Advanced Data Communications Principles Report - University Name
VerifiedAdded on 2022/11/27
|9
|1306
|355
Report
AI Summary
This report provides a detailed analysis of advanced data communications principles. It begins with a comparative study of PBX and VOIP technologies, evaluating their infrastructure, scalability, features, and costs. The report highlights the advantages and disadvantages of each system, offering recommendations for a medium-sized company seeking to upgrade its network. It also covers email security, demonstrating the process of creating and sending forged emails, including steps for creating the sender information, subject, attachment and content. The report uses figures and screenshots to illustrate the email sending process. The assignment includes the analysis of CRC-8, codeword extraction, and single-bit error detection, demonstrating the practical application of these concepts in data transmission. The report concludes with a bibliography of referenced sources.

Running head: ADVANCED DATA COMMUNICATIONS PRINCIPLES
Advanced Data Communications Principles
Name of the Student
Name of the University
Author’s Note
Advanced Data Communications Principles
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Answer to Question 2:
Introduction
The report is prepared for a medium sized company that currently uses PBX technology for
communicating with the other branches and the clients and needs replace their existing network
with internet phone. A brief description of the existing technology and its pros and cons are
given in the report along with the description of the new technology and its pros and cons that
can be adopted for increasing the efficiency and performance of the current network.
Brief description of Technology
PBX
Private Branch Exchange is a private telephone network that is used by the company for making
internal and external communication with communication channels like VOIP, analog or ISDN
(Zanuttini et al., 2018). There are proprietary phones used in PBX that are reused with different
systems.
Pros
Infrastructure
It can run on cat3 or above cables and does not needs data
Simplicity
It has many functionalities that can make it productive but not many that can be used for
overwhelming the user
Reliability
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Answer to Question 2:
Introduction
The report is prepared for a medium sized company that currently uses PBX technology for
communicating with the other branches and the clients and needs replace their existing network
with internet phone. A brief description of the existing technology and its pros and cons are
given in the report along with the description of the new technology and its pros and cons that
can be adopted for increasing the efficiency and performance of the current network.
Brief description of Technology
PBX
Private Branch Exchange is a private telephone network that is used by the company for making
internal and external communication with communication channels like VOIP, analog or ISDN
(Zanuttini et al., 2018). There are proprietary phones used in PBX that are reused with different
systems.
Pros
Infrastructure
It can run on cat3 or above cables and does not needs data
Simplicity
It has many functionalities that can make it productive but not many that can be used for
overwhelming the user
Reliability

2
ADVANCED DATA COMMUNICATIONS PRINCIPLES
The internet disruption cannot affect the quality issues on the call since traditional telephone
lines are used for making calls.
Cost
It cost less than the VOIP or hosted VOIP but it cannot provide the quality of service that is
provided by its superior.
Cons
Scalability and Expansion – For adding a new phone with the system a new port is required and
no port is available a card is needed to be installed. For the addition of the card a slot is
necessary in the cabinet and if there are no slots available in the cabinet and new cabinet is
needed to be installed.
Management - For the addition of new card or cabinet the business partner needs to make an
onsite visit and physically install the components.
VOIP Phone Systems
In this technology the voice is converted into data, packetized and transmitted over the data
network. It can be hosted or on premise and it is developed later than PBX and works on recent
technology and platform.
Pros
Scalability
It is a licensed based system and addition of new license causes access to more features and
extensions. It can thus help in growth of the organization and an ideal solution for the seasonal
business.
ADVANCED DATA COMMUNICATIONS PRINCIPLES
The internet disruption cannot affect the quality issues on the call since traditional telephone
lines are used for making calls.
Cost
It cost less than the VOIP or hosted VOIP but it cannot provide the quality of service that is
provided by its superior.
Cons
Scalability and Expansion – For adding a new phone with the system a new port is required and
no port is available a card is needed to be installed. For the addition of the card a slot is
necessary in the cabinet and if there are no slots available in the cabinet and new cabinet is
needed to be installed.
Management - For the addition of new card or cabinet the business partner needs to make an
onsite visit and physically install the components.
