Analysis of Client/Server Application Components in Data Communication
VerifiedAdded on 2023/01/06
|23
|5991
|87
Report
AI Summary
This report provides a comprehensive analysis of client/server application components within the realm of data communication and computer networks. It begins with an introduction to client/server applications, highlighting the impact of increasing network bandwidth and multi-threaded operating systems. The report delves into key technologies such as rich transaction processing, roaming agents, rich data management, intelligent self-managing entities, and intelligent middleware. It then explores various services offered by client/server applications, including file sharing, database-centered systems, groupware, transactional processing, and distributed objects. The report further classifies client/server applications into different categories based on processing distribution: host-based, server-based, client-based, and cooperative processing. It also examines client services, including inter-process communication, remote services, and window services. The report concludes by discussing client/server application connectivity, middleware, and layered architecture. This assignment comprehensively covers the architecture, services, and technologies associated with client/server applications.

Faculty:
CS&IT
Department:
Information Technology
Subject:
Data Communication & Computer Network
Assignment:
Client/Server Application components
Lecturer:
Abdijabar Awais Osman
CS&IT
Department:
Information Technology
Subject:
Data Communication & Computer Network
Assignment:
Client/Server Application components
Lecturer:
Abdijabar Awais Osman
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Group Names ID Number Title
Abdisamad Yusuf Omar 17386 5.1 Introduction
5.2 Technologies for
Client/Server Application
5.3 Service of a Client/Server
Application
Sharmake Ahmed Mohamed 17564 5.4 Categories of
Client/Server Applications
5.5 Client Services
5.5.1 Inter Process
Communication
5.5.2 Remote Services
5.5.3 Window Services
Ilham Abubakar Hirabe 18027 Client Services
5.5.4 Dynamic Data Exchange
(DDE)
5.5.5 Object Linking and
Embedding (OLE)
5.5.6 Common Object Request
Broker Architecture (CORBA)
Mohamed Hassan Mohamed 17515 Client Services
5.5.7 Print/Fax Services
5.5.8 Database Services
5.6 Server Services
Abshir Muse Hussein 17460 5.7 Client/Server
Application: Connectivity
5.7.1 Role and Mechanism of
Middleware
Abdihakin Hassan Mohamud 17844 5.8 Client/Server
Application: Layered
Architecture
5.8.1 Design Approach
5.8.2 Interface in Three Layers
Chapter Summary
Group B: CLIENT/SERVER APPLICATION COMPONENTS
Abdisamad Yusuf Omar 17386 5.1 Introduction
5.2 Technologies for
Client/Server Application
5.3 Service of a Client/Server
Application
Sharmake Ahmed Mohamed 17564 5.4 Categories of
Client/Server Applications
5.5 Client Services
5.5.1 Inter Process
Communication
5.5.2 Remote Services
5.5.3 Window Services
Ilham Abubakar Hirabe 18027 Client Services
5.5.4 Dynamic Data Exchange
(DDE)
5.5.5 Object Linking and
Embedding (OLE)
5.5.6 Common Object Request
Broker Architecture (CORBA)
Mohamed Hassan Mohamed 17515 Client Services
5.5.7 Print/Fax Services
5.5.8 Database Services
5.6 Server Services
Abshir Muse Hussein 17460 5.7 Client/Server
Application: Connectivity
5.7.1 Role and Mechanism of
Middleware
Abdihakin Hassan Mohamud 17844 5.8 Client/Server
Application: Layered
Architecture
5.8.1 Design Approach
5.8.2 Interface in Three Layers
Chapter Summary
Group B: CLIENT/SERVER APPLICATION COMPONENTS

5.1 INTRODUCTION
A Client/Server application stand at a new threshold brought on by the exponential increase
Of low cost bandwidth on Wide Area Networks, for example, the Internet and CompuServe;
And shows a new generation of network enabled, multi-threaded desktop operating systems,
Some key technologies are needed at the Client/Server
application level to make all this happen, including:
Rich transaction processing: In addition to supporting
the venerable flat transaction, the new environment
requires nested transactions that can span across multiple
servers, long-lived transactions that execute over long
periods of time as they travel from server to server, and queued transactions that can be
used in secure business-to-business dealings. Most nodes on the network should be able
to participate in a secured transaction; super server nodes will handle the massive
transaction loads.
Roaming agents: The new environment will be populated with electronic agents of all
types. Consumers will have personal agents that look after their interests; businesses will
deploy agents to sell their wares on the network; and sniffer agents will be sitting on the
network, at all times, collecting information to do system management or simply looking
for trends. Agent technology includes cross-platform scripting engines, workflow, and
Java-like mobile code environments that allow agents to live on any machine on the
network.
