Advanced Networking Engineering (Data Centre Planning Proposal)
VerifiedAdded on 2021/05/31
|21
|5948
|66
Project
AI Summary
This project presents a comprehensive proposal for data center planning tailored for GlobalNets Pty Ltd. It meticulously addresses key aspects including site selection, utility considerations, building design, and security measures. The proposal outlines detailed specifications and standards for building a secure and efficient data center, emphasizing the importance of factors such as site safety, redundant power grids, and robust security systems. Furthermore, the project delves into the architecture and topology of the data center, advocating for a multi-tier model and a Fat Tree-based architecture to ensure scalability and flexibility in deployment. It also covers the integration of the data center with various branches and components of the organization. Additionally, the project touches upon the management of big data databases, distributed file storage, and the selection of appropriate tools and software for managing a large number of servers and equipment. The proposal is designed to provide GlobalNets with a strategic roadmap for establishing a state-of-the-art data center capable of delivering a wide range of network services in the cloud.

Running head: ADVANCED NETWORKING ENGINEERING 1
Advanced Networking Engineering (Call for Proposals for Data Centre Planning)
Name:
Institution Affiliation:
Advanced Networking Engineering (Call for Proposals for Data Centre Planning)
Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADVANCED NETWORKING ENGINEERING 2
Executive Summary
In this proposal it is on the call for the Proposals for the Data Centre Planning. In this proposal it is to plan
Data Centre for the General Data and Network services for the GlobalNets Pty Ltd. Through this proposal it
will enable GlobalNets organization to follow it in the building of the actual and then operate a data centre to
numerous network services in the cloud. The aspects which will be discussed are on; specifications and the
standards to build on the data centre, architecture and the topology to the data centre and its integration to all
the branches, offices as well as other components of the organizations which are to be served. Other aspects
discussed in the proposal are databases for the big data, distributed file storage as well as its management.
The research would also mention on the mechanisms, tools and the potential software for the management to
numerous servers and other equipment.
Contents
Executive Summary
In this proposal it is on the call for the Proposals for the Data Centre Planning. In this proposal it is to plan
Data Centre for the General Data and Network services for the GlobalNets Pty Ltd. Through this proposal it
will enable GlobalNets organization to follow it in the building of the actual and then operate a data centre to
numerous network services in the cloud. The aspects which will be discussed are on; specifications and the
standards to build on the data centre, architecture and the topology to the data centre and its integration to all
the branches, offices as well as other components of the organizations which are to be served. Other aspects
discussed in the proposal are databases for the big data, distributed file storage as well as its management.
The research would also mention on the mechanisms, tools and the potential software for the management to
numerous servers and other equipment.
Contents

ADVANCED NETWORKING ENGINEERING 3
Introduction...................................................................................................................................................................... 4
Background of the project.........................................................................................................................................4
General specifications and standard for building the data centre......................................................................................4
Architecture and topology of data centre and integration with all branches and other components served.......................7
Databases of big data, distributed file storage and management.....................................................................................10
Mechanisms, tools and potential software for management of hundred of servers and other equipment........................13
Conclusion...................................................................................................................................................................... 14
References...................................................................................................................................................................... 15
Appendix........................................................................................................................................................................ 17
Personal Reflections...............................................................................................................................................17
CV............................................................................................................................................................................ 1
Introduction...................................................................................................................................................................... 4
Background of the project.........................................................................................................................................4
General specifications and standard for building the data centre......................................................................................4
Architecture and topology of data centre and integration with all branches and other components served.......................7
Databases of big data, distributed file storage and management.....................................................................................10
Mechanisms, tools and potential software for management of hundred of servers and other equipment........................13
Conclusion...................................................................................................................................................................... 14
References...................................................................................................................................................................... 15
Appendix........................................................................................................................................................................ 17
Personal Reflections...............................................................................................................................................17
CV............................................................................................................................................................................ 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ADVANCED NETWORKING ENGINEERING 4
Introduction
Background of the project
In this report, it is about call of the proposal for the Data Centre planning. In this proposal it examines the
planning of the Data Centre for the General Data and Network Services GlobalNets Pty Ltd. This
organization has been tasked with the objective to build and manage a data center for an IT organization. In
this proposal it would enable the GlobalNets organization to build as well as operate such data centre to the
variety of the network services in the cloud (Coakley, Raftery & Keane, 2014). The aspects which would be
considered in this research are specifications and the standards to build on the data centre, architecture and
the topology to the data centre and its integration to all the branches, offices as well as other components of
the organizations which are to be served (Aljohani, King & Narayanaswamy, 2016). Additionally, the
research would examine on the databases for the big data, distributed file storage as well as its management.
