Data and Information Management: Logical Database Design Report
VerifiedAdded on 2021/06/14
|8
|1379
|259
Report
AI Summary
This report delves into the realm of data and information management, concentrating on the creation and analysis of a logical database design. The report presents an Entity Relationship Diagram (ERD) to visually represent the database structure, including tables for Workers, Patients, Shifts, Admissions, Beds, Prescriptions, and Medicines, along with their attributes and constraints. The core of the report identifies and discusses critical issues in data management, such as determining scalability, formulating effective data strategies, ensuring proper data collection, managing authorization, and addressing low data protection. Each issue is examined with real-world examples and supported by relevant literature, offering insights into the challenges and complexities of managing data in various organizational contexts. The report concludes with a comprehensive bibliography of cited sources.

Running head: DATA AND INFORMATION MANAGEMENT
Data and Information Management
Name of the Student
Name of the University
Data and Information Management
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA AND INFORMATION MANAGEMENT
Logical Database Design:
Figure 1: Entity Relationship Diagram
(Source: Created by Author)
Logical Database Design:
Figure 1: Entity Relationship Diagram
(Source: Created by Author)
2DATA AND INFORMATION MANAGEMENT
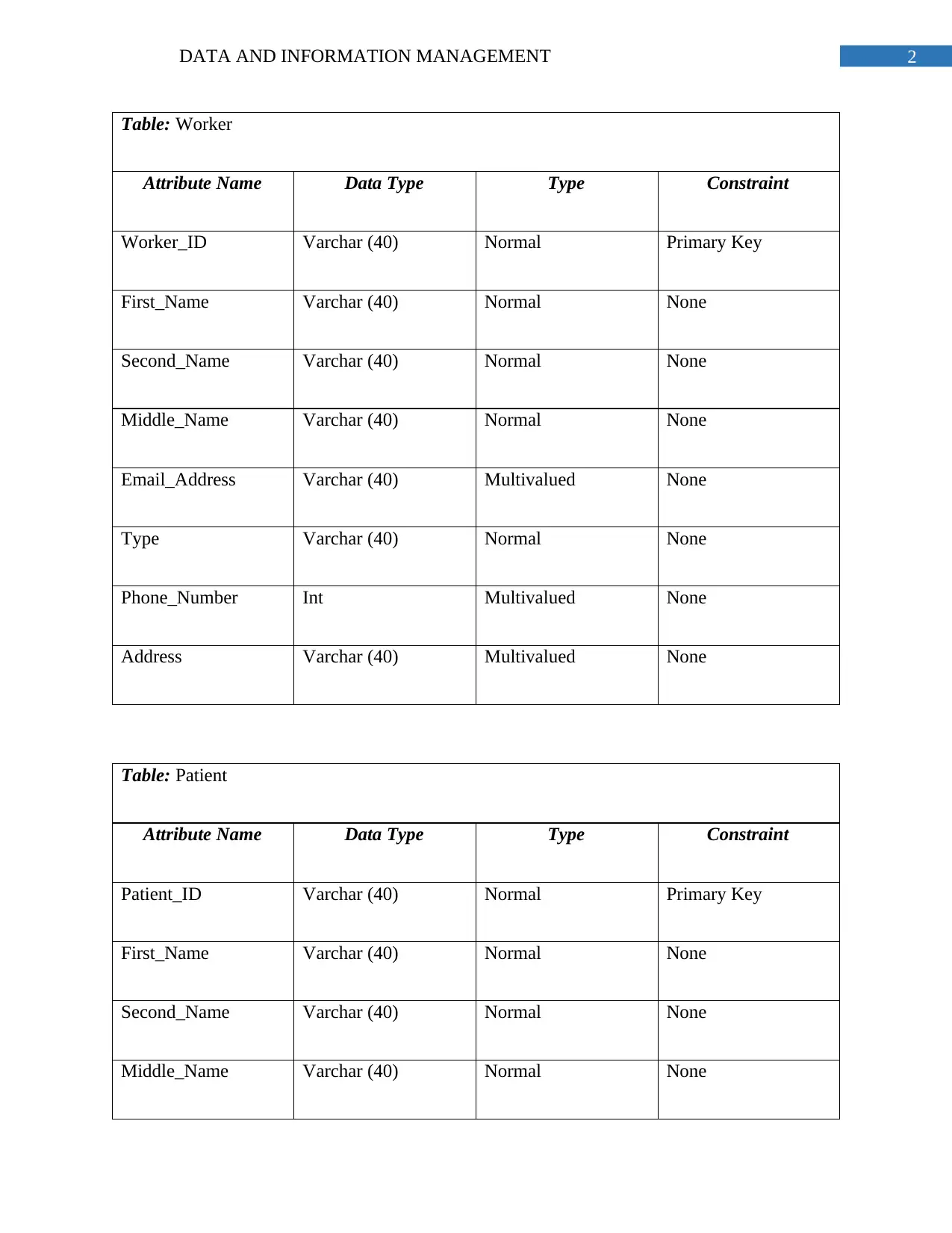
Table: Worker
Attribute Name Data Type Type Constraint
Worker_ID Varchar (40) Normal Primary Key
First_Name Varchar (40) Normal None
Second_Name Varchar (40) Normal None
Middle_Name Varchar (40) Normal None
Email_Address Varchar (40) Multivalued None
Type Varchar (40) Normal None
Phone_Number Int Multivalued None
Address Varchar (40) Multivalued None
Table: Patient
Attribute Name Data Type Type Constraint
Patient_ID Varchar (40) Normal Primary Key
First_Name Varchar (40) Normal None
Second_Name Varchar (40) Normal None
Middle_Name Varchar (40) Normal None
Table: Worker
Attribute Name Data Type Type Constraint
Worker_ID Varchar (40) Normal Primary Key
First_Name Varchar (40) Normal None
Second_Name Varchar (40) Normal None
Middle_Name Varchar (40) Normal None
Email_Address Varchar (40) Multivalued None
Type Varchar (40) Normal None
Phone_Number Int Multivalued None
