University Data Communication and Networks Report Analysis
VerifiedAdded on 2020/05/28
|12
|1744
|66
Report
AI Summary
This report analyzes data communication and networks, focusing on the selection and justification of network monitoring tools for various scenarios. The report explores the features of the PRTG Network Monitor, a freeware tool, and how it can be applied to monitor data flow, identify the status of connected computers, and secure wireless access points. It provides screenshots of the tool's interface, illustrating its capabilities in QoS round trip monitoring, network security, and performance evaluation. The report justifies the choice of PRTG by comparing it to other available tools, highlighting its ability to monitor the entire network, analyze server health, and generate reports on network traffic and bandwidth usage. Furthermore, the report discusses the tool's effectiveness in addressing the three given scenarios, emphasizing its role in optimizing network connections, ensuring device availability, and evaluating network performance through QoS analysis. The conclusion summarizes the findings, emphasizing the importance of selecting appropriate tools for network fault identification, security, and performance optimization.

Running head: DATA COMMUNICATION AND NETWORKS
Data Communication and Networks
Name of the Student
Name of the University
Author’s Note
Data Communication and Networks
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
DATA COMMUNICATION AND NETWORKS
Table of Contents
Introduction..........................................................................................................................2
Tools’ features that are important for the scenarios............................................................2
Justification of the tool choice.............................................................................................7
Conclusion...........................................................................................................................9
Bibliography......................................................................................................................10
DATA COMMUNICATION AND NETWORKS
Table of Contents
Introduction..........................................................................................................................2
Tools’ features that are important for the scenarios............................................................2
Justification of the tool choice.............................................................................................7
Conclusion...........................................................................................................................9
Bibliography......................................................................................................................10

2
DATA COMMUNICATION AND NETWORKS
Introduction
The report is prepared after analysis of the three scenario and learning the principles of
data communication and networks. Research is made on the different tools that can be applied in