The research would also mention on the mechanisms, tools and the potential software for the management to
numerous servers and other equipment.
General specifications and standard for building the data centre
To build a secure data centre there certain specifications and standards which should be met; the following
are these requirements.
Site selection
This is the locality to in which the facility would be located. It must be selected very carefully by GlobalNets
organization to get the best mix of the ideal features (Aljohani, King & Narayanaswamy, 2016). The site
needs to be safe area which is not subjected any natural environmental risk such as the flood planes or the
areas which are subjected to the landslides. Based on the case study GlobalNets aims to building it to the
regional town which is about one hundred kilometers away from the major capital city. The site selected in
the regional town need to have adequate drainage and the runoff path so that the localized floods do not take
place during the heavy rains or the snow melts (Bertoldi, Avgerinou & Castellazzi, 2017). In case the facility
would be below the grade spaces it is important to make sure that there is a perk test which has been done
Introduction
Background of the project
In this report, it is about call of the proposal for the Data Centre planning. In this proposal it examines the
planning of the Data Centre for the General Data and Network Services GlobalNets Pty Ltd. This
organization has been tasked with the objective to build and manage a data center for an IT organization. In
this proposal it would enable the GlobalNets organization to build as well as operate such data centre to the
variety of the network services in the cloud (Coakley, Raftery & Keane, 2014). The aspects which would be
considered in this research are specifications and the standards to build on the data centre, architecture and
the topology to the data centre and its integration to all the branches, offices as well as other components of
the organizations which are to be served (Aljohani, King & Narayanaswamy, 2016). Additionally, the
research would examine on the databases for the big data, distributed file storage as well as its management.
The research would also mention on the mechanisms, tools and the potential software for the management to
numerous servers and other equipment.
General specifications and standard for building the data centre
To build a secure data centre there certain specifications and standards which should be met; the following
are these requirements.
Site selection
This is the locality to in which the facility would be located. It must be selected very carefully by GlobalNets
organization to get the best mix of the ideal features (Aljohani, King & Narayanaswamy, 2016). The site
needs to be safe area which is not subjected any natural environmental risk such as the flood planes or the
areas which are subjected to the landslides. Based on the case study GlobalNets aims to building it to the
regional town which is about one hundred kilometers away from the major capital city. The site selected in
the regional town need to have adequate drainage and the runoff path so that the localized floods do not take
place during the heavy rains or the snow melts (Bertoldi, Avgerinou & Castellazzi, 2017). In case the facility
would be below the grade spaces it is important to make sure that there is a perk test which has been done
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADVANCED NETWORKING ENGINEERING 5
(Bertoldi, Avgerinou & Castellazzi, 2017). The protected data center needs to be constructed in the quiet
areas which have low surface traffic, but together it must have multiple access roads into the area. It must be
innocuous and unassuming.
Utilities
A site which is good is usually located in an area where there is availability to the fiber from numerous
providers as well as redundant power grids (Bittner, Schietinger, Schroth & Weinkopf, 2017). When this is
done it would be less likely for this organization to rely on the backup generators if the facility is drawing
power from the multiple grids. Given that the organization has the option to choose where the data center
would be located they need to look at the historical data from the local power providers (Bertoldi, Avgerinou
& Castellazzi, 2017). These are all not created equally. The aspect of the fiber access would be more
dependable as well as cost effective should they have the options from the numerous providers. It is also
important that the organization looks close to the municipal services such as the fire and the police (Coakley,
Raftery & Keane, 2014). However, it is hopeful that the organization might not need them but if they do they
would respond on time on their issue.
Building design
The building design should be located to the center of the site and needs to be clear from any specific
unimpeded views to all the sides. The extreme critical installations have to be fenced. It is important that the
organization should not advertise on the nature of their facility. False name to the building could help to
camouflage their operations (Bittner, Schietinger, Schroth & Weinkopf, 2017). The design of the data center
needs to be based on the durable materials which could exceed the normal design loads (Coakley, Raftery &
Keane, 2014). On the roofs as well as the materials they should be chosen and designed in order to refrain
from not only the water but also the winds, ponding, snow loads as well as the uplift (Coakley, Raftery &
Keane, 2014).
Mechanism/ Electrical systems
(Bertoldi, Avgerinou & Castellazzi, 2017). The protected data center needs to be constructed in the quiet
areas which have low surface traffic, but together it must have multiple access roads into the area. It must be
innocuous and unassuming.
