CP5631 Network Redesign and Cloud Computing for Data Analytics Firm
VerifiedAdded on 2023/06/11
|13
|1798
|66
Report
AI Summary
This report presents a network design and cloud computing proposal for an Australian data analytics company. It includes a network diagram connecting multiple branches, subnetting using VLSM, and IP address assignments. The report evaluates appropriate hardware devices based on a weighted decision matrix, considering factors like cost, configuration, and reliability. A cloud computing proposal is presented to reduce maintenance costs and increase efficiency, addressing security concerns with encryption and monitoring. The document concludes by weighing the risks and benefits of cloud deployment, emphasizing the importance of vendor selection and data availability.

Running head: INTERNET FUNDAMENTALS
Internet Fundamentals
Name of the Student
Name of the University
Author’s Note
Internet Fundamentals
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNET FUNDAMENTALS
Table of Contents
Part 1 - Executive Summary......................................................................................................2
Purpose...................................................................................................................................2
Scope......................................................................................................................................2
Objectives...............................................................................................................................2
Part 2 - Network Specifications and Diagram............................................................................3
Network Structure..................................................................................................................3
Part 3 – Network subnetting using VLSM.................................................................................3
Subnetting..............................................................................................................................3
PART 4 - Research on the appropriate device...........................................................................6
Executive Summary...............................................................................................................6
Weighted Decision Matrix – hardware resource requirements analysis................................6
Budget....................................................................................................................................7
PART 5 – Cloud computing proposal........................................................................................8
Introduction............................................................................................................................8
Relocation of the in-house servers.........................................................................................9
Security..................................................................................................................................9
Issues......................................................................................................................................9
Conclusion............................................................................................................................10
Bibliography.............................................................................................................................11
INTERNET FUNDAMENTALS
Table of Contents
Part 1 - Executive Summary......................................................................................................2
Purpose...................................................................................................................................2
Scope......................................................................................................................................2
Objectives...............................................................................................................................2
Part 2 - Network Specifications and Diagram............................................................................3
Network Structure..................................................................................................................3
Part 3 – Network subnetting using VLSM.................................................................................3
Subnetting..............................................................................................................................3
PART 4 - Research on the appropriate device...........................................................................6
Executive Summary...............................................................................................................6
Weighted Decision Matrix – hardware resource requirements analysis................................6
Budget....................................................................................................................................7
PART 5 – Cloud computing proposal........................................................................................8
Introduction............................................................................................................................8
Relocation of the in-house servers.........................................................................................9
Security..................................................................................................................................9
Issues......................................................................................................................................9
Conclusion............................................................................................................................10
Bibliography.............................................................................................................................11

2
INTERNET FUNDAMENTALS
INTERNET FUNDAMENTALS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INTERNET FUNDAMENTALS
Part 1 - Executive Summary
Purpose
The network diagram is created for Australian Data Analytics Company for
connecting the different branches of the organization and enabling the
employees to communicate with each other. The different technologies
that can be applied for development of the network is evaluated and
applied for the development of the network framework.
Scope
The main scope identified for the development of the network solution for
Australian Data Analytics Company is to connect the different branches of
the organization and enable them to communicate with each other by
sending and receiving data packets from different sources in the network.
A VPN connection should be established with the remote router such that
the user can access the resources and organizational network using a
secure communication channel.
Objectives
The objectives for the development of the network solution are as follows:
To create a model of the network and create an event log for increasing the security of
the network solution.
To increase the scalability of the network and extent the network for addition of new
branches for the organization.
To create redundant link for connecting the branches with each other such that the
data can be sent using different path.
INTERNET FUNDAMENTALS
Part 1 - Executive Summary
Purpose
The network diagram is created for Australian Data Analytics Company for
connecting the different branches of the organization and enabling the
employees to communicate with each other. The different technologies
that can be applied for development of the network is evaluated and
applied for the development of the network framework.
Scope
The main scope identified for the development of the network solution for
Australian Data Analytics Company is to connect the different branches of
the organization and enable them to communicate with each other by
sending and receiving data packets from different sources in the network.
A VPN connection should be established with the remote router such that
the user can access the resources and organizational network using a
secure communication channel.
Objectives
The objectives for the development of the network solution are as follows:
To create a model of the network and create an event log for increasing the security of
the network solution.
To increase the scalability of the network and extent the network for addition of new
branches for the organization.
