Data Communication and Networks: Freeware Tools for Network Analysis
VerifiedAdded on 2020/05/16
|17
|1856
|113
Report
AI Summary
This report explores three freeware tools suitable for network analysis and monitoring. It begins by introducing the concept of data communication and networks, emphasizing the exchange of data between a receiver and a source and the sharing of resources among nodes. The report then justifies the selection of Oracle VM VirtualBox, Wireshark, and OMNeT++ for specific scenarios, detailing their installation processes and features. VirtualBox is chosen for network monitoring, Wireshark for Wi-Fi scanning and performance evaluation, and OMNeT++ for QoS evaluation. The report further discusses the necessary features of each tool in the context of the scenarios, including networking capabilities of VirtualBox, the open-source nature of Wireshark, and the INET framework of OMNeT++. The conclusion summarizes the report's contribution to understanding network configurations and enhancing skills for designing and analyzing systems to meet client needs. Finally, the report includes a bibliography of cited sources.

Running head: DATA COMMUNICATION AND NETWORKS
Data Communication and Networks
Name of the student:
Name of the university:
Author Note
Data Communication and Networks
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA COMMUNICATION AND NETWORKS
Executive summary
The report has identified three different freeware tools. They have effectively controlling complex
network and showing status of computers in a network. The study also analyzes tools for QoS
evaluation, performance and WiFi scanning.
Executive summary
The report has identified three different freeware tools. They have effectively controlling complex
network and showing status of computers in a network. The study also analyzes tools for QoS
evaluation, performance and WiFi scanning.

2DATA COMMUNICATION AND NETWORKS
Table of Contents
1. Introduction:......................................................................................................................................3
2. Justification of tool choice:................................................................................................................3
2.1. Scenario 1:..................................................................................................................................3
2.1.1. Installation:..........................................................................................................................4
2.1.2. Exploring the features:.........................................................................................................4
2.2. Scenario 2:..................................................................................................................................4
2.2.1. Installation:..........................................................................................................................5
2.2.2. Exploring the features:.........................................................................................................8
2.3. Scenario 3:..................................................................................................................................8
2.3.1. Installation:..........................................................................................................................8
2.3.2. Exploring the features:.........................................................................................................9
3. Features of the tool necessary in the present scenario:....................................................................10
4. Conclusion:......................................................................................................................................15
5. Bibliography:...................................................................................................................................16
Table of Contents
1. Introduction:......................................................................................................................................3
2. Justification of tool choice:................................................................................................................3
2.1. Scenario 1:..................................................................................................................................3
2.1.1. Installation:..........................................................................................................................4
2.1.2. Exploring the features:.........................................................................................................4
2.2. Scenario 2:..................................................................................................................................4
2.2.1. Installation:..........................................................................................................................5
2.2.2. Exploring the features:.........................................................................................................8
2.3. Scenario 3:..................................................................................................................................8
2.3.1. Installation:..........................................................................................................................8
2.3.2. Exploring the features:.........................................................................................................9
3. Features of the tool necessary in the present scenario:....................................................................10
4. Conclusion:......................................................................................................................................15
5. Bibliography:...................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DATA COMMUNICATION AND NETWORKS
1. Introduction:
Data communication denotes exchange of data between receiver and source. Data network is
the network of digital communication allowing nodes in sharing resources.
The following report is prepared to recognize freeware tool monitoring complete network
and showing a status of every computer in the network. Then a freeware tool is identified for Wi-Fi
scanning, performance and QoS evaluation tool.
2. Justification of tool choice:
Here how this tool fits with necessities in every section.
2.1. Scenario 1:
For the given scenario Oracle VM VirtualBox is chosen to be the most appropriate one. This
is a free virtual manager of a machine, mainly from Sun and developed and available from Oracle. In
many cases controlling virtual machines is a hassle and expensive. A new version of the software
has been providing excessive features and wide support for various platforms and systems1. This
included Linux (2.4 and 2.6), Server 2003, Windows 7, Windows NT, Open BSD and plus Solaris.
Further, it supports OS/2. This comprises of an X86 virtualization package of software and working
as advertised.
1 Langone, J., Key, S. and Alder, U.S., 2015. Oracle announces beta for VM Virtualbox 5.0.
1. Introduction:
Data communication denotes exchange of data between receiver and source. Data network is
the network of digital communication allowing nodes in sharing resources.
