Analyzing Data Safety Concerns and Ransomware Threats (ISYS100)
VerifiedAdded on 2022/11/14
|16
|3563
|4
Report
AI Summary
This report delves into the critical issue of data safety, particularly in the context of increasing ransomware threats. It begins by emphasizing the value of data as a crucial asset for commercial enterprises and highlights the ongoing challenges in maintaining its security. The report then proceeds to analyze three significant ransomware attacks from the past five years: TeslaCrypt, Simple Locker, and WannaCry. Each example is examined in detail, including its classification, the platform of the attack, the date of occurrence, and the specific impacts on data security, such as data encryption and alteration. The analysis includes figures and diagrams to illustrate the data breaches and the methods used by the cybercriminals. The report concludes by suggesting that current data security measures are insufficient, especially for data transmitted over private networks, and that more robust and secure platforms for data transmission are needed. The report stresses the importance of reliable data backup and the adoption of updated security measures to mitigate the risks associated with ransomware attacks.

Running head: DATA SAFETY CONSIDERING RANSOMWARE
Data safety considering Ransomware
Name of the Student
Name of the University
Author Note:
Data safety considering Ransomware
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA SAFETY CONSIDERING RANSOMWARE
Table of Contents
Introduction......................................................................................................................................2
Example 1: Tesla Crypt...................................................................................................................3
Example 2: Simple Locker..............................................................................................................5
Example 3: Wanna Cry ransomeware attack...................................................................................8
Recommendations..........................................................................................................................10
Conclusion.....................................................................................................................................11
Reference.......................................................................................................................................13
Table of Contents
Introduction......................................................................................................................................2
Example 1: Tesla Crypt...................................................................................................................3
Example 2: Simple Locker..............................................................................................................5
Example 3: Wanna Cry ransomeware attack...................................................................................8
Recommendations..........................................................................................................................10
Conclusion.....................................................................................................................................11
Reference.......................................................................................................................................13

2DATA SAFETY CONSIDERING RANSOMWARE
Topic: With so much discussion about ransomware in the media in recent times, discuss
how safe our data is right now. Use high profile examples from the past 5 years to support
your position.
Introduction
Data is considered as an asset in most of the commercial enterprises these days, at the
same time it can also be said that the data security is a huge concern in our society as well.
However, it can be said that there are lots of data security challenges which exists these days
such as the authorized data access and the data alteration (Javed et al. 2019). Data protection is a
very important factor as it is responsible for profit and loss of commercial organization where
data is considered as an asset. The different aspects of data security are user authentication, data
encryption and data erasure. Data plays a huge role to maintain business reputation in most of the
commercial organizations. Adequate security measures are needed to secure the organization
data from the threats coming from both inside as well from outside the organization (Kamoun
and Nicho 2018). The threats coming outside the organization in terms of the cyber security will
be evaluated in this paper. Based on the external threats such as the threat coming from cyber
security issues such as Ramsomware it can be said that the data which are used in our society as
well as the data which are transported from one place to the other are not very much safe (Hong
2018). Any kinds of data manipulation as well as data alteration can have a huge impact in most
of the commercial organizations.
Inspite of the International data protection rules and regulations such as the General
Data Protection Regulation which was enacted in the year 2016, it can be said that the social
engineers are also enhancing their actions and strategies to encrypt the business data. Social
engineers from all over the world are using advanced encryption technique to encrypt different
Topic: With so much discussion about ransomware in the media in recent times, discuss
how safe our data is right now. Use high profile examples from the past 5 years to support
your position.
Introduction
Data is considered as an asset in most of the commercial enterprises these days, at the
same time it can also be said that the data security is a huge concern in our society as well.
