Cybersecurity Report: Data Breaches, Privacy, and Business Impact
VerifiedAdded on 2022/08/14
|12
|3721
|11
Report
AI Summary
This report delves into the critical topic of technology security, specifically focusing on data breaches and privacy concerns within businesses. It begins with an introduction to the subject, highlighting the importance of cybersecurity in today's digital landscape. The report then explores the definition of data breaches, their various forms, and the significance of data privacy. It investigates the causes and threats associated with data breaches, including system vulnerabilities, weak passwords, malware attacks, and malicious insiders, and presents real-world examples of companies affected by data breaches, such as Yahoo, eBay, and Marriott. The report further examines the consequences of data breaches, which include loss of reputation, financial penalties, and impact on intellectual property. Finally, it discusses effective strategies for managing and mitigating data breaches, emphasizing the importance of monitoring systems, intrusion detection, and proactive security measures. The report aims to provide a comprehensive understanding of the challenges and solutions related to data breaches and privacy in the context of technology security.

RUNNING HEAD: TECHNOLOGY SECURITY 0
Title: Technology Security
Student’s Details-
Introduction
Technology security is wide term to be used for the various issue concerning the
information technology (Ahson & Ilyas, 2017). Here, the paper is based on the cyber security
topic ‘data breaches and privacy’ which is regarded as the major challenge for the business and
requires appropriate management. Moreover, data breaches can arise due to the technological
errors and the irresponsibility of the companies with respect to the safety and security systems.
As a result, this can affect the entire business reputation and also can impact the relationships
with the customers (Buczak & Guven, 2015). This needs the appropriate management through
the installation of the secured system that can reduce the vulnerabilities of data threats. Here, the
report is prepared on the topic of data breaches and the privacy that can hamper the business and
gives rise to several issue such as cyberattacks. Also, the report had discussed the causes and
threats of data breaches that entices the various loss of information and being causing the various
kinds of cybercrimes. Further, it has discussed the consequences data breaches on the business
through the use of relevant examples of real-life companies’ examples along with the
management of the security systems to be implemented into the business.
2020
Title: Technology Security
Student’s Details-
Introduction
Technology security is wide term to be used for the various issue concerning the
information technology (Ahson & Ilyas, 2017). Here, the paper is based on the cyber security
topic ‘data breaches and privacy’ which is regarded as the major challenge for the business and
requires appropriate management. Moreover, data breaches can arise due to the technological
errors and the irresponsibility of the companies with respect to the safety and security systems.
As a result, this can affect the entire business reputation and also can impact the relationships
with the customers (Buczak & Guven, 2015). This needs the appropriate management through
the installation of the secured system that can reduce the vulnerabilities of data threats. Here, the
report is prepared on the topic of data breaches and the privacy that can hamper the business and
gives rise to several issue such as cyberattacks. Also, the report had discussed the causes and
threats of data breaches that entices the various loss of information and being causing the various
kinds of cybercrimes. Further, it has discussed the consequences data breaches on the business
through the use of relevant examples of real-life companies’ examples along with the
management of the security systems to be implemented into the business.
2020
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TECHNOLOGY SECURITY 1
Data Breaches and Privacy
Data breaches is related with the security incident which is caused as a result of the
access of information without authorization. This gives rise to the cyberattacks that can cause
damage to the reputation of the business due to the lack of information security (Wheatley,
Maillart, & Sornette, 2016). It affects the consumers and subsequently it takes certain time to get
repaired. Therefore, the privacy of information is crucial for the business in which the companies
tend to make policies regarding the protection of the personal identifiable information which
includes the name, date of birth and card details for maintaining the privacy of information and
avoiding the data beaches. Further, phishing is one of the type of data breach that can be caused
due to the email malware which can create the tendency of entering of the unintentional virus
into the system (Manworren, Letwat, & Daily, 2016). Also, data breach can be through the
Denial of Service in which attackers basically use flood attack in which attackers target the
traffic that makes the system slower which makes the system slower.
Further, there are companies that are involved in the data breaches due to the unsecured
systems that damages the privacy of the people. For example, Yahoo has announced the data
breach in September 2016 which is proved to be the greatest data breach in history that
compromised the private information of customers that specifically included the names, date of
birth and contact number of 500 million users. Also, Yahoo ranks higher in the data breach
scandal as is shown from the following graph:
Data Breaches and Privacy
Data breaches is related with the security incident which is caused as a result of the
access of information without authorization. This gives rise to the cyberattacks that can cause
damage to the reputation of the business due to the lack of information security (Wheatley,
Maillart, & Sornette, 2016). It affects the consumers and subsequently it takes certain time to get
repaired. Therefore, the privacy of information is crucial for the business in which the companies
tend to make policies regarding the protection of the personal identifiable information which
includes the name, date of birth and card details for maintaining the privacy of information and
avoiding the data beaches. Further, phishing is one of the type of data breach that can be caused
due to the email malware which can create the tendency of entering of the unintentional virus
into the system (Manworren, Letwat, & Daily, 2016). Also, data breach can be through the
Denial of Service in which attackers basically use flood attack in which attackers target the
traffic that makes the system slower which makes the system slower.
