Cybersecurity Analysis and Recommendations for Zoom Printing Company
VerifiedAdded on 2021/02/18
|16
|3609
|44
Report
AI Summary
This report provides a comprehensive analysis of the computer security vulnerabilities within Zoom Printing Company. It identifies several critical issues, including the use of outdated operating systems, lack of security software, insecure data backup practices, and the presence of a compromised Windows 2000 server. The report details the potential consequences of these vulnerabilities, such as ransomware attacks, data breaches, and unauthorized access to sensitive information, particularly given the company's handling of confidential government files. The report proposes specific solutions, such as installing security software, updating systems, implementing secure data backup systems, and upgrading the server infrastructure. It also emphasizes the importance of employee security practices, including unique user accounts and email credentials, to ensure accountability and data confidentiality. The report concludes by comparing the proposed solutions with alternative approaches, emphasizing the cost-effectiveness and improved security posture achieved through the recommended measures, with the aim of protecting Zoom Printing Company from cyber threats.

Running head: COMPUTER SECURITY 1
Computer Security of Zoom
Printing Company
1
Computer Security of Zoom
Printing Company
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER SECURITY 2

COMPUTER SECURITY 3
Table of Contents
Introduction......................................................................................................................................4
Why the chosen cyber security issue is being included within the “top 8”? ..............................6
An explanation/demonstration of the potential consequences of the identified issue.................9
A detailed explanation/demonstration of how you propose to address the issue......................12
Why is your chosen solution better than alternative approaches?.............................................13
A detailed breakdown of the cost in addressing the selected issue...........................................14
Conclusion.....................................................................................................................................15
References......................................................................................................................................16
Table of Contents
Introduction......................................................................................................................................4
Why the chosen cyber security issue is being included within the “top 8”? ..............................6
An explanation/demonstration of the potential consequences of the identified issue.................9
A detailed explanation/demonstration of how you propose to address the issue......................12
Why is your chosen solution better than alternative approaches?.............................................13
A detailed breakdown of the cost in addressing the selected issue...........................................14
Conclusion.....................................................................................................................................15
References......................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY 4
Introduction
Information and data security is the most important aspect of every organization within
the cyber field. Cybersecurity and information security have raised international concerns that
ultimately extend to the economic endangerment of the global economy. In this aspect, the
various key components of the cybersecurity should be considered to ensure data security. An
organization should ensure that the software, hardware, and data are protected against cyber-
related vulnerabilities. Information security in this context involves both cyber-oriented security
and physical security. This report conducts an evaluation of the various components of the zoom
Printing company considering all the cybersecurity issues and then generates recommendations
that should be taken into consideration.
The SOE consists of a mix of Windows 7/10 laptops.
Computer hardware is a vital component of every firm that conducts information
technology-oriented operations. In the context of search engine optimization (SEO), the type and
specification of every computer within the company's network should be standard. In the case
where employees carry their work computers home, there are high chances of contracting
malware due to connection to foreign networks which may be hosted or hijacked by individuals
with malicious intentions. Consequently, bringing their personal computers to work and
connecting them to the work network may result in the spread of malware in the company's
network (Mo et al., 2012). The result is unauthorized access to classified information. The worst
case scenario is one in which data is lost due to viruses or ransom wares. Additionally, having
different operating systems installed in the individual work computers is not recommended since
it makes maintenance tiresome. ZP should make sure the operating system of the work
computers are universal to make sure that patches and system updates are made with a great level
Introduction
Information and data security is the most important aspect of every organization within
the cyber field. Cybersecurity and information security have raised international concerns that
ultimately extend to the economic endangerment of the global economy. In this aspect, the
various key components of the cybersecurity should be considered to ensure data security. An
organization should ensure that the software, hardware, and data are protected against cyber-
related vulnerabilities. Information security in this context involves both cyber-oriented security
and physical security. This report conducts an evaluation of the various components of the zoom
Printing company considering all the cybersecurity issues and then generates recommendations
that should be taken into consideration.
The SOE consists of a mix of Windows 7/10 laptops.