However, it can be said that there are lots of data security challenges which exists these days
such as the authorized data access and the data alteration (Javed et al. 2019). Data protection is a
very important factor as it is responsible for profit and loss of commercial organization where
data is considered as an asset. The different aspects of data security are user authentication, data
encryption and data erasure. Data plays a huge role to maintain business reputation in most of the
commercial organizations. Adequate security measures are needed to secure the organization
data from the threats coming from both inside as well from outside the organization (Kamoun
and Nicho 2018). The threats coming outside the organization in terms of the cyber security will
be evaluated in this paper. Based on the external threats such as the threat coming from cyber
security issues such as Ramsomware it can be said that the data which are used in our society as
well as the data which are transported from one place to the other are not very much safe (Hong
2018). Any kinds of data manipulation as well as data alteration can have a huge impact in most
of the commercial organizations.
Inspite of the International data protection rules and regulations such as the General
Data Protection Regulation which was enacted in the year 2016, it can be said that the social
engineers are also enhancing their actions and strategies to encrypt the business data. Social
engineers from all over the world are using advanced encryption technique to encrypt different
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DATA SAFETY CONSIDERING RANSOMWARE
types of data such as the business data, organizational data as well as the organizational data. The
average cost of securing any data in a cloud servers such as Amazon Web Services is also
increasing each day.
It can be said that there are different types of data threats such as the computer viruses,
rogue security software, spyware and adware, computer worms, cyber security threats such as
ransomeware, DDoS attacks, phishing emails, Rootkit. Network security threats are also
increasing each day due to the presence of harmful viruses such as the Trojan horse and the SQL
injection attack (Piper 2018). There are different ransomeware attack which occurred in the last 5
years which had a direct impact on the data security. The following unit of the paper will be
describing each of the 5 examples in a detailed manner.
Example 1: Tesla Crypt
Classification: Is can be defined as a category of ransomeware Trojan. This harmful
virus was created independently. Wide range of encryption techniques were used by this harmful
virus during this ransomeware attack.
Platform of the attack: One of the most significant platform which were used in this
ransomware attack is the Angler Adobe Flash. The security vulnerabilities as well as the
loopholes of the Angler Adobe Flash were utilized by the social engineers of this ransomeware
attack. Both symmetric as well as the asymmetric data encryption techniques were used in this
ransomeware attack (Russo et al. 2016). Security vulnerabilities of Kaspersky which is one of
the most reputed anti-virus software applications were also capitalized by the social engineers of
the Tesla Crypt.
types of data such as the business data, organizational data as well as the organizational data. The
average cost of securing any data in a cloud servers such as Amazon Web Services is also
increasing each day.
It can be said that there are different types of data threats such as the computer viruses,
rogue security software, spyware and adware, computer worms, cyber security threats such as
ransomeware, DDoS attacks, phishing emails, Rootkit. Network security threats are also
increasing each day due to the presence of harmful viruses such as the Trojan horse and the SQL
injection attack (Piper 2018). There are different ransomeware attack which occurred in the last 5
years which had a direct impact on the data security. The following unit of the paper will be
describing each of the 5 examples in a detailed manner.
Example 1: Tesla Crypt
Classification: Is can be defined as a category of ransomeware Trojan. This harmful
virus was created independently. Wide range of encryption techniques were used by this harmful
virus during this ransomeware attack.
