3LAL0908 - Research Report on Data Storage Security in Cloud
VerifiedAdded on 2023/06/09
|11
|2271
|115
Report
AI Summary
This research report delves into the critical aspects of data storage security within cloud computing environments. It addresses the increasing reliance on cloud services for data storage and the associated security challenges that organizations face. The report identifies key security threats, such as unauthorized access, collusion attacks, and malicious data modification, and explores various mitigation techniques. It further analyzes data from surveys and scholarly articles to assess the importance of cloud computing for data management and IT needs, as well as the measures taken by professionals to ensure data privacy. The research also examines secure data storage methods, including token correctness and error localization. The report concludes by emphasizing the significance of data storage security in cloud computing and highlighting the advantages and disadvantages of cloud data storage security, ultimately providing insights into securing organizational data in the cloud.

Running head: IT RESEARCH METHODOLOGY
Data Storage Security in Cloud Computing: Research Paper
Name of Student-
Name of University-
Author’s Note-
Data Storage Security in Cloud Computing: Research Paper
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RESEARCH METHODOLOGY
Topic: Data Storage Security in Cloud Computing
1. Abstract
Cloud computing is considered to be an emerging field because of the advantages that it
provides to the organizations. The use of cloud computing is increasing because of it high
performance, higher availability as well as low the cost of the storing data. The cloud provides
many service to the client. The main feature of the service providers of cloud includes data
storage. The service of cloud mainly provides storage of data to many companies which
produces huge amount of data each day. With all its advantages, there are many organizations as
well that do not implement the cloud technology because of the security that the cloud provide
for storing the data. Data storage of cloud computing needs to implement security policy and
protection against the weakness of data storage in the organizations. This research paper consists
of all the data storage security measures that cloud computing addresses and the ways to solve
those issues.
1.1 Introduction
According to Feng (2018), cloud computing is usually defined as new style for
computing which is scalable and virtualized resources are also provided by the service of cloud
over internet. The cloud computing transmits application software and the data base to large
number of data centers, where the administration of data as well as service is not totally trusted.
This imposes security challenges for the data storage in the organizations. The cloud storage
capacity is mainly focused in this research paper that includes improving the quality of service of
cloud computing. There are many effective as well as flexible technique for the management of
data storage in the organization. This research paper explains many encryption technique
Topic: Data Storage Security in Cloud Computing
1. Abstract
Cloud computing is considered to be an emerging field because of the advantages that it
provides to the organizations. The use of cloud computing is increasing because of it high
performance, higher availability as well as low the cost of the storing data. The cloud provides
many service to the client. The main feature of the service providers of cloud includes data
storage. The service of cloud mainly provides storage of data to many companies which
produces huge amount of data each day. With all its advantages, there are many organizations as
well that do not implement the cloud technology because of the security that the cloud provide
for storing the data. Data storage of cloud computing needs to implement security policy and
protection against the weakness of data storage in the organizations. This research paper consists
of all the data storage security measures that cloud computing addresses and the ways to solve
those issues.
1.1 Introduction
According to Feng (2018), cloud computing is usually defined as new style for
computing which is scalable and virtualized resources are also provided by the service of cloud
over internet. The cloud computing transmits application software and the data base to large
number of data centers, where the administration of data as well as service is not totally trusted.
This imposes security challenges for the data storage in the organizations. The cloud storage
capacity is mainly focused in this research paper that includes improving the quality of service of
cloud computing. There are many effective as well as flexible technique for the management of
data storage in the organization. This research paper explains many encryption technique

2IT RESEARCH METHODOLOGY
algorithm with authentication of coded data. There are many reasons for which the cloud
computing faces security threats. The security threat may come from unauthenticated person who
can attack some authorized file, avoids the collusion attacks, and attack of malicious data
modification.
1.2 Problem Statement
There are several trends that opens up in the era where cloud computing plays an
important role in most of the industrial sectors. The cloud computing technology is mainly a
development that is internet based and also uses the technology of computing in it. As there are
advantages as well as disadvantages of all technologies, the data storage technology of cloud
computing also serves the industries with advantages as well as disadvantages to work with (Ali,
Khan & Vasilakos, 2015). As cloud computing provides service over the internet, there may be
lot of issues in the internet while accessing the service of cloud computing.
Cloud computing plays the most important role for storing the data in an organization.
But, the problem states when security issue arises with the implementation of data storage in an
organization. All the data storage security issues of cloud computing and the ways to mitigate
them are described in this research paper. Being a cheaper as well as powerful processor, the
cloud computing is combine with Software as a Service (SaaS) architecture that transforms the
data centers of computing on a large scale. There always lies a problem of providing high quality
service to the customers with flexible connections of network. There are many companies that
provide cloud service to the companies. So, to provide the best service for the cloud is also an
important factor in the companies.
algorithm with authentication of coded data. There are many reasons for which the cloud
computing faces security threats. The security threat may come from unauthenticated person who
can attack some authorized file, avoids the collusion attacks, and attack of malicious data
modification.
