KIT201/501 Assignment: Data Breach Analysis and Legislative Efforts
VerifiedAdded on 2022/09/28
|12
|2758
|51
Essay
AI Summary
This essay analyzes the Australian National University (ANU) data breach, exploring its causes, impacts, and the measures taken to address it. The essay details the stolen data, including personal and academic information, and discusses factors that contributed to the breach, such as weak credentials, application vulnerabilities, and insider threats. It examines the outcomes of the data breach, focusing on the legislative efforts by the Australian Notifiable Data Breach (NDB) scheme to mitigate the impact and ensure data privacy. The essay highlights the NDB scheme's role in guiding organizations in responding to data breaches and the importance of notifying individuals and the Commissioner of potential risks. The conclusion emphasizes the need for robust security measures to prevent future data breaches and protect sensitive information. The essay references data breaches at Canva and Whatsapp to illustrate the scope of the problem.

Running head: DATA BREACH
Data Breach
Name of the Student
Name of the University
Author’s Note
Data Breach
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA BREACH
Table of Contents
Introduction................................................................................................................................2
Chosen Data Breach: Australian National University...............................................................2
Measures taken by ANU............................................................................................................3
Factors that lead to Data Breach................................................................................................4
Outcomes of Data Breach in ANU.............................................................................................6
Legislative efforts taken by Australian NDB.............................................................................7
Conclusion..................................................................................................................................8
Table of Contents
Introduction................................................................................................................................2
Chosen Data Breach: Australian National University...............................................................2
Measures taken by ANU............................................................................................................3
Factors that lead to Data Breach................................................................................................4
Outcomes of Data Breach in ANU.............................................................................................6
Legislative efforts taken by Australian NDB.............................................................................7
Conclusion..................................................................................................................................8

2DATA BREACH
Introduction
As the technology is turning out more dominant in the way, in which the storage of
the information or data is changing. Instead of storing the data into the cabinets, the
information or data is being stored in the database. This raises the hackers and the security
breaches correspondingly, where the hackers can access to the sensitive and confidential data
or information (Jones et al. 2014). A data breach is the incident, which causes the
unauthorized access of the data, devices, networks, services and application by bypassing the
underlying security techniques (Romanosky Hoffman and Acquisti 2014). A data breach is
the early stage of the security attack by any malicious intruder. Data breach happens if the
system, producers or the security policies are violated. This study aims to highlight on some
of the high profile data breaches in Australia, in which the Australian National University,
Canva and Whatsapp were the victims of the data breach. This study discusses about the
impact, mitigation and the factors that has lead the organization to the breach and the
legislative efforts by the scheme of Australia’s Notifiable Data Breach that helped in this
case of data breach.
Fig: Data Breach diagram
(Source: Created by Author)
Introduction
As the technology is turning out more dominant in the way, in which the storage of
the information or data is changing. Instead of storing the data into the cabinets, the
information or data is being stored in the database. This raises the hackers and the security
breaches correspondingly, where the hackers can access to the sensitive and confidential data
or information (Jones et al. 2014). A data breach is the incident, which causes the
unauthorized access of the data, devices, networks, services and application by bypassing the
underlying security techniques (Romanosky Hoffman and Acquisti 2014). A data breach is
the early stage of the security attack by any malicious intruder. Data breach happens if the
system, producers or the security policies are violated. This study aims to highlight on some
of the high profile data breaches in Australia, in which the Australian National University,
Canva and Whatsapp were the victims of the data breach. This study discusses about the
impact, mitigation and the factors that has lead the organization to the breach and the
legislative efforts by the scheme of Australia’s Notifiable Data Breach that helped in this
case of data breach.
Fig: Data Breach diagram
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DATA BREACH
Data Breaches
The first data breach is discussed in this report is the Australian national University
data breach attack. Universities data breaches are not entirely explored and pose many
unanswered queries. Research on universities data breaches is very essential as this has the
strong ability for identifying the factors, which make the institution or the universities more
prone to the data breaches. The significant losses are connected with the educational
institutes. Breaches irresistible risks happen because of such incidents. It is very important to
understand the effective way to recover and manage from the breach and the importance in
the educational institute (Mello 2018). In this study, the chosen data breach is the Australian
National University data breach, which happened on June 2019. The personal information of
the staffs and students has been stolen in the cyber security attack or data breach. 19 years of
data or information was accessed by some intruders (Patterson 2019). Names, personal
address, date of birth, email address, phone number, emergency contact details, tax file
number, passport details, payroll information and bank account details were the stolen data
and the records of student academic also were accessed (ANU, 2019). These are the very
essential data. Security and privacy will be always at risks if these types of information are
hacked.