Further, there are companies that are involved in the data breaches due to the unsecured
systems that damages the privacy of the people. For example, Yahoo has announced the data
breach in September 2016 which is proved to be the greatest data breach in history that
compromised the private information of customers that specifically included the names, date of
birth and contact number of 500 million users. Also, Yahoo ranks higher in the data breach
scandal as is shown from the following graph:
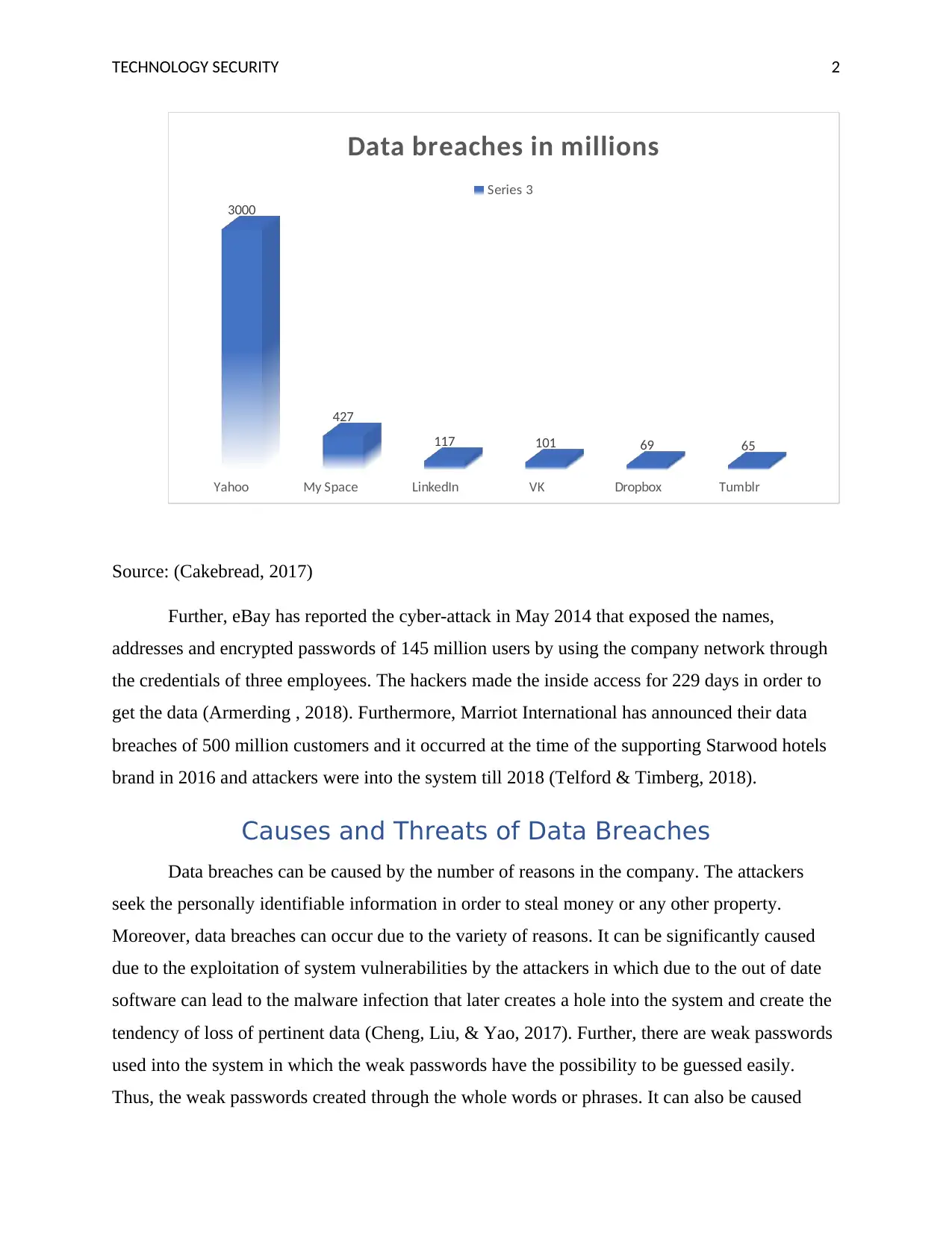
TECHNOLOGY SECURITY 2
Yahoo My Space LinkedIn VK Dropbox Tumblr
3000
427
117 101 69 65
Data breaches in millions
Series 3
Source: (Cakebread, 2017)
Further, eBay has reported the cyber-attack in May 2014 that exposed the names,
addresses and encrypted passwords of 145 million users by using the company network through
the credentials of three employees. The hackers made the inside access for 229 days in order to
get the data (Armerding , 2018). Furthermore, Marriot International has announced their data
breaches of 500 million customers and it occurred at the time of the supporting Starwood hotels
brand in 2016 and attackers were into the system till 2018 (Telford & Timberg, 2018).
Causes and Threats of Data Breaches
Data breaches can be caused by the number of reasons in the company. The attackers
seek the personally identifiable information in order to steal money or any other property.
Moreover, data breaches can occur due to the variety of reasons. It can be significantly caused
due to the exploitation of system vulnerabilities by the attackers in which due to the out of date
software can lead to the malware infection that later creates a hole into the system and create the
tendency of loss of pertinent data (Cheng, Liu, & Yao, 2017). Further, there are weak passwords
used into the system in which the weak passwords have the possibility to be guessed easily.
Thus, the weak passwords created through the whole words or phrases. It can also be caused
Yahoo My Space LinkedIn VK Dropbox Tumblr
3000
427
117 101 69 65
Data breaches in millions
Series 3
Source: (Cakebread, 2017)
Further, eBay has reported the cyber-attack in May 2014 that exposed the names,
addresses and encrypted passwords of 145 million users by using the company network through
the credentials of three employees. The hackers made the inside access for 229 days in order to
get the data (Armerding , 2018). Furthermore, Marriot International has announced their data
breaches of 500 million customers and it occurred at the time of the supporting Starwood hotels
brand in 2016 and attackers were into the system till 2018 (Telford & Timberg, 2018).
Causes and Threats of Data Breaches
Data breaches can be caused by the number of reasons in the company. The attackers
seek the personally identifiable information in order to steal money or any other property.
Moreover, data breaches can occur due to the variety of reasons. It can be significantly caused
due to the exploitation of system vulnerabilities by the attackers in which due to the out of date
software can lead to the malware infection that later creates a hole into the system and create the
tendency of loss of pertinent data (Cheng, Liu, & Yao, 2017). Further, there are weak passwords
used into the system in which the weak passwords have the possibility to be guessed easily.
