ITECH1102 Report: Data Link, Transport, Cloud Computing Analysis
VerifiedAdded on 2023/04/21
|12
|2301
|198
Report
AI Summary
This report provides a comprehensive analysis of three key topics in networking and security: the data link layer, the transport layer, and cloud computing. The data link layer section delves into its functions, including coding, decoding, framing, physical addressing, access control, error control, and flow control, emphasizing its role as an interface between the physical and network layers and its importance in node-to-node data delivery. The transport layer section examines its role in providing port addressing, multiplexing, and ensuring reliable and efficient data delivery, including protocols like UDP and TCP. Finally, the cloud computing section discusses the benefits of cloud computing, its various types (public, private, hybrid), and its impact on business operations and IT infrastructure, highlighting its role in cost reduction, scalability, and security. The report also includes relevant references to support the analysis.
IT write up
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 | P a g e
Table of Contents
Topic 1: Data Link Layer......................................................................................................................2
Topic 2: Transport Layer.......................................................................................................................4
Topic 3-Cloud computing and network.................................................................................................7
References...........................................................................................................................................10
Table of Contents
Topic 1: Data Link Layer......................................................................................................................2
Topic 2: Transport Layer.......................................................................................................................4
Topic 3-Cloud computing and network.................................................................................................7
References...........................................................................................................................................10

2 | P a g e
Topic 1: Data Link Layer
The data link layer is used for coding and decoding the bits of data. In this the data packets
are framed and addressed into layers. The sub layer of data link layer is MAC layer. The
MAC layer allows the data to be transmitted in a best way. The data link layer is used for
communicating with devices that are present on the same network. It can be said as an
interface between physical and network layer (Xu, Li, Li, Zhang & Muntean, 2015). It is the
second layer of OSI model and the main functions of this layer is to transfer the data to
network layer ad regulate the data flow. They also deal with the transmission error by
making sure that information is transferred by encoding the data (Armstrong, et. al, 2015).
Data link layer assures that every piece of information is secured and then it is transferred to
desired location.
(Source: https://www.studytonight.com/computer-networks/osi-model-datalink-layer)
It is a most reliable node to node delivery of data as in this packet is received from network
layer and it is transferred to physical layer. The data is transferred in encoded form so that
only authorised user can access the information. The network layer is not able to detect the
transmission error that is done by the data link layer (Xu, Li, Li, Zhang & Muntean, 2015).
This is done by breaking the message into small packets and then transferring the data into
Topic 1: Data Link Layer
The data link layer is used for coding and decoding the bits of data. In this the data packets
are framed and addressed into layers. The sub layer of data link layer is MAC layer. The
MAC layer allows the data to be transmitted in a best way. The data link layer is used for
communicating with devices that are present on the same network. It can be said as an
interface between physical and network layer (Xu, Li, Li, Zhang & Muntean, 2015). It is the
second layer of OSI model and the main functions of this layer is to transfer the data to
network layer ad regulate the data flow. They also deal with the transmission error by
making sure that information is transferred by encoding the data (Armstrong, et. al, 2015).
Data link layer assures that every piece of information is secured and then it is transferred to
desired location.
(Source: https://www.studytonight.com/computer-networks/osi-model-datalink-layer)
It is a most reliable node to node delivery of data as in this packet is received from network
layer and it is transferred to physical layer. The data is transferred in encoded form so that
only authorised user can access the information. The network layer is not able to detect the
transmission error that is done by the data link layer (Xu, Li, Li, Zhang & Muntean, 2015).
