Data Breach Analysis: Incidents, Regulations, and Flowcharts
VerifiedAdded on 2022/10/04
|12
|2782
|255
Report
AI Summary
This report provides an analysis of various data breaches, detailing incidents across different sectors such as healthcare, technology, and finance. It includes specific examples of organizations affected, the number of records compromised, and the nature of the breaches. The report also examines the impact of data breaches, including the estimated costs and the importance of data security. Furthermore, it discusses regulatory frameworks, specifically Australia’s Notifiable Data Breach scheme and the European Union's General Data Protection Regulation (GDPR), along with flowcharts illustrating data breach reporting processes and compliance measures. The report concludes by emphasizing the significance of data protection and the need for robust security practices to mitigate the risks associated with data breaches.

Running head: DATA BREACH
DATA BREACH
Name of Student:
Name of University:
Author note:
DATA BREACH
Name of Student:
Name of University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA BREACH
There is a list of data breaches that occurred in various regions. This is the list that
includes the theft which has more than 30000 and more records. There are certain
organizations where the number of a data breach is not known though they are also listed in
the record. There is a certain breach of data that occurred in North America (Solove and
Citron 2017). An estimated cost of a data breach which is more than $150 million recorded in
the year 2020 and globally it was recorded around $2.1 trillion. A data breach occurred in
Accendo Insurance Co. in the year of 2011 which has a total record of 1,75,350. This is a
healthcare organization that had poor security of online data that caused this breach. After
this Adobe Systems also encountered a breach of data in the year 2013, which recorded
around 152,000,000. This is a tech organization that was hacked and thus this breach
happened (Manworren, Letwat and Daily 2016). Another organization named Advocate
Medical Group whose data was breached in the year of 2013 with a total count of 4,000,000.
This is a healthcare organization in which the data was stolen (Chakraborty et al. 2016).
Another organization named AerServ had an attack in the year of 2018 with a total record of
75,000. This is an advertising organization that was also hacked. Next, another organization
is Affinity Health Plan, Inc. that had a data breach in the year of 2009 with a total count of
3,44,579. This is a healthcare organization where the data was stolen. Another organization
mentioned is Air Canada which had the data breach in the year of 2018, had a total count of
20,000. This is a transport organization that was hacked. Amertide is another organization
that had a breach in the year 2005 had a total count of 2,00,000 (Ablon et al. 2016). This is a
financial organization where the data was stolen. Ancestry, com is the name of another
organization that had a data breach in the year of 2015 with a total count of 3,00,000. This is
a web-based organization with poor security on data (Cheng, Liu and Yao 2017). Anthem
Inc. is another organization that had an attack in the year of 2015 with a total count of
80,000,000. This is a healthcare organization that was hacked and thus the data was breached.
There is a list of data breaches that occurred in various regions. This is the list that
includes the theft which has more than 30000 and more records. There are certain
organizations where the number of a data breach is not known though they are also listed in
the record. There is a certain breach of data that occurred in North America (Solove and
Citron 2017). An estimated cost of a data breach which is more than $150 million recorded in
the year 2020 and globally it was recorded around $2.1 trillion. A data breach occurred in
Accendo Insurance Co. in the year of 2011 which has a total record of 1,75,350. This is a
healthcare organization that had poor security of online data that caused this breach. After
this Adobe Systems also encountered a breach of data in the year 2013, which recorded
around 152,000,000. This is a tech organization that was hacked and thus this breach
happened (Manworren, Letwat and Daily 2016). Another organization named Advocate
Medical Group whose data was breached in the year of 2013 with a total count of 4,000,000.
This is a healthcare organization in which the data was stolen (Chakraborty et al. 2016).
Another organization named AerServ had an attack in the year of 2018 with a total record of
75,000. This is an advertising organization that was also hacked. Next, another organization
is Affinity Health Plan, Inc. that had a data breach in the year of 2009 with a total count of
3,44,579. This is a healthcare organization where the data was stolen. Another organization
mentioned is Air Canada which had the data breach in the year of 2018, had a total count of
20,000. This is a transport organization that was hacked. Amertide is another organization
that had a breach in the year 2005 had a total count of 2,00,000 (Ablon et al. 2016). This is a
financial organization where the data was stolen. Ancestry, com is the name of another
organization that had a data breach in the year of 2015 with a total count of 3,00,000. This is
a web-based organization with poor security on data (Cheng, Liu and Yao 2017). Anthem
Inc. is another organization that had an attack in the year of 2015 with a total count of
80,000,000. This is a healthcare organization that was hacked and thus the data was breached.

