CKIT519 Lab 3 & 4: Data Leakage Analysis and Evidence Collection
VerifiedAdded on 2022/09/22
|5
|954
|22
Practical Assignment
AI Summary
This assignment focuses on data leakage analysis using FTK Imager and OSForensics, based on a case scenario from the NIST CFREDS project. The student utilized an AWS Windows Server Desktop to analyze .dd image files of a PC and removable media. The process involved creating raw images with FTK Imager, exploring the tool's features in automatic, text, and hex modes, and discussing its pros and cons. The analysis included identifying file structures, contact information, and other evidence. The student also highlighted critical steps in evidence collection, such as using encrypted hard drives, generating MD5 hash files, and ensuring proper knowledge of forensic tools. The assignment covered potential mistakes in evidence handling, emphasizing the importance of password protection and hardware security. The student also used OSForensics for a more detailed view of the evidence and provided references for further study.

Lab 3 & 4 week: Data Leakage Analysis
Introduction
Here we had given a case scenario from the NIST CFREDS project, called the Data Leaked
Analysis, where we have given some images of the Operating system given. Here we have to
perform the analysis of the .dd file and one removable device file with the tool called FTK
images.
After that, we have to provide the information we gather out as an evidence which we can
submit in court which is admissible as an evidence.
Procedure:
I have taken the remote of AWS Windows Server Desktop, connection, after that check the
resources given for the analysis part.
Now I open the FTK Image tool for analysis and I got the below information after access it.
Firstly the FTK tool is use to create raw images of Hard Drive to securely submit the
image file to forensic lab for investigation on it.
After that we can see three type of mode, to check the evidences in FTK;
o Automatic Mode: Here we can see all the web graphics, web content, files,
images and video content.
o Text Mode: Here we can able to see the evidence contain in ASCII and
Unicode format.
o Hexa-format Mode: In this mode, it allows us to view every file data into hex-
decimal format.
Introduction
Here we had given a case scenario from the NIST CFREDS project, called the Data Leaked
Analysis, where we have given some images of the Operating system given. Here we have to
perform the analysis of the .dd file and one removable device file with the tool called FTK
images.
After that, we have to provide the information we gather out as an evidence which we can
submit in court which is admissible as an evidence.
Procedure:
I have taken the remote of AWS Windows Server Desktop, connection, after that check the
resources given for the analysis part.
Now I open the FTK Image tool for analysis and I got the below information after access it.
Firstly the FTK tool is use to create raw images of Hard Drive to securely submit the