This is done by breaking the message into small packets and then transferring the data into
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3 | P a g e
frames and that too sequentially (Lopacinski, Nolte, Buechner, Brzozowski & Kraemer,
2015). The receiver’s future confirms the data packet received by sending the
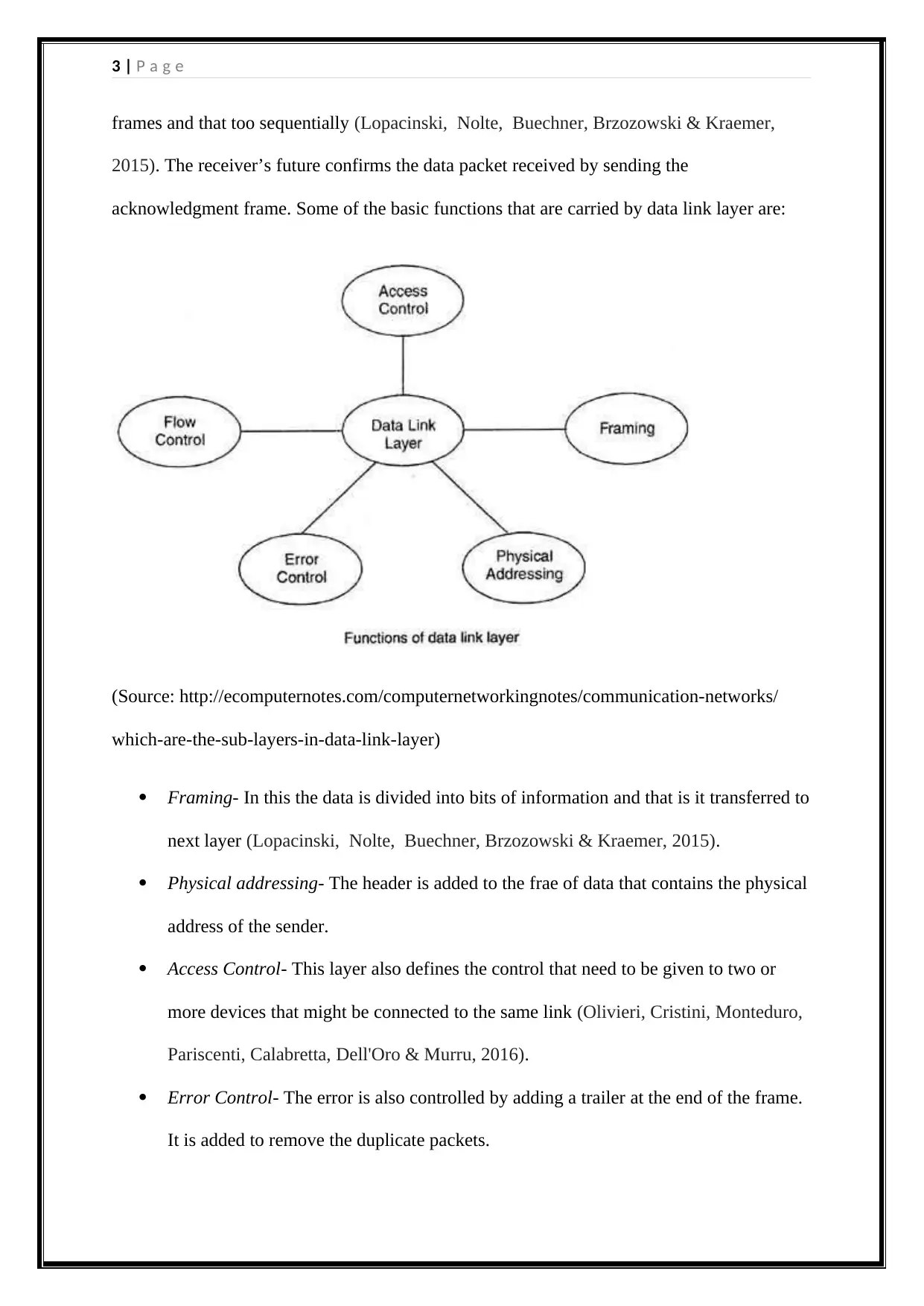
acknowledgment frame. Some of the basic functions that are carried by data link layer are:
(Source: http://ecomputernotes.com/computernetworkingnotes/communication-networks/
which-are-the-sub-layers-in-data-link-layer)
Framing- In this the data is divided into bits of information and that is it transferred to
next layer (Lopacinski, Nolte, Buechner, Brzozowski & Kraemer, 2015).
Physical addressing- The header is added to the frae of data that contains the physical
address of the sender.
Access Control- This layer also defines the control that need to be given to two or
more devices that might be connected to the same link (Olivieri, Cristini, Monteduro,
Pariscenti, Calabretta, Dell'Oro & Murru, 2016).
Error Control- The error is also controlled by adding a trailer at the end of the frame.
It is added to remove the duplicate packets.
frames and that too sequentially (Lopacinski, Nolte, Buechner, Brzozowski & Kraemer,
2015). The receiver’s future confirms the data packet received by sending the
acknowledgment frame. Some of the basic functions that are carried by data link layer are:
(Source: http://ecomputernotes.com/computernetworkingnotes/communication-networks/
which-are-the-sub-layers-in-data-link-layer)
Framing- In this the data is divided into bits of information and that is it transferred to
next layer (Lopacinski, Nolte, Buechner, Brzozowski & Kraemer, 2015).
Physical addressing- The header is added to the frae of data that contains the physical
address of the sender.