Rich data management: This includes active multimedia compound documents that you
can move, store, view, and edit in-place anywhere on the network. Again, most nodes on
the network should provide compound document technology — for example, OLE or
OpenDoc – for doing mobile document management. Of course, this environment must
also be able to support existing record-based structured data including SQL databases.
Intelligent self-managing entities: With the introduction of new multi-threaded, high-
volume, network-ready desktop operating systems; we anticipate a world where millions
5.2
TECHNOLOGIES
FOR
CLIENT/SERVER
APPLICATION
A Client/Server application stand at a new threshold brought on by the exponential increase
Of low cost bandwidth on Wide Area Networks, for example, the Internet and CompuServe;
And shows a new generation of network enabled, multi-threaded desktop operating systems,
Some key technologies are needed at the Client/Server
application level to make all this happen, including:
Rich transaction processing: In addition to supporting
the venerable flat transaction, the new environment
requires nested transactions that can span across multiple
servers, long-lived transactions that execute over long
periods of time as they travel from server to server, and queued transactions that can be
used in secure business-to-business dealings. Most nodes on the network should be able
to participate in a secured transaction; super server nodes will handle the massive
transaction loads.
Roaming agents: The new environment will be populated with electronic agents of all
types. Consumers will have personal agents that look after their interests; businesses will
deploy agents to sell their wares on the network; and sniffer agents will be sitting on the
network, at all times, collecting information to do system management or simply looking
for trends. Agent technology includes cross-platform scripting engines, workflow, and
Java-like mobile code environments that allow agents to live on any machine on the
network.
Rich data management: This includes active multimedia compound documents that you
can move, store, view, and edit in-place anywhere on the network. Again, most nodes on
the network should provide compound document technology — for example, OLE or
OpenDoc – for doing mobile document management. Of course, this environment must
also be able to support existing record-based structured data including SQL databases.
Intelligent self-managing entities: With the introduction of new multi-threaded, high-
volume, network-ready desktop operating systems; we anticipate a world where millions
5.2
TECHNOLOGIES
FOR
CLIENT/SERVER
APPLICATION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

of machines can be both clients and servers. However, we can’t afford to ship a system
administrator with every $99 operating system. To avoid doing this, we need distributed
software that knows how to manage and configure itself and protect itself against threats.
Intelligent middleware: The distributed environment must provide the semblance of a
single-system-image across potentially millions of hybrid Client/Server machines.
The middleware must create this Houdini-sized illusion by making all servers on the
global network appear to behave like a single computer system. Users and programs
should be able to dynamically join and leave the network, and then discover each other.
You should be able to use the same naming conventions to locate any resource on the
network.
In this section, the discussion is about most widely used five
types of Client/Server applications. In no way is this meant to
cover all Client/Server applications available today. The truth,
there is no agreement within the computer industry as to what
constitutes Client/Server and therefore, what one expect or
vendor may claim to be Client/Server may not necessarily fit the
definition of others.
In general, Client/Server is a system. It is not just hardware or software. It is not necessarily a
program that comes in a box to be installed onto your computer’s hard drive (although many
software manufacturers are seeing the potential market for Client/Server products, and therefore
are anxious to develop and sell such programs). Client/Server is a conglomeration of computer
equipment, infrastructure, and software programs working together to accomplish computing
tasks which enable their users to be more efficient and productive. Client/Server applications can
be distinguished by the nature of the service or type of solutions they provide. Among them five
common types of solutions are as given below.
5.3 SERVICE
OF A
CLIENT/SER
VER
APPLICATIO
N
administrator with every $99 operating system. To avoid doing this, we need distributed
software that knows how to manage and configure itself and protect itself against threats.
Intelligent middleware: The distributed environment must provide the semblance of a
single-system-image across potentially millions of hybrid Client/Server machines.
The middleware must create this Houdini-sized illusion by making all servers on the
global network appear to behave like a single computer system. Users and programs
should be able to dynamically join and leave the network, and then discover each other.
You should be able to use the same naming conventions to locate any resource on the
network.
In this section, the discussion is about most widely used five
types of Client/Server applications. In no way is this meant to
cover all Client/Server applications available today. The truth,
there is no agreement within the computer industry as to what
constitutes Client/Server and therefore, what one expect or
vendor may claim to be Client/Server may not necessarily fit the
definition of others.
In general, Client/Server is a system. It is not just hardware or software. It is not necessarily a
program that comes in a box to be installed onto your computer’s hard drive (although many
software manufacturers are seeing the potential market for Client/Server products, and therefore
are anxious to develop and sell such programs). Client/Server is a conglomeration of computer
equipment, infrastructure, and software programs working together to accomplish computing
tasks which enable their users to be more efficient and productive. Client/Server applications can
be distinguished by the nature of the service or type of solutions they provide. Among them five
common types of solutions are as given below.
