Data Encryption Techniques: A Presentation for MITS5004 IT Security
VerifiedAdded on 2022/10/19
|11
|600
|182
Presentation
AI Summary
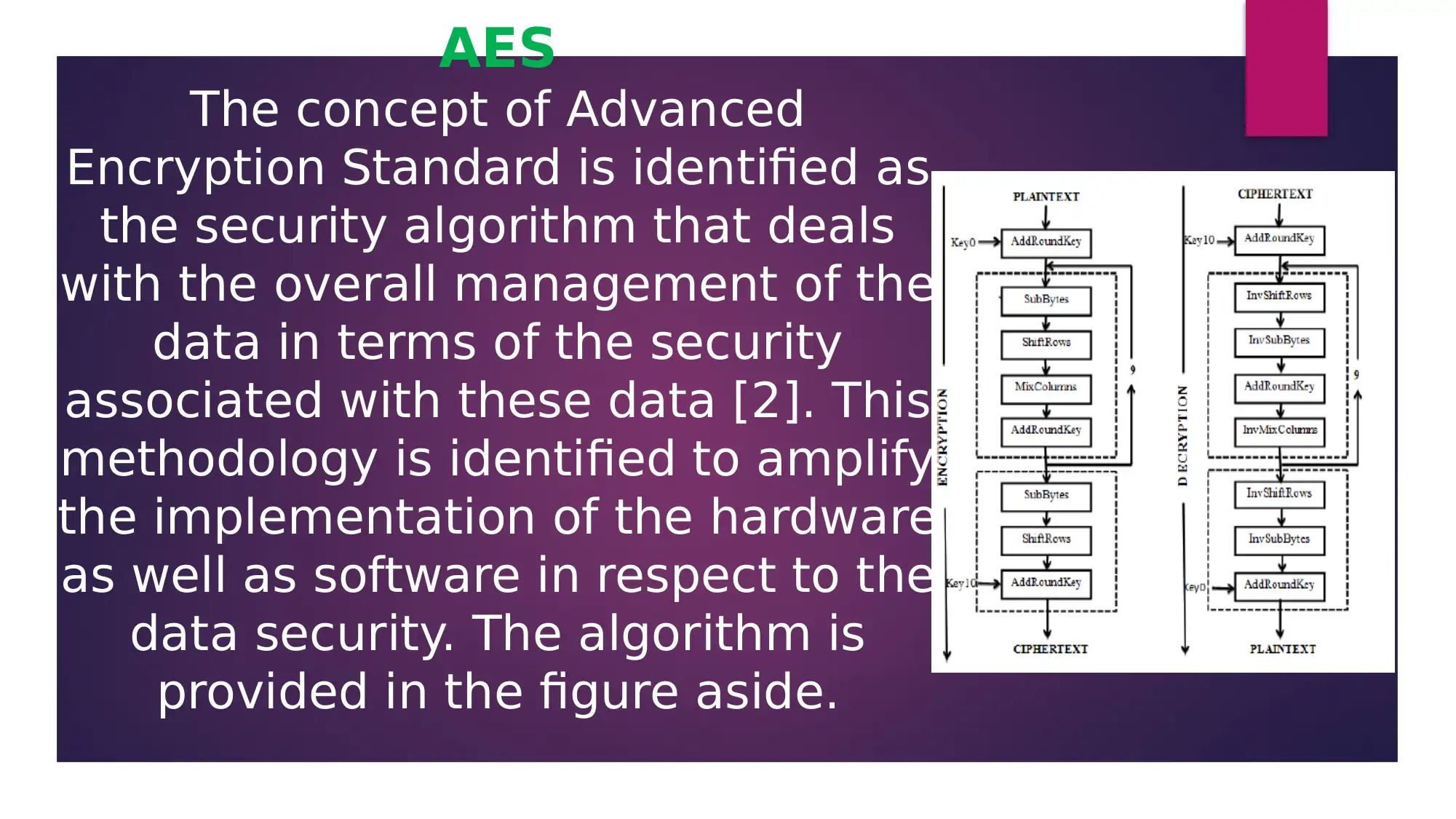
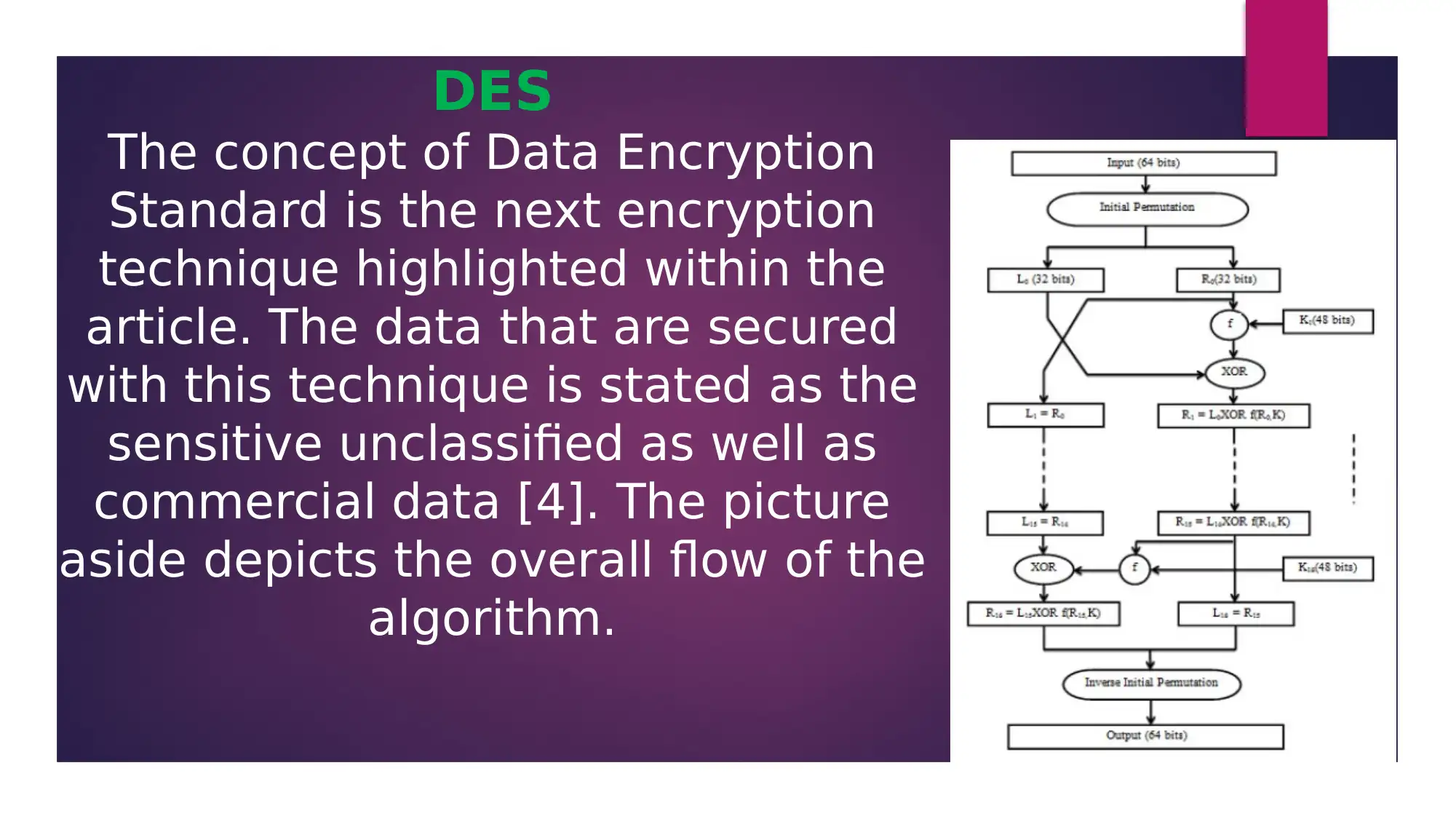
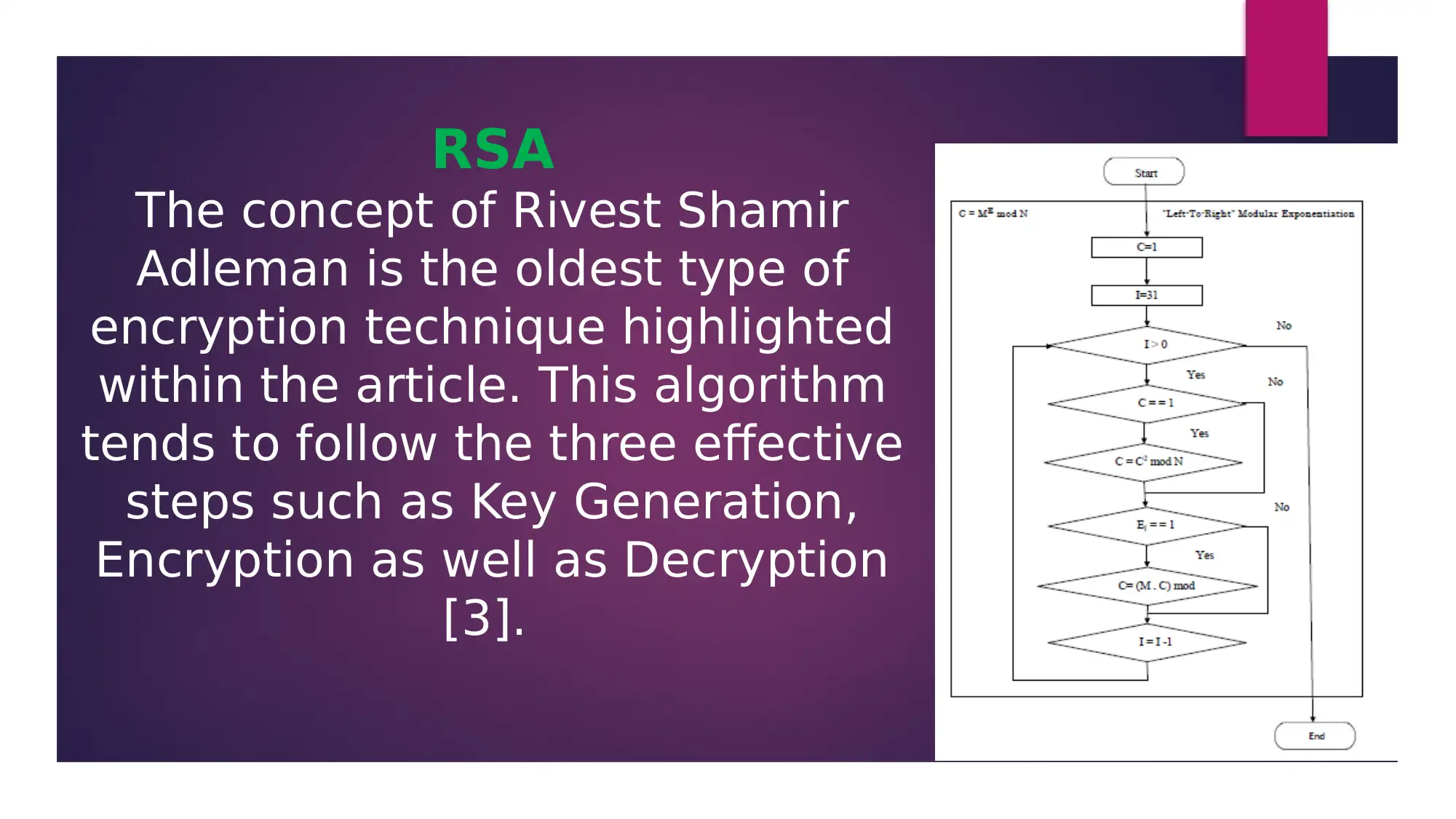
This presentation provides an overview of data encryption techniques, focusing on three key algorithms: Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Rivest Shamir Adleman (RSA). The presentation analyzes an academic paper that discusses these algorithms, highlighting their significance in maintaining data security within network servers. It explores the implementation of AES, DES, and RSA, discussing their strengths and weaknesses in terms of key size, algorithm types, and hardware/software implementation. The presentation concludes that the appropriate selection of these algorithms is crucial for securing data within network systems, particularly in today's data-driven world. References to the original research paper and related studies are included to support the analysis.
1 out of 11











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)