Address Varchar (40) Multivalued None
Table: Patient
Attribute Name Data Type Type Constraint
Patient_ID Varchar (40) Normal Primary Key
First_Name Varchar (40) Normal None
Second_Name Varchar (40) Normal None
Middle_Name Varchar (40) Normal None
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3DATA AND INFORMATION MANAGEMENT
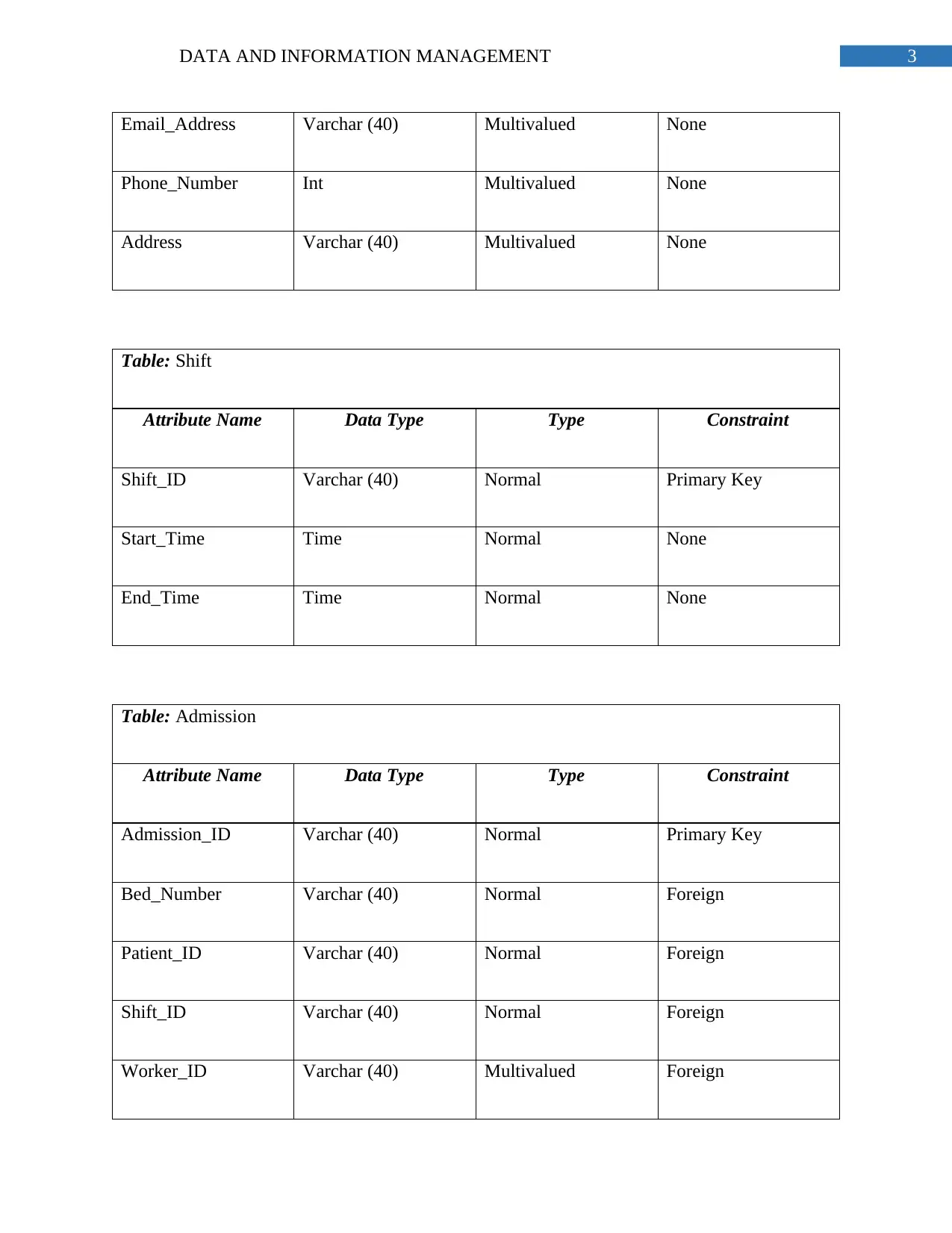
Email_Address Varchar (40) Multivalued None
Phone_Number Int Multivalued None
Address Varchar (40) Multivalued None
Table: Shift
Attribute Name Data Type Type Constraint
Shift_ID Varchar (40) Normal Primary Key
Start_Time Time Normal None
End_Time Time Normal None
Table: Admission
Attribute Name Data Type Type Constraint
Admission_ID Varchar (40) Normal Primary Key
Bed_Number Varchar (40) Normal Foreign
Patient_ID Varchar (40) Normal Foreign
Shift_ID Varchar (40) Normal Foreign
Worker_ID Varchar (40) Multivalued Foreign
Email_Address Varchar (40) Multivalued None
Phone_Number Int Multivalued None
Address Varchar (40) Multivalued None
Table: Shift
Attribute Name Data Type Type Constraint
Shift_ID Varchar (40) Normal Primary Key
Start_Time Time Normal None
End_Time Time Normal None
Table: Admission