5.3 SERVICE
OF A
CLIENT/SER
VER
APPLICATIO
N
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

File sharing.
Database centered systems.
Groupware.
Transactional processing.
Distributed objects.
• File sharing: File sharing is Client/Server in its most primitive form. It is the earliest form of
computing over a network. Some purists would deny that file sharing is Client/Server
technology. In file sharing, a client computer simply sends a request for a file or records to a file
server. The server, in turn, searches its database and fills the request. Usually, in a file sharing
environment, the users of the information have little need for control over the data or rarely have
to make modifications to the files or records. File sharing is ideal for organizations that have
shared repositories of documents, images, large data objects, read-only files, etc.
• Database centered systems: The most common use of Client/Server technology is to provide
access to a commonly shared database to users (clients) on a network.
This differs from simple file sharing in that a database centered system not only allows clients to
request data and data-related services, but it also enables them to modify the information on file
in the database. In such systems, the database server not only houses the database itself; it helps
to manage the data by providing secured access and access by multiple users at the same time.
Database-centered systems utilize SQL, a simple computer language which enables data request
and fulfillment messages to be understood by both clients and servers. Database-centered
Client/Server applications generally fall into one of two categories:
(i) Decision-Support Systems (DSS) or
(ii) Online Transaction Processing (OLTP).
Both provide data on request but differ in the kinds of information needs they fulfill.
(i) Decision-support systems (DSS): Decision-Support Systems (DSS) are used when clients on
the system frequently do analysis of the data or use the data to create reports and other
documents. DSS provides a “snapshot” of data at a particular point in time. Typically, DSS
might be utilized for a library catalog,
WWW pages, or patient records in a doctor’s office.
Database centered systems.
Groupware.
Transactional processing.
Distributed objects.
• File sharing: File sharing is Client/Server in its most primitive form. It is the earliest form of
computing over a network. Some purists would deny that file sharing is Client/Server
technology. In file sharing, a client computer simply sends a request for a file or records to a file
server. The server, in turn, searches its database and fills the request. Usually, in a file sharing
environment, the users of the information have little need for control over the data or rarely have
to make modifications to the files or records. File sharing is ideal for organizations that have
shared repositories of documents, images, large data objects, read-only files, etc.
• Database centered systems: The most common use of Client/Server technology is to provide
access to a commonly shared database to users (clients) on a network.
This differs from simple file sharing in that a database centered system not only allows clients to
request data and data-related services, but it also enables them to modify the information on file
in the database. In such systems, the database server not only houses the database itself; it helps
to manage the data by providing secured access and access by multiple users at the same time.
Database-centered systems utilize SQL, a simple computer language which enables data request
and fulfillment messages to be understood by both clients and servers. Database-centered
Client/Server applications generally fall into one of two categories:
(i) Decision-Support Systems (DSS) or
(ii) Online Transaction Processing (OLTP).
Both provide data on request but differ in the kinds of information needs they fulfill.
(i) Decision-support systems (DSS): Decision-Support Systems (DSS) are used when clients on
the system frequently do analysis of the data or use the data to create reports and other
documents. DSS provides a “snapshot” of data at a particular point in time. Typically, DSS
might be utilized for a library catalog,
WWW pages, or patient records in a doctor’s office.

(ii) Online transaction processing: Online Transaction Processing (OLTP) provides current,
up-to-the-minute information reflecting changes and continuous updates.
Users of an OLTP system typically require mission-critical applications that perform data access
functions and other transactions with a one to two seconds response time.
Airline reservations systems, point-of-sale tracking systems (i.e., “cash registers” in large
department stores or super markets), and a stockbroker’s workstation are
OLTP applications.
• Groupware: Groupware brings together five basic technologies multimedia document
management, workflow, scheduling, conferencing, and electronic mail, in order to facilitate work
activities.
One author defines groupware as “software that supports creation, flow, and tracking of non-
structured information in direct support of collaborative group activity.” Groupware removes
control over documents from the server and distributes it over a network, thus enabling
collaboration on specific tasks and projects. The collaborative activity is virtually concurrent
meaning that clients on the network, wherever they may be, can contribute, produce, and modify
documents, and in the end, using the management and tracking features, synchronizes everything
and produces a collective group product.
Multimedia Document Managements (MMDM)
With groupware, clients can have access to documents and images as needed. Multimedia
document management (MMDM) allows them to take those documents and modify them.
The modifications can take place in real time with several clients making changes and
modifications simultaneously, or they can be modified, stored on the server for review or future
action by other clients. MMDM is, in essence, an electronic filing cabinet that holds documents
in the form of text, images, graphics, voice clips, video, and other media.
• Transactional Processing
To create truly effective Client/Server solutions, the various components within the system (the
application software, the network operating system, utilities, and other programs) need to work
together in unison. If infrastructure and software which enable Client/Server computing are
musicians in a symphony, transaction processing would be the conductor.
up-to-the-minute information reflecting changes and continuous updates.