The following report is prepared to recognize freeware tool monitoring complete network
and showing a status of every computer in the network. Then a freeware tool is identified for Wi-Fi
scanning, performance and QoS evaluation tool.
2. Justification of tool choice:
Here how this tool fits with necessities in every section.
2.1. Scenario 1:
For the given scenario Oracle VM VirtualBox is chosen to be the most appropriate one. This
is a free virtual manager of a machine, mainly from Sun and developed and available from Oracle. In
many cases controlling virtual machines is a hassle and expensive. A new version of the software
has been providing excessive features and wide support for various platforms and systems1. This
included Linux (2.4 and 2.6), Server 2003, Windows 7, Windows NT, Open BSD and plus Solaris.
Further, it supports OS/2. This comprises of an X86 virtualization package of software and working
as advertised.
1 Langone, J., Key, S. and Alder, U.S., 2015. Oracle announces beta for VM Virtualbox 5.0.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DATA COMMUNICATION AND NETWORKS
2.1.1. Installation:
Firstly one of the mirrors by distribution in /etc/apt/sources.lst is added.
Then, public key and register are downloaded with apt-key for verification of a signature.
Lastly, VirtualBox gets installed.
2.1.2. Exploring the features:
It is helpful for monitoring networks because of its supported guest operating systems and
different platforms it has been running on. Different network problems are detected through packet
logging at the host or guest side 2. Using built-in capacity of the tool create pcap filed supplies more
helpful information. This is because it contains a log of every packet sent and received by a guest.
2.2. Scenario 2:
For the present scenario, Wireshark is chosen to be appropriate. It comprises of huge user
communities and consistent improvements 3.
2 Kuhn, D., Kim, C. and Lopuz, B., 2015. VirtualBox for Oracle. In Linux and Solaris Recipes for Oracle DBAs (pp.
325-344). Apress.
3 Sanders, C., 2017. Practical packet analysis: Using Wireshark to solve real-world network problems. No Starch Press.
2.1.1. Installation:
Firstly one of the mirrors by distribution in /etc/apt/sources.lst is added.
Then, public key and register are downloaded with apt-key for verification of a signature.
Lastly, VirtualBox gets installed.
2.1.2. Exploring the features:
It is helpful for monitoring networks because of its supported guest operating systems and
different platforms it has been running on. Different network problems are detected through packet
logging at the host or guest side 2. Using built-in capacity of the tool create pcap filed supplies more
helpful information. This is because it contains a log of every packet sent and received by a guest.
2.2. Scenario 2:
For the present scenario, Wireshark is chosen to be appropriate. It comprises of huge user
communities and consistent improvements 3.
2 Kuhn, D., Kim, C. and Lopuz, B., 2015. VirtualBox for Oracle. In Linux and Solaris Recipes for Oracle DBAs (pp.
325-344). Apress.