Computer hardware is a vital component of every firm that conducts information
technology-oriented operations. In the context of search engine optimization (SEO), the type and
specification of every computer within the company's network should be standard. In the case
where employees carry their work computers home, there are high chances of contracting
malware due to connection to foreign networks which may be hosted or hijacked by individuals
with malicious intentions. Consequently, bringing their personal computers to work and
connecting them to the work network may result in the spread of malware in the company's
network (Mo et al., 2012). The result is unauthorized access to classified information. The worst
case scenario is one in which data is lost due to viruses or ransom wares. Additionally, having
different operating systems installed in the individual work computers is not recommended since
it makes maintenance tiresome. ZP should make sure the operating system of the work
computers are universal to make sure that patches and system updates are made with a great level
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER SECURITY 5
of consistency. Employees should not take their work computers home or bring their personal
computers to work. Measures should be put in place to restrict the employees from bringing in
foreign devices and from carrying work computing devices home. This solution is better since it
saves the company money that would be used to pay ransoms in cases of ransomware or
compensating clients whose data was compromised by malware attacks. In terms of cost, the
amount of money spent is worthwhile since it guarantees the company optimum information
security.
None of the laptops contains any security software.
Lack of active security software in a personal computer implies that it is not optimized
for security vulnerabilities. A computer that lacks security software is vulnerable to a wide range
of threats. The origin of the attacks ranges from remote attacks from hackers to physical attacks
that may result from executing malicious programs. The result of the attacks is a loss or
compromising of the integrity of information. The vulnerability may be countered by installation
and proper configuration of trusted security software systems (Obrst, Chase, & Markeloff, 2012).
The system administrators may also utilize the system security feature such as windows defender
which provide security optimizations of the entire system without installing secondary software.
Utilizing the security feature on Windows 10 provides real-time security optimization and at no
extra cost. Additionally, proper configuration of the system firewall ensures that there are no
remote attacks on the system by malicious individuals. These functionalities are inbuilt and come
pre-installed in the system so there is no extra cash needed to ensure system security such as
purchasing licenses for secondary software.
Why the chosen cyber security issue is being included within the “top 8”?
This issue is being included in top because it shows that how confidential data of
government can be stolen or hacked in companies if they are not having proper security
of consistency. Employees should not take their work computers home or bring their personal
computers to work. Measures should be put in place to restrict the employees from bringing in
foreign devices and from carrying work computing devices home. This solution is better since it
saves the company money that would be used to pay ransoms in cases of ransomware or
compensating clients whose data was compromised by malware attacks. In terms of cost, the
amount of money spent is worthwhile since it guarantees the company optimum information
security.
None of the laptops contains any security software.
Lack of active security software in a personal computer implies that it is not optimized
for security vulnerabilities. A computer that lacks security software is vulnerable to a wide range
of threats. The origin of the attacks ranges from remote attacks from hackers to physical attacks
that may result from executing malicious programs. The result of the attacks is a loss or
compromising of the integrity of information. The vulnerability may be countered by installation
and proper configuration of trusted security software systems (Obrst, Chase, & Markeloff, 2012).
The system administrators may also utilize the system security feature such as windows defender
which provide security optimizations of the entire system without installing secondary software.
Utilizing the security feature on Windows 10 provides real-time security optimization and at no
extra cost. Additionally, proper configuration of the system firewall ensures that there are no
remote attacks on the system by malicious individuals. These functionalities are inbuilt and come
pre-installed in the system so there is no extra cash needed to ensure system security such as
purchasing licenses for secondary software.
Why the chosen cyber security issue is being included within the “top 8”?
This issue is being included in top because it shows that how confidential data of
government can be stolen or hacked in companies if they are not having proper security

COMPUTER SECURITY 6
equipment installed in computers. Moreover, it is discussed that network requirements should be
as per the configuration of system. If not then it can lead to risk of attacks and ransomware in
systems. Along with this, there were no policies and laws related to cyber security. Due to this
ZP computer systems were storing data without any cryptographic techniques. So it described
that if data is not transferred or stored in cryptographic manner it can lead to data loss.
Furthermore, due to this employee behavior can also be hampered. They also might try to steal
data for their benefit. Additionally, this issue is a major source through which hackers can enter
in database and steal data.
Patch/update levels across laptops is unknown with each workstation encompassing
varying desktop configurations.
The last time any known updates were applied was November 2016.Using computers whose
operating system is not up to date makes the computer vulnerable to exploits that apply to older
versions of the operating system. System patches or updates are created by system developers to
ensure that bugs and vulnerabilities in previous versions of a system are fixed and system users
get the best services from using the system. The result of using outdated versions of desktop
configurations is that the system is exposed to risks that are associated with prior sets of
configurations. The result is the loss or compromising the integrity of information. To counteract
this issues, the system administrator should sign up for newsletters from the system
manufacturers to make sure they keep up with the trend and release of new system patches or
updates (Mo et al., 2012). The administrator should then follow instructions from the system
developers and install the recommended system patches. Additionally, the configurations should
be updated and patched regularly and consistently to ensure optimization of the system.
