CYB-362 Lab 1: Establishing a VM Lab for Cybersecurity Testing
VerifiedAdded on 2022/09/09
|35
|2571
|18
Practical Assignment
AI Summary
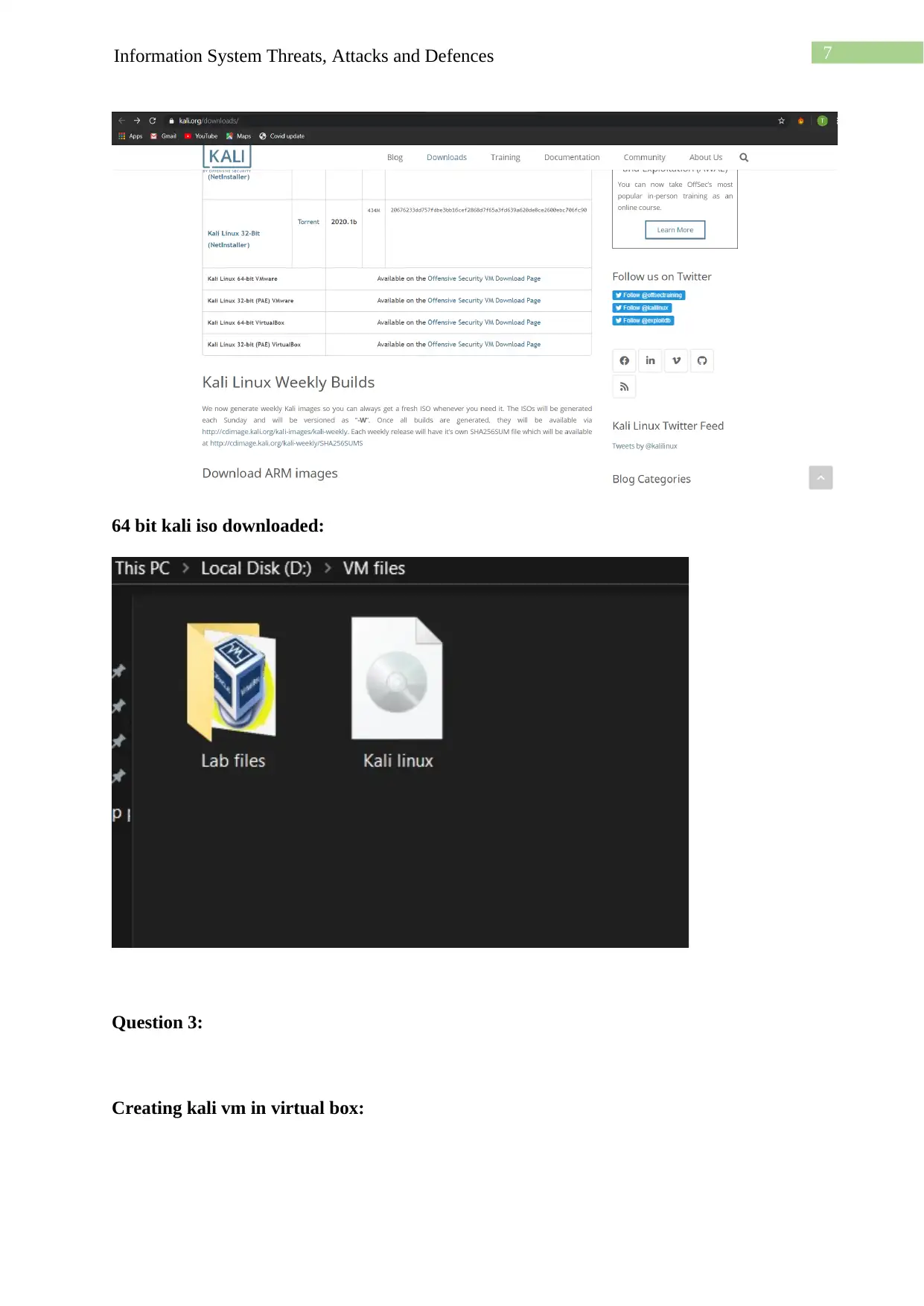
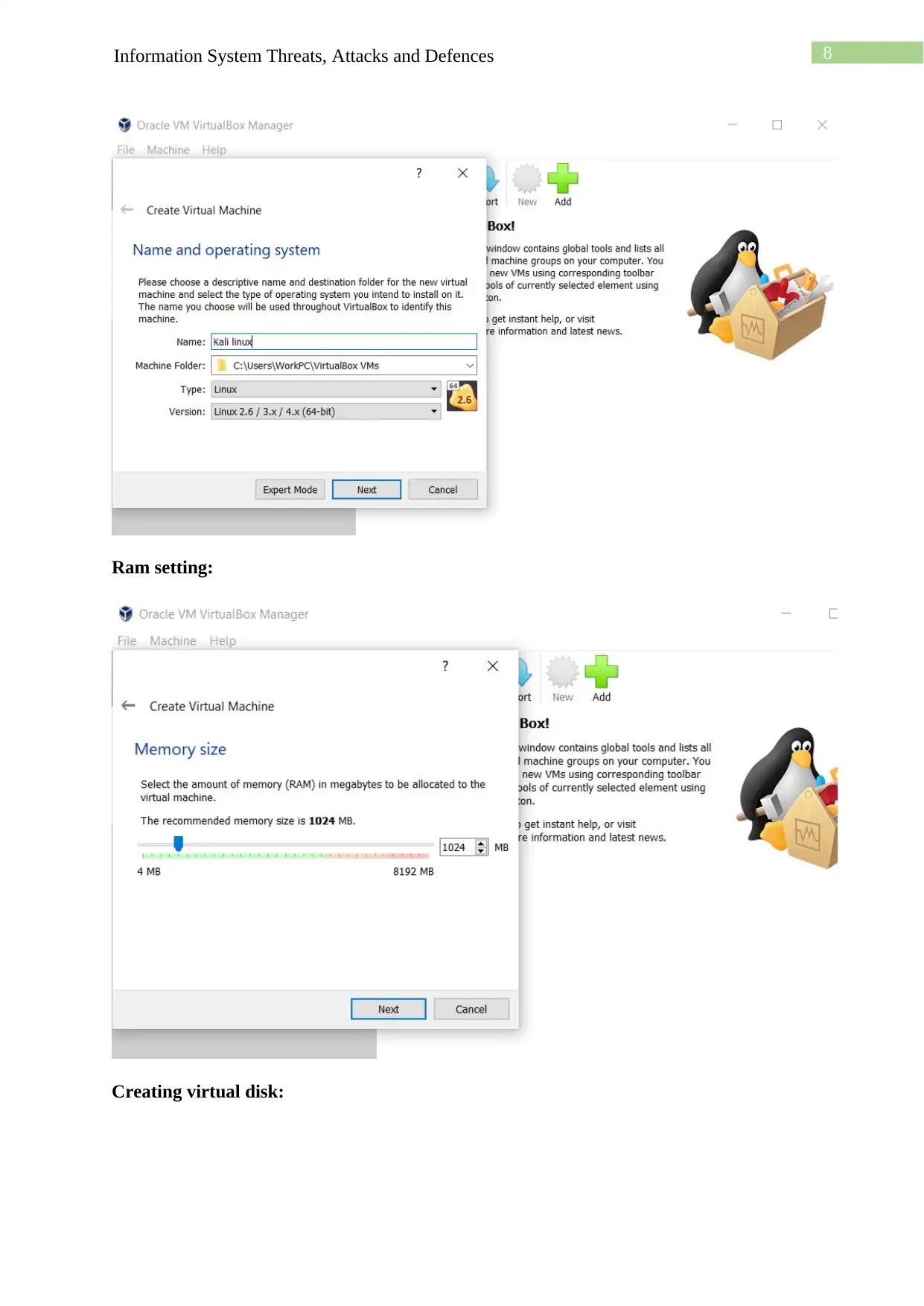
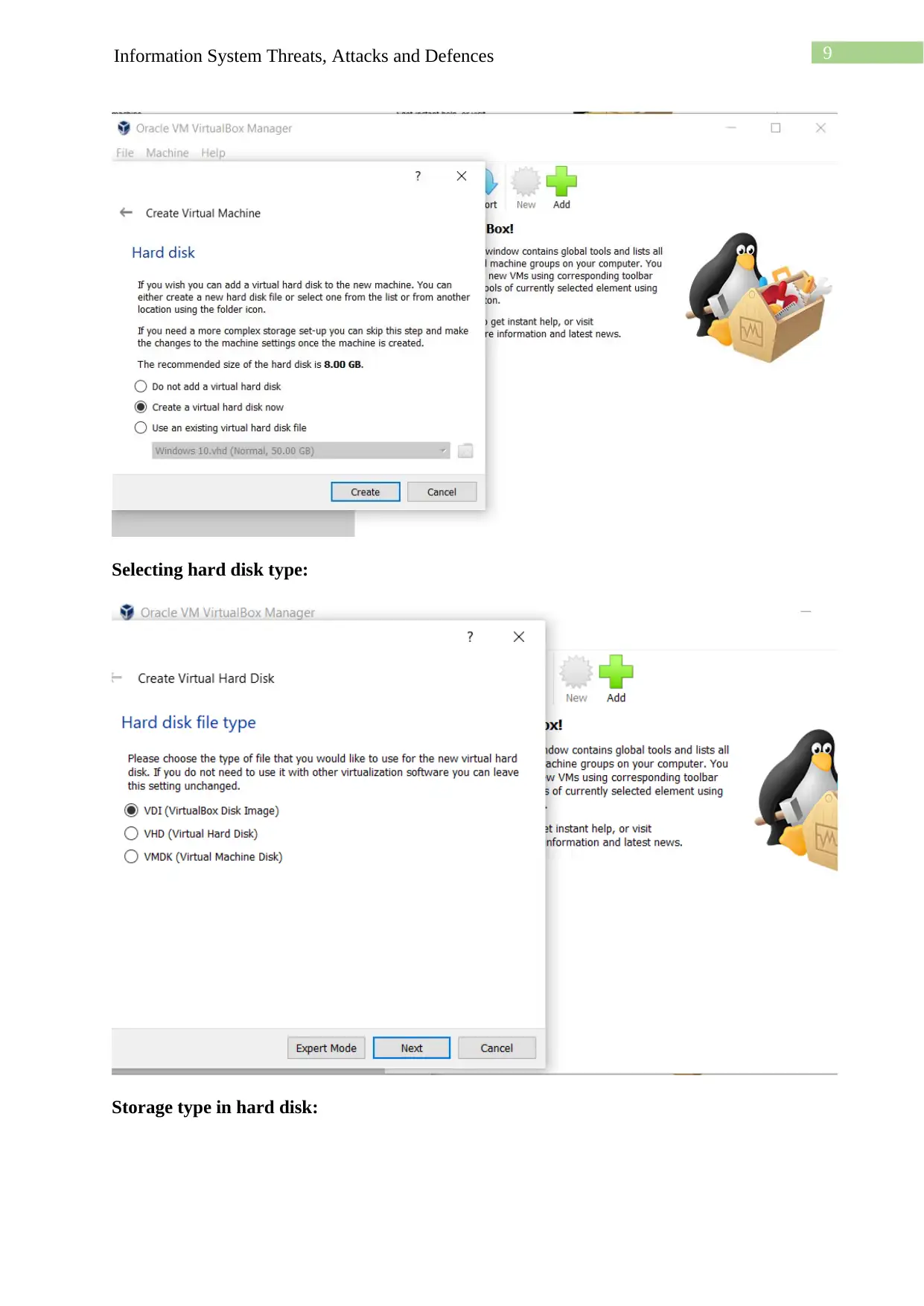
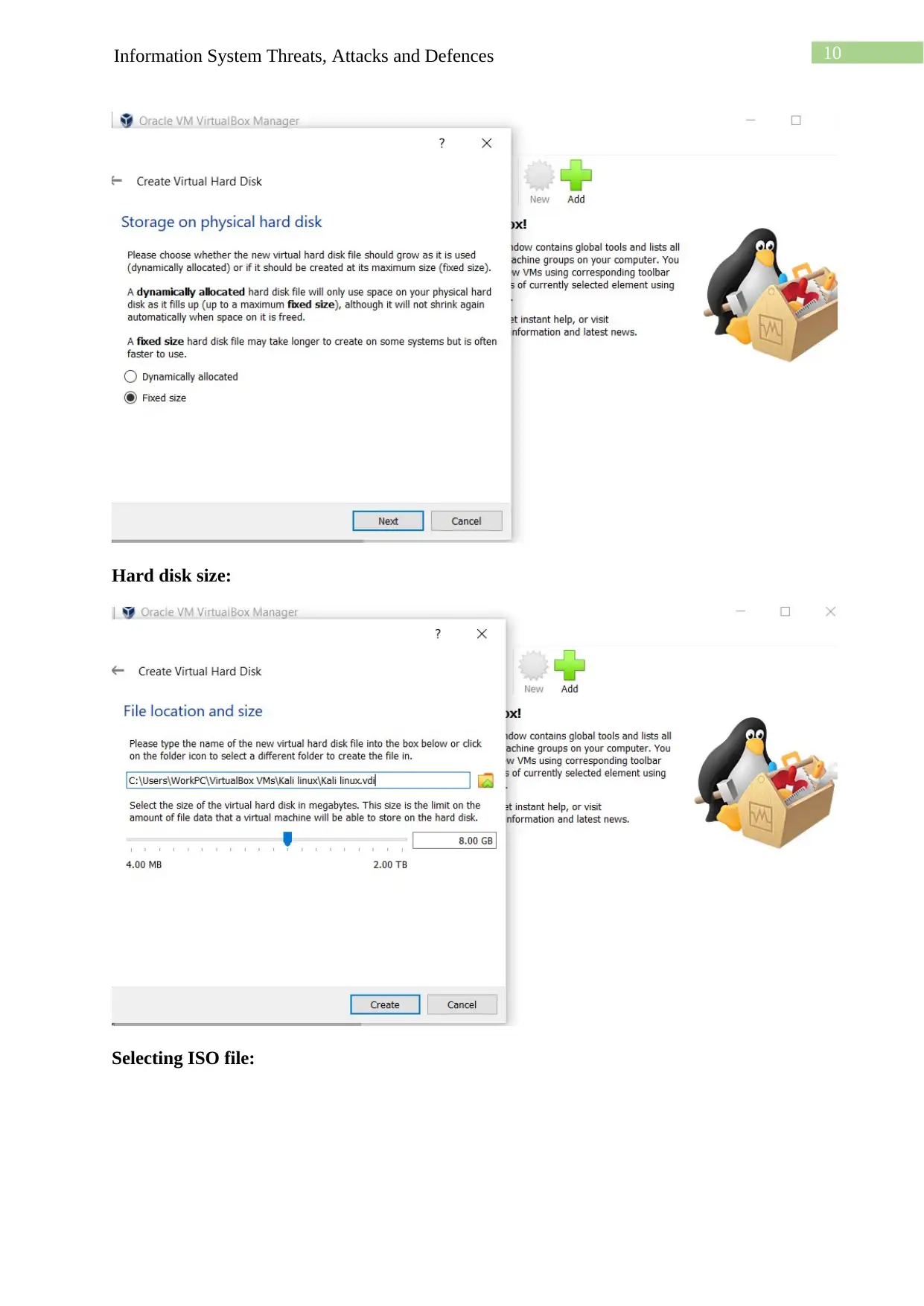