To create redundant link for connecting the branches with each other such that the
data can be sent using different path.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INTERNET FUNDAMENTALS
To maintain the network such that the performance of the network is not down and
the device are secured with the latest patch.
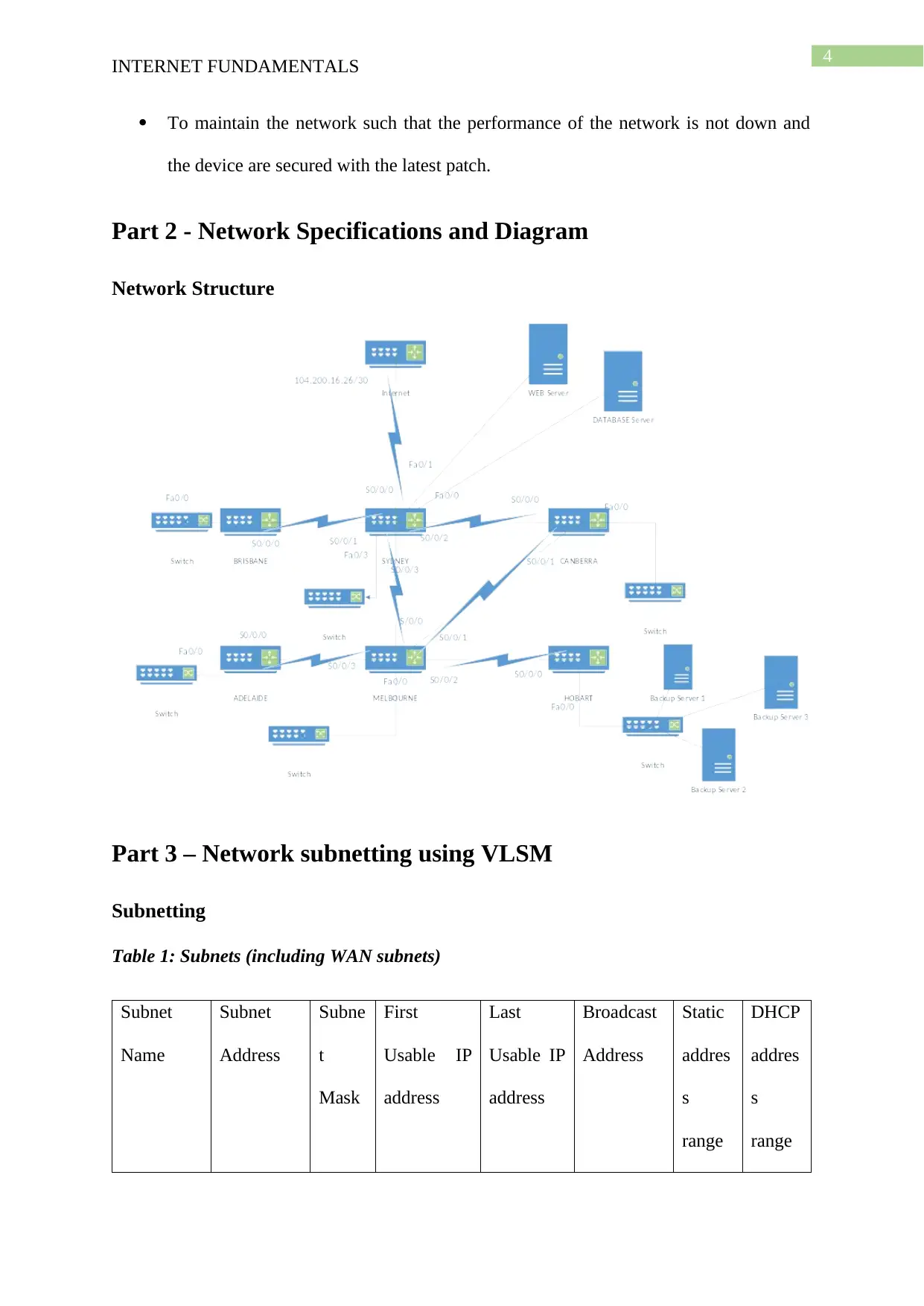
Part 2 - Network Specifications and Diagram
Network Structure
Part 3 – Network subnetting using VLSM
Subnetting
Table 1: Subnets (including WAN subnets)
Subnet
Name
Subnet
Address
Subne
t
Mask
First
Usable IP
address
Last
Usable IP
address
Broadcast
Address
Static
addres
s
range
DHCP
addres
s
range
INTERNET FUNDAMENTALS
To maintain the network such that the performance of the network is not down and
the device are secured with the latest patch.