Some other data breach attacks are Canva, which is a huge graphic design company in
Australia data breach attack and Whatsapp data breach attack. Both the attacks were occurred
in May 2019.
Data breach attack on Canva stole the information of approximately 139 million of
users (Vickovich 2019). Thousands of user names, phone numbers, email address, password
are stolen from the system. In some case, the artworks of the users are also stolen. ACSE
(Australian Cyber Security Centre) has confirmed about their knowledge of the attack and
Data Breaches
The first data breach is discussed in this report is the Australian national University
data breach attack. Universities data breaches are not entirely explored and pose many
unanswered queries. Research on universities data breaches is very essential as this has the
strong ability for identifying the factors, which make the institution or the universities more
prone to the data breaches. The significant losses are connected with the educational
institutes. Breaches irresistible risks happen because of such incidents. It is very important to
understand the effective way to recover and manage from the breach and the importance in
the educational institute (Mello 2018). In this study, the chosen data breach is the Australian
National University data breach, which happened on June 2019. The personal information of
the staffs and students has been stolen in the cyber security attack or data breach. 19 years of
data or information was accessed by some intruders (Patterson 2019). Names, personal
address, date of birth, email address, phone number, emergency contact details, tax file
number, passport details, payroll information and bank account details were the stolen data
and the records of student academic also were accessed (ANU, 2019). These are the very
essential data. Security and privacy will be always at risks if these types of information are
hacked.
Some other data breach attacks are Canva, which is a huge graphic design company in
Australia data breach attack and Whatsapp data breach attack. Both the attacks were occurred
in May 2019.
Data breach attack on Canva stole the information of approximately 139 million of
users (Vickovich 2019). Thousands of user names, phone numbers, email address, password
are stolen from the system. In some case, the artworks of the users are also stolen. ACSE
(Australian Cyber Security Centre) has confirmed about their knowledge of the attack and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4DATA BREACH
they advised the users to change their log in credentials. The organization also proactively
alerted to the ACSE about the data breach attack. The data breach follows $70 million fresh
capital of Canva. In spite of the extreme nature of theft, the organization maintains the details
of the credit cards or the actual funds that have appear to be stolen. The organization stated
that they were working with the FBI and forensic team for diagnosing the attack that are
putting in the process for preventing another data breach attack.
Whatsapp has revealed that vulnerability has identified in the system that might allow
the intruders to enter to the mobile phones of the users. The encrypted messaging system of
Facebook has stated that the system has discovered and fixed the risk of the attacks
(9news.com.au. 2019). The intruders could access to the phones and install malicious
functions on the victim’s mobile by placing some random calls on the Whatsapp. For attack,
the victim may not answer to the calls to be infected. The data breach has the hallmarks of the
private company that works with the government of Australia for delivering the spyware,
which will take over the function in the phone and the operating system.