VOIP Phone Systems
In this technology the voice is converted into data, packetized and transmitted over the data
network. It can be hosted or on premise and it is developed later than PBX and works on recent
technology and platform.
Pros
Scalability
It is a licensed based system and addition of new license causes access to more features and
extensions. It can thus help in growth of the organization and an ideal solution for the seasonal
business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Features
The VOIP is simple and can be integrated with new technologies for increasing the functionality
and bringing telephony to a new level.
Redundancy
Since the IP technology is subjected to network downtime redundancy can be incorporated for
the phone system and the components that are essential for communication using the VOIP
phones.
Virtualization
A full phone system can be used as a virtual instance and it can also be hosted in the data center
for management of communications.
BYOD
SIP platform are used for the VOIP and it allows to use different types of phones. It eliminates
the vendor lock in and enables the use of any SIP device. The mobile phones of the employees
can be used as business telephones and even the computers can be used as telephone endpoint.
Integration
The VOIP technology can be integrated with other technologies for allowing the phones to be
controlled with different software and increasing the functionality of the system (McInnes, Wills
& Zaluska, 2019). Unified communication platform can be created and the phones can be
controlled by mouse with the features like drag and drop transfer calls, clicking to dial, instant
messaging etc.
Cons
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Features
The VOIP is simple and can be integrated with new technologies for increasing the functionality
and bringing telephony to a new level.
Redundancy
Since the IP technology is subjected to network downtime redundancy can be incorporated for
the phone system and the components that are essential for communication using the VOIP
phones.
Virtualization
A full phone system can be used as a virtual instance and it can also be hosted in the data center
for management of communications.
BYOD
SIP platform are used for the VOIP and it allows to use different types of phones. It eliminates
the vendor lock in and enables the use of any SIP device. The mobile phones of the employees
can be used as business telephones and even the computers can be used as telephone endpoint.
Integration
The VOIP technology can be integrated with other technologies for allowing the phones to be
controlled with different software and increasing the functionality of the system (McInnes, Wills
& Zaluska, 2019). Unified communication platform can be created and the phones can be
controlled by mouse with the features like drag and drop transfer calls, clicking to dial, instant
messaging etc.
Cons
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Infrastructure
Cat 5 cables are required for connecting the IP phone and the traffic generated from the VOIP
phones uses the same data network thus the network is needed to be stable and sufficient
bandwidth for the management of voice packets. The switches installed in the network is needed
to have additional ports and if not new switches are needed to be installed.
IT involvement
It needs the involvement of the IT staff and it is needed to be make sure that the IT team has
sufficient time for adding this work as priority.
Points of failure
The data network can be impacted with the use of VoIP because switches are used for connecting
the IP phones and servers for housing the phone system. Sometimes multiple servers are needed
to be installed for managing multiple service. It also needs cat5 cabling for connecting the
phones and the failure point is more than the PBX solution.
Vendor Selection
The VoIP has opened ability for the business for installing and service telephony and it has
allowed options for the companies for getting in the telephony market as industry expert. The
service provider is needed to be selected because many of the service provider may be inefficient
and can create a mess for the organization.
Recommendation
Since the existing local area network uses cat 5 cables and have available ports for the
switches it is recommended that the adoption of the VOIP technology would help the
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Infrastructure
Cat 5 cables are required for connecting the IP phone and the traffic generated from the VOIP
phones uses the same data network thus the network is needed to be stable and sufficient
bandwidth for the management of voice packets. The switches installed in the network is needed
to have additional ports and if not new switches are needed to be installed.
IT involvement
It needs the involvement of the IT staff and it is needed to be make sure that the IT team has
sufficient time for adding this work as priority.
Points of failure
The data network can be impacted with the use of VoIP because switches are used for connecting
the IP phones and servers for housing the phone system. Sometimes multiple servers are needed
to be installed for managing multiple service. It also needs cat5 cabling for connecting the
phones and the failure point is more than the PBX solution.
