Data Security and Privacy in IoT/CPS: Issues and Solutions
VerifiedAdded on 2022/09/18
|9
|1721
|26
Report
AI Summary
This report addresses the critical issues of data security and privacy within Cyber-Physical Systems (CPS) and the Internet of Things (IoT). It begins by outlining the background, problem statement, and research objectives, emphasizing the increasing risks associated with CPS. The literature review explores the architecture of CPS, including perceptual, data transmission, and application layers, and identifies vulnerabilities and threats such as Man-in-the-Middle and Denial of Service (DoS) attacks. The methodology section details the qualitative approach, descriptive research design, and data collection from secondary sources like online journals and academic papers, with thematic analysis used to identify data privacy issues and mitigation strategies. The report aims to identify current issues related to data privacy and security faced in CPS/IoT systems, analyze proper solutions to mitigate these issues, and recommend strategies for the proper usage of CPS/IoT systems. The expected outcomes will help in identifying data privacy issues in CPS/IoT system and strategies for mitigating it properly.

Data Security and Privacy in the IOT/CPS
Name of the Student
Name of the University
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction..................................................................................................................................3
1.1 Background............................................................................................................................3
1.2 Problem Statement.................................................................................................................3
1.3 Aim, Objectives and Research questions...............................................................................4
2. Literature Review........................................................................................................................5
3. Methodology................................................................................................................................7
References........................................................................................................................................9
1. Introduction..................................................................................................................................3
1.1 Background............................................................................................................................3
1.2 Problem Statement.................................................................................................................3
1.3 Aim, Objectives and Research questions...............................................................................4
2. Literature Review........................................................................................................................5
3. Methodology................................................................................................................................7
References........................................................................................................................................9

1. Introduction
1.1 Background
Cyber Physical System (CPS) has been one of the core technologies has been realizing Internet
of Things (IoT) CPS has been creating a new environment which involve cyber and physical
world in our daily lives. However, there are certain issues created by the usage of CPS layers that
is related to threats (Yu et al. 2017). Therefore, it has been necessary to understand and research
on CPS security. The CPS include number of issues through present security fairs and issues.
The digital environment which is computed, managed and communicated by computer programs.
The CPS include hardware, software, sensors, embedded systems and actuators which are
connected by network in order to form complex systems. The state of being has been running on
various sensors and Internet of Things. The improvement of CPS development has been a key for
redesigning individual fulfillment viably. The advancement CPS innovation is the way to
improving the personal satisfaction all the more productively. Dangers getting more and intense
regarding security. The CPS experiences issues of surveying dangers and vulnerabilities brought
about by collaborations. The physical environment has been running on various sensors and
Internet of Things. The development of CPS technology has been a key for enhancing quality of
life efficiently. However, risks have been making in more acute in the society. This research will
focus in different risks including data privacy and security in the CPS. Several effects of these
threats have been analyzed in the research.
1.2 Problem Statement
CPS has been providing various benefits to enhance life style of human lives. However, there are
certain risks involved in the CPS (Lin et al. 2017). Data security and privacy have been one of
1.1 Background
Cyber Physical System (CPS) has been one of the core technologies has been realizing Internet
of Things (IoT) CPS has been creating a new environment which involve cyber and physical
world in our daily lives. However, there are certain issues created by the usage of CPS layers that
is related to threats (Yu et al. 2017). Therefore, it has been necessary to understand and research
on CPS security. The CPS include number of issues through present security fairs and issues.
The digital environment which is computed, managed and communicated by computer programs.
The CPS include hardware, software, sensors, embedded systems and actuators which are
connected by network in order to form complex systems. The state of being has been running on
various sensors and Internet of Things. The improvement of CPS development has been a key for
redesigning individual fulfillment viably. The advancement CPS innovation is the way to
improving the personal satisfaction all the more productively. Dangers getting more and intense
regarding security. The CPS experiences issues of surveying dangers and vulnerabilities brought
about by collaborations. The physical environment has been running on various sensors and
Internet of Things. The development of CPS technology has been a key for enhancing quality of
life efficiently. However, risks have been making in more acute in the society. This research will
focus in different risks including data privacy and security in the CPS. Several effects of these
threats have been analyzed in the research.