image file to forensic lab for investigation on it.
After that we can see three type of mode, to check the evidences in FTK;
o Automatic Mode: Here we can see all the web graphics, web content, files,
images and video content.
o Text Mode: Here we can able to see the evidence contain in ASCII and
Unicode format.
o Hexa-format Mode: In this mode, it allows us to view every file data into hex-
decimal format.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
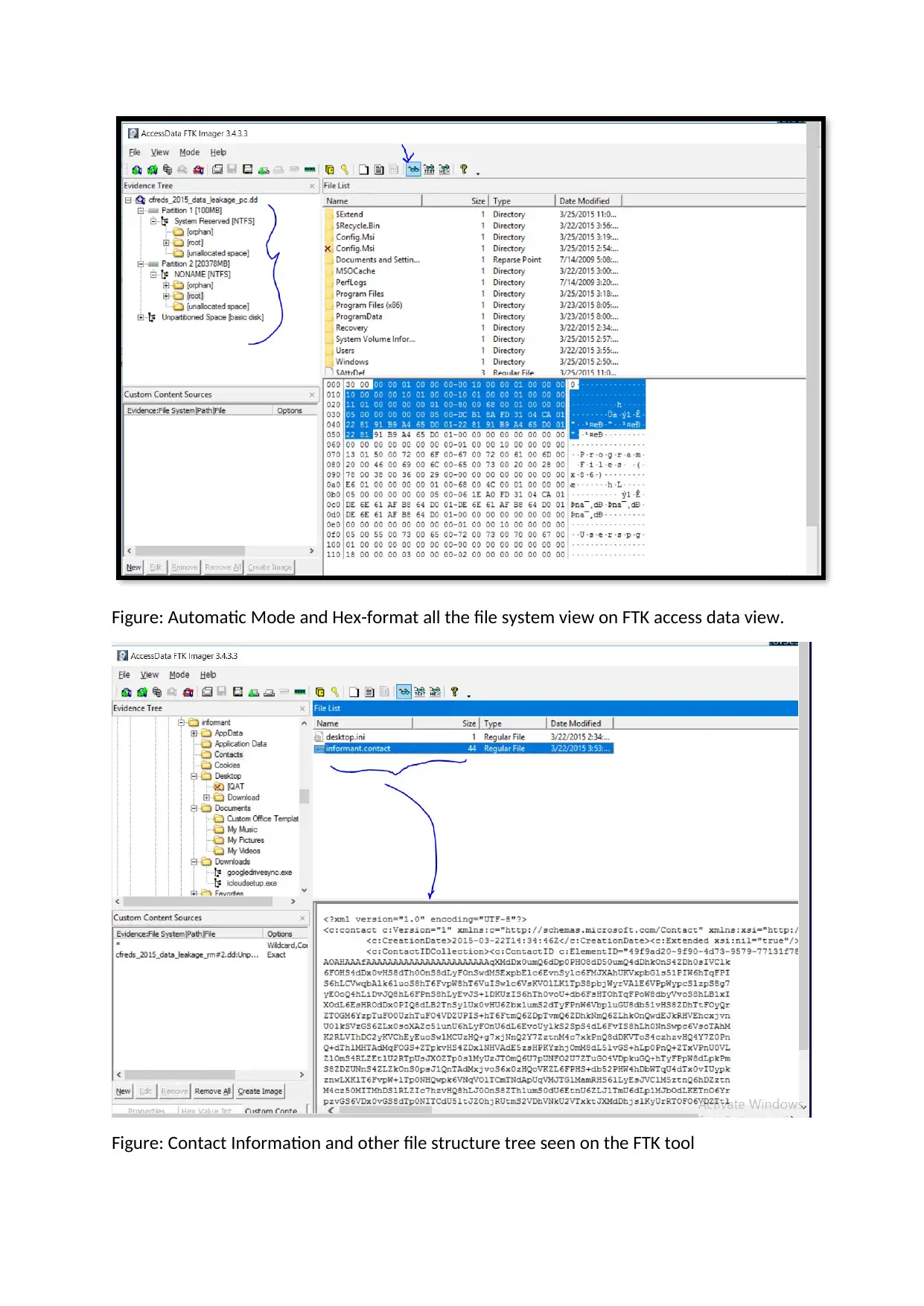
Figure: Automatic Mode and Hex-format all the file system view on FTK access data view.
Figure: Contact Information and other file structure tree seen on the FTK tool
Figure: Contact Information and other file structure tree seen on the FTK tool

Now let see some Pros and Cons of the FTK Tool, to understand why it is very critical
important to transfer data from one system to another.
Pros:
Very simple interface to use it.
Not so much critical options are available to access the tool.
The main benefit of this tool is we can create Image file for investigation
like .dd, .raw, .eo and .adi file formats.
It also capable of generating the Case Log files
Good bookmarking and salient reporting features are available as compare to other
tools
Also it comes free of cost.
Cons:
It does not support the scripting features, why we need it, because we can update
any file data for view in more details, and for decrypt any file which is protected or
some files formats we can change to view in plain text which is admissible in court as
an evidence.
Also it does not support Multi –tasking work, because to get the evidence we have to
check it File structure tree one by one which is time consuming.
Also, we don’t able to see the progress bar or any line bar, while we create the
Image file for transferring from victim system to secure Hard drive it can able to get
idea how much time it will take to complete the Imaging process.
Also don’t have any timeline view to check the information and other evidence in
proper view.
Also, it does not support the gallery view which not fit to picture on the windows
The tool has only 2 million file limit only
Not support AVI and PSD file part, so that we can able to see the images files and
videos in this format.
Because the PSD file is photoshoot file extension, as if someone modified the file or
editing is done in images, then we don’t get the real evidence from the tool, we
should use some other tools.
So, for getting other evidence that we can’t able to access from the FTK tool we can use
tools, like EnCase, Autospy, OSForensic, the SluethKit, etc.
Some are paid versions tool, but we get all details of evidence that we can recover from FTK
tool.
important to transfer data from one system to another.
Pros:
Very simple interface to use it.
Not so much critical options are available to access the tool.
The main benefit of this tool is we can create Image file for investigation
like .dd, .raw, .eo and .adi file formats.
