Aventis School Digital Forensics Report: Data Leak Investigation
VerifiedAdded on 2022/12/15
|13
|2577
|198
Report
AI Summary
This digital forensics report explores the challenges of traditional data collection methods in the context of evolving storage technologies, advocating for a smart collection paradigm to reduce investigation time in data leak cases. It outlines the importance of digital forensics in the face of increasing cybercrime, defining its role in the collection, validation, and analysis of digital evidence. The report details methodologies for hard disk collection, including the use of write-blockers and data compression. It also examines common data leak channels, such as USB devices and email, and presents a step-by-step approach to investigations, including data collection, analysis, and report writing. The report emphasizes the importance of selective imaging, user identification, and evidence preservation, providing examples of how digital forensic analysis aids in identifying and quantifying data leaks. Furthermore, it highlights the significance of link file analysis and the need for concise, understandable reports for legal proceedings, supporting the main thesis about a probable information leak case and emphasizing the importance of evidence in court.

Running head: DIGITAL FORENSICS 1
Digital Forensics
Date
Student Name/ Student Number
Digital Forensics
Date
Student Name/ Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSICS 2
Executive summary
The ever developing storage device functionality poses an excessive restrict to the same
old digital forensics collection tactics primarily based on duplicating the unique storage device
through the way of growing a chunk‐through manner of‐bit replica. Such a traditional method is
accompanied, even though the aim of the research is to find out a constrained amount of virtual
objects to guide or refute investigative speculation related to a particular case elegance.
Consequently, on this paper, we advise a new technique to address data leak cases, through
utilizing a smart collection paradigm, a quick analysis technique that reduces studies time.
Executive summary
The ever developing storage device functionality poses an excessive restrict to the same
old digital forensics collection tactics primarily based on duplicating the unique storage device
through the way of growing a chunk‐through manner of‐bit replica. Such a traditional method is
accompanied, even though the aim of the research is to find out a constrained amount of virtual
objects to guide or refute investigative speculation related to a particular case elegance.
Consequently, on this paper, we advise a new technique to address data leak cases, through
utilizing a smart collection paradigm, a quick analysis technique that reduces studies time.

DIGITAL FORENSICS 3
Table of Contents
Executive summary.....................................................................................................................................2
Introduction.................................................................................................................................................4
Hard disk collection.................................................................................................................................5
Ordinary leak channels............................................................................................................................6
Methodology used......................................................................................................................................7
Investigations..........................................................................................................................................7
Evidence collection and preservation......................................................................................................8
Discussion................................................................................................................................................9
Supporting evidence..............................................................................................................................10
Summary and conclusion...........................................................................................................................12
References.................................................................................................................................................12
Table of Contents
Executive summary.....................................................................................................................................2
Introduction.................................................................................................................................................4
Hard disk collection.................................................................................................................................5
Ordinary leak channels............................................................................................................................6
Methodology used......................................................................................................................................7
Investigations..........................................................................................................................................7
Evidence collection and preservation......................................................................................................8
Discussion................................................................................................................................................9
Supporting evidence..............................................................................................................................10
Summary and conclusion...........................................................................................................................12
References.................................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DIGITAL FORENSICS 4
Introduction
Living in the virtual era, we have emerged depending on digital statistics and its
associated fields of applications. Regrettably, the pervasiveness of the digital era has given
upward push to an excessive amount of cybercrime, which might also range from identity
robbery to a leak of sensitive digital records. The challenge that aids investigators whilst dealing
with digital crimes is referred to as virtual forensics. It’s been described because of the exercise
of scientifically derived and proven technical techniques closer to the safety, collection,
validation, identification, evaluation, documentation, and presentation of digital facts for the
reason of furthering reconstruction of criminal activities and facilitating smooth prediction for
adverse and unauthorized behaviors Palmer, (2011).
To this point, the investigative fashion has been toward a state of affairs in which the
virtual statistics frequently represents the handiest possible clue that can resolve the related case.
