Data Security and Management: University Database Report
VerifiedAdded on 2022/08/29
|19
|3471
|23
Report
AI Summary
This report provides a comprehensive analysis of data and knowledge management principles applied to a university database system. The report begins by exploring the importance of data security and management within a relational database management system (RDBMS), emphasizing data consistency, integrity, and quality achieved through constraints and effective database design processes. It then delves into the creation of an Entity Relationship Diagram (ERD) to model the university's entities and their relationships. Normalization techniques, including First, Second, and Third Normal Forms, are employed to simplify relations, reduce redundancy, and maintain data integrity. The report presents the database schema and data dictionary, detailing table structures, attributes, data types, and constraints. An evaluation and implementation of the relational database are discussed, including the creation of tables using SQL Data Definition Language (DDL) statements, the application of key constraints to establish relationships, and the population of tables with sample data using Data Manipulation Language (DML) statements (INSERT). Various SQL queries, employing GROUP BY, INNER JOIN, RIGHT JOIN, and LEFT JOIN, are developed to retrieve and analyze data. Finally, the rationale for using the relational model, particularly its consistency and integrity, is presented, highlighting the star schema structure of the developed database.

Running head: DATA & KNOWLEDGE MANAGEMENT
DATA & KNOWLEDGE MANAGEMENT
Name of the Student
Name of the University
Author Note
DATA & KNOWLEDGE MANAGEMENT
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA & KNOWLEDGE MANAGEMENT
Table of Contents
An analysis of the data security and data management...................................................................2
ERD.................................................................................................................................................2
Normalization..................................................................................................................................4
First Order Normalization............................................................................................................4
Second Order Normalization.......................................................................................................4
Third Order Normalization..........................................................................................................5
Database Schema.............................................................................................................................5
Data Dictionary................................................................................................................................6
An evaluation & Implementation of the relational database...........................................................8
Creation........................................................................................................................................9
Constraints.................................................................................................................................11
Population..................................................................................................................................11
Queries.......................................................................................................................................13
Rationale for the use of the relational model.................................................................................15
References......................................................................................................................................16
Table of Contents
An analysis of the data security and data management...................................................................2
ERD.................................................................................................................................................2
Normalization..................................................................................................................................4
First Order Normalization............................................................................................................4
Second Order Normalization.......................................................................................................4
Third Order Normalization..........................................................................................................5
Database Schema.............................................................................................................................5
Data Dictionary................................................................................................................................6
An evaluation & Implementation of the relational database...........................................................8
Creation........................................................................................................................................9
Constraints.................................................................................................................................11
Population..................................................................................................................................11
Queries.......................................................................................................................................13
Rationale for the use of the relational model.................................................................................15
References......................................................................................................................................16

2DATA & KNOWLEDGE MANAGEMENT
An analysis of the data security and data management
Data security and management, both are the main aspects of using relational database
management system (RDBMS). The data security can be achieved by maintain the data
consistency, integrity and quality (Liu et al. 2018). The data quality can be achieved by using
constraints in a database along with the integrity and consistency. On other hand, the
management of the data is also achieved during the design process of the database design. For
data security and management several designing processes are utilized, such as Entity
relationship diagram modelling, normalization, and data dictionary which stores the Meta data of
the database (Jukic, Vrbsky and Nestorov 2014).
ERD
In a Relational Database Management System, the real world objects are identified as
Entities. These Entity sets stored in a database keeps the information. Attributes are used for
keeping the information for an Entities (Rossi 2014). Before implementing the physical database
system, system analysis and design is done by developing Entity relationship Diagram (ERD).