Thus, the weak passwords created through the whole words or phrases. It can also be caused
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
TECHNOLOGY SECURITY 3
through the drive-by-downloads when one unintentionally downloads the virus which is brought
up by the compromised web page that takes the advantage of the out of update software or has a
security flaw. Further, it can be caused through the malware attacks by using phishing email
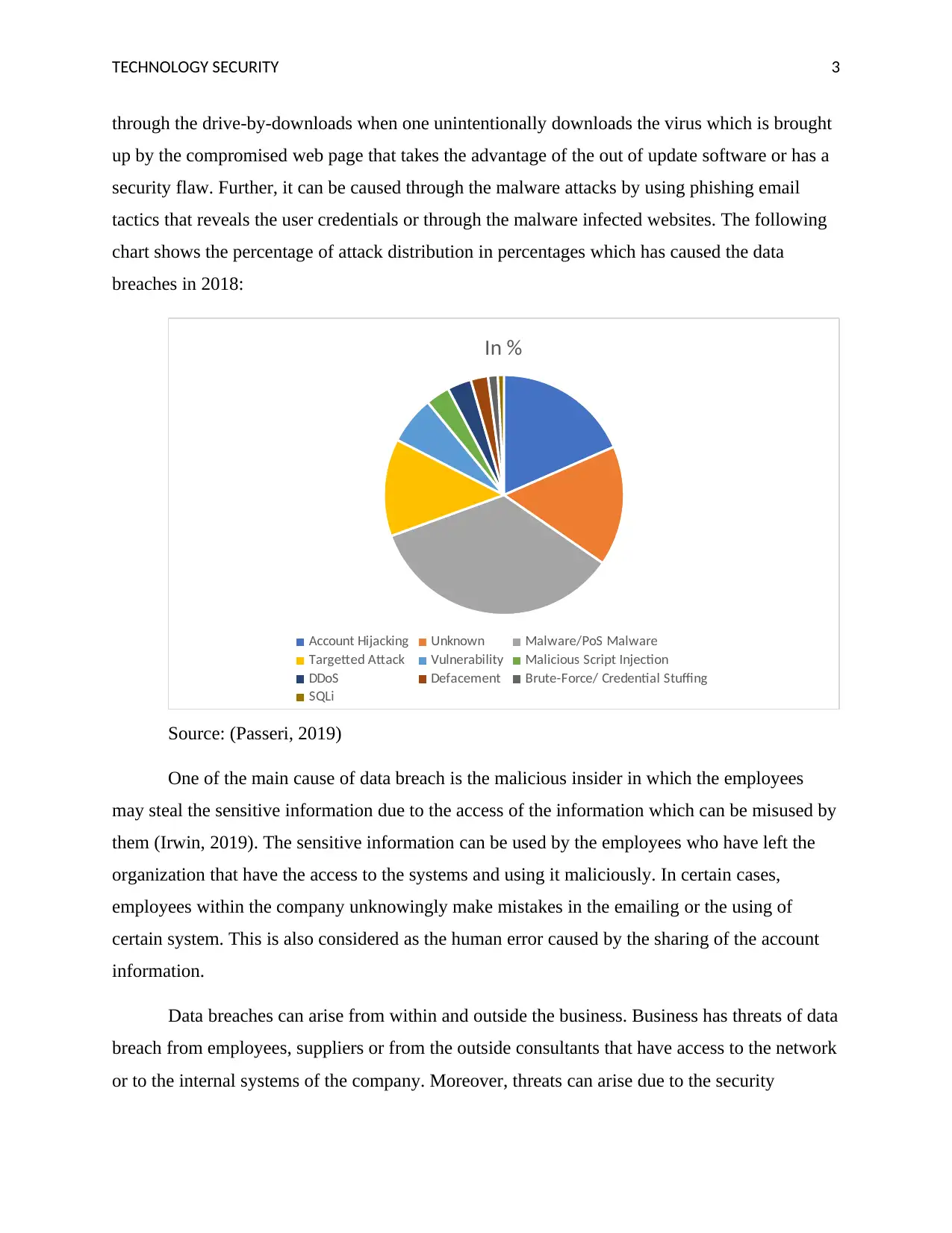
tactics that reveals the user credentials or through the malware infected websites. The following
chart shows the percentage of attack distribution in percentages which has caused the data
breaches in 2018:
In %
Account Hijacking Unknown Malware/PoS Malware
Targetted Attack Vulnerability Malicious Script Injection
DDoS Defacement Brute-Force/ Credential Stuffing
SQLi
Source: (Passeri, 2019)
One of the main cause of data breach is the malicious insider in which the employees
may steal the sensitive information due to the access of the information which can be misused by
them (Irwin, 2019). The sensitive information can be used by the employees who have left the
organization that have the access to the systems and using it maliciously. In certain cases,
employees within the company unknowingly make mistakes in the emailing or the using of
certain system. This is also considered as the human error caused by the sharing of the account
information.
Data breaches can arise from within and outside the business. Business has threats of data
breach from employees, suppliers or from the outside consultants that have access to the network
or to the internal systems of the company. Moreover, threats can arise due to the security
through the drive-by-downloads when one unintentionally downloads the virus which is brought
up by the compromised web page that takes the advantage of the out of update software or has a
security flaw. Further, it can be caused through the malware attacks by using phishing email
tactics that reveals the user credentials or through the malware infected websites. The following
chart shows the percentage of attack distribution in percentages which has caused the data
breaches in 2018:
In %
Account Hijacking Unknown Malware/PoS Malware
Targetted Attack Vulnerability Malicious Script Injection
DDoS Defacement Brute-Force/ Credential Stuffing
SQLi
Source: (Passeri, 2019)
One of the main cause of data breach is the malicious insider in which the employees
may steal the sensitive information due to the access of the information which can be misused by
them (Irwin, 2019). The sensitive information can be used by the employees who have left the
organization that have the access to the systems and using it maliciously. In certain cases,
employees within the company unknowingly make mistakes in the emailing or the using of
certain system. This is also considered as the human error caused by the sharing of the account
information.
