Data Communication: Network Stack Layers and Boolean Operation Drills
VerifiedAdded on 2023/06/14
|11
|1805
|144
Homework Assignment
AI Summary
This assignment solution provides a comprehensive overview of data communication concepts, focusing on the importance of different layers within the network stack, including the physical, data link, and internet layers. It details how each layer contributes to error-free, robust, and reliable communication through various techniques such as line coding, carrier collision detection, signal equalization, and traffic control. The solution also includes practical drills on boolean operations with bit patterns and subnet mask calculations, demonstrating the application of these concepts in network management. Furthermore, it differentiates between controlled access and contention-based access methods to physical mediums. Desklib offers this assignment, along with a wealth of other solved assignments and past papers, to aid students in their studies.

Running head: DATA COMMUNICATIONS
DATA COMMUNICATIONS
Name of the student:
Name of the university:
Author note:
DATA COMMUNICATIONS
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA COMMUNICATIONS
Question 1 - Network Stack
Importance of Physical layer:
The physical layer refers to the first layer of the Open System Interconnection
Model or the OSI model. The bit-level transmission is managed in this layer. Transmission
between physical devices is controlled by this layer. The mechanical or electrical interface that is
needed for the communication between the communicating devices is also provided by this layer
(Chen et al. 2015).
The layer is responsible for dealing with the various physical connections that the
network needs for data communication. It includes the wireless transmission, cabling standards,
various types of connectors, interface cards and many more as needed by the network (Goseling,
Gastpar and Weber 2015).
Error free communication:
The data that hardware devices generate are optimized by the layer to make it suitable
for digital communication. Without the optimization the data will communication may not be
effective due to discrete timing over the network. This optimization of data timing to make it
suitable for the transmissions makes the communication error free. The optimization is done
using the line coding technique (Zou et al. 2015). The layer also allows for interleaving of bits
which helps to improve the error correction.
Question 1 - Network Stack
Importance of Physical layer:
The physical layer refers to the first layer of the Open System Interconnection
Model or the OSI model. The bit-level transmission is managed in this layer. Transmission
between physical devices is controlled by this layer. The mechanical or electrical interface that is
needed for the communication between the communicating devices is also provided by this layer
(Chen et al. 2015).
The layer is responsible for dealing with the various physical connections that the
network needs for data communication. It includes the wireless transmission, cabling standards,
various types of connectors, interface cards and many more as needed by the network (Goseling,
Gastpar and Weber 2015).
Error free communication:
The data that hardware devices generate are optimized by the layer to make it suitable
for digital communication. Without the optimization the data will communication may not be
effective due to discrete timing over the network. This optimization of data timing to make it
suitable for the transmissions makes the communication error free. The optimization is done
using the line coding technique (Zou et al. 2015). The layer also allows for interleaving of bits
which helps to improve the error correction.

2DATA COMMUNICATIONS
Robust communication:
The layer helps to detect the carrier collision. It can sense if there are sufficient carrier
is available for data communications and this helps to avoid carrier congestion created due to the
data packets undelivered for unavailability of data carriers and thus ensures robust
communication (Kapetanovic, Zheng and Rusek 2015).
Reliable communication:
The layer with the help of Signal equalization and multiplexing technique helps in
ensuring reliable communication (Mukherjee et al. 2014).
Robust communication:
The layer helps to detect the carrier collision. It can sense if there are sufficient carrier
is available for data communications and this helps to avoid carrier congestion created due to the
data packets undelivered for unavailability of data carriers and thus ensures robust
communication (Kapetanovic, Zheng and Rusek 2015).
Reliable communication:
The layer with the help of Signal equalization and multiplexing technique helps in
ensuring reliable communication (Mukherjee et al. 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DATA COMMUNICATIONS
Importance of Data-Link layer:
The data link layer is the second layer in the seven layer OSI model. It helps to
connect two nodes that are involved in the data communication. The connection is made using
the logical link. The link that is established between the nodes is also terminated by the layer
once the communication is completed (Marquardt 2017).
Ease of communication:
The layer provides end-to-end message delivery with proper acknowledgement of
message delivery, thus ensures ease of communication (Cui , Yu and Yan 2016).
Error free communication:
In order to ensure error free transmission the layer control the traffic generated by the
data frame. It communicate with the transmission node for telling it to “back -off” when there is
no availability of buffer message (Kizza 2017).