Following the reports created by the system, developers are better than following instructions
from other unauthorized developers. The instructions from system developers are also certified
equipment installed in computers. Moreover, it is discussed that network requirements should be
as per the configuration of system. If not then it can lead to risk of attacks and ransomware in
systems. Along with this, there were no policies and laws related to cyber security. Due to this
ZP computer systems were storing data without any cryptographic techniques. So it described
that if data is not transferred or stored in cryptographic manner it can lead to data loss.
Furthermore, due to this employee behavior can also be hampered. They also might try to steal
data for their benefit. Additionally, this issue is a major source through which hackers can enter
in database and steal data.
Patch/update levels across laptops is unknown with each workstation encompassing
varying desktop configurations.
The last time any known updates were applied was November 2016.Using computers whose
operating system is not up to date makes the computer vulnerable to exploits that apply to older
versions of the operating system. System patches or updates are created by system developers to
ensure that bugs and vulnerabilities in previous versions of a system are fixed and system users
get the best services from using the system. The result of using outdated versions of desktop
configurations is that the system is exposed to risks that are associated with prior sets of
configurations. The result is the loss or compromising the integrity of information. To counteract
this issues, the system administrator should sign up for newsletters from the system
manufacturers to make sure they keep up with the trend and release of new system patches or
updates (Mo et al., 2012). The administrator should then follow instructions from the system
developers and install the recommended system patches. Additionally, the configurations should
be updated and patched regularly and consistently to ensure optimization of the system.
Following the reports created by the system, developers are better than following instructions
from other unauthorized developers. The instructions from system developers are also certified
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY 7
implying that there are no risks of incompatibility. Following certified instructions will also save
on the cost of fixing breakdown and data recovery that results from system incompatibility.
A QNap TS-412 NAS is used to backup workstation data (at each employee’s discretion)
using WinSCP.
The username/password for the NAS admin account is zoom/zoom.Data and information backup
is important to make sure that data is not lost in case of accidents. In the case of zoom printing
company, handling highly confidential government files is a sensitive task that calls for a backup
system that is reliable and efficient. The current situation in which zoom printing company uses
QNap TS-412 NAS as a backup server and allowing individual employees to initialize backups is
not ideal in the case of handling sensitive information (Obrst, Chase, & Markeloff, 2012). The
ideal situation is one in which zoom printing company uses the available real-time cloud backup
services to back up their systems. Consequently, the system administrators should put in place
strategies allow automatic system backup in a consistent manner to ensure efficiency in the
process (Yan et al., 2012). Additionally, the system administrator should formulate unique
credentials in the order of username and password. The backup criteria should make sure only
specific authorized employees have access to the server to conduct backups. A backup schedule
should be created in which all computers sync at the same time maybe every evening before
logging out. This will make the backup process efficient and ensure consistent backup of all the
information in the workstations. Additionally, a credible and efficient backup of software should
be used such as NovaBackup PC and Acronis True Image among others. This will save on the
money that would be used for data recovery processes in the case of data losses.
A Windows 2000 Server was previously operational in the organization but a power surge
resulted in hardware no longer functioning.
implying that there are no risks of incompatibility. Following certified instructions will also save
on the cost of fixing breakdown and data recovery that results from system incompatibility.
A QNap TS-412 NAS is used to backup workstation data (at each employee’s discretion)
using WinSCP.
The username/password for the NAS admin account is zoom/zoom.Data and information backup
is important to make sure that data is not lost in case of accidents. In the case of zoom printing
company, handling highly confidential government files is a sensitive task that calls for a backup
system that is reliable and efficient. The current situation in which zoom printing company uses
QNap TS-412 NAS as a backup server and allowing individual employees to initialize backups is
not ideal in the case of handling sensitive information (Obrst, Chase, & Markeloff, 2012). The
ideal situation is one in which zoom printing company uses the available real-time cloud backup
services to back up their systems. Consequently, the system administrators should put in place
strategies allow automatic system backup in a consistent manner to ensure efficiency in the
process (Yan et al., 2012). Additionally, the system administrator should formulate unique
credentials in the order of username and password. The backup criteria should make sure only
specific authorized employees have access to the server to conduct backups. A backup schedule
should be created in which all computers sync at the same time maybe every evening before
logging out. This will make the backup process efficient and ensure consistent backup of all the
information in the workstations. Additionally, a credible and efficient backup of software should
be used such as NovaBackup PC and Acronis True Image among others. This will save on the
money that would be used for data recovery processes in the case of data losses.