2DATA BREACH
AOL is another organization which had the attack in the year of 2004 with a total count of
92,000,000 (Trautman and Ormerod 2016). This is a web-based organization that was
hacked. After this, the same organization again had an attack in the year of 2006 and the year
of 2014 with a total count of 20,000,000 and 2,400,000. This is a web-based organization that
was published accidentally and on the next time it was hacked (Schatz and Bashroush 2016).
Apple also had a data breach in the year of 2012 with a total count of 2,75,000. This is a tech-
based organization that was hacked. The organization named Apple Health Medicaid had a
data breach in the year of 2016, where the total count of a breach was 91,000 (Leonard and
Principal 2018). This is a health care organization that had poor security of data. Another
organization named Ashley Madison had a data breach in the year of 2015. The total count
was 32,000,000, this is a web-based organization that was hacked. AT&T is an organization
that had an attack in the year of 2008 had a total count of 113000. This is a telecom based
organization where the data was stolen. The same organization also had an attack in the year
of 2010 where the breach count was 1,14,000. Automatic data processing is the name of
another organization which had an attack in the year of 2005. The total count of the attack
was 1,25,000. This is a financial organization that had poor security of data. The Bank of
New York Mellon is another organization that had an attack in the year of 2008 had a total
cont of 12,500,000. This is a financial organization where the data was stolen. Bank of
America is the name of another organization that had a breach in the year 2005 with a total
count of 1,200,000. This is a finance-based organization where the data was stolen. Barnes &
Nobel is the name of another organization that had a data breach in the year of 2012. This is
an organization of retail stores. In this organization, they had a breach on 63 of their stores
which was hacked. Bell Canada is the name of another organization that had an attack in the
year 2017 with a total count of 1,900,000. This is a telecom organization with poor security
(Carter and Hartridge 2018). The same organization also had an attack in the year of 2018
AOL is another organization which had the attack in the year of 2004 with a total count of
92,000,000 (Trautman and Ormerod 2016). This is a web-based organization that was
hacked. After this, the same organization again had an attack in the year of 2006 and the year
of 2014 with a total count of 20,000,000 and 2,400,000. This is a web-based organization that
was published accidentally and on the next time it was hacked (Schatz and Bashroush 2016).
Apple also had a data breach in the year of 2012 with a total count of 2,75,000. This is a tech-
based organization that was hacked. The organization named Apple Health Medicaid had a
data breach in the year of 2016, where the total count of a breach was 91,000 (Leonard and
Principal 2018). This is a health care organization that had poor security of data. Another
organization named Ashley Madison had a data breach in the year of 2015. The total count
was 32,000,000, this is a web-based organization that was hacked. AT&T is an organization
that had an attack in the year of 2008 had a total count of 113000. This is a telecom based
organization where the data was stolen. The same organization also had an attack in the year
of 2010 where the breach count was 1,14,000. Automatic data processing is the name of
another organization which had an attack in the year of 2005. The total count of the attack
was 1,25,000. This is a financial organization that had poor security of data. The Bank of
New York Mellon is another organization that had an attack in the year of 2008 had a total
cont of 12,500,000. This is a financial organization where the data was stolen. Bank of
America is the name of another organization that had a breach in the year 2005 with a total
count of 1,200,000. This is a finance-based organization where the data was stolen. Barnes &
Nobel is the name of another organization that had a data breach in the year of 2012. This is
an organization of retail stores. In this organization, they had a breach on 63 of their stores
which was hacked. Bell Canada is the name of another organization that had an attack in the
year 2017 with a total count of 1,900,000. This is a telecom organization with poor security
(Carter and Hartridge 2018). The same organization also had an attack in the year of 2018
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DATA BREACH
with a total count of 1,00,000. Betfair is another organization that had a breach in the year
2010. The total count of the attack was 2,300,000. This is a web-based organization that was
hacked. Bethesda Game Studios is the name of another organization that had an attack in the
year of 2011. The total count of the breach was 200,000. This is a gaming organization that
was hacked. The same organization had an attack in the year of 2018. Black media games are
the name of another organization which had an attack in the year of 2018, the total count of
the attack was 7,633,234. This is a gaming organization that was hacked (Goodman and
Flaxman 2017). Blizzard Entertainment is the name of another organization that had a breach
in the year 2012. The total count of the attack was 7,633,234, this is a gaming organization
that was hacked. Blizzard Entertainment is another organization that had a breach in the year
2012 with a total count of 14,000,000. This is a gaming organization that was hacked. British
Airways is another organization that had an attack in the year of 2018 with a total breach
count of 380,000. This is a transport organization that was hacked. Besides this, the
organization also had an attack in the year 2015 where 10,000 was the count. This is the part
of the organization which is based on the retail industry that was hacked.