Vendor Selection
The VoIP has opened ability for the business for installing and service telephony and it has
allowed options for the companies for getting in the telephony market as industry expert. The
service provider is needed to be selected because many of the service provider may be inefficient
and can create a mess for the organization.
Recommendation
Since the existing local area network uses cat 5 cables and have available ports for the
switches it is recommended that the adoption of the VOIP technology would help the

5
ADVANCED DATA COMMUNICATIONS PRINCIPLES
organization gain competitive advantage. It can be integrated with other technologies for
improving the customer management and communication. The adoption of the VOIP would also
help the organization to increase the scalability and grow the organization by improving the
business operation and performance of the employees.
Answer to Question 3:
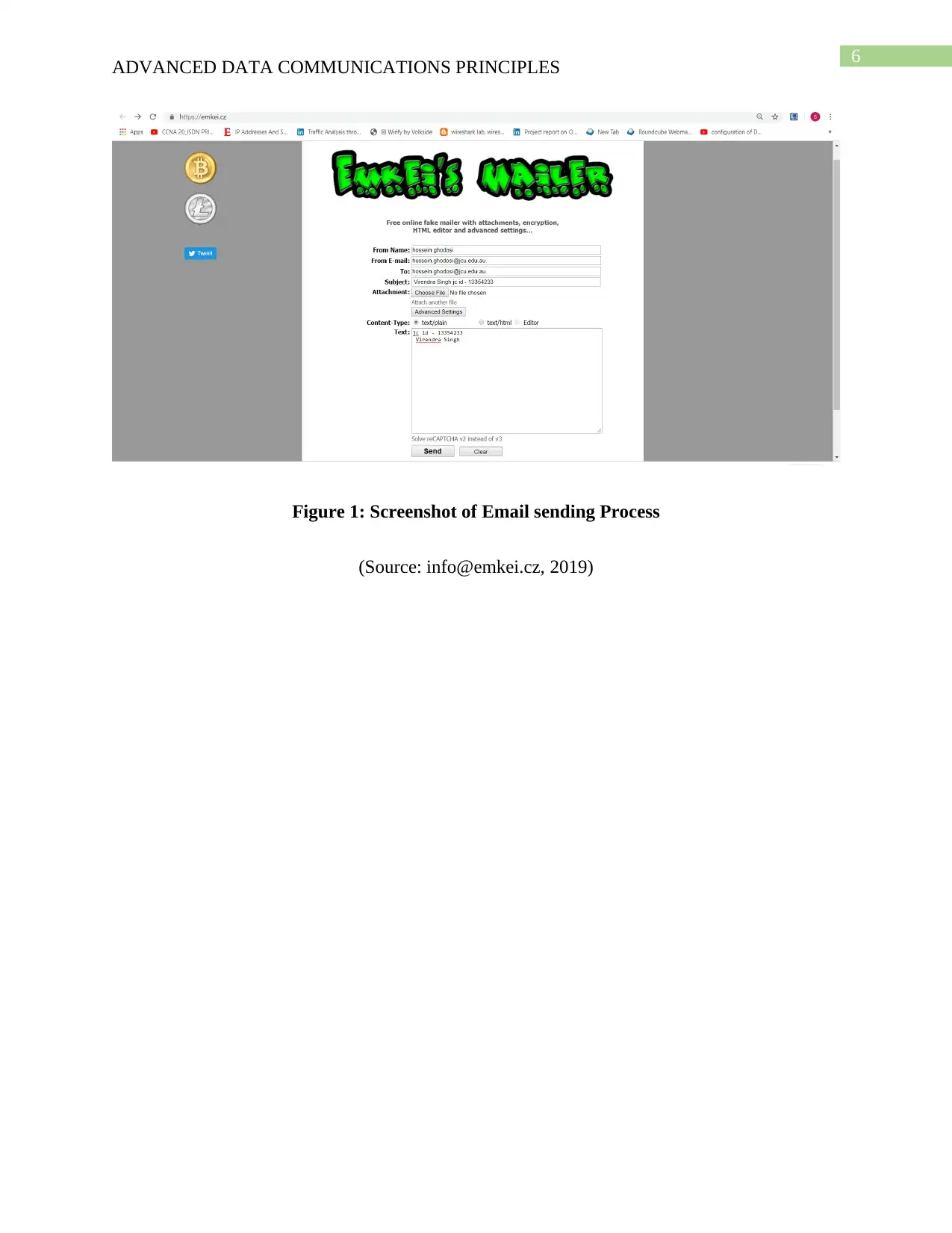
For sending email with forged sender address we have selected a third party platform that is
readily available on the internet. The steps for creating and sending the email are given below:
1. From Name: It contains the name of the lecturer since for sending the forged email the send
and the receiver bit har the lecturer.
