Data Communication and Networking Report - Seagull International
VerifiedAdded on 2022/09/02
|15
|2957
|15
Report
AI Summary
This report details a comprehensive network solution for Seagull International, a company with 50 employees across two locations. It begins with a network diagram and discusses the feasibility of desktop (Windows 10) and server (Windows Server 2016) operating systems, justifying the selections based on features like remote access capabilities, security enhancements, and server roles. The report then explores remote connectivity solutions using VPN, comparing various VPN protocols (IPSec, SSL, etc.) and recommending a VPN solution. It analyzes internet and telephone connectivity options from Australian providers like Telstra, Optus, and TPG, ultimately recommending Telstra for its balance of cost, speed, and flexibility. Furthermore, the report addresses network security for wireless LANs, suggesting WPA2 encryption and security policies to prevent unauthorized access. Finally, it outlines an IP addressing plan to reduce IP address wastage and improve security.

Running head: DATA COMMUNICATION AND NETWORK
Data communication and network
Name of the Student
Name of the University
Author’s Note
Data communication and network
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
DATA COMMUNICATION AND NETWORK
Executive Summary
The roles of desktop server operating system is discussed in the report and an operating system is
selected that would be feasible for the solution. A discussion is also made on the remote
connection setup for the sales team such that they can remotely access the network. An internet
and telephony solution is also given in the report that can help in improving the performance of
the administrator and team of data entry such that they can work competently. A WLAN setup is
also recommended that can help the employees and the guest to associate their wireless device
with the wireless access point for sharing files and information. The network is developed by
creating subnet plan ensuring that IP address wastage is reduced and the security is improved.
DATA COMMUNICATION AND NETWORK
Executive Summary
The roles of desktop server operating system is discussed in the report and an operating system is
selected that would be feasible for the solution. A discussion is also made on the remote
connection setup for the sales team such that they can remotely access the network. An internet
and telephony solution is also given in the report that can help in improving the performance of
the administrator and team of data entry such that they can work competently. A WLAN setup is
also recommended that can help the employees and the guest to associate their wireless device
with the wireless access point for sharing files and information. The network is developed by
creating subnet plan ensuring that IP address wastage is reduced and the security is improved.

2
DATA COMMUNICATION AND NETWORK
Table of Contents
Introduction......................................................................................................................................3
Network Diagram for the Office Setup...........................................................................................3
Feasibility of Desktop and Server Operating System......................................................................3
Remote connectivity Network Solution...........................................................................................5
Internet and telephone connectivity Solution..................................................................................7
Network Security Solution for wireless LAN.................................................................................9
IP Addressing plan.........................................................................................................................10
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
DATA COMMUNICATION AND NETWORK
Table of Contents
Introduction......................................................................................................................................3
Network Diagram for the Office Setup...........................................................................................3
Feasibility of Desktop and Server Operating System......................................................................3
Remote connectivity Network Solution...........................................................................................5
Internet and telephone connectivity Solution..................................................................................7
Network Security Solution for wireless LAN.................................................................................9
IP Addressing plan.........................................................................................................................10
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
DATA COMMUNICATION AND NETWORK
Introduction
A network solution for Seagull International having 50 internal employees’ works in 2
different location is prepared and the steps involved in development of the network are given in
the report. A network solution is developed for the administrative staffs and the data entry
operators such that the staffs are able to access the internet, word processing software, printers
and centralized database and data entry. A network diagram is drawn and attached with the
report demonstrating the essential network device that are needed for setting up the network. A
discussion is made on the feasibility of desktop and server OS. A remote network connectivity
solution is proposed along with the internet and telephone connectivity solution. Network
security solution for WLAN and IP address for the network device is given in the report that can
help in increasing the feasibility of deployment of the network.
Network Diagram for the Office Setup
Feasibility of Desktop and Server Operating System
The network solution requires a desktop and server operating system for the management
of the daily needs of the users.