Data breaches can arise from within and outside the business. Business has threats of data
breach from employees, suppliers or from the outside consultants that have access to the network
or to the internal systems of the company. Moreover, threats can arise due to the security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TECHNOLOGY SECURITY 4
vulnerabilities being caused by the exploitation of the information and lack of implementation of
the repair and maintenance system. Further, due to the mistakes or the human errors into the
system can be threat for the business to be indulged into the data breaches (Cheng, Liu, & Yao,
2017). Device used for the business purpose of the business can be the risk factor as it can store
the sensitive information for the access of the corporate credentials which may have the threat of
getting stolen. Also, improper configuration of the devices or the systems in which information
can be stored and gathered can be the threat for the business and can lead to the data breaches.
Consequences of Data Breaches
There can be severe consequences of data breaches and it depends upon the type of data
stolen. Majorly, the companies face the loss of reputation and lack of trust when involved in such
cases of privacy breach. Moreover, it increases the burden of the companies who are involved in
the data breaches through the contractual formalities. As per the study of The Ponemon Institute
in 2018, the average cost for the data breaches is $3.86 million globally and the average cost of
every stolen record or data is $148 in 2018 (Wordpay, 2019). Further, there are direct fine and
penalties when the company found guilty in the undertaking of such acts. Also, when the
business is likely to be using the debit card and credit card for the payment, then the companies
need to bear a certain sum of money as fines as per the regulation of the card network brands.
Due to getting involved into the data breach, the companies face the loss of reputation of
the business in which the companies suffer from the damage to the brand reputation in which
there is difficulty in the getting the revenue. Also, there has been impact on the intellectual
property in which the hackers particularly target the designs and the strategies which can lead to
the loss of intellectual property. Further, the companies having the history of data breaches can
be easily targeted by the hackers which can cause the loss of data and often causes the loss of
reputation of the companies (Hemphill & Longstreet, 2016). Also, the companies might suffer
from the future security costs in which the company has to incur the certain amount of money on
the monitoring of the customer’s data. The companies suffer from the serious consequences of
the data breaches and the safeguarding of the same can be the major goal of the company for
preventing themselves from the negative image. The following table shows the affected
companies which have data breach records:
vulnerabilities being caused by the exploitation of the information and lack of implementation of
the repair and maintenance system. Further, due to the mistakes or the human errors into the
system can be threat for the business to be indulged into the data breaches (Cheng, Liu, & Yao,
2017). Device used for the business purpose of the business can be the risk factor as it can store
the sensitive information for the access of the corporate credentials which may have the threat of
getting stolen. Also, improper configuration of the devices or the systems in which information
can be stored and gathered can be the threat for the business and can lead to the data breaches.
Consequences of Data Breaches
There can be severe consequences of data breaches and it depends upon the type of data
stolen. Majorly, the companies face the loss of reputation and lack of trust when involved in such
cases of privacy breach. Moreover, it increases the burden of the companies who are involved in
the data breaches through the contractual formalities. As per the study of The Ponemon Institute
in 2018, the average cost for the data breaches is $3.86 million globally and the average cost of
every stolen record or data is $148 in 2018 (Wordpay, 2019). Further, there are direct fine and
penalties when the company found guilty in the undertaking of such acts. Also, when the
business is likely to be using the debit card and credit card for the payment, then the companies
need to bear a certain sum of money as fines as per the regulation of the card network brands.
Due to getting involved into the data breach, the companies face the loss of reputation of
the business in which the companies suffer from the damage to the brand reputation in which
there is difficulty in the getting the revenue. Also, there has been impact on the intellectual
property in which the hackers particularly target the designs and the strategies which can lead to
the loss of intellectual property. Further, the companies having the history of data breaches can
be easily targeted by the hackers which can cause the loss of data and often causes the loss of
reputation of the companies (Hemphill & Longstreet, 2016). Also, the companies might suffer
from the future security costs in which the company has to incur the certain amount of money on
the monitoring of the customer’s data. The companies suffer from the serious consequences of
the data breaches and the safeguarding of the same can be the major goal of the company for
preventing themselves from the negative image. The following table shows the affected
companies which have data breach records:

TECHNOLOGY SECURITY 5
Company Accounts Hacked Date of Hack
Yahoo 3 Billion August 2013
Marriott 500 Million 2014-2018
Yahoo 500 Million Late 2014
Adult Friend Finder 412 Million October 2016
My Space 360 Million May 2016
Under Armor 150 Million February 2018
Equifax 145.5 Million July 2017
eBay 145 Million May 2014
Target 110 Million November 2013
Heartland Payment
System
100+ Million May 2008
Source: (Panda, 2018)
For example, Marriott has been impacted by the data breaches as the huge number of
records were stolen and as a result the company has to bear the losses and also it affected the
good will of the company. As the company was reported to be compromised with the reservation
details of the customers in Starwood property, the company had to bear the severe consequences
and often had to make the enforcement law that can investigate and address the breach in a
proper way (Youn & Winsor, 2018). Further, the company has been facing the data breach
expenses in which the company has incurred $350 million for the breach of 50 million records
(Dignan, 2018).
Further, the Under Armour has reported the data breach of 150 million users through
their application MyFitnessPal. This loss of data includes the emails, username and the hashed
passwords. As a result, the company has seen the loss of shares 3.8 percent after the reporting of
the information being exposed in front of public (Newman, 2018). Moreover, the company has
been using bcrypt hashing which is the strong password and will take a longer time to break
easily.
One of the example of data breaches can be seen from the Facebook which has reported
the unprotected storing of customer’s password that later led the company to face the problems.
Company Accounts Hacked Date of Hack
Yahoo 3 Billion August 2013
Marriott 500 Million 2014-2018
Yahoo 500 Million Late 2014
Adult Friend Finder 412 Million October 2016
My Space 360 Million May 2016
Under Armor 150 Million February 2018
Equifax 145.5 Million July 2017
eBay 145 Million May 2014
Target 110 Million November 2013
Heartland Payment
System
100+ Million May 2008
Source: (Panda, 2018)
For example, Marriott has been impacted by the data breaches as the huge number of
records were stolen and as a result the company has to bear the losses and also it affected the
good will of the company. As the company was reported to be compromised with the reservation
details of the customers in Starwood property, the company had to bear the severe consequences
and often had to make the enforcement law that can investigate and address the breach in a
proper way (Youn & Winsor, 2018). Further, the company has been facing the data breach
expenses in which the company has incurred $350 million for the breach of 50 million records
(Dignan, 2018).