A Windows 2000 Server was previously operational in the organization but a power surge
resulted in hardware no longer functioning.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
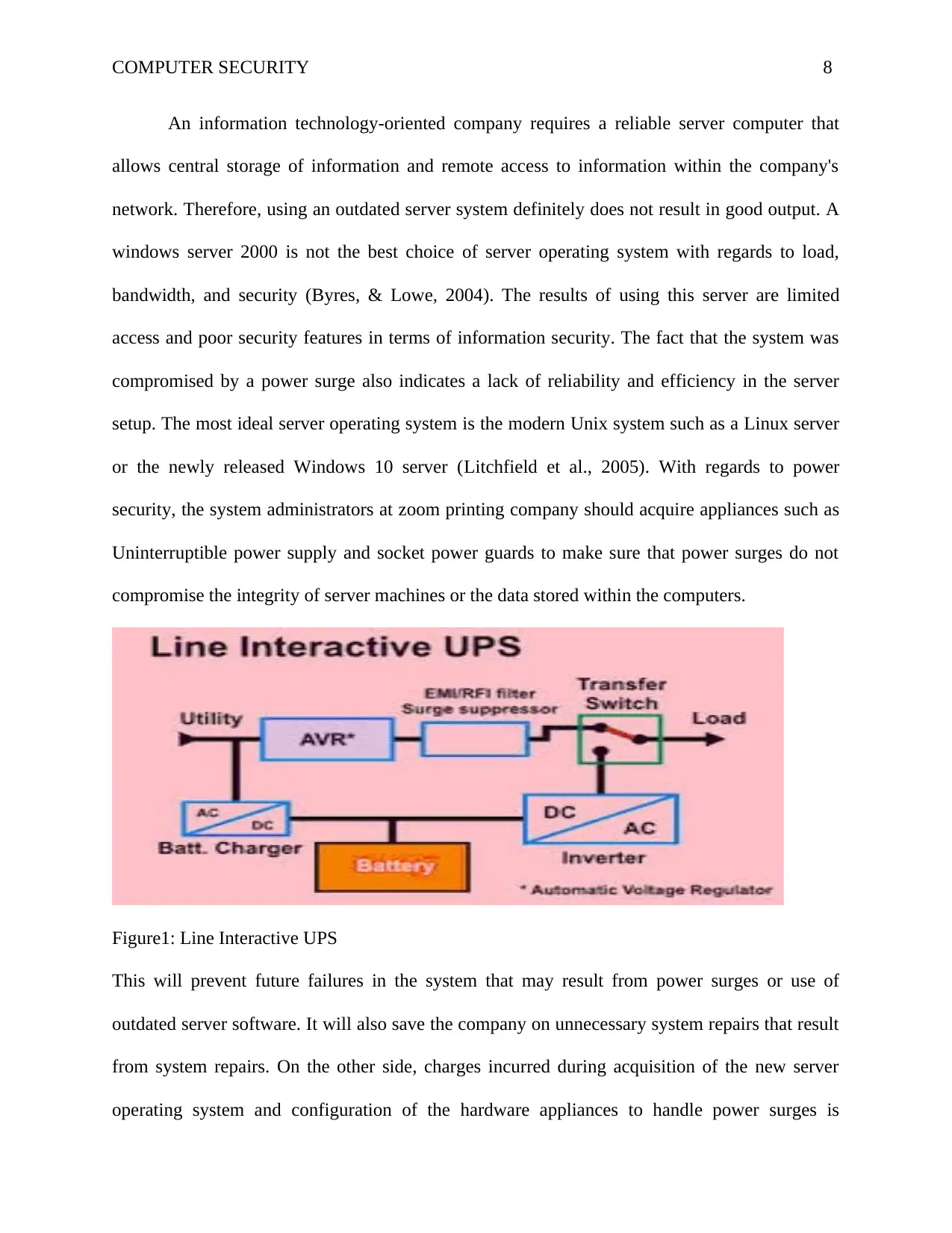
COMPUTER SECURITY 8
An information technology-oriented company requires a reliable server computer that
allows central storage of information and remote access to information within the company's
network. Therefore, using an outdated server system definitely does not result in good output. A
windows server 2000 is not the best choice of server operating system with regards to load,
bandwidth, and security (Byres, & Lowe, 2004). The results of using this server are limited
access and poor security features in terms of information security. The fact that the system was
compromised by a power surge also indicates a lack of reliability and efficiency in the server
setup. The most ideal server operating system is the modern Unix system such as a Linux server
or the newly released Windows 10 server (Litchfield et al., 2005). With regards to power
security, the system administrators at zoom printing company should acquire appliances such as
Uninterruptible power supply and socket power guards to make sure that power surges do not
compromise the integrity of server machines or the data stored within the computers.
