2513
|288
Project
AI Summary
This research project investigates the crucial role of cybersecurity laws within the European Union and the United Kingdom. It begins with an introduction highlighting the importance of cybersecurity for data and information protection, followed by a clear statement of research aims, objectives, and questions. A literature review explores existing knowledge on cybersecurity laws, emphasizing the significance of the EU and UK's roles in this area, and identifies challenges faced in creating these laws. The methodology section details the research philosophy (positivism), approach (deductive), and choices (quantitative), along with data collection methods, including the use of questionnaires and sampling techniques. A Gantt chart outlines the project timeline, and the project addresses potential risks, budget considerations, required resources, skills, and health and safety measures. The conclusion summarizes key findings, emphasizing the need for continued development in cybersecurity regulations, particularly concerning emerging threats like cloud theft and data breaches. The project underscores the need for adequate funding and resources to support the ongoing evolution of cybersecurity laws within the EU and UK. The project has been prepared by a student and is available on Desklib.

Research Project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Topic: The importance of the European Union and United Kingdom on cybersecurity laws”.......3
Introduction /Background................................................................................................................3
Research aim:...............................................................................................................................3
Research Objectives:...................................................................................................................3
Research Questions......................................................................................................................3
Description and selection of methods used.....................................................................................3
Deliverables from the selected approach/GANT chart /proposed methods....................................5
Conclusion and areas for future development.................................................................................5
REFERENCES................................................................................................................................6
Topic: The importance of the European Union and United Kingdom on cybersecurity laws”.......3
Introduction /Background................................................................................................................3
Research aim:...............................................................................................................................3
Research Objectives:...................................................................................................................3
Research Questions......................................................................................................................3
Description and selection of methods used.....................................................................................3
Deliverables from the selected approach/GANT chart /proposed methods....................................5
Conclusion and areas for future development.................................................................................5
REFERENCES................................................................................................................................6

Topic: The importance of the European Union and United Kingdom on
cybersecurity laws”
Introduction /Background
Cyber security is considered to be a highly important concept for the protection of the
information and the data. For this objective, the different cyber security acts have been
implemented by the UK nation and European Countries. All these acts plays a very important
and significant role in protecting the confidential data in effective manner. In reference to the
present research work, it will help in deep understanding about the significance of the United
Kingdom and European Union on the Cybersecurity Laws (Halouzka and Buřita, 2019).
Research aim:
“To analyse the importance of the European Union and United Kingdom on cybersecurity
laws”.
Research Objectives:
To develop knowledge regarding cybersecurity laws.
To understand the importance of European Union and United Kingdom on cybersecurity
laws.
To identify the challenges faced by European Union and United Kingdom while
preparing laws related to cybersecurity.
Research Questions
Discuss knowledge regarding cybersecurity laws?
What is the importance of European Union and United Kingdom on cybersecurity laws?
What are the challenges faced by European Union and United Kingdom while preparing
laws related to cybersecurity?
Literature Review
To develop knowledge regarding cybersecurity laws
cybersecurity laws”
Introduction /Background
Cyber security is considered to be a highly important concept for the protection of the
information and the data. For this objective, the different cyber security acts have been
implemented by the UK nation and European Countries. All these acts plays a very important
and significant role in protecting the confidential data in effective manner. In reference to the
present research work, it will help in deep understanding about the significance of the United
Kingdom and European Union on the Cybersecurity Laws (Halouzka and Buřita, 2019).
Research aim:
“To analyse the importance of the European Union and United Kingdom on cybersecurity
laws”.
Research Objectives:
To develop knowledge regarding cybersecurity laws.
To understand the importance of European Union and United Kingdom on cybersecurity
laws.
To identify the challenges faced by European Union and United Kingdom while
preparing laws related to cybersecurity.
Research Questions
Discuss knowledge regarding cybersecurity laws?
What is the importance of European Union and United Kingdom on cybersecurity laws?
What are the challenges faced by European Union and United Kingdom while preparing
laws related to cybersecurity?
Literature Review
To develop knowledge regarding cybersecurity laws
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

According to Baadsgaard, (2021), cyber security basically comprises of various laws that
helps in dealing with the relationship of the internet with various other components that
comprises of the software, technological elements, computer hardware and much more. In
reference to Cyber Law, it basically known as the Internet Law. In addition to that, cyberlaw
could reduce the harm or damage in relation to the various activities related to Crime through
protecting from the communications, IP and unnecessary access. In the current scenario, the
increase use of the internet could result in enhancing the various legal issues across the globe
(Brexit and Cyber Security , 2021).
