Minimize Unauthorized Data Leakage: Research Proposal, MITS
VerifiedAdded on 2022/08/24
|8
|3577
|16
Project
AI Summary
This research proposal, submitted to the Victorian Institute of Technology, explores the critical issue of unauthorized data leakage in cloud computing environments. The proposal, titled "Minimize Unauthorized Data Leakage," outlines a comprehensive research plan to identify and mitigate the vulnerabilities that lead to data breaches. It emphasizes the importance of network security, data privacy, and the impact of data leakage on the reliability and integrity of cloud-based data. The research will employ a systematic literature review, utilizing secondary data from peer-reviewed journals, analyzed through a qualitative approach. The proposal delves into various aspects, including the rationale for the research, the research questions, methodological approaches (specifically realism philosophy and an inductive research approach), and the data analysis techniques to be used. The study aims to provide insights into the causes of data leakage, propose strategies to minimize risks, and ultimately enhance the security of cloud computing services. The proposal includes an outline of the research, background information, the purpose of the research, its rationale, research questions, and the methodological approach, including data analysis and sampling techniques. A timeline for the research activities is also provided.

MITS Advanced Research Techniques
Research Proposal
Candidate:
Student Name
Higher Education Department
Victorian Institute of Technology
Proposed Title:
Minimize unauthorized data leakage
Abstract
Data leakage is the main limitation related with the deployment of cloud computing services which is
progressively used in our society as well as in corporate organizations. The reliability, validity and
integrity of the data can be compromised due to data leakage issues in the cloud computing
environment. This proposal is very much noteworthy for the readers of this proposal to recognize the
security loopholes of a network. The ways to minimize the data leakages issues shall be evacuated in
this proposal from ta network security perspective. The proposal shall be having numerous sections and
each of the section will be very much significant to enhance the validity of the discussions of the paper.
This proposal shall be considering secondary data analysis technique where data will be collected from
dependable secondary data sources like the peer reviewed journals. The collected data shall not
require any sort of numeric analysis hence the collected secondary data shall be analyzed with the help
of qualitative technique. Systematic literature review shall be considered as the research design of this
proposal and the sampling technique which will be considered in this proposal is random sampling
technique. The research philosophy which shall be considered in this proposal is realism philosophy.
The concluding section of this proposal shall be presenting a time frame which will be stating the time
required for each of the activities involved in the research.
Outline of the Proposed Research
Corruption of database is one of the prime challenges which are faced due to the data leakage issues in
the cloud servers. In order to address these challenges few precautionary steps are required to be taken
so that the chances of data leakage gets reduced. The rationale and the purpose of this research shall
be discussed in this section of the proposal. Data leakage is defined as the type of unauthorized data
tramission from cloud servers, data can be transferred from the cloud services both electronically as
well as physically. Data leakage occurs in a cloud computing environment due to numerous issues such
as weaker passwords of the cloud computing accounts, theft of the credential of the cloud computing
accounts, exploitation of the networking vulnerabilities by the social engineers, diverse categories of
malicious attacks, downtime issues, data privacy issues and vendor lock in. There are diverse
Research Proposal
Candidate:
Student Name
Higher Education Department
Victorian Institute of Technology
Proposed Title:
Minimize unauthorized data leakage
Abstract
Data leakage is the main limitation related with the deployment of cloud computing services which is
progressively used in our society as well as in corporate organizations. The reliability, validity and
integrity of the data can be compromised due to data leakage issues in the cloud computing
environment. This proposal is very much noteworthy for the readers of this proposal to recognize the
security loopholes of a network. The ways to minimize the data leakages issues shall be evacuated in
this proposal from ta network security perspective. The proposal shall be having numerous sections and
each of the section will be very much significant to enhance the validity of the discussions of the paper.
This proposal shall be considering secondary data analysis technique where data will be collected from
dependable secondary data sources like the peer reviewed journals. The collected data shall not
require any sort of numeric analysis hence the collected secondary data shall be analyzed with the help
of qualitative technique. Systematic literature review shall be considered as the research design of this
proposal and the sampling technique which will be considered in this proposal is random sampling
technique. The research philosophy which shall be considered in this proposal is realism philosophy.
The concluding section of this proposal shall be presenting a time frame which will be stating the time
required for each of the activities involved in the research.
Outline of the Proposed Research
Corruption of database is one of the prime challenges which are faced due to the data leakage issues in
the cloud servers. In order to address these challenges few precautionary steps are required to be taken
so that the chances of data leakage gets reduced. The rationale and the purpose of this research shall
be discussed in this section of the proposal. Data leakage is defined as the type of unauthorized data
tramission from cloud servers, data can be transferred from the cloud services both electronically as
well as physically. Data leakage occurs in a cloud computing environment due to numerous issues such
as weaker passwords of the cloud computing accounts, theft of the credential of the cloud computing
accounts, exploitation of the networking vulnerabilities by the social engineers, diverse categories of
malicious attacks, downtime issues, data privacy issues and vendor lock in. There are diverse
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

categories of network security which can have a direct impact on the data which are stored in the cloud
computing servers such as the Distributed Denial of Service (DDoS), firewall, email gateways,
Intrusion Detection System (IDS), network access control, (NAC) and Virtual Private Networks
(VPN).The protection to the access to the files is known as network security, it is very much essential to
maintain the security and integrity of the data which are stored, managed and retrieved in the cloud
servers. Numerous workstations can be created in the network which can ensure the security of a
network from the data security. Thus, this proposal will be very much important to understand how the
privacy issues of the cloud computing will be minimized so that the security of the data which are
stored in the cloud servers is maintained.