2. From Email: It contains the email address of the lecturer
3. To: It contains the email address of the lecturer
4. Subject: It contains an attractive text that would attract the lecturer to open the email
5. Attachment: It is optional because the mail can be sent with or without adding the
attachment. The attachment can be different files or format and may also contain embedded
virus that can infect the targeted machine.
6. Content Type: there are two types of content i.e. text/plain, text/html. Primarily the text has a
subtype plain and it is used for indicating plain / unformatted text. The text/html option is
used for sending the text is different format such as tables.
7. Text: It contains the content of the email and the texts that are used for communicating with
the lecturer or the receiver of the email.
ADVANCED DATA COMMUNICATIONS PRINCIPLES
organization gain competitive advantage. It can be integrated with other technologies for
improving the customer management and communication. The adoption of the VOIP would also
help the organization to increase the scalability and grow the organization by improving the
business operation and performance of the employees.
Answer to Question 3:
For sending email with forged sender address we have selected a third party platform that is
readily available on the internet. The steps for creating and sending the email are given below:
1. From Name: It contains the name of the lecturer since for sending the forged email the send
and the receiver bit har the lecturer.
2. From Email: It contains the email address of the lecturer
3. To: It contains the email address of the lecturer
4. Subject: It contains an attractive text that would attract the lecturer to open the email
5. Attachment: It is optional because the mail can be sent with or without adding the
attachment. The attachment can be different files or format and may also contain embedded
virus that can infect the targeted machine.
6. Content Type: there are two types of content i.e. text/plain, text/html. Primarily the text has a