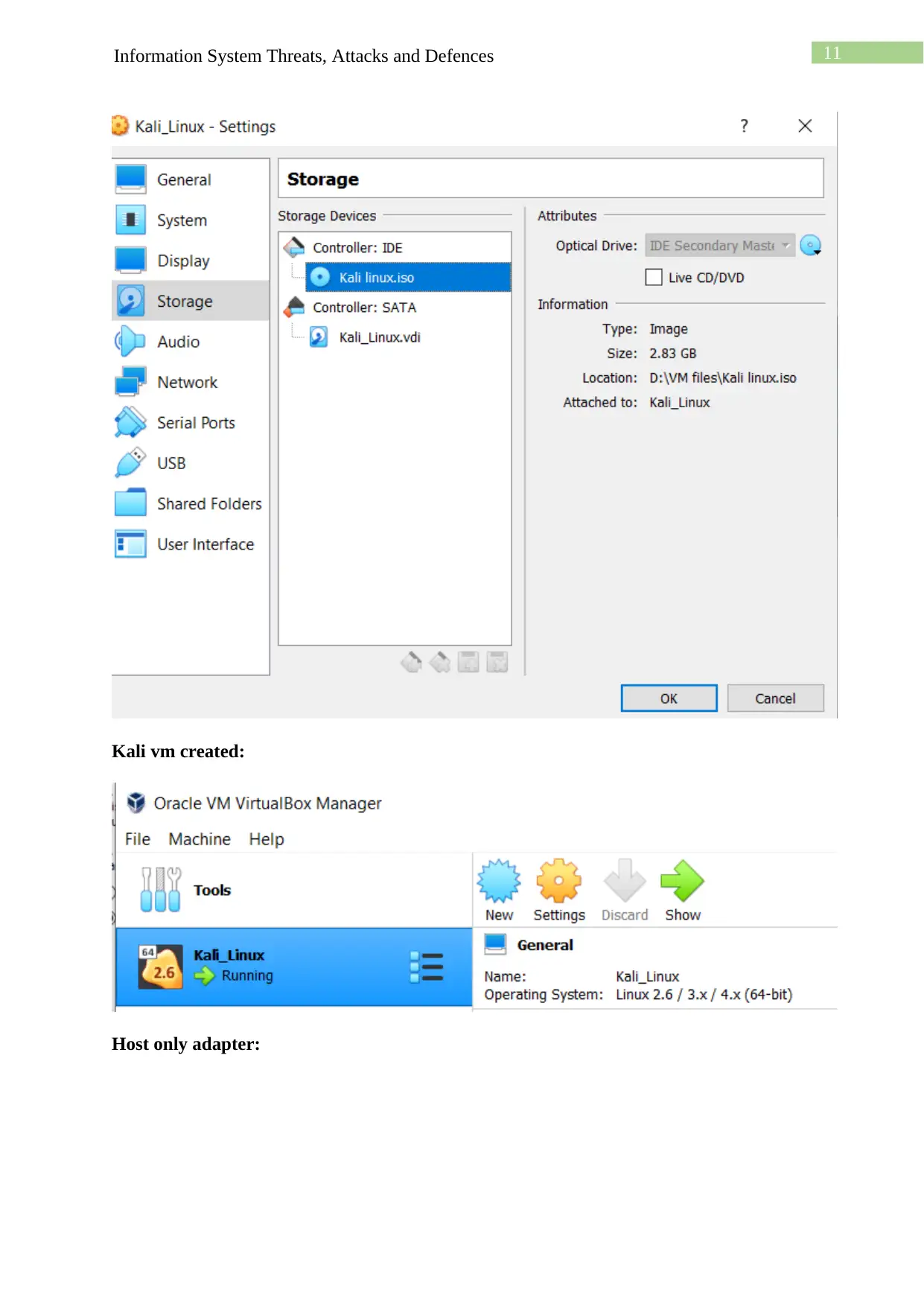
This assignment details the process of creating a virtual machine (VM) lab environment for cybersecurity purposes. The student begins by downloading and installing VirtualBox, followed by the installation of Kali Linux and Windows operating systems as VMs within VirtualBox. The lab setup includes configuring a host-only network to enable communication between the VMs. The student then installs guest additions and explores network connectivity through ping tests and the use of Nmap for network scanning. The assignment also covers setting up and accessing an Apache web server within the Kali Linux environment and utilizing Netcat for network utility. The student demonstrates understanding of the installation processes, network configuration, and the functionality of essential security tools within the virtualized environment. The document provides screenshots and detailed explanations of each step, concluding with a discussion of the challenges faced and the knowledge gained throughout the lab exercise.
1 out of 35




![[object Object]](/_next/static/media/star-bottom.7253800d.svg)