Users of an OLTP system typically require mission-critical applications that perform data access
functions and other transactions with a one to two seconds response time.
Airline reservations systems, point-of-sale tracking systems (i.e., “cash registers” in large
department stores or super markets), and a stockbroker’s workstation are
OLTP applications.
• Groupware: Groupware brings together five basic technologies multimedia document
management, workflow, scheduling, conferencing, and electronic mail, in order to facilitate work
activities.
One author defines groupware as “software that supports creation, flow, and tracking of non-
structured information in direct support of collaborative group activity.” Groupware removes
control over documents from the server and distributes it over a network, thus enabling
collaboration on specific tasks and projects. The collaborative activity is virtually concurrent
meaning that clients on the network, wherever they may be, can contribute, produce, and modify
documents, and in the end, using the management and tracking features, synchronizes everything
and produces a collective group product.
Multimedia Document Managements (MMDM)
With groupware, clients can have access to documents and images as needed. Multimedia
document management (MMDM) allows them to take those documents and modify them.
The modifications can take place in real time with several clients making changes and
modifications simultaneously, or they can be modified, stored on the server for review or future
action by other clients. MMDM is, in essence, an electronic filing cabinet that holds documents
in the form of text, images, graphics, voice clips, video, and other media.
• Transactional Processing
To create truly effective Client/Server solutions, the various components within the system (the
application software, the network operating system, utilities, and other programs) need to work
together in unison. If infrastructure and software which enable Client/Server computing are
musicians in a symphony, transaction processing would be the conductor.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

• Distributed Objects
A distributed object is a vague term used to describe the technologies which allow clients and
servers from different technologies from different environments and platforms to work
seamlessly together. Its goal is to provide users with single-image, easy-to-use, virtually
transparent applications.
Distributed object technology is still in its infancy and has yet to fulfill its promise of making
Client/Server into the flexible, robust, intelligent, and self-managing systems that most users
want and expect. Distributed objects technology has great “potential” but at this point in time, it
remains just that potential.
CATEGORIES OF CLIENT/SERVER APPLICATIONS
There are variety of ways to divide the processing between client and server. But the exact
distribution of data and application programming depends on the nature of the database, the type
of application supported, the availability of interoperable vendor equipment, and the usage
patterns within an organization. Depending on the database applications various classes of
Client/Server Application has been characterized.
(i) Host-based processing.
(ii) Server-based processing.
(iii) Client-based processing.
(iv) Cooperative processing.
Host-based processing: Virtually all the processing is done on a central host, often user
interface is via a dumb terminal. It is mainly mainframe environment, not true Client/Server
computing.In such a processing’s workstations have very limited role as shown in Fig. 5.1 given
below:
A distributed object is a vague term used to describe the technologies which allow clients and
servers from different technologies from different environments and platforms to work
seamlessly together. Its goal is to provide users with single-image, easy-to-use, virtually
transparent applications.
Distributed object technology is still in its infancy and has yet to fulfill its promise of making
Client/Server into the flexible, robust, intelligent, and self-managing systems that most users
want and expect. Distributed objects technology has great “potential” but at this point in time, it
remains just that potential.
CATEGORIES OF CLIENT/SERVER APPLICATIONS
There are variety of ways to divide the processing between client and server. But the exact
distribution of data and application programming depends on the nature of the database, the type
of application supported, the availability of interoperable vendor equipment, and the usage
patterns within an organization. Depending on the database applications various classes of
Client/Server Application has been characterized.
(i) Host-based processing.
(ii) Server-based processing.
(iii) Client-based processing.
(iv) Cooperative processing.
