Zenith Stock Exchange Data Breach: A Comprehensive Malware Case Study
VerifiedAdded on 2023/04/21
|15
|1137
|222
Case Study
AI Summary
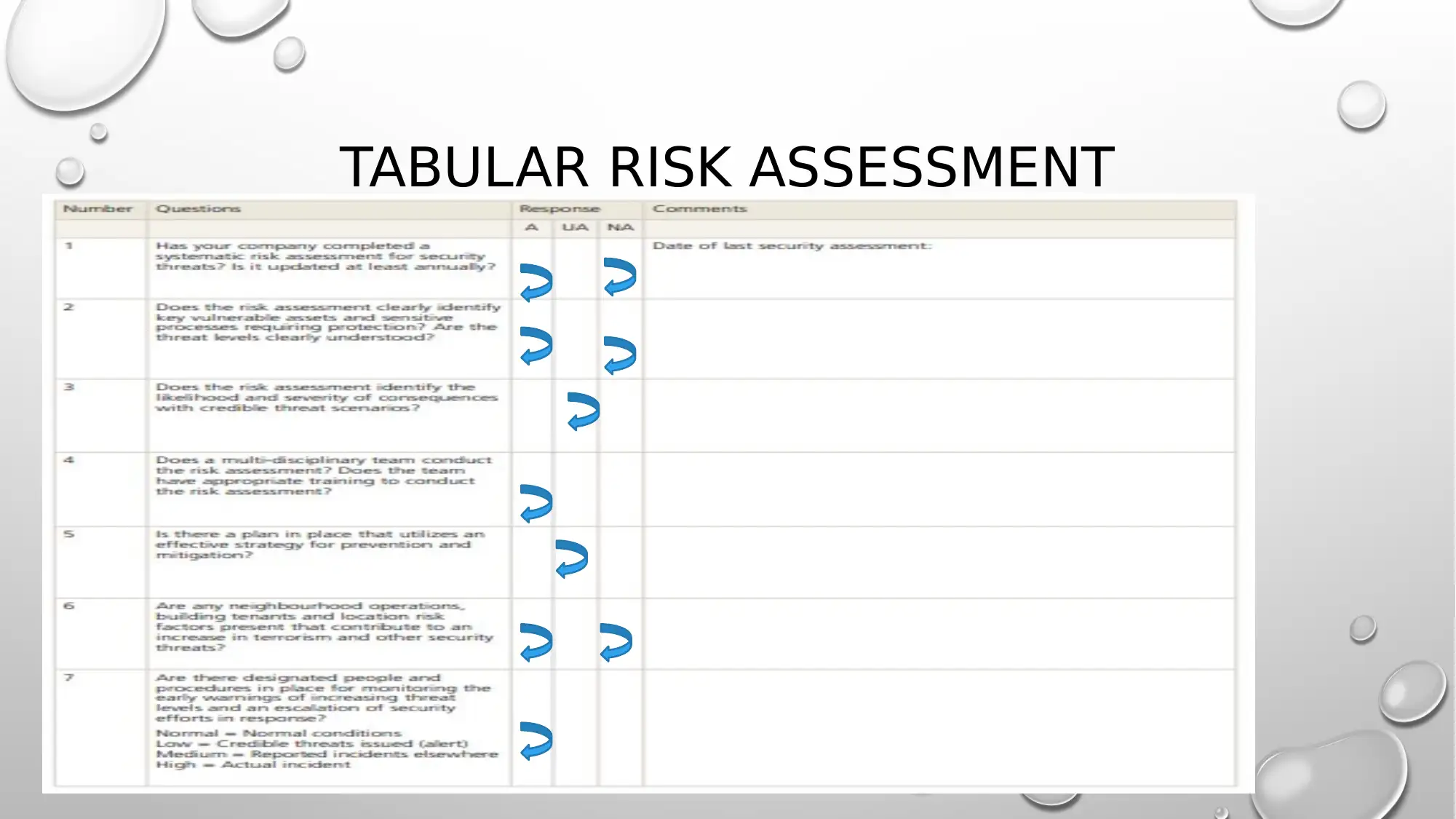
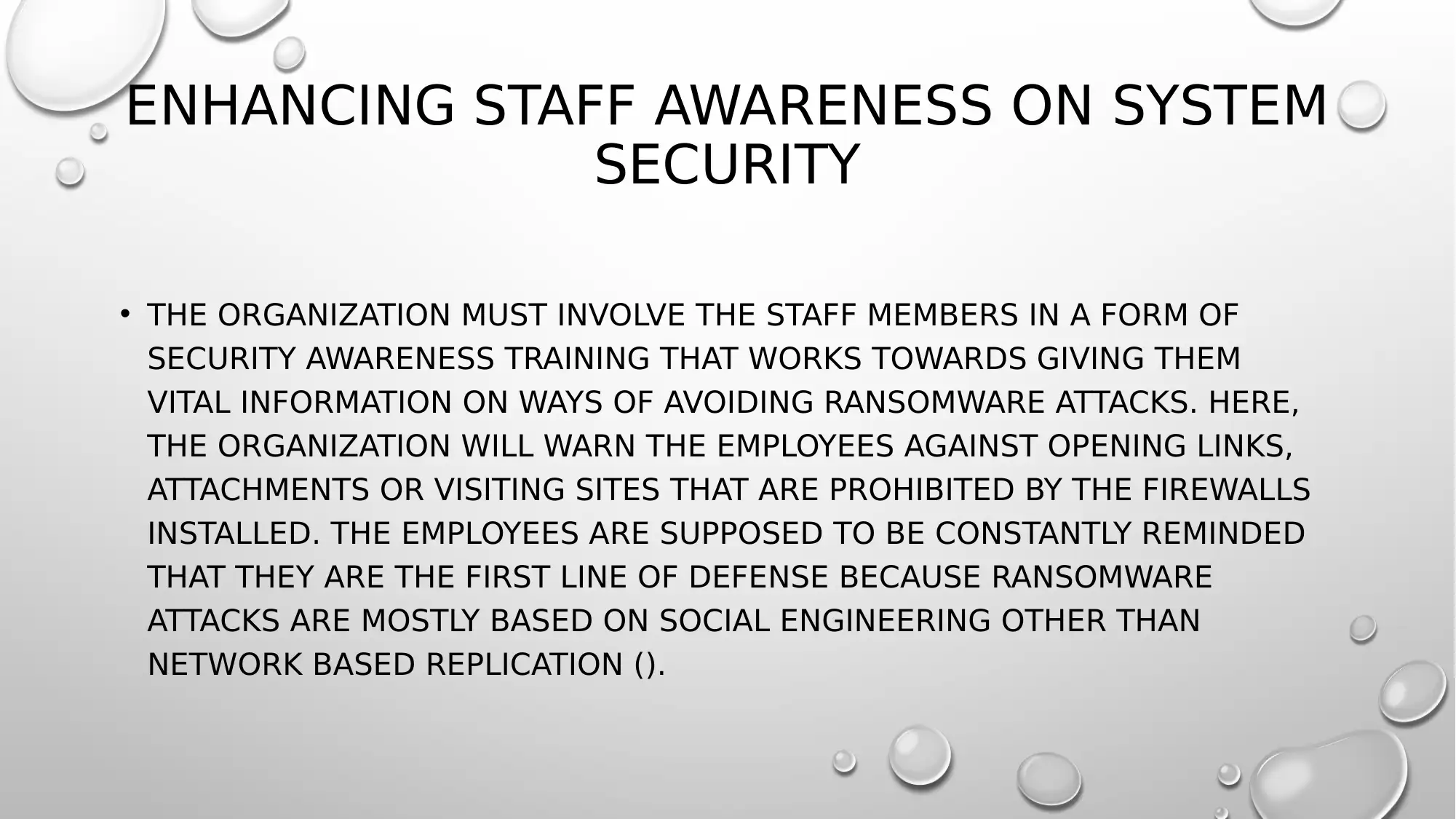
This case study examines a ransomware attack on the Zenith Stock Exchange, where hackers gained control of vital data and demanded a US$25 million ransom in Bitcoin. The attack originated from a phishing email targeting the head of security, leading to system-wide lockdown. The organization paid the ransom, and a subsequent data audit confirmed data integrity. The report outlines preventative measures, including installing antivirus software and firewalls, enhancing staff security awareness, creating data backups, patching systems, implementing GPO restrictions, enforcing admin rights and access controls, preventing data leakage, installing plugins and whitelists, and employing unified threat management on edge devices. These measures aim to strengthen the exchange's defenses against future attacks by addressing vulnerabilities and improving overall system security. Desklib offers a variety of resources, including solved assignments and study tools, to aid students in understanding complex topics like cybersecurity.
1 out of 15

















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)