To understand the importance of European Union and United Kingdom on cybersecurity
laws.
As per the viewpoint of Fuster and Jasmontaite, (2020), it has been analysed that
cybersecurity laws plays a very significant importance when in comes to security of the
information and important data in a significant manner. For this objective, the European
countries are focusing on implementing various laws which plays a major role in managing the
information and data in a significant manner. With the help of cyber security laws, it plays a very
important role in improving the European Union agency for the cybersecurity. In addition to that,
it helps in establishing a particular certified framework for the various services and products
(Cybersecurity Regulation in the European Union, 2020).
To identify the challenges faced by European Union and United Kingdom while preparing
laws related to cybersecurity
According to Stevens and Kevin, (2019), there are various challenge and issues which are
faced by the UK and European Countries while figuring out and structing the various laws in
relation to the Cyber Security. In relation to these, it is very important for the authorities to have
deep understanding and analysing the components in relation to the security and much more.
Moreover, they also have to deal with the problems in relation to the cloud threats and Data
breaches and also it is very important for the authorities to carry out important steps prior
formulation of the various cybersecurity laws in a significant manner (Cybersecurity Laws &
Regulations, 2020).
helps in dealing with the relationship of the internet with various other components that
comprises of the software, technological elements, computer hardware and much more. In
reference to Cyber Law, it basically known as the Internet Law. In addition to that, cyberlaw
could reduce the harm or damage in relation to the various activities related to Crime through
protecting from the communications, IP and unnecessary access. In the current scenario, the
increase use of the internet could result in enhancing the various legal issues across the globe
(Brexit and Cyber Security , 2021).
To understand the importance of European Union and United Kingdom on cybersecurity
laws.
As per the viewpoint of Fuster and Jasmontaite, (2020), it has been analysed that
cybersecurity laws plays a very significant importance when in comes to security of the
information and important data in a significant manner. For this objective, the European
countries are focusing on implementing various laws which plays a major role in managing the
information and data in a significant manner. With the help of cyber security laws, it plays a very
important role in improving the European Union agency for the cybersecurity. In addition to that,
it helps in establishing a particular certified framework for the various services and products
(Cybersecurity Regulation in the European Union, 2020).
To identify the challenges faced by European Union and United Kingdom while preparing
laws related to cybersecurity
According to Stevens and Kevin, (2019), there are various challenge and issues which are
faced by the UK and European Countries while figuring out and structing the various laws in
relation to the Cyber Security. In relation to these, it is very important for the authorities to have
deep understanding and analysing the components in relation to the security and much more.
Moreover, they also have to deal with the problems in relation to the cloud threats and Data
breaches and also it is very important for the authorities to carry out important steps prior
formulation of the various cybersecurity laws in a significant manner (Cybersecurity Laws &
Regulations, 2020).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Methodology
It basically refers to the method of collection and interpretation of the information in a effective
manner. It further comprises of the various steps for the purpose to carry out important decisions.
Quantitative analysis: In context to this method, it is basically related to the numerical data and
comprises of the various mathematical and statistical tools for the purpose to collect information
in a effective way.
Qualitative analysis: In context to this analysis, it is basically considered to be an imperative
method and is highly related to the non-numerical data.
Description and selection of methods used
Research philosophy: It is define as the belief about the manner in which information about a
phenomenon is collected, used and analysed. In addition to this, it is mainly of two types which
are positivism and interpretivism. With reference to present study, positivism research
philosophy is applied and the major reason to use is it supports in analysing and collection of
the quantitative data in less time and cost. Moreover, it also assist researcher in gathering
objective information because of which positive results can be attained (Didenko, 2020).
Research approach: It is defined as the procedure that assist in identifying whether theories and
hypothesis is accepted or rejected as per the collected information. It is mainly of two forms that
is deductive and inductive approach. In context to the current study, this approach is used as it
helps to better explain the casual relationship among the variables and concepts. Moreover, it
also allows investigator to gather information in a economical way and in minimum time.
Research choice: It is one of the significant part of research methodology which guide
the investigator to analyse what type of information is required to collect from the chosen topic.