Utilities
A site which is good is usually located in an area where there is availability to the fiber from numerous
providers as well as redundant power grids (Bittner, Schietinger, Schroth & Weinkopf, 2017). When this is
done it would be less likely for this organization to rely on the backup generators if the facility is drawing
power from the multiple grids. Given that the organization has the option to choose where the data center
would be located they need to look at the historical data from the local power providers (Bertoldi, Avgerinou
& Castellazzi, 2017). These are all not created equally. The aspect of the fiber access would be more
dependable as well as cost effective should they have the options from the numerous providers. It is also
important that the organization looks close to the municipal services such as the fire and the police (Coakley,
Raftery & Keane, 2014). However, it is hopeful that the organization might not need them but if they do they
would respond on time on their issue.
Building design
The building design should be located to the center of the site and needs to be clear from any specific
unimpeded views to all the sides. The extreme critical installations have to be fenced. It is important that the
organization should not advertise on the nature of their facility. False name to the building could help to
camouflage their operations (Bittner, Schietinger, Schroth & Weinkopf, 2017). The design of the data center
needs to be based on the durable materials which could exceed the normal design loads (Coakley, Raftery &
Keane, 2014). On the roofs as well as the materials they should be chosen and designed in order to refrain
from not only the water but also the winds, ponding, snow loads as well as the uplift (Coakley, Raftery &
Keane, 2014).
Mechanism/ Electrical systems

ADVANCED NETWORKING ENGINEERING 6
The data center needs to be best with dual electrical service feeds and distribution from the numerous energy
grid sub-stations (Baghdadi et. al 2015). It is important for the organization to protect on their equipments
with the use of the power conditioning for the purposes of the surges, brownouts and the blackouts along
with the high energy transients (Coakley, Raftery & Keane, 2014). It is important for the electrical power
design to have isolated end point distribution in order to address on the harmonic loads as well as the surges
which could be caused by the internal equipments (Eastman, 2018). It is crucial for the GlobalNets
organization to avoid the ground loops to their power design (Baghdadi et. al 2015). This might happen in
case they ties to the grounds building equipments as well as the computers together (Di Rocco, Di Ruscio,
Iovino & Pierantonio, 2015). The surges which are from the equipment startup could back the feed to the
ground wire leg and perhaps damage on the sensitive gears such as the computers.
In the computer rooms it should have numerous pieces of the electrical equipment which is often used. You
will need to provide an access floor in order to create an interstitial holding place to the cords as well as the
cables which are required for the system (Di Rocco, Di Ruscio, Iovino & Pierantonio, 2015). The access
rooms are usually constructed of 24 inch by 24 inch panels on the frame. The panels are usually interchanged
so they allow the wire as well as the cable changes without the disrupting on the center for the operations.
Facility security/Monitoring
When it comes to monitoring of the environmental system, there is need to equip the data center with
numerous security systems (Eastman, 2018). There should be control of the passage into and out of the
facility through use of a card or the biometric access systems. It is also important to monitor all day long on
the activities which have been logged onsite as well as through any remote location (Eastman, 2018). The
alarm need to specify the exact location to the fault to that there is no wastage of the time especially in
searching on the source of an issue if it arises. The workers should only have an access to the areas which are
required through particular duties (Coakley, Raftery & Keane, 2014). All the visitors who have been
appointed are usually equipped before they are allowing the escorted access only to the locations which are
necessary.
The data center needs to be best with dual electrical service feeds and distribution from the numerous energy
grid sub-stations (Baghdadi et. al 2015). It is important for the organization to protect on their equipments
with the use of the power conditioning for the purposes of the surges, brownouts and the blackouts along
with the high energy transients (Coakley, Raftery & Keane, 2014). It is important for the electrical power
design to have isolated end point distribution in order to address on the harmonic loads as well as the surges
which could be caused by the internal equipments (Eastman, 2018). It is crucial for the GlobalNets
organization to avoid the ground loops to their power design (Baghdadi et. al 2015). This might happen in
case they ties to the grounds building equipments as well as the computers together (Di Rocco, Di Ruscio,
Iovino & Pierantonio, 2015). The surges which are from the equipment startup could back the feed to the
ground wire leg and perhaps damage on the sensitive gears such as the computers.
In the computer rooms it should have numerous pieces of the electrical equipment which is often used. You
will need to provide an access floor in order to create an interstitial holding place to the cords as well as the
cables which are required for the system (Di Rocco, Di Ruscio, Iovino & Pierantonio, 2015). The access
rooms are usually constructed of 24 inch by 24 inch panels on the frame. The panels are usually interchanged
so they allow the wire as well as the cable changes without the disrupting on the center for the operations.