Figure1: Line Interactive UPS
This will prevent future failures in the system that may result from power surges or use of
outdated server software. It will also save the company on unnecessary system repairs that result
from system repairs. On the other side, charges incurred during acquisition of the new server
operating system and configuration of the hardware appliances to handle power surges is
An information technology-oriented company requires a reliable server computer that
allows central storage of information and remote access to information within the company's
network. Therefore, using an outdated server system definitely does not result in good output. A
windows server 2000 is not the best choice of server operating system with regards to load,
bandwidth, and security (Byres, & Lowe, 2004). The results of using this server are limited
access and poor security features in terms of information security. The fact that the system was
compromised by a power surge also indicates a lack of reliability and efficiency in the server
setup. The most ideal server operating system is the modern Unix system such as a Linux server
or the newly released Windows 10 server (Litchfield et al., 2005). With regards to power
security, the system administrators at zoom printing company should acquire appliances such as
Uninterruptible power supply and socket power guards to make sure that power surges do not
compromise the integrity of server machines or the data stored within the computers.
Figure1: Line Interactive UPS
This will prevent future failures in the system that may result from power surges or use of
outdated server software. It will also save the company on unnecessary system repairs that result
from system repairs. On the other side, charges incurred during acquisition of the new server
operating system and configuration of the hardware appliances to handle power surges is

COMPUTER SECURITY 9
worthwhile since it promotes information integrity. The purchase of the electrical appliances
such as the UPS, power guard and backup batteries are not very expensive based on
considerations of the later, which results in information loss thus making the acquisition cost
worthwhile.
An explanation/demonstration of the potential consequences of the identified
issue.
In July 2017 – two workstations succumbed to a ransomware attack and ZP paid the
ransom.
Ransomware ware, in this case, refers to malware that prevents access to information
unless a bounty is paid to the malicious individuals. Ransomware attacks may result in data loss
as well as compromising the integrity of information which it does not foster reliability in the
case of handling classified government documents (Hampton, & Baig, 2015). The ideal solution
to ransomware is through a consistent update of the computer systems and secure configuration
of the system security software and firewalls. Use of anti-ransomware security software is the
ideal solution in comparison to paying the ransom. Configuring the firewall to block execution of
ransomware scripts is also very effective and cheap in comparison to purchasing secondary
security software. Additionally, using servers with uptight security features that have policies
preventing such attacks saves on the cost of paying off ransoms to gain access to information.
Adoption of the recommended system setting is cheap in comparison to paying off ransoms.
Example is evident in the below diagram:
worthwhile since it promotes information integrity. The purchase of the electrical appliances
such as the UPS, power guard and backup batteries are not very expensive based on
considerations of the later, which results in information loss thus making the acquisition cost
worthwhile.
An explanation/demonstration of the potential consequences of the identified
issue.
In July 2017 – two workstations succumbed to a ransomware attack and ZP paid the
ransom.
Ransomware ware, in this case, refers to malware that prevents access to information
unless a bounty is paid to the malicious individuals. Ransomware attacks may result in data loss
as well as compromising the integrity of information which it does not foster reliability in the
case of handling classified government documents (Hampton, & Baig, 2015). The ideal solution
to ransomware is through a consistent update of the computer systems and secure configuration
of the system security software and firewalls. Use of anti-ransomware security software is the
ideal solution in comparison to paying the ransom. Configuring the firewall to block execution of
ransomware scripts is also very effective and cheap in comparison to purchasing secondary
security software. Additionally, using servers with uptight security features that have policies
preventing such attacks saves on the cost of paying off ransoms to gain access to information.
Adoption of the recommended system setting is cheap in comparison to paying off ransoms.