Platform of the attack: One of the most significant platform which were used in this
ransomware attack is the Angler Adobe Flash. The security vulnerabilities as well as the
loopholes of the Angler Adobe Flash were utilized by the social engineers of this ransomeware
attack. Both symmetric as well as the asymmetric data encryption techniques were used in this
ransomeware attack (Russo et al. 2016). Security vulnerabilities of Kaspersky which is one of
the most reputed anti-virus software applications were also capitalized by the social engineers of
the Tesla Crypt.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
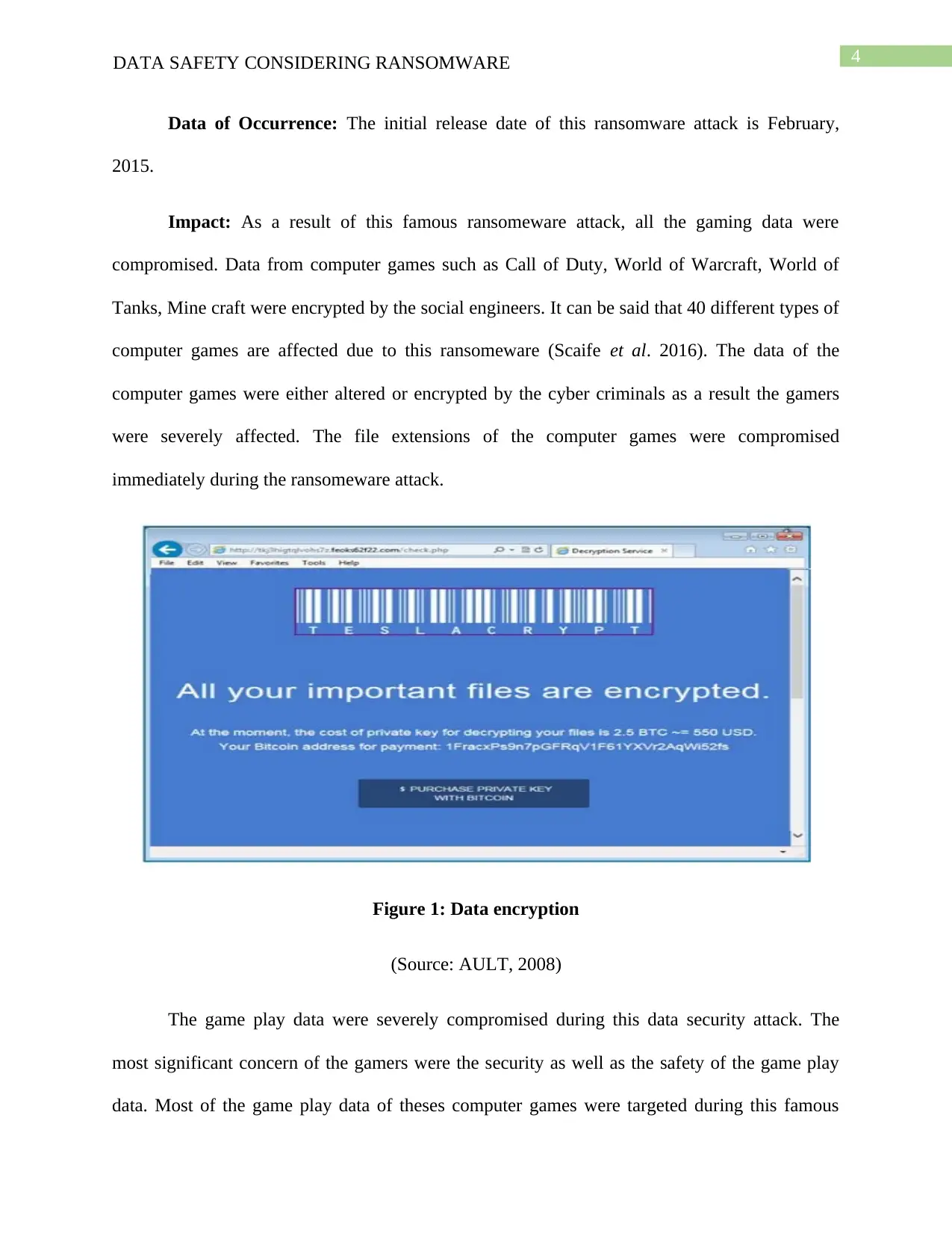
4DATA SAFETY CONSIDERING RANSOMWARE
Data of Occurrence: The initial release date of this ransomware attack is February,
2015.
Impact: As a result of this famous ransomeware attack, all the gaming data were
compromised. Data from computer games such as Call of Duty, World of Warcraft, World of
Tanks, Mine craft were encrypted by the social engineers. It can be said that 40 different types of
computer games are affected due to this ransomeware (Scaife et al. 2016). The data of the
computer games were either altered or encrypted by the cyber criminals as a result the gamers
were severely affected. The file extensions of the computer games were compromised
immediately during the ransomeware attack.