Background
Cloud leak is defined as the type of leakage where some of the essential or sensitive data
which are stowed in the cloud servers are exposed to the internet [9]. Network security is
defined as the set of policies which are set by the networking engineers which protects the
usability as well as the integrity of the network and the data which comes in and out of a
private network. The practice of using a network of remote servers which are hosted in the
internet to manage diverse types of data is termed as cloud computing. Billions of people all
around the globe is using cloud computing services to protect the integrity of the data. Any
sort of data security issues like data leakage can have a huge impact on the data which are
stored in the cloud servers [10]. There are numerous ways which can address the data
leakage issues in a cloud environment such as the good quality encryption, training the users
of the cloud environment. Setting a decent password policy is one of the prime ways to restrict
the social engineers to identify the network security vulnerabilities. Data backup can be very
much significant to deal with issues like data alteration. This proposal will be different from
the other researches as it will be conducted based on network security perspective.
There are numerous ways which can ensure minimization of data leakage in any cloud
environment like the identification of the critical data of the business, the use of the data loss
prevention software is also very much significant to protect the data from the data leakage
threats [12]. Monitoring the traffic of all networks is also be very much significant ways to
minimize data leakage threats in a cloud computing environment. It can also be said that the
employees who works in the cloud computing environment must be following Bring Your Own
Device policy which can ensure that there are no data leakage threats coming from the cloud
computing environment [11]. Checking the sensitivity of the data is very much essential for
the protection of the data from the data leakage threats as well. Data leak prevention policy
and Information Leak prevention can be very much significant to minimize the data leakage
threats as well.
Purpose
The objective of the research can be understood in the first place from this unit of the proposal. The
engagement of the sources is one of the prime objectives of any research proposal. The expected final
result of a result can also be identified with the help of this section of the proposal. The primary
purposes of this proposal are to identify the reasons behind the unauthorized data leakage in cloud
computing and minimize the chances of data leakage so that cloud computing. The goal of this research
is to conduct secondary data from peer reviewed journal to identify the exact way by which data
leakage occurs in any cloud commuting environment. Analysis and justifications provided by the
computing servers such as the Distributed Denial of Service (DDoS), firewall, email gateways,
Intrusion Detection System (IDS), network access control, (NAC) and Virtual Private Networks
(VPN).The protection to the access to the files is known as network security, it is very much essential to
maintain the security and integrity of the data which are stored, managed and retrieved in the cloud
servers. Numerous workstations can be created in the network which can ensure the security of a
network from the data security. Thus, this proposal will be very much important to understand how the
privacy issues of the cloud computing will be minimized so that the security of the data which are
stored in the cloud servers is maintained.
Background
Cloud leak is defined as the type of leakage where some of the essential or sensitive data
which are stowed in the cloud servers are exposed to the internet [9]. Network security is
defined as the set of policies which are set by the networking engineers which protects the
usability as well as the integrity of the network and the data which comes in and out of a
private network. The practice of using a network of remote servers which are hosted in the
internet to manage diverse types of data is termed as cloud computing. Billions of people all
around the globe is using cloud computing services to protect the integrity of the data. Any
sort of data security issues like data leakage can have a huge impact on the data which are
stored in the cloud servers [10]. There are numerous ways which can address the data
leakage issues in a cloud environment such as the good quality encryption, training the users
of the cloud environment. Setting a decent password policy is one of the prime ways to restrict
the social engineers to identify the network security vulnerabilities. Data backup can be very
much significant to deal with issues like data alteration. This proposal will be different from
the other researches as it will be conducted based on network security perspective.
There are numerous ways which can ensure minimization of data leakage in any cloud
environment like the identification of the critical data of the business, the use of the data loss
prevention software is also very much significant to protect the data from the data leakage
threats [12]. Monitoring the traffic of all networks is also be very much significant ways to
minimize data leakage threats in a cloud computing environment. It can also be said that the
employees who works in the cloud computing environment must be following Bring Your Own
Device policy which can ensure that there are no data leakage threats coming from the cloud
computing environment [11]. Checking the sensitivity of the data is very much essential for
the protection of the data from the data leakage threats as well. Data leak prevention policy
and Information Leak prevention can be very much significant to minimize the data leakage
threats as well.