Facility security/Monitoring
When it comes to monitoring of the environmental system, there is need to equip the data center with
numerous security systems (Eastman, 2018). There should be control of the passage into and out of the
facility through use of a card or the biometric access systems. It is also important to monitor all day long on
the activities which have been logged onsite as well as through any remote location (Eastman, 2018). The
alarm need to specify the exact location to the fault to that there is no wastage of the time especially in
searching on the source of an issue if it arises. The workers should only have an access to the areas which are
required through particular duties (Coakley, Raftery & Keane, 2014). All the visitors who have been
appointed are usually equipped before they are allowing the escorted access only to the locations which are
necessary.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ADVANCED NETWORKING ENGINEERING 7
Construction Monitoring
The monitoring and access control to the data center facility must start in the beginning whenever the
construction is done before the foundations are even excavated . This really is important to the critical
business such as this IT firm (Bertoldi, Avgerinou & Castellazzi, 2017). It is important to ensure that all the
construction has been monitored and the site has been secured completely even at night. In case the
organization feels they are at risk, the building should be swept to the various stages of the construction for
any devices which could be implanted.
Architecture and topology of data centre and integration with all branches and other components
served.
GlobalNets organization aims at building a new data centre to provide integrated and cloud services to the IT
organization (Eastman, 2018). The data center is a haven for the computational power, storage space and
programs which are important to support on this enterprise business. The infrastructure of the data centre is
the central to the IT architecture, from which the content continues to be sourced. Proper planning facets of
the data center infrastructure design are vital along with the performance, resiliency as well as scalability
(Flucker, Tozer & Whitehead, 2018). The crucial aspect to the data center design is the aspect of the
flexibility in deployment as well as supporting on the new services. The data center network architecture is
designed on the proven layered approach which has been tested and improved in the past years to some of the
largest data center implementation in the globe.
In this organization it will utilize the multi-tier model which has been dominated by the HTTP-based
application to the multi-tier approach (Bittner, Schietinger, Schroth & Weinkopf, 2017). The multi-tier
incorporates the web, application as well as the database tiers of the servers. Presently, many of the web
applications are usually built as the multi-tier programs ( Manvi & Shyam , 2014 ) . They use software which
could run as the separate processes to the same machine utilizing the intercrosses communication or maybe
on different machines with the communications over the coverage. GlobalNets organization aims utilizing the
Construction Monitoring
The monitoring and access control to the data center facility must start in the beginning whenever the
construction is done before the foundations are even excavated . This really is important to the critical
business such as this IT firm (Bertoldi, Avgerinou & Castellazzi, 2017). It is important to ensure that all the
construction has been monitored and the site has been secured completely even at night. In case the
organization feels they are at risk, the building should be swept to the various stages of the construction for
any devices which could be implanted.
Architecture and topology of data centre and integration with all branches and other components
served.
GlobalNets organization aims at building a new data centre to provide integrated and cloud services to the IT
organization (Eastman, 2018). The data center is a haven for the computational power, storage space and
programs which are important to support on this enterprise business. The infrastructure of the data centre is
the central to the IT architecture, from which the content continues to be sourced. Proper planning facets of
the data center infrastructure design are vital along with the performance, resiliency as well as scalability
(Flucker, Tozer & Whitehead, 2018). The crucial aspect to the data center design is the aspect of the
flexibility in deployment as well as supporting on the new services. The data center network architecture is
designed on the proven layered approach which has been tested and improved in the past years to some of the
largest data center implementation in the globe.
In this organization it will utilize the multi-tier model which has been dominated by the HTTP-based
application to the multi-tier approach (Bittner, Schietinger, Schroth & Weinkopf, 2017). The multi-tier
incorporates the web, application as well as the database tiers of the servers. Presently, many of the web
applications are usually built as the multi-tier programs ( Manvi & Shyam , 2014 ) . They use software which
could run as the separate processes to the same machine utilizing the intercrosses communication or maybe
on different machines with the communications over the coverage. GlobalNets organization aims utilizing the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADVANCED NETWORKING ENGINEERING 8
cloud services in their integration with other companies therefore the architecture they would use is the Tree
DCN to their data center (Manvi & Shyam, 2014).
Fat Tree-based Architecture
This data center network is usually composed by three years of the switches. On the architecture the top layer
as the root it is thought to be the core layer (Peng et .al 2015). On the middle layer it really is regarded as the
aggregation layer, and at the bottom it is known as the access layer. On the higher layer the devices usually
possess as the higher performance as well as value (Bittner, Schietinger, Schroth & Weinkopf, 2017). The
core layer is comprised with numerous routers that have equal redundancies when accessing on the external
coverage on just one of the side, or implementing on the external Border Gateway Protocol or even the static
routing protocol and using on the internal network to the other side, or implementing Interior Gateway
Protocol.