The identification of the Entities and their attributes are done on the basis of the business process
of a company (Weske 2019). The ERD collects these entities and represent the attributes and
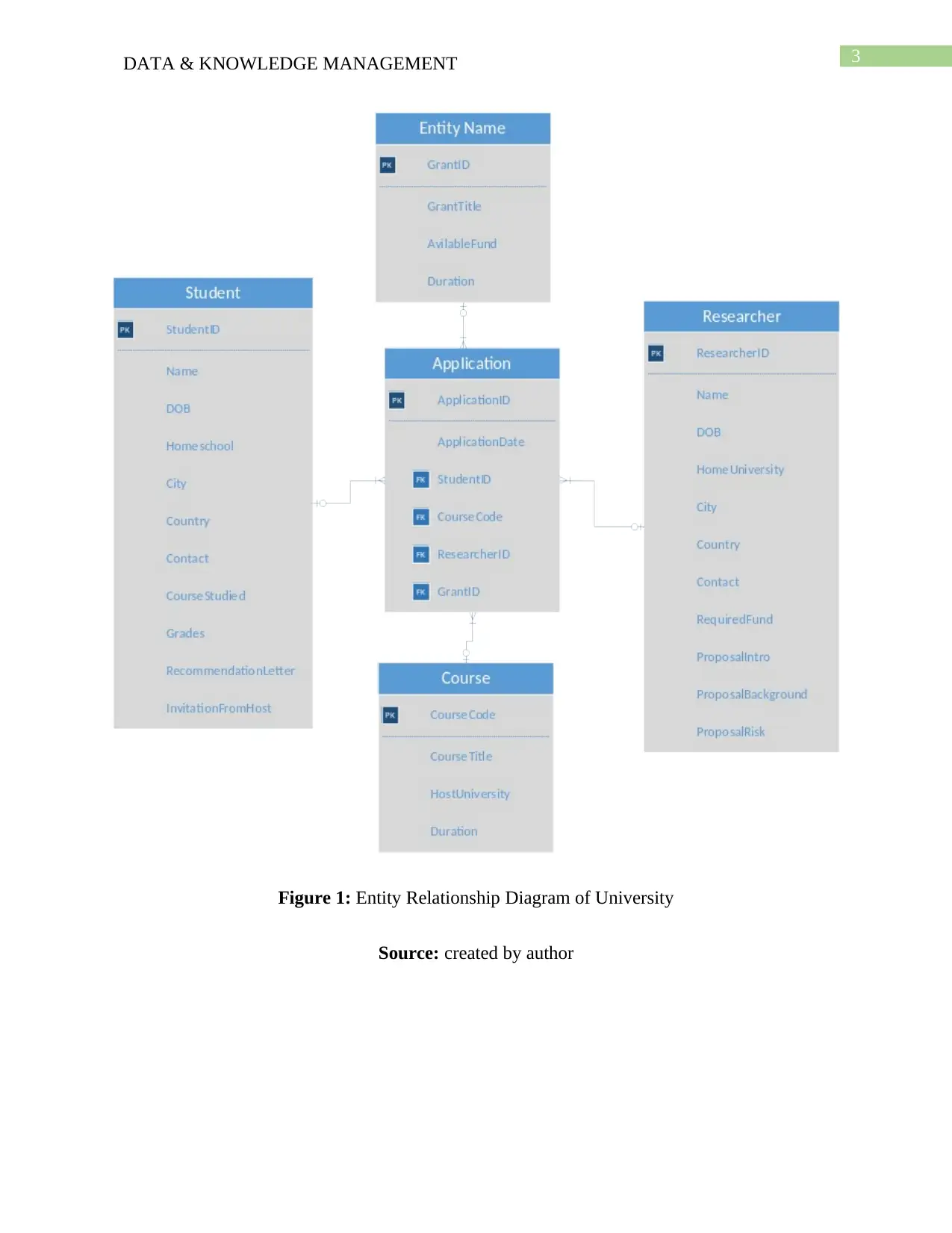
relations between the entities. Here the ERD of university is provided in figure 1.
An analysis of the data security and data management
Data security and management, both are the main aspects of using relational database
management system (RDBMS). The data security can be achieved by maintain the data
consistency, integrity and quality (Liu et al. 2018). The data quality can be achieved by using
constraints in a database along with the integrity and consistency. On other hand, the
management of the data is also achieved during the design process of the database design. For
data security and management several designing processes are utilized, such as Entity
relationship diagram modelling, normalization, and data dictionary which stores the Meta data of
the database (Jukic, Vrbsky and Nestorov 2014).
ERD
In a Relational Database Management System, the real world objects are identified as
Entities. These Entity sets stored in a database keeps the information. Attributes are used for
keeping the information for an Entities (Rossi 2014). Before implementing the physical database
system, system analysis and design is done by developing Entity relationship Diagram (ERD).