Figure 1: Data encryption
(Source: AULT, 2008)
The game play data were severely compromised during this data security attack. The
most significant concern of the gamers were the security as well as the safety of the game play
data. Most of the game play data of theses computer games were targeted during this famous
Data of Occurrence: The initial release date of this ransomware attack is February,
2015.
Impact: As a result of this famous ransomeware attack, all the gaming data were
compromised. Data from computer games such as Call of Duty, World of Warcraft, World of
Tanks, Mine craft were encrypted by the social engineers. It can be said that 40 different types of
computer games are affected due to this ransomeware (Scaife et al. 2016). The data of the
computer games were either altered or encrypted by the cyber criminals as a result the gamers
were severely affected. The file extensions of the computer games were compromised
immediately during the ransomeware attack.
Figure 1: Data encryption
(Source: AULT, 2008)
The game play data were severely compromised during this data security attack. The
most significant concern of the gamers were the security as well as the safety of the game play
data. Most of the game play data of theses computer games were targeted during this famous

5DATA SAFETY CONSIDERING RANSOMWARE
security attack (Georgiou et al. 2018). This ransomeware attack had a direct impact on the player
profiles and custom maps. The customized map of each of the games were altered during this
attack. Different aspects of the computer games were seriously altered which was a serious
concern for the computer gamers.
The hard drives and most of the connected devices of the computer gamers were also
significantly affected during this security attack. Different categories of data in the form of PDF
files, JPEG files, and Microsoft Word files are affected during this security attack (Formby,
Durbha and Beyah 2017). The form as well as the function of each of these files were changed
by the cybercriminals after they are encrypted. The social engineers who were involved in this
ransomware attack demanded a huge ransomware of $500 USD to decrypt the files they
encrypted during this security attack. This ransomeware attack were resolved when the social
engineers of this attack provide the Tesla-crypt decryption tool to the affected users.
Example 2: Simple Locker
Classification: It is defined as the type of android infection virus which had a direct
impact on the data of the android users. All the different categories of data which are accessed to
and from the android device were significant affected during this ransomware attack.
Platform of the attack: More than 150,000 android users were infected using this
ransomeware attack. The dodgy applications which are present in the Google Store were the
platform used by the scammers of this ransomeware. These infection rapidly spread across
Europe and North America (Baek et al. 2018). All the unprotected mobile devices which are
connected with the mobiles devices of the users were also infected by this android infection
virus.
security attack (Georgiou et al. 2018). This ransomeware attack had a direct impact on the player
profiles and custom maps. The customized map of each of the games were altered during this
attack. Different aspects of the computer games were seriously altered which was a serious
concern for the computer gamers.
The hard drives and most of the connected devices of the computer gamers were also
significantly affected during this security attack. Different categories of data in the form of PDF
files, JPEG files, and Microsoft Word files are affected during this security attack (Formby,
Durbha and Beyah 2017). The form as well as the function of each of these files were changed
by the cybercriminals after they are encrypted. The social engineers who were involved in this
ransomware attack demanded a huge ransomware of $500 USD to decrypt the files they
encrypted during this security attack. This ransomeware attack were resolved when the social
engineers of this attack provide the Tesla-crypt decryption tool to the affected users.
Example 2: Simple Locker
Classification: It is defined as the type of android infection virus which had a direct
impact on the data of the android users. All the different categories of data which are accessed to
and from the android device were significant affected during this ransomware attack.
Platform of the attack: More than 150,000 android users were infected using this
ransomeware attack. The dodgy applications which are present in the Google Store were the
platform used by the scammers of this ransomeware. These infection rapidly spread across
Europe and North America (Baek et al. 2018). All the unprotected mobile devices which are
connected with the mobiles devices of the users were also infected by this android infection
virus.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DATA SAFETY CONSIDERING RANSOMWARE
Figure 2: Encryption of files during the Simple Locker Ransomware attack
(Source: Thornton, Dworak and Manikas 2017)
Data of Occurrence: This ransomware attack occurred in the late 2015 in the Easter
Europe as well as in United States of America. The scammers of this ransomeware utilized the
security loopholes of the Android operating system. However, this ransomeware was first
detected on 4th of June.