Topology architecture
Figure 1: Topology of a fat-tree architecture
There are ranges of switches in the square which are regarded as the Pod. There are K=4 switches to each of
the pod and half of these belong to the edge switches and have are the aggregation switches (Bittner,
Schietinger, Schroth & Weinkopf, 2017). The aggregation switches usually use each of the k/2 ports while
they are connecting to the edge and the core switches. Thus, the maximum number of the servers in this
would be K3/4 and 5K2/4 switches. This architecture in most of the time uses the 10.0.0.0/8 on the private range
cloud services in their integration with other companies therefore the architecture they would use is the Tree
DCN to their data center (Manvi & Shyam, 2014).
Fat Tree-based Architecture
This data center network is usually composed by three years of the switches. On the architecture the top layer
as the root it is thought to be the core layer (Peng et .al 2015). On the middle layer it really is regarded as the
aggregation layer, and at the bottom it is known as the access layer. On the higher layer the devices usually
possess as the higher performance as well as value (Bittner, Schietinger, Schroth & Weinkopf, 2017). The
core layer is comprised with numerous routers that have equal redundancies when accessing on the external
coverage on just one of the side, or implementing on the external Border Gateway Protocol or even the static
routing protocol and using on the internal network to the other side, or implementing Interior Gateway
Protocol.
Topology architecture
Figure 1: Topology of a fat-tree architecture
There are ranges of switches in the square which are regarded as the Pod. There are K=4 switches to each of
the pod and half of these belong to the edge switches and have are the aggregation switches (Bittner,
Schietinger, Schroth & Weinkopf, 2017). The aggregation switches usually use each of the k/2 ports while
they are connecting to the edge and the core switches. Thus, the maximum number of the servers in this
would be K3/4 and 5K2/4 switches. This architecture in most of the time uses the 10.0.0.0/8 on the private range
ADVANCED NETWORKING ENGINEERING 9
setting to the interior DCN address and the format deployed for the switch is 10.pod.switch.1 (Bittner,
Schietinger, Schroth & Weinkopf, 2017). The use of this architecture improves on the cost effectiveness
through deployment of the large number of the low cost switches with the use of the complex connections in
order to replace the expensive as well as more complex switches (Lemoudden & El Ouahidi, (2015). It is also
important to note that the equal number of the links in the various layers usually attains non-blocking
communication amongst the servers, and this aids in reducing on the network bandwidth issues.
Nevertheless, the scale of the fat-tree architecture is restricted by the amount of the devices in the port
(Tselios & Tsolis, 2016). For instance a range of the 48 ports switches usually support a maximum of twenty
seven thousand six hundred and forty eight servers only.
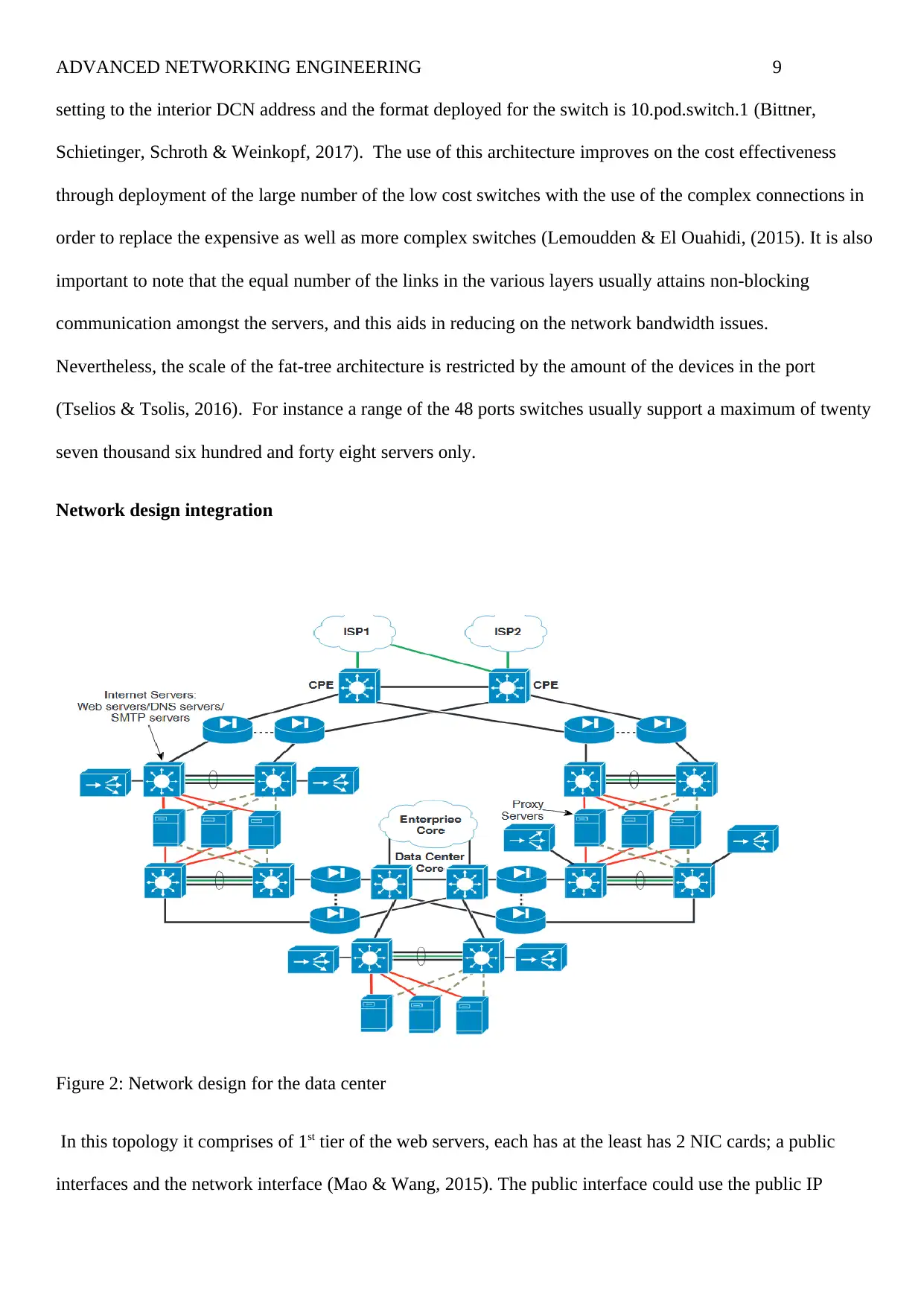
Network design integration
Figure 2: Network design for the data center
In this topology it comprises of 1st tier of the web servers, each has at the least has 2 NIC cards; a public
interfaces and the network interface (Mao & Wang, 2015). The public interface could use the public IP