Further, the Under Armour has reported the data breach of 150 million users through
their application MyFitnessPal. This loss of data includes the emails, username and the hashed
passwords. As a result, the company has seen the loss of shares 3.8 percent after the reporting of
the information being exposed in front of public (Newman, 2018). Moreover, the company has
been using bcrypt hashing which is the strong password and will take a longer time to break
easily.
One of the example of data breaches can be seen from the Facebook which has reported
the unprotected storing of customer’s password that later led the company to face the problems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
TECHNOLOGY SECURITY 6
The company had made the user’s passwords unencrypted that later led to the stealing of data
(Hern, 2019). This incident created a lot of conflicts with others and also lead to downfall into
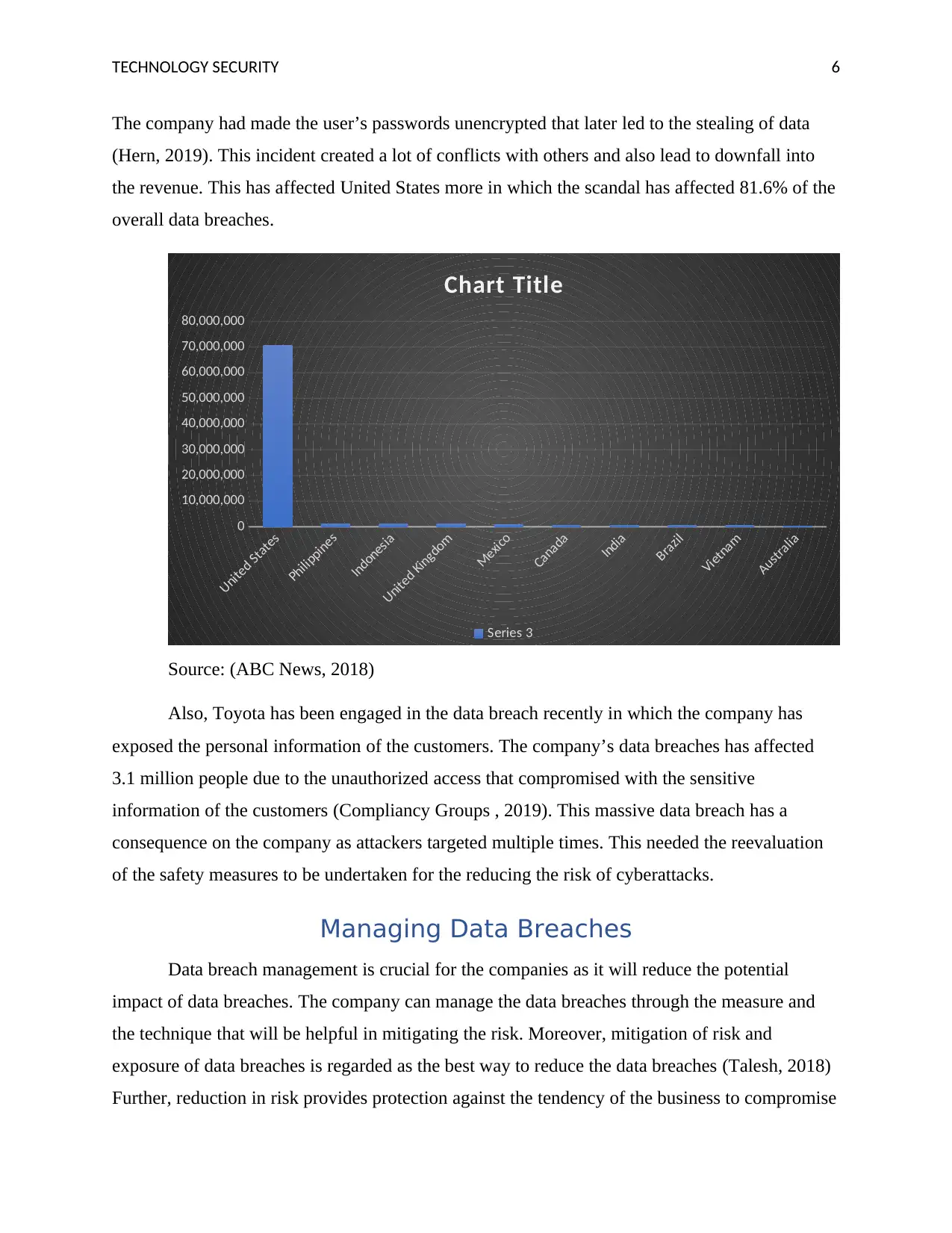
the revenue. This has affected United States more in which the scandal has affected 81.6% of the
overall data breaches.
United States
Philippines
Indonesia
United Kingdom
Mexico
Canada
India
Brazil
Vietnam
Australia
0
10,000,000
20,000,000
30,000,000
40,000,000
50,000,000
60,000,000
70,000,000
80,000,000
Chart Title
Series 3
Source: (ABC News, 2018)
Also, Toyota has been engaged in the data breach recently in which the company has
exposed the personal information of the customers. The company’s data breaches has affected
3.1 million people due to the unauthorized access that compromised with the sensitive
information of the customers (Compliancy Groups , 2019). This massive data breach has a
consequence on the company as attackers targeted multiple times. This needed the reevaluation
of the safety measures to be undertaken for the reducing the risk of cyberattacks.