Part 2 - Network Specifications and Diagram
Network Structure
Part 3 – Network subnetting using VLSM
Subnetting
Table 1: Subnets (including WAN subnets)
Subnet
Name
Subnet
Address
Subne
t
Mask
First
Usable IP
address
Last
Usable IP
address
Broadcast
Address
Static
addres
s
range
DHCP
addres
s
range
5
INTERNET FUNDAMENTALS
Sydney 128.1.0.0 /23 128.1.0.1 128.1.1.2
54
128.1.1.25
5
128.1.
0.1 -
128.1.
0.253
128.1.
0.254
-
128.1.
1.255
Brisbane 128.1.2.0 /24 128.1.2.1 128.1.2.2
54
128.1.2.25
5
128.1.
2.1 -
128.1.
2.104
128.1.
2.104
–
128.1.
2.254
Melbourn
e
128.1.3.0 /25 128.1.3.1 128.1.3.1
26
128.1.3.12
7
128.1.
3.1 –
128.1.
3.78
128.1.
3.79 -
128.1.
3.126
Adelaide 128.1.3.12
8
/25 128.1.3.129 128.1.3.2
54
128.1.3.25
5
Canberra 128.1.4.0 /26 128.1.4.1 128.1.4.6
2
128.1.4.6
3
Hobart 128.1.4.64 /27 128.1.4.65 128.1.4.9
4
128.1.4.95
Table 2: Router Interfaces
Location Interface IP address Subnet Mask
Sydney s0/0/0 104.200.16.26 /30
INTERNET FUNDAMENTALS
Sydney 128.1.0.0 /23 128.1.0.1 128.1.1.2
54
128.1.1.25
5
128.1.
0.1 -
128.1.
0.253
128.1.
0.254
-
128.1.
1.255
Brisbane 128.1.2.0 /24 128.1.2.1 128.1.2.2
54
128.1.2.25
5
128.1.
2.1 -
128.1.
2.104
128.1.
2.104
–
128.1.
2.254
Melbourn
e
128.1.3.0 /25 128.1.3.1 128.1.3.1
26
128.1.3.12
7
128.1.
3.1 –
128.1.
3.78
128.1.
3.79 -
128.1.
3.126
Adelaide 128.1.3.12
8
/25 128.1.3.129 128.1.3.2
54
128.1.3.25
5
Canberra 128.1.4.0 /26 128.1.4.1 128.1.4.6
2
128.1.4.6
3
Hobart 128.1.4.64 /27 128.1.4.65 128.1.4.9
4
128.1.4.95
Table 2: Router Interfaces
Location Interface IP address Subnet Mask
Sydney s0/0/0 104.200.16.26 /30
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTERNET FUNDAMENTALS
s0/0/1
s0/0/2
s0/0/3
Fa0/1
Fa0/2
Fa0/3
128.1.0.1
128.1.0.5
128.1.0.10
128.1.0.15
128.1.0.20
128.1.0.25
/30
/30
/30
/30
/30
Brisbane S0/0/0
Fa0/0
128.1.0.2
128.1.2.1
/30
/24
Melbourne S0/0/0
S0/0/1
S0/0/2
S0/0/3
Fa0/0
128.1.0.11
128.1.3.1
128.1.3.5
128.1.3.10
128.1.3.20
/30
/30
/30
/30
/25
Adelaide S0/0/0
Fa0/0
128.1.3.11
128.1.3.129
/30
/25