Robust communication:
The layer helps in detecting the any errors occurred in the physical layers and based
on that the errors are acknowledged and again retransmitted by rectifying the errors and making
necessary correction. Thus ensures error free and robust communication (Ding and Jiang 2016).
Importance for lower layers:
The data link layer helps in error-free data transmission between the nodes with proper
control over the physical layer that resides bellow the data link layer in the OSI model. The error
free transmission helps layers above it in assuming transmission which is virtually error free
(Zafar and Ejaz 2016).
Importance of Data-Link layer:
The data link layer is the second layer in the seven layer OSI model. It helps to
connect two nodes that are involved in the data communication. The connection is made using
the logical link. The link that is established between the nodes is also terminated by the layer
once the communication is completed (Marquardt 2017).
Ease of communication:
The layer provides end-to-end message delivery with proper acknowledgement of
message delivery, thus ensures ease of communication (Cui , Yu and Yan 2016).
Error free communication:
In order to ensure error free transmission the layer control the traffic generated by the
data frame. It communicate with the transmission node for telling it to “back -off” when there is
no availability of buffer message (Kizza 2017).
Robust communication:
The layer helps in detecting the any errors occurred in the physical layers and based
on that the errors are acknowledged and again retransmitted by rectifying the errors and making
necessary correction. Thus ensures error free and robust communication (Ding and Jiang 2016).
Importance for lower layers:
The data link layer helps in error-free data transmission between the nodes with proper
control over the physical layer that resides bellow the data link layer in the OSI model. The error
free transmission helps layers above it in assuming transmission which is virtually error free
(Zafar and Ejaz 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DATA COMMUNICATIONS

5DATA COMMUNICATIONS
Importance of internet layers:
The internet layer lies above the physical and data link layer. The layer plays an
important role in data communication and also helps in managing the layers below it (Blekneni
et al. 2016).
Error free communication:
The layer helps in controlling the subnet traffic. Whenever the any router in this layer
exceeds the buffer limit the layer sends an instruction to the transmission station to hold on the
transmission to avoid error in data communication (Qadir et al. 2015).
Robust communication:
The layer allows for frame fragmentation that helps in determining the maximum
transmission unit or the MTU for the router that is used for the downstream communication. It
checks if the data fragment size is less or greater than the transmission unit size. In case the
fragment size is greater than the transmission unit size, then fragmentation is done on the data
frame and at the time of receiving the data at the destination site the data is again reassembled to
keep the data integrity and robustness of the system (Kalakech 2016).
Importance for lower layers:
The network layer control how the subnet will operate. It decides the allocation of the
physical path for the data communication to take place to facilitate the network conditions and
the service priority. The data link layer acts as an interface between the physical layer and
network layer (Garman and Sherman 2015). The data link layer with the help of the network
layer helps for smooth operation of the physical layer by proper resource allocation of the
Importance of internet layers:
The internet layer lies above the physical and data link layer. The layer plays an
important role in data communication and also helps in managing the layers below it (Blekneni
et al. 2016).
Error free communication:
The layer helps in controlling the subnet traffic. Whenever the any router in this layer
exceeds the buffer limit the layer sends an instruction to the transmission station to hold on the
transmission to avoid error in data communication (Qadir et al. 2015).
Robust communication:
The layer allows for frame fragmentation that helps in determining the maximum
transmission unit or the MTU for the router that is used for the downstream communication. It
checks if the data fragment size is less or greater than the transmission unit size. In case the
fragment size is greater than the transmission unit size, then fragmentation is done on the data
frame and at the time of receiving the data at the destination site the data is again reassembled to
keep the data integrity and robustness of the system (Kalakech 2016).