the organizational network for monitoring the data flow in the network and identification of the
status of each of the computers connected in the network. The wireless access point installed in
the network are also analyzed using the freeware tool for securing the network from illegal
access. An analysis is made on the freeware tool that can be implemented in the network for
evaluation of the performance by identification of the faults in the network and maintaining
quality of service. The justification of the tool applied for each of the scenario is given with the
screenshot of the tool interface that would help to understand the working of the tool used.
Tools’ features that are important for the scenarios
The features of the tools are described with the screenshots below:
DATA COMMUNICATION AND NETWORKS
Introduction
The report is prepared after analysis of the three scenario and learning the principles of
data communication and networks. Research is made on the different tools that can be applied in
the organizational network for monitoring the data flow in the network and identification of the
status of each of the computers connected in the network. The wireless access point installed in
the network are also analyzed using the freeware tool for securing the network from illegal
access. An analysis is made on the freeware tool that can be implemented in the network for
evaluation of the performance by identification of the faults in the network and maintaining
quality of service. The justification of the tool applied for each of the scenario is given with the
screenshot of the tool interface that would help to understand the working of the tool used.
Tools’ features that are important for the scenarios
The features of the tools are described with the screenshots below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
DATA COMMUNICATION AND NETWORKS
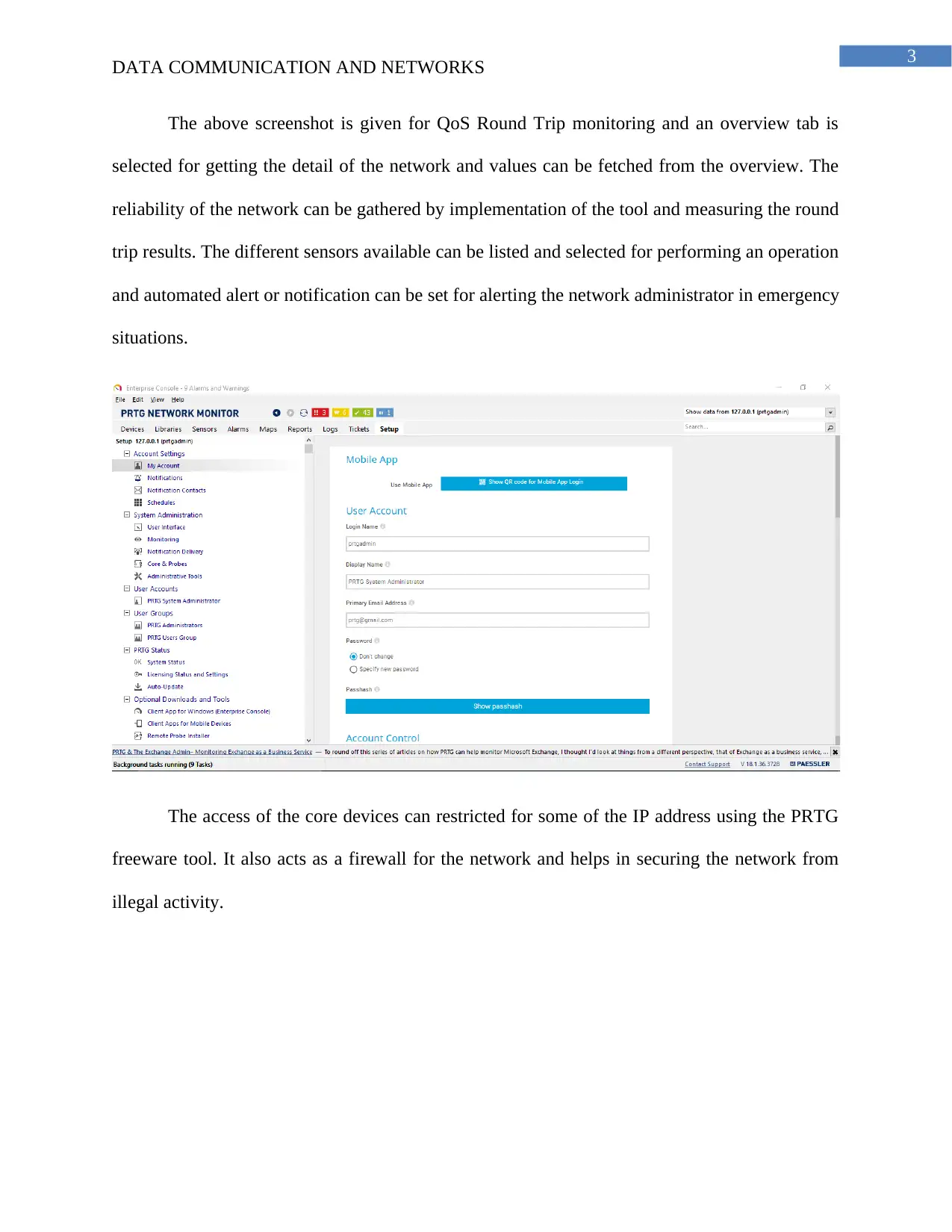
The above screenshot is given for QoS Round Trip monitoring and an overview tab is
selected for getting the detail of the network and values can be fetched from the overview. The
reliability of the network can be gathered by implementation of the tool and measuring the round
trip results. The different sensors available can be listed and selected for performing an operation
and automated alert or notification can be set for alerting the network administrator in emergency
situations.
The access of the core devices can restricted for some of the IP address using the PRTG
freeware tool. It also acts as a firewall for the network and helps in securing the network from
illegal activity.
DATA COMMUNICATION AND NETWORKS
The above screenshot is given for QoS Round Trip monitoring and an overview tab is
selected for getting the detail of the network and values can be fetched from the overview. The
reliability of the network can be gathered by implementation of the tool and measuring the round
trip results. The different sensors available can be listed and selected for performing an operation
and automated alert or notification can be set for alerting the network administrator in emergency
situations.