Access Control- This layer also defines the control that need to be given to two or
more devices that might be connected to the same link (Olivieri, Cristini, Monteduro,
Pariscenti, Calabretta, Dell'Oro & Murru, 2016).
Error Control- The error is also controlled by adding a trailer at the end of the frame.
It is added to remove the duplicate packets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4 | P a g e
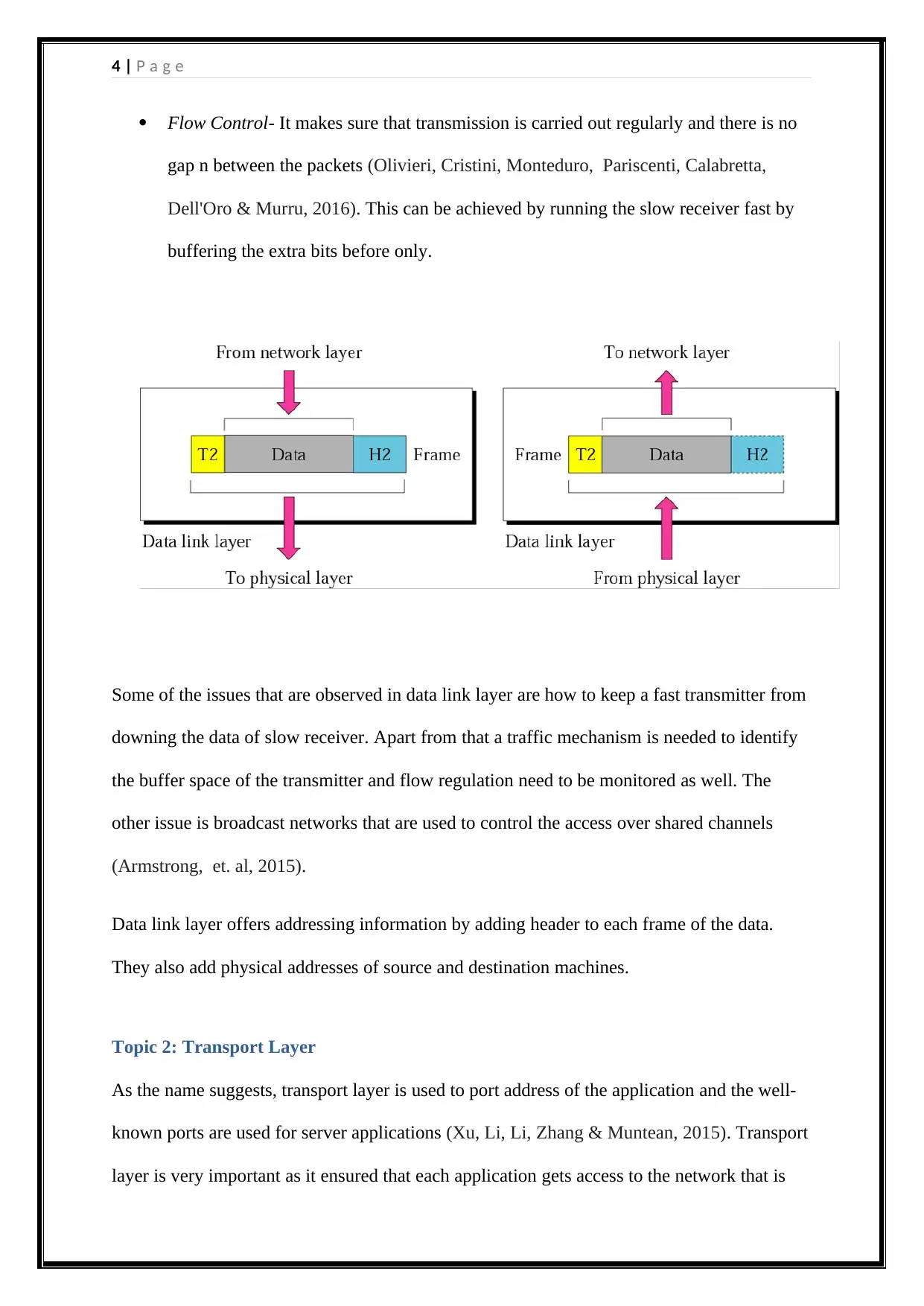
Flow Control- It makes sure that transmission is carried out regularly and there is no
gap n between the packets (Olivieri, Cristini, Monteduro, Pariscenti, Calabretta,
Dell'Oro & Murru, 2016). This can be achieved by running the slow receiver fast by
buffering the extra bits before only.