Due to the fact the number of instances concerning virtual records is growing, investigative
groups are in excessive call for. Some accounting and regulation businesses have already set up
such centers, wherein they utilize a wide style of digital forensic technology. As an example, a
first-rate South Korean digital forensics middle has become set up to cope with critical instances,
which includes Il‐Shim celebration, Shin Jung‐Ah, and lots of extras.
In this paper, we endorse a framework that may be used to address information leak
instances. To begin with, an outline of a selective information series technique can be given.
Then, the taxonomy of data leak channels will be outlined and strategies for studying data leak
artifacts can be mentioned. Complete examples of records leak instances will be defined and
mentioned, pointing out how the ensuing digital investigation is progressed in comparison with
the same old forensic method.
Introduction
Living in the virtual era, we have emerged depending on digital statistics and its
associated fields of applications. Regrettably, the pervasiveness of the digital era has given
upward push to an excessive amount of cybercrime, which might also range from identity
robbery to a leak of sensitive digital records. The challenge that aids investigators whilst dealing
with digital crimes is referred to as virtual forensics. It’s been described because of the exercise
of scientifically derived and proven technical techniques closer to the safety, collection,
validation, identification, evaluation, documentation, and presentation of digital facts for the
reason of furthering reconstruction of criminal activities and facilitating smooth prediction for
adverse and unauthorized behaviors Palmer, (2011).
To this point, the investigative fashion has been toward a state of affairs in which the
virtual statistics frequently represents the handiest possible clue that can resolve the related case.
Due to the fact the number of instances concerning virtual records is growing, investigative
groups are in excessive call for. Some accounting and regulation businesses have already set up
such centers, wherein they utilize a wide style of digital forensic technology. As an example, a
first-rate South Korean digital forensics middle has become set up to cope with critical instances,
which includes Il‐Shim celebration, Shin Jung‐Ah, and lots of extras.
In this paper, we endorse a framework that may be used to address information leak
instances. To begin with, an outline of a selective information series technique can be given.
Then, the taxonomy of data leak channels will be outlined and strategies for studying data leak
artifacts can be mentioned. Complete examples of records leak instances will be defined and
mentioned, pointing out how the ensuing digital investigation is progressed in comparison with
the same old forensic method.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSICS 5
Hard disk collection
In this segment, we are able to present a few noteworthy effects concerning the statistics
series time whilst the use of the usual collection approach as said by way of the digital forensics
field. The required time in generating the primary picture and the related hash cost relies upon on
the tough power potential and on the hardware abilities of the gathering tool. As an example,
imaging a Serial advanced generation Attachment (SATA) difficult drive of 250 GB takes about
one hundred min with present-day imager tools.
In our experiments, we've considered distinctive hard disks, as illustrated in table 1. The
collection section has been executed via a write‐blocker answer, namely FastBloc2 discipline
version, issued by using EnCase (v6.eleven) eight. At the host aspect, FastBloc2 has two
FireWire four hundred interfaces, a conventional Serial Bus (USB) interface, and a strength
connector. On the force aspect, there's an advanced generation Attachment (ATA) interface and a
Molex strength connector. The seized difficult power turned into plugged to the write blocker via
an IDE interface. Furthermore, the write blocker became linked to the forensic workstation via a
USB 2 hyperlink that gives up to four hundred‐Mbps bandwidth. Further, the compression option
became enabled to reduce the ensuing binary image.
Table 1.0
C:\Documents and Settings\Jo\My
Documents\Jo_Clients\NUP 20080207524-00000002.png
20080207524-00000003.png
20080207524-00000004.png
NUP_v017.png
C:\Documents and Settings\Jo\My
Documents\Jo_Clients\Star_Lord Star_Lord_Splash_02.bmp
Sniper2.png
Gated_Map78.png
Flagstaff1.png
Controlls_Defaults9.png
Hard disk collection
In this segment, we are able to present a few noteworthy effects concerning the statistics
series time whilst the use of the usual collection approach as said by way of the digital forensics
field. The required time in generating the primary picture and the related hash cost relies upon on
the tough power potential and on the hardware abilities of the gathering tool. As an example,
imaging a Serial advanced generation Attachment (SATA) difficult drive of 250 GB takes about
one hundred min with present-day imager tools.