setting to the interior DCN address and the format deployed for the switch is 10.pod.switch.1 (Bittner,
Schietinger, Schroth & Weinkopf, 2017). The use of this architecture improves on the cost effectiveness
through deployment of the large number of the low cost switches with the use of the complex connections in
order to replace the expensive as well as more complex switches (Lemoudden & El Ouahidi, (2015). It is also
important to note that the equal number of the links in the various layers usually attains non-blocking
communication amongst the servers, and this aids in reducing on the network bandwidth issues.
Nevertheless, the scale of the fat-tree architecture is restricted by the amount of the devices in the port
(Tselios & Tsolis, 2016). For instance a range of the 48 ports switches usually support a maximum of twenty
seven thousand six hundred and forty eight servers only.
Network design integration
Figure 2: Network design for the data center
In this topology it comprises of 1st tier of the web servers, each has at the least has 2 NIC cards; a public
interfaces and the network interface (Mao & Wang, 2015). The public interface could use the public IP
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ADVANCED NETWORKING ENGINEERING 10
address or the private address that has a firewall or even the load balancer hence offering the Network
Address Translation that is NAT (Newcombe, 2017). On the private address interfaces it generally utilizes
the address and provides an usage of the application server through the pair of the firewalls subsequently the
servers of the applications have a minimum of two NICsone for the purpose of the communication with the
server within the web and the other to communication with the database servers (Newcombe, 2017).
This architecture present numerous advantages of the ease of the wire when there is adding a number of the
ports as well as the levels on the switches (Newcombe, 2017). Therefore, GlobalNets Company needs to
utilize this data center architecture to ensure they integrate to all their other branches and the offices so that
they could all be connected to a common center.
Databases of big data, distributed file storage and management
Big data is the fashionable subject which has been used by many individuals in numerous contexts and
without precise semantics ( Newcombe , 2017 ) . For the storage as well as processing of the Big Data there
are 2 functions which are preferred which are scalability and the high speed use of the massive volume of the
data (Newcombe, 2017). There are numerous Big Data databases these are discussed as follows;
NoSQL databases
This is a relatively new kind of the database that has been initiated by the Web companies. Some of the
popular list of them includes the non-relational data stores such as the XML databases (Bittner, Schietinger,
Schroth & Weinkopf, 2017). Besides their typical features such as the simplified data model, rather than the
query driven database design they provide little to no support to the OLTP which is essential to most
organizations applications. Some of the NoSQL databases are usually part to the more complex software
architecture such as the Hadoop stack or perhaps the Big Data Management systems (Funnell, Shi, Costa,
Watts, Ballani, & Thomsen, 2017). DBMS layers usually allow for the manipulating data and these systems
could allow access to the data through the numerous means which are different layers.