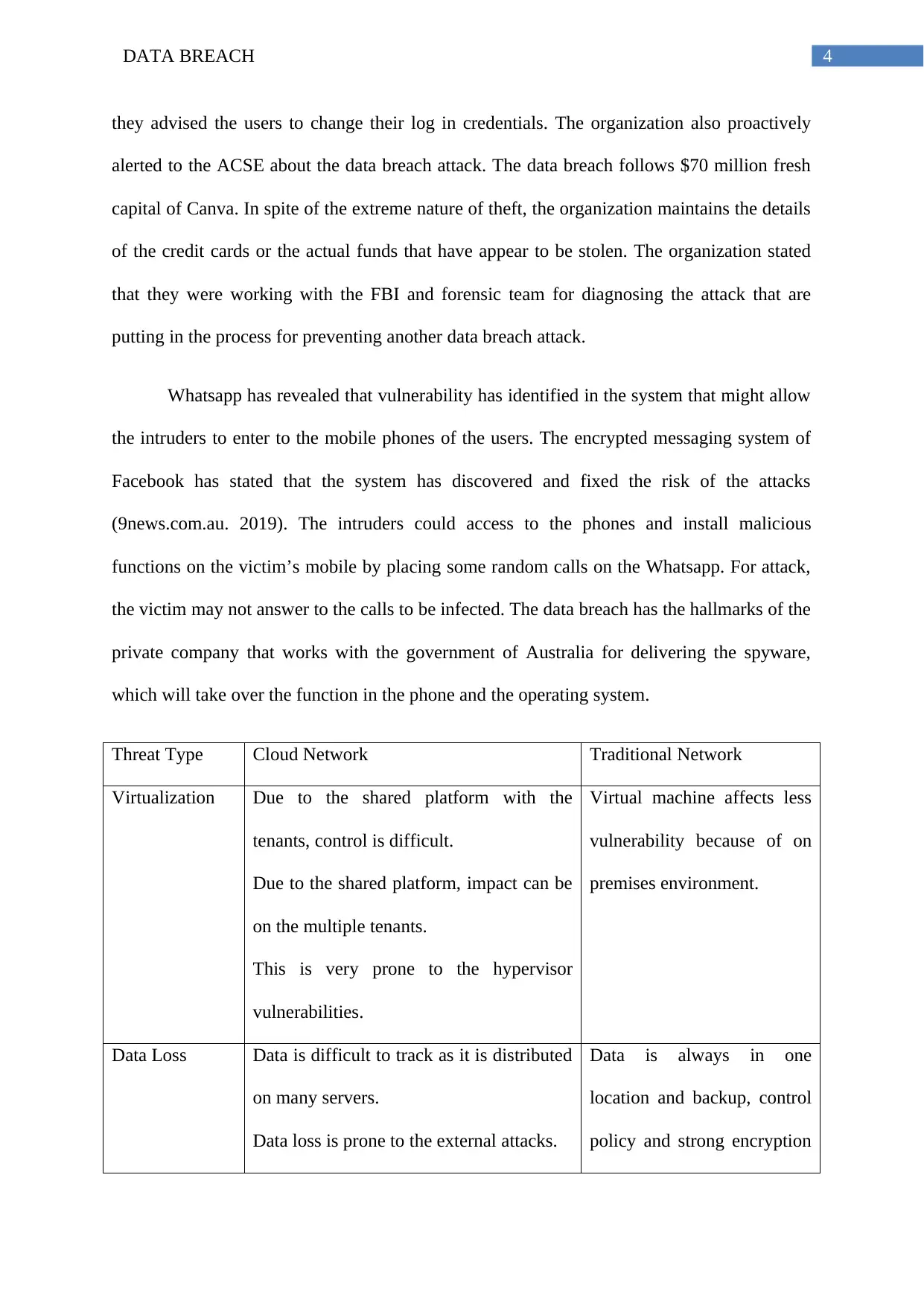
Threat Type Cloud Network Traditional Network
Virtualization Due to the shared platform with the
tenants, control is difficult.
Due to the shared platform, impact can be
on the multiple tenants.
This is very prone to the hypervisor
vulnerabilities.
Virtual machine affects less
vulnerability because of on
premises environment.
Data Loss Data is difficult to track as it is distributed
on many servers.
Data loss is prone to the external attacks.
Data is always in one
location and backup, control
policy and strong encryption
they advised the users to change their log in credentials. The organization also proactively
alerted to the ACSE about the data breach attack. The data breach follows $70 million fresh
capital of Canva. In spite of the extreme nature of theft, the organization maintains the details
of the credit cards or the actual funds that have appear to be stolen. The organization stated
that they were working with the FBI and forensic team for diagnosing the attack that are
putting in the process for preventing another data breach attack.
Whatsapp has revealed that vulnerability has identified in the system that might allow
the intruders to enter to the mobile phones of the users. The encrypted messaging system of
Facebook has stated that the system has discovered and fixed the risk of the attacks
(9news.com.au. 2019). The intruders could access to the phones and install malicious
functions on the victim’s mobile by placing some random calls on the Whatsapp. For attack,
the victim may not answer to the calls to be infected. The data breach has the hallmarks of the
private company that works with the government of Australia for delivering the spyware,
which will take over the function in the phone and the operating system.
Threat Type Cloud Network Traditional Network
Virtualization Due to the shared platform with the
tenants, control is difficult.
Due to the shared platform, impact can be
on the multiple tenants.
This is very prone to the hypervisor
vulnerabilities.
Virtual machine affects less
vulnerability because of on
premises environment.
Data Loss Data is difficult to track as it is distributed
on many servers.