Impact: All the data which are accessed from the mobile devices were severely
compromised during this ransomeware attack. As a result of this ransomeware attack it can be
said that this blocker attack were common only in the android phone users (Beyer, Birnbaum and
Zech 2018). All the payment gateways which were used in the android phones were
compromised during this ransomware attack.
Figure 2: Encryption of files during the Simple Locker Ransomware attack
(Source: Thornton, Dworak and Manikas 2017)
Data of Occurrence: This ransomware attack occurred in the late 2015 in the Easter
Europe as well as in United States of America. The scammers of this ransomeware utilized the
security loopholes of the Android operating system. However, this ransomeware was first
detected on 4th of June.
Impact: All the data which are accessed from the mobile devices were severely
compromised during this ransomeware attack. As a result of this ransomeware attack it can be
said that this blocker attack were common only in the android phone users (Beyer, Birnbaum and
Zech 2018). All the payment gateways which were used in the android phones were
compromised during this ransomware attack.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DATA SAFETY CONSIDERING RANSOMWARE
Figure 2: Infected SD card during this ransomware attack
(Source: Butler, 2017)
Most of the anti-malware problems were unable to secure the threats coming from this
ransomeware attack. This locker virus restricted the users of the Android phones to get access to
the sensitive information. All the memory devices which are connected with the Android
smartphones such as the SD cards were also affected during this rannsomware attack.
During this ransomeware attack, it was seen that the anti-ransomeware tools were could
not be installed in the Android devices. Google Corporation suggested that most of the users of
the Android phones must change their login credentials with strong alphanumeric passwords.
However, after this ransomware attack it can be recommended it can be said that the
Symantec security response can be very much important to address the threat coming from the
Figure 2: Infected SD card during this ransomware attack
(Source: Butler, 2017)
Most of the anti-malware problems were unable to secure the threats coming from this
ransomeware attack. This locker virus restricted the users of the Android phones to get access to
the sensitive information. All the memory devices which are connected with the Android
smartphones such as the SD cards were also affected during this rannsomware attack.
During this ransomeware attack, it was seen that the anti-ransomeware tools were could
not be installed in the Android devices. Google Corporation suggested that most of the users of
the Android phones must change their login credentials with strong alphanumeric passwords.
However, after this ransomware attack it can be recommended it can be said that the
Symantec security response can be very much important to address the threat coming from the

8DATA SAFETY CONSIDERING RANSOMWARE
Simple Locker. It can be said that disabling the auto play option in the Android phones can be
very much important to resolve the security loopholes of the Android phones. The file sharing
facility of the Android phones are very much important to address the threats of Simple Locker.
All the unnecessary services which are runs in the background of the Android applications must
be stopped in the first place in order to deal with the security threat of the Simple Locker (Butt et
al. 2019). The patch levels of the Android smart phones must be updated by the users of the
Android devices so that the entry of the Simple locker can be restricted. The email servers of the
Android smart phones must be regularly updated so that the harmful extensions of
the .vbs, .bat, .exe and .scr files.
The droid box and the android emulator can be very much important to address the
security risks coming from the Simple Locker Ransomware. The threats coming from the java
source codes can be significantly affected using the JD-GUI.
Example 3: Wanna Cry ransomeware attack
Classification: This ransomware attack was conducted with the help of deadly crypto
worms, mostly the Microsoft Windows Operating System were severely affected in this
ransomeware attack.
Platform of the attack: During this attack data were encrypted by the social engineers
and they asked huge payments in the form of bit coins from the infected users.
Data of Occurrence: This ransomeware attack occurred in May, 2017 throughout the
world. The duration of this ransomeware attack was about 4 days. The minimum demand of the
cybercriminals from the infected users were between $300-$600 USD. The attack began on 12th
of May, 2017 when the infection was spotted in the SMB port.
Simple Locker. It can be said that disabling the auto play option in the Android phones can be
very much important to resolve the security loopholes of the Android phones. The file sharing
facility of the Android phones are very much important to address the threats of Simple Locker.