3 Sanders, C., 2017. Practical packet analysis: Using Wireshark to solve real-world network problems. No Starch Press.
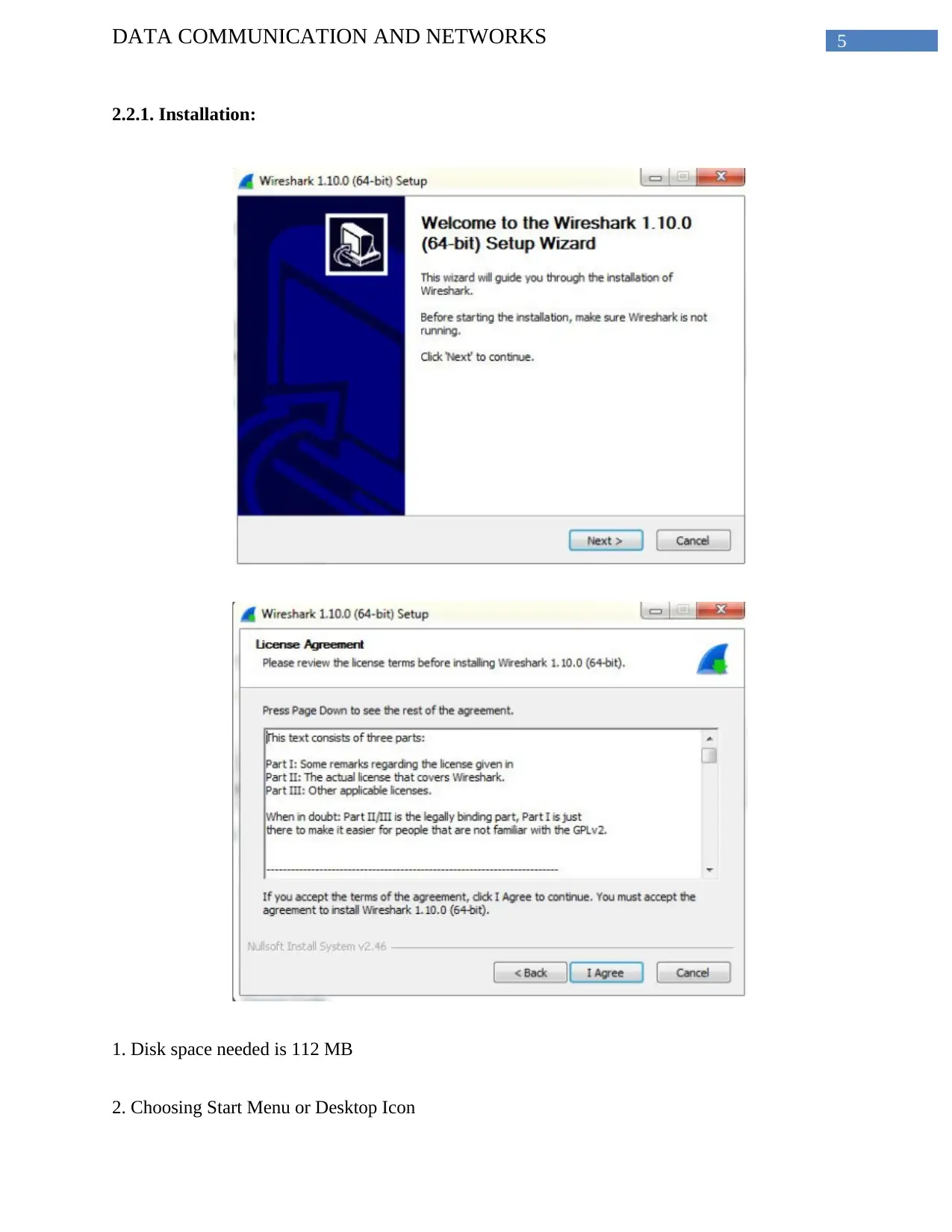
5DATA COMMUNICATION AND NETWORKS
2.2.1. Installation:
1. Disk space needed is 112 MB
2. Choosing Start Menu or Desktop Icon
2.2.1. Installation:
1. Disk space needed is 112 MB
2. Choosing Start Menu or Desktop Icon
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
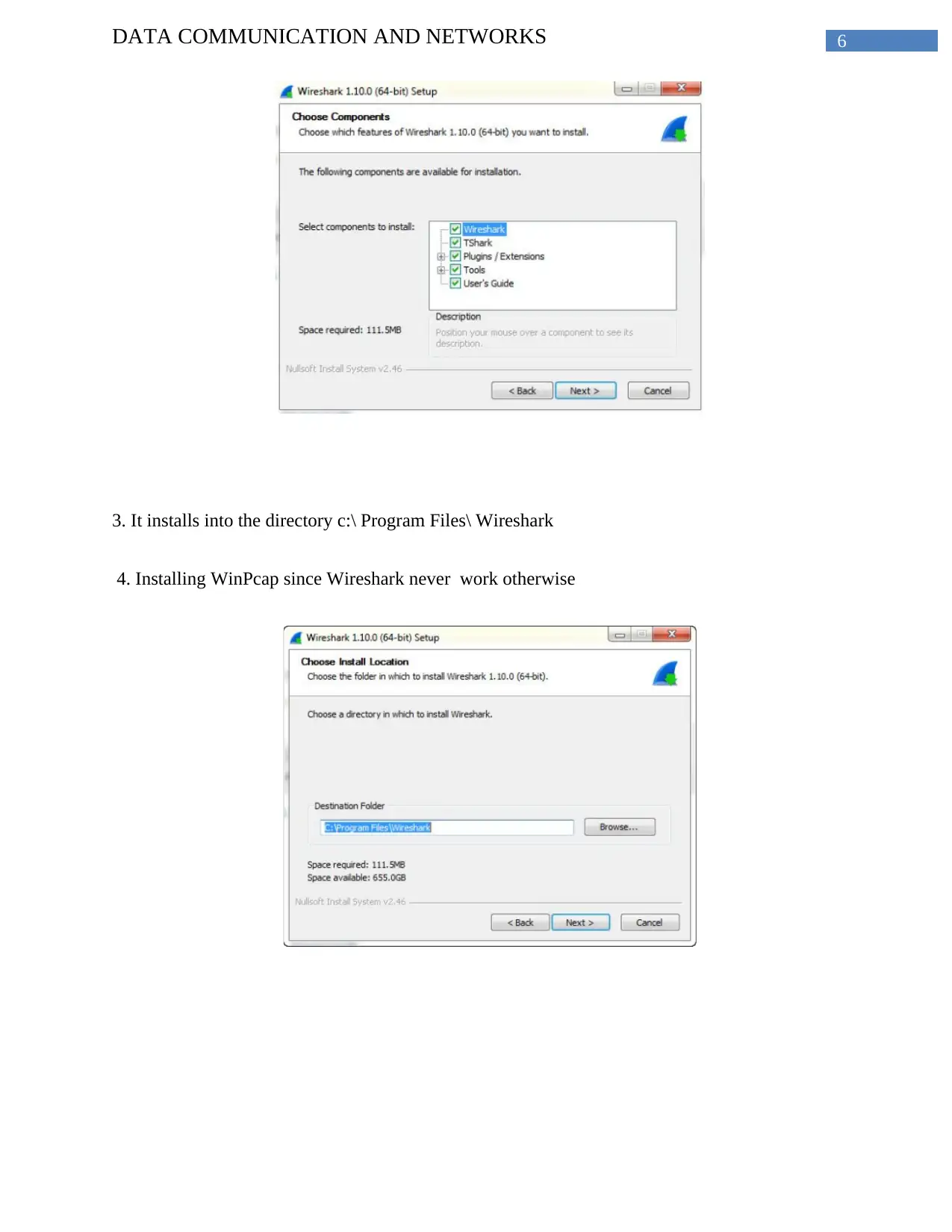
6DATA COMMUNICATION AND NETWORKS
3. It installs into the directory c:\ Program Files\ Wireshark
4. Installing WinPcap since Wireshark never work otherwise
3. It installs into the directory c:\ Program Files\ Wireshark
4. Installing WinPcap since Wireshark never work otherwise
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
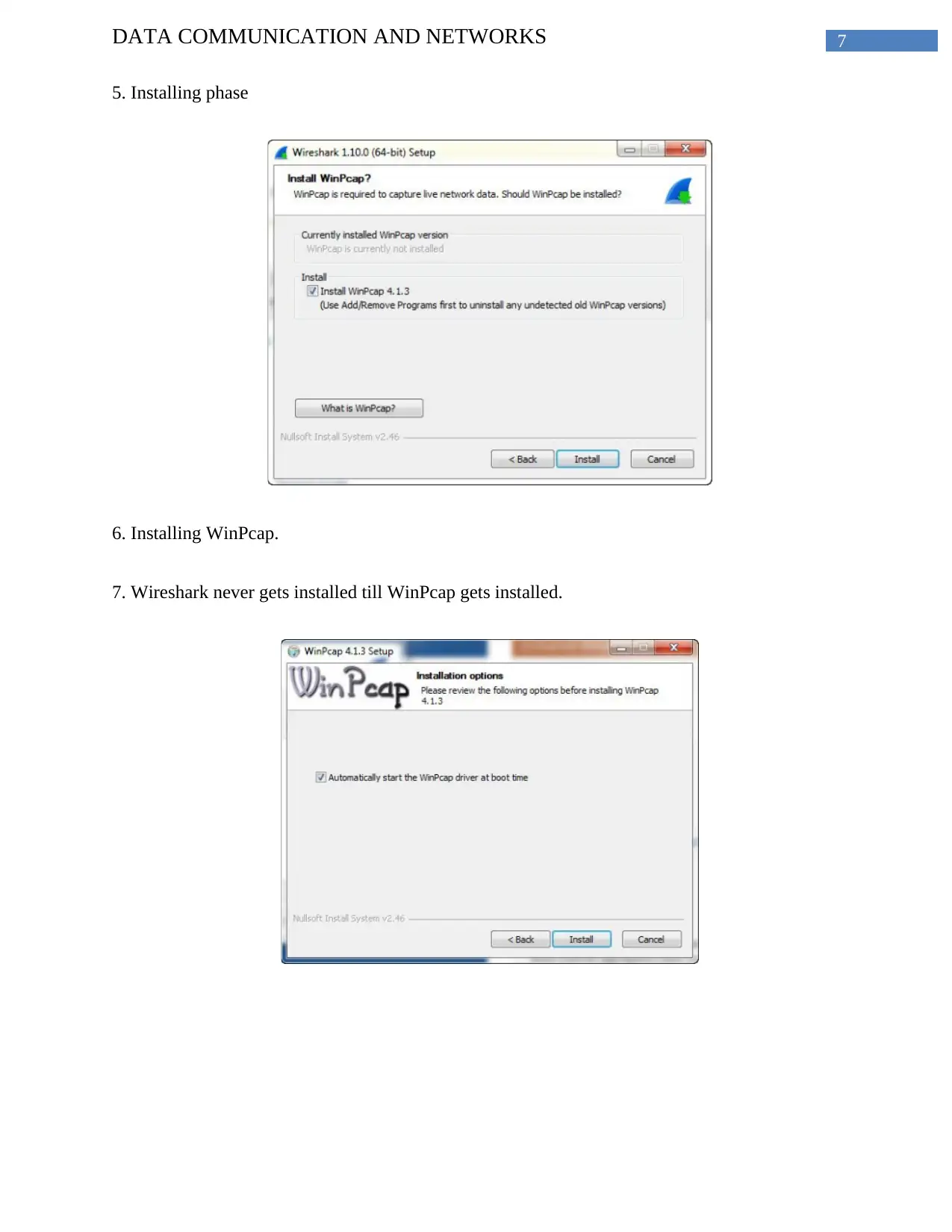
7DATA COMMUNICATION AND NETWORKS
5. Installing phase
6. Installing WinPcap.