The processor size of the system may vary in functionality and size and the system are
needed to share files and application with each other while connected in the network. Some of
DATA COMMUNICATION AND NETWORK
Introduction
A network solution for Seagull International having 50 internal employees’ works in 2
different location is prepared and the steps involved in development of the network are given in
the report. A network solution is developed for the administrative staffs and the data entry
operators such that the staffs are able to access the internet, word processing software, printers
and centralized database and data entry. A network diagram is drawn and attached with the
report demonstrating the essential network device that are needed for setting up the network. A
discussion is made on the feasibility of desktop and server OS. A remote network connectivity
solution is proposed along with the internet and telephone connectivity solution. Network
security solution for WLAN and IP address for the network device is given in the report that can
help in increasing the feasibility of deployment of the network.
Network Diagram for the Office Setup
Feasibility of Desktop and Server Operating System
The network solution requires a desktop and server operating system for the management
of the daily needs of the users.
The processor size of the system may vary in functionality and size and the system are
needed to share files and application with each other while connected in the network. Some of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
DATA COMMUNICATION AND NETWORK
the desktop is needed to be enabled with remote access and thus Windows 10 is selected as the
desktop operating system (Pokhrel, Rodrigo and Tsokos, 2017). The main reason behind the
selection of windows 10 is that it does not need any driver software to be installed for running a
device and the device can smoothly run. The booting time is faster than the other desktop
operating system and also provides improved security and enhancement. It has the support for
non-windows devices for example iOS and android.
The servers ae used for providing feature such as unlimited connection for users, usage of
large memory, act as a web, database, email or other server roles, optimized for the network
other than running local application, extension for management, holding the domain and
tolerating fault and avoidance of downtime. For the management of roles of the server the
Windows Server 2016 is selected since it has the support for 24 Tb of memory while the desktop
operating system like Windows 10 have support for 2 TB of memory. The server operating
system has a well CPU usage and it can be configured in different ways for managing different
server roles and as a Hyper V server (Dahouk and Abu-Naser 2018). The server is configured for
controlling the client system running different desktop operating system. It also servers the
request generated from the client computer by working on the base of client server architecture.
The server OS acts as the topmost software on which the other software and application run. The
selection of the Windows server 2016 OS can benefit the organization to get a hybrid and cloud
ready solution and evolve their IT infrastructure (Pan et al. 2018). New security layers are
provided that can secure virtualization and identity of the user. It has the support for cloud ready
application that can help in easy migration of the server to cloud platform.
DATA COMMUNICATION AND NETWORK
the desktop is needed to be enabled with remote access and thus Windows 10 is selected as the
desktop operating system (Pokhrel, Rodrigo and Tsokos, 2017). The main reason behind the
selection of windows 10 is that it does not need any driver software to be installed for running a
device and the device can smoothly run. The booting time is faster than the other desktop
operating system and also provides improved security and enhancement. It has the support for
non-windows devices for example iOS and android.
The servers ae used for providing feature such as unlimited connection for users, usage of
large memory, act as a web, database, email or other server roles, optimized for the network
other than running local application, extension for management, holding the domain and
tolerating fault and avoidance of downtime. For the management of roles of the server the
Windows Server 2016 is selected since it has the support for 24 Tb of memory while the desktop
operating system like Windows 10 have support for 2 TB of memory. The server operating
system has a well CPU usage and it can be configured in different ways for managing different
server roles and as a Hyper V server (Dahouk and Abu-Naser 2018). The server is configured for
controlling the client system running different desktop operating system. It also servers the
request generated from the client computer by working on the base of client server architecture.
The server OS acts as the topmost software on which the other software and application run. The
selection of the Windows server 2016 OS can benefit the organization to get a hybrid and cloud
ready solution and evolve their IT infrastructure (Pan et al. 2018). New security layers are
provided that can secure virtualization and identity of the user. It has the support for cloud ready
application that can help in easy migration of the server to cloud platform.