1.2 Problem Statement
CPS has been providing various benefits to enhance life style of human lives. However, there are
certain risks involved in the CPS (Lin et al. 2017). Data security and privacy have been one of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the main issues discussed in this research. Cyber-attacks including Denial of Service attack
(DoS) attack and Man in middle attack are actively affecting CPS. This research will focus on
these attacks which create threat to data privacy and security.
1.3 Aim, Objectives and Research questions
The aim of the research has been focused on data privacy and security related issues in CPS/IoT
systems.
Following are objectives of the research:
To identify current issues related to data privacy and security faced in CPS/IoT systems
To analyze proper solutions to mitigate issues related to data privacy and security in
CPS/IoT systems
To recommend strategies for proper usage of CPS/IoT systems
Following are research questions inckuded in this research:
What current issues related to data privacy and security are faced in CPS/IoT systems?
How to mitigate these issues related to data privacy and security in CPS/IoT systems?
What strategies can be implemented for proper utilization of CPS/IoT systems?
(DoS) attack and Man in middle attack are actively affecting CPS. This research will focus on
these attacks which create threat to data privacy and security.
1.3 Aim, Objectives and Research questions
The aim of the research has been focused on data privacy and security related issues in CPS/IoT
systems.
Following are objectives of the research:
To identify current issues related to data privacy and security faced in CPS/IoT systems
To analyze proper solutions to mitigate issues related to data privacy and security in
CPS/IoT systems
To recommend strategies for proper usage of CPS/IoT systems
Following are research questions inckuded in this research:
What current issues related to data privacy and security are faced in CPS/IoT systems?
How to mitigate these issues related to data privacy and security in CPS/IoT systems?
What strategies can be implemented for proper utilization of CPS/IoT systems?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Literature Review
As commented by Ashibani and Mahmoud (2017), Cyber Physical Systems has been creating
new environment which can be communicated and managed by a world created by computer
programs. CPS has been a technology which is related to the IoT and a next generation network
based distributed control system that helps in combining a physical system with sensors and
actuators and a computing element that controls it. It has been emphasizing several exchanges
between cyber and physical worlds. Dependence on the CPS is gradually increasing in a variety
of application in the energy, transportation, medical and manufacturing sectors. The CPS
incorporate number of issues through current security markets and security issues. The advanced
condition which is registered, overseen and conveyed by PC programs. The CPS incorporate
equipment, programming, sensors, implanted frameworks and actuators which are associated by
organize so as to shape complex frameworks (Kim et al. 2018). The physical condition has been
running on different sensors and Internet of Things. The improvement of CPS innovation has
been a key for upgrading personal satisfaction effectively. The development CPS technology is
the key to improving the quality of life more efficiently. Risks becoming more and acute in terms
of security. The CPS has difficulty of assessing threats and vulnerabilities caused by interactions.
Cyber-terrorists have been attacking real control systems as well as information security in
virtual spaces including computers on Internet servers. All IoT devices and sensors are connected
and controlled on the network which result in spread of security damage from virtual space.
There are three different layers including perceptual layer, data transmission layer and
application layer. The first layer include recognition and sensor consists of global positioning
system (GPS), RFID, sensor, actuator, camera and IoT (Al-Omary et al. 2018). The collected
data can be compromised of sound light, mechanical, chemical, thermal, electrical, biology and
As commented by Ashibani and Mahmoud (2017), Cyber Physical Systems has been creating
new environment which can be communicated and managed by a world created by computer
programs. CPS has been a technology which is related to the IoT and a next generation network
based distributed control system that helps in combining a physical system with sensors and
actuators and a computing element that controls it. It has been emphasizing several exchanges
between cyber and physical worlds. Dependence on the CPS is gradually increasing in a variety
of application in the energy, transportation, medical and manufacturing sectors. The CPS
incorporate number of issues through current security markets and security issues. The advanced
condition which is registered, overseen and conveyed by PC programs. The CPS incorporate
equipment, programming, sensors, implanted frameworks and actuators which are associated by
organize so as to shape complex frameworks (Kim et al. 2018). The physical condition has been
running on different sensors and Internet of Things. The improvement of CPS innovation has
been a key for upgrading personal satisfaction effectively. The development CPS technology is
the key to improving the quality of life more efficiently. Risks becoming more and acute in terms
of security. The CPS has difficulty of assessing threats and vulnerabilities caused by interactions.