7. Wireshark never gets installed till WinPcap gets installed.
5. Installing phase
6. Installing WinPcap.
7. Wireshark never gets installed till WinPcap gets installed.
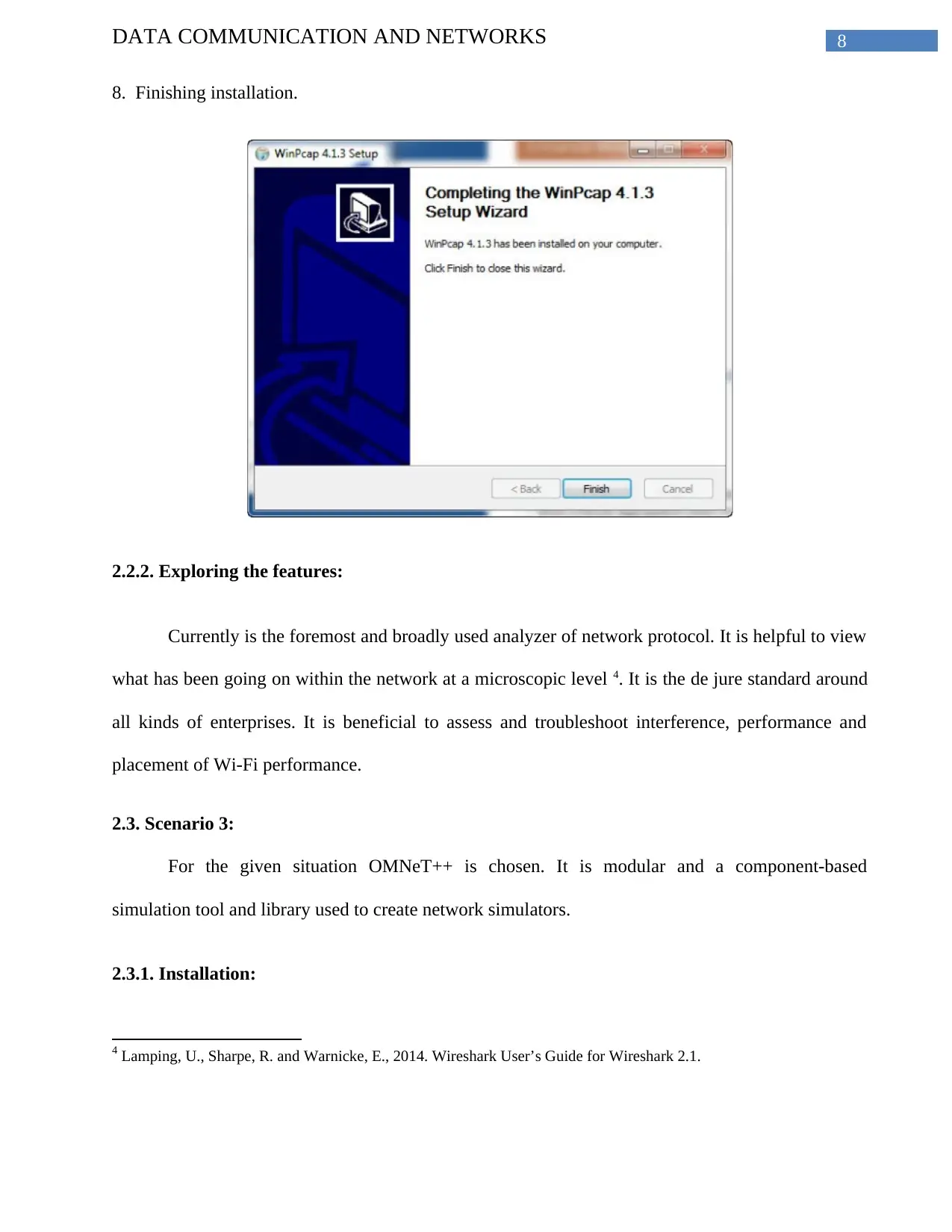
8DATA COMMUNICATION AND NETWORKS
8. Finishing installation.
2.2.2. Exploring the features:
Currently is the foremost and broadly used analyzer of network protocol. It is helpful to view
what has been going on within the network at a microscopic level 4. It is the de jure standard around
all kinds of enterprises. It is beneficial to assess and troubleshoot interference, performance and
placement of Wi-Fi performance.
2.3. Scenario 3:
For the given situation OMNeT++ is chosen. It is modular and a component-based
simulation tool and library used to create network simulators.
2.3.1. Installation:
4 Lamping, U., Sharpe, R. and Warnicke, E., 2014. Wireshark User’s Guide for Wireshark 2.1.
8. Finishing installation.