The identification of the Entities and their attributes are done on the basis of the business process
of a company (Weske 2019). The ERD collects these entities and represent the attributes and
relations between the entities. Here the ERD of university is provided in figure 1.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3DATA & KNOWLEDGE MANAGEMENT
Figure 1: Entity Relationship Diagram of University
Source: created by author
Figure 1: Entity Relationship Diagram of University
Source: created by author
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DATA & KNOWLEDGE MANAGEMENT
Normalization
To design the database schema from the conceptual diagram, Normalization is a method
used for the simplification of the relations and entities. In this technique tables are organized in
way that it should reduce redundancy, manage integrity and consistency of the data (Al-Absi and
Kang 2014). The dependencies between the data is also reduced during this process. The process
actually divides larger tables into smaller tables and links them using relations. The process of
normalizing the university database involves three steps named First Order Normalization,
Second Order Normalization and Third Order Normalization.
First Order Normalization
According to the first order normalization, the tables should only have atomic values. It
means the values stored by the attribute should only contain single values. The developed ERD
has the attributes that only stores single values (Cellary, Morzy and Gelenbe 2014). The proposal
details were first holding three values intro, background and risk. These three have been
reorganized as single attribute in the researcher table named, proposalIntro, proposalBackground
and proposalrisk. Rest of the relations are in first normal form.
Second Order Normalization
According to second form of normalization, the relations should be in first order
normalized and all the non key attributes of a relation should be depend on the key attribute of
the table. The key attributes of the table are defined as the primary keys of the table. In the
developed ERD, all the non-key attributes depends on the primary key of the table (di Vimercati
et al. 2014). For example the student name, city, country, contact etc. can be identified by
student id. Hence it can be said that the relations are in Second Normal form.
Normalization
To design the database schema from the conceptual diagram, Normalization is a method
used for the simplification of the relations and entities. In this technique tables are organized in
way that it should reduce redundancy, manage integrity and consistency of the data (Al-Absi and
Kang 2014). The dependencies between the data is also reduced during this process. The process
actually divides larger tables into smaller tables and links them using relations. The process of
normalizing the university database involves three steps named First Order Normalization,
Second Order Normalization and Third Order Normalization.
First Order Normalization
According to the first order normalization, the tables should only have atomic values. It
means the values stored by the attribute should only contain single values. The developed ERD
has the attributes that only stores single values (Cellary, Morzy and Gelenbe 2014). The proposal
details were first holding three values intro, background and risk. These three have been
reorganized as single attribute in the researcher table named, proposalIntro, proposalBackground
and proposalrisk. Rest of the relations are in first normal form.
Second Order Normalization
According to second form of normalization, the relations should be in first order
normalized and all the non key attributes of a relation should be depend on the key attribute of
the table. The key attributes of the table are defined as the primary keys of the table. In the
developed ERD, all the non-key attributes depends on the primary key of the table (di Vimercati
et al. 2014). For example the student name, city, country, contact etc. can be identified by
student id. Hence it can be said that the relations are in Second Normal form.

5DATA & KNOWLEDGE MANAGEMENT
Third Order Normalization
According to the third normal form, the relations should be in second normal form first
and there should not be any transitive functional dependencies between the attributes (Varga
2019). To eliminate the transitive functional dependencies between the course and student as
well as researchers and grants, a new table is construct named application. It stores the all other
tables primary keys as foreign keys. Hence, it can be said that the relation is in Third Normal
form.
Database Schema
Database schema represents the physical structure of the database. It consisting of tables,
attributes, their data type and data sizes (Cleve et al. 2015). The database schema for the
University database is given below in figure 2.
Third Order Normalization
According to the third normal form, the relations should be in second normal form first
and there should not be any transitive functional dependencies between the attributes (Varga
2019). To eliminate the transitive functional dependencies between the course and student as
well as researchers and grants, a new table is construct named application. It stores the all other
tables primary keys as foreign keys. Hence, it can be said that the relation is in Third Normal
form.