Data loss is prone to the external attacks.
Data is always in one
location and backup, control
policy and strong encryption
5DATA BREACH
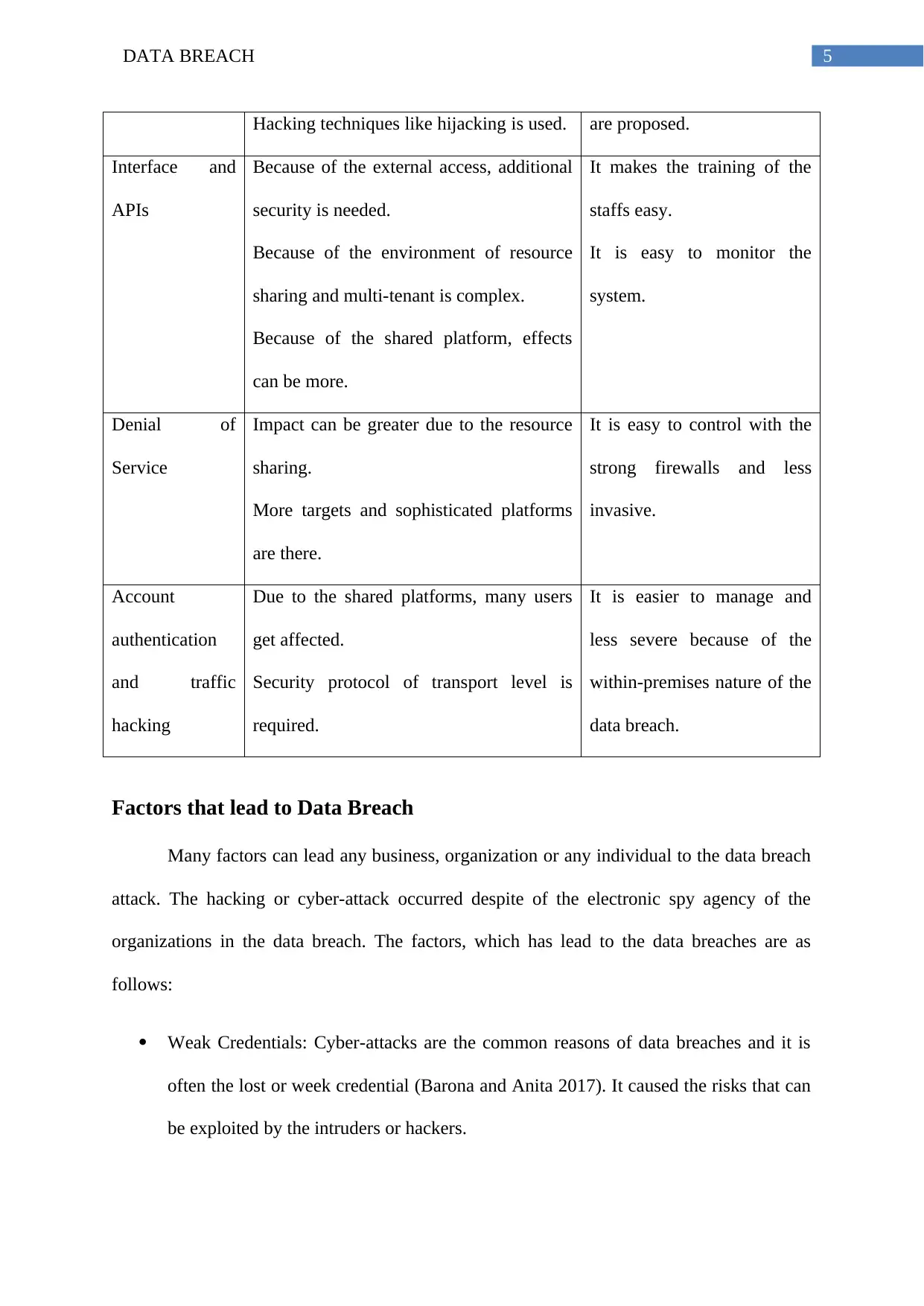
Hacking techniques like hijacking is used. are proposed.
Interface and
APIs
Because of the external access, additional
security is needed.
Because of the environment of resource
sharing and multi-tenant is complex.
Because of the shared platform, effects
can be more.
It makes the training of the
staffs easy.
It is easy to monitor the
system.
Denial of
Service
Impact can be greater due to the resource
sharing.