Canberra S0/0/0
S0/0/1
Fa0/0
128.1.0.6
128.1.3.2
128.1.4.1
/30
/30
/26
Hobart S0/0/0
Fa0/0
128.1.3.6
128.1.4.65
/30
/27
Table 3: Servers
Location Server Name IP address Subnet Mask
Sydney Web server
Database Server
128.1.0.16
128.1.0.26
/30
/30
Hobart Backup server 1 128.1.4.66 /27
INTERNET FUNDAMENTALS
s0/0/1
s0/0/2
s0/0/3
Fa0/1
Fa0/2
Fa0/3
128.1.0.1
128.1.0.5
128.1.0.10
128.1.0.15
128.1.0.20
128.1.0.25
/30
/30
/30
/30
/30
Brisbane S0/0/0
Fa0/0
128.1.0.2
128.1.2.1
/30
/24
Melbourne S0/0/0
S0/0/1
S0/0/2
S0/0/3
Fa0/0
128.1.0.11
128.1.3.1
128.1.3.5
128.1.3.10
128.1.3.20
/30
/30
/30
/30
/25
Adelaide S0/0/0
Fa0/0
128.1.3.11
128.1.3.129
/30
/25
Canberra S0/0/0
S0/0/1
Fa0/0
128.1.0.6
128.1.3.2
128.1.4.1
/30
/30
/26
Hobart S0/0/0
Fa0/0
128.1.3.6
128.1.4.65
/30
/27
Table 3: Servers
Location Server Name IP address Subnet Mask
Sydney Web server
Database Server
128.1.0.16
128.1.0.26
/30
/30
Hobart Backup server 1 128.1.4.66 /27
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INTERNET FUNDAMENTALS
Backup Server
2
Backup Server
3
128.1.4.67
128.1.4.68 /27
/27
PART 4 - Research on the appropriate device
Executive Summary
The Hobart and the Sydney branch network should be configured with the
enforcement of the security mechanism because this branches are connected with the servers
and the access of the servers must be limited depending upon the group of users. The wireless
access point should also be configured with encryption algorithm such that it is not kept open
for all the users. A weighted and decision matrix is created for the network such that the
feasibility and scalability of the network solution is identified and effective decision is taken
for the completion of the project within the allocated budget.
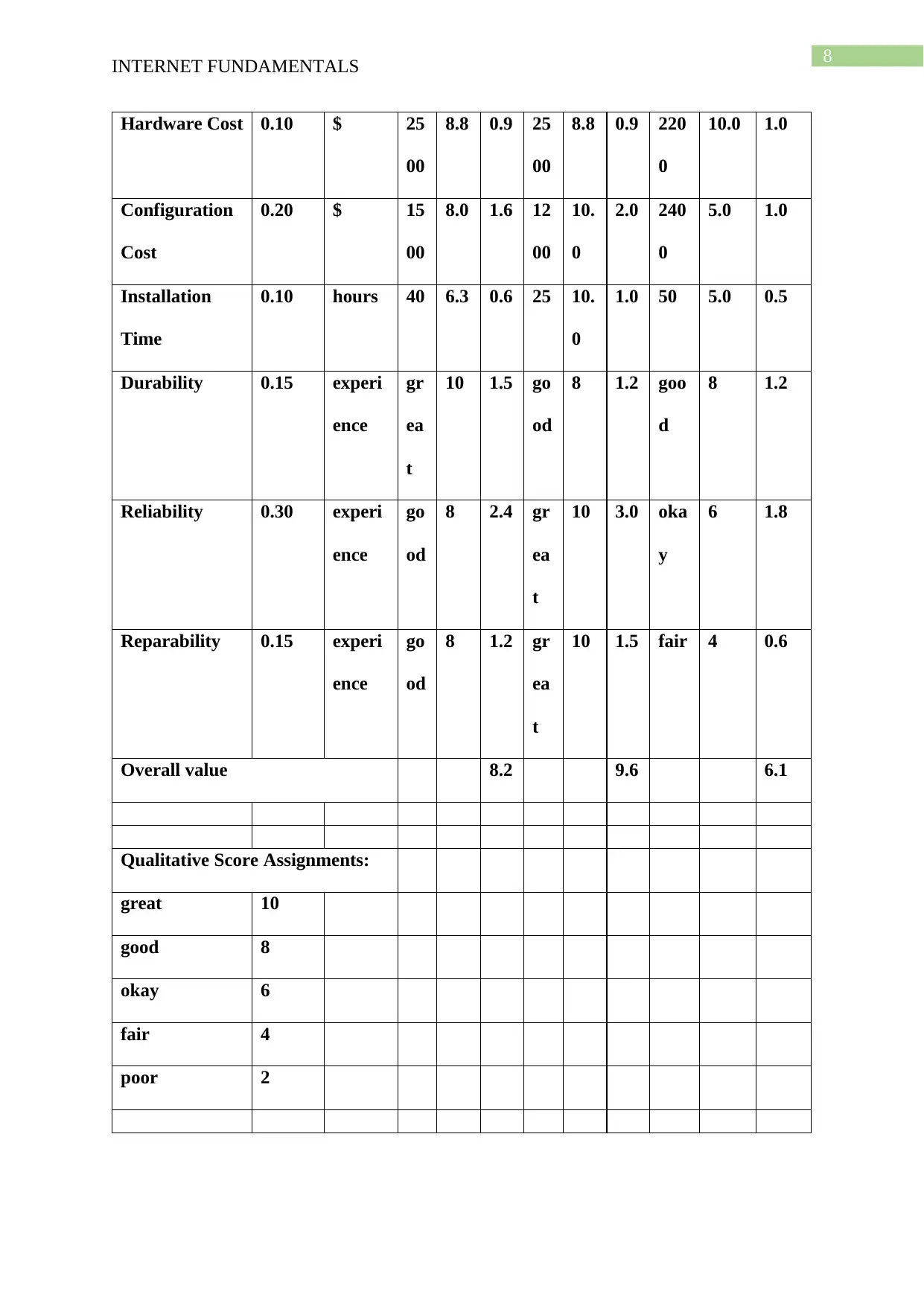
Weighted Decision Matrix – hardware resource requirements analysis
Decision matrix for the design a network
Network Design Hobart
Network
Sydney
Network
Designing the
whole Network
Objective Weigh
ting
Factor
Param
eter
M
ag
.