Importance for lower layers:
The network layer control how the subnet will operate. It decides the allocation of the
physical path for the data communication to take place to facilitate the network conditions and
the service priority. The data link layer acts as an interface between the physical layer and
network layer (Garman and Sherman 2015). The data link layer with the help of the network
layer helps for smooth operation of the physical layer by proper resource allocation of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DATA COMMUNICATIONS
physical layer entities allowing for robust and error free execution of the physical layer
components with proper resource management
Question 2 - Drills:
a) Boolean operation on bit patterns:
i. not 0010111000101100 : 1101000111010011
ii. 0010111000101100 or 1110000011100001: 1110111011101100
iii. 0010111000101100 and 1110000011100001: 10000000100000
iv. 1100111000111011 and 0110111100011100: 100111000011000
b) What are the subnet masks for the following slash address blocks
Slash address blocks Subnet masks
/8 255.0.0.0
/15 255.254.0.0
physical layer entities allowing for robust and error free execution of the physical layer
components with proper resource management
Question 2 - Drills:
a) Boolean operation on bit patterns:
i. not 0010111000101100 : 1101000111010011
ii. 0010111000101100 or 1110000011100001: 1110111011101100
iii. 0010111000101100 and 1110000011100001: 10000000100000
iv. 1100111000111011 and 0110111100011100: 100111000011000
b) What are the subnet masks for the following slash address blocks
Slash address blocks Subnet masks
/8 255.0.0.0
/15 255.254.0.0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7DATA COMMUNICATIONS
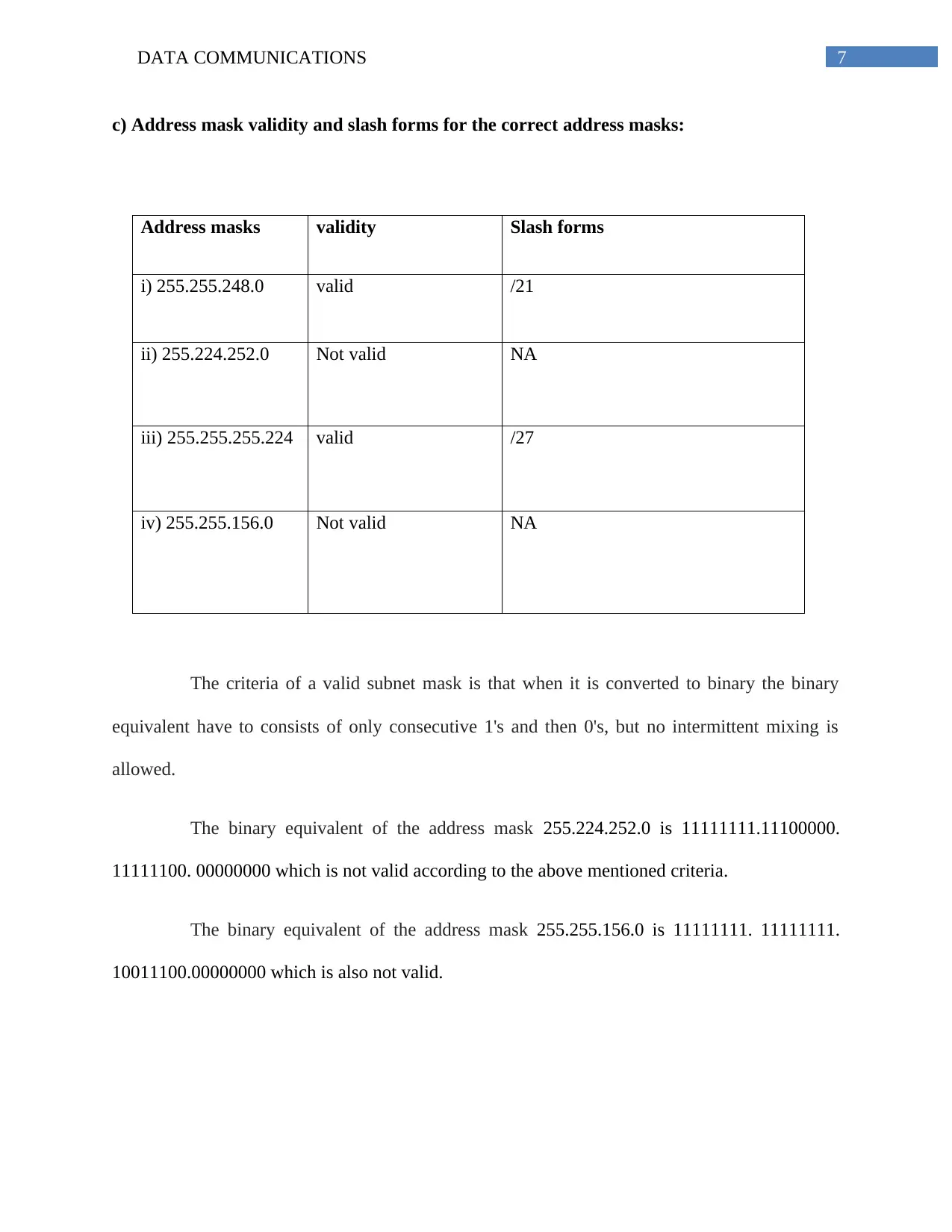
c) Address mask validity and slash forms for the correct address masks:
Address masks validity Slash forms
i) 255.255.248.0 valid /21
ii) 255.224.252.0 Not valid NA
iii) 255.255.255.224 valid /27
iv) 255.255.156.0 Not valid NA
The criteria of a valid subnet mask is that when it is converted to binary the binary
equivalent have to consists of only consecutive 1's and then 0's, but no intermittent mixing is
allowed.