More targets and sophisticated platforms
are there.
It is easy to control with the
strong firewalls and less
invasive.
Account
authentication
and traffic
hacking
Due to the shared platforms, many users
get affected.
Security protocol of transport level is
required.
It is easier to manage and
less severe because of the
within-premises nature of the
data breach.
Factors that lead to Data Breach
Many factors can lead any business, organization or any individual to the data breach
attack. The hacking or cyber-attack occurred despite of the electronic spy agency of the
organizations in the data breach. The factors, which has lead to the data breaches are as
follows:
Weak Credentials: Cyber-attacks are the common reasons of data breaches and it is
often the lost or week credential (Barona and Anita 2017). It caused the risks that can
be exploited by the intruders or hackers.
Hacking techniques like hijacking is used. are proposed.
Interface and
APIs
Because of the external access, additional
security is needed.
Because of the environment of resource
sharing and multi-tenant is complex.
Because of the shared platform, effects
can be more.
It makes the training of the
staffs easy.
It is easy to monitor the
system.
Denial of
Service
Impact can be greater due to the resource
sharing.
More targets and sophisticated platforms
are there.
It is easy to control with the
strong firewalls and less
invasive.
Account
authentication
and traffic
hacking
Due to the shared platforms, many users
get affected.
Security protocol of transport level is
required.
It is easier to manage and
less severe because of the
within-premises nature of the
data breach.
Factors that lead to Data Breach
Many factors can lead any business, organization or any individual to the data breach
attack. The hacking or cyber-attack occurred despite of the electronic spy agency of the
organizations in the data breach. The factors, which has lead to the data breaches are as
follows:
Weak Credentials: Cyber-attacks are the common reasons of data breaches and it is
often the lost or week credential (Barona and Anita 2017). It caused the risks that can
be exploited by the intruders or hackers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DATA BREACH
Application Vulnerabilities: Intruders exploited the software applications that are poor
network system or weakly programmed or poorly implemented or designed (Fonseca
et al. 2013). This poor design made a way for the hackers to crawl straight to the data
directly.
Malware: The usages of the direct and in-direct malware are on the edge. Malware is
malicious or harmful software, which is loaded without any intention and the
malicious content, opens the access for the hackers for exploiting the system and the
other connected devices or systems (Thomas et al. 2017)
Physical Attack: The intruders have the strong line and high visibility jackets in
plausible patter for enabling themselves to work in the way into the organization and
the systems of the organization.
Insider Threats: There may be some rouge staffs of the organizations. They are not
bright enough for knowing the things better and they are given the access or
permission for accessing the data (Chou 2013). That creates the major problem for
data breach.
Too Many Permission: The organization did not keep the tight rein on the access
within the organization. They may have given the access or permission to the wrong
staffs. It left the permissions for the hackers to exploit the data.
Legislative efforts taken by Australian NDB
Some legislative efforts by Australia's Notifiable Data Breach scheme helped ANU to
mitigate the data breach. The NDB scheme refers to organizations that have a duty to
safeguard their private data under APP 11 of a Privacy Act (Leonard and Principal 2018).
The NDB scheme refers only to companies and stocks of private data already subject to
Application Vulnerabilities: Intruders exploited the software applications that are poor
network system or weakly programmed or poorly implemented or designed (Fonseca
et al. 2013). This poor design made a way for the hackers to crawl straight to the data
directly.
Malware: The usages of the direct and in-direct malware are on the edge. Malware is
malicious or harmful software, which is loaded without any intention and the
malicious content, opens the access for the hackers for exploiting the system and the
other connected devices or systems (Thomas et al. 2017)
Physical Attack: The intruders have the strong line and high visibility jackets in
plausible patter for enabling themselves to work in the way into the organization and
the systems of the organization.
Insider Threats: There may be some rouge staffs of the organizations. They are not
bright enough for knowing the things better and they are given the access or
permission for accessing the data (Chou 2013). That creates the major problem for
data breach.
Too Many Permission: The organization did not keep the tight rein on the access
within the organization. They may have given the access or permission to the wrong
staffs. It left the permissions for the hackers to exploit the data.
Legislative efforts taken by Australian NDB
Some legislative efforts by Australia's Notifiable Data Breach scheme helped ANU to
mitigate the data breach. The NDB scheme refers to organizations that have a duty to
safeguard their private data under APP 11 of a Privacy Act (Leonard and Principal 2018).