5
DATA COMMUNICATION AND NETWORK
Remote connectivity Network Solution
When the users are not able to connect with the computer system physically the remote
connection is used with the help of internet. Peoples of the local branches can telecommute with
the sales employees travelling in different location for accessing different files and information.
A secured remote access network is needed to be created that would protect the in-house servers
and the cloud system (Murphy and Edmonds 2018). The solution is developed such that it can eb
managed with the minimum knowledge and assistance of the IT. The development of the remote
access solution would help the remote employees to access the site and fix or troubleshoot the
different problems. The need for travelling and allowing the employees working efficiently can
be reduced for handling different system simultaneously. The remote access network can be set
up simply and is easy to use and thus making it ideal for different industry. Simple settings for
configuration of network devices are used that requires limited technical knowledge and make
the device work together. A secure access is used that can help in securing system without the
need of reconfiguring firewall (Pirinen et al. 2019). VPN solution is deployed that can help in
creating an encrypted ad secured connection with the use of common public internet. Tunneling
protocol is used for the encryption of data during sending and decrypting at the receiving end.
Additional security can be provided with the encryption of sending and receiving address in the
network. The remote employee can use software application that is hosted at the proprietary
network for gaining access of the restricted network with the use of VPN. Authorization is
needed to be used for using the app with the help of password, biometric data or token. The VPN
works by creating a tunnel and creating a point to point connection that cannot be used by the
unknown user. For the creation of the tunnel VPN client software should run on the end client in
cloud or locally. Background service is used for running the VPN client software and it cannot
DATA COMMUNICATION AND NETWORK
Remote connectivity Network Solution
When the users are not able to connect with the computer system physically the remote
connection is used with the help of internet. Peoples of the local branches can telecommute with
the sales employees travelling in different location for accessing different files and information.
A secured remote access network is needed to be created that would protect the in-house servers
and the cloud system (Murphy and Edmonds 2018). The solution is developed such that it can eb
managed with the minimum knowledge and assistance of the IT. The development of the remote
access solution would help the remote employees to access the site and fix or troubleshoot the
different problems. The need for travelling and allowing the employees working efficiently can
be reduced for handling different system simultaneously. The remote access network can be set
up simply and is easy to use and thus making it ideal for different industry. Simple settings for
configuration of network devices are used that requires limited technical knowledge and make
the device work together. A secure access is used that can help in securing system without the
need of reconfiguring firewall (Pirinen et al. 2019). VPN solution is deployed that can help in
creating an encrypted ad secured connection with the use of common public internet. Tunneling
protocol is used for the encryption of data during sending and decrypting at the receiving end.
Additional security can be provided with the encryption of sending and receiving address in the
network. The remote employee can use software application that is hosted at the proprietary
network for gaining access of the restricted network with the use of VPN. Authorization is
needed to be used for using the app with the help of password, biometric data or token. The VPN
works by creating a tunnel and creating a point to point connection that cannot be used by the
unknown user. For the creation of the tunnel VPN client software should run on the end client in
cloud or locally. Background service is used for running the VPN client software and it cannot
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
DATA COMMUNICATION AND NETWORK
be noticed until any issue in performance is noticed. There are different factors affecting the
performance of the VPN such as the interne speed, protocols used by the ISP and the encryption
type (Chibuye and Phiri 2017). The poor quality of service of the enterprise network can also
affect the VPN performance. There are multiple VPN protocols that can be applied for ensuring
that an appropriate security level is achieved for connecting with the system with the network
infrastructure of the organization. The protocols include:
IP Security
Secure Socket layer
Transport Security layer