Some of the issues that are observed in data link layer are how to keep a fast transmitter from
downing the data of slow receiver. Apart from that a traffic mechanism is needed to identify
the buffer space of the transmitter and flow regulation need to be monitored as well. The
other issue is broadcast networks that are used to control the access over shared channels
(Armstrong, et. al, 2015).
Data link layer offers addressing information by adding header to each frame of the data.
They also add physical addresses of source and destination machines.
Topic 2: Transport Layer
As the name suggests, transport layer is used to port address of the application and the well-
known ports are used for server applications (Xu, Li, Li, Zhang & Muntean, 2015). Transport
layer is very important as it ensured that each application gets access to the network that is
Flow Control- It makes sure that transmission is carried out regularly and there is no
gap n between the packets (Olivieri, Cristini, Monteduro, Pariscenti, Calabretta,
Dell'Oro & Murru, 2016). This can be achieved by running the slow receiver fast by
buffering the extra bits before only.
Some of the issues that are observed in data link layer are how to keep a fast transmitter from
downing the data of slow receiver. Apart from that a traffic mechanism is needed to identify
the buffer space of the transmitter and flow regulation need to be monitored as well. The
other issue is broadcast networks that are used to control the access over shared channels
(Armstrong, et. al, 2015).
Data link layer offers addressing information by adding header to each frame of the data.
They also add physical addresses of source and destination machines.
Topic 2: Transport Layer
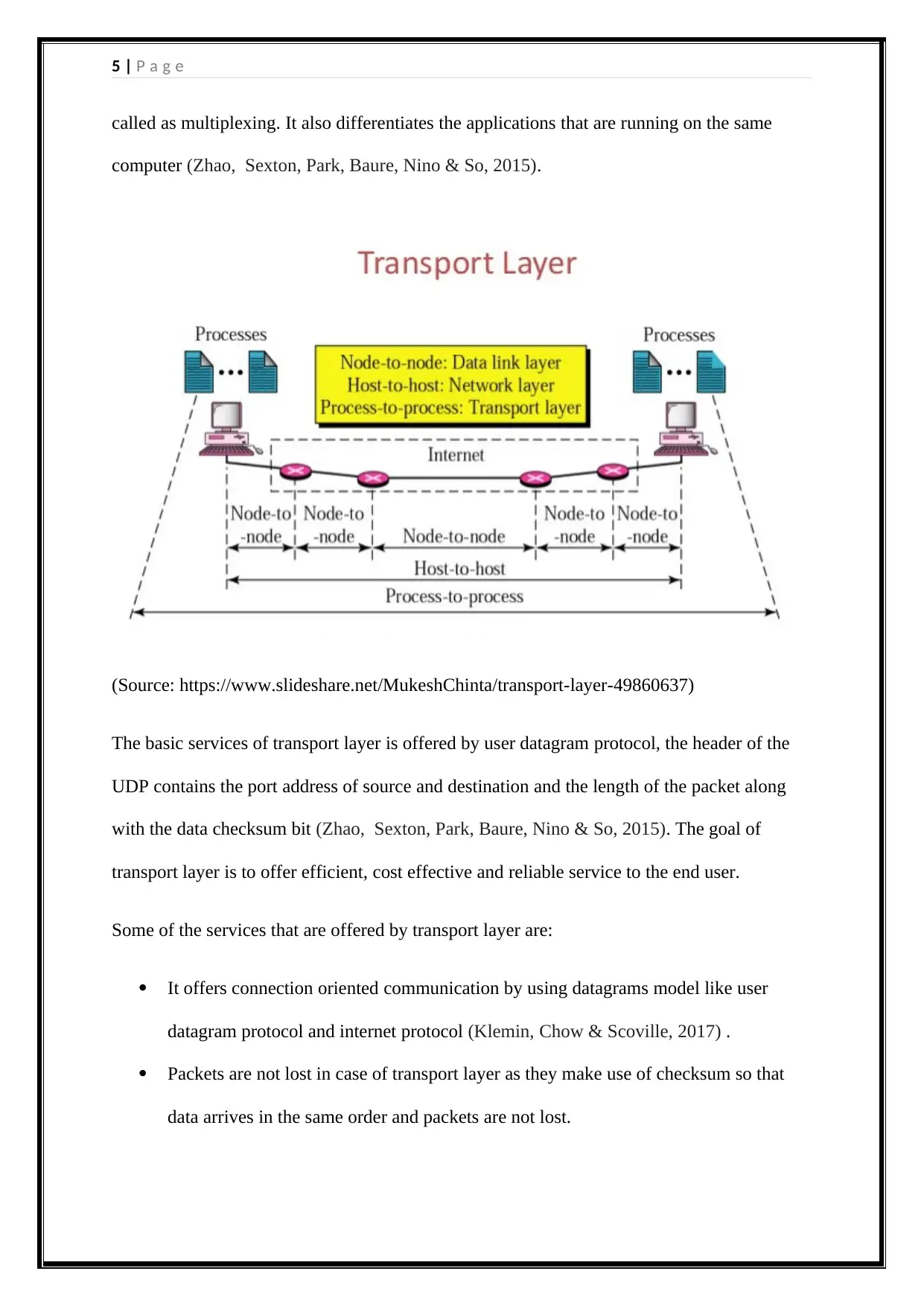
As the name suggests, transport layer is used to port address of the application and the well-
known ports are used for server applications (Xu, Li, Li, Zhang & Muntean, 2015). Transport
layer is very important as it ensured that each application gets access to the network that is
5 | P a g e
called as multiplexing. It also differentiates the applications that are running on the same
computer (Zhao, Sexton, Park, Baure, Nino & So, 2015).