Purpose
The objective of the research can be understood in the first place from this unit of the proposal. The
engagement of the sources is one of the prime objectives of any research proposal. The expected final
result of a result can also be identified with the help of this section of the proposal. The primary
purposes of this proposal are to identify the reasons behind the unauthorized data leakage in cloud
computing and minimize the chances of data leakage so that cloud computing. The goal of this research
is to conduct secondary data from peer reviewed journal to identify the exact way by which data
leakage occurs in any cloud commuting environment. Analysis and justifications provided by the

scholars of the peer reviewed journals shall be considered to identify the ways by which data leakage
can be minimized. Thus, thus research can be very much beneficial for the readers of this proposal as it
can make them understand the procedures required to minimize the chances of data leakage while
using cloud computing services from the network security perspective.
Rationale
The reason behind the conduction of a research can be understood using the research rationale. The
hypothesis of a research is conducted using research rationale as well. Research rationale are very
much common in descriptive research, experimental research as well as library research.
There are numerous reasons behind the data leakage issues which are faced in cloud computing
environment such as the security loop holes of the network. Apart from that there are numerous factors
which cause data leakage such as the carelessness of the employees, setting the weak passwords,
accidental emailing of sensitive information, human error and system glitches [8]. Thus, it can be said
that each of these factors has to be addressed by the strategic planners of the cloud computing
environment in order to deal with data leakage threats [7]. There are previous researches has only
focused on the ways by which data leakage occurs in the cloud computing servers. On the contrary this
research shall not only identify the ways by which data leakage occurs but also recommend the ways
which can this issue can be minimized. The loopholes of the cloud computing services shall be
identified in this research which was not discussed in any of the previous researches. This research
shall also focus on the improvements which is required in the cloud computing servers which can
minimize the network vulnerabilities.
This research shall be very much beneficial for both the strategic planners of the cloud computing
services as well as for the users of this service. The strategic planners of the cloud computing services
can understand the ways by which data leakage occurs from this research. This research paper shall
also help the cloud computing users to identify the ways which can minimize the chances of data
leakage whenever they store their essential data in the cloud servers.
Research Topic and central research question
Research questions is defined as the type of questions which can help to understand the content of a
research [6]. The sub sections of a research paper can easily be understood using the research
questions. The specific concerns or the actual reason behind the conduction of a project can be
understood with the help of the research questions [13]. The selection of the research questions
depends upon the nature of the project and perception of the analyst of the research. Research
questions must be very much specific so that the exact reason behind the conduction of the proposal is
identified by the researchers of the proposal.
Based on the background proposal it can be understood that data leakage can have a huge impact on
the data which are stored in the cloud servers. Thus, it can be said that there are few areas related with
data leakage of cloud computing which has to be focused, discussed and analyzed so that the chances
of data leakage gets reduced to a significant extent. The research questions of this proposal are as
followings:
What are network security issues related with the deployment of the cloud computing services?
can be minimized. Thus, thus research can be very much beneficial for the readers of this proposal as it
can make them understand the procedures required to minimize the chances of data leakage while
using cloud computing services from the network security perspective.
Rationale
The reason behind the conduction of a research can be understood using the research rationale. The
hypothesis of a research is conducted using research rationale as well. Research rationale are very
much common in descriptive research, experimental research as well as library research.
There are numerous reasons behind the data leakage issues which are faced in cloud computing
environment such as the security loop holes of the network. Apart from that there are numerous factors
which cause data leakage such as the carelessness of the employees, setting the weak passwords,
accidental emailing of sensitive information, human error and system glitches [8]. Thus, it can be said
that each of these factors has to be addressed by the strategic planners of the cloud computing
environment in order to deal with data leakage threats [7]. There are previous researches has only
focused on the ways by which data leakage occurs in the cloud computing servers. On the contrary this
research shall not only identify the ways by which data leakage occurs but also recommend the ways
which can this issue can be minimized. The loopholes of the cloud computing services shall be
identified in this research which was not discussed in any of the previous researches. This research
shall also focus on the improvements which is required in the cloud computing servers which can
minimize the network vulnerabilities.
This research shall be very much beneficial for both the strategic planners of the cloud computing
services as well as for the users of this service. The strategic planners of the cloud computing services
can understand the ways by which data leakage occurs from this research. This research paper shall
also help the cloud computing users to identify the ways which can minimize the chances of data
leakage whenever they store their essential data in the cloud servers.
Research Topic and central research question
Research questions is defined as the type of questions which can help to understand the content of a
research [6]. The sub sections of a research paper can easily be understood using the research
questions. The specific concerns or the actual reason behind the conduction of a project can be
understood with the help of the research questions [13]. The selection of the research questions
depends upon the nature of the project and perception of the analyst of the research. Research
questions must be very much specific so that the exact reason behind the conduction of the proposal is
identified by the researchers of the proposal.