subtype plain and it is used for indicating plain / unformatted text. The text/html option is
used for sending the text is different format such as tables.
7. Text: It contains the content of the email and the texts that are used for communicating with
the lecturer or the receiver of the email.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Figure 1: Screenshot of Email sending Process
(Source: info@emkei.cz, 2019)
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Figure 1: Screenshot of Email sending Process
(Source: info@emkei.cz, 2019)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ADVANCED DATA COMMUNICATIONS PRINCIPLES
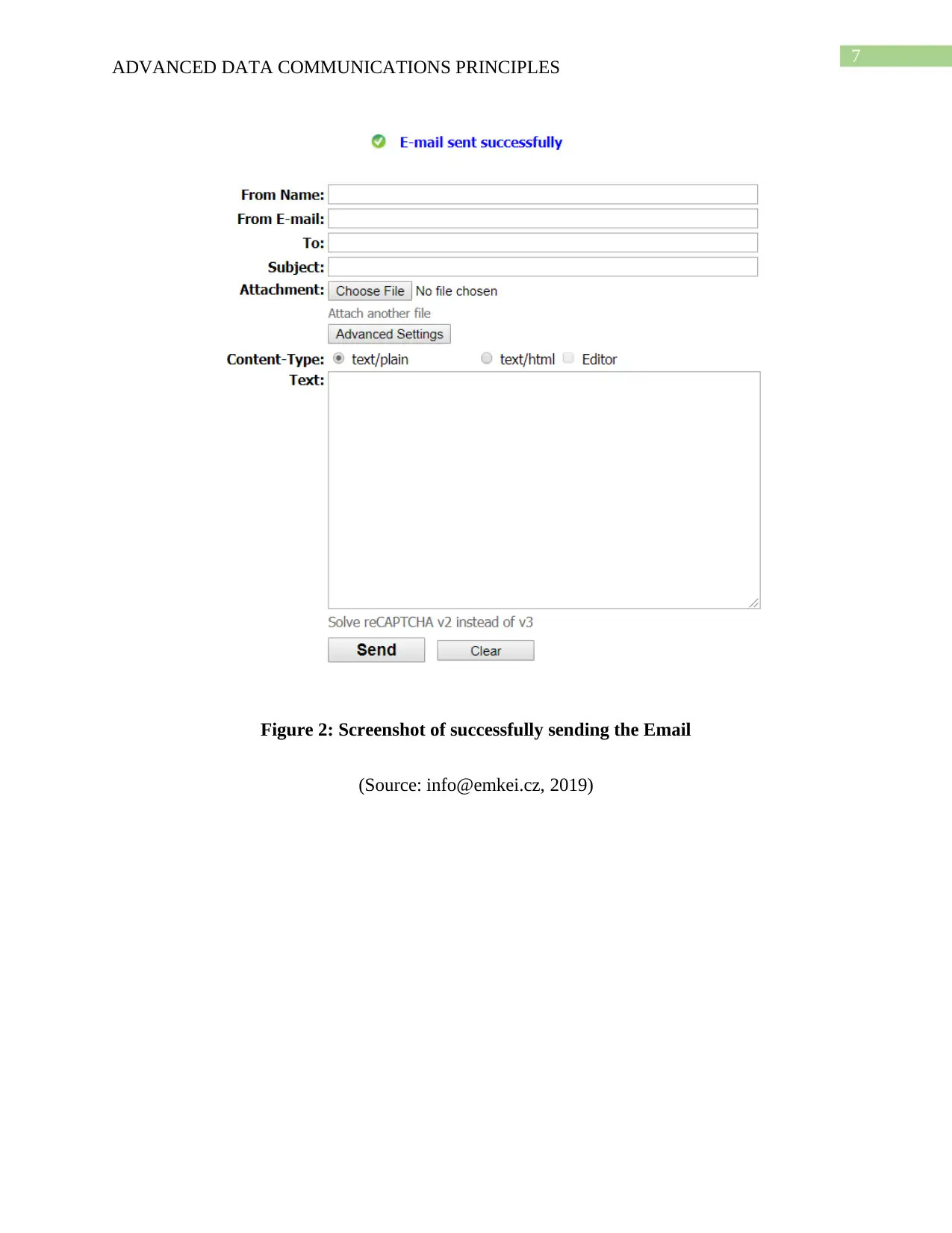
Figure 2: Screenshot of successfully sending the Email
(Source: info@emkei.cz, 2019)
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Figure 2: Screenshot of successfully sending the Email
(Source: info@emkei.cz, 2019)

8
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Bibliography
info@emkei.cz, E. (2019). Emkei's Fake Mailer. Emkei.cz. Retrieved 28 May 2019, from
https://emkei.cz/
McInnes, N., Wills, G., & Zaluska, E. (2019). Analysis of threats on a VoIP based PBX
honeypot.
Zanuttini, D., Andres, C., Gonzalez, J., Lacapmesure, A., Priano, D., Pucci, N., & Bullian, P.
(2018, November). Using Software Defined Networking for Call Admission Control and
VoIP applications. In 2018 Congreso Argentino de Ciencias de la Informática y
Desarrollos de Investigación (CACIDI) (pp. 1-5). IEEE.
ADVANCED DATA COMMUNICATIONS PRINCIPLES
Bibliography
info@emkei.cz, E. (2019). Emkei's Fake Mailer. Emkei.cz. Retrieved 28 May 2019, from
https://emkei.cz/
McInnes, N., Wills, G., & Zaluska, E. (2019). Analysis of threats on a VoIP based PBX
honeypot.
Zanuttini, D., Andres, C., Gonzalez, J., Lacapmesure, A., Priano, D., Pucci, N., & Bullian, P.
(2018, November). Using Software Defined Networking for Call Admission Control and
VoIP applications. In 2018 Congreso Argentino de Ciencias de la Informática y
Desarrollos de Investigación (CACIDI) (pp. 1-5). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