The access of the core devices can restricted for some of the IP address using the PRTG
freeware tool. It also acts as a firewall for the network and helps in securing the network from
illegal activity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
DATA COMMUNICATION AND NETWORKS
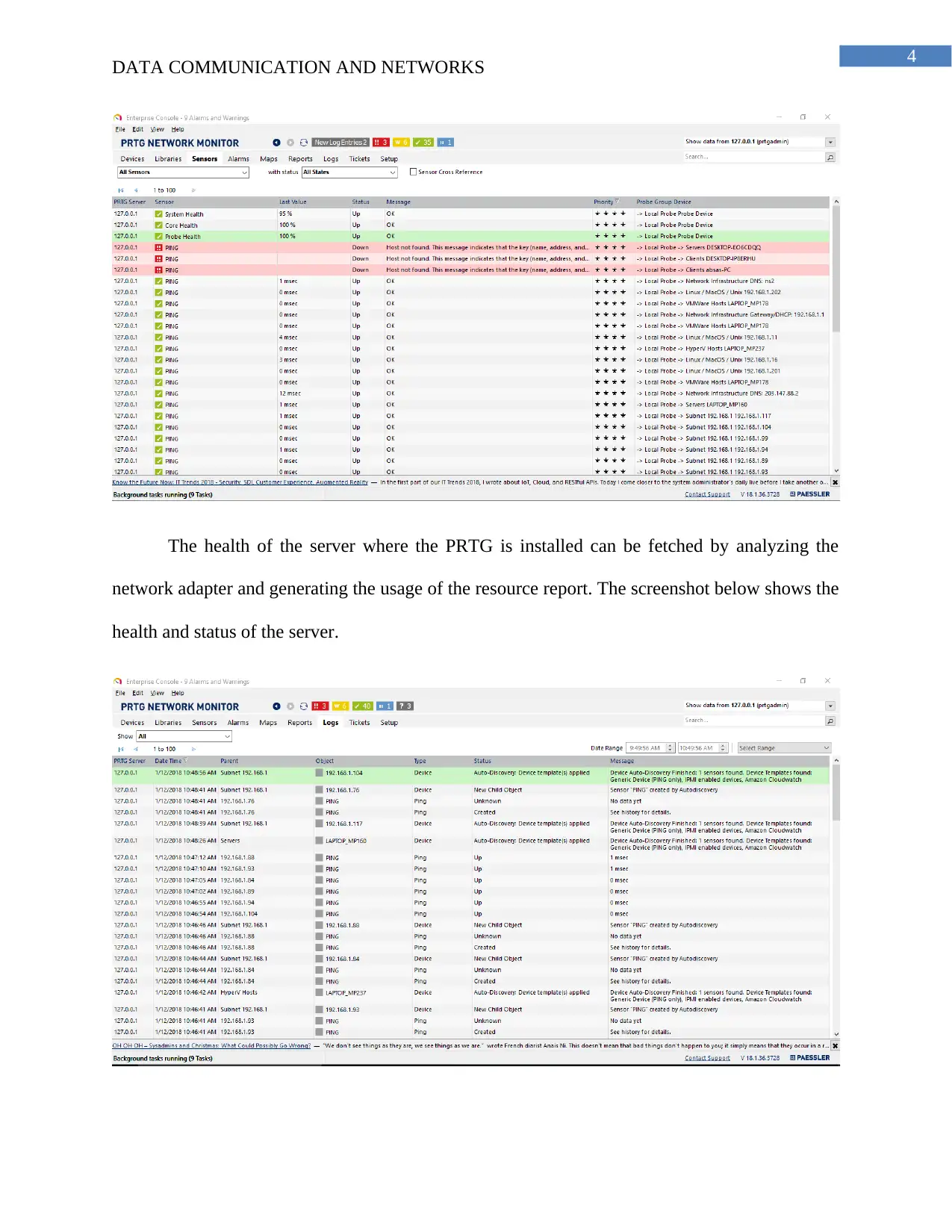
The health of the server where the PRTG is installed can be fetched by analyzing the
network adapter and generating the usage of the resource report. The screenshot below shows the
health and status of the server.
DATA COMMUNICATION AND NETWORKS
The health of the server where the PRTG is installed can be fetched by analyzing the
network adapter and generating the usage of the resource report. The screenshot below shows the
health and status of the server.
5
DATA COMMUNICATION AND NETWORKS
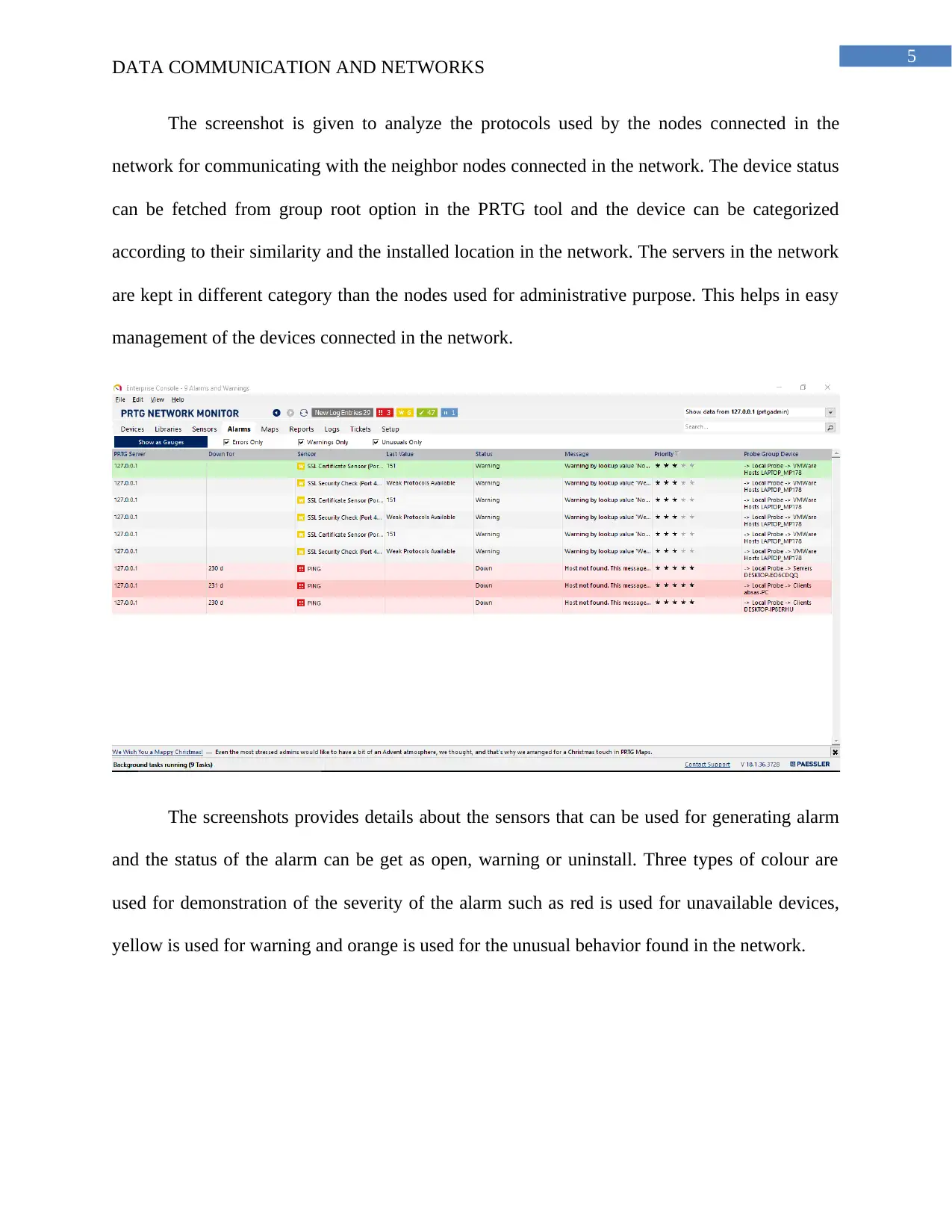
The screenshot is given to analyze the protocols used by the nodes connected in the
network for communicating with the neighbor nodes connected in the network. The device status
can be fetched from group root option in the PRTG tool and the device can be categorized
according to their similarity and the installed location in the network. The servers in the network
are kept in different category than the nodes used for administrative purpose. This helps in easy
management of the devices connected in the network.
The screenshots provides details about the sensors that can be used for generating alarm
and the status of the alarm can be get as open, warning or uninstall. Three types of colour are
used for demonstration of the severity of the alarm such as red is used for unavailable devices,
yellow is used for warning and orange is used for the unusual behavior found in the network.
DATA COMMUNICATION AND NETWORKS
The screenshot is given to analyze the protocols used by the nodes connected in the
network for communicating with the neighbor nodes connected in the network. The device status
can be fetched from group root option in the PRTG tool and the device can be categorized
according to their similarity and the installed location in the network. The servers in the network
are kept in different category than the nodes used for administrative purpose. This helps in easy
management of the devices connected in the network.