Managing Data Breaches
Data breach management is crucial for the companies as it will reduce the potential
impact of data breaches. The company can manage the data breaches through the measure and
the technique that will be helpful in mitigating the risk. Moreover, mitigation of risk and
exposure of data breaches is regarded as the best way to reduce the data breaches (Talesh, 2018)
Further, reduction in risk provides protection against the tendency of the business to compromise
The company had made the user’s passwords unencrypted that later led to the stealing of data
(Hern, 2019). This incident created a lot of conflicts with others and also lead to downfall into
the revenue. This has affected United States more in which the scandal has affected 81.6% of the
overall data breaches.
United States
Philippines
Indonesia
United Kingdom
Mexico
Canada
India
Brazil
Vietnam
Australia
0
10,000,000
20,000,000
30,000,000
40,000,000
50,000,000
60,000,000
70,000,000
80,000,000
Chart Title
Series 3
Source: (ABC News, 2018)
Also, Toyota has been engaged in the data breach recently in which the company has
exposed the personal information of the customers. The company’s data breaches has affected
3.1 million people due to the unauthorized access that compromised with the sensitive
information of the customers (Compliancy Groups , 2019). This massive data breach has a
consequence on the company as attackers targeted multiple times. This needed the reevaluation
of the safety measures to be undertaken for the reducing the risk of cyberattacks.
Managing Data Breaches
Data breach management is crucial for the companies as it will reduce the potential
impact of data breaches. The company can manage the data breaches through the measure and
the technique that will be helpful in mitigating the risk. Moreover, mitigation of risk and
exposure of data breaches is regarded as the best way to reduce the data breaches (Talesh, 2018)
Further, reduction in risk provides protection against the tendency of the business to compromise
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TECHNOLOGY SECURITY 7
the data and the exposure is protects the company from the consequences of data breaches.
Security measures include the monitoring of the products or services relating to security
regularly and keeping them up to date. Specifically, the companies can manage the data breaches
through the monitoring of the inbound and outbound traffic within the website and also take the
pre-emptive actions for the potential threats. Moreover, the companies can make the monitoring
for the abnormal network activities (Brown, 2016). The companies can use the real-time
intrusion software for the detection of the unauthorized user activities on the network and attacks
of the hackers.
Further, the companies can use the security cameras for the monitoring of the secured
areas such as server rooms and the data centers. This can prevent the tendency of heavy losses
caused in the data breach. Further, the companies can make the data breach management plan
which is based on the needs of the company and its processes. This can include the reporting of
the data breaches through suspecting and confirming of the data breach. The employee of the
companies must be trained and should be aware of process of reporting of data breaches weather
they are real time or previously made (Corti, Van den Eynden, Bishop, & Woollard, 2019). The
companies then make the assessment and management of the data breach through the facilitation
of roles and responsibilities. Further, there should be proper planning of the prevention against
the data breaches. This can include the management of the plan for the further reduction of the
breach made. This can make the management of potential risks and assessing them through the
continued remedial efforts.
Moreover, data breach is the important issue in IT security that can be managed through
the training of the employees regarding the cybersecurity. Further, the company should give
special importance to the sensitive data that can harm the storage through the disposing of
irrelevant data. Furthermore, the companies should set strong passwords and encrypt the data.
There should be timely monitoring of data that can cause the misuse of the data. This proper
monitoring must consist of the tracking of the data that can make reduce the exploitation of the
data. The precautions also include the system access which should be given to the relevant
professionals and departments (Carter & Hartridge, 2018). Additionally, the systems should be
checked accordingly in order to identify that they are properly up to date so that the website
vulnerabilities are checked and being checked in a regular time period. Two-factor authentication
the data and the exposure is protects the company from the consequences of data breaches.
Security measures include the monitoring of the products or services relating to security
regularly and keeping them up to date. Specifically, the companies can manage the data breaches
through the monitoring of the inbound and outbound traffic within the website and also take the
pre-emptive actions for the potential threats. Moreover, the companies can make the monitoring
for the abnormal network activities (Brown, 2016). The companies can use the real-time
intrusion software for the detection of the unauthorized user activities on the network and attacks
of the hackers.
Further, the companies can use the security cameras for the monitoring of the secured
areas such as server rooms and the data centers. This can prevent the tendency of heavy losses
caused in the data breach. Further, the companies can make the data breach management plan
which is based on the needs of the company and its processes. This can include the reporting of
the data breaches through suspecting and confirming of the data breach. The employee of the
companies must be trained and should be aware of process of reporting of data breaches weather
they are real time or previously made (Corti, Van den Eynden, Bishop, & Woollard, 2019). The
companies then make the assessment and management of the data breach through the facilitation
of roles and responsibilities. Further, there should be proper planning of the prevention against
the data breaches. This can include the management of the plan for the further reduction of the
breach made. This can make the management of potential risks and assessing them through the
continued remedial efforts.
Moreover, data breach is the important issue in IT security that can be managed through
the training of the employees regarding the cybersecurity. Further, the company should give
special importance to the sensitive data that can harm the storage through the disposing of
irrelevant data. Furthermore, the companies should set strong passwords and encrypt the data.
There should be timely monitoring of data that can cause the misuse of the data. This proper
monitoring must consist of the tracking of the data that can make reduce the exploitation of the
data. The precautions also include the system access which should be given to the relevant
professionals and departments (Carter & Hartridge, 2018). Additionally, the systems should be
checked accordingly in order to identify that they are properly up to date so that the website
vulnerabilities are checked and being checked in a regular time period. Two-factor authentication

TECHNOLOGY SECURITY 8
is the best way to deal with the security systems and avoid the data breaches for a longer time
period.
Recommendation
From the above analysis, it can be recommended that business must ensure the safe
access of consumer details and maintain the system of security that can maintain the privacy of
confidential information (Talesh, 2018). Further, business must be aware of the consequences of
data breaches and various tools for the security of the information. It can be recommended that
the business must ensure that there are security systems for the reduction of the vulnerabilities of
data risk and threats. The companies should bear the full responsibility of the data breaches and
make the forward steps for the reduction of the future vulnerabilities. Also, the companies should
make the improvisation in the external and internal process and make suitable security checks
that can make the security of information stronger and later the companies should ensure that the
proper security checks are made for the safe storing and transmitting of confidential information
and avoiding data breaches (Brown, 2016).