with a total count of 1,00,000. Betfair is another organization that had a breach in the year
2010. The total count of the attack was 2,300,000. This is a web-based organization that was
hacked. Bethesda Game Studios is the name of another organization that had an attack in the
year of 2011. The total count of the breach was 200,000. This is a gaming organization that
was hacked. The same organization had an attack in the year of 2018. Black media games are
the name of another organization which had an attack in the year of 2018, the total count of
the attack was 7,633,234. This is a gaming organization that was hacked (Goodman and
Flaxman 2017). Blizzard Entertainment is the name of another organization that had a breach
in the year 2012. The total count of the attack was 7,633,234, this is a gaming organization
that was hacked. Blizzard Entertainment is another organization that had a breach in the year
2012 with a total count of 14,000,000. This is a gaming organization that was hacked. British
Airways is another organization that had an attack in the year of 2018 with a total breach
count of 380,000. This is a transport organization that was hacked. Besides this, the
organization also had an attack in the year 2015 where 10,000 was the count. This is the part
of the organization which is based on the retail industry that was hacked.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
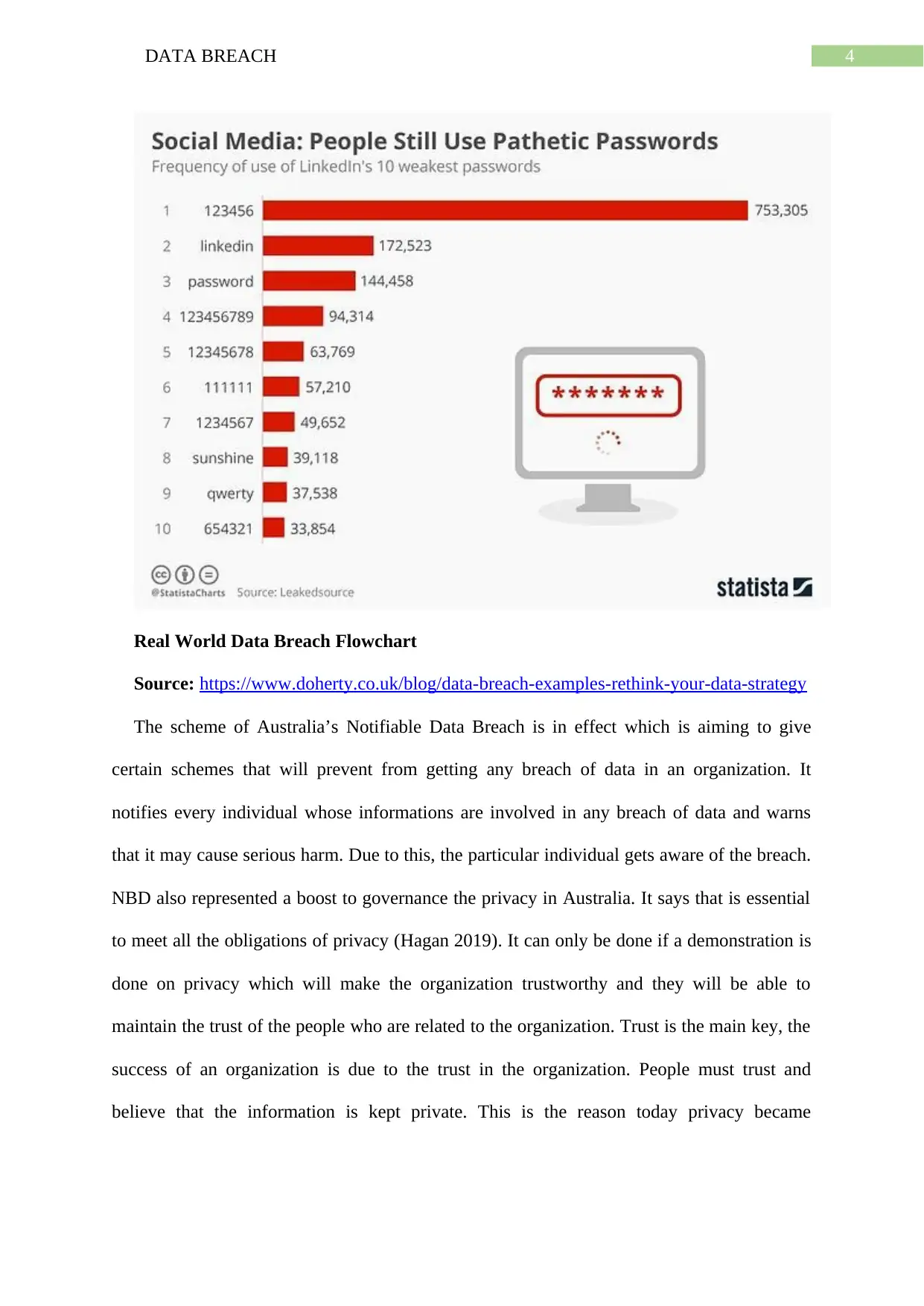
4DATA BREACH
Real World Data Breach Flowchart
Source: https://www.doherty.co.uk/blog/data-breach-examples-rethink-your-data-strategy
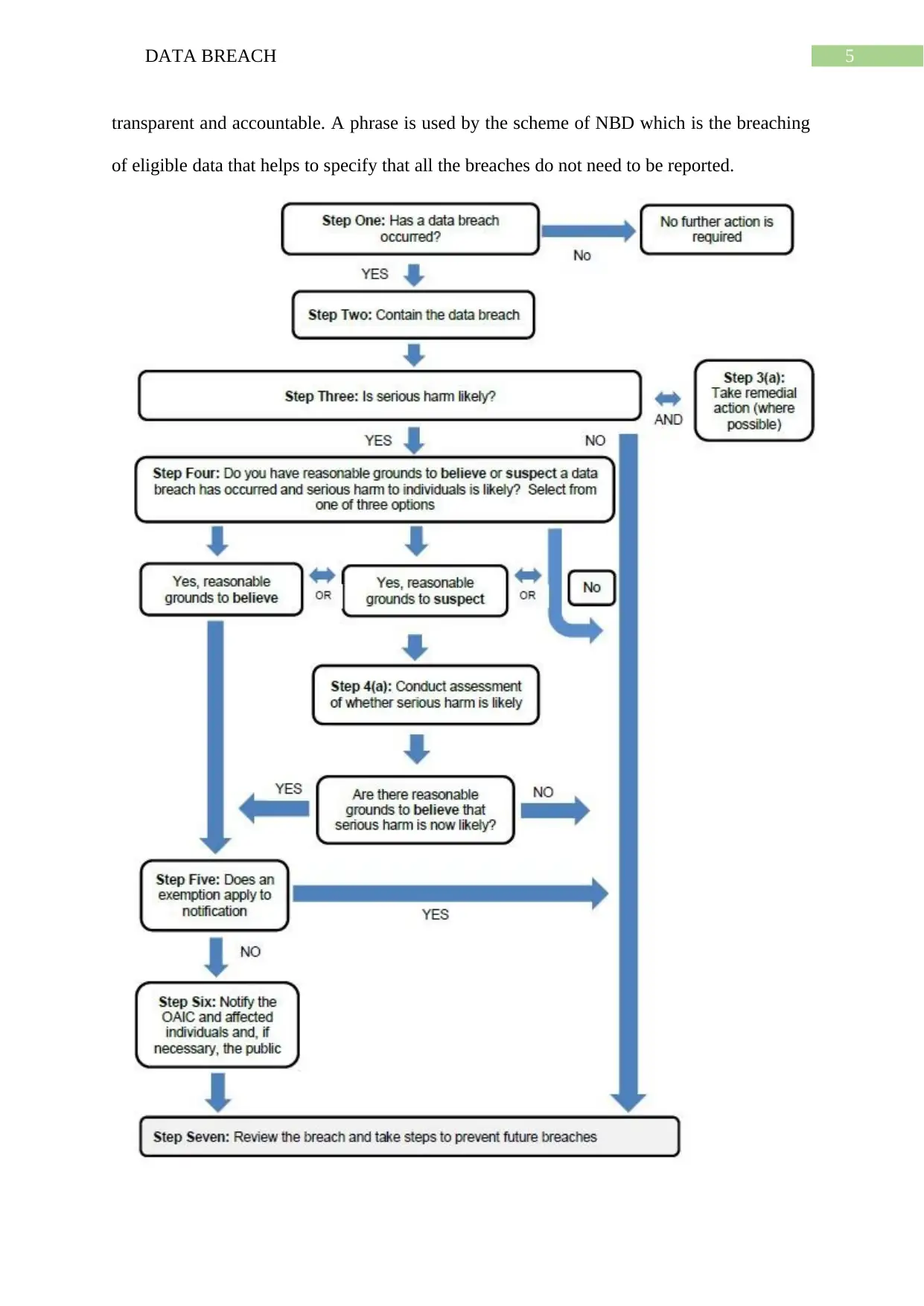
The scheme of Australia’s Notifiable Data Breach is in effect which is aiming to give
certain schemes that will prevent from getting any breach of data in an organization. It
notifies every individual whose informations are involved in any breach of data and warns
that it may cause serious harm. Due to this, the particular individual gets aware of the breach.