The NDB scheme refers only to companies and stocks of private data already subject to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DATA BREACH
safety criteria under the Privacy Act (OAIC 2019). The guide has assisted the organizations
to prepare and respond to the data breaches with the obligations under Privacy Act 1988.
Entities with current commitments to safeguard private data under the Privacy Act must
conform to the NDB system. The NDB system refers to all loan suppliers, whether they are
APP companies or not. (Leonard 2018). The portion of the Privacy Act that requires a loan
supplier to conform to the plan will rely on what data the data breach involves.
Conduct a fair and expeditious evaluation of a presumed qualified violation of
information making all appropriate measures to guarantee that this evaluation is finished
within 30 days to become conscious of it. Prepare a data breach declaration and provide the
Commissioner with a duplicate as quickly as practicable. Notify the substance of the
declaration as quickly as practicable to people at danger of severe damage or post the
declaration in certain conditions.
Entities that have safety responsibilities under the Privacy Act with respect to specific
kinds of information only, for instance, are not needed to notify tiny companies that are
needed to obtain tax file number of data about data breaches that influence other sorts of
information outside the range of their responsibilities under the Privacy Act.
The NDB scheme extends to the activities of the agency of Australian Government. It
applies to the organizations that have the Australian link (OAIC 2019). The organizations
have the Australian link as it carriers on the business in the external territory of Australian or
in Australia. It has held the personal information in the external territory of Australia and in
Australia either at time or before time of the practice or act.
If the APP entity exposes the personal details to any overseas recipient with the
requirement, then the entity holds the information or details for the NDB scheme purpose.
safety criteria under the Privacy Act (OAIC 2019). The guide has assisted the organizations
to prepare and respond to the data breaches with the obligations under Privacy Act 1988.
Entities with current commitments to safeguard private data under the Privacy Act must
conform to the NDB system. The NDB system refers to all loan suppliers, whether they are
APP companies or not. (Leonard 2018). The portion of the Privacy Act that requires a loan
supplier to conform to the plan will rely on what data the data breach involves.
Conduct a fair and expeditious evaluation of a presumed qualified violation of
information making all appropriate measures to guarantee that this evaluation is finished
within 30 days to become conscious of it. Prepare a data breach declaration and provide the
Commissioner with a duplicate as quickly as practicable. Notify the substance of the
declaration as quickly as practicable to people at danger of severe damage or post the
declaration in certain conditions.
Entities that have safety responsibilities under the Privacy Act with respect to specific
kinds of information only, for instance, are not needed to notify tiny companies that are
needed to obtain tax file number of data about data breaches that influence other sorts of
information outside the range of their responsibilities under the Privacy Act.
The NDB scheme extends to the activities of the agency of Australian Government. It
applies to the organizations that have the Australian link (OAIC 2019). The organizations
have the Australian link as it carriers on the business in the external territory of Australian or
in Australia. It has held the personal information in the external territory of Australia and in
Australia either at time or before time of the practice or act.
If the APP entity exposes the personal details to any overseas recipient with the
requirement, then the entity holds the information or details for the NDB scheme purpose.

8DATA BREACH
One of the APP entity states that the entity that exposes the personal details of the users to the
external recipient needs to take the reasonable steps for ensuring the recipient of overseas do
not breach the data or the personal information in the relation with APP to the details. That
means if the personal details, which is the data of the users of overseas countries are about to
unauthorized entry, disclosure and loss, the entity of APP will be accountable for the loss if
the attack is eligible data breach, which will be tributary of Privacy Act. If the atttack is not
eligible then the serious risks to any individual will be provided to the Commissioner of
Australia. The NDB scheme needs to regulate the entities for notifying the specific
individuals and the Commissioner regarding the data breaches. The data breach will be
eligible if the attack of data breach results any harm or risks to the organization or any
individual with whom the information will be related (Callahan 2017). If any of the entity
remediates the data breach, the result of the attack of data breach will not cause any fatal risk.
Then there is no need for notifying to the Commissioner or the individual. However, it can be
expected to be notified in some certain circumstances.