It is basically divided into two types which is qualitative and quantitative as well. With
reference to present investigation, Quantitative research choice is effective and valuable as it
It basically refers to the method of collection and interpretation of the information in a effective
manner. It further comprises of the various steps for the purpose to carry out important decisions.
Quantitative analysis: In context to this method, it is basically related to the numerical data and
comprises of the various mathematical and statistical tools for the purpose to collect information
in a effective way.
Qualitative analysis: In context to this analysis, it is basically considered to be an imperative
method and is highly related to the non-numerical data.
Description and selection of methods used
Research philosophy: It is define as the belief about the manner in which information about a
phenomenon is collected, used and analysed. In addition to this, it is mainly of two types which
are positivism and interpretivism. With reference to present study, positivism research
philosophy is applied and the major reason to use is it supports in analysing and collection of
the quantitative data in less time and cost. Moreover, it also assist researcher in gathering
objective information because of which positive results can be attained (Didenko, 2020).
Research approach: It is defined as the procedure that assist in identifying whether theories and
hypothesis is accepted or rejected as per the collected information. It is mainly of two forms that
is deductive and inductive approach. In context to the current study, this approach is used as it
helps to better explain the casual relationship among the variables and concepts. Moreover, it
also allows investigator to gather information in a economical way and in minimum time.
Research choice: It is one of the significant part of research methodology which guide
the investigator to analyse what type of information is required to collect from the chosen topic.
It is basically divided into two types which is qualitative and quantitative as well. With
reference to present investigation, Quantitative research choice is effective and valuable as it

assist researcher to collect numerical data which is mainly based on facts and figures. Along with
this, it also help in attaining the objective in accurate and valid manner (Newman, 2020).
Research strategy: It is defined as the detailed planned process that is used to give blueprint to
accumulate and extract information. There are different kinds of research strategies that is action
research, focus group, action research, systematic literature review and many more. In relation to
present study, survey as a strategy of strategy is effective and highly supportive as it help
investigator in gaining deep knowledge about a particular topic so that better results can be
attained. Moreover, it also help to gather data directly from the sources which includes high
validity and reliability.
Data collection: It is basically the process of gathering, measuring and analysing data associated
to the selected topic. The data is collected by researcher for the purpose to attain aim and
objectives in an effective way. There are majorly two types of data collection which is primary
and secondary method. It is defined as the information which is directly collected from the
sources and is first hand information. On the other side, secondary information is referred as the
data which is already available and is collected through books, Journals, articles and many more.
In relation to current study, both secondary and primary data is used as it supports in gaining in
depth knowledge about topic which directly leads towards attainment of outcomes.
Research instrument: It is basically a technique which is used by researcher in order to gather
information or data. The tools basically comprises of the interview, questionnaire, focus group
and much more. It is vital for researcher to select and appropriate research instrument so that
valid data is collected that has direct impact on the results of study. In reference to the present
study, questionnaire is used as it helps to gather data directly from source or the respondents due
to which investigator gain in-depth knowledge regarding topic. Moreover, it also helps in gaining
insight about viewpoint of different people on topic that leads to attainment of objectives and
gaining of results as well.
Sampling: It is considered to be a method of choosing the trial size from the entire lot
population within the study. It is categorised into which is non-probability and probability
sampling ways. With reference to current investigation, sampling that is a basically considered
to be a part of probability sampling is taken into consideration. The main reason to select random
this, it also help in attaining the objective in accurate and valid manner (Newman, 2020).
Research strategy: It is defined as the detailed planned process that is used to give blueprint to
accumulate and extract information. There are different kinds of research strategies that is action
research, focus group, action research, systematic literature review and many more. In relation to
present study, survey as a strategy of strategy is effective and highly supportive as it help
investigator in gaining deep knowledge about a particular topic so that better results can be
attained. Moreover, it also help to gather data directly from the sources which includes high
validity and reliability.
Data collection: It is basically the process of gathering, measuring and analysing data associated
to the selected topic. The data is collected by researcher for the purpose to attain aim and
objectives in an effective way. There are majorly two types of data collection which is primary
and secondary method. It is defined as the information which is directly collected from the
sources and is first hand information. On the other side, secondary information is referred as the
data which is already available and is collected through books, Journals, articles and many more.
In relation to current study, both secondary and primary data is used as it supports in gaining in
depth knowledge about topic which directly leads towards attainment of outcomes.