NBD also represented a boost to governance the privacy in Australia. It says that is essential
to meet all the obligations of privacy (Hagan 2019). It can only be done if a demonstration is
done on privacy which will make the organization trustworthy and they will be able to
maintain the trust of the people who are related to the organization. Trust is the main key, the
success of an organization is due to the trust in the organization. People must trust and
believe that the information is kept private. This is the reason today privacy became
Real World Data Breach Flowchart
Source: https://www.doherty.co.uk/blog/data-breach-examples-rethink-your-data-strategy
The scheme of Australia’s Notifiable Data Breach is in effect which is aiming to give
certain schemes that will prevent from getting any breach of data in an organization. It
notifies every individual whose informations are involved in any breach of data and warns
that it may cause serious harm. Due to this, the particular individual gets aware of the breach.
NBD also represented a boost to governance the privacy in Australia. It says that is essential
to meet all the obligations of privacy (Hagan 2019). It can only be done if a demonstration is
done on privacy which will make the organization trustworthy and they will be able to
maintain the trust of the people who are related to the organization. Trust is the main key, the
success of an organization is due to the trust in the organization. People must trust and
believe that the information is kept private. This is the reason today privacy became
5DATA BREACH
transparent and accountable. A phrase is used by the scheme of NBD which is the breaching
of eligible data that helps to specify that all the breaches do not need to be reported.
transparent and accountable. A phrase is used by the scheme of NBD which is the breaching
of eligible data that helps to specify that all the breaches do not need to be reported.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DATA BREACH
Notifiable data breach diagram
Source: https://www.ccct.com.au/superdocs/data-breach-response-procedure
The European Union's General Data Protection Regulation (GDPR) is a regulation in the
law of the EU for protecting the data (De Hert and Papakonstantinou 2016). It also addresses
all the data transfers that are out of the economic area of Europe. The main of GDPR is to
control the individuals by their data and also to simplify the regulatory environment in case
of international business. The scheme includes the processing of data. It maintains the legal
obligations of the data controller, it protects the interests for a data subject and also for
another person. The scheme also performs a task with the interest of the public (La Torre et
al. 2018). The scheme also fulfills the obligations along with a data subject. If the subject of
the data has given consent for processing the personal data of a particular person the scheme
serves in that case. According to the scheme, the subjects of the data should always allow to
take over the consent at any time and the process should not be hard. According to the
scheme, the data controller should not refuse any type of service for the users who have
declined the consent for the processing which is not necessary for using the service.
According to GDPR, the multiple processing should not be gathered together in a particular
affirmation prompt because this is not exact for each of the data use and the permission for
the individuals is also not given properly.
Notifiable data breach diagram
Source: https://www.ccct.com.au/superdocs/data-breach-response-procedure
The European Union's General Data Protection Regulation (GDPR) is a regulation in the
law of the EU for protecting the data (De Hert and Papakonstantinou 2016). It also addresses
all the data transfers that are out of the economic area of Europe. The main of GDPR is to
control the individuals by their data and also to simplify the regulatory environment in case
of international business. The scheme includes the processing of data. It maintains the legal
obligations of the data controller, it protects the interests for a data subject and also for
another person. The scheme also performs a task with the interest of the public (La Torre et
al. 2018). The scheme also fulfills the obligations along with a data subject. If the subject of
the data has given consent for processing the personal data of a particular person the scheme
serves in that case. According to the scheme, the subjects of the data should always allow to
take over the consent at any time and the process should not be hard. According to the
scheme, the data controller should not refuse any type of service for the users who have
declined the consent for the processing which is not necessary for using the service.