Point to Point Tunnel Protocol
Layer 2 Tunneling Protocol
OpenVPN
For the deployment of the VPN there are multiple option for the network administrator and it can
be
Remote access VPN
Site to site VPN
Mobile VPN
Hardware VPN
VPN appliance
VPN reconnects
Dynamic multipoint VPN
DATA COMMUNICATION AND NETWORK
be noticed until any issue in performance is noticed. There are different factors affecting the
performance of the VPN such as the interne speed, protocols used by the ISP and the encryption
type (Chibuye and Phiri 2017). The poor quality of service of the enterprise network can also
affect the VPN performance. There are multiple VPN protocols that can be applied for ensuring
that an appropriate security level is achieved for connecting with the system with the network
infrastructure of the organization. The protocols include:
IP Security
Secure Socket layer
Transport Security layer
Point to Point Tunnel Protocol
Layer 2 Tunneling Protocol
OpenVPN
For the deployment of the VPN there are multiple option for the network administrator and it can
be
Remote access VPN
Site to site VPN
Mobile VPN
Hardware VPN
VPN appliance
VPN reconnects
Dynamic multipoint VPN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
DATA COMMUNICATION AND NETWORK
The gateway used here is a RADIUS server that manages the authenticity of the device trying
to access the internal network before granting access to the resources of the organizational
network (Nguyen and Kim 2018). The resource of the network can be printers, file server,
intranets, etc. IPSec security protocol is used along with SSL connection for increasing the
security and encrypting the communication channel.
Internet and telephone connectivity Solution
There are different internet and telephone service provider in Australia having different
plans and option for providing internet. After analysis of the service that are needed in the
current business for 40 – 50 people the option provided by Telstra is selected as the best option.
The service plan and feature provided by the other service provider is compared with each other
for selection of the best suited plan.
Telstra –
$90 per month
Unlimited data
Includes phone service
Telstra Smart Modem
Optus –
$115 per month
Unlimited data
TPG –
DATA COMMUNICATION AND NETWORK
The gateway used here is a RADIUS server that manages the authenticity of the device trying
to access the internal network before granting access to the resources of the organizational
network (Nguyen and Kim 2018). The resource of the network can be printers, file server,
intranets, etc. IPSec security protocol is used along with SSL connection for increasing the
security and encrypting the communication channel.
Internet and telephone connectivity Solution
There are different internet and telephone service provider in Australia having different
plans and option for providing internet. After analysis of the service that are needed in the
current business for 40 – 50 people the option provided by Telstra is selected as the best option.
The service plan and feature provided by the other service provider is compared with each other
for selection of the best suited plan.
Telstra –
$90 per month
Unlimited data
Includes phone service
Telstra Smart Modem
Optus –
$115 per month
Unlimited data
TPG –

8
DATA COMMUNICATION AND NETWORK
$ 59.99 per month + setup cost $99.95
11mbps
For 18-month contract
$79.95
Modem included
Includes phone line
The Telstra plan is recommended since TGP has 18 months contact and huge amount of
money is needed to be spent for initial setup of internet connection. $1189.77 is the minimum
charges for initially set up internet in the office with TGP with the inclusion of modem. The
internet speed is also low when it is compared with the other service provider. If the service of
TGP is selected the service is needed to be used for 18 months and if thee is any new service
required the service cannot be changed and the organization might face stuck in (Tpg.com.au.
2020). The service plan and tariff offered by Optus can meet the requirement of the organization
but the charges or the service is high when compared with Telstra. The service provided by
Optus does not cover all the areas of Australia and the user needs to by the modem separately
that adds on extra charges for the installation of internet connection. Moreover, there are no
phone line connectivity option provided by the service provided for this on-premise solution is
needed to be installed and VoIP configuration is needed to be set up that also adds additional
cost of maintenance for the network solution (Optus 2020). The service and option provided by
Telstra is the best and it meets all the requirement making the network solution reliable and have
higher capacity. The service offered by Telstra is scalable and provides option of adding more
bandwidth for increasing the performance and coverage of the network solution of the enterprise.