Database Schema
Database schema represents the physical structure of the database. It consisting of tables,
attributes, their data type and data sizes (Cleve et al. 2015). The database schema for the
University database is given below in figure 2.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DATA & KNOWLEDGE MANAGEMENT
Figure 2: Database Schema
Source: created by author
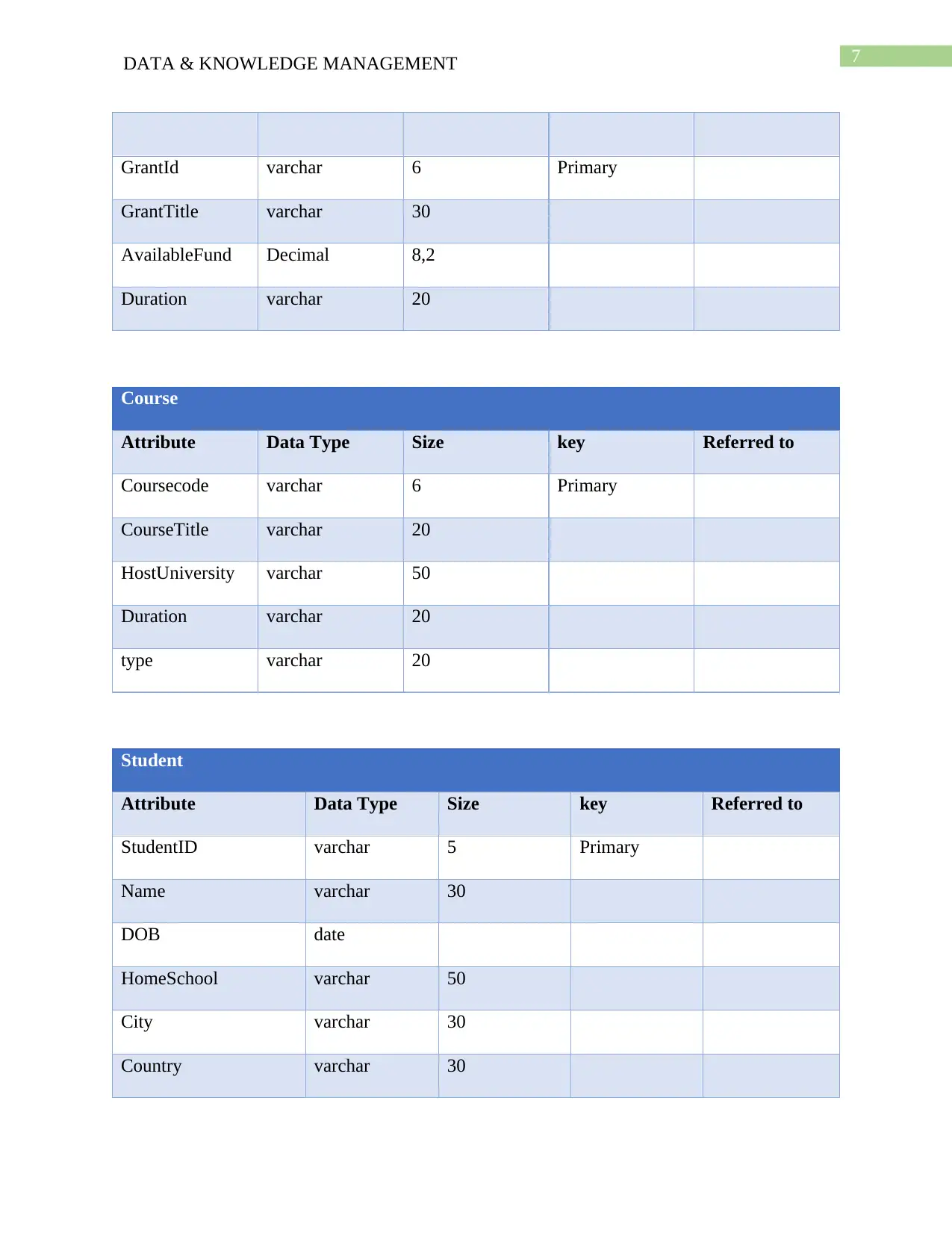
Data Dictionary
Data dictionary of a Relational database management system contains the metadata of the
database. It contains the information about the objects used in the database such as table names,
constraints in tables, columns, owner of the table, data types and data sizes of the columns
(Kramer and Thalheim 2014). The data dictionary developed for the university database is given
below:
Grants
Attribute Data Type Size key Referred to
Figure 2: Database Schema
Source: created by author
Data Dictionary
Data dictionary of a Relational database management system contains the metadata of the
database. It contains the information about the objects used in the database such as table names,
constraints in tables, columns, owner of the table, data types and data sizes of the columns
(Kramer and Thalheim 2014). The data dictionary developed for the university database is given
below:
Grants
Attribute Data Type Size key Referred to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7DATA & KNOWLEDGE MANAGEMENT
GrantId varchar 6 Primary
GrantTitle varchar 30
AvailableFund Decimal 8,2
Duration varchar 20
Course
Attribute Data Type Size key Referred to
Coursecode varchar 6 Primary
CourseTitle varchar 20
HostUniversity varchar 50
Duration varchar 20
type varchar 20
Student