All the unnecessary services which are runs in the background of the Android applications must
be stopped in the first place in order to deal with the security threat of the Simple Locker (Butt et
al. 2019). The patch levels of the Android smart phones must be updated by the users of the
Android devices so that the entry of the Simple locker can be restricted. The email servers of the
Android smart phones must be regularly updated so that the harmful extensions of
the .vbs, .bat, .exe and .scr files.
The droid box and the android emulator can be very much important to address the
security risks coming from the Simple Locker Ransomware. The threats coming from the java
source codes can be significantly affected using the JD-GUI.
Example 3: Wanna Cry ransomeware attack
Classification: This ransomware attack was conducted with the help of deadly crypto
worms, mostly the Microsoft Windows Operating System were severely affected in this
ransomeware attack.
Platform of the attack: During this attack data were encrypted by the social engineers
and they asked huge payments in the form of bit coins from the infected users.
Data of Occurrence: This ransomeware attack occurred in May, 2017 throughout the
world. The duration of this ransomeware attack was about 4 days. The minimum demand of the
cybercriminals from the infected users were between $300-$600 USD. The attack began on 12th
of May, 2017 when the infection was spotted in the SMB port.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DATA SAFETY CONSIDERING RANSOMWARE
Impact: Operating systems such as the Windows XP and the Windows Server 2003 are
the most affected Operating Systems during this ransomeware attack. More than 300000
computer systems were infected during this ransomeware attack across 150 nations all over the
world. Electronic devices such as the computers systems, MRI scanners (Basu and Nikam 2006).
Theatre equipment’s and blood storage refrigerates are most affected during this ransomeware
attack. One of the most affected countries of this ransomeware attack are India, Taiwan, Ukraine
and Russia.
Figure 4: Encryption procedure in ransomware
(Source: ur Rehman et al. 2018)
There are different categories of industries such as the hospital industry as well as the
manufacturing industries. However, based on the investigation it can be said that this
ransomeware threat had a low impact as compared with the other categories of ransomware.
Major manufacturing organizations such as the Nissan Motor Manufacturing organization
Impact: Operating systems such as the Windows XP and the Windows Server 2003 are
the most affected Operating Systems during this ransomeware attack. More than 300000
computer systems were infected during this ransomeware attack across 150 nations all over the
world. Electronic devices such as the computers systems, MRI scanners (Basu and Nikam 2006).
Theatre equipment’s and blood storage refrigerates are most affected during this ransomeware
attack. One of the most affected countries of this ransomeware attack are India, Taiwan, Ukraine
and Russia.
Figure 4: Encryption procedure in ransomware
(Source: ur Rehman et al. 2018)
There are different categories of industries such as the hospital industry as well as the
manufacturing industries. However, based on the investigation it can be said that this
ransomeware threat had a low impact as compared with the other categories of ransomware.
Major manufacturing organizations such as the Nissan Motor Manufacturing organization
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DATA SAFETY CONSIDERING RANSOMWARE
severely affected during this ransomware attack when their business data and the financial data
were encrypted by the social engineers (Cuzzocrea, Martinelli and Mercaldo 2018). This
ransomware attack had a great negative impact on the growth and productivity of each of these
affected industries in terms of financial loss and reputational loss.This ransomeware attack was
successfully addressed by Microsoft Corporation. The kill switch patch released by Microsoft
Corporation was very much important to resolve the issue of Ransomeware in most of the
Windows Operating system. The issue of the DNS sinkhole was also successfully addressed
using the security patch released by the Microsoft Windows.