Example is evident in the below diagram:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY
10
Figure 2: How ransomware works
Employees can access each other’s computers and email accounts.
In the setting of handling highly classified and confidential government information,
confidentiality is a vital consideration. With this in mind, every employee should have a secure
computer user account and confidential email credentials. The implication of sharing email and
user accounts is lack of accountability since individual employees are not accountable for
activities conducted using specific email accounts (Liu et al, 2012). The ideal situation is one in
which every employee has a unique user account in their personal work computers through
which they can sign in to their personal accounts. They should also have unique email accounts
through which they receive work newsletters. This scenario is better than having universal email
accounts or unprotected user accounts in the work computers. Assigning every employee, a set of
user account credentials will foster accountability since activities are associated with the various
corresponding account sessions. This means that employee activity can be monitored based on
the activities carried out using the individual account details. Additionally, the solution that
entails the creation of individual accounts does not require any financial support. Example is
evident in the below diagram:
10
Figure 2: How ransomware works
Employees can access each other’s computers and email accounts.
In the setting of handling highly classified and confidential government information,
confidentiality is a vital consideration. With this in mind, every employee should have a secure
computer user account and confidential email credentials. The implication of sharing email and
user accounts is lack of accountability since individual employees are not accountable for
activities conducted using specific email accounts (Liu et al, 2012). The ideal situation is one in
which every employee has a unique user account in their personal work computers through
which they can sign in to their personal accounts. They should also have unique email accounts
through which they receive work newsletters. This scenario is better than having universal email
accounts or unprotected user accounts in the work computers. Assigning every employee, a set of
user account credentials will foster accountability since activities are associated with the various
corresponding account sessions. This means that employee activity can be monitored based on
the activities carried out using the individual account details. Additionally, the solution that
entails the creation of individual accounts does not require any financial support. Example is
evident in the below diagram:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER SECURITY
11
Figure 3:7client interaction
It can lead to cyber crime
The non existence of policies and laws can lead to cyber crimes. It can allow
unauthorized people to access government data and share it with some groups. This can create a
high risk and major consequences. Moreover, government will not be able to catch the thief. This
will also encourage other to get involve in it. Apart from this, company will suffer a huge loss.
Therefore, there will be increase in number of cyber crimes in other companies as well as
countries.
Confidential data is emailed/stored without using any cryptographic techniques.
Security and confidentiality of sensitive and classified government information are vital
in this setup. As a result, storage and transfer of information with a low level of security are not
ideal in the case (Yan et al., 2012). The result is that there is low confidentiality and
eavesdropping on the transmissions may leak data which is meant to be classified. The
implication is that the term confidential is obsolete.
11
Figure 3:7client interaction
It can lead to cyber crime
The non existence of policies and laws can lead to cyber crimes. It can allow
unauthorized people to access government data and share it with some groups. This can create a
high risk and major consequences. Moreover, government will not be able to catch the thief. This
will also encourage other to get involve in it. Apart from this, company will suffer a huge loss.
Therefore, there will be increase in number of cyber crimes in other companies as well as
countries.
Confidential data is emailed/stored without using any cryptographic techniques.
Security and confidentiality of sensitive and classified government information are vital
in this setup. As a result, storage and transfer of information with a low level of security are not
ideal in the case (Yan et al., 2012). The result is that there is low confidentiality and
eavesdropping on the transmissions may leak data which is meant to be classified. The
implication is that the term confidential is obsolete.
