Report on EDMS Data Analysis: Information Assets Protection Strategies
VerifiedAdded on 2022/08/26
|18
|414
|23
Report
AI Summary
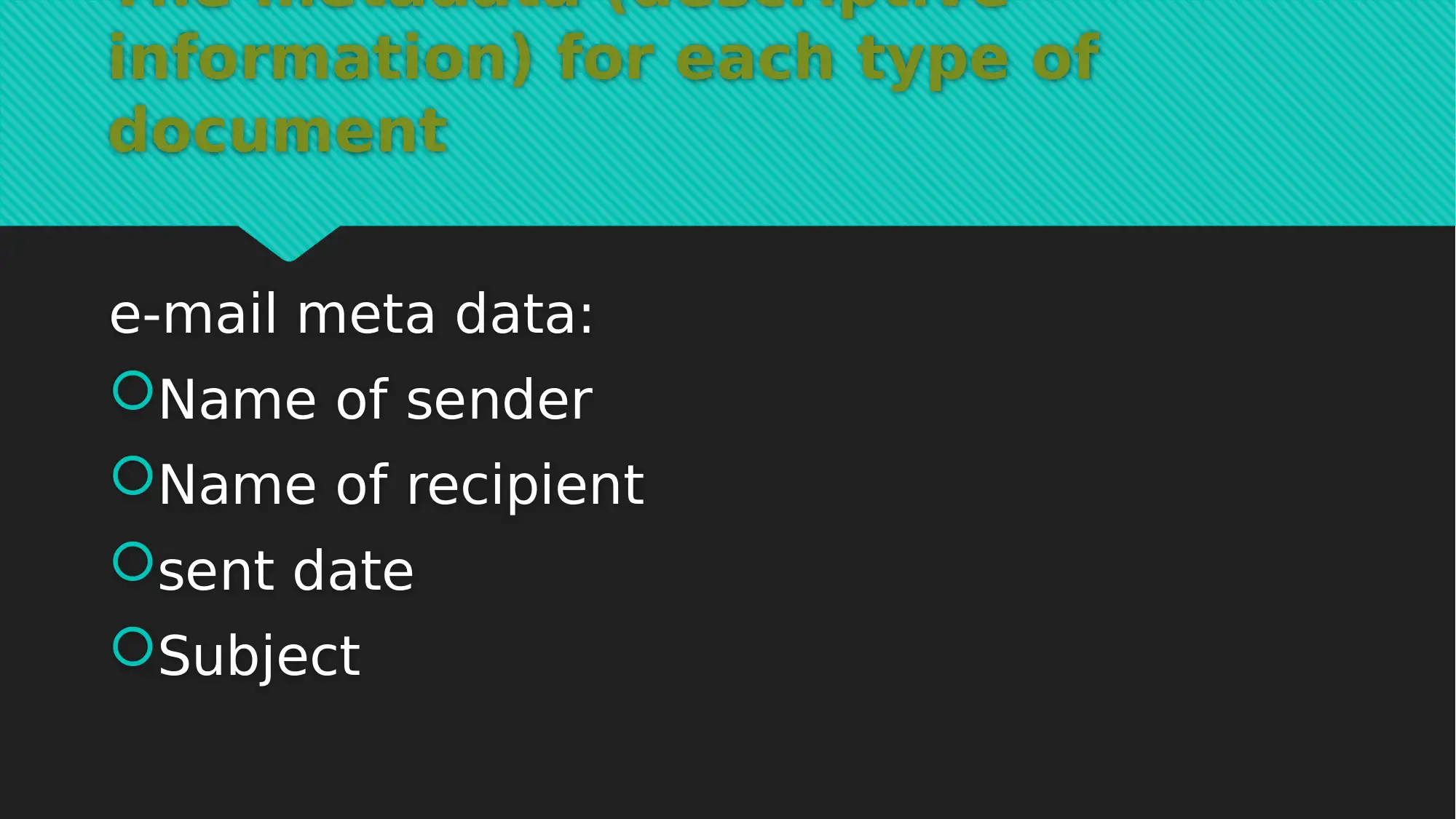
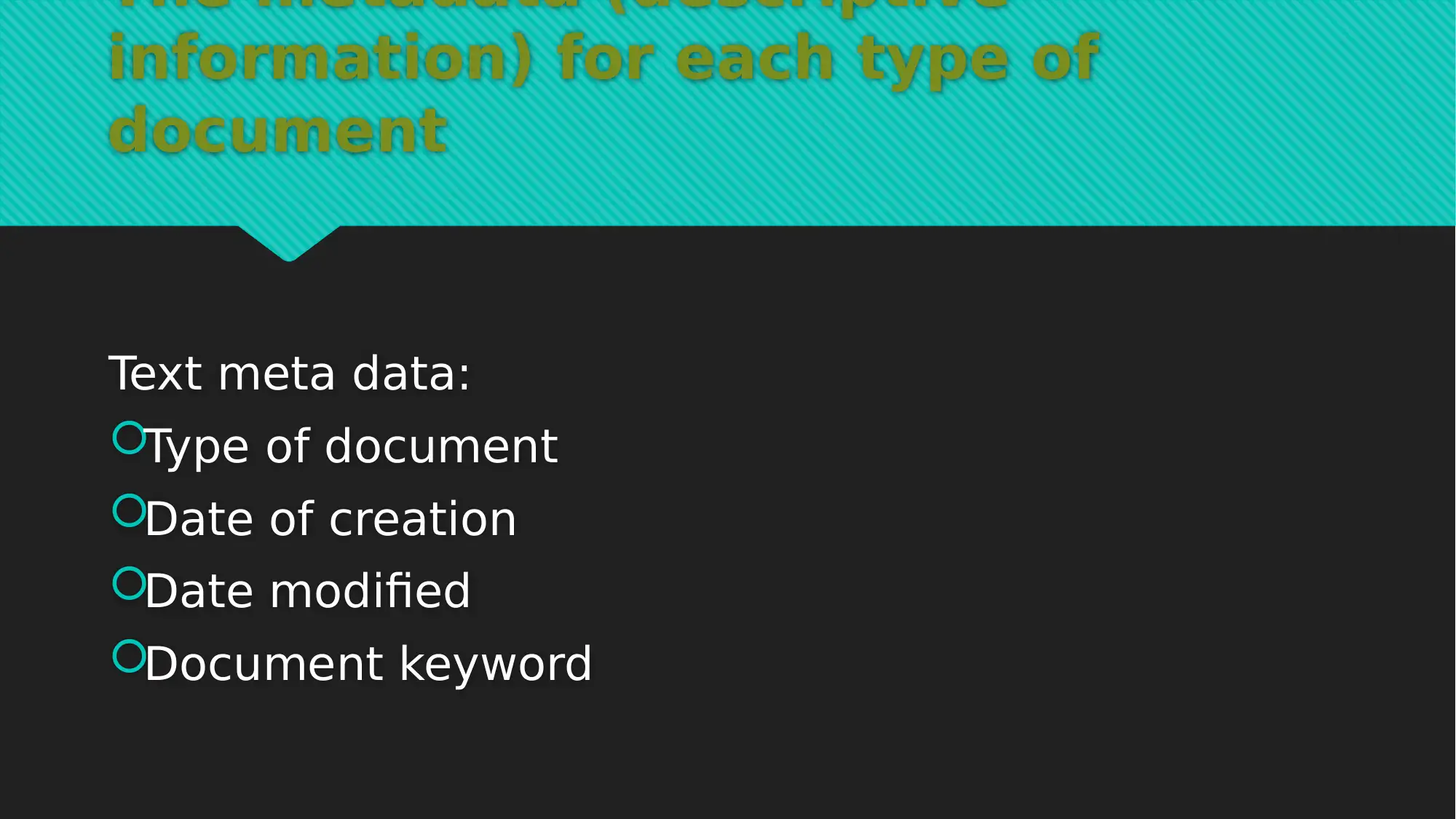
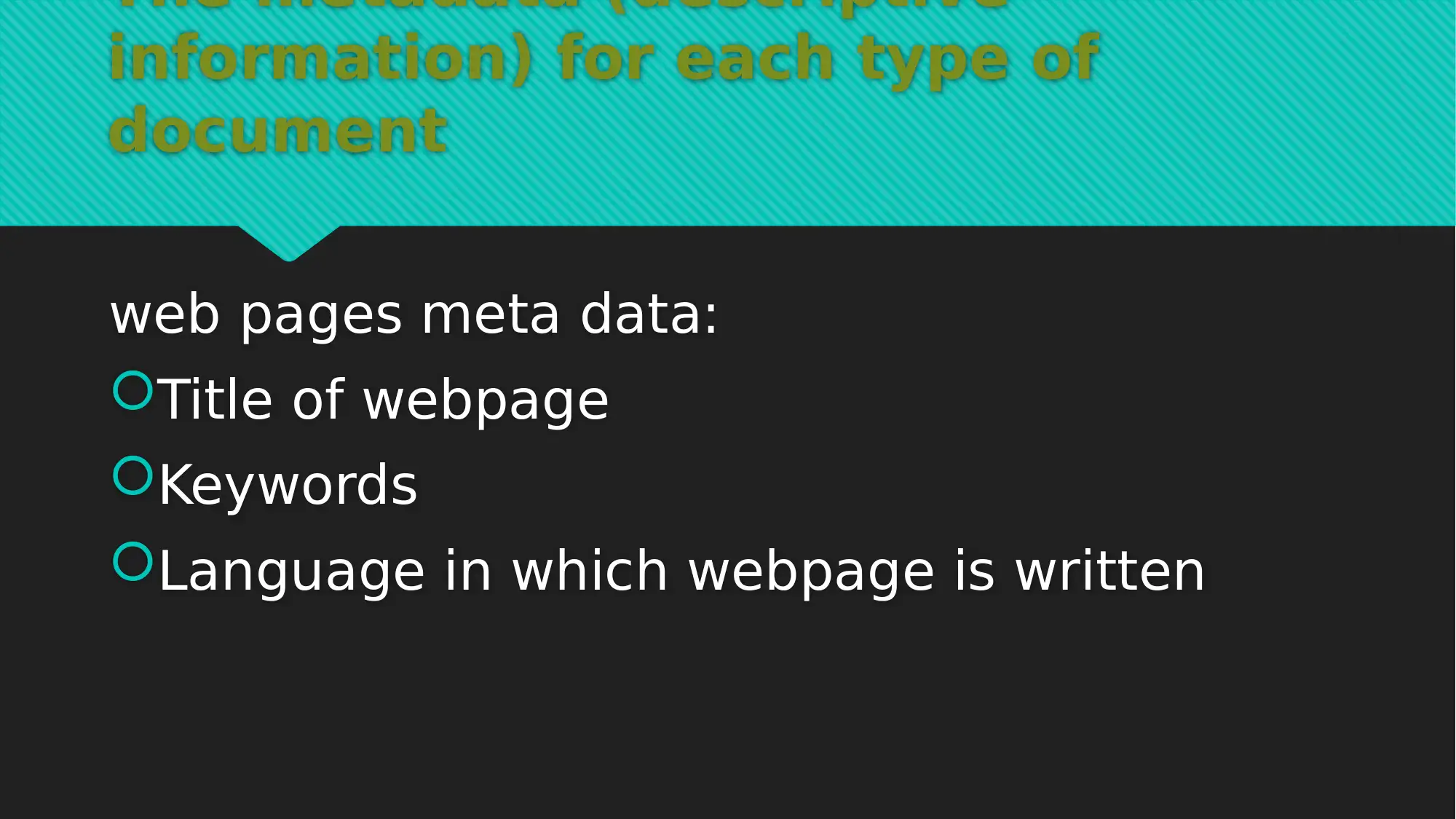
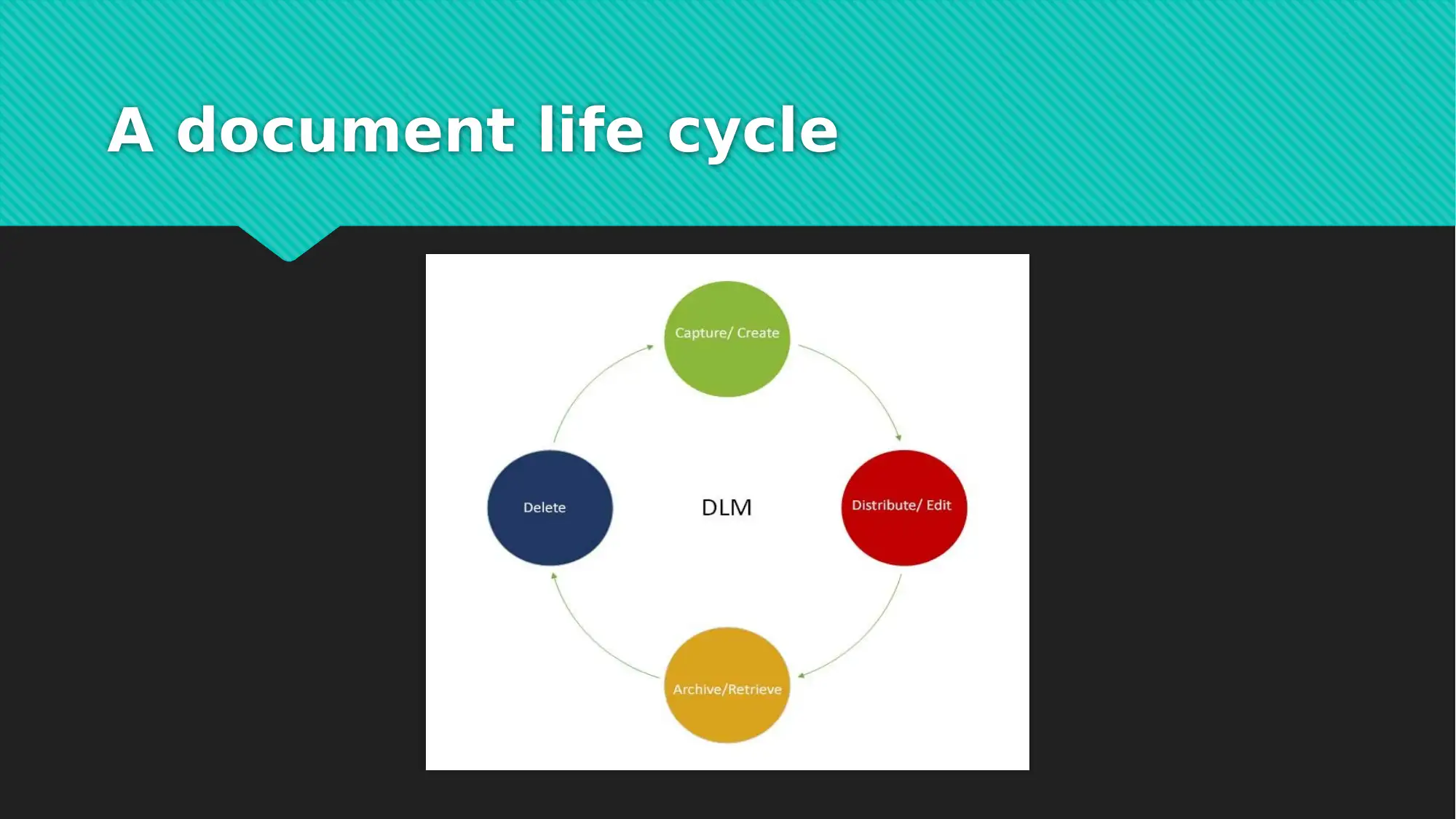
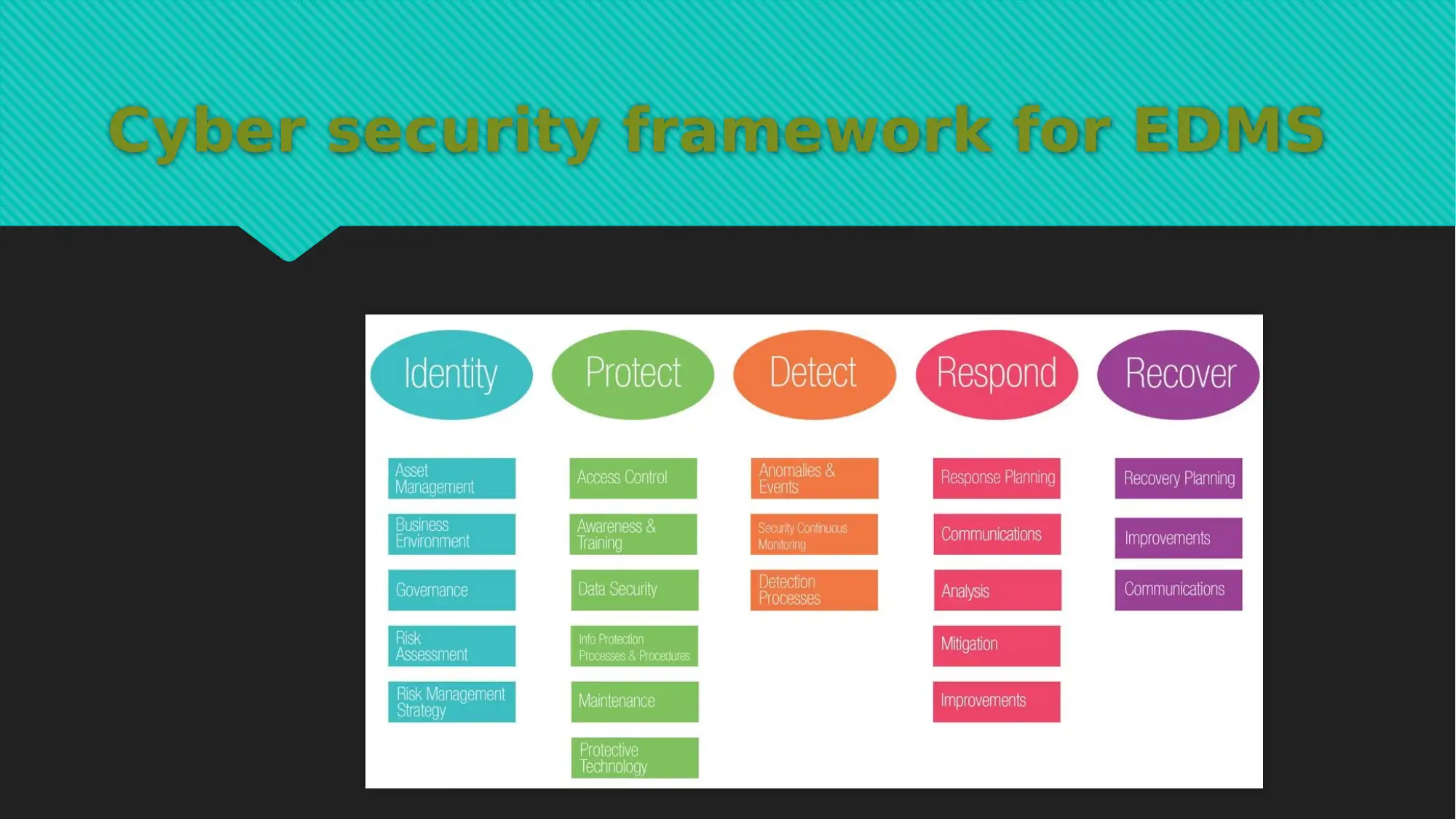
This report provides a comprehensive analysis of EDMS data, focusing on information assets protection. It details the types of data considered, including e-mails, text documents, orders, invoices, and web pages, and outlines the associated metadata for each. The report covers the document lifecycle, emphasizing data creation, editing, retrieval, and deletion, and discusses the use of local database servers and cloud storage. A significant portion of the report is dedicated to a cybersecurity framework for EDMS, addressing data audit, access control, data retention, and data encryption. Justifications for the framework are provided, highlighting its role in data classification, data elimination, and data storage strategies. The report also outlines data classification levels, including secret, confidential, business application only, and public levels, and provides tools for each level such as data audit, access control monitoring, network traffic analysis, and database authentication. This report is a valuable resource for understanding the crucial aspects of information assets protection within an EDMS environment.
1 out of 18







![Data and System Security Assignment - [Course Name] Overview](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fea%2Fc6a7b1592b5747cb82c287512501193a.jpg&w=256&q=75)



![[object Object]](/_next/static/media/star-bottom.7253800d.svg)