Cyber-terrorists have been attacking real control systems as well as information security in
virtual spaces including computers on Internet servers. All IoT devices and sensors are connected
and controlled on the network which result in spread of security damage from virtual space.
There are three different layers including perceptual layer, data transmission layer and
application layer. The first layer include recognition and sensor consists of global positioning
system (GPS), RFID, sensor, actuator, camera and IoT (Al-Omary et al. 2018). The collected
data can be compromised of sound light, mechanical, chemical, thermal, electrical, biology and
location data and sensor can generate real time data through node collaboration in wide area and
local network domains. The communication layer has been responsible for reliability and support
real-time transmission. The application layer have been applied and interacted with various fields
and referred by different name depending on application.
There have been several attacks on the CPS/IOT systems which are named below:
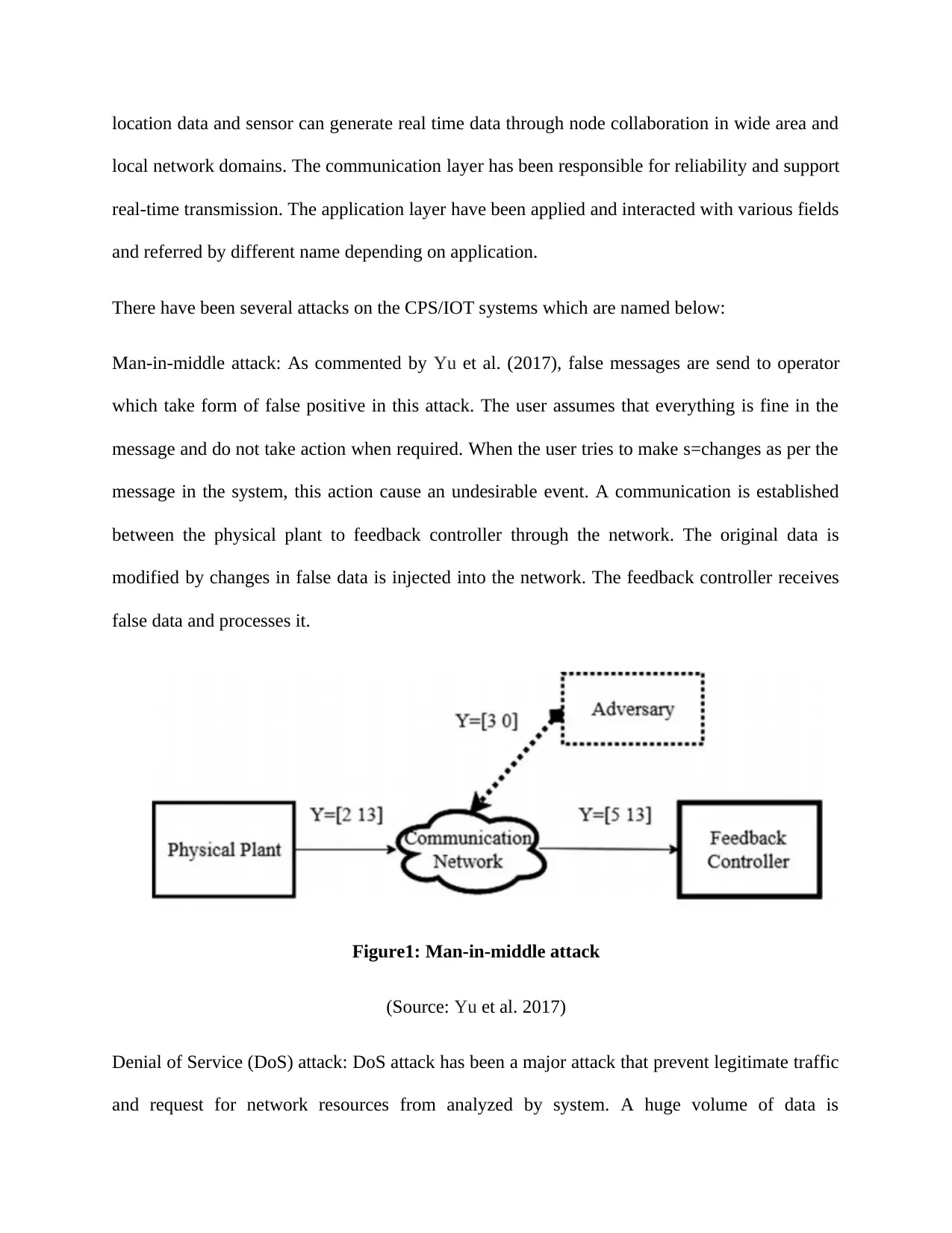
Man-in-middle attack: As commented by Yu et al. (2017), false messages are send to operator
which take form of false positive in this attack. The user assumes that everything is fine in the
message and do not take action when required. When the user tries to make s=changes as per the
message in the system, this action cause an undesirable event. A communication is established
between the physical plant to feedback controller through the network. The original data is
modified by changes in false data is injected into the network. The feedback controller receives
false data and processes it.
Figure1: Man-in-middle attack
(Source: Yu et al. 2017)
Denial of Service (DoS) attack: DoS attack has been a major attack that prevent legitimate traffic