Based on the background proposal it can be understood that data leakage can have a huge impact on
the data which are stored in the cloud servers. Thus, it can be said that there are few areas related with
data leakage of cloud computing which has to be focused, discussed and analyzed so that the chances
of data leakage gets reduced to a significant extent. The research questions of this proposal are as
followings:
What are network security issues related with the deployment of the cloud computing services?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

How the security issues are having a negative effect on the privacy of the data which are
managed and stored in the cloud servers?
To what extent the privacy issues of the cloud computing can be resolved?
Can the issues of cloud computing minimized?
What are the exact ways to minimize the data leakage issues in cloud computing environment?
Methodological Approach
It is research approach which are very much significant to explore the topic of the proposal. There are
numerous methodologies which are considered in proposals like the research philosophy, research
approach, data analysis, and sampling technique [5]. The reliability and validity of this proposal shall
be maintained with the help of the methods which will be considered while working on this proposal
[14]. The detailed description followed by the justification willbe provided in this section of the
proposal as well.
Philosophy: There are numerous philosophies which are considered in research proposals such as
epistemology, positivism, realism, interpretivism, and axiology [4]. The selection of the philosophy is
depended on the topic of the research and the data collection process which are considered in the
research [15]. Realism philosophy shall be considered in this proposal to gain in-depth knowledge
about the selected topic.
Justification: Meta physical certainty of the proposal shall be maintained using this philosophy. The
view points of the researchers whose data shall be considered in the proposal can be understood in a
transparent modus using this philosophy.
Approach: There are many research approaches which are followed in research proposals such as the
exploratory approach, methodological study, historical study, abductive approach, inductive approach,
and explanatory research approach [16]. Out of these different categories of research approaches
Inductive research approach shall be considered in this proposal.
Justification: The secondary data from the peer reviewed journals will be evaluated with the help of
generalized explanations which are supported by the inductive approach [5]. The use of theories and
methodologies in the data collection method shall also be supported using this research approach.
Data analysis: Data analysis is one of the prime way to improve the validity and the reliability of the
research paper [18]. There are two different categories of data analysis technique which are
considered in research papers like the quantitative and qualitative data analysis. Analysis which
require numerical calculations is done with the help of statistical tools like SPSS and the data which do
not have any sort of numerical analysis can be conducted using qualitative data analysis technique [4].
Qualitative data analysis technique shall be considered to analyze the data which will be collected
from secondary sources [17]. Critical analysis of the secondary data will be very much significant to
analyze the secondary data.
Justification: In-depth analysis of the collected secondary data can be evaluated using this technique
[3]. Identification of the potential data points is the other major reason behind selecting this category
of data analysis.
Sampling technique: Random sampling technique shall be considered to determine the sample of this
managed and stored in the cloud servers?
To what extent the privacy issues of the cloud computing can be resolved?
Can the issues of cloud computing minimized?
What are the exact ways to minimize the data leakage issues in cloud computing environment?
Methodological Approach
It is research approach which are very much significant to explore the topic of the proposal. There are
numerous methodologies which are considered in proposals like the research philosophy, research
approach, data analysis, and sampling technique [5]. The reliability and validity of this proposal shall
be maintained with the help of the methods which will be considered while working on this proposal
[14]. The detailed description followed by the justification willbe provided in this section of the
proposal as well.
Philosophy: There are numerous philosophies which are considered in research proposals such as
epistemology, positivism, realism, interpretivism, and axiology [4]. The selection of the philosophy is
depended on the topic of the research and the data collection process which are considered in the
research [15]. Realism philosophy shall be considered in this proposal to gain in-depth knowledge
about the selected topic.
Justification: Meta physical certainty of the proposal shall be maintained using this philosophy. The
view points of the researchers whose data shall be considered in the proposal can be understood in a
transparent modus using this philosophy.
Approach: There are many research approaches which are followed in research proposals such as the
exploratory approach, methodological study, historical study, abductive approach, inductive approach,
and explanatory research approach [16]. Out of these different categories of research approaches
Inductive research approach shall be considered in this proposal.
Justification: The secondary data from the peer reviewed journals will be evaluated with the help of
generalized explanations which are supported by the inductive approach [5]. The use of theories and
methodologies in the data collection method shall also be supported using this research approach.
Data analysis: Data analysis is one of the prime way to improve the validity and the reliability of the
research paper [18]. There are two different categories of data analysis technique which are
considered in research papers like the quantitative and qualitative data analysis. Analysis which
require numerical calculations is done with the help of statistical tools like SPSS and the data which do
not have any sort of numerical analysis can be conducted using qualitative data analysis technique [4].
Qualitative data analysis technique shall be considered to analyze the data which will be collected
from secondary sources [17]. Critical analysis of the secondary data will be very much significant to
analyze the secondary data.
Justification: In-depth analysis of the collected secondary data can be evaluated using this technique
[3]. Identification of the potential data points is the other major reason behind selecting this category
of data analysis.
Sampling technique: Random sampling technique shall be considered to determine the sample of this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

research.