Conclusion
Conclusively, it can be said that cyber security is crucial for the companies as it has a
direct impact on the goodwill and reputation of the companies. Data breaches is one of the key
issues to be faced by today’s organization and can impact them severely. This is considered to be
the important element of cyber security in which the companies report the data breaches when
they are targeted by the attacker. Here, the paper has discussed the threats and consequences of
data breaches which can affect the productivity of the companies. Further, the paper has
discussed the possible management plan of the data breaches through the installation of security
systems and also the secured use of personal information of the customers being made into the
companies.
is the best way to deal with the security systems and avoid the data breaches for a longer time
period.
Recommendation
From the above analysis, it can be recommended that business must ensure the safe
access of consumer details and maintain the system of security that can maintain the privacy of
confidential information (Talesh, 2018). Further, business must be aware of the consequences of
data breaches and various tools for the security of the information. It can be recommended that
the business must ensure that there are security systems for the reduction of the vulnerabilities of
data risk and threats. The companies should bear the full responsibility of the data breaches and
make the forward steps for the reduction of the future vulnerabilities. Also, the companies should
make the improvisation in the external and internal process and make suitable security checks
that can make the security of information stronger and later the companies should ensure that the
proper security checks are made for the safe storing and transmitting of confidential information
and avoiding data breaches (Brown, 2016).
Conclusion
Conclusively, it can be said that cyber security is crucial for the companies as it has a
direct impact on the goodwill and reputation of the companies. Data breaches is one of the key
issues to be faced by today’s organization and can impact them severely. This is considered to be
the important element of cyber security in which the companies report the data breaches when
they are targeted by the attacker. Here, the paper has discussed the threats and consequences of
data breaches which can affect the productivity of the companies. Further, the paper has
discussed the possible management plan of the data breaches through the installation of security
systems and also the secured use of personal information of the customers being made into the
companies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TECHNOLOGY SECURITY 9
References
ABC News. (2018, April 5). Facebook's graph of people affected by the Cambridge Analytica
scandal. Retrieved February 15, 2020, from ABC News:
https://www.abc.net.au/news/2018-04-05/facebooks-graph-of-people-affected-by-the-
cambridge-analytica/9621048
Ahson, S., & Ilyas, M. (2017). RFID handbook: applications, technology, security, and privacy.
CRC Press.
Armerding , T. (2018, December 20). The 18 biggest data breaches of the 21st century.
Retrieved February 14, 2020, from CSO:
https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-
century.html
Brown, H. (2016). After the data breach: Managing the crisis and mitigating the impact. Journal
of business continuity & emergency planning, 9(4), 317-328.
Buczak, A., & Guven, E. (2015). A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications surveys & tutorials, 18(2),
1153-1176.
Cakebread, C. (2017, October 5). Other web service data breaches pale in comparison to the 3-
billion user Yahoo hack. Retrieved February 15, 2020, from Business Insider:
https://www.businessinsider.in/tech/other-web-service-data-breaches-pale-in-
comparison-to-the-3-billion-user-yahoo-hack/articleshow/60948055.cms
Carter, D., & Hartridge, S. (2018). Managing Data Breaches and New Mandatory Disclosure
Requirements in Medical Practice. Medical Journal of Australia.
Cheng, L., Liu, F., & Yao, D. (2017). Enterprise data breach: causes, challenges, prevention, and
future directions. Wiley Interdisciplinary Reviews: Data Mining and Knowledge
Discovery, 7(5), e1211.
References
ABC News. (2018, April 5). Facebook's graph of people affected by the Cambridge Analytica
scandal. Retrieved February 15, 2020, from ABC News:
https://www.abc.net.au/news/2018-04-05/facebooks-graph-of-people-affected-by-the-
cambridge-analytica/9621048
Ahson, S., & Ilyas, M. (2017). RFID handbook: applications, technology, security, and privacy.
CRC Press.
Armerding , T. (2018, December 20). The 18 biggest data breaches of the 21st century.
Retrieved February 14, 2020, from CSO:
https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-
century.html
Brown, H. (2016). After the data breach: Managing the crisis and mitigating the impact. Journal
of business continuity & emergency planning, 9(4), 317-328.
Buczak, A., & Guven, E. (2015). A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications surveys & tutorials, 18(2),
1153-1176.
Cakebread, C. (2017, October 5). Other web service data breaches pale in comparison to the 3-
billion user Yahoo hack. Retrieved February 15, 2020, from Business Insider:
https://www.businessinsider.in/tech/other-web-service-data-breaches-pale-in-
comparison-to-the-3-billion-user-yahoo-hack/articleshow/60948055.cms
Carter, D., & Hartridge, S. (2018). Managing Data Breaches and New Mandatory Disclosure
Requirements in Medical Practice. Medical Journal of Australia.
Cheng, L., Liu, F., & Yao, D. (2017). Enterprise data breach: causes, challenges, prevention, and
future directions. Wiley Interdisciplinary Reviews: Data Mining and Knowledge
Discovery, 7(5), e1211.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TECHNOLOGY SECURITY 10
Compliancy Groups . (2019, December 16). Toyota Data Breach Affects Millions. Retrieved
February 14, 2020, from Compliancy Groups: https://compliancy-group.com/toyota-data-
breach-affects-millions/
Corti, L., Van den Eynden, V., Bishop, L., & Woollard, M. (2019). Managing and sharing
research data: a guide to good practice. SAGE Publications Limited.
Dignan, L. (2018, November 30). Marriott faces massive data breach expenses even with
cybersecurity insurance. Retrieved February 15, 2020, from ZD Net:
https://www.zdnet.com/article/marriott-faces-massive-data-breach-expenses-even-with-
cybersecurity-insurance/
Hemphill, T., & Longstreet, P. (2016). Financial data breaches in the US retail economy:
Restoring confidence in information technology security standards. Technology in
Society, 44, 30-38.