According to GDPR, the multiple processing should not be gathered together in a particular
affirmation prompt because this is not exact for each of the data use and the permission for
the individuals is also not given properly.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
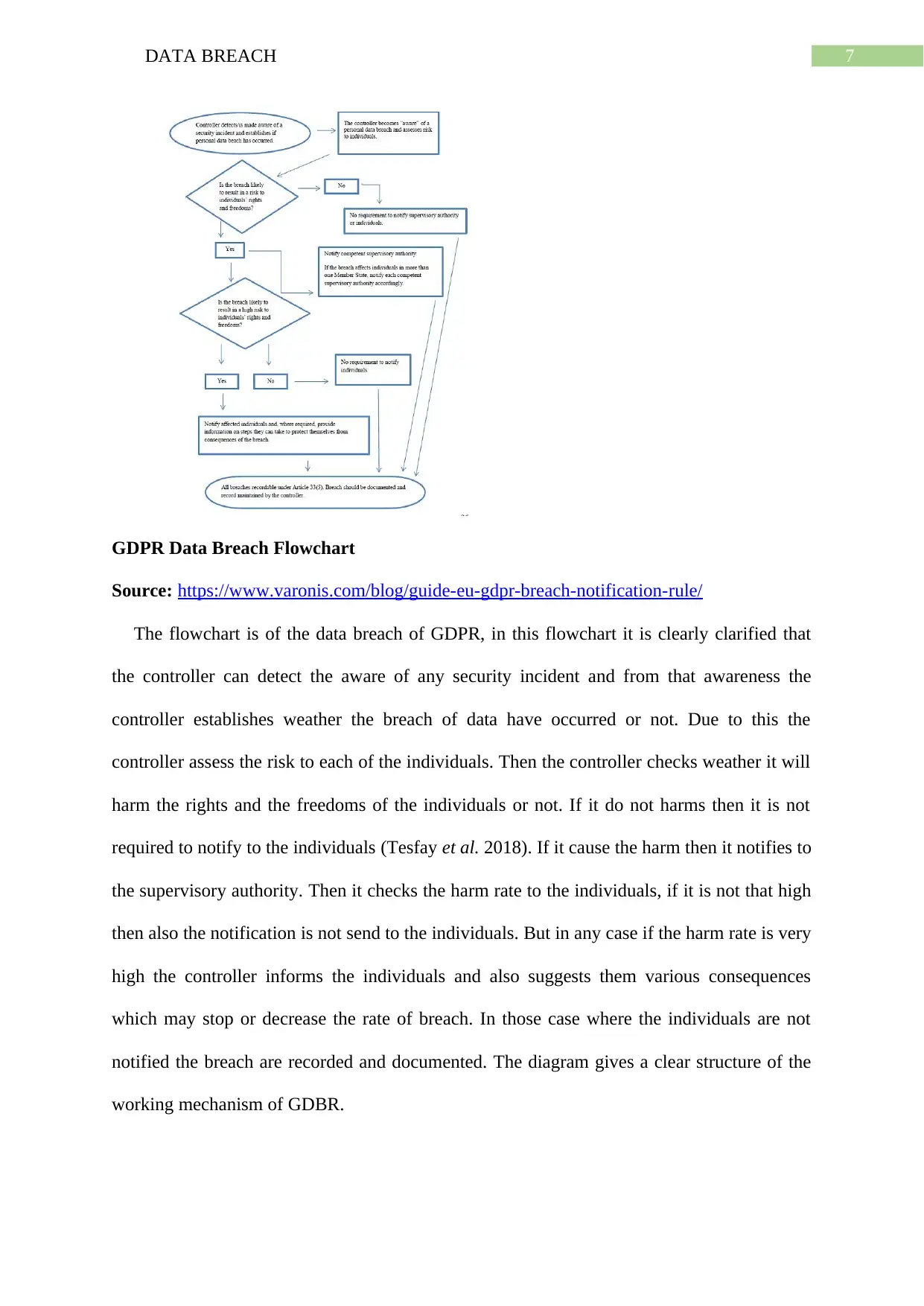
7DATA BREACH
GDPR Data Breach Flowchart
Source: https://www.varonis.com/blog/guide-eu-gdpr-breach-notification-rule/
The flowchart is of the data breach of GDPR, in this flowchart it is clearly clarified that
the controller can detect the aware of any security incident and from that awareness the
controller establishes weather the breach of data have occurred or not. Due to this the
controller assess the risk to each of the individuals. Then the controller checks weather it will
harm the rights and the freedoms of the individuals or not. If it do not harms then it is not
required to notify to the individuals (Tesfay et al. 2018). If it cause the harm then it notifies to
the supervisory authority. Then it checks the harm rate to the individuals, if it is not that high
then also the notification is not send to the individuals. But in any case if the harm rate is very
high the controller informs the individuals and also suggests them various consequences
which may stop or decrease the rate of breach. In those case where the individuals are not
notified the breach are recorded and documented. The diagram gives a clear structure of the
working mechanism of GDBR.
GDPR Data Breach Flowchart
Source: https://www.varonis.com/blog/guide-eu-gdpr-breach-notification-rule/
The flowchart is of the data breach of GDPR, in this flowchart it is clearly clarified that
the controller can detect the aware of any security incident and from that awareness the
controller establishes weather the breach of data have occurred or not. Due to this the
controller assess the risk to each of the individuals. Then the controller checks weather it will
harm the rights and the freedoms of the individuals or not. If it do not harms then it is not
required to notify to the individuals (Tesfay et al. 2018). If it cause the harm then it notifies to
the supervisory authority. Then it checks the harm rate to the individuals, if it is not that high
then also the notification is not send to the individuals. But in any case if the harm rate is very
high the controller informs the individuals and also suggests them various consequences
which may stop or decrease the rate of breach. In those case where the individuals are not
notified the breach are recorded and documented. The diagram gives a clear structure of the
working mechanism of GDBR.