Research instrument: It is basically a technique which is used by researcher in order to gather
information or data. The tools basically comprises of the interview, questionnaire, focus group
and much more. It is vital for researcher to select and appropriate research instrument so that
valid data is collected that has direct impact on the results of study. In reference to the present
study, questionnaire is used as it helps to gather data directly from source or the respondents due
to which investigator gain in-depth knowledge regarding topic. Moreover, it also helps in gaining
insight about viewpoint of different people on topic that leads to attainment of objectives and
gaining of results as well.
Sampling: It is considered to be a method of choosing the trial size from the entire lot
population within the study. It is categorised into which is non-probability and probability
sampling ways. With reference to current investigation, sampling that is a basically considered
to be a part of probability sampling is taken into consideration. The main reason to select random
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
sampling is it help investigator to select large sample size without any biasness. The 30 people is
randomly selected in order to collect data on the research topic( Felkner and et.al, 2021).
Data analysis: It is the process to analyse the collected data by using different methods so that
effective findings can be developed. In addition to this, thee are various data analysis forms
which comprises of frequency distribution, thematic analysis and much more. In relation to
current study, it is basically a method which is suitable as it allows researcher to examine the
primary data in an significant manner. Furthermore, it also supports researcher to identify the
findings in form of graphs, charts that is easy to understand and interpret by others.
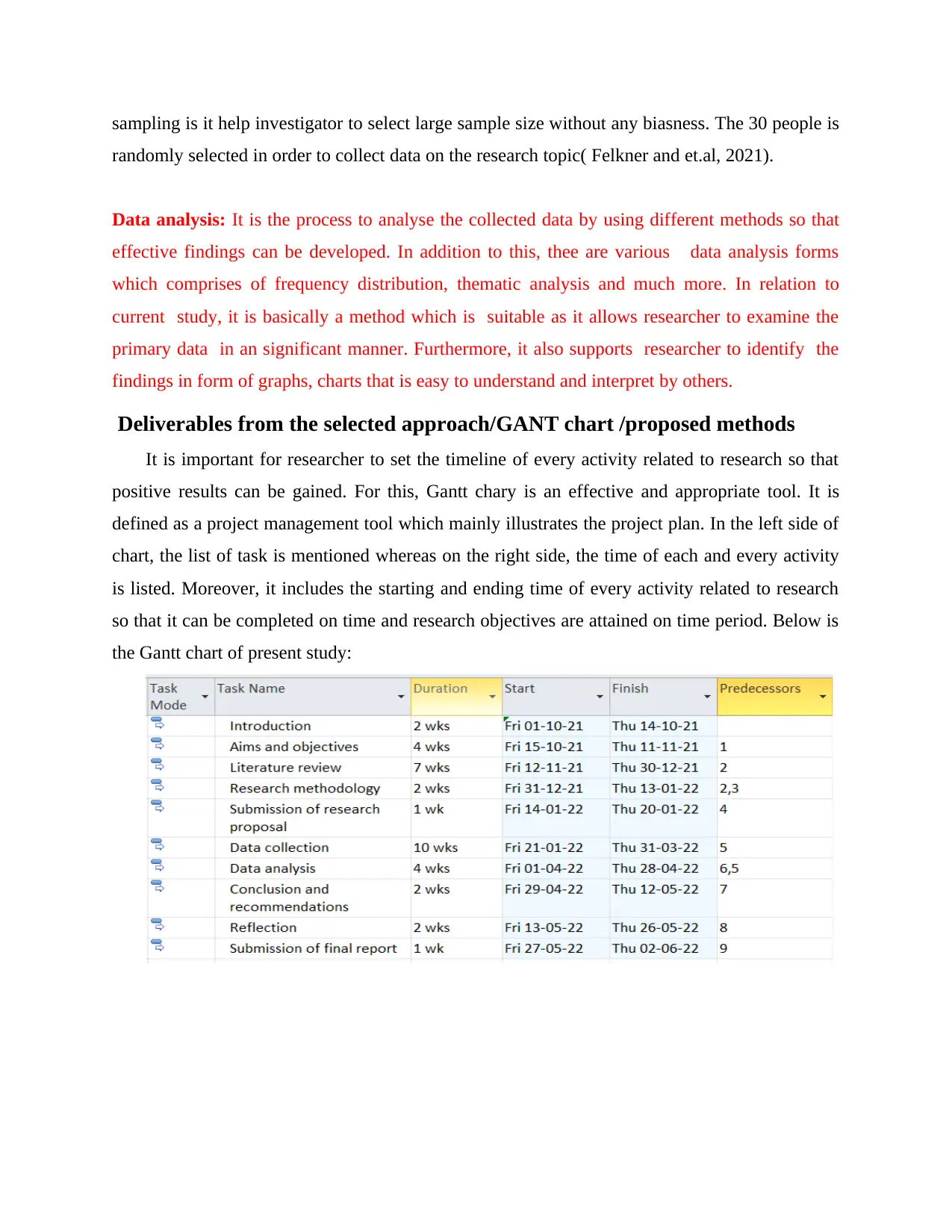
Deliverables from the selected approach/GANT chart /proposed methods
It is important for researcher to set the timeline of every activity related to research so that
positive results can be gained. For this, Gantt chary is an effective and appropriate tool. It is
defined as a project management tool which mainly illustrates the project plan. In the left side of
chart, the list of task is mentioned whereas on the right side, the time of each and every activity
is listed. Moreover, it includes the starting and ending time of every activity related to research
so that it can be completed on time and research objectives are attained on time period. Below is
the Gantt chart of present study:
randomly selected in order to collect data on the research topic( Felkner and et.al, 2021).