2.2.2. Exploring the features:
Currently is the foremost and broadly used analyzer of network protocol. It is helpful to view
what has been going on within the network at a microscopic level 4. It is the de jure standard around
all kinds of enterprises. It is beneficial to assess and troubleshoot interference, performance and
placement of Wi-Fi performance.
2.3. Scenario 3:
For the given situation OMNeT++ is chosen. It is modular and a component-based
simulation tool and library used to create network simulators.
2.3.1. Installation:
4 Lamping, U., Sharpe, R. and Warnicke, E., 2014. Wireshark User’s Guide for Wireshark 2.1.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DATA COMMUNICATION AND NETWORKS
Manual installation includes the following steps.
Downloading INET sources.
Unpacking it to directory of the choice: tar xvfz inet-<version>.tgz
Starting OMNet++ IDE and importing project through a file, import and existing projects
respectively to the workspace.
A project called INET appears.
Then the “project” is “build”.
2.3.2. Exploring the features:
To monitor networks the tool includes a broader sense of wired and wireless communication
networks. On-chip networks and queuing networks are also considered here 5. Moreover, it provides
domain-specific functionalities like ad-hoc wireless networks, sensor networks, performance
modeling, Internet protocols, photonic networks and many more.
5 Dubey, S. and Tripathi, N., 2015. Detection of Anomalous Behavior for Real Time Wide Area Network Traffic Using
Wireshark.
Manual installation includes the following steps.
Downloading INET sources.
Unpacking it to directory of the choice: tar xvfz inet-<version>.tgz
Starting OMNet++ IDE and importing project through a file, import and existing projects
respectively to the workspace.
A project called INET appears.