The binary equivalent of the address mask 255.224.252.0 is 11111111.11100000.
11111100. 00000000 which is not valid according to the above mentioned criteria.
The binary equivalent of the address mask 255.255.156.0 is 11111111. 11111111.
10011100.00000000 which is also not valid.
c) Address mask validity and slash forms for the correct address masks:
Address masks validity Slash forms
i) 255.255.248.0 valid /21
ii) 255.224.252.0 Not valid NA
iii) 255.255.255.224 valid /27
iv) 255.255.156.0 Not valid NA
The criteria of a valid subnet mask is that when it is converted to binary the binary
equivalent have to consists of only consecutive 1's and then 0's, but no intermittent mixing is
allowed.
The binary equivalent of the address mask 255.224.252.0 is 11111111.11100000.
11111100. 00000000 which is not valid according to the above mentioned criteria.
The binary equivalent of the address mask 255.255.156.0 is 11111111. 11111111.
10011100.00000000 which is also not valid.
8DATA COMMUNICATIONS
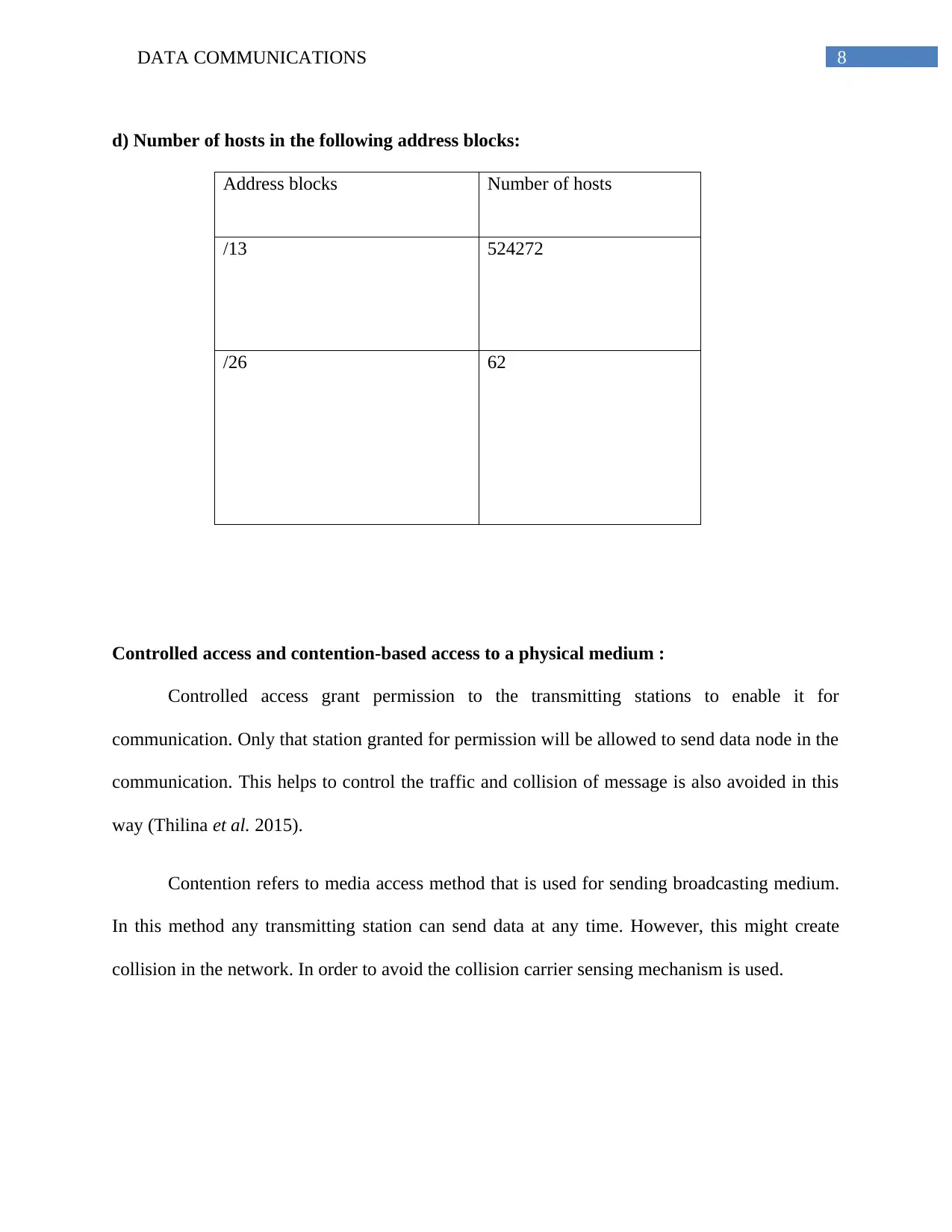
d) Number of hosts in the following address blocks:
Address blocks Number of hosts
/13 524272
/26 62
Controlled access and contention-based access to a physical medium :
Controlled access grant permission to the transmitting stations to enable it for
communication. Only that station granted for permission will be allowed to send data node in the
communication. This helps to control the traffic and collision of message is also avoided in this
way (Thilina et al. 2015).
Contention refers to media access method that is used for sending broadcasting medium.
In this method any transmitting station can send data at any time. However, this might create
collision in the network. In order to avoid the collision carrier sensing mechanism is used.
d) Number of hosts in the following address blocks:
Address blocks Number of hosts
/13 524272
/26 62
Controlled access and contention-based access to a physical medium :
Controlled access grant permission to the transmitting stations to enable it for
communication. Only that station granted for permission will be allowed to send data node in the