Conclusion
Only time will show what is going to happen next. The unfortunate thing is that it's in the
wind that intruders have robbed critical information. The results may be minimal or they may
be catastrophic, based on the plans of the hackers. This can be concluded by this research that
if the intruders still have connections to systems through an existing backdoor and drain off
critical information as it arises, a major problem will be. In the attacks researched, thousands
of data of people were stolen from their personal data and proprietary information. Hackers
are highly attracted by the quantity of private, economic, and other delicate information
accessible in the system and network. The essence of an organization of openness and
cooperation and the amount of private appliances permitted and endorsed on organizations
One of the APP entity states that the entity that exposes the personal details of the users to the
external recipient needs to take the reasonable steps for ensuring the recipient of overseas do
not breach the data or the personal information in the relation with APP to the details. That
means if the personal details, which is the data of the users of overseas countries are about to
unauthorized entry, disclosure and loss, the entity of APP will be accountable for the loss if
the attack is eligible data breach, which will be tributary of Privacy Act. If the atttack is not
eligible then the serious risks to any individual will be provided to the Commissioner of
Australia. The NDB scheme needs to regulate the entities for notifying the specific
individuals and the Commissioner regarding the data breaches. The data breach will be
eligible if the attack of data breach results any harm or risks to the organization or any
individual with whom the information will be related (Callahan 2017). If any of the entity
remediates the data breach, the result of the attack of data breach will not cause any fatal risk.
Then there is no need for notifying to the Commissioner or the individual. However, it can be
expected to be notified in some certain circumstances.
Conclusion
Only time will show what is going to happen next. The unfortunate thing is that it's in the
wind that intruders have robbed critical information. The results may be minimal or they may
be catastrophic, based on the plans of the hackers. This can be concluded by this research that
if the intruders still have connections to systems through an existing backdoor and drain off
critical information as it arises, a major problem will be. In the attacks researched, thousands
of data of people were stolen from their personal data and proprietary information. Hackers
are highly attracted by the quantity of private, economic, and other delicate information
accessible in the system and network. The essence of an organization of openness and
cooperation and the amount of private appliances permitted and endorsed on organizations
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DATA BREACH
premises make it hard to safeguard organizational networks. Organizations need to use best
practices to safeguard information; including data breach prevention schemes and measures
to be taken once an infringement has been identified. It is component of a strong safety
scheme to educate the customer community about the significance of safety and the position
of customers in creating the network safer. In authenticating network users of the system and
tracking for unlawful entry, the organizational staff must be vigilant.
premises make it hard to safeguard organizational networks. Organizations need to use best
practices to safeguard information; including data breach prevention schemes and measures
to be taken once an infringement has been identified. It is component of a strong safety
scheme to educate the customer community about the significance of safety and the position
of customers in creating the network safer. In authenticating network users of the system and
tracking for unlawful entry, the organizational staff must be vigilant.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DATA BREACH
References
9news.com.au. 2019. WhatsApp major security flaw could let hackers access phones. [online]
Available at: <https://www.9news.com.au/national/news-security-whatsapp-reveals-major-
security-flaw-that-could-let-hackers-access-phones/702e51e2-9f8c-4b8d-a59f-
c74253bc4c3f> [Accessed 7 Sep. 2019].
ANU, 2019. Data breach FAQs. [online] ANU. Available at:
<https://www.anu.edu.au/news/all-news/data-breach-faqs> [Accessed 27 Aug. 2019].
Barona, R. and Anita, E., 2017, April. A survey on data breach challenges in cloud
computing security: Issues and threats. In 2017 International Conference on Circuit, Power
and Computing Technologies (ICCPCT) (pp. 1-8). IEEE.
Chou, T.S., 2013. Security threats on cloud computing vulnerabilities. International Journal
of Computer Science & Information Technology, 5(3), p.79.
Fonseca, J., Seixas, N., Vieira, M. and Madeira, H., 2013. Analysis of field data on web
security vulnerabilities. IEEE transactions on dependable and secure computing, 11(2),
pp.89-100.
Jones, B.H., Chin, A.G. and Aiken, P., 2014. Risky business: Students and
smartphones. TechTrends, 58(6), pp.73-83.
Leonard, P. 2018. The new Australian Notifiable Data Breach Scheme. [ebook]. Available
at: <http://www.iot.org.au/wp/wp-content/uploads/2016/12/Notifiable-Data-Breach-Scheme-
for-Australia-12-Feb-2018.pdf> [Accessed 26 Aug. 2019].
Leonard, P. and Principal, D.S., 2018. The new Australian Notifiable Data Breach
Scheme. Available at SSRN 3154271.