NewSQL databases
address or the private address that has a firewall or even the load balancer hence offering the Network
Address Translation that is NAT (Newcombe, 2017). On the private address interfaces it generally utilizes
the address and provides an usage of the application server through the pair of the firewalls subsequently the
servers of the applications have a minimum of two NICsone for the purpose of the communication with the
server within the web and the other to communication with the database servers (Newcombe, 2017).
This architecture present numerous advantages of the ease of the wire when there is adding a number of the
ports as well as the levels on the switches (Newcombe, 2017). Therefore, GlobalNets Company needs to
utilize this data center architecture to ensure they integrate to all their other branches and the offices so that
they could all be connected to a common center.
Databases of big data, distributed file storage and management
Big data is the fashionable subject which has been used by many individuals in numerous contexts and
without precise semantics ( Newcombe , 2017 ) . For the storage as well as processing of the Big Data there
are 2 functions which are preferred which are scalability and the high speed use of the massive volume of the
data (Newcombe, 2017). There are numerous Big Data databases these are discussed as follows;
NoSQL databases
This is a relatively new kind of the database that has been initiated by the Web companies. Some of the
popular list of them includes the non-relational data stores such as the XML databases (Bittner, Schietinger,
Schroth & Weinkopf, 2017). Besides their typical features such as the simplified data model, rather than the
query driven database design they provide little to no support to the OLTP which is essential to most
organizations applications. Some of the NoSQL databases are usually part to the more complex software
architecture such as the Hadoop stack or perhaps the Big Data Management systems (Funnell, Shi, Costa,
Watts, Ballani, & Thomsen, 2017). DBMS layers usually allow for the manipulating data and these systems
could allow access to the data through the numerous means which are different layers.
NewSQL databases
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADVANCED NETWORKING ENGINEERING 11
This is the subcategory to the RDBMSs preserving the SQL language as well as the ACID properties (Salom,
Oró & Garcia, 2015). These types of the databases usually attain the high performance as well as scalability
through offering of the architectural redesigns which could take many core machines that have huge or non-
volatile in the memory storage (Salom, Oró & Garcia, 2015). They usually allow the real time analytics as
well as transaction processing at same time.
Distributed file storage and management
The distributed file system to the cloud services which would be implemented by GlobalNets organization
would enable the IT organization to have access to the data as well as the support operation on that particular
data. Each of the data file will be partitioned into numerous parts regarded as the chunks (Dhers, Feltham &
Brooker, 2015). Each of these chunks will be stored on various remote machines, which facilitate on the
parallel execution to the applications within the system. The users will share the computing resources through
the internet via the cloud services which will be implemented.
The network file system which utilizes the client server architecture would allow the sharing of the files
between the numerous machines on the network as if they are located locally, and this provide standardized
view (Ramachandran, 2016). The NFS protocol would allow the heterogeneous process of the clients, which
might run on the various machines under different OS, to gain access to the files on the servers that are at
distant.
Cloud based synchronization
There are more users who have many devices that have the ad hoc connectivity within this organization
(Bittner, Schietinger, Schroth & Weinkopf, 2017). The data sets which are replicated on these devices of the
IT firm should be synchronized among the arbitrary number of the servers (Bittner, Schietinger, Schroth &
Weinkopf, 2017). This is important to backup especially for the offline operation. When the network of the
users is not good, then their devices would selectively replicate on the part of the data which would be
modified later as well as offline. Once the network condition becomes good, then the device has been
This is the subcategory to the RDBMSs preserving the SQL language as well as the ACID properties (Salom,
Oró & Garcia, 2015). These types of the databases usually attain the high performance as well as scalability
through offering of the architectural redesigns which could take many core machines that have huge or non-
volatile in the memory storage (Salom, Oró & Garcia, 2015). They usually allow the real time analytics as
well as transaction processing at same time.
Distributed file storage and management
The distributed file system to the cloud services which would be implemented by GlobalNets organization
would enable the IT organization to have access to the data as well as the support operation on that particular
data. Each of the data file will be partitioned into numerous parts regarded as the chunks (Dhers, Feltham &
Brooker, 2015). Each of these chunks will be stored on various remote machines, which facilitate on the
parallel execution to the applications within the system. The users will share the computing resources through
the internet via the cloud services which will be implemented.
The network file system which utilizes the client server architecture would allow the sharing of the files
between the numerous machines on the network as if they are located locally, and this provide standardized
view (Ramachandran, 2016). The NFS protocol would allow the heterogeneous process of the clients, which
might run on the various machines under different OS, to gain access to the files on the servers that are at
distant.