Based on the above three examples of the three different types of ransomeware attack it
can be said that our data is not at all safe which are transmitted in a private network without any
sort of encryption. The business data which are circulated in the commercial organizations must
be transmitted using a secured platform which cannot be accessed by the social engineers (Dinu
2018). At the same time, it can be also said that some of the business organizations have very
faulty backup systems which is itself a very big concern regarding the reliability of the data. The
frequency of the backup must be done in a professional manner so that the cost associated with
the data storage can be minimized considerably. The location of the backups must not be falling
in the hands of the cyber criminals, at the same the location of the data backup must not be
exposed publicly. The safety and the security of the data must be understood by both the citizens
as well as the employees working in commercial organization. The detailed knowledge of data
security can be very much important to address any type of data security issues. The do’s and the
don’t during any kinds of cyber security attack can be also known to the users if they have a
detailed knowledge about the impact of the data security issues.
severely affected during this ransomware attack when their business data and the financial data
were encrypted by the social engineers (Cuzzocrea, Martinelli and Mercaldo 2018). This
ransomware attack had a great negative impact on the growth and productivity of each of these
affected industries in terms of financial loss and reputational loss.This ransomeware attack was
successfully addressed by Microsoft Corporation. The kill switch patch released by Microsoft
Corporation was very much important to resolve the issue of Ransomeware in most of the
Windows Operating system. The issue of the DNS sinkhole was also successfully addressed
using the security patch released by the Microsoft Windows.
Based on the above three examples of the three different types of ransomeware attack it
can be said that our data is not at all safe which are transmitted in a private network without any
sort of encryption. The business data which are circulated in the commercial organizations must
be transmitted using a secured platform which cannot be accessed by the social engineers (Dinu
2018). At the same time, it can be also said that some of the business organizations have very
faulty backup systems which is itself a very big concern regarding the reliability of the data. The
frequency of the backup must be done in a professional manner so that the cost associated with
the data storage can be minimized considerably. The location of the backups must not be falling
in the hands of the cyber criminals, at the same the location of the data backup must not be
exposed publicly. The safety and the security of the data must be understood by both the citizens
as well as the employees working in commercial organization. The detailed knowledge of data
security can be very much important to address any type of data security issues. The do’s and the
don’t during any kinds of cyber security attack can be also known to the users if they have a
detailed knowledge about the impact of the data security issues.

11DATA SAFETY CONSIDERING RANSOMWARE
Recommendations
There are different ways to ensure data security such as the followings:
Protection: Maintainable of the strong alphanumeric passwords can also be very much
important to deal with the data security threats coming from cyber security attacks such
as ransomeware.
Two factors authentication: The two factor authentication can be very much important
to address the data security issues which are faced in our society.
Controlling the privacy settings: The privacy settings of the organizational portals
should be very much strong in order to resolve the data security issues.
Keep your browser: The browsers which are used in most of the business organizations
as well as in our society must be secured from external threats such as the ransomware
using tools such as ad-blocker (Gilbert, 1992). Most of the pop-up applications is a
source of concern as it can the reason behind security issues such as the ransomware.
Installation of new updates: The security patches of the operating systems can also be
very much important to fix the bugs and the loopholes of the operating system which can
lead to security vulnerabilities such as ransomware.
Conclusion
The paper was very much important to understand the security challenges of the data
which are considered as an asset in most of the commercial organizations. The paper was also
very much important to understand that data security can be compromised from both inside or
outside business organizations. It can be be also determined that the International data protection
Recommendations
There are different ways to ensure data security such as the followings:
Protection: Maintainable of the strong alphanumeric passwords can also be very much
important to deal with the data security threats coming from cyber security attacks such
as ransomeware.
Two factors authentication: The two factor authentication can be very much important
to address the data security issues which are faced in our society.
Controlling the privacy settings: The privacy settings of the organizational portals
should be very much strong in order to resolve the data security issues.
Keep your browser: The browsers which are used in most of the business organizations
as well as in our society must be secured from external threats such as the ransomware
using tools such as ad-blocker (Gilbert, 1992). Most of the pop-up applications is a
source of concern as it can the reason behind security issues such as the ransomware.
Installation of new updates: The security patches of the operating systems can also be
very much important to fix the bugs and the loopholes of the operating system which can
lead to security vulnerabilities such as ransomware.
Conclusion
The paper was very much important to understand the security challenges of the data
which are considered as an asset in most of the commercial organizations. The paper was also
very much important to understand that data security can be compromised from both inside or
outside business organizations. It can be be also determined that the International data protection
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