Attribute Name Data Type Type Constraint
Admission_ID Varchar (40) Normal Primary Key
Bed_Number Varchar (40) Normal Foreign
Patient_ID Varchar (40) Normal Foreign
Shift_ID Varchar (40) Normal Foreign
Worker_ID Varchar (40) Multivalued Foreign
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4DATA AND INFORMATION MANAGEMENT
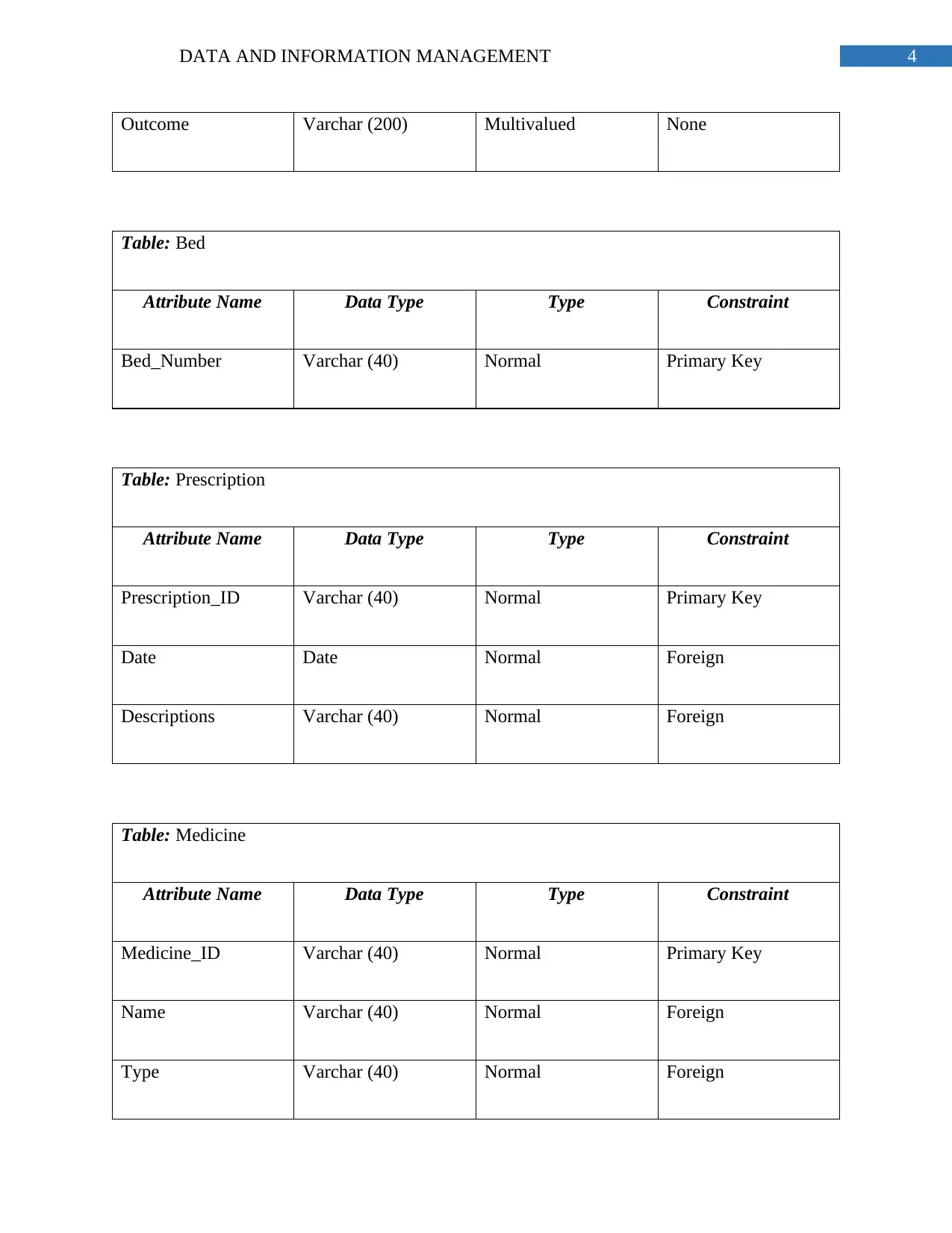
Outcome Varchar (200) Multivalued None
Table: Bed
Attribute Name Data Type Type Constraint
Bed_Number Varchar (40) Normal Primary Key
Table: Prescription
Attribute Name Data Type Type Constraint
Prescription_ID Varchar (40) Normal Primary Key
Date Date Normal Foreign
Descriptions Varchar (40) Normal Foreign
Table: Medicine
Attribute Name Data Type Type Constraint
Medicine_ID Varchar (40) Normal Primary Key
Name Varchar (40) Normal Foreign
Type Varchar (40) Normal Foreign
Outcome Varchar (200) Multivalued None
Table: Bed
Attribute Name Data Type Type Constraint
Bed_Number Varchar (40) Normal Primary Key
Table: Prescription
Attribute Name Data Type Type Constraint
Prescription_ID Varchar (40) Normal Primary Key
Date Date Normal Foreign
Descriptions Varchar (40) Normal Foreign
Table: Medicine
Attribute Name Data Type Type Constraint