In our experiments, we've considered distinctive hard disks, as illustrated in table 1. The
collection section has been executed via a write‐blocker answer, namely FastBloc2 discipline
version, issued by using EnCase (v6.eleven) eight. At the host aspect, FastBloc2 has two
FireWire four hundred interfaces, a conventional Serial Bus (USB) interface, and a strength
connector. On the force aspect, there's an advanced generation Attachment (ATA) interface and a
Molex strength connector. The seized difficult power turned into plugged to the write blocker via
an IDE interface. Furthermore, the write blocker became linked to the forensic workstation via a
USB 2 hyperlink that gives up to four hundred‐Mbps bandwidth. Further, the compression option
became enabled to reduce the ensuing binary image.
Table 1.0
C:\Documents and Settings\Jo\My
Documents\Jo_Clients\NUP 20080207524-00000002.png
20080207524-00000003.png
20080207524-00000004.png
NUP_v017.png
C:\Documents and Settings\Jo\My
Documents\Jo_Clients\Star_Lord Star_Lord_Splash_02.bmp
Sniper2.png
Gated_Map78.png
Flagstaff1.png
Controlls_Defaults9.png

DIGITAL FORENSICS 6
C:\Documents and Settings\Jo\My
Documents\My Pictures bday_cake.jpg
bday_present.jpg
card_Pat.jpg
card_the-Jerk.jpg
susan_work.jpg
IMG_2454.jpg
IMG_2458.jpg
IMG_2463.jpg
IMG_2902
IMG_2913
IMG_2917
IMG_2919
Ordinary leak channels
In January 2009, two digital forensic companies conducted a survey of 1000 folks that
had retired in 2008 (United States). It confirmed that 58% of the respondents stole exclusive
information, such as the customer lists of the corporation thirteen. Further, 52% of respondents
answered that they copied private facts to a CD or DVD, 45% copied information in a USB
memory, and 35% responded that they used private e‐mail to switch confidential records. In the
end, 79% of the respondents spoke back that they stole information without permission of the
company or employers; 82% replied that there has been no audit or examination of electronic
documents before they left the employer. 24% responded that they could access the pc device of
the corporation or network, even once they retired. The document confirmed that there have been
diverse statistics leak channels, however commonly, four principal ones had been used: copying