It also capable of generating the Case Log files
Good bookmarking and salient reporting features are available as compare to other
tools
Also it comes free of cost.
Cons:
It does not support the scripting features, why we need it, because we can update
any file data for view in more details, and for decrypt any file which is protected or
some files formats we can change to view in plain text which is admissible in court as
an evidence.
Also it does not support Multi –tasking work, because to get the evidence we have to
check it File structure tree one by one which is time consuming.
Also, we don’t able to see the progress bar or any line bar, while we create the
Image file for transferring from victim system to secure Hard drive it can able to get
idea how much time it will take to complete the Imaging process.
Also don’t have any timeline view to check the information and other evidence in
proper view.
Also, it does not support the gallery view which not fit to picture on the windows
The tool has only 2 million file limit only
Not support AVI and PSD file part, so that we can able to see the images files and
videos in this format.
Because the PSD file is photoshoot file extension, as if someone modified the file or
editing is done in images, then we don’t get the real evidence from the tool, we
should use some other tools.
So, for getting other evidence that we can’t able to access from the FTK tool we can use
tools, like EnCase, Autospy, OSForensic, the SluethKit, etc.
Some are paid versions tool, but we get all details of evidence that we can recover from FTK
tool.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
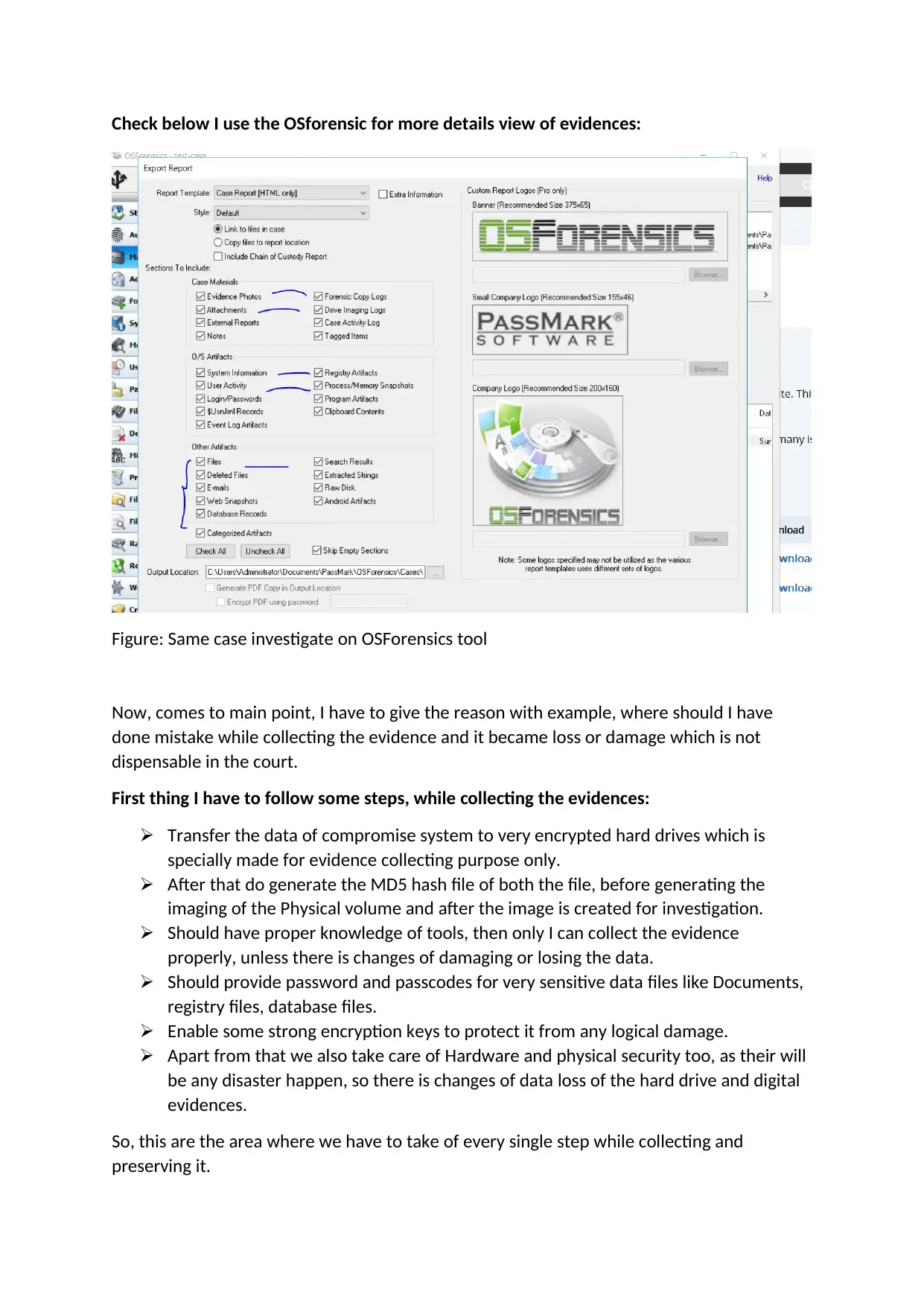
Check below I use the OSforensic for more details view of evidences:
Figure: Same case investigate on OSForensics tool
Now, comes to main point, I have to give the reason with example, where should I have
done mistake while collecting the evidence and it became loss or damage which is not
dispensable in the court.