The screenshots provides details about the sensors that can be used for generating alarm
and the status of the alarm can be get as open, warning or uninstall. Three types of colour are
used for demonstration of the severity of the alarm such as red is used for unavailable devices,
yellow is used for warning and orange is used for the unusual behavior found in the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
DATA COMMUNICATION AND NETWORKS
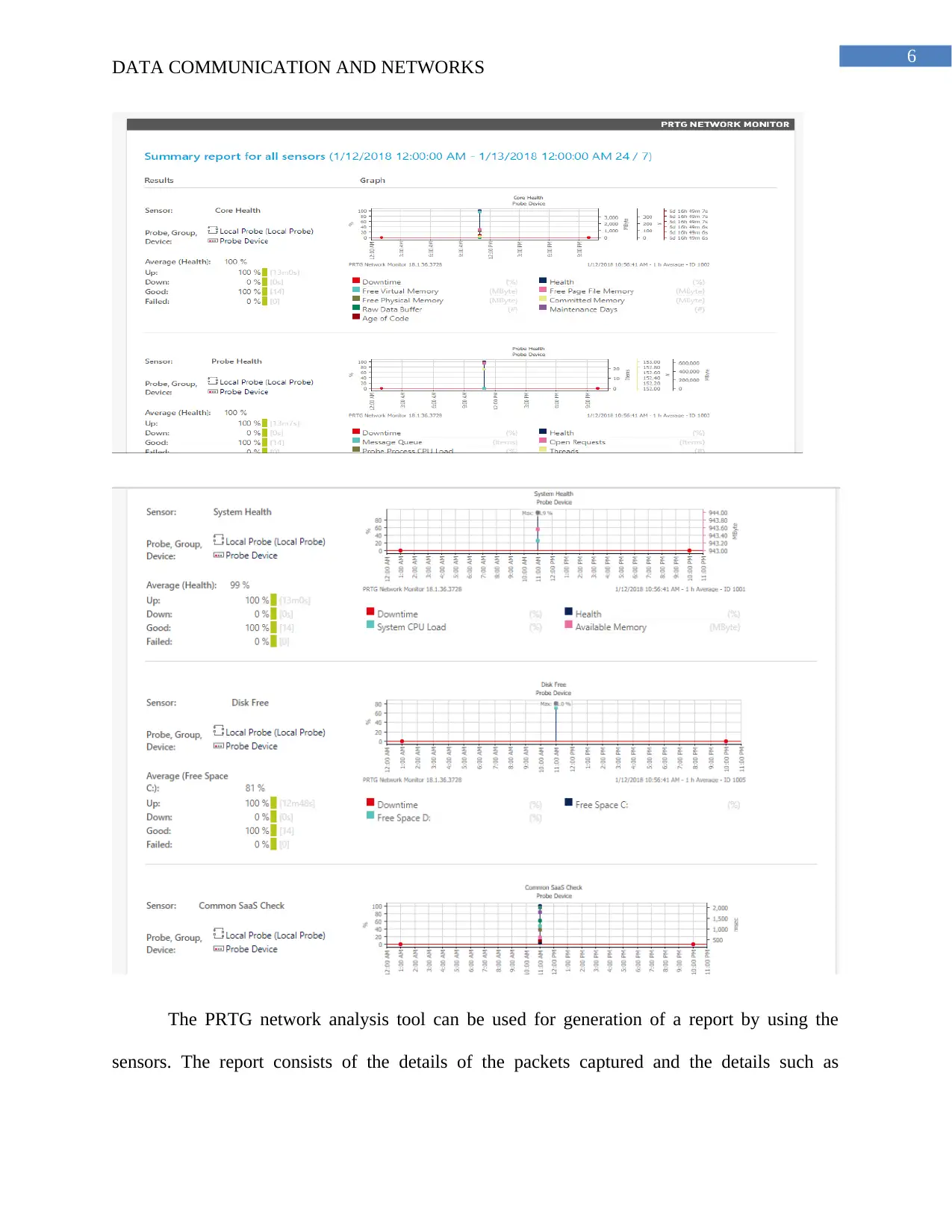
The PRTG network analysis tool can be used for generation of a report by using the
sensors. The report consists of the details of the packets captured and the details such as
DATA COMMUNICATION AND NETWORKS
The PRTG network analysis tool can be used for generation of a report by using the
sensors. The report consists of the details of the packets captured and the details such as
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
DATA COMMUNICATION AND NETWORKS
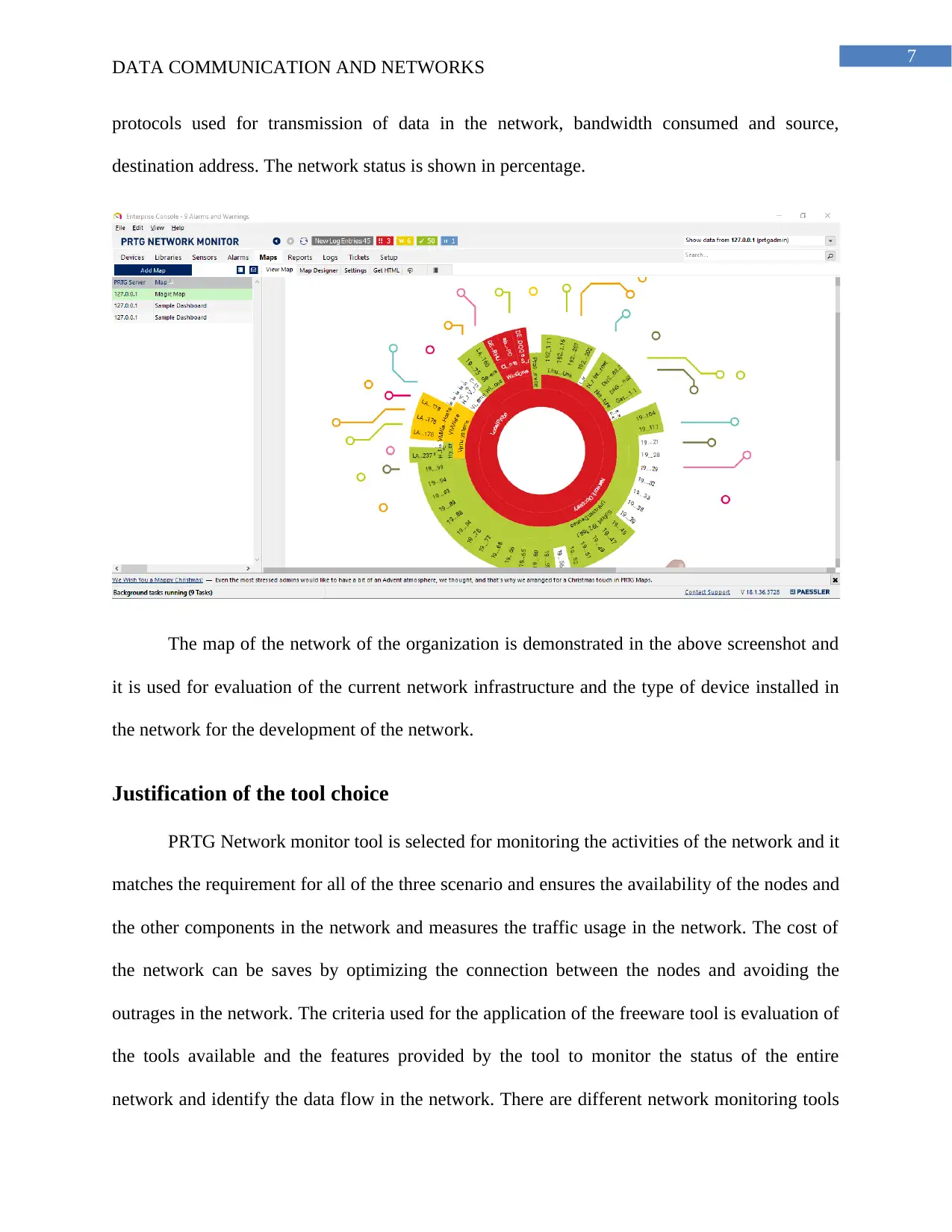
protocols used for transmission of data in the network, bandwidth consumed and source,
destination address. The network status is shown in percentage.
The map of the network of the organization is demonstrated in the above screenshot and
it is used for evaluation of the current network infrastructure and the type of device installed in
the network for the development of the network.
Justification of the tool choice
PRTG Network monitor tool is selected for monitoring the activities of the network and it
matches the requirement for all of the three scenario and ensures the availability of the nodes and
the other components in the network and measures the traffic usage in the network. The cost of
the network can be saves by optimizing the connection between the nodes and avoiding the
outrages in the network. The criteria used for the application of the freeware tool is evaluation of