8DATA BREACH
GDPR Data Breach Reporting Diagram
Source: https://www.imperva.com/blog/72-hours-understanding-the-gdpr-data-breach-
reporting-timeline/
The steps of data breach of GDPR is explained clearly in the reporting diagram. All the
investigations are carried out clearly in the diagram. The diagram also informs about the
regulators of the breach and the individuals of the breach. The diagram also give specific
information of the data that is impacted along with the addressing of the issues. All of these
tasks are performed within 72 hours of the breach. In any case no notification is received to
the individuals within the next 72 hours of the breach the GDPR sends a request where it so
mentioned to the controller to provide an acceptable justification of the delay (Lindqvist
2017). The additional disruption are added to the operations of the regular business and to the
hassle of exasperating administrative. Firstly the breach is carried out with various stages of
information. After this the regulators are informed which impacts the individuals. After this
the data that are impacted is noticed. Thereafter a draft is made for the containment plan.
GDPR Data Breach Reporting Diagram
Source: https://www.imperva.com/blog/72-hours-understanding-the-gdpr-data-breach-
reporting-timeline/
The steps of data breach of GDPR is explained clearly in the reporting diagram. All the
investigations are carried out clearly in the diagram. The diagram also informs about the
regulators of the breach and the individuals of the breach. The diagram also give specific
information of the data that is impacted along with the addressing of the issues. All of these
tasks are performed within 72 hours of the breach. In any case no notification is received to
the individuals within the next 72 hours of the breach the GDPR sends a request where it so
mentioned to the controller to provide an acceptable justification of the delay (Lindqvist
2017). The additional disruption are added to the operations of the regular business and to the
hassle of exasperating administrative. Firstly the breach is carried out with various stages of
information. After this the regulators are informed which impacts the individuals. After this
the data that are impacted is noticed. Thereafter a draft is made for the containment plan.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DATA BREACH
The report states a clear conclusion that data breach may take place, which can be harmful or
in some cases less harmful as well. In this paper there are mentioned a list of data breach
incidents which are explained (Kurtz and Semmann 2018). The paper also gives information
about Australia’s Notifiable Data Breach along with various diagrams and flowcharts. The
paper also provides GDPR Data Breach Flowchart and a data breach reporting diagram of
GDPR.
The report states a clear conclusion that data breach may take place, which can be harmful or
in some cases less harmful as well. In this paper there are mentioned a list of data breach
incidents which are explained (Kurtz and Semmann 2018). The paper also gives information
about Australia’s Notifiable Data Breach along with various diagrams and flowcharts. The
paper also provides GDPR Data Breach Flowchart and a data breach reporting diagram of
GDPR.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DATA BREACH
Reference:
Ablon, L., Heaton, P., Lavery, D.C. and Romanosky, S., 2016. Consumer attitudes toward
data breach notifications and loss of personal information. Rand Corporation.
Carter, D.J. and Hartridge, S., 2018. Mandatory data breach notification requirements for
medical practice. The Medical Journal of Australia, 209(5), pp.204-205.
Chakraborty, R., Lee, J., Bagchi-Sen, S., Upadhyaya, S. and Rao, H.R., 2016. Online
shopping intention in the context of data breach in online retail stores: An examination of
older and younger adults. Decision Support Systems, 83, pp.47-56.
Cheng, L., Liu, F. and Yao, D.D., 2017. Enterprise data breach: causes, challenges,
prevention, and future directions. Wiley Interdisciplinary Reviews: Data Mining and
Knowledge Discovery, 7(5).
De Hert, P. and Papakonstantinou, V., 2016. The new General Data Protection Regulation:
Still a sound system for the protection of individuals?. Computer Law & Security
Review, 32(2), pp.179-194.
Goodman, B. and Flaxman, S., 2017. European Union regulations on algorithmic decision-
making and a “right to explanation”. AI Magazine, 38(3), pp.50-57.
Leonard, P. and Principal, D.S., 2018. The new Australian Notifiable Data Breach
Scheme. Available at SSRN 3154271.
Manworren, N., Letwat, J. and Daily, O., 2016. Why you should care about the Target data
breach. Business Horizons, 59(3), pp.257-266.
Schatz, D. and Bashroush, R., 2016. The impact of repeated data breach events on
organisations’ market value. Information & Computer Security, 24(1), pp.73-92.
Solove, D.J. and Citron, D.K., 2017. Risk and anxiety: A theory of data-breach harms. Tex.