Attribute Data Type Size key Referred to
StudentID varchar 5 Primary
Name varchar 30
DOB date
HomeSchool varchar 50
City varchar 30
Country varchar 30
GrantId varchar 6 Primary
GrantTitle varchar 30
AvailableFund Decimal 8,2
Duration varchar 20
Course
Attribute Data Type Size key Referred to
Coursecode varchar 6 Primary
CourseTitle varchar 20
HostUniversity varchar 50
Duration varchar 20
type varchar 20
Student
Attribute Data Type Size key Referred to
StudentID varchar 5 Primary
Name varchar 30
DOB date
HomeSchool varchar 50
City varchar 30
Country varchar 30
8DATA & KNOWLEDGE MANAGEMENT
Contact int
CourseStudied varchar 50
Grades varchar 15
RecommendationLetter varchar 3
InvitationFromtheHost varchar 3
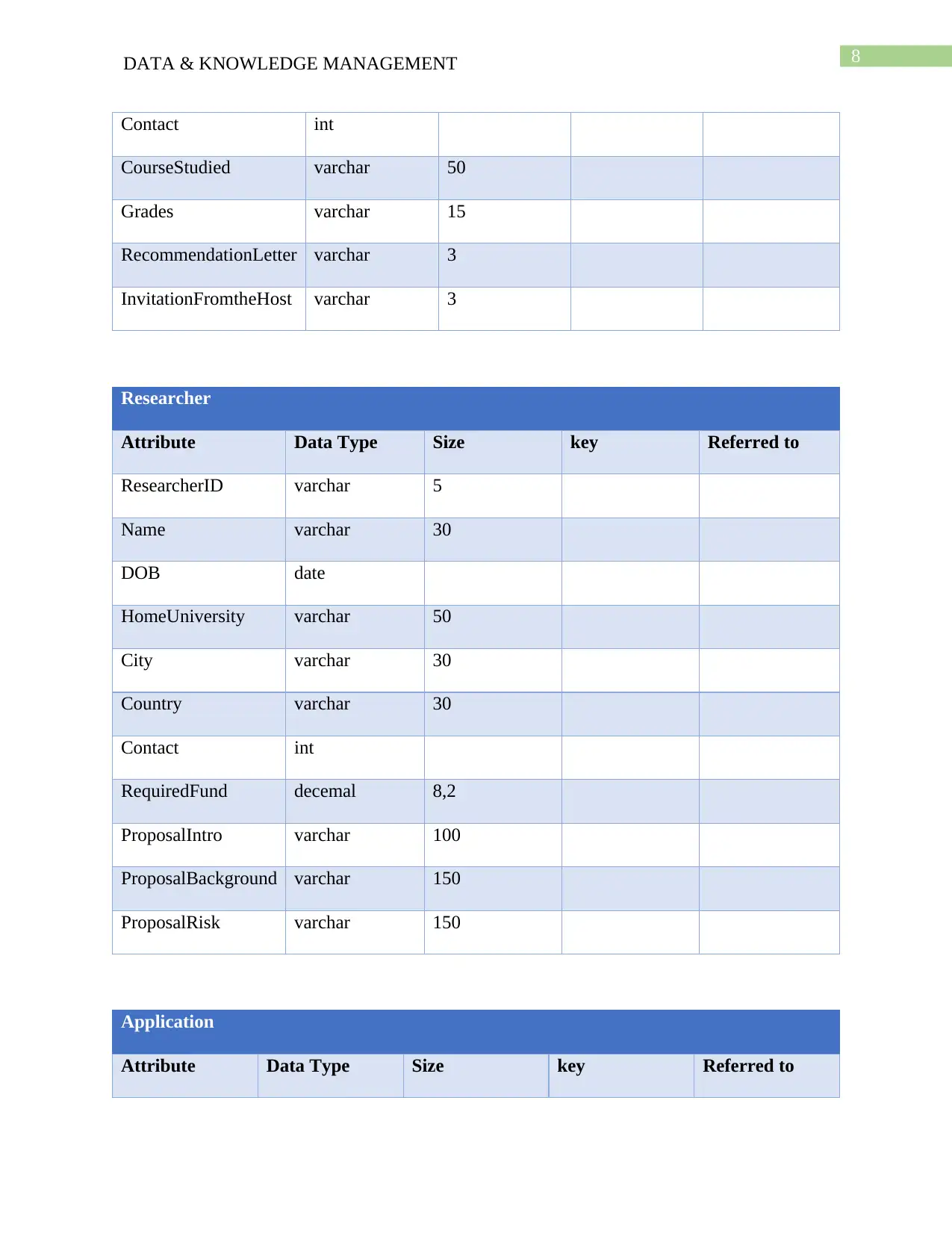
Researcher
Attribute Data Type Size key Referred to
ResearcherID varchar 5
Name varchar 30
DOB date
HomeUniversity varchar 50
City varchar 30
Country varchar 30
Contact int
RequiredFund decemal 8,2
ProposalIntro varchar 100
ProposalBackground varchar 150
ProposalRisk varchar 150
Application
Attribute Data Type Size key Referred to
Contact int
CourseStudied varchar 50
Grades varchar 15
RecommendationLetter varchar 3
InvitationFromtheHost varchar 3
Researcher
Attribute Data Type Size key Referred to
ResearcherID varchar 5
Name varchar 30
DOB date
HomeUniversity varchar 50
City varchar 30
Country varchar 30
Contact int
RequiredFund decemal 8,2
ProposalIntro varchar 100
ProposalBackground varchar 150
ProposalRisk varchar 150
Application
Attribute Data Type Size key Referred to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DATA & KNOWLEDGE MANAGEMENT
ApplicationID varchar 5 Primary
ApplicationDate date
StudentID varchar 5 Foreign Student