and request for network resources from analyzed by system. A huge volume of data is
local network domains. The communication layer has been responsible for reliability and support
real-time transmission. The application layer have been applied and interacted with various fields
and referred by different name depending on application.
There have been several attacks on the CPS/IOT systems which are named below:
Man-in-middle attack: As commented by Yu et al. (2017), false messages are send to operator
which take form of false positive in this attack. The user assumes that everything is fine in the
message and do not take action when required. When the user tries to make s=changes as per the
message in the system, this action cause an undesirable event. A communication is established
between the physical plant to feedback controller through the network. The original data is
modified by changes in false data is injected into the network. The feedback controller receives
false data and processes it.
Figure1: Man-in-middle attack
(Source: Yu et al. 2017)
Denial of Service (DoS) attack: DoS attack has been a major attack that prevent legitimate traffic
and request for network resources from analyzed by system. A huge volume of data is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
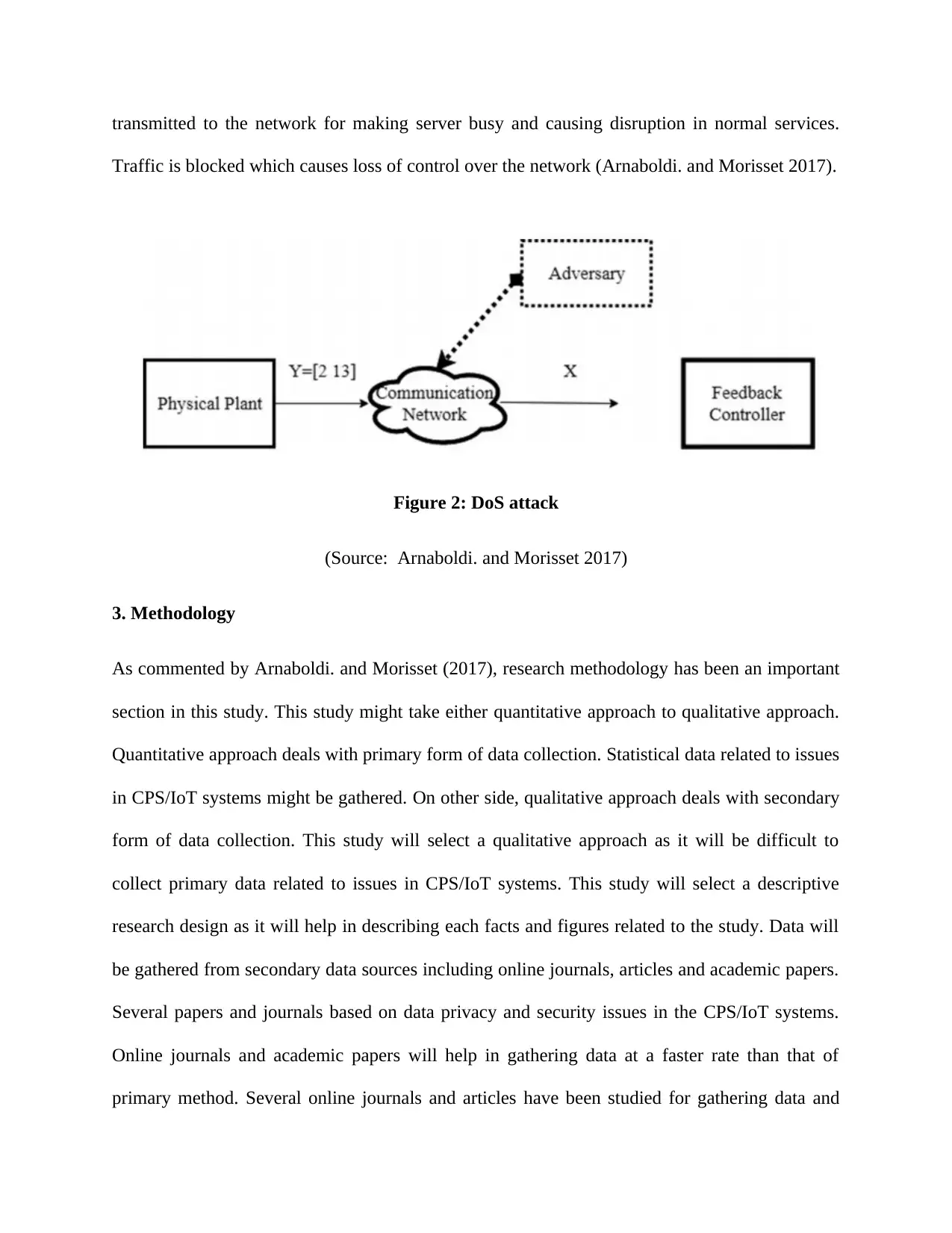
transmitted to the network for making server busy and causing disruption in normal services.
Traffic is blocked which causes loss of control over the network (Arnaboldi. and Morisset 2017).
Figure 2: DoS attack
(Source: Arnaboldi. and Morisset 2017)
3. Methodology
As commented by Arnaboldi. and Morisset (2017), research methodology has been an important
section in this study. This study might take either quantitative approach to qualitative approach.
Quantitative approach deals with primary form of data collection. Statistical data related to issues