The charge of Telstra is also minimum when compared with the other service provider and
DATA COMMUNICATION AND NETWORK
$ 59.99 per month + setup cost $99.95
11mbps
For 18-month contract
$79.95
Modem included
Includes phone line
The Telstra plan is recommended since TGP has 18 months contact and huge amount of
money is needed to be spent for initial setup of internet connection. $1189.77 is the minimum
charges for initially set up internet in the office with TGP with the inclusion of modem. The
internet speed is also low when it is compared with the other service provider. If the service of
TGP is selected the service is needed to be used for 18 months and if thee is any new service
required the service cannot be changed and the organization might face stuck in (Tpg.com.au.
2020). The service plan and tariff offered by Optus can meet the requirement of the organization
but the charges or the service is high when compared with Telstra. The service provided by
Optus does not cover all the areas of Australia and the user needs to by the modem separately
that adds on extra charges for the installation of internet connection. Moreover, there are no
phone line connectivity option provided by the service provided for this on-premise solution is
needed to be installed and VoIP configuration is needed to be set up that also adds additional
cost of maintenance for the network solution (Optus 2020). The service and option provided by
Telstra is the best and it meets all the requirement making the network solution reliable and have
higher capacity. The service offered by Telstra is scalable and provides option of adding more
bandwidth for increasing the performance and coverage of the network solution of the enterprise.
The charge of Telstra is also minimum when compared with the other service provider and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
DATA COMMUNICATION AND NETWORK
provides the maximum speed of 46.30 mbps that is faster enough for handling heavy interne
traffic for 40 – 50 employees using the internet service. Thee is unlimited standard and national
calls to the fixed lines and mobiles. There is no contract that is needed to be signed and thus the
organization does not have to stuck in with Telstra and can easily move in with other service
provider if any problem is faced with their service (Telstra.com.au. 2020). The same price is
needed to be payed for the ADSL and NBN connection and thus the ADSL option can eb
selected for its application in the organization.
Network Security Solution for wireless LAN
For the development of the network security solution the wireless network devices are
needed to be configured with WPA2 encryption algorithm and security policy such that the
unauthroised access of the organizational network is prevented and the resources of the network
are secured. Most of the wireless devices that are currently available supports the WPA2 security
encryption and be integrated with the current network solution for the mitigation of threats. The
wireless network can face security issues like denial of service, rogue access or passive
capturing. It can be prevented with the deployment of firewall, intrusion detection system,
content filtering, authentication and data encryption (Goswami and Asadollahi 2018). The
firewall can prevent unidentified access and secure the network availability for the remote and
the on-site employees, customers and business partners. It can also be used for the wired or
wireless environment. The intrusion detection system uses the software intelligence for
identifying hacks, worms, viruses, trojan and other types of threats. The content filtering is
applied in the network such that the network is secured from the internal activity and preventing
the employees to access malicious websites containing threats that can be harmful if operated
(Wilson 2018). The authentication is used for protection and securing data in the network and
DATA COMMUNICATION AND NETWORK
provides the maximum speed of 46.30 mbps that is faster enough for handling heavy interne
traffic for 40 – 50 employees using the internet service. Thee is unlimited standard and national
calls to the fixed lines and mobiles. There is no contract that is needed to be signed and thus the
organization does not have to stuck in with Telstra and can easily move in with other service
provider if any problem is faced with their service (Telstra.com.au. 2020). The same price is
needed to be payed for the ADSL and NBN connection and thus the ADSL option can eb
selected for its application in the organization.