Host-based processing: Virtually all the processing is done on a central host, often user
interface is via a dumb terminal. It is mainly mainframe environment, not true Client/Server
computing.In such a processing’s workstations have very limited role as shown in Fig. 5.1 given
below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(ii) Server-based processing: All the processing is done on the server, and server is responsible
for providing graphical user interface. A considerable fraction of the load is on the server, so this
is also called fat server modelshown in Fig. 5.2 given below:
(iii) Client-based processing: Virtually all application processing may be done at the client,
with the exception of data validation routines and other database logic functions that are best
performed at the server. Some of the sophisticated database logic functions residing on the client
side. This architecture is the most common Client/Server approach in current use.It enables the
user to employ applications tailored to local need shown in Fig 5.3 given below:
(iv) Cooperative processing: Taking the advantage of the strengths of both client and server
machine and of the distribution of data, the application processing is performed in an optimized
fashion. Such a configuration of Client/Server approach is more complex to set up and
maintain.But in the long run, this configuration may offer greater user productivity gain and
greater network efficiency than others Client/Server approaches. A considerable fraction of the
load is on the client, so this is also called fat client model. In case of some application
development tools this model is very popular shown in Fig. 5.4 given below:
for providing graphical user interface. A considerable fraction of the load is on the server, so this
is also called fat server modelshown in Fig. 5.2 given below:
(iii) Client-based processing: Virtually all application processing may be done at the client,
with the exception of data validation routines and other database logic functions that are best
performed at the server. Some of the sophisticated database logic functions residing on the client
side. This architecture is the most common Client/Server approach in current use.It enables the
user to employ applications tailored to local need shown in Fig 5.3 given below:
(iv) Cooperative processing: Taking the advantage of the strengths of both client and server
machine and of the distribution of data, the application processing is performed in an optimized
fashion. Such a configuration of Client/Server approach is more complex to set up and
maintain.But in the long run, this configuration may offer greater user productivity gain and
greater network efficiency than others Client/Server approaches. A considerable fraction of the
load is on the client, so this is also called fat client model. In case of some application
development tools this model is very popular shown in Fig. 5.4 given below:

CLIENT SERVICE
Any workstation that is used by a single user is a client, it has been noticed during last decade the
workstations are improving their performance surprisingly. Having same cost you can purchase
CPU that can perform more than 50 times, main memory approximately Introduction to
Client/Server Computing86 30 times and Hard Disk up to 40 times. These are considered as
power factor of computer, hence; as a result, more sophisticated applications can be run from the
workstations. To run various applications workstation uses the available operating systems like
DOS, Windows (98, 2000, NT) and UNIX or Linux, Mac, OS/2. In case of, network
environment (LAN, WAN) workstations also avails the services provided by the network
operating systems. Client workstations request services from the attached server. Whether this
server is in fact the same processor or a network processor, the application format of the request
is the same. Network operating system translates or adds the specifics required by the targeted
requester to the application request. Communication between all these running processes are
better described by Inter Process Communication (IPC), these processes might be on the same
computer, across the LAN, or WAN.
Some of the main services that client performs (role of client) are listed below:
Responsible for managing the user interface.
Provides presentation services.
Accepts and checks the syntax of user inputs. User input and final output, if any, are
presented at the client workstation.
Acts as a consumer of services Generates database request and transmits to server.
Passes response back to server.
Local processing by the workstation might calculate the invoice amount and format the response
to the workstation screen. Now, it is important to understand that a workstation can operate as a
client in some instances while acting as a server in other instances. For example, in a LAN
Manager environment, a workstation might act as a client for one user while simultaneously
acting as a print server for many users. Apart from these services discussed above some of the
Any workstation that is used by a single user is a client, it has been noticed during last decade the
workstations are improving their performance surprisingly. Having same cost you can purchase
CPU that can perform more than 50 times, main memory approximately Introduction to
Client/Server Computing86 30 times and Hard Disk up to 40 times. These are considered as
power factor of computer, hence; as a result, more sophisticated applications can be run from the
workstations. To run various applications workstation uses the available operating systems like
DOS, Windows (98, 2000, NT) and UNIX or Linux, Mac, OS/2. In case of, network
environment (LAN, WAN) workstations also avails the services provided by the network
operating systems. Client workstations request services from the attached server. Whether this
server is in fact the same processor or a network processor, the application format of the request
is the same. Network operating system translates or adds the specifics required by the targeted
requester to the application request. Communication between all these running processes are
better described by Inter Process Communication (IPC), these processes might be on the same
computer, across the LAN, or WAN.
Some of the main services that client performs (role of client) are listed below:
Responsible for managing the user interface.
Provides presentation services.
Accepts and checks the syntax of user inputs. User input and final output, if any, are
presented at the client workstation.
Acts as a consumer of services Generates database request and transmits to server.
Passes response back to server.
Local processing by the workstation might calculate the invoice amount and format the response
to the workstation screen. Now, it is important to understand that a workstation can operate as a
client in some instances while acting as a server in other instances. For example, in a LAN
Manager environment, a workstation might act as a client for one user while simultaneously
acting as a print server for many users. Apart from these services discussed above some of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
other important services that are directly or indirectly attached with the client services are given
below:
(a) Inter process communication.
(b) Remote services.
(c) Window services.
(a) Inter Process Communication The communication between two processes take place via
buffer. The alternative way of communication is the process of the interprocess communication.
The simple mechanism of this is synchronizing their action and without sharing the same address
space. The more redefined method of inter process communication are message queues,
semaphores and shared memory. There are four types of mechanisms, involved for such a
communications:
(i) Message passing.
(ii) Direct communication.
(iii) Indirect communication.