communication. This helps to control the traffic and collision of message is also avoided in this
way (Thilina et al. 2015).
Contention refers to media access method that is used for sending broadcasting medium.
In this method any transmitting station can send data at any time. However, this might create
collision in the network. In order to avoid the collision carrier sensing mechanism is used.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DATA COMMUNICATIONS
References:
Belkneni, M., Bennani, M.T., Ahmed, S.B. and Kalakech, A., 2016, October. Network Layer
Benchmarking: Investigation of AODV Dependability. In International Symposium on Computer
and Information Sciences (pp. 225-232). Springer, Cham.
Chen, G., Gong, Y., Xiao, P. and Chambers, J.A., 2015. Physical layer network security in the
full-duplex relay system. IEEE transactions on information forensics and security, 10(3),
pp.574-583.
Cui, L., Yu, F.R. and Yan, Q., 2016. When big data meets software-defined networking: SDN
for big data and big data for SDN. IEEE network, 30(1), pp.58-65.
Ding, R. and Jiang, H., 2016. Simulation of data-link networks used in cooperative terminal
guidance. In Electronics, Electrical Engineering and Information Science: Proceedings of the
2015 International Conference on Electronics, Electrical Engineering and Information Science
(EEEIS2015) (pp. 504-511).
Garman, S. and Sherman, R., 2015. Automation at the Network Layer.
Goseling, J., Gastpar, M. and Weber, J.H., 2015. Random access with physical-layer network
coding. IEEE Transactions on Information Theory, 61(7), pp.3670-3681.
Kalakech, A., 2016, September. Network Layer Benchmarking: Investigation of AODV
Dependability. In Computer and Information Sciences: 31st International Symposium, ISCIS
2016, Kraków, Poland, October 27–28, 2016, Proceedings (Vol. 659, p. 225). Springer.
References:
Belkneni, M., Bennani, M.T., Ahmed, S.B. and Kalakech, A., 2016, October. Network Layer
Benchmarking: Investigation of AODV Dependability. In International Symposium on Computer
and Information Sciences (pp. 225-232). Springer, Cham.