Justification: The easier enactment of this sampling method is very much easier and it is one of the
prime reasons behind selecting this sampling technique [19]. Accuracy of the data representation is
one of the other reason behind the selection of this sampling technique.
Research Design
It is the segment of a proposal which are very much beneficial for the readers of this proposal to
understand the design which was selected to collect the data for this proposal [2]. This research
proposal shall be considered secondary data collection, hence data analysis shall not be conducted
with the help of any sort of simulation software or statistical tool. The detailed description of the design
of this research are as followings:
Data collection: Secondary data collection shall be considered in this proposal, data will be collected
from peer reviewed journals where reputed scholars have stated their opinion about the selected topic
of this proposal [1]. Recent journals shall be chosen in this proposal to collect secondary data.
Justification: The prime reason behind selecting this data collection method is that is much
economical as compared with the other data collection techniques. Minimum effort from the analysts is
required to collect and interpret data from secondary resources. Identification of the research gaps is
much easier in the secondary data.
Design: Systematic literature review design shall be considered in this proposal as it can help to review
the secondary data which will be composed from the secondary sources [20].
Justification: The overview of the available evidence can be understood in an accurate modus using
this research design. This research design emphasizes mainly on the research questions and also helps
the analyst of the research to interpret the secondary data. Critical analysis can be very conducted in
an accurate modus using this research design as well.
Contribution
This research will be very much significant for the readers as they can understand the exact way to
minimize the data leakage in a clod computing environment. The gaps in knowledge can also be
understood from this research proposal. This research can be very much significant for the readers to
have an in-depth knowledge about the ways by which data leakage issues can be minimized in a cloud
computing environment. This research shall also be very much significant as it will identify the
potential and the capabilities of the social engineers who are trying out different techniques to identify
the security loopholes in a private network. This research will also help the analyst to maintain the
schedule of each phase of the proposal such as the selection of the topic to the analysis of the data
which will be collected from secondary sources.
Proposed Time Schedule
Justification: The easier enactment of this sampling method is very much easier and it is one of the
prime reasons behind selecting this sampling technique [19]. Accuracy of the data representation is
one of the other reason behind the selection of this sampling technique.
Research Design
It is the segment of a proposal which are very much beneficial for the readers of this proposal to
understand the design which was selected to collect the data for this proposal [2]. This research
proposal shall be considered secondary data collection, hence data analysis shall not be conducted
with the help of any sort of simulation software or statistical tool. The detailed description of the design
of this research are as followings:
Data collection: Secondary data collection shall be considered in this proposal, data will be collected
from peer reviewed journals where reputed scholars have stated their opinion about the selected topic
of this proposal [1]. Recent journals shall be chosen in this proposal to collect secondary data.
Justification: The prime reason behind selecting this data collection method is that is much
economical as compared with the other data collection techniques. Minimum effort from the analysts is
required to collect and interpret data from secondary resources. Identification of the research gaps is
much easier in the secondary data.
Design: Systematic literature review design shall be considered in this proposal as it can help to review
the secondary data which will be composed from the secondary sources [20].
Justification: The overview of the available evidence can be understood in an accurate modus using
this research design. This research design emphasizes mainly on the research questions and also helps
the analyst of the research to interpret the secondary data. Critical analysis can be very conducted in
an accurate modus using this research design as well.
Contribution
This research will be very much significant for the readers as they can understand the exact way to
minimize the data leakage in a clod computing environment. The gaps in knowledge can also be
understood from this research proposal. This research can be very much significant for the readers to
have an in-depth knowledge about the ways by which data leakage issues can be minimized in a cloud
computing environment. This research shall also be very much significant as it will identify the
potential and the capabilities of the social engineers who are trying out different techniques to identify
the security loopholes in a private network. This research will also help the analyst to maintain the
schedule of each phase of the proposal such as the selection of the topic to the analysis of the data
which will be collected from secondary sources.