(iv) Remote procedures call
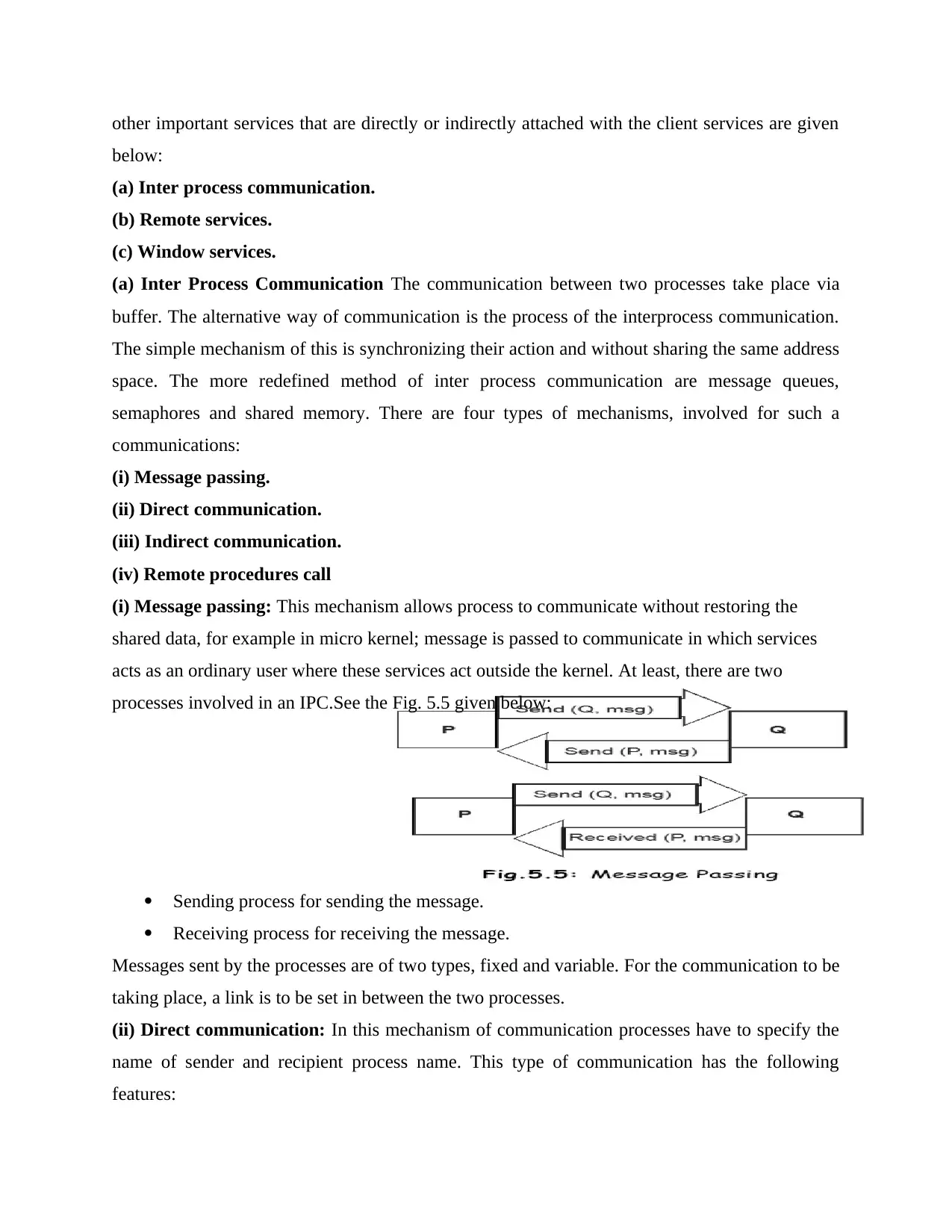
(i) Message passing: This mechanism allows process to communicate without restoring the
shared data, for example in micro kernel; message is passed to communicate in which services
acts as an ordinary user where these services act outside the kernel. At least, there are two
processes involved in an IPC.See the Fig. 5.5 given below:
Sending process for sending the message.
Receiving process for receiving the message.
Messages sent by the processes are of two types, fixed and variable. For the communication to be
taking place, a link is to be set in between the two processes.
(ii) Direct communication: In this mechanism of communication processes have to specify the
name of sender and recipient process name. This type of communication has the following
features:
below:
(a) Inter process communication.
(b) Remote services.
(c) Window services.
(a) Inter Process Communication The communication between two processes take place via
buffer. The alternative way of communication is the process of the interprocess communication.
The simple mechanism of this is synchronizing their action and without sharing the same address
space. The more redefined method of inter process communication are message queues,
semaphores and shared memory. There are four types of mechanisms, involved for such a
communications:
(i) Message passing.
(ii) Direct communication.
(iii) Indirect communication.