CourseCode varchar 6 Foreign Course
ResearcherID varchar 5 Foreign Researcher
GrantID varchar 6 Foreign Grants
An evaluation & Implementation of the relational database
The evaluation of the database starts with the creation of the database with the help of the
developed Entity relationship diagram. The tables are structured and created using the Data
definition Language (Elmasri 2018). All the key constraints are implemented wherever it
required. The key constraints helps in establishing relationship between the table and makes the
data identifiable.
Creation
Below the creation of the database tables are explained using SQL (DDL statement) codes.
Application Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[Application](
[ApplicationID] [varchar](5) NOT NULL,
[ApplicationDate] [date] NOT NULL,
[StudentID] [varchar](5) NULL,
[CourseCode] [varchar](6) NULL,
[ResearcherID] [varchar](5) NULL,
[GrantID] [varchar](6) NULL,
PRIMARY KEY CLUSTERED
ApplicationID varchar 5 Primary
ApplicationDate date
StudentID varchar 5 Foreign Student
CourseCode varchar 6 Foreign Course
ResearcherID varchar 5 Foreign Researcher
GrantID varchar 6 Foreign Grants
An evaluation & Implementation of the relational database
The evaluation of the database starts with the creation of the database with the help of the
developed Entity relationship diagram. The tables are structured and created using the Data
definition Language (Elmasri 2018). All the key constraints are implemented wherever it
required. The key constraints helps in establishing relationship between the table and makes the
data identifiable.
Creation
Below the creation of the database tables are explained using SQL (DDL statement) codes.