Proposed Time Schedule
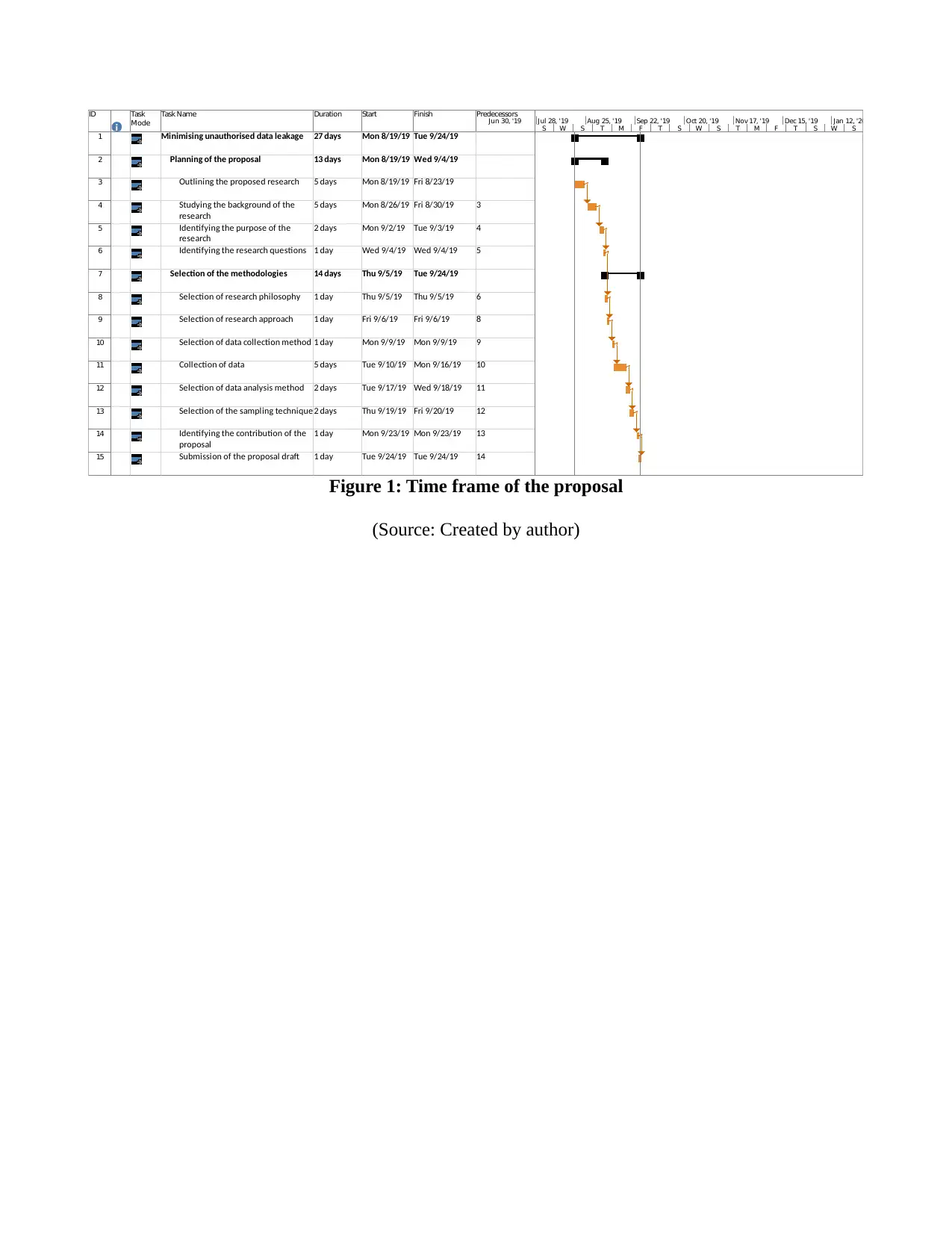
ID Task
Mode
Task Name Duration Start Finish Predecessors
1 Minimising unauthorised data leakage 27 days Mon 8/19/19 Tue 9/24/19
2 Planning of the proposal 13 days Mon 8/19/19 Wed 9/4/19
3 Outlining the proposed research 5 days Mon 8/19/19 Fri 8/23/19
4 Studying the background of the
research
5 days Mon 8/26/19 Fri 8/30/19 3
5 Identifying the purpose of the
research
2 days Mon 9/2/19 Tue 9/3/19 4
6 Identifying the research questions 1 day Wed 9/4/19 Wed 9/4/19 5
7 Selection of the methodologies 14 days Thu 9/5/19 Tue 9/24/19
8 Selection of research philosophy 1 day Thu 9/5/19 Thu 9/5/19 6
9 Selection of research approach 1 day Fri 9/6/19 Fri 9/6/19 8
10 Selection of data collection method 1 day Mon 9/9/19 Mon 9/9/19 9
11 Collection of data 5 days Tue 9/10/19 Mon 9/16/19 10
12 Selection of data analysis method 2 days Tue 9/17/19 Wed 9/18/19 11
13 Selection of the sampling technique 2 days Thu 9/19/19 Fri 9/20/19 12
14 Identifying the contribution of the
proposal
1 day Mon 9/23/19 Mon 9/23/19 13
15 Submission of the proposal draft 1 day Tue 9/24/19 Tue 9/24/19 14
S W S T M F T S W S T M F T S W S
Jun 30, '19 Jul 28, '19 Aug 25, '19 Sep 22, '19 Oct 20, '19 Nov 17, '19 Dec 15, '19 Jan 12, '20
Figure 1: Time frame of the proposal
(Source: Created by author)
Mode
Task Name Duration Start Finish Predecessors
1 Minimising unauthorised data leakage 27 days Mon 8/19/19 Tue 9/24/19
2 Planning of the proposal 13 days Mon 8/19/19 Wed 9/4/19
3 Outlining the proposed research 5 days Mon 8/19/19 Fri 8/23/19
4 Studying the background of the
research
5 days Mon 8/26/19 Fri 8/30/19 3
5 Identifying the purpose of the
research
2 days Mon 9/2/19 Tue 9/3/19 4
6 Identifying the research questions 1 day Wed 9/4/19 Wed 9/4/19 5
7 Selection of the methodologies 14 days Thu 9/5/19 Tue 9/24/19
8 Selection of research philosophy 1 day Thu 9/5/19 Thu 9/5/19 6
9 Selection of research approach 1 day Fri 9/6/19 Fri 9/6/19 8
10 Selection of data collection method 1 day Mon 9/9/19 Mon 9/9/19 9
11 Collection of data 5 days Tue 9/10/19 Mon 9/16/19 10
12 Selection of data analysis method 2 days Tue 9/17/19 Wed 9/18/19 11
13 Selection of the sampling technique 2 days Thu 9/19/19 Fri 9/20/19 12
14 Identifying the contribution of the
proposal
1 day Mon 9/23/19 Mon 9/23/19 13
15 Submission of the proposal draft 1 day Tue 9/24/19 Tue 9/24/19 14
S W S T M F T S W S T M F T S W S
Jun 30, '19 Jul 28, '19 Aug 25, '19 Sep 22, '19 Oct 20, '19 Nov 17, '19 Dec 15, '19 Jan 12, '20
Figure 1: Time frame of the proposal
(Source: Created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Literature References
[1] S. Nagpure, A. Gandhi, A. Varshney and B. Varshney. Data Leakage Agent Detection in Cloud
Computing. Available at SSRN 3370757, 2019
[2] K. Kaur, I. Gupta, and A.K. Singh. A Comparative Evaluation of Data Leakage/Loss prevention
Systems (DLPS). In Proc. 4th Int. Conf. Computer Science & Information Technology (CS & IT-