Cloud based synchronization
There are more users who have many devices that have the ad hoc connectivity within this organization
(Bittner, Schietinger, Schroth & Weinkopf, 2017). The data sets which are replicated on these devices of the
IT firm should be synchronized among the arbitrary number of the servers (Bittner, Schietinger, Schroth &
Weinkopf, 2017). This is important to backup especially for the offline operation. When the network of the
users is not good, then their devices would selectively replicate on the part of the data which would be
modified later as well as offline. Once the network condition becomes good, then the device has been

ADVANCED NETWORKING ENGINEERING 12
synchronized (Harrison, Wright & Trembath, 2017). There are two approaches to which exists in order to
address the distributed synchronization problems they are the controlled peer to peer synchronization and the
cloud master replica synchronization (Nativi, Mazzetti, Santoro, Papeschi, Craglia & Ochiai, 2015). With
regards to the user controlled peer to peer, software such as the rsync should be installed to the whole user’s
PC which contains their data. The files are then synchronized through the peer to peer synchronization
software in which the customers could highlights on the network addresses as well as the synchronization
parameters (Royapoor & Roskilly, 2015). This process is done manually. On the second approach is on the
cloud master replica synchronization, this is the one which would be utilized by GlobalNets Company to
synchronize on the data for this IT organization (Salom, Oró & Garcia, 2015). This method is used by the
cloud services, where there is a master replica that is maintained in cloud. All the upgrades as well as
synchronization operations are usually on the master copy (Salom, Oró & Garcia, 2015). This strategy
provides an excellent degree of the availability and dependability in the event of any failures.
Distributed file management backup
A universal issue among businesses such as this IT firm which operate numerous branches that are separated
geographically is on the issue of the file storage (Gorton & Klein, 2015). This could present numerous issues
which could include duplicating of the files, difficulties to identify on the latest version to the files,
protection of the files from being corrupted or changed by the individuals who are unauthorized, and the
focus to the necessitate to backing up all the data to the various branch locations (Gorton & Klein, 2015). To
address on this issue the GlobalNets organization would create a centralized data center at the main office
which is 100km from the regional town (Hill, 2018).They would establish a secure, coherent, consistent as
well as scalable and managed system which would support all the branch offices all across the nation and
around the world (Hill, 2018). This solution need to offer the same level of the performance to the workers
anywhere in the nation. The business would establish this centralized pool of the data then utilize CloudFast
software in order to offer access to different branch offices (Salom, Oró & Garcia, 2015). This would support
the file locking and at the same time provide high performance access to all the employees everywhere
synchronized (Harrison, Wright & Trembath, 2017). There are two approaches to which exists in order to
address the distributed synchronization problems they are the controlled peer to peer synchronization and the
cloud master replica synchronization (Nativi, Mazzetti, Santoro, Papeschi, Craglia & Ochiai, 2015). With
regards to the user controlled peer to peer, software such as the rsync should be installed to the whole user’s
PC which contains their data. The files are then synchronized through the peer to peer synchronization
software in which the customers could highlights on the network addresses as well as the synchronization
parameters (Royapoor & Roskilly, 2015). This process is done manually. On the second approach is on the
cloud master replica synchronization, this is the one which would be utilized by GlobalNets Company to
synchronize on the data for this IT organization (Salom, Oró & Garcia, 2015). This method is used by the
cloud services, where there is a master replica that is maintained in cloud. All the upgrades as well as
synchronization operations are usually on the master copy (Salom, Oró & Garcia, 2015). This strategy
provides an excellent degree of the availability and dependability in the event of any failures.
Distributed file management backup
A universal issue among businesses such as this IT firm which operate numerous branches that are separated
geographically is on the issue of the file storage (Gorton & Klein, 2015). This could present numerous issues
which could include duplicating of the files, difficulties to identify on the latest version to the files,
protection of the files from being corrupted or changed by the individuals who are unauthorized, and the
focus to the necessitate to backing up all the data to the various branch locations (Gorton & Klein, 2015). To
address on this issue the GlobalNets organization would create a centralized data center at the main office
which is 100km from the regional town (Hill, 2018).They would establish a secure, coherent, consistent as
well as scalable and managed system which would support all the branch offices all across the nation and
around the world (Hill, 2018). This solution need to offer the same level of the performance to the workers
anywhere in the nation. The business would establish this centralized pool of the data then utilize CloudFast
software in order to offer access to different branch offices (Salom, Oró & Garcia, 2015). This would support
the file locking and at the same time provide high performance access to all the employees everywhere
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