Sc
ore
Va
lue
M
ag
.
Sc
ore
Va
lue
Ma
g.
Scor
e
Valu
e
INTERNET FUNDAMENTALS
Backup Server
2
Backup Server
3
128.1.4.67
128.1.4.68 /27
/27
PART 4 - Research on the appropriate device
Executive Summary
The Hobart and the Sydney branch network should be configured with the
enforcement of the security mechanism because this branches are connected with the servers
and the access of the servers must be limited depending upon the group of users. The wireless
access point should also be configured with encryption algorithm such that it is not kept open
for all the users. A weighted and decision matrix is created for the network such that the
feasibility and scalability of the network solution is identified and effective decision is taken
for the completion of the project within the allocated budget.
Weighted Decision Matrix – hardware resource requirements analysis
Decision matrix for the design a network
Network Design Hobart
Network
Sydney
Network
Designing the
whole Network
Objective Weigh
ting
Factor
Param
eter
M
ag
.
Sc
ore
Va
lue
M
ag
.
Sc
ore
Va
lue
Ma
g.
Scor
e
Valu
e
8
INTERNET FUNDAMENTALS
Hardware Cost 0.10 $ 25
00
8.8 0.9 25
00
8.8 0.9 220
0
10.0 1.0
Configuration
Cost
0.20 $ 15
00
8.0 1.6 12
00
10.
0
2.0 240
0
5.0 1.0
Installation
Time
0.10 hours 40 6.3 0.6 25 10.
0
1.0 50 5.0 0.5
Durability 0.15 experi
ence
gr
ea
t
10 1.5 go
od
8 1.2 goo
d
8 1.2
Reliability 0.30 experi
ence
go
od
8 2.4 gr
ea
t
10 3.0 oka
y
6 1.8
Reparability 0.15 experi
ence
go
od
8 1.2 gr
ea
t
10 1.5 fair 4 0.6
Overall value 8.2 9.6 6.1
Qualitative Score Assignments:
great 10
good 8
okay 6
fair 4
poor 2
INTERNET FUNDAMENTALS
Hardware Cost 0.10 $ 25
00
8.8 0.9 25
00
8.8 0.9 220
0
10.0 1.0
Configuration
Cost
0.20 $ 15
00
8.0 1.6 12
00
10.
0
2.0 240
0
5.0 1.0
Installation
Time
0.10 hours 40 6.3 0.6 25 10.