Medicine_ID Varchar (40) Normal Primary Key
Name Varchar (40) Normal Foreign
Type Varchar (40) Normal Foreign
5DATA AND INFORMATION MANAGEMENT
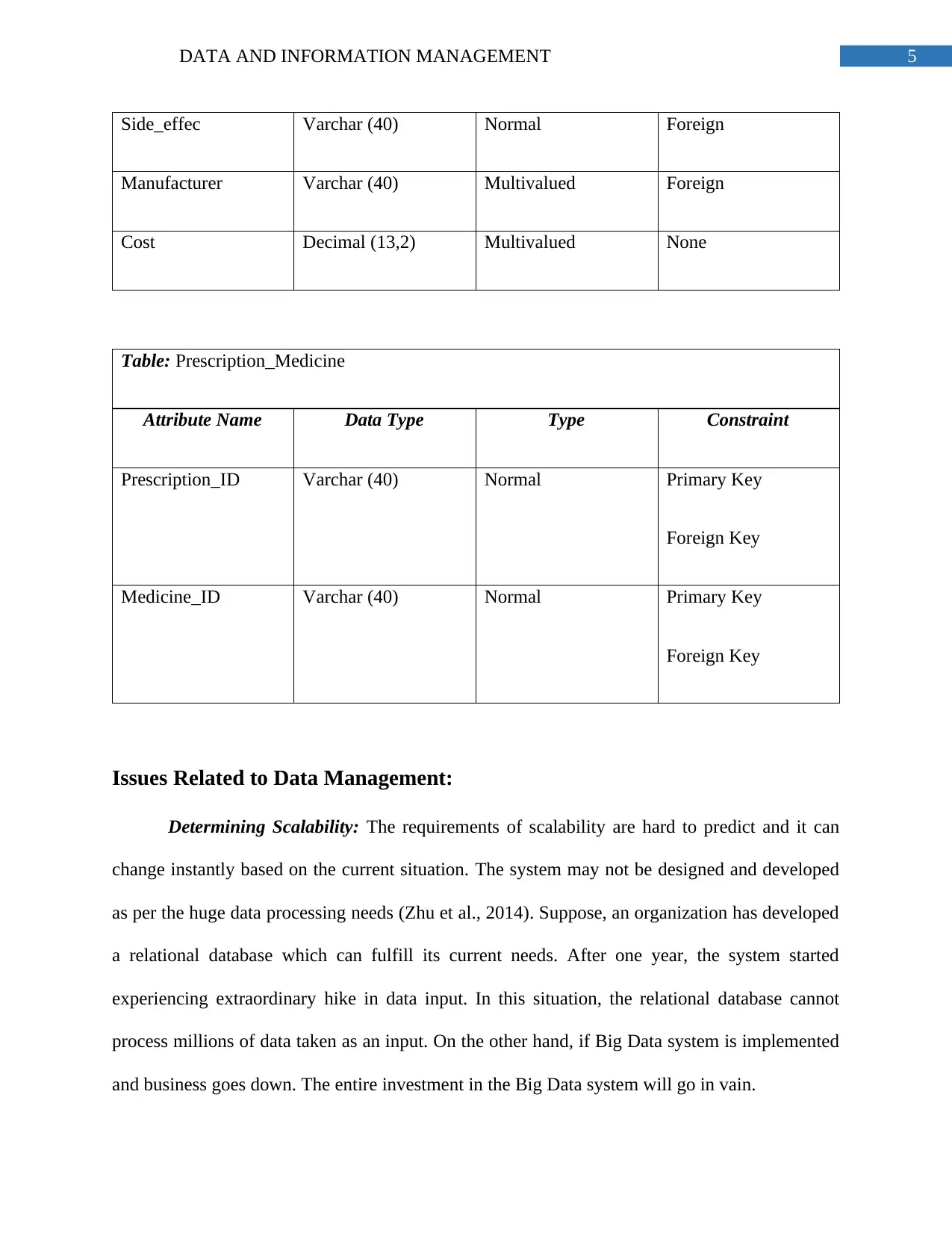
Side_effec Varchar (40) Normal Foreign
Manufacturer Varchar (40) Multivalued Foreign
Cost Decimal (13,2) Multivalued None
Table: Prescription_Medicine
Attribute Name Data Type Type Constraint
Prescription_ID Varchar (40) Normal Primary Key
Foreign Key
Medicine_ID Varchar (40) Normal Primary Key
Foreign Key
Issues Related to Data Management:
Determining Scalability: The requirements of scalability are hard to predict and it can
change instantly based on the current situation. The system may not be designed and developed
as per the huge data processing needs (Zhu et al., 2014). Suppose, an organization has developed
a relational database which can fulfill its current needs. After one year, the system started
experiencing extraordinary hike in data input. In this situation, the relational database cannot
process millions of data taken as an input. On the other hand, if Big Data system is implemented
and business goes down. The entire investment in the Big Data system will go in vain.