CSCP), Dubai, UAE (pp. 87-95), 2017
[3] S.A. Hussain, M. Fatima, A. Saeed, I. Raza, and R. K. Shahzad. Multilevel classification of security
concerns in cloud computing. Applied Computing and Informatics, 13(1), pp.57-65, 2017
[4] Z. Yan, R.H. Deng, and V. Varadharajan. Cryptography and data security in cloud computing, 2017
[5] J. Calleja. Data leakage in SaaS (Bachelor's thesis, University of Malta), (2019).
[6] H. Khapekar, S. Gunde, S. Shingne, P. Shende and D. Moon. Data Leakage Detection Using Client-
Server Mechanism, 2017
[7] A. Ghorbel, M. Ghorbel, M. and Jmaiel. Privacy in cloud computing environments: a survey and
research challenges. The Journal of Supercomputing, 73(6), pp.2763-2800, 2017.
[8] D. Ulybyshev, B. Bhargava, and A. Oqab-Alsalem. Secure Data Exchange and Data Leakage
Detection in an Untrusted Cloud. In International Conference on Application of Computing and
Communication Technologies (pp. 99-113). Springer, Singapore, 2018
[9] I. Gupta and A. K. Singh. A probability based model for data leakage detection using bigraph. In
Proceedings of the 2017 the 7th International Conference on Communication and Network Security
(pp. 1-5), 2017.
[10] S. Alneyadi, E. Sithirasenan, and V. Muthukkumarasamy. A survey on data leakage prevention
systems. Journal of Network and Computer Applications, 62, pp.137-152, 2016
[11] A.K. Yadav, R.K. Bharti, and R.S. Raw. Security Solution to Prevent Data Leakage Over
Multitenant Cloud Infrastructure. International Journal of Pure and Applied Mathematics, 118(7),
pp.269-276, 2018
[12] S. Geetha, M. Nishanthini, G. Shanthi, K. Sivabharathi and M. Suganya. Data Leakage Detection
and Security Using Cloud Computing. International Journal of Engineering Research and
Applications, 6(3), 2016
[13] T. Ahmad, H. Aslam, and S. Shahzad. Security of Provider sides in Data Privacy and Data
Accessibility Issues in Cloud computing. University of Sindh Journal of Information and
Communication Technology, 2(1), pp.7-10, 2018
[14] S. Chhabra and A. K. Singh. Dynamic data leakage detection model based approach for
MapReduce computational security in cloud. In 2016 Fifth International Conference on Eco-friendly
Computing and Communication Systems (ICECCS) (pp. 13-19). IEEE, 2016
[1] S. Nagpure, A. Gandhi, A. Varshney and B. Varshney. Data Leakage Agent Detection in Cloud
Computing. Available at SSRN 3370757, 2019
[2] K. Kaur, I. Gupta, and A.K. Singh. A Comparative Evaluation of Data Leakage/Loss prevention
Systems (DLPS). In Proc. 4th Int. Conf. Computer Science & Information Technology (CS & IT-
CSCP), Dubai, UAE (pp. 87-95), 2017
[3] S.A. Hussain, M. Fatima, A. Saeed, I. Raza, and R. K. Shahzad. Multilevel classification of security
concerns in cloud computing. Applied Computing and Informatics, 13(1), pp.57-65, 2017
[4] Z. Yan, R.H. Deng, and V. Varadharajan. Cryptography and data security in cloud computing, 2017
[5] J. Calleja. Data leakage in SaaS (Bachelor's thesis, University of Malta), (2019).