documents by way of connecting an external storage tool thru USB, FireWire, or the to be had
channel links; statistics leak by way of burning data on a CD‐ROM; sending information via
C:\Documents and Settings\Jo\My
Documents\My Pictures bday_cake.jpg
bday_present.jpg
card_Pat.jpg
card_the-Jerk.jpg
susan_work.jpg
IMG_2454.jpg
IMG_2458.jpg
IMG_2463.jpg
IMG_2902
IMG_2913
IMG_2917
IMG_2919
Ordinary leak channels
In January 2009, two digital forensic companies conducted a survey of 1000 folks that
had retired in 2008 (United States). It confirmed that 58% of the respondents stole exclusive
information, such as the customer lists of the corporation thirteen. Further, 52% of respondents
answered that they copied private facts to a CD or DVD, 45% copied information in a USB
memory, and 35% responded that they used private e‐mail to switch confidential records. In the
end, 79% of the respondents spoke back that they stole information without permission of the
company or employers; 82% replied that there has been no audit or examination of electronic
documents before they left the employer. 24% responded that they could access the pc device of
the corporation or network, even once they retired. The document confirmed that there have been
diverse statistics leak channels, however commonly, four principal ones had been used: copying
documents by way of connecting an external storage tool thru USB, FireWire, or the to be had
channel links; statistics leak by way of burning data on a CD‐ROM; sending information via
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
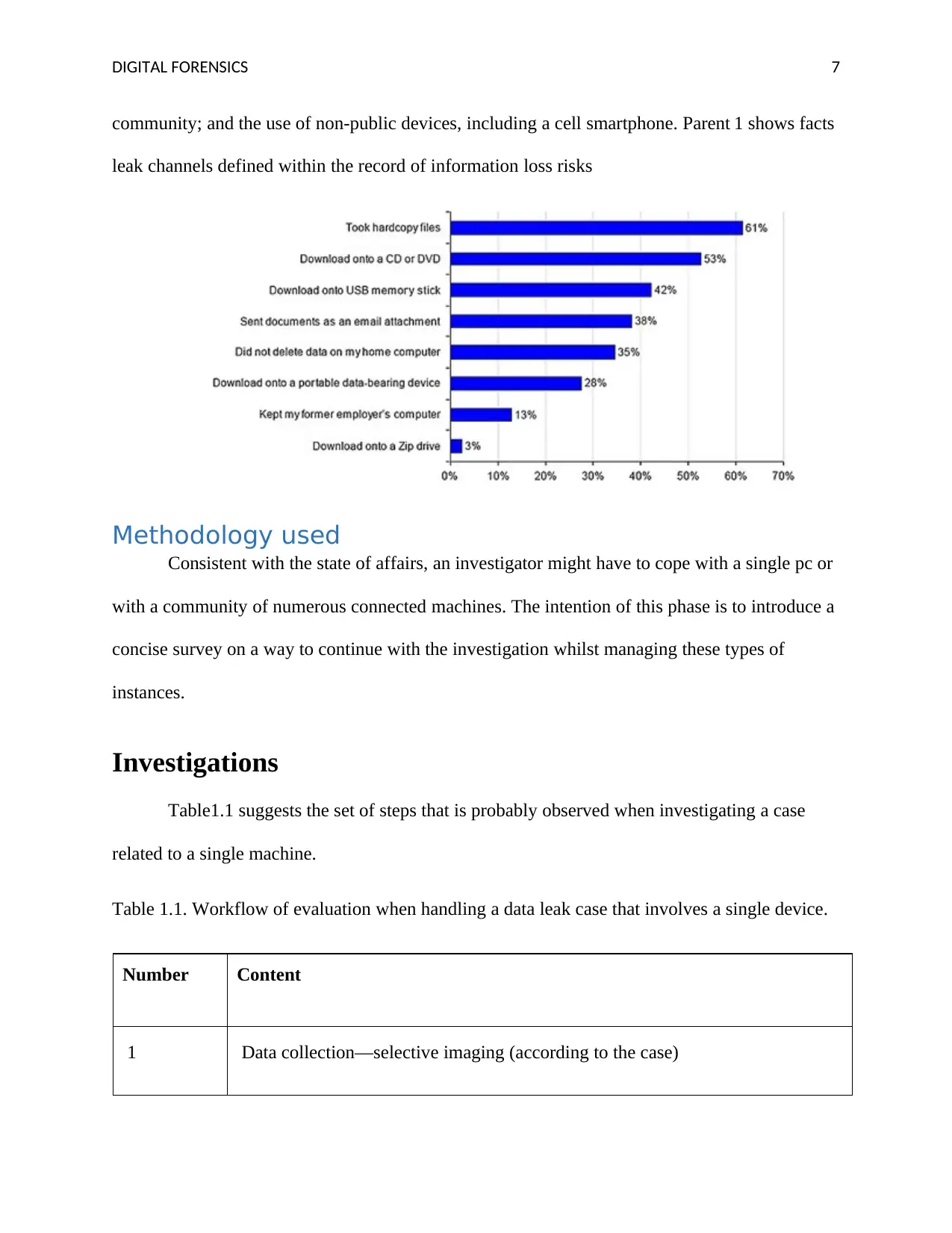
DIGITAL FORENSICS 7
community; and the use of non-public devices, including a cell smartphone. Parent 1 shows facts
leak channels defined within the record of information loss risks
Methodology used
Consistent with the state of affairs, an investigator might have to cope with a single pc or
with a community of numerous connected machines. The intention of this phase is to introduce a
concise survey on a way to continue with the investigation whilst managing these types of
instances.
Investigations
Table1.1 suggests the set of steps that is probably observed when investigating a case
related to a single machine.
Table 1.1. Workflow of evaluation when handling a data leak case that involves a single device.