the tools available and the features provided by the tool to monitor the status of the entire
network and identify the data flow in the network. There are different network monitoring tools
DATA COMMUNICATION AND NETWORKS
protocols used for transmission of data in the network, bandwidth consumed and source,
destination address. The network status is shown in percentage.
The map of the network of the organization is demonstrated in the above screenshot and
it is used for evaluation of the current network infrastructure and the type of device installed in
the network for the development of the network.
Justification of the tool choice
PRTG Network monitor tool is selected for monitoring the activities of the network and it
matches the requirement for all of the three scenario and ensures the availability of the nodes and
the other components in the network and measures the traffic usage in the network. The cost of
the network can be saves by optimizing the connection between the nodes and avoiding the
outrages in the network. The criteria used for the application of the freeware tool is evaluation of
the tools available and the features provided by the tool to monitor the status of the entire
network and identify the data flow in the network. There are different network monitoring tools

8
DATA COMMUNICATION AND NETWORKS
available and the features are compared with each other for the selection of the best network
monitoring tool and application in the network for management of the activities of the users. The
PRTG can be installed in the central server of a network for analyzing the health of the server,
throughput and the network traffic. It can also be used for analyzing the current drawn for each
of the circuit. It can be used for creation of a group and more device can be added in the group
and the auto discovery function of the tool helps in creation of an alert for grabbing the attention
of the network administrator.