Data analysis: It is the process to analyse the collected data by using different methods so that
effective findings can be developed. In addition to this, thee are various data analysis forms
which comprises of frequency distribution, thematic analysis and much more. In relation to
current study, it is basically a method which is suitable as it allows researcher to examine the
primary data in an significant manner. Furthermore, it also supports researcher to identify the
findings in form of graphs, charts that is easy to understand and interpret by others.
Deliverables from the selected approach/GANT chart /proposed methods
It is important for researcher to set the timeline of every activity related to research so that
positive results can be gained. For this, Gantt chary is an effective and appropriate tool. It is
defined as a project management tool which mainly illustrates the project plan. In the left side of
chart, the list of task is mentioned whereas on the right side, the time of each and every activity
is listed. Moreover, it includes the starting and ending time of every activity related to research
so that it can be completed on time and research objectives are attained on time period. Below is
the Gantt chart of present study:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risks: In reference to the present study, there are various risks in relation to the various
equipment’s, lack of funds and various resources. All these risks need to be resolved through
carrying out effective steps in the most appropriate and suitable manner.
Budget: In order to complete this research project, there is a necessity for the purpose to
prepare a proper budget. In relation to the budget, it involves the price of the tools, necessary
resources and various equipment which are basically used for the purpose to complete the
research work. In context to the current research, the overall budget is approximately 90 Euros.
Resources: In context to the resources, for the purpose of present study’s accomplishment,
there is a requirement of the right amount of resources and all these resources basically
equipment’s, lack of funds and various resources. All these risks need to be resolved through
carrying out effective steps in the most appropriate and suitable manner.
Budget: In order to complete this research project, there is a necessity for the purpose to
prepare a proper budget. In relation to the budget, it involves the price of the tools, necessary
resources and various equipment which are basically used for the purpose to complete the
research work. In context to the current research, the overall budget is approximately 90 Euros.
Resources: In context to the resources, for the purpose of present study’s accomplishment,
there is a requirement of the right amount of resources and all these resources basically

comprises of the equipment, funds, staff and much more (Toapanta, Gurumendi and Gallegos,
2019).
Skills: In context to the research, it is being carried out by various individuals. For the
purpose to complete a project in a successful, there is a need for the effective and efficient skills
in relation to the decision making skills, communication skills, time management skill,
presentation skills and much more.
Health and Safety: In context to the present study, there is need for the take care of the health and
safety of the various requirements for the objective of getting effective and meaningful results in
a effective and efficient way.
Conclusion and areas for future development
From the above mentioned study, it has been analysed that the Cyber Security laws plays a
very important for the objective of the security of the data and the protection of the information
and data. In Relation to the above study, it is basically based upon the UK and European
countries on the cybersecurity laws. In context to the Cyber Security, it is considered to be highly
important for the purpose to protect the information and the data. In reference to areas for the
future development, it is very important for the European and United Kingdom to focus on the
cybersecurity laws and regulations in a effective and efficient manner with the support of the
funds, skills and other important resources. In addition to that when it comes to Cyber security
laws, there are various areas which needed development which comprises of cloud theft, IT and
hacking. In reference to cyber security, it is very essential to make use of the relevant resources
and funds for the purpose to implements the laws related to the cyber security in a effective and
efficient manner.