L. Rev., 96, p.737.
Reference:
Ablon, L., Heaton, P., Lavery, D.C. and Romanosky, S., 2016. Consumer attitudes toward
data breach notifications and loss of personal information. Rand Corporation.
Carter, D.J. and Hartridge, S., 2018. Mandatory data breach notification requirements for
medical practice. The Medical Journal of Australia, 209(5), pp.204-205.
Chakraborty, R., Lee, J., Bagchi-Sen, S., Upadhyaya, S. and Rao, H.R., 2016. Online
shopping intention in the context of data breach in online retail stores: An examination of
older and younger adults. Decision Support Systems, 83, pp.47-56.
Cheng, L., Liu, F. and Yao, D.D., 2017. Enterprise data breach: causes, challenges,
prevention, and future directions. Wiley Interdisciplinary Reviews: Data Mining and
Knowledge Discovery, 7(5).
De Hert, P. and Papakonstantinou, V., 2016. The new General Data Protection Regulation:
Still a sound system for the protection of individuals?. Computer Law & Security
Review, 32(2), pp.179-194.
Goodman, B. and Flaxman, S., 2017. European Union regulations on algorithmic decision-
making and a “right to explanation”. AI Magazine, 38(3), pp.50-57.
Leonard, P. and Principal, D.S., 2018. The new Australian Notifiable Data Breach
Scheme. Available at SSRN 3154271.
Manworren, N., Letwat, J. and Daily, O., 2016. Why you should care about the Target data
breach. Business Horizons, 59(3), pp.257-266.
Schatz, D. and Bashroush, R., 2016. The impact of repeated data breach events on
organisations’ market value. Information & Computer Security, 24(1), pp.73-92.
Solove, D.J. and Citron, D.K., 2017. Risk and anxiety: A theory of data-breach harms. Tex.
L. Rev., 96, p.737.

11DATA BREACH
Trautman, L.J. and Ormerod, P.C., 2016. Corporate Directors' and Officers' Cybersecurity
Standard of Care: The Yahoo Data Breach. Am. UL Rev., 66, p.1231.
Lindqvist, J., 2017. New challenges to personal data processing agreements: is the GDPR fit to deal
with contract, accountability and liability in a world of the Internet of Things?. International Journal of
Law and Information Technology, 26(1), pp.45-63.
Kurtz, C. and Semmann, M., 2018. Privacy by Design to Comply with GDPR: A Review on Third-Party
Data Processors.
Tesfay, W.B., Hofmann, P., Nakamura, T., Kiyomoto, S. and Serna, J., 2018, March. PrivacyGuide:
towards an implementation of the EU GDPR on internet privacy policy evaluation. In Proceedings of
the Fourth ACM International Workshop on Security and Privacy Analytics (pp. 15-21). ACM.
La Torre, M., Botes, V.L., Dumay, J., Rea, M.A. and Odendaal, E., 2018. The fall and rise of
intellectual capital accounting: new prospects from the Big Data revolution. Meditari Accountancy
Research, 26(3), pp.381-399.
Hagan, H., 2019. How to Protect Consumer Data: Leave It to the Consumer Protection Agency: FTC
Rulemaking as a Path to Federal Cybersecurity Regulation. Colum. Bus. L. Rev., p.735.
Trautman, L.J. and Ormerod, P.C., 2016. Corporate Directors' and Officers' Cybersecurity
Standard of Care: The Yahoo Data Breach. Am. UL Rev., 66, p.1231.
Lindqvist, J., 2017. New challenges to personal data processing agreements: is the GDPR fit to deal
with contract, accountability and liability in a world of the Internet of Things?. International Journal of
Law and Information Technology, 26(1), pp.45-63.
Kurtz, C. and Semmann, M., 2018. Privacy by Design to Comply with GDPR: A Review on Third-Party
Data Processors.
Tesfay, W.B., Hofmann, P., Nakamura, T., Kiyomoto, S. and Serna, J., 2018, March. PrivacyGuide:
towards an implementation of the EU GDPR on internet privacy policy evaluation. In Proceedings of
the Fourth ACM International Workshop on Security and Privacy Analytics (pp. 15-21). ACM.
La Torre, M., Botes, V.L., Dumay, J., Rea, M.A. and Odendaal, E., 2018. The fall and rise of
intellectual capital accounting: new prospects from the Big Data revolution. Meditari Accountancy
Research, 26(3), pp.381-399.
Hagan, H., 2019. How to Protect Consumer Data: Leave It to the Consumer Protection Agency: FTC
Rulemaking as a Path to Federal Cybersecurity Regulation. Colum. Bus. L. Rev., p.735.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