References
9news.com.au. 2019. WhatsApp major security flaw could let hackers access phones. [online]
Available at: <https://www.9news.com.au/national/news-security-whatsapp-reveals-major-
security-flaw-that-could-let-hackers-access-phones/702e51e2-9f8c-4b8d-a59f-
c74253bc4c3f> [Accessed 7 Sep. 2019].
ANU, 2019. Data breach FAQs. [online] ANU. Available at:
<https://www.anu.edu.au/news/all-news/data-breach-faqs> [Accessed 27 Aug. 2019].
Barona, R. and Anita, E., 2017, April. A survey on data breach challenges in cloud
computing security: Issues and threats. In 2017 International Conference on Circuit, Power
and Computing Technologies (ICCPCT) (pp. 1-8). IEEE.
Chou, T.S., 2013. Security threats on cloud computing vulnerabilities. International Journal
of Computer Science & Information Technology, 5(3), p.79.
Fonseca, J., Seixas, N., Vieira, M. and Madeira, H., 2013. Analysis of field data on web
security vulnerabilities. IEEE transactions on dependable and secure computing, 11(2),
pp.89-100.
Jones, B.H., Chin, A.G. and Aiken, P., 2014. Risky business: Students and
smartphones. TechTrends, 58(6), pp.73-83.
Leonard, P. 2018. The new Australian Notifiable Data Breach Scheme. [ebook]. Available
at: <http://www.iot.org.au/wp/wp-content/uploads/2016/12/Notifiable-Data-Breach-Scheme-
for-Australia-12-Feb-2018.pdf> [Accessed 26 Aug. 2019].
Leonard, P. and Principal, D.S., 2018. The new Australian Notifiable Data Breach
Scheme. Available at SSRN 3154271.

11DATA BREACH
Mello, S., 2018. Data Breaches in Higher Education Institutions.
OAIC. 2019. Part 4: Notifiable Data Breach (NDB) Scheme. [online] Available at:
<https://www.oaic.gov.au/privacy/guidance-and-advice/data-breach-preparation-and-
response/part-4-notifiable-data-breach-ndb-scheme/> [Accessed 26 Aug. 2019].
Patterson, N. 2019. Almost 20 years of personal data was stolen from ANU. It could show up
on the dark web. [online] SBS News. Available at: <https://www.sbs.com.au/news/almost-
20-years-of-personal-data-was-stolen-from-anu-it-could-show-up-on-the-dark-web>
[Accessed 26 Aug. 2019].
Romanosky, S., Hoffman, D. and Acquisti, A., 2014. Empirical analysis of data breach
litigation. Journal of Empirical Legal Studies, 11(1), pp.74-104.
Vickovich, A. 2019. Canva under cyber-attack, with reportedly as many as 139 million users
affected. [online] Business Insider Australia. Available at:
<https://www.businessinsider.com.au/canva-under-cyber-attack-with-reportedly-as-many-as-
139-million-users-affected-2019-5> [Accessed 7 Sep. 2019].
Callahan, M.E., 2017. Once more into the breach. Criminal Justice, 32(2), p.20.
Mello, S., 2018. Data Breaches in Higher Education Institutions.
OAIC. 2019. Part 4: Notifiable Data Breach (NDB) Scheme. [online] Available at:
<https://www.oaic.gov.au/privacy/guidance-and-advice/data-breach-preparation-and-
response/part-4-notifiable-data-breach-ndb-scheme/> [Accessed 26 Aug. 2019].
Patterson, N. 2019. Almost 20 years of personal data was stolen from ANU. It could show up
on the dark web. [online] SBS News. Available at: <https://www.sbs.com.au/news/almost-
20-years-of-personal-data-was-stolen-from-anu-it-could-show-up-on-the-dark-web>
[Accessed 26 Aug. 2019].
Romanosky, S., Hoffman, D. and Acquisti, A., 2014. Empirical analysis of data breach
litigation. Journal of Empirical Legal Studies, 11(1), pp.74-104.
Vickovich, A. 2019. Canva under cyber-attack, with reportedly as many as 139 million users
affected. [online] Business Insider Australia. Available at:
<https://www.businessinsider.com.au/canva-under-cyber-attack-with-reportedly-as-many-as-
139-million-users-affected-2019-5> [Accessed 7 Sep. 2019].
Callahan, M.E., 2017. Once more into the breach. Criminal Justice, 32(2), p.20.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