Network Security Solution for wireless LAN
For the development of the network security solution the wireless network devices are
needed to be configured with WPA2 encryption algorithm and security policy such that the
unauthroised access of the organizational network is prevented and the resources of the network
are secured. Most of the wireless devices that are currently available supports the WPA2 security
encryption and be integrated with the current network solution for the mitigation of threats. The
wireless network can face security issues like denial of service, rogue access or passive
capturing. It can be prevented with the deployment of firewall, intrusion detection system,
content filtering, authentication and data encryption (Goswami and Asadollahi 2018). The
firewall can prevent unidentified access and secure the network availability for the remote and
the on-site employees, customers and business partners. It can also be used for the wired or
wireless environment. The intrusion detection system uses the software intelligence for
identifying hacks, worms, viruses, trojan and other types of threats. The content filtering is
applied in the network such that the network is secured from the internal activity and preventing
the employees to access malicious websites containing threats that can be harmful if operated
(Wilson 2018). The authentication is used for protection and securing data in the network and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
DATA COMMUNICATION AND NETWORK
with the addition of password protection such as WPA2, WPSK2, biometric authentication it is
also needed to be ensured that proper authority have the access to the secured data such that the
wireless network is kept safe. The data encryption is applied for sharing and analyzing vital
information about customer and business and also securing the VPN and wireless network. Cisco
WAP121, Ruckus wireless ZoneFlex, Catalyst 9100 access point, etc. are the device that can be
deployed in the network for meeting the current needs.
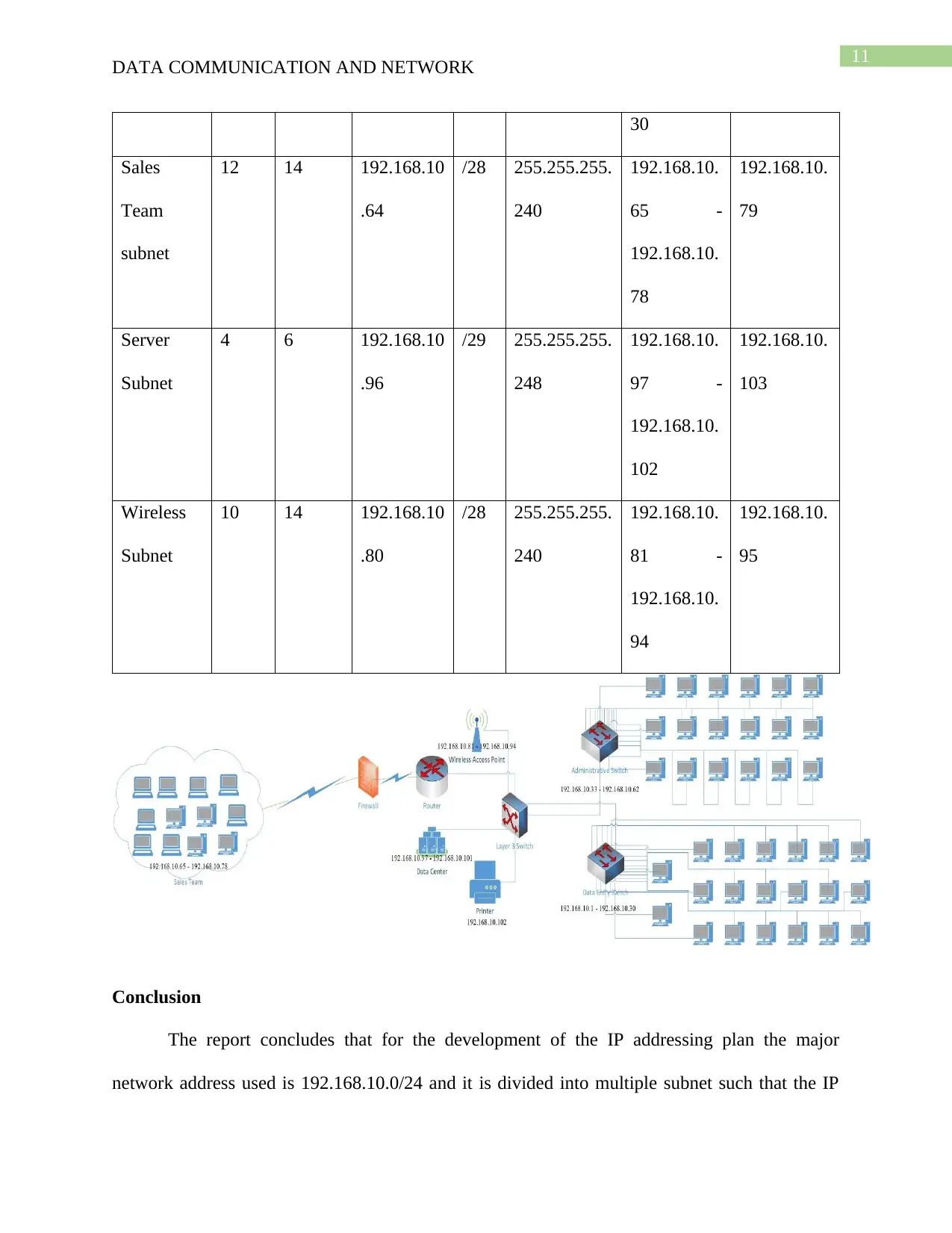
IP Addressing plan
The following is the IP addressing plan provided for the network diagram created for
Seagull international having 18 administrative staffs, 20 data entry operators, 12 sales team and
server network.