Side_effec Varchar (40) Normal Foreign
Manufacturer Varchar (40) Multivalued Foreign
Cost Decimal (13,2) Multivalued None
Table: Prescription_Medicine
Attribute Name Data Type Type Constraint
Prescription_ID Varchar (40) Normal Primary Key
Foreign Key
Medicine_ID Varchar (40) Normal Primary Key
Foreign Key
Issues Related to Data Management:
Determining Scalability: The requirements of scalability are hard to predict and it can
change instantly based on the current situation. The system may not be designed and developed
as per the huge data processing needs (Zhu et al., 2014). Suppose, an organization has developed
a relational database which can fulfill its current needs. After one year, the system started
experiencing extraordinary hike in data input. In this situation, the relational database cannot
process millions of data taken as an input. On the other hand, if Big Data system is implemented
and business goes down. The entire investment in the Big Data system will go in vain.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DATA AND INFORMATION MANAGEMENT
Data Strategy: The data strategy refers to the process of driving and overarching
structure of managing data. The data strategy of ER refers to the method of collecting, handling,
managing and storing data. If the data strategy is not defined properly then ER will have
numerous issues, specifically in collecting or storing data (Hashem et al., 2015). Suppose, ER
uses a third party system. The staff of ER can access the reports and other details but they will
not access the finical data like card number, bank account numbers and other information.
Data Collection: The database system developers and designers must identify the
requirements of the system and purpose of it. If they are not able to identify the audiences of the
system and what information to be shared with them, the whole data collection process will not
function. Data are not collected from the end-users only (Laudon & Laudon, 2016). Data comes
from various industrial equipment also. It often happens, that required data are not stored in the
database. This issue results in big gap in processes like decision making, process management
and many more.
Authorization: It is a big issue that needs to be handled with proper accuracy and skill.
The analysts identify which end-user requires which data to complete their tasks. Based on this
finding, the system provides access to the data to various users (Wilkinson et al., 2016).
Restricting all the users from access the whole data set is called as authorization. Often,
authorization levels are not defined properly and unauthorized data is sent to a user unwantedly.
In this situation, the user can use that data for illegal activities or any other wrong purpose.
Low Protection: Significant increase in the cyber-attacks have made the system
vulnerable. The attackers can hack into the system and access the required data unauthorized.
Recent attacks on various repeated organization’s system have showed that the attackers can
Data Strategy: The data strategy refers to the process of driving and overarching
structure of managing data. The data strategy of ER refers to the method of collecting, handling,
managing and storing data. If the data strategy is not defined properly then ER will have
numerous issues, specifically in collecting or storing data (Hashem et al., 2015). Suppose, ER
uses a third party system. The staff of ER can access the reports and other details but they will
not access the finical data like card number, bank account numbers and other information.
Data Collection: The database system developers and designers must identify the
requirements of the system and purpose of it. If they are not able to identify the audiences of the
system and what information to be shared with them, the whole data collection process will not
function. Data are not collected from the end-users only (Laudon & Laudon, 2016). Data comes
from various industrial equipment also. It often happens, that required data are not stored in the
database. This issue results in big gap in processes like decision making, process management
and many more.
Authorization: It is a big issue that needs to be handled with proper accuracy and skill.
The analysts identify which end-user requires which data to complete their tasks. Based on this
finding, the system provides access to the data to various users (Wilkinson et al., 2016).
Restricting all the users from access the whole data set is called as authorization. Often,
authorization levels are not defined properly and unauthorized data is sent to a user unwantedly.
In this situation, the user can use that data for illegal activities or any other wrong purpose.
Low Protection: Significant increase in the cyber-attacks have made the system
vulnerable. The attackers can hack into the system and access the required data unauthorized.
Recent attacks on various repeated organization’s system have showed that the attackers can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DATA AND INFORMATION MANAGEMENT
remain in the system and continuously steal the data coming in or going out of the system. The
DoS attacks can be used for bringing down a whole system and paralyze it (Zhang et al., 2015).
The attackers can get access to the system and steal all the data. Insider attacks are also very
severe for the data management. Because of the impact of the low data protection on data
management, it is considered as the most severe issue.
remain in the system and continuously steal the data coming in or going out of the system. The
DoS attacks can be used for bringing down a whole system and paralyze it (Zhang et al., 2015).
The attackers can get access to the system and steal all the data. Insider attacks are also very
severe for the data management. Because of the impact of the low data protection on data
management, it is considered as the most severe issue.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