(Source: https://www.slideshare.net/MukeshChinta/transport-layer-49860637)
The basic services of transport layer is offered by user datagram protocol, the header of the
UDP contains the port address of source and destination and the length of the packet along
with the data checksum bit (Zhao, Sexton, Park, Baure, Nino & So, 2015). The goal of
transport layer is to offer efficient, cost effective and reliable service to the end user.
Some of the services that are offered by transport layer are:
It offers connection oriented communication by using datagrams model like user
datagram protocol and internet protocol (Klemin, Chow & Scoville, 2017) .
Packets are not lost in case of transport layer as they make use of checksum so that
data arrives in the same order and packets are not lost.
called as multiplexing. It also differentiates the applications that are running on the same
computer (Zhao, Sexton, Park, Baure, Nino & So, 2015).
(Source: https://www.slideshare.net/MukeshChinta/transport-layer-49860637)
The basic services of transport layer is offered by user datagram protocol, the header of the
UDP contains the port address of source and destination and the length of the packet along
with the data checksum bit (Zhao, Sexton, Park, Baure, Nino & So, 2015). The goal of
transport layer is to offer efficient, cost effective and reliable service to the end user.
Some of the services that are offered by transport layer are:
It offers connection oriented communication by using datagrams model like user
datagram protocol and internet protocol (Klemin, Chow & Scoville, 2017) .
Packets are not lost in case of transport layer as they make use of checksum so that
data arrives in the same order and packets are not lost.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6 | P a g e
The congestion is also avoided by controlling the traffic over the telecommunication
network. Thus, it can be said that transport layer is responsible for delivering the data
to the appreciate place over the host (Klemin, Chow & Scoville, 2017) .
The processes that are completed on transport layer is multiplexing of data from
different processes and then adding source ad destination port numbers in header.
This helps in identifying the address of the hosts.
Some of the basic functions of data link layer are which breaks the information into small
units known as segments (Boucher, Blightman, Peter, Higgen,Philbrick & Starr, 2016) .
These segments are then transmitted to application layer. It ensures that data is kept in
same sequence and also offers end to end delivery. The two main protocols that are used
by transport layer are transmission control protocol and user datagram protocol that
provides a reliable and unreliable communication between hosts. The transport layer is
responsible for end to end communication and offers a reliable and correct
communication. It delivers the data without any error.
It also offers multiplexing of data by sending the stream of data to many sources and then
permitting users to access the services across the network. Transport layer is a layered
architecture model in network stack that provides host to host communication services for
applications. The purpose of transport layer is to offer end to end communication over the
network. It provides logical communication between processes so that architecture of
protocols is not an issue (Boucher, Blightman, Peter, Higgen,Philbrick & Starr, 2016) .
Transport layer also offer connection less and connection oriented transmission between
source machine and destination machine.
The congestion is also avoided by controlling the traffic over the telecommunication
network. Thus, it can be said that transport layer is responsible for delivering the data
to the appreciate place over the host (Klemin, Chow & Scoville, 2017) .
The processes that are completed on transport layer is multiplexing of data from
different processes and then adding source ad destination port numbers in header.
This helps in identifying the address of the hosts.
Some of the basic functions of data link layer are which breaks the information into small
units known as segments (Boucher, Blightman, Peter, Higgen,Philbrick & Starr, 2016) .