2019).
Skills: In context to the research, it is being carried out by various individuals. For the
purpose to complete a project in a successful, there is a need for the effective and efficient skills
in relation to the decision making skills, communication skills, time management skill,
presentation skills and much more.
Health and Safety: In context to the present study, there is need for the take care of the health and
safety of the various requirements for the objective of getting effective and meaningful results in
a effective and efficient way.
Conclusion and areas for future development
From the above mentioned study, it has been analysed that the Cyber Security laws plays a
very important for the objective of the security of the data and the protection of the information
and data. In Relation to the above study, it is basically based upon the UK and European
countries on the cybersecurity laws. In context to the Cyber Security, it is considered to be highly
important for the purpose to protect the information and the data. In reference to areas for the
future development, it is very important for the European and United Kingdom to focus on the
cybersecurity laws and regulations in a effective and efficient manner with the support of the
funds, skills and other important resources. In addition to that when it comes to Cyber security
laws, there are various areas which needed development which comprises of cloud theft, IT and
hacking. In reference to cyber security, it is very essential to make use of the relevant resources
and funds for the purpose to implements the laws related to the cyber security in a effective and
efficient manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Books & Journal
Didenko, A.N., 2020. Cybersecurity regulation in the financial sector: prospects of legal
harmonization in the European Union and beyond. Uniform Law Review, 25(1), pp.125-167.
Felkner, A., Kadobayashi, Y., Janiszewski, M., Fantin, S., Ruiz, J.F., Kozakiewicz, A. and
Blanc, G., 2021. Cybersecurity Research Analysis Report for Europe and Japan (Vol. 75, p. 172).
Springer.
Halouzka, K. and Buřita, L., 2019, May. Cyber Security Strategic Documents Analysis. In 2019
International Conference on Military Technologies (ICMT) (pp. 1-6). IEEE.
Newman, A.L., 2020. Digital Policy-Making in the European Union. Policy-Making in the
European Union, 275.
Toapanta, S.M.T., Gurumendi, A.J. and Gallegos, L.E.M., 2019, December. An approach of
national and international cybersecurity laws and standards to mitigate information risks in
public organizations of ecuador. In Proceedings of the 2019 2nd International Conference on
Education Technology Management (pp. 61-66).
Online
Stevens and Kevin, 2019. Brexit and Cyber Security [Online] Available Through
<https://www.ipohub.org/cybersecurity-laws-regulations/>
Fuster and Lina, 2020. Cybersecurity Regulation in the European Union [Online] Available
Through
<https://link.springer.com/chapter/10.1007/978-3-030-29053-5_5>
John, 2021. Cybersecurity Laws & Regulations [Online] Available Through
<https://www.tandfonline.com/doi/full/10.1080/03071847.2019.1643256>
Books & Journal
Didenko, A.N., 2020. Cybersecurity regulation in the financial sector: prospects of legal
harmonization in the European Union and beyond. Uniform Law Review, 25(1), pp.125-167.
Felkner, A., Kadobayashi, Y., Janiszewski, M., Fantin, S., Ruiz, J.F., Kozakiewicz, A. and
Blanc, G., 2021. Cybersecurity Research Analysis Report for Europe and Japan (Vol. 75, p. 172).
Springer.
Halouzka, K. and Buřita, L., 2019, May. Cyber Security Strategic Documents Analysis. In 2019
International Conference on Military Technologies (ICMT) (pp. 1-6). IEEE.
Newman, A.L., 2020. Digital Policy-Making in the European Union. Policy-Making in the
European Union, 275.
Toapanta, S.M.T., Gurumendi, A.J. and Gallegos, L.E.M., 2019, December. An approach of
national and international cybersecurity laws and standards to mitigate information risks in
public organizations of ecuador. In Proceedings of the 2019 2nd International Conference on
Education Technology Management (pp. 61-66).
Online
Stevens and Kevin, 2019. Brexit and Cyber Security [Online] Available Through
<https://www.ipohub.org/cybersecurity-laws-regulations/>
Fuster and Lina, 2020. Cybersecurity Regulation in the European Union [Online] Available
Through
<https://link.springer.com/chapter/10.1007/978-3-030-29053-5_5>
John, 2021. Cybersecurity Laws & Regulations [Online] Available Through
<https://www.tandfonline.com/doi/full/10.1080/03071847.2019.1643256>
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