Number Content
1 Data collection—selective imaging (according to the case)
community; and the use of non-public devices, including a cell smartphone. Parent 1 shows facts
leak channels defined within the record of information loss risks
Methodology used
Consistent with the state of affairs, an investigator might have to cope with a single pc or
with a community of numerous connected machines. The intention of this phase is to introduce a
concise survey on a way to continue with the investigation whilst managing these types of
instances.
Investigations
Table1.1 suggests the set of steps that is probably observed when investigating a case
related to a single machine.
Table 1.1. Workflow of evaluation when handling a data leak case that involves a single device.
Number Content
1 Data collection—selective imaging (according to the case)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSICS 8
Number Content
2 Data analysis
User identification
Registry analysis
Profile external storage devices
System event log analysis
CD/DVD/Blu‐ray ROM burning tool log analysis
Link file analysis
MAC times analysis and correlation
Timeline creation
3 Writing analysis report
Evidence collection and preservation
Data collection might be accomplished on‐the‐spot on live structures, as well as on a
switched‐off gadget. The gathering should regard some objects, together with the ones associated
Number Content
2 Data analysis
User identification
Registry analysis
Profile external storage devices
System event log analysis
CD/DVD/Blu‐ray ROM burning tool log analysis
Link file analysis
MAC times analysis and correlation
Timeline creation
3 Writing analysis report
Evidence collection and preservation
Data collection might be accomplished on‐the‐spot on live structures, as well as on a
switched‐off gadget. The gathering should regard some objects, together with the ones associated

DIGITAL FORENSICS 9
with a data leak research 2.1. (Carrier & Spafford, 2013) Then, a sound analysis of gathered
records should be finished. As a first step, the user(s) of the investigated machine need to be
identified. This challenge is commonly finished by means of analyzing the SAM (safety Account
supervisor) hive of the Registry eleven. Subsequent, thorough profiling of plugged devices need
to be carried out, following the taxonomy offered in table 1. This challenge usually involves the
analysis of the Registry, in particular of those keys associated with community and BUS physical
layers, as mentioned in phase 3. A clean assessment of profiling and what steps to take is
supplied in 11 and 15. for instance, USB profiling regards the gathering of statistics, which
include supplier, product, version, serial quantity, the drive letter to which the tool is mapped,
global specific Identifier, person associated with the device, the primary time that the device
turned into connected (installation time), the primary time that the tool was related after
remaining reboot, and the closing time that the tool changed into connected. Greater precisely,
the final time the device became connected should be correlated with MFT MAC (changed,
Accessed, Created) time evaluation to decide events, along with a bulk replica, which suggests a
massive transfer of files from a computer to an external tool. Turner, (2016). In this sort of case,
as a minimum in working systems (OSs) as much as Windows XP SP3, the get admission to time
of copied‐out files can be determined as non-stop and developing, and a time interval from the
start of the copy to its stop may be detected (e.g., ▽T = t2 − t1). This isn't always real in later
OSs, consisting of Windows Vista and seven where, for optimization purposes, the access time
update has been disabled as default via setting NtfsDisableLastAccessUpdatekey to 0 (HKLM\
machine\CurrentControlSet\manage\FileSystem).
with a data leak research 2.1. (Carrier & Spafford, 2013) Then, a sound analysis of gathered
records should be finished. As a first step, the user(s) of the investigated machine need to be
identified. This challenge is commonly finished by means of analyzing the SAM (safety Account
supervisor) hive of the Registry eleven. Subsequent, thorough profiling of plugged devices need
to be carried out, following the taxonomy offered in table 1. This challenge usually involves the
analysis of the Registry, in particular of those keys associated with community and BUS physical
layers, as mentioned in phase 3. A clean assessment of profiling and what steps to take is
supplied in 11 and 15. for instance, USB profiling regards the gathering of statistics, which
include supplier, product, version, serial quantity, the drive letter to which the tool is mapped,
global specific Identifier, person associated with the device, the primary time that the device
turned into connected (installation time), the primary time that the tool was related after
remaining reboot, and the closing time that the tool changed into connected. Greater precisely,
the final time the device became connected should be correlated with MFT MAC (changed,
Accessed, Created) time evaluation to decide events, along with a bulk replica, which suggests a
massive transfer of files from a computer to an external tool. Turner, (2016). In this sort of case,
as a minimum in working systems (OSs) as much as Windows XP SP3, the get admission to time
of copied‐out files can be determined as non-stop and developing, and a time interval from the
start of the copy to its stop may be detected (e.g., ▽T = t2 − t1). This isn't always real in later
OSs, consisting of Windows Vista and seven where, for optimization purposes, the access time
update has been disabled as default via setting NtfsDisableLastAccessUpdatekey to 0 (HKLM\
machine\CurrentControlSet\manage\FileSystem).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DIGITAL FORENSICS 10
Discussion
Different sources of evidence may be the machine event logs and burning force tool logs.