These segments are then transmitted to application layer. It ensures that data is kept in
same sequence and also offers end to end delivery. The two main protocols that are used
by transport layer are transmission control protocol and user datagram protocol that
provides a reliable and unreliable communication between hosts. The transport layer is
responsible for end to end communication and offers a reliable and correct
communication. It delivers the data without any error.
It also offers multiplexing of data by sending the stream of data to many sources and then
permitting users to access the services across the network. Transport layer is a layered
architecture model in network stack that provides host to host communication services for
applications. The purpose of transport layer is to offer end to end communication over the
network. It provides logical communication between processes so that architecture of
protocols is not an issue (Boucher, Blightman, Peter, Higgen,Philbrick & Starr, 2016) .
Transport layer also offer connection less and connection oriented transmission between
source machine and destination machine.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7 | P a g e
Topic 3-Cloud computing and network
Cloud computing is a group of resources that offer services to user at minimum cost. Cloud
computing allow organisation to focus on business goals rather than focusing on the
resources or maintenance of infrastructure (Rittinghouse & Ransome, 2016). Cloud
computing has minimised the infrastructure cost by allowing the organisation to use the
services and pay accordingly. It is practises that allow networks to gain remote services and
allow them to gain access through internet. Cloud computing are eh resources made available
by the third party.
The business operations and processes have shifted to cloud computing due to various
benefits. It is observed that cloud computing has eliminated the cost of capital expenses and
infrastructure cost that is needed to run the software’s. Cloud computing increases the speed
as it make the resources available on a single click. The other benefit of cloud computing is
the ability to scale elastically. It requires less computing power, poor storage and bandwidth
and allow user to access from any geographical location.
Cloud computing removes the need of additional efforts as it is the duty of IT team to invest
time so that business goals be achieved. It is majorly used due to its security services. It
works on large set of policies so that security postures are corrected (Rittinghouse &
Ransome, 2016). There are different type of cloud network available; like public, private and
hybrid. Public clouds are handled by a third party user and they delvers their services so that
it can be used by other users. One popular example of public cloud is Microsoft Azure.
Private cloud is used by an individual or an organisation it is basically used to store personal
data. On the other hand, hybrid clouds are the combination of public as well as private cloud.
Topic 3-Cloud computing and network
Cloud computing is a group of resources that offer services to user at minimum cost. Cloud
computing allow organisation to focus on business goals rather than focusing on the
resources or maintenance of infrastructure (Rittinghouse & Ransome, 2016). Cloud
computing has minimised the infrastructure cost by allowing the organisation to use the
services and pay accordingly. It is practises that allow networks to gain remote services and
allow them to gain access through internet. Cloud computing are eh resources made available
by the third party.
The business operations and processes have shifted to cloud computing due to various
benefits. It is observed that cloud computing has eliminated the cost of capital expenses and
infrastructure cost that is needed to run the software’s. Cloud computing increases the speed
as it make the resources available on a single click. The other benefit of cloud computing is
the ability to scale elastically. It requires less computing power, poor storage and bandwidth
and allow user to access from any geographical location.
Cloud computing removes the need of additional efforts as it is the duty of IT team to invest
time so that business goals be achieved. It is majorly used due to its security services. It
works on large set of policies so that security postures are corrected (Rittinghouse &
Ransome, 2016). There are different type of cloud network available; like public, private and
hybrid. Public clouds are handled by a third party user and they delvers their services so that
it can be used by other users. One popular example of public cloud is Microsoft Azure.
Private cloud is used by an individual or an organisation it is basically used to store personal
data. On the other hand, hybrid clouds are the combination of public as well as private cloud.