The PRTG can be installed in the central server and used for all the three scenario and
monitor the activity in the network irrespective of the medium such as wired or wireless
connection. For the wireless network its status should be maintained and the WiFi analyzer the
freeware tool PRTG network monitor analyzes every aspects such as devices, availability, traffic,
load and the signal strengths of the wireless network. SNMP sensors can be deployed in the
network for monitoring the security instance of the network and it also uses packet sniffing and
NetFlow for monitoring the wifi traffic. It supports Cisco as well as the Juniper routers and thus
it is reliable for fast and easy wireless monitoring. It can be used as a central monitoring tool for
the wireless access points installed at different location of a network and monitor the bandwidth
and the devices connected in the network. The dashboard of the PRTG can be used for getting a
quick overview and it comes with 200 predefined sensors that can save energy for monitoring the
wireless network. If an abnormal activity is identified in the network the PRTG prompts an alert
for the disruption and prevents the network from crashing.
For the third scenario the PRTG is an ideal solution because it can be used for the
evaluation of the performance and QoS evaluation of the network. The PRTG provides real time
monitoring of the bandwidth usage uses QoS round trip sensor for analyzing the data packets
DATA COMMUNICATION AND NETWORKS
available and the features are compared with each other for the selection of the best network
monitoring tool and application in the network for management of the activities of the users. The
PRTG can be installed in the central server of a network for analyzing the health of the server,
throughput and the network traffic. It can also be used for analyzing the current drawn for each
of the circuit. It can be used for creation of a group and more device can be added in the group
and the auto discovery function of the tool helps in creation of an alert for grabbing the attention
of the network administrator.
The PRTG can be installed in the central server and used for all the three scenario and
monitor the activity in the network irrespective of the medium such as wired or wireless
connection. For the wireless network its status should be maintained and the WiFi analyzer the
freeware tool PRTG network monitor analyzes every aspects such as devices, availability, traffic,
load and the signal strengths of the wireless network. SNMP sensors can be deployed in the
network for monitoring the security instance of the network and it also uses packet sniffing and
NetFlow for monitoring the wifi traffic. It supports Cisco as well as the Juniper routers and thus
it is reliable for fast and easy wireless monitoring. It can be used as a central monitoring tool for
the wireless access points installed at different location of a network and monitor the bandwidth
and the devices connected in the network. The dashboard of the PRTG can be used for getting a
quick overview and it comes with 200 predefined sensors that can save energy for monitoring the
wireless network. If an abnormal activity is identified in the network the PRTG prompts an alert
for the disruption and prevents the network from crashing.
For the third scenario the PRTG is an ideal solution because it can be used for the
evaluation of the performance and QoS evaluation of the network. The PRTG provides real time
monitoring of the bandwidth usage uses QoS round trip sensor for analyzing the data packets
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
DATA COMMUNICATION AND NETWORKS
passing over the network. The QoS round trip sensor works by sending many UDP packets in the
network and measures the result by analyzing the packets lost, packets duplicated, packets out
order, packets corrupted, delay and jitter. This helps in building a network minimizing the errors
in the network and increasing the quality of service.
Conclusion
For the selection of the freeware devices different available tools are analyzed according
to the scenario and applied in the network for meeting the criteria. The use of the PRTG network
analyzer helps in ident6ifiaction of the fault of the network and the security protocols used for
the configuration of the devices. The data flow between the devices can also be identified for
monitoring the performance of the network and maintaining the network quality. The network
protocol analyzer can also be used for securing the wireless access points installed in different
location of the network by analyzing the unauthorized access and using secure security
mechanism for restricting the unauthorized users to access the wireless devices. There are
different sensors available that is useful for the identification of the jitter and the loss of data
packets in the network.
DATA COMMUNICATION AND NETWORKS
passing over the network. The QoS round trip sensor works by sending many UDP packets in the
network and measures the result by analyzing the packets lost, packets duplicated, packets out
order, packets corrupted, delay and jitter. This helps in building a network minimizing the errors
in the network and increasing the quality of service.
Conclusion
For the selection of the freeware devices different available tools are analyzed according
to the scenario and applied in the network for meeting the criteria. The use of the PRTG network
analyzer helps in ident6ifiaction of the fault of the network and the security protocols used for
the configuration of the devices. The data flow between the devices can also be identified for
monitoring the performance of the network and maintaining the network quality. The network
protocol analyzer can also be used for securing the wireless access points installed in different
location of the network by analyzing the unauthorized access and using secure security
mechanism for restricting the unauthorized users to access the wireless devices. There are
different sensors available that is useful for the identification of the jitter and the loss of data
packets in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
DATA COMMUNICATION AND NETWORKS
Bibliography
Akkaya, K., Guvenc, I., Aygun, R., Pala, N. and Kadri, A., 2015, March. IoT-based occupancy
monitoring techniques for energy-efficient smart buildings. In Wireless Communications and
Networking Conference Workshops (WCNCW), 2015 IEEE (pp. 58-63). IEEE.