in CPS/IoT systems might be gathered. On other side, qualitative approach deals with secondary
form of data collection. This study will select a qualitative approach as it will be difficult to
collect primary data related to issues in CPS/IoT systems. This study will select a descriptive
research design as it will help in describing each facts and figures related to the study. Data will
be gathered from secondary data sources including online journals, articles and academic papers.
Several papers and journals based on data privacy and security issues in the CPS/IoT systems.
Online journals and academic papers will help in gathering data at a faster rate than that of
primary method. Several online journals and articles have been studied for gathering data and
Traffic is blocked which causes loss of control over the network (Arnaboldi. and Morisset 2017).
Figure 2: DoS attack
(Source: Arnaboldi. and Morisset 2017)
3. Methodology
As commented by Arnaboldi. and Morisset (2017), research methodology has been an important
section in this study. This study might take either quantitative approach to qualitative approach.
Quantitative approach deals with primary form of data collection. Statistical data related to issues
in CPS/IoT systems might be gathered. On other side, qualitative approach deals with secondary
form of data collection. This study will select a qualitative approach as it will be difficult to
collect primary data related to issues in CPS/IoT systems. This study will select a descriptive
research design as it will help in describing each facts and figures related to the study. Data will
be gathered from secondary data sources including online journals, articles and academic papers.
Several papers and journals based on data privacy and security issues in the CPS/IoT systems.