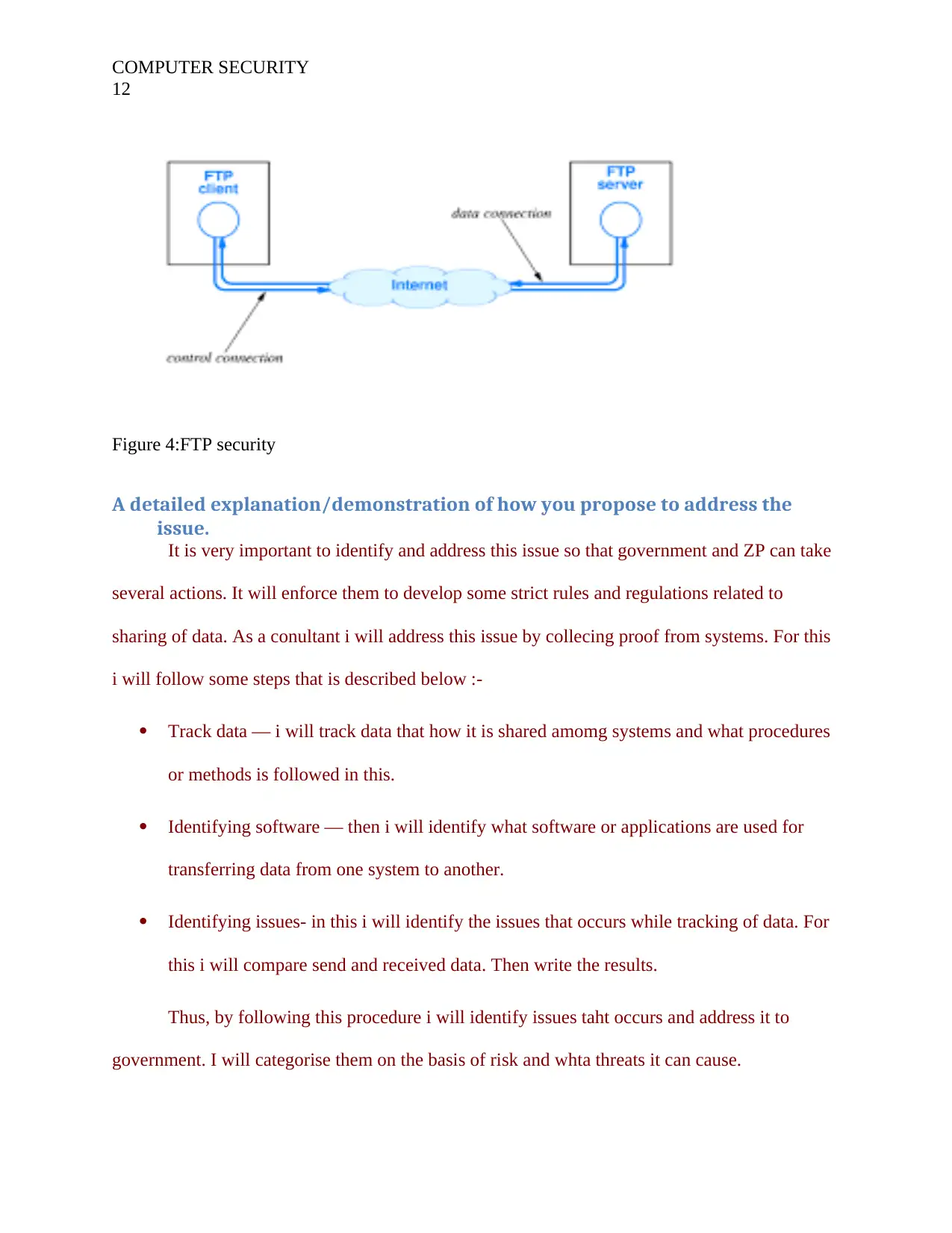
COMPUTER SECURITY
12
Figure 4:FTP security
A detailed explanation/demonstration of how you propose to address the
issue.
It is very important to identify and address this issue so that government and ZP can take
several actions. It will enforce them to develop some strict rules and regulations related to
sharing of data. As a conultant i will address this issue by collecing proof from systems. For this
i will follow some steps that is described below :-
Track data — i will track data that how it is shared amomg systems and what procedures
or methods is followed in this.
Identifying software — then i will identify what software or applications are used for
transferring data from one system to another.
Identifying issues- in this i will identify the issues that occurs while tracking of data. For
this i will compare send and received data. Then write the results.
Thus, by following this procedure i will identify issues taht occurs and address it to
government. I will categorise them on the basis of risk and whta threats it can cause.
12
Figure 4:FTP security
A detailed explanation/demonstration of how you propose to address the
issue.
It is very important to identify and address this issue so that government and ZP can take
several actions. It will enforce them to develop some strict rules and regulations related to
sharing of data. As a conultant i will address this issue by collecing proof from systems. For this
i will follow some steps that is described below :-
Track data — i will track data that how it is shared amomg systems and what procedures
or methods is followed in this.
Identifying software — then i will identify what software or applications are used for
transferring data from one system to another.
Identifying issues- in this i will identify the issues that occurs while tracking of data. For
this i will compare send and received data. Then write the results.
Thus, by following this procedure i will identify issues taht occurs and address it to
government. I will categorise them on the basis of risk and whta threats it can cause.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