0
1.0 50 5.0 0.5
Durability 0.15 experi
ence
gr
ea
t
10 1.5 go
od
8 1.2 goo
d
8 1.2
Reliability 0.30 experi
ence
go
od
8 2.4 gr
ea
t
10 3.0 oka
y
6 1.8
Reparability 0.15 experi
ence
go
od
8 1.2 gr
ea
t
10 1.5 fair 4 0.6
Overall value 8.2 9.6 6.1
Qualitative Score Assignments:
great 10
good 8
okay 6
fair 4
poor 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INTERNET FUNDAMENTALS
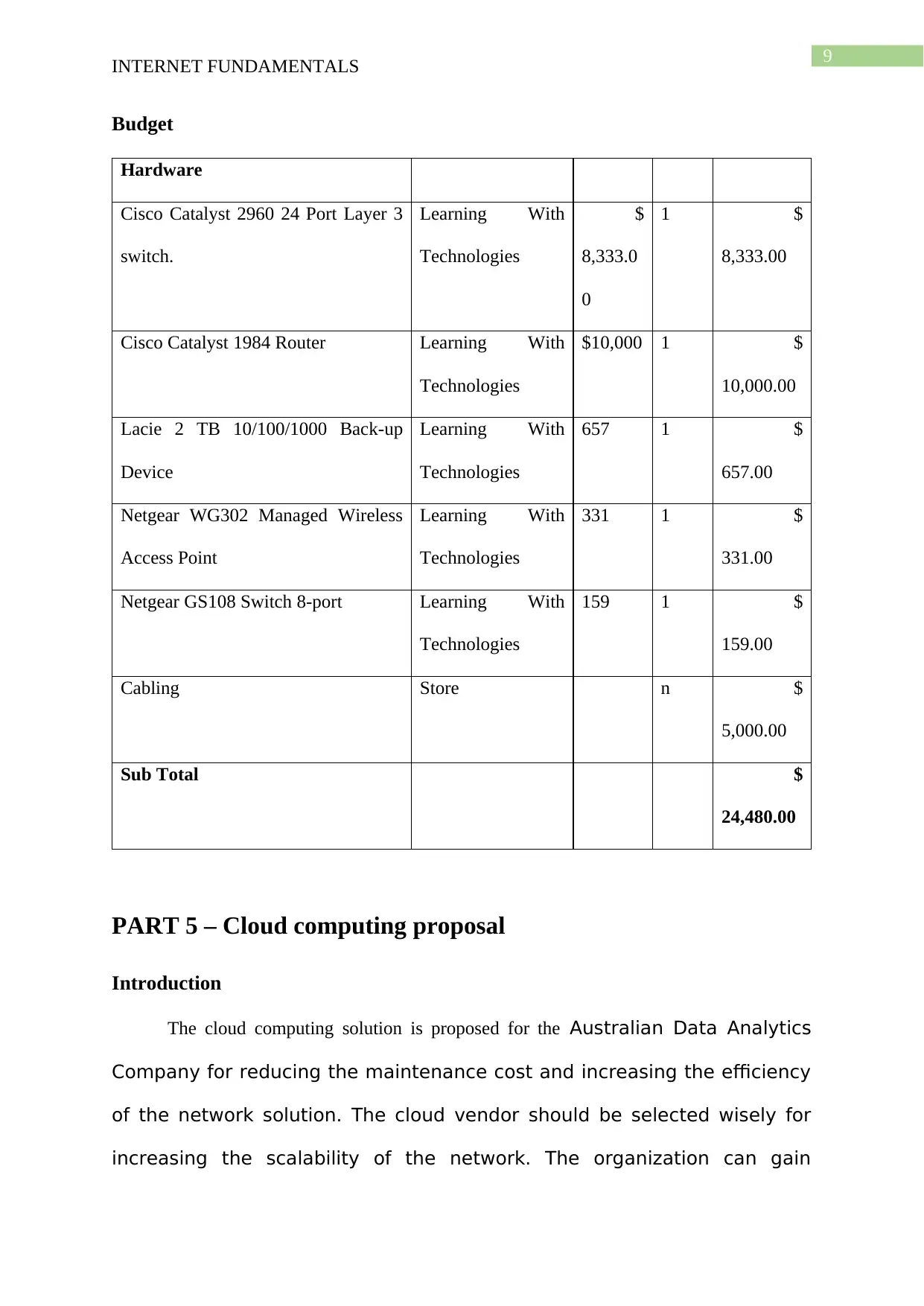
Budget
Hardware
Cisco Catalyst 2960 24 Port Layer 3
switch.
Learning With
Technologies
$
8,333.0
0
1 $
8,333.00
Cisco Catalyst 1984 Router Learning With
Technologies
$10,000 1 $
10,000.00
Lacie 2 TB 10/100/1000 Back-up
Device
Learning With
Technologies
657 1 $
657.00
Netgear WG302 Managed Wireless
Access Point
Learning With
Technologies
331 1 $
331.00
Netgear GS108 Switch 8-port Learning With
Technologies
159 1 $
159.00
Cabling Store n $
5,000.00
Sub Total $
24,480.00
PART 5 – Cloud computing proposal
Introduction
The cloud computing solution is proposed for the Australian Data Analytics
Company for reducing the maintenance cost and increasing the efficiency
of the network solution. The cloud vendor should be selected wisely for
increasing the scalability of the network. The organization can gain
INTERNET FUNDAMENTALS
Budget
Hardware
Cisco Catalyst 2960 24 Port Layer 3
switch.