[6] H. Khapekar, S. Gunde, S. Shingne, P. Shende and D. Moon. Data Leakage Detection Using Client-
Server Mechanism, 2017
[7] A. Ghorbel, M. Ghorbel, M. and Jmaiel. Privacy in cloud computing environments: a survey and
research challenges. The Journal of Supercomputing, 73(6), pp.2763-2800, 2017.
[8] D. Ulybyshev, B. Bhargava, and A. Oqab-Alsalem. Secure Data Exchange and Data Leakage
Detection in an Untrusted Cloud. In International Conference on Application of Computing and
Communication Technologies (pp. 99-113). Springer, Singapore, 2018
[9] I. Gupta and A. K. Singh. A probability based model for data leakage detection using bigraph. In
Proceedings of the 2017 the 7th International Conference on Communication and Network Security
(pp. 1-5), 2017.
[10] S. Alneyadi, E. Sithirasenan, and V. Muthukkumarasamy. A survey on data leakage prevention
systems. Journal of Network and Computer Applications, 62, pp.137-152, 2016
[11] A.K. Yadav, R.K. Bharti, and R.S. Raw. Security Solution to Prevent Data Leakage Over
Multitenant Cloud Infrastructure. International Journal of Pure and Applied Mathematics, 118(7),
pp.269-276, 2018
[12] S. Geetha, M. Nishanthini, G. Shanthi, K. Sivabharathi and M. Suganya. Data Leakage Detection
and Security Using Cloud Computing. International Journal of Engineering Research and
Applications, 6(3), 2016
[13] T. Ahmad, H. Aslam, and S. Shahzad. Security of Provider sides in Data Privacy and Data
Accessibility Issues in Cloud computing. University of Sindh Journal of Information and
Communication Technology, 2(1), pp.7-10, 2018
[14] S. Chhabra and A. K. Singh. Dynamic data leakage detection model based approach for
MapReduce computational security in cloud. In 2016 Fifth International Conference on Eco-friendly
Computing and Communication Systems (ICECCS) (pp. 13-19). IEEE, 2016
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[15] S. Srinivasan and K. Raja. An Advanced Dynamic Authentic Security Method for Cloud
Computing. In Cyber Security (pp. 143-152). Springer, Singapore, 2018
[16] H. Allam, N. Nassiri, A. Rajan, A. and J. Ahmad. A critical overview of latest challenges and
solutions of Mobile Cloud Computing. In 2017 Second international conference on fog and mobile
edge computing (FMEC) (pp. 225-229). IEEE, 2017
[17] G.M. George, and L.S. Jayashree. Safest Secure and Consistent Data Services in the Storage of
Cloud Computing. In International Conference on Artificial Intelligence, Smart Grid and Smart City
Applications (pp. 433-447). Springer, Cham, 2019
[18] Z. Yang, W. Wang, and Y. Huang. Ensuring reliable logging for data accountability in untrusted
cloud storage. In 2017 IEEE International Conference on Communications (ICC) (pp. 1-6). IEEE, 2017
[19] U. Gupta, M.S. Saluja, and M.T. Tiwari. Enhancement of Cloud Security and removal of anti-
patterns using multilevel encryption algorithms, 2018
[20] B.P. Van Leeuwen, V. Urias, W. Stout and H.W. Lin. Applying a Threat Model to Cloud
Computing (No. SAND2018-11061C). Sandia National Lab.(SNL-NM), Albuquerque, NM (United
States) (2018)
Computing. In Cyber Security (pp. 143-152). Springer, Singapore, 2018
[16] H. Allam, N. Nassiri, A. Rajan, A. and J. Ahmad. A critical overview of latest challenges and
solutions of Mobile Cloud Computing. In 2017 Second international conference on fog and mobile
edge computing (FMEC) (pp. 225-229). IEEE, 2017
[17] G.M. George, and L.S. Jayashree. Safest Secure and Consistent Data Services in the Storage of
Cloud Computing. In International Conference on Artificial Intelligence, Smart Grid and Smart City
Applications (pp. 433-447). Springer, Cham, 2019
[18] Z. Yang, W. Wang, and Y. Huang. Ensuring reliable logging for data accountability in untrusted
cloud storage. In 2017 IEEE International Conference on Communications (ICC) (pp. 1-6). IEEE, 2017
[19] U. Gupta, M.S. Saluja, and M.T. Tiwari. Enhancement of Cloud Security and removal of anti-
patterns using multilevel encryption algorithms, 2018
[20] B.P. Van Leeuwen, V. Urias, W. Stout and H.W. Lin. Applying a Threat Model to Cloud
Computing (No. SAND2018-11061C). Sandia National Lab.(SNL-NM), Albuquerque, NM (United
States) (2018)
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