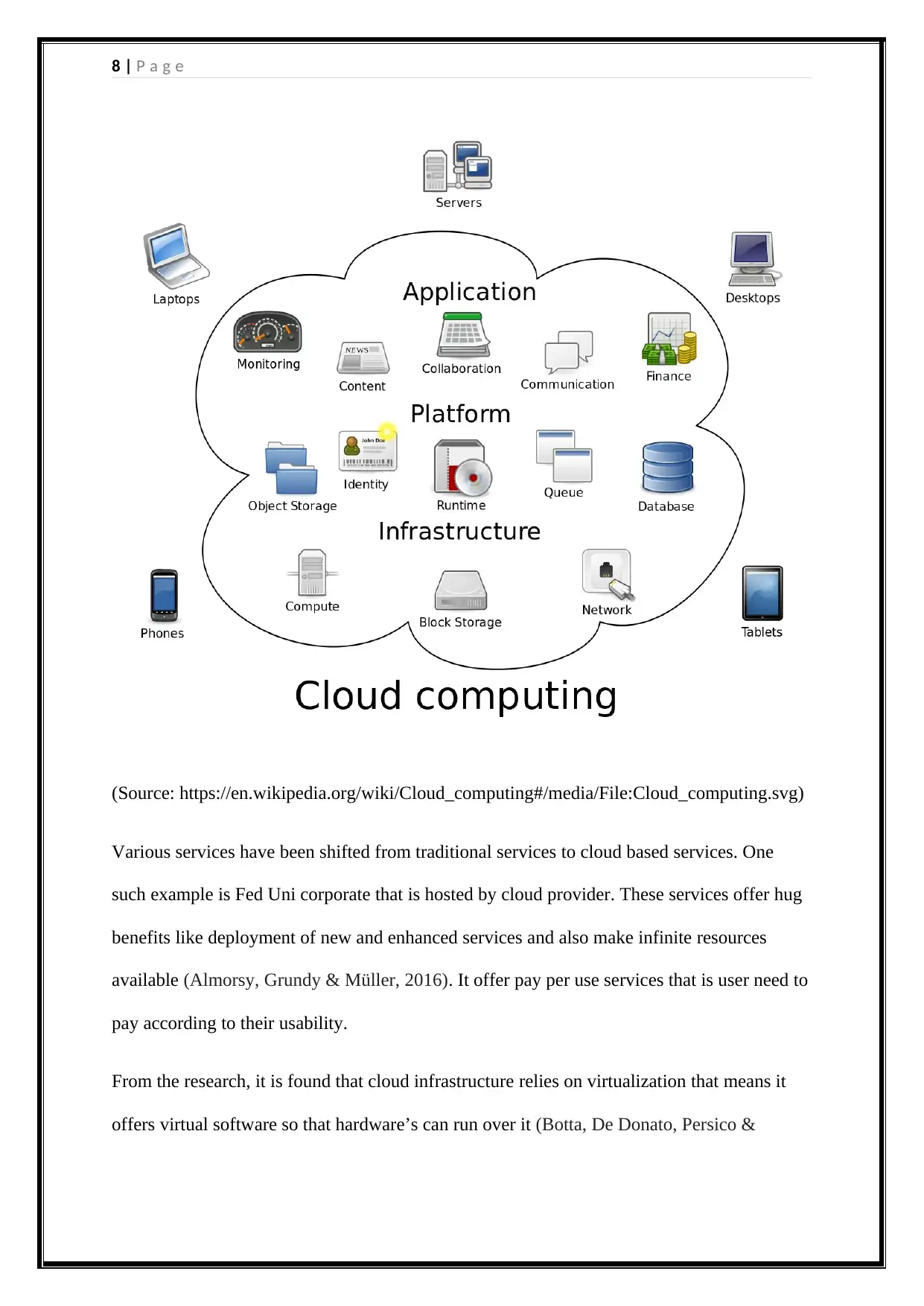
8 | P a g e
(Source: https://en.wikipedia.org/wiki/Cloud_computing#/media/File:Cloud_computing.svg)
Various services have been shifted from traditional services to cloud based services. One
such example is Fed Uni corporate that is hosted by cloud provider. These services offer hug
benefits like deployment of new and enhanced services and also make infinite resources
available (Almorsy, Grundy & Müller, 2016). It offer pay per use services that is user need to
pay according to their usability.
From the research, it is found that cloud infrastructure relies on virtualization that means it
offers virtual software so that hardware’s can run over it (Botta, De Donato, Persico &
(Source: https://en.wikipedia.org/wiki/Cloud_computing#/media/File:Cloud_computing.svg)
Various services have been shifted from traditional services to cloud based services. One
such example is Fed Uni corporate that is hosted by cloud provider. These services offer hug
benefits like deployment of new and enhanced services and also make infinite resources
available (Almorsy, Grundy & Müller, 2016). It offer pay per use services that is user need to
pay according to their usability.
From the research, it is found that cloud infrastructure relies on virtualization that means it
offers virtual software so that hardware’s can run over it (Botta, De Donato, Persico &
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9 | P a g e
Pescapé, 2016)s. The network of cloud and mobile has captured the market. Mobile network
have allowed continuously connection while moving from one cell to another.
Cloud computing network has been used in various ways like creating of new software or
service, storing the data, analysing the information, testing and building applications and
delivering services on demand (Ali, Khan, & Vasilakos, 2015). Cloud computing offers
friendly services that makes it easier for IT team to manage about resources. It saves the
overall cost of the organisation of virtually offering them access to resources instead of
downloading it.