Chen, G., Gong, Y., Xiao, P. and Chambers, J.A., 2015. Physical layer network security in the
full-duplex relay system. IEEE transactions on information forensics and security, 10(3),
pp.574-583.
Cui, L., Yu, F.R. and Yan, Q., 2016. When big data meets software-defined networking: SDN
for big data and big data for SDN. IEEE network, 30(1), pp.58-65.
Ding, R. and Jiang, H., 2016. Simulation of data-link networks used in cooperative terminal
guidance. In Electronics, Electrical Engineering and Information Science: Proceedings of the
2015 International Conference on Electronics, Electrical Engineering and Information Science
(EEEIS2015) (pp. 504-511).
Garman, S. and Sherman, R., 2015. Automation at the Network Layer.
Goseling, J., Gastpar, M. and Weber, J.H., 2015. Random access with physical-layer network
coding. IEEE Transactions on Information Theory, 61(7), pp.3670-3681.
Kalakech, A., 2016, September. Network Layer Benchmarking: Investigation of AODV
Dependability. In Computer and Information Sciences: 31st International Symposium, ISCIS
2016, Kraków, Poland, October 27–28, 2016, Proceedings (Vol. 659, p. 225). Springer.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DATA COMMUNICATIONS
Kapetanovic, D., Zheng, G. and Rusek, F., 2015. Physical layer security for massive MIMO: An
overview on passive eavesdropping and active attacks. IEEE Communications Magazine, 53(6),
pp.21-27.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Marquardt, R.R., 2017. Data Link Layer Trust Signaling in Communication Network. filed
Jul, 11.
Mukherjee, A., Fakoorian, S.A.A., Huang, J. and Swindlehurst, A.L., 2014. Principles of
physical layer security in multiuser wireless networks: A survey. IEEE Communications Surveys
& Tutorials, 16(3), pp.1550-1573.
Qadir, J., Ali, A., Yau, K.L.A., Sathiaseelan, A. and Crowcroft, J., 2015. Exploiting the power of
multiplicity: a holistic survey of network-layer multipath. IEEE Communications Surveys &
Tutorials, 17(4), pp.2176-2213.
Thilina, K.M., Tabassum, H., Hossain, E. and Kim, D.I., 2015. Medium access control design for
full duplex wireless systems: challenges and approaches. IEEE Communications
Magazine, 53(5), pp.112-120.
Zafar, S. and Ejaz, U., 2016. SCTP-aware Link Layer Retransmission Mechanism for Smart-grid
Communication Network. Engineering, Technology & Applied Science Research, 6(4), pp.1093-
1098.
Zou, Y., Zhu, J., Wang, X. and Leung, V.C., 2015. Improving physical-layer security in wireless
communications using diversity techniques. IEEE Network, 29(1), pp.42-48.
Kapetanovic, D., Zheng, G. and Rusek, F., 2015. Physical layer security for massive MIMO: An
overview on passive eavesdropping and active attacks. IEEE Communications Magazine, 53(6),
pp.21-27.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Marquardt, R.R., 2017. Data Link Layer Trust Signaling in Communication Network. filed
Jul, 11.
Mukherjee, A., Fakoorian, S.A.A., Huang, J. and Swindlehurst, A.L., 2014. Principles of
physical layer security in multiuser wireless networks: A survey. IEEE Communications Surveys
& Tutorials, 16(3), pp.1550-1573.
Qadir, J., Ali, A., Yau, K.L.A., Sathiaseelan, A. and Crowcroft, J., 2015. Exploiting the power of
multiplicity: a holistic survey of network-layer multipath. IEEE Communications Surveys &
Tutorials, 17(4), pp.2176-2213.
Thilina, K.M., Tabassum, H., Hossain, E. and Kim, D.I., 2015. Medium access control design for
full duplex wireless systems: challenges and approaches. IEEE Communications
Magazine, 53(5), pp.112-120.
Zafar, S. and Ejaz, U., 2016. SCTP-aware Link Layer Retransmission Mechanism for Smart-grid
Communication Network. Engineering, Technology & Applied Science Research, 6(4), pp.1093-
1098.
Zou, Y., Zhu, J., Wang, X. and Leung, V.C., 2015. Improving physical-layer security in wireless
communications using diversity techniques. IEEE Network, 29(1), pp.42-48.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