(iv) Remote procedures call
(i) Message passing: This mechanism allows process to communicate without restoring the
shared data, for example in micro kernel; message is passed to communicate in which services
acts as an ordinary user where these services act outside the kernel. At least, there are two
processes involved in an IPC.See the Fig. 5.5 given below:
Sending process for sending the message.
Receiving process for receiving the message.
Messages sent by the processes are of two types, fixed and variable. For the communication to be
taking place, a link is to be set in between the two processes.
(ii) Direct communication: In this mechanism of communication processes have to specify the
name of sender and recipient process name. This type of communication has the following
features:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
A link is established in between the sender and receiver along with full known
information of their names and addresses.
One link must be established in between the processes.
There is symmetry in between the communication of the processes
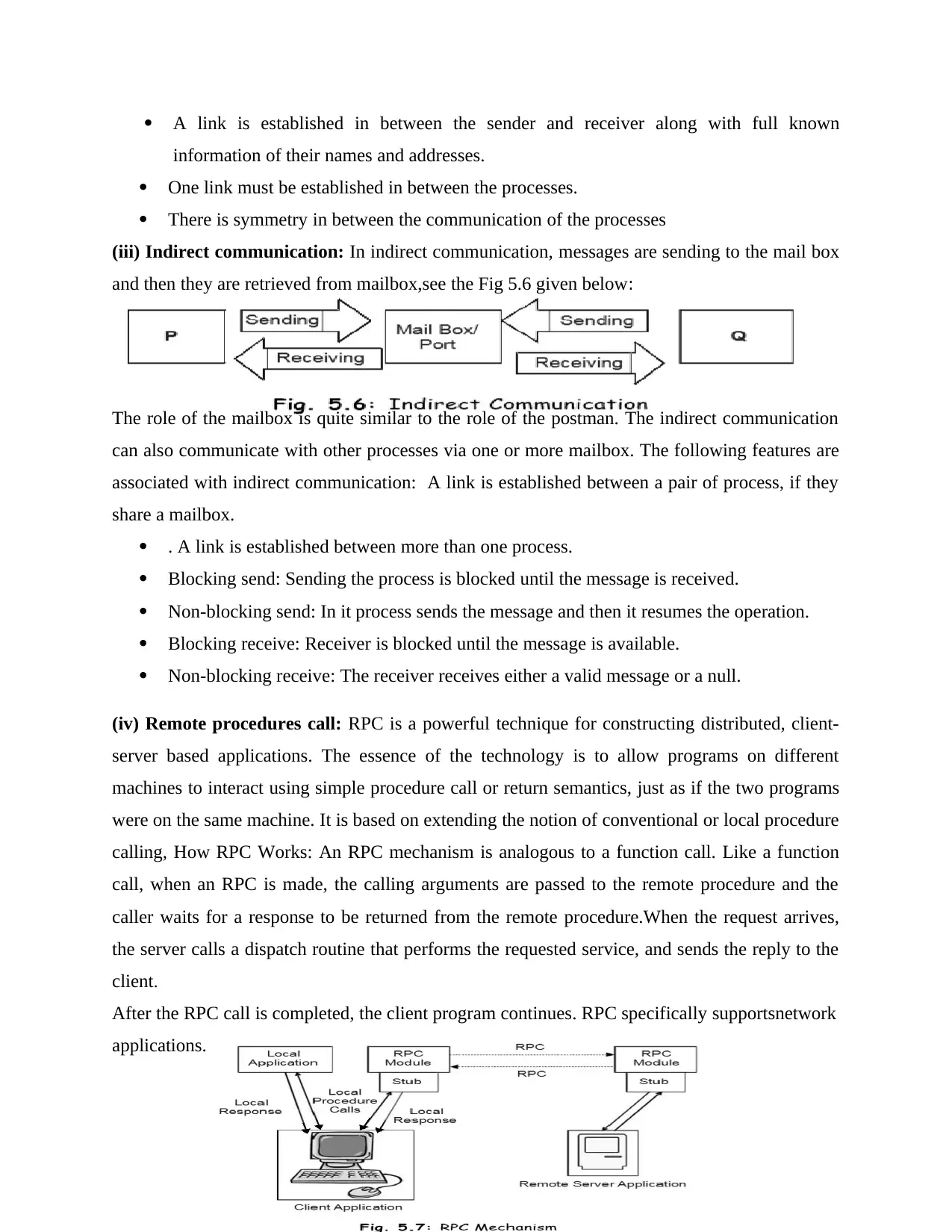
(iii) Indirect communication: In indirect communication, messages are sending to the mail box
and then they are retrieved from mailbox,see the Fig 5.6 given below:
The role of the mailbox is quite similar to the role of the postman. The indirect communication
can also communicate with other processes via one or more mailbox. The following features are
associated with indirect communication: A link is established between a pair of process, if they
share a mailbox.
. A link is established between more than one process.