Application Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[Application](
[ApplicationID] [varchar](5) NOT NULL,
[ApplicationDate] [date] NOT NULL,
[StudentID] [varchar](5) NULL,
[CourseCode] [varchar](6) NULL,
[ResearcherID] [varchar](5) NULL,
[GrantID] [varchar](6) NULL,
PRIMARY KEY CLUSTERED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DATA & KNOWLEDGE MANAGEMENT
(
[ApplicationID] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
Grants Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[Grants](
[GrantID] [varchar](6) NOT NULL,
[GrantTitle] [varchar](30) NULL,
[AvailableFund] [decimal](8, 2) NOT NULL,
[Duration] [varchar](20) NOT NULL,
PRIMARY KEY CLUSTERED
(
[GrantID] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
Course Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[course](
[CourseCode] [varchar](6) NOT NULL,
[CourseTitle] [varchar](20) NOT NULL,
[HostUniversity] [varchar](50) NOT NULL,
[Duration] [varchar](20) NOT NULL,
[Type] [varchar](20) NOT NULL,
PRIMARY KEY CLUSTERED
(
[CourseCode] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
(
[ApplicationID] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
Grants Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[Grants](
[GrantID] [varchar](6) NOT NULL,
[GrantTitle] [varchar](30) NULL,
[AvailableFund] [decimal](8, 2) NOT NULL,
[Duration] [varchar](20) NOT NULL,
PRIMARY KEY CLUSTERED
(
[GrantID] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
Course Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[course](
[CourseCode] [varchar](6) NOT NULL,
[CourseTitle] [varchar](20) NOT NULL,
[HostUniversity] [varchar](50) NOT NULL,
[Duration] [varchar](20) NOT NULL,
[Type] [varchar](20) NOT NULL,
PRIMARY KEY CLUSTERED
(
[CourseCode] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO

11DATA & KNOWLEDGE MANAGEMENT
Student Tale
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[student](
[StudentID] [varchar](5) NOT NULL,
[Name] [varchar](30) NOT NULL,
[DOB] [date] NOT NULL,
[HomeSchool] [varchar](50) NOT NULL,
[City] [varchar](30) NOT NULL,
[Country] [varchar](30) NOT NULL,
[Contact] [int] NOT NULL,
[CourseStudied] [varchar](50) NOT NULL,
[Grades] [varchar](15) NOT NULL,
[RecommendationLetter] [varchar](3) NOT NULL,
[InvitationFromTheHost] [varchar](3) NOT NULL,
PRIMARY KEY CLUSTERED
(
[StudentID] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
Researcher Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[Researcher](
[ResearcherID] [varchar](5) NOT NULL,
[Name] [varchar](30) NOT NULL,
[DOB] [date] NOT NULL,
[HomeUniversity] [varchar](50) NOT NULL,
[City] [varchar](30) NOT NULL,
[Country] [varchar](30) NOT NULL,
[Contact] [int] NOT NULL,
[RequiredFund] [decimal](8, 2) NOT NULL,
[ProposalIntro] [varchar](100) NOT NULL,
[ProposalBackground] [varchar](150) NOT NULL,
[ProposalRisk] [varchar](150) NOT NULL,
PRIMARY KEY CLUSTERED
(
[ResearcherID] ASC
Student Tale
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[student](
[StudentID] [varchar](5) NOT NULL,
[Name] [varchar](30) NOT NULL,
[DOB] [date] NOT NULL,
[HomeSchool] [varchar](50) NOT NULL,
[City] [varchar](30) NOT NULL,
[Country] [varchar](30) NOT NULL,
[Contact] [int] NOT NULL,
[CourseStudied] [varchar](50) NOT NULL,
[Grades] [varchar](15) NOT NULL,
[RecommendationLetter] [varchar](3) NOT NULL,
[InvitationFromTheHost] [varchar](3) NOT NULL,
PRIMARY KEY CLUSTERED
(
[StudentID] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY =
OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
Researcher Table
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[Researcher](
[ResearcherID] [varchar](5) NOT NULL,
[Name] [varchar](30) NOT NULL,
[DOB] [date] NOT NULL,
[HomeUniversity] [varchar](50) NOT NULL,
[City] [varchar](30) NOT NULL,
[Country] [varchar](30) NOT NULL,
[Contact] [int] NOT NULL,
[RequiredFund] [decimal](8, 2) NOT NULL,
[ProposalIntro] [varchar](100) NOT NULL,
[ProposalBackground] [varchar](150) NOT NULL,
[ProposalRisk] [varchar](150) NOT NULL,
PRIMARY KEY CLUSTERED
(
[ResearcherID] ASC
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