Learning With
Technologies
$
8,333.0
0
1 $
8,333.00
Cisco Catalyst 1984 Router Learning With
Technologies
$10,000 1 $
10,000.00
Lacie 2 TB 10/100/1000 Back-up
Device
Learning With
Technologies
657 1 $
657.00
Netgear WG302 Managed Wireless
Access Point
Learning With
Technologies
331 1 $
331.00
Netgear GS108 Switch 8-port Learning With
Technologies
159 1 $
159.00
Cabling Store n $
5,000.00
Sub Total $
24,480.00
PART 5 – Cloud computing proposal
Introduction
The cloud computing solution is proposed for the Australian Data Analytics
Company for reducing the maintenance cost and increasing the efficiency
of the network solution. The cloud vendor should be selected wisely for
increasing the scalability of the network. The organization can gain
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INTERNET FUNDAMENTALS
different benefits such as reducing in the electricity bill and maintenance
cost with the implementation of the cloud solution.
Relocation of the in-house servers
The requirement of the organization should be analysed for the selection of the cloud
vendor and the platform should be identified such as IaaS and SaaS depending upon the
service that are required. The different service that should be moved to the cloud platform
should be identified and the permission that should be given to the user for accessing the files
residing in the cloud platform should also be identified.
Security
The security of the files should be considered and the security is the main factor for the
success of the network solution. The storage of the cloud should be divided into different
segments such as private and public for storing the normal files and the sensitive files in the
cloud storage. For increasing the security of the cloud solution the following techniques
should be applied such as:
Application of end to end encryption for securing the communication channels and
eliminate the risk of data loss.
Monitoring the network and analysis of the activity of the user and gathering an
evidence of the access of the data residing in the cloud platform
Application of distributed framework for increasing the availability of the data
residing in the cloud platform.
Issues
There are different risk associated with the cloud storage option such as migration of
the cloud data is not possible because it take lots of time to move the data from the cloud
storage to another storage option. The availability of the data depends on the internet service
INTERNET FUNDAMENTALS
different benefits such as reducing in the electricity bill and maintenance
cost with the implementation of the cloud solution.
Relocation of the in-house servers
The requirement of the organization should be analysed for the selection of the cloud
vendor and the platform should be identified such as IaaS and SaaS depending upon the
service that are required. The different service that should be moved to the cloud platform
should be identified and the permission that should be given to the user for accessing the files
residing in the cloud platform should also be identified.
Security
The security of the files should be considered and the security is the main factor for the
success of the network solution. The storage of the cloud should be divided into different
segments such as private and public for storing the normal files and the sensitive files in the
cloud storage. For increasing the security of the cloud solution the following techniques
should be applied such as:
Application of end to end encryption for securing the communication channels and
eliminate the risk of data loss.
Monitoring the network and analysis of the activity of the user and gathering an
evidence of the access of the data residing in the cloud platform
Application of distributed framework for increasing the availability of the data
residing in the cloud platform.
Issues
There are different risk associated with the cloud storage option such as migration of
the cloud data is not possible because it take lots of time to move the data from the cloud
storage to another storage option. The availability of the data depends on the internet service

11
INTERNET FUNDAMENTALS
provider because if the internet is down the user may not connect with the cloud servers for
accessing the data.
Conclusion
From the above report it can be concluded that with the deployment of the cloud
solution the different risk associated with the cloud platform should be evaluated. The
maintenance cost of the in-house servers and the charges of the cloud vendors should be
compared for the selection of the cloud vendor and deploy in the network for increasing the
flexibility of the network solution.
INTERNET FUNDAMENTALS
provider because if the internet is down the user may not connect with the cloud servers for
accessing the data.
Conclusion
From the above report it can be concluded that with the deployment of the cloud
solution the different risk associated with the cloud platform should be evaluated. The
maintenance cost of the in-house servers and the charges of the cloud vendors should be
compared for the selection of the cloud vendor and deploy in the network for increasing the
flexibility of the network solution.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