Hern, A. (2019, March 21). Facebook stored hundreds of millions of passwords unprotected.
Retrieved February 14, 2020, from The Gaurdian:
https://www.theguardian.com/technology/2019/mar/21/facebook-admits-passwords-
unprotected
Irwin, L. (2019, April 9). The most common causes of data breaches and how you can spot them.
Retrieved February 14, 2020, from IT Governance:
https://www.itgovernance.eu/blog/en/the-most-common-causes-of-data-breaches-and-
how-you-can-spot-them
Manworren, N., Letwat, J., & Daily, O. (2016). Why you should care about the Target data
breach. Business Horizons, 59(3), 257-266.
Newman, L. (2018, March 30). The Under Armour Hack Was Even Worse Than It Had To Be.
Retrieved February 14, 2020, from Wired: https://www.wired.com/story/under-armour-
myfitnesspal-hack-password-hashing/
Panda. (2018, December 3). Marriott International, protagonist of the second largest data
breach of all time. Retrieved February 15, 2020, from Panda:
https://www.pandasecurity.com/mediacenter/security/marriott-massive-data-breach/
Compliancy Groups . (2019, December 16). Toyota Data Breach Affects Millions. Retrieved
February 14, 2020, from Compliancy Groups: https://compliancy-group.com/toyota-data-
breach-affects-millions/
Corti, L., Van den Eynden, V., Bishop, L., & Woollard, M. (2019). Managing and sharing
research data: a guide to good practice. SAGE Publications Limited.
Dignan, L. (2018, November 30). Marriott faces massive data breach expenses even with
cybersecurity insurance. Retrieved February 15, 2020, from ZD Net:
https://www.zdnet.com/article/marriott-faces-massive-data-breach-expenses-even-with-
cybersecurity-insurance/
Hemphill, T., & Longstreet, P. (2016). Financial data breaches in the US retail economy:
Restoring confidence in information technology security standards. Technology in
Society, 44, 30-38.
Hern, A. (2019, March 21). Facebook stored hundreds of millions of passwords unprotected.
Retrieved February 14, 2020, from The Gaurdian:
https://www.theguardian.com/technology/2019/mar/21/facebook-admits-passwords-
unprotected
Irwin, L. (2019, April 9). The most common causes of data breaches and how you can spot them.
Retrieved February 14, 2020, from IT Governance:
https://www.itgovernance.eu/blog/en/the-most-common-causes-of-data-breaches-and-
how-you-can-spot-them
Manworren, N., Letwat, J., & Daily, O. (2016). Why you should care about the Target data
breach. Business Horizons, 59(3), 257-266.
Newman, L. (2018, March 30). The Under Armour Hack Was Even Worse Than It Had To Be.
Retrieved February 14, 2020, from Wired: https://www.wired.com/story/under-armour-
myfitnesspal-hack-password-hashing/
Panda. (2018, December 3). Marriott International, protagonist of the second largest data
breach of all time. Retrieved February 15, 2020, from Panda:
https://www.pandasecurity.com/mediacenter/security/marriott-massive-data-breach/

TECHNOLOGY SECURITY 11
Passeri, P. (2019, January 15). 2018: A Year of Cyber Attacks. Retrieved February 20, 2020,
from hack mageddon: https://www.hackmageddon.com/2019/01/15/2018-a-year-of-
cyber-attacks/
Talesh, S. (2018). Data breach, privacy, and cyber insurance: How insurance companies act as
“compliance managers” for businesses. Law & Social Inquiry, 43(2), 417-440.
Telford, T., & Timberg, C. (2018, November 30). Marriott discloses massive data breach
affecting up to 500 million guests. Retrieved February 14, 2020, from The Washington
Post: https://www.washingtonpost.com/business/2018/11/30/marriott-discloses-massive-
data-breach-impacting-million-guests/
Wheatley, S., Maillart, T., & Sornette, D. (2016). The extreme risk of personal data breaches and
the erosion of privacy. The European Physical Journal B, 89(1), 1-12.
Wordpay. (2019, June 10). How the consequences of a data breach threaten small businesses.
Retrieved February 11, 2020, from Wordpay: https://www.worldpay.com/en-us/insights-
hub/article/how-the-consequences-of-a-data-breach-threaten-small-businesses
Youn, S., & Winsor, M. (2018, November 30). Marriott says data breach may affect up to 500
million Starwood hotel guests. Retrieved February 14, 2020, from ABC News:
https://abcnews.go.com/Business/marriott-data-breach-affect-500-million-starwood-
hotel/story?id=59517801
Passeri, P. (2019, January 15). 2018: A Year of Cyber Attacks. Retrieved February 20, 2020,
from hack mageddon: https://www.hackmageddon.com/2019/01/15/2018-a-year-of-
cyber-attacks/
Talesh, S. (2018). Data breach, privacy, and cyber insurance: How insurance companies act as
“compliance managers” for businesses. Law & Social Inquiry, 43(2), 417-440.
Telford, T., & Timberg, C. (2018, November 30). Marriott discloses massive data breach
affecting up to 500 million guests. Retrieved February 14, 2020, from The Washington
Post: https://www.washingtonpost.com/business/2018/11/30/marriott-discloses-massive-
data-breach-impacting-million-guests/
Wheatley, S., Maillart, T., & Sornette, D. (2016). The extreme risk of personal data breaches and
the erosion of privacy. The European Physical Journal B, 89(1), 1-12.
Wordpay. (2019, June 10). How the consequences of a data breach threaten small businesses.
Retrieved February 11, 2020, from Wordpay: https://www.worldpay.com/en-us/insights-
hub/article/how-the-consequences-of-a-data-breach-threaten-small-businesses
Youn, S., & Winsor, M. (2018, November 30). Marriott says data breach may affect up to 500
million Starwood hotel guests. Retrieved February 14, 2020, from ABC News:
https://abcnews.go.com/Business/marriott-data-breach-affect-500-million-starwood-
hotel/story?id=59517801
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