First thing I have to follow some steps, while collecting the evidences:
Transfer the data of compromise system to very encrypted hard drives which is
specially made for evidence collecting purpose only.
After that do generate the MD5 hash file of both the file, before generating the
imaging of the Physical volume and after the image is created for investigation.
Should have proper knowledge of tools, then only I can collect the evidence
properly, unless there is changes of damaging or losing the data.
Should provide password and passcodes for very sensitive data files like Documents,
registry files, database files.
Enable some strong encryption keys to protect it from any logical damage.
Apart from that we also take care of Hardware and physical security too, as their will
be any disaster happen, so there is changes of data loss of the hard drive and digital
evidences.
So, this are the area where we have to take of every single step while collecting and
preserving it.
Figure: Same case investigate on OSForensics tool
Now, comes to main point, I have to give the reason with example, where should I have
done mistake while collecting the evidence and it became loss or damage which is not
dispensable in the court.
First thing I have to follow some steps, while collecting the evidences:
Transfer the data of compromise system to very encrypted hard drives which is
specially made for evidence collecting purpose only.
After that do generate the MD5 hash file of both the file, before generating the
imaging of the Physical volume and after the image is created for investigation.
Should have proper knowledge of tools, then only I can collect the evidence
properly, unless there is changes of damaging or losing the data.
Should provide password and passcodes for very sensitive data files like Documents,
registry files, database files.
Enable some strong encryption keys to protect it from any logical damage.
Apart from that we also take care of Hardware and physical security too, as their will
be any disaster happen, so there is changes of data loss of the hard drive and digital
evidences.
So, this are the area where we have to take of every single step while collecting and
preserving it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References:
https://www.cfreds.nist.gov/data_leakage_case/data-leakage-case.html.
https://drivesaversdatarecovery.com/blog/digital-forensic-process-preservation-
collections/
https://pressbooks.bccampus.ca/criminalinvestigation/chapter/chapter-10-forensic-
sciences/
http://ijcsit.com/docs/Volume%206/vol6issue05/ijcsit20150605150.pdf
http://www.forensicsciencesimplified.org/digital/how.html
https://www.ncjrs.gov/pdffiles1/nij/211314.pdf
http://acid-burninfo.blogspot.com/2011/04/sadvantages-and-disadvantages-of-
ftk.html
https://www.cyberstudents.org/blog-post/popular-forensic-software/
https://resources.infosecinstitute.com/category/computerforensics/introduction/
commercial-computer-forensics-tools/tool-comparison/
https://www.cfreds.nist.gov/data_leakage_case/data-leakage-case.html.
https://drivesaversdatarecovery.com/blog/digital-forensic-process-preservation-
collections/
https://pressbooks.bccampus.ca/criminalinvestigation/chapter/chapter-10-forensic-
sciences/
http://ijcsit.com/docs/Volume%206/vol6issue05/ijcsit20150605150.pdf
http://www.forensicsciencesimplified.org/digital/how.html
https://www.ncjrs.gov/pdffiles1/nij/211314.pdf
http://acid-burninfo.blogspot.com/2011/04/sadvantages-and-disadvantages-of-
ftk.html
https://www.cyberstudents.org/blog-post/popular-forensic-software/
https://resources.infosecinstitute.com/category/computerforensics/introduction/
commercial-computer-forensics-tools/tool-comparison/
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