The former category information diffusion of day‐to‐day activities that occur on windows
structures and is configurable to report a variety of additional activities. Those events are broken
up into categories carried out thru diverse event logs themselves, inclusive of security, system,
and alertness occasion logs. An investigator might discover the number of attempts that a person
tried to log on a system by means of analyzing such documents. The latter category of logs is
associated with using burning tools that might be used to copy sensitive facts. For instance, Nero
burning Rom maintains a trace of the burning interest in the Nerohistory.log record that
represents a crucial report for which to look whilst investigating data leak cases.
What we have verified is that with the aid of selecting unique information related to a
leak scenario, the investigation can be conducted a whole lot quicker as compared with
traditional post‐mortem analysis. Several assets of evidence had been concerned in this case.
Evidence from the document server became collected on‐the‐spot through a live methodology.
The Registry, occasion files, unstable reminiscence, page file, and burning software logs had
been collected, offering essential and relevant statistics nearly in actual time. The essence of this
investigative method is to look for proof that is strictly associated with the type of case that the
investigator is examining.
Supporting evidence
The effective course and the file call of the original documents are left on this folder, so
we are able to check the traces of an outside storage tool and unique record names. Similarly,
despite the fact that a consumer deletes files, modifications their names, or moves record, the
Discussion
Different sources of evidence may be the machine event logs and burning force tool logs.
The former category information diffusion of day‐to‐day activities that occur on windows
structures and is configurable to report a variety of additional activities. Those events are broken
up into categories carried out thru diverse event logs themselves, inclusive of security, system,
and alertness occasion logs. An investigator might discover the number of attempts that a person
tried to log on a system by means of analyzing such documents. The latter category of logs is
associated with using burning tools that might be used to copy sensitive facts. For instance, Nero
burning Rom maintains a trace of the burning interest in the Nerohistory.log record that
represents a crucial report for which to look whilst investigating data leak cases.
What we have verified is that with the aid of selecting unique information related to a
leak scenario, the investigation can be conducted a whole lot quicker as compared with
traditional post‐mortem analysis. Several assets of evidence had been concerned in this case.
Evidence from the document server became collected on‐the‐spot through a live methodology.
The Registry, occasion files, unstable reminiscence, page file, and burning software logs had
been collected, offering essential and relevant statistics nearly in actual time. The essence of this
investigative method is to look for proof that is strictly associated with the type of case that the
investigator is examining.
Supporting evidence
The effective course and the file call of the original documents are left on this folder, so
we are able to check the traces of an outside storage tool and unique record names. Similarly,
despite the fact that a consumer deletes files, modifications their names, or moves record, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSICS 11
associated link file isn't deleted and the ultimate updated time is left. Therefore, we are able to
take into account that a specific document became used. In addition, the direction name of the
original record remains within the link file. Inside the case of inspecting the course called, on
occasion, the force course might not exist in the present day machine. This truth may be justified
through thinking about that an external garage device has been plugged into the machine and
used. The hyperlink file analysis is sizable because it could be used to aid the main thesis
approximately a probable information leak case.