Blocking send: Sending the process is blocked until the message is received.
Non-blocking send: In it process sends the message and then it resumes the operation.
Blocking receive: Receiver is blocked until the message is available.
Non-blocking receive: The receiver receives either a valid message or a null.
(iv) Remote procedures call: RPC is a powerful technique for constructing distributed, client-
server based applications. The essence of the technology is to allow programs on different
machines to interact using simple procedure call or return semantics, just as if the two programs
were on the same machine. It is based on extending the notion of conventional or local procedure
calling, How RPC Works: An RPC mechanism is analogous to a function call. Like a function
call, when an RPC is made, the calling arguments are passed to the remote procedure and the
caller waits for a response to be returned from the remote procedure.When the request arrives,
the server calls a dispatch routine that performs the requested service, and sends the reply to the
client.
After the RPC call is completed, the client program continues. RPC specifically supportsnetwork
applications.
information of their names and addresses.
One link must be established in between the processes.
There is symmetry in between the communication of the processes
(iii) Indirect communication: In indirect communication, messages are sending to the mail box
and then they are retrieved from mailbox,see the Fig 5.6 given below:
The role of the mailbox is quite similar to the role of the postman. The indirect communication
can also communicate with other processes via one or more mailbox. The following features are
associated with indirect communication: A link is established between a pair of process, if they
share a mailbox.
. A link is established between more than one process.
Blocking send: Sending the process is blocked until the message is received.
Non-blocking send: In it process sends the message and then it resumes the operation.
Blocking receive: Receiver is blocked until the message is available.
Non-blocking receive: The receiver receives either a valid message or a null.
(iv) Remote procedures call: RPC is a powerful technique for constructing distributed, client-
server based applications. The essence of the technology is to allow programs on different
machines to interact using simple procedure call or return semantics, just as if the two programs
were on the same machine. It is based on extending the notion of conventional or local procedure
calling, How RPC Works: An RPC mechanism is analogous to a function call. Like a function
call, when an RPC is made, the calling arguments are passed to the remote procedure and the
caller waits for a response to be returned from the remote procedure.When the request arrives,
the server calls a dispatch routine that performs the requested service, and sends the reply to the
client.
After the RPC call is completed, the client program continues. RPC specifically supportsnetwork
applications.

A remote procedure is uniquely identified by the triple: (program number, version number,
procedure number), the program number identifies a group of related remote procedures
Tools of RPC comprises of:
• A language and a compiler to produce portable source code.
• Some run time facilities to make the system architecture and network protocols transparent to
the application procedure. Figure 5.8 given below, illustrates the general architecture
understanding.
(b) Remote Services
In client server model applications can be invoked directly from the client to execute remotely
on a server. The workstation is responsible to provide various remote services remote backup
services, remote tape drive access and remote boot services, and remote data access are
important. Software available with Network Operating System is responsible to run on the client
workstation to initiate all these remote services. Client server technology supports full-powered
workstations with the capability for GUI applications consistent with the desktop
implementation. Remote command execution is when a process on a host cause a program to be
executed on another host, usually the invoking process wants to pass data to the remote program,
and capture its output also. From a client workstation backup services may be invoked remotely.
To run the application, some of the workstation clients (like X-terminals) do not have the local
storage facility. In such scenario, client provides appropriate software’s that are burned into E-
PROM (Erasable Programmable Read-Only Memory) to start the initial program load (IPL)that
is known as Boot Process. If E-PROM is inbuilt with X-terminals to hold the Basic Input/output
System services. Then partial operating system will be able to load the remote software’s that
procedure number), the program number identifies a group of related remote procedures
Tools of RPC comprises of:
• A language and a compiler to produce portable source code.
• Some run time facilities to make the system architecture and network protocols transparent to
the application procedure. Figure 5.8 given below, illustrates the general architecture
understanding.
(b) Remote Services
In client server model applications can be invoked directly from the client to execute remotely
on a server. The workstation is responsible to provide various remote services remote backup
services, remote tape drive access and remote boot services, and remote data access are
important. Software available with Network Operating System is responsible to run on the client
workstation to initiate all these remote services. Client server technology supports full-powered
workstations with the capability for GUI applications consistent with the desktop
implementation. Remote command execution is when a process on a host cause a program to be
executed on another host, usually the invoking process wants to pass data to the remote program,
and capture its output also. From a client workstation backup services may be invoked remotely.
To run the application, some of the workstation clients (like X-terminals) do not have the local
storage facility. In such scenario, client provides appropriate software’s that are burned into E-
PROM (Erasable Programmable Read-Only Memory) to start the initial program load (IPL)that
is known as Boot Process. If E-PROM is inbuilt with X-terminals to hold the Basic Input/output
System services. Then partial operating system will be able to load the remote software’s that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