Pescapé, 2016)s. The network of cloud and mobile has captured the market. Mobile network
have allowed continuously connection while moving from one cell to another.
Cloud computing network has been used in various ways like creating of new software or
service, storing the data, analysing the information, testing and building applications and
delivering services on demand (Ali, Khan, & Vasilakos, 2015). Cloud computing offers
friendly services that makes it easier for IT team to manage about resources. It saves the
overall cost of the organisation of virtually offering them access to resources instead of
downloading it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10 | P a g e
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Armstrong, W. J., Basso, C., Chang, C. J., Gusat, M., Lynch, J. J., Minkenberg, C. J., &
Walk, K. M. (2015). U.S. Patent No. 9,077,636. Washington, DC: U.S. Patent and
Trademark Office.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Boucher, L., Blightman, S., Peter, C., Higgen, D., Philbrick, C., & Starr, D. (2016). U.S.
Patent Application No. 15/185,349.
Klemin, B. A., Chow, R., & Scoville, D. (2017). U.S. Patent No. 9,674,303. Washington,
DC: U.S. Patent and Trademark Office.
Lopacinski, L., Nolte, J., Buechner, S., Brzozowski, M., & Kraemer, R. (2015). 100 Gbps
wireless–data link layer VHDL implementation. Measurement Automation
Monitoring, 61.
Olivieri, D., Cristini, F., Monteduro, G., Pariscenti, L., Calabretta, M., Dell'Oro, R., & Murru,
F. A. (2016). U.S. Patent No. 9,378,252. Washington, DC: U.S. Patent and Trademark
Office.
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Armstrong, W. J., Basso, C., Chang, C. J., Gusat, M., Lynch, J. J., Minkenberg, C. J., &
Walk, K. M. (2015). U.S. Patent No. 9,077,636. Washington, DC: U.S. Patent and
Trademark Office.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Boucher, L., Blightman, S., Peter, C., Higgen, D., Philbrick, C., & Starr, D. (2016). U.S.
Patent Application No. 15/185,349.
Klemin, B. A., Chow, R., & Scoville, D. (2017). U.S. Patent No. 9,674,303. Washington,
DC: U.S. Patent and Trademark Office.
Lopacinski, L., Nolte, J., Buechner, S., Brzozowski, M., & Kraemer, R. (2015). 100 Gbps
wireless–data link layer VHDL implementation. Measurement Automation
Monitoring, 61.
Olivieri, D., Cristini, F., Monteduro, G., Pariscenti, L., Calabretta, M., Dell'Oro, R., & Murru,
F. A. (2016). U.S. Patent No. 9,378,252. Washington, DC: U.S. Patent and Trademark
Office.

11 | P a g e
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation,
management, and security. CRC press.
Xu, C., Li, Z., Li, J., Zhang, H., & Muntean, G. M. (2015). Cross-layer fairness-driven
concurrent multipath video delivery over heterogeneous wireless networks. IEEE
Transactions on Circuits and Systems for Video Technology, 25(7), 1175-1189.
Xu, C., Li, Z., Li, J., Zhang, H., & Muntean, G. M. (2015). Cross-layer fairness-driven
concurrent multipath video delivery over heterogeneous wireless networks. IEEE
Transactions on Circuits and Systems for Video Technology, 25(7), 1175-1189.
Zhao, D., Sexton, M., Park, H. Y., Baure, G., Nino, J. C., & So, F. (2015). High‐Efficiency
Solution‐Processed Planar Perovskite Solar Cells with a Polymer Hole Transport
Layer. Advanced Energy Materials, 5(6), 1401855.
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation,
management, and security. CRC press.
Xu, C., Li, Z., Li, J., Zhang, H., & Muntean, G. M. (2015). Cross-layer fairness-driven
concurrent multipath video delivery over heterogeneous wireless networks. IEEE
Transactions on Circuits and Systems for Video Technology, 25(7), 1175-1189.
Xu, C., Li, Z., Li, J., Zhang, H., & Muntean, G. M. (2015). Cross-layer fairness-driven
concurrent multipath video delivery over heterogeneous wireless networks. IEEE
Transactions on Circuits and Systems for Video Technology, 25(7), 1175-1189.
Zhao, D., Sexton, M., Park, H. Y., Baure, G., Nino, J. C., & So, F. (2015). High‐Efficiency
Solution‐Processed Planar Perovskite Solar Cells with a Polymer Hole Transport
Layer. Advanced Energy Materials, 5(6), 1401855.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