The digital forensic analysis reports concern an outline of proof that has been determined,
as well as its content and layout. (Korean Law, 2010) Most of the people of virtual forensic
reviews make a specialty of technical info and is not smooth to recognize with the aid of people
without the desired technical heritage, such as lawyers or judges. As a result, they require a
simple and concise, however entire, record. Particular information need to be supplied to apply a
document in a courtroom of law. First, the statistics related to the identification of the consumer
need to be protected. Certainly, the consequences of the evaluation will now not have any that
means if the data is accrued without verifying the consumer's identity. Second, the total time of
use of the tough disk is likewise very essential. Commonly, this time is predicted as the time
interval among the OS set up and the confiscation date. In addition, this unique time needs to be
verified considering a preceding OS set up that changed into related to every other computer
user. If strains of data leak are discovered and are related to a previous set up, that is, to a
preceding user, they want now not to be considered within the analysis, due to the fact they're
now not associated with the contemporary user. 1/3, the degree of facts leak harm need to be
recorded and quantified by means of summing all the facts leak contributions. Hence, we ought
to recall the financial harm resulting from distinctive data categories that have been stolen.
associated link file isn't deleted and the ultimate updated time is left. Therefore, we are able to
take into account that a specific document became used. In addition, the direction name of the
original record remains within the link file. Inside the case of inspecting the course called, on
occasion, the force course might not exist in the present day machine. This truth may be justified
through thinking about that an external garage device has been plugged into the machine and
used. The hyperlink file analysis is sizable because it could be used to aid the main thesis
approximately a probable information leak case.
The digital forensic analysis reports concern an outline of proof that has been determined,
as well as its content and layout. (Korean Law, 2010) Most of the people of virtual forensic
reviews make a specialty of technical info and is not smooth to recognize with the aid of people
without the desired technical heritage, such as lawyers or judges. As a result, they require a
simple and concise, however entire, record. Particular information need to be supplied to apply a
document in a courtroom of law. First, the statistics related to the identification of the consumer
need to be protected. Certainly, the consequences of the evaluation will now not have any that
means if the data is accrued without verifying the consumer's identity. Second, the total time of
use of the tough disk is likewise very essential. Commonly, this time is predicted as the time
interval among the OS set up and the confiscation date. In addition, this unique time needs to be
verified considering a preceding OS set up that changed into related to every other computer
user. If strains of data leak are discovered and are related to a previous set up, that is, to a
preceding user, they want now not to be considered within the analysis, due to the fact they're
now not associated with the contemporary user. 1/3, the degree of facts leak harm need to be
recorded and quantified by means of summing all the facts leak contributions. Hence, we ought
to recall the financial harm resulting from distinctive data categories that have been stolen.

DIGITAL FORENSICS 12
Fourth, we need to offer an in-depth record to justify and prove that an information leak case has
passed off.
Summary and conclusion
The method to create a primary photograph of a difficult disk has a demerit in terms of
speed, which could every so often draw out beside the point consequences of analysis, or may
additionally sluggish down the investigation. Consequently, on this paper, we've suggested the
correct proof collection approach and analysis specifically centered at statistics leak instances,
for each unmarried and network laptop‐primarily based structures. Thorough records leak
taxonomy has been presented and illustrated. In addition, the key elements of a quick triage of
essential proof in both unmarried and network instances has been provided. Sooner or later, a
sound instance of an actual case regarding network facts leaks research has been discussed, with
the aid of highlighting the maximum relevant elements. We believe that the discussed method
can drastically boost up comparable investigations and growing recognition in the virtual
forensic network.
Fourth, we need to offer an in-depth record to justify and prove that an information leak case has
passed off.
Summary and conclusion
The method to create a primary photograph of a difficult disk has a demerit in terms of
speed, which could every so often draw out beside the point consequences of analysis, or may
additionally sluggish down the investigation. Consequently, on this paper, we've suggested the
correct proof collection approach and analysis specifically centered at statistics leak instances,
for each unmarried and network laptop‐primarily based structures. Thorough records leak
taxonomy has been presented and illustrated. In addition, the key elements of a quick triage of
essential proof in both unmarried and network instances has been provided. Sooner or later, a
sound instance of an actual case regarding network facts leaks research has been discussed, with
the aid of highlighting the maximum relevant elements. We believe that the discussed method
can drastically boost up comparable investigations and growing recognition in the virtual
forensic network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