Then the “project” is “build”.
2.3.2. Exploring the features:
To monitor networks the tool includes a broader sense of wired and wireless communication
networks. On-chip networks and queuing networks are also considered here 5. Moreover, it provides
domain-specific functionalities like ad-hoc wireless networks, sensor networks, performance
modeling, Internet protocols, photonic networks and many more.
5 Dubey, S. and Tripathi, N., 2015. Detection of Anomalous Behavior for Real Time Wide Area Network Traffic Using
Wireshark.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10DATA COMMUNICATION AND NETWORKS
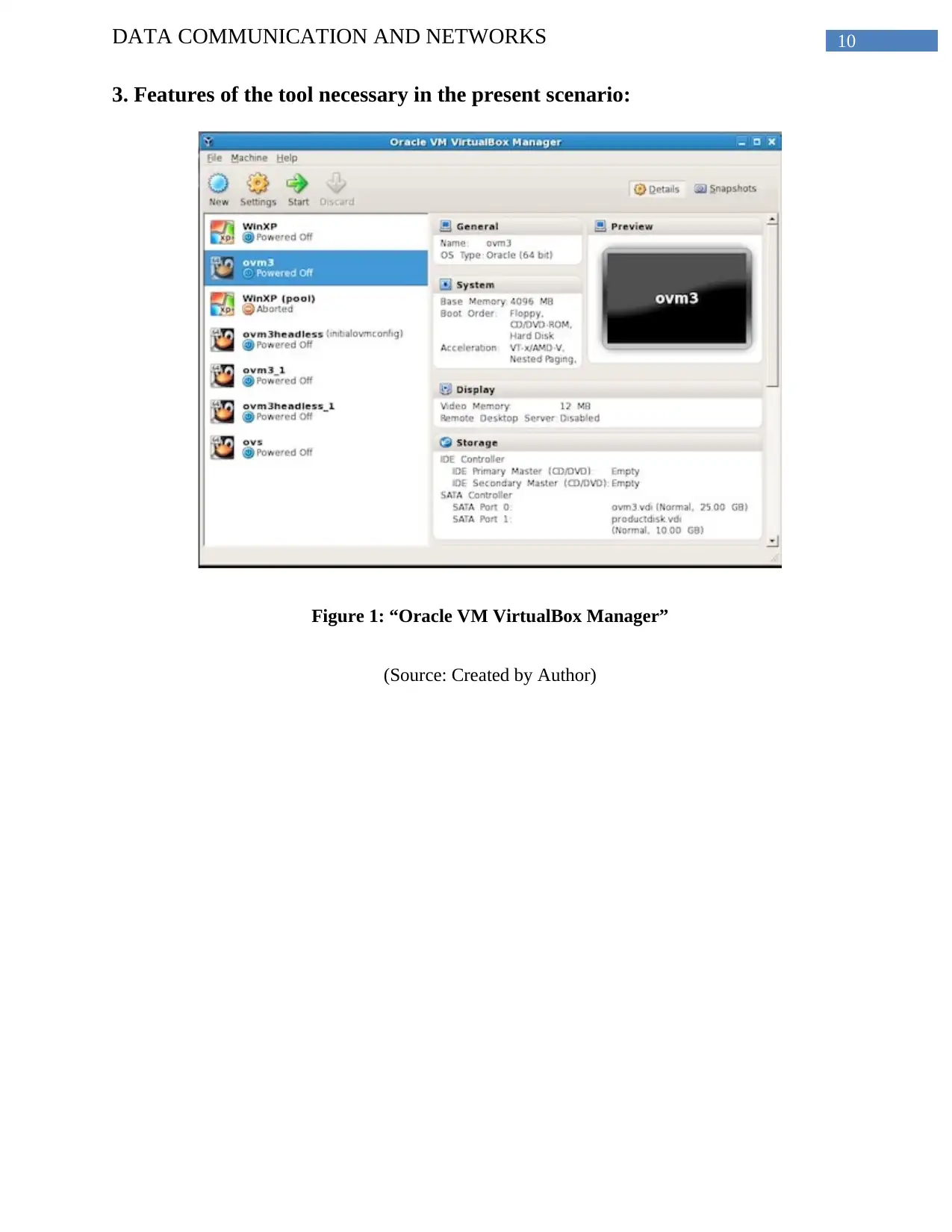
3. Features of the tool necessary in the present scenario:
Figure 1: “Oracle VM VirtualBox Manager”
(Source: Created by Author)
3. Features of the tool necessary in the present scenario:
Figure 1: “Oracle VM VirtualBox Manager”
(Source: Created by Author)
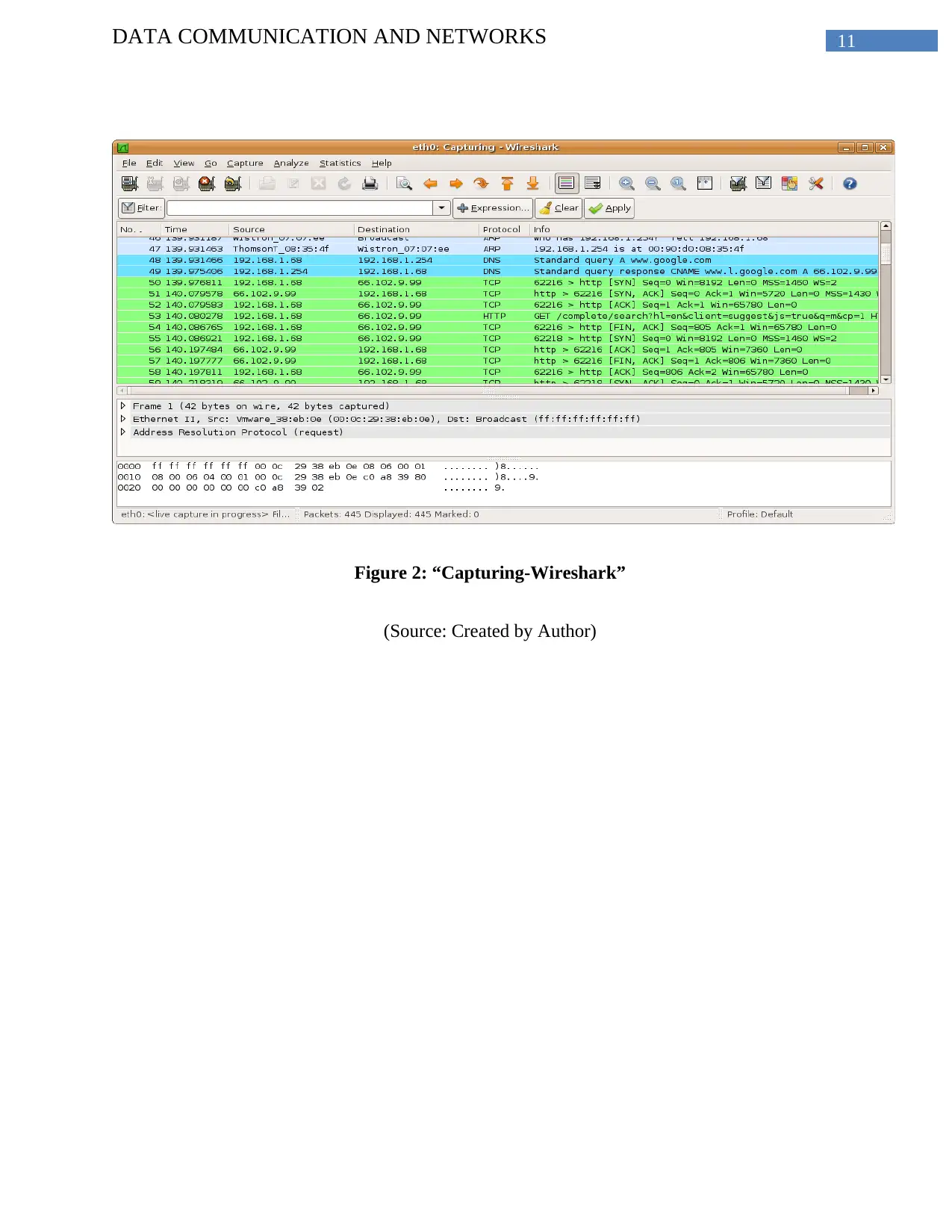
11DATA COMMUNICATION AND NETWORKS
Figure 2: “Capturing-Wireshark”
(Source: Created by Author)
Figure 2: “Capturing-Wireshark”
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.