Online journals and academic papers will help in gathering data at a faster rate than that of
primary method. Several online journals and articles have been studied for gathering data and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information related to the data privacy and security. Sample size of 15 journals related to the
research topic will be selected for data collection in the research. Data will be analyzed with the
help of qualitative data analysis method. Themes will be created based on the research
objectives. Thematic analysis will be done on the themes. Expected outcomes will help in
identifying data privacy issues in CPS/IoT system and strategies for mitigating it properly. Data
and information will be kept safe under Data Protection Act 1998.
research topic will be selected for data collection in the research. Data will be analyzed with the
help of qualitative data analysis method. Themes will be created based on the research
objectives. Thematic analysis will be done on the themes. Expected outcomes will help in
identifying data privacy issues in CPS/IoT system and strategies for mitigating it properly. Data
and information will be kept safe under Data Protection Act 1998.

References
Al-Omary, A., Othman, A., AlSabbagh, H.M. and Al-Rizzo, H., 2018. Survey of hardware-based
security support for IoT/CPS systems. KnE Engineering, pp.52-70.
https://knepublishing.com/index.php/KnE-Engineering/article/view/3072/6567
Arnaboldi, L. and Morisset, C., 2017, September. Quantitative analysis of dos attacks and client
puzzles in iot systems. In International Workshop on Security and Trust Management (pp. 224-
233). Springer, Cham. https://arxiv.org/pdf/1710.11021.pdf
Ashibani, Y. and Mahmoud, Q.H., 2017. Cyber physical systems security: Analysis, challenges
and solutions. Computers & Security, 68, pp.81-97.
https://fardapaper.ir/mohavaha/uploads/2019/09/Fardapaper-Cyber-physical-systems-security-
Analysis-challenges-and-solutions.pdf
Kim, N.Y., Rathore, S., Ryu, J.H., Park, J.H. and Park, J.H., 2018. A Survey on Cyber Physical
System Security for IoT: Issues, Challenges, Threats, Solutions. Journal of Information
Processing Systems, 14(6). https://s3.ap-northeast-2.amazonaws.com/journal-home/journal/jips/
fullText/98/jips_613.pdf
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.
https://sites.cs.ucsb.edu/~rich/class/cs293s-iot/lecture-6.pdf
Yu, W., Fu, X., Song, H., Economides, A.A., Jo, M. and Zhao, W., 2017. Guest Editorial Special
Issue on Security and Privacy in Cyber-Physical Systems. IEEE Internet of Things Journal, 4(6),
pp.1798-1801. https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=8176069
Al-Omary, A., Othman, A., AlSabbagh, H.M. and Al-Rizzo, H., 2018. Survey of hardware-based
security support for IoT/CPS systems. KnE Engineering, pp.52-70.
https://knepublishing.com/index.php/KnE-Engineering/article/view/3072/6567
Arnaboldi, L. and Morisset, C., 2017, September. Quantitative analysis of dos attacks and client
puzzles in iot systems. In International Workshop on Security and Trust Management (pp. 224-
233). Springer, Cham. https://arxiv.org/pdf/1710.11021.pdf
Ashibani, Y. and Mahmoud, Q.H., 2017. Cyber physical systems security: Analysis, challenges
and solutions. Computers & Security, 68, pp.81-97.
https://fardapaper.ir/mohavaha/uploads/2019/09/Fardapaper-Cyber-physical-systems-security-
Analysis-challenges-and-solutions.pdf
Kim, N.Y., Rathore, S., Ryu, J.H., Park, J.H. and Park, J.H., 2018. A Survey on Cyber Physical
System Security for IoT: Issues, Challenges, Threats, Solutions. Journal of Information
Processing Systems, 14(6). https://s3.ap-northeast-2.amazonaws.com/journal-home/journal/jips/
fullText/98/jips_613.pdf
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.
https://sites.cs.ucsb.edu/~rich/class/cs293s-iot/lecture-6.pdf
Yu, W., Fu, X., Song, H., Economides, A.A., Jo, M. and Zhao, W., 2017. Guest Editorial Special
Issue on Security and Privacy in Cyber-Physical Systems. IEEE Internet of Things Journal, 4(6),
pp.1798-1801. https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=8176069
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