The subnetting of the IP address would increase the efficiency and performance of the
network.
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Administr
ator subnet
18 30 192.168.10
.32
/27 255.255.255.
224
192.168.10.
33 -
192.168.10.
62
192.168.10.
63
Data entry
Subnet
20 30 192.168.10
.0
/27 255.255.255.
224
192.168.10.
1 -
192.168.10.
192.168.10.
31
DATA COMMUNICATION AND NETWORK
with the addition of password protection such as WPA2, WPSK2, biometric authentication it is
also needed to be ensured that proper authority have the access to the secured data such that the
wireless network is kept safe. The data encryption is applied for sharing and analyzing vital
information about customer and business and also securing the VPN and wireless network. Cisco
WAP121, Ruckus wireless ZoneFlex, Catalyst 9100 access point, etc. are the device that can be
deployed in the network for meeting the current needs.
IP Addressing plan
The following is the IP addressing plan provided for the network diagram created for
Seagull international having 18 administrative staffs, 20 data entry operators, 12 sales team and
server network.
The subnetting of the IP address would increase the efficiency and performance of the
network.
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Administr
ator subnet
18 30 192.168.10
.32
/27 255.255.255.
224
192.168.10.
33 -
192.168.10.
62
192.168.10.
63
Data entry
Subnet
20 30 192.168.10
.0
/27 255.255.255.
224
192.168.10.
1 -
192.168.10.
192.168.10.
31
11
DATA COMMUNICATION AND NETWORK
30
Sales
Team
subnet
12 14 192.168.10
.64
/28 255.255.255.
240
192.168.10.
65 -
192.168.10.
78
192.168.10.
79
Server
Subnet
4 6 192.168.10
.96
/29 255.255.255.
248
192.168.10.
97 -
192.168.10.
102
192.168.10.
103
Wireless
Subnet
10 14 192.168.10
.80
/28 255.255.255.
240
192.168.10.
81 -
192.168.10.
94
192.168.10.
95
Conclusion
The report concludes that for the development of the IP addressing plan the major
network address used is 192.168.10.0/24 and it is divided into multiple subnet such that the IP
DATA COMMUNICATION AND NETWORK
30
Sales
Team
subnet
12 14 192.168.10
.64
/28 255.255.255.
240
192.168.10.
65 -
192.168.10.
78
192.168.10.
79
Server
Subnet
4 6 192.168.10
.96
/29 255.255.255.
248
192.168.10.
97 -
192.168.10.
102
192.168.10.
103
Wireless
Subnet
10 14 192.168.10
.80
/28 255.255.255.
240
192.168.10.
81 -
192.168.10.
94
192.168.10.
95
Conclusion
The report concludes that for the development of the IP addressing plan the major
network address used is 192.168.10.0/24 and it is divided into multiple subnet such that the IP
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