Alhamazani, K., Ranjan, R., Mitra, K., Rabhi, F., Jayaraman, P.P., Khan, S.U., Guabtni, A. and
Bhatnagar, V., 2015. An overview of the commercial cloud monitoring tools: research
dimensions, design issues, and state-of-the-art. Computing, 97(4), pp.357-377.
Campos Filho, A.S., Novaes, M.A. and Gomes, A.S., 2015. A 3D visualization framework to
social network monitoring and analysis. Computers in Human Behavior, 49, pp.623-634.
Paessler.com. (2018). Congrats! This is Your Free License Key for PRTG Network Monitor.
[online] Available at: https://www.paessler.com/download/prtg-download [Accessed 12 Jan.
2018].
Prendergast, L.J. and Gavin, K., 2014. A review of bridge scour monitoring techniques. Journal
of Rock Mechanics and Geotechnical Engineering, 6(2), pp.138-149.
Thakur, P., Kumar, A., Pandit, S., Singh, G. and Satashia, S.N., 2016, December. Performance
improvement of cognitive radio network using spectrum prediction and monitoring techniques
for spectrum mobility. In Parallel, Distributed and Grid Computing (PDGC), 2016 Fourth
International Conference on (pp. 679-684). IEEE.
Van Adrichem, N.L., Doerr, C. and Kuipers, F.A., 2014, May. Opennetmon: Network
monitoring in openflow software-defined networks. In Network Operations and Management
Symposium (NOMS), 2014 IEEE (pp. 1-8). IEEE.
DATA COMMUNICATION AND NETWORKS
Bibliography
Akkaya, K., Guvenc, I., Aygun, R., Pala, N. and Kadri, A., 2015, March. IoT-based occupancy
monitoring techniques for energy-efficient smart buildings. In Wireless Communications and
Networking Conference Workshops (WCNCW), 2015 IEEE (pp. 58-63). IEEE.
Alhamazani, K., Ranjan, R., Mitra, K., Rabhi, F., Jayaraman, P.P., Khan, S.U., Guabtni, A. and
Bhatnagar, V., 2015. An overview of the commercial cloud monitoring tools: research
dimensions, design issues, and state-of-the-art. Computing, 97(4), pp.357-377.
Campos Filho, A.S., Novaes, M.A. and Gomes, A.S., 2015. A 3D visualization framework to
social network monitoring and analysis. Computers in Human Behavior, 49, pp.623-634.
Paessler.com. (2018). Congrats! This is Your Free License Key for PRTG Network Monitor.
[online] Available at: https://www.paessler.com/download/prtg-download [Accessed 12 Jan.
2018].
Prendergast, L.J. and Gavin, K., 2014. A review of bridge scour monitoring techniques. Journal
of Rock Mechanics and Geotechnical Engineering, 6(2), pp.138-149.
Thakur, P., Kumar, A., Pandit, S., Singh, G. and Satashia, S.N., 2016, December. Performance
improvement of cognitive radio network using spectrum prediction and monitoring techniques
for spectrum mobility. In Parallel, Distributed and Grid Computing (PDGC), 2016 Fourth
International Conference on (pp. 679-684). IEEE.
Van Adrichem, N.L., Doerr, C. and Kuipers, F.A., 2014, May. Opennetmon: Network
monitoring in openflow software-defined networks. In Network Operations and Management
Symposium (NOMS), 2014 IEEE (pp. 1-8). IEEE.

11
DATA COMMUNICATION AND NETWORKS
Ventre, P.L., Caponi, A., Siracusano, G., Palmisano, D., Salsano, S., Bonola, M. and Bianchi, G.,
2017, June. D-STREAMON: from middlebox to distributed NFV framework for network
monitoring. In Local and Metropolitan Area Networks (LANMAN), 2017 IEEE International
Symposium on(pp. 1-2). IEEE.
DATA COMMUNICATION AND NETWORKS
Ventre, P.L., Caponi, A., Siracusano, G., Palmisano, D., Salsano, S., Bonola, M. and Bianchi, G.,
2017, June. D-STREAMON: from middlebox to distributed NFV framework for network
monitoring. In Local and Metropolitan Area Networks (LANMAN), 2017 IEEE International
Symposium on(pp. 1-2). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