1.2 Problem Statement
There are several trends that opens up in the era where cloud computing plays an
important role in most of the industrial sectors. The cloud computing technology is mainly a
development that is internet based and also uses the technology of computing in it. As there are
advantages as well as disadvantages of all technologies, the data storage technology of cloud
computing also serves the industries with advantages as well as disadvantages to work with (Ali,
Khan & Vasilakos, 2015). As cloud computing provides service over the internet, there may be
lot of issues in the internet while accessing the service of cloud computing.
Cloud computing plays the most important role for storing the data in an organization.
But, the problem states when security issue arises with the implementation of data storage in an
organization. All the data storage security issues of cloud computing and the ways to mitigate
them are described in this research paper. Being a cheaper as well as powerful processor, the
cloud computing is combine with Software as a Service (SaaS) architecture that transforms the
data centers of computing on a large scale. There always lies a problem of providing high quality
service to the customers with flexible connections of network. There are many companies that
provide cloud service to the companies. So, to provide the best service for the cloud is also an
important factor in the companies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RESEARCH METHODOLOGY
1.3 Scope and Objectives
The main aim of this research paper is to find out data storage security of cloud
computing the industrial sectors. As many companies cannot trust cloud computing because of
the security issues, all such security issues related to data storage are to be studied. To mitigate
those security issues, many measures are taken which are also studied in this research paper.
Cloud computing is one of the tremendous emerging technology in the internet technology sector
and helps to mitigate the problem of data storage in small as well as large organizations
(Sookhak et al., 2017). So, to ensure that all companies can use the technology of data storing of
cloud computing, this research paper mitigates the security issues related to data storage in cloud
computing.
1.4 Methodology
In the context the research study, the main reason for conducting this research review is
to analyze and study the effect of data storage security related to cloud computing (Rao &
Selvamani, 2015). The methodology that is used in this research paper is mixed research of
quantitative research. In this research paper, the study about the importance of cloud computing
is analyzed from different papers, and primary research are also conducted with survey
questions. The secondary quantitative data are collected from other journal article in which
quantitative data are studied by different authors.
This research is carried out mainly by forwarding questions like “How data storage of
cloud computing is important to the industries”. “Is the data storage security profitable for the
organization”. “What are the techniques that the company follows as a preventive method of data
storage cloud computing?” Another question that can be asked to the respondents is “How the
1.3 Scope and Objectives
The main aim of this research paper is to find out data storage security of cloud
computing the industrial sectors. As many companies cannot trust cloud computing because of
the security issues, all such security issues related to data storage are to be studied. To mitigate
those security issues, many measures are taken which are also studied in this research paper.
Cloud computing is one of the tremendous emerging technology in the internet technology sector
and helps to mitigate the problem of data storage in small as well as large organizations
(Sookhak et al., 2017). So, to ensure that all companies can use the technology of data storing of
cloud computing, this research paper mitigates the security issues related to data storage in cloud
computing.
1.4 Methodology
In the context the research study, the main reason for conducting this research review is
to analyze and study the effect of data storage security related to cloud computing (Rao &
Selvamani, 2015). The methodology that is used in this research paper is mixed research of
quantitative research. In this research paper, the study about the importance of cloud computing
is analyzed from different papers, and primary research are also conducted with survey
questions. The secondary quantitative data are collected from other journal article in which
quantitative data are studied by different authors.
This research is carried out mainly by forwarding questions like “How data storage of
cloud computing is important to the industries”. “Is the data storage security profitable for the
organization”. “What are the techniques that the company follows as a preventive method of data
storage cloud computing?” Another question that can be asked to the respondents is “How the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RESEARCH METHODOLOGY
cloud data storage helps to keep the data safe in the organization? ” There are many other similar
questions that are to be carried out while carrying the research study. There are many inquiries
that the respondents are asked regarding the cloud data storage in the organization.
2. Methods
INTERVIEWS
Interviews are organized by the researchers by conducting question surveys among the
respondents of some organization. Total 50 responses are to be taken from the researchers over
telephonic interview and the responses from them are analyzed. The response of the respondents
helps to analyze the study of data storage security in the industrial sectors.
ANALYZING DATA FROM OTHER SCHOLAR ARTICLES
The other secondary data that are carried out for this research paper consists of studying
other papers that are related to data storage security of cloud computing. Many scholarly articles
are taken for analyzing such data in which the authors have already carried out the research that
are very useful for solving the objective of this research paper.
cloud data storage helps to keep the data safe in the organization? ” There are many other similar
questions that are to be carried out while carrying the research study. There are many inquiries
that the respondents are asked regarding the cloud data storage in the organization.
2. Methods
INTERVIEWS
Interviews are organized by the researchers by conducting question surveys among the
respondents of some organization. Total 50 responses are to be taken from the researchers over
telephonic interview and the responses from them are analyzed. The response of the respondents
helps to analyze the study of data storage security in the industrial sectors.
ANALYZING DATA FROM OTHER SCHOLAR ARTICLES
The other secondary data that are carried out for this research paper consists of studying
other papers that are related to data storage security of cloud computing. Many scholarly articles
are taken for analyzing such data in which the authors have already carried out the research that
are very useful for solving the objective of this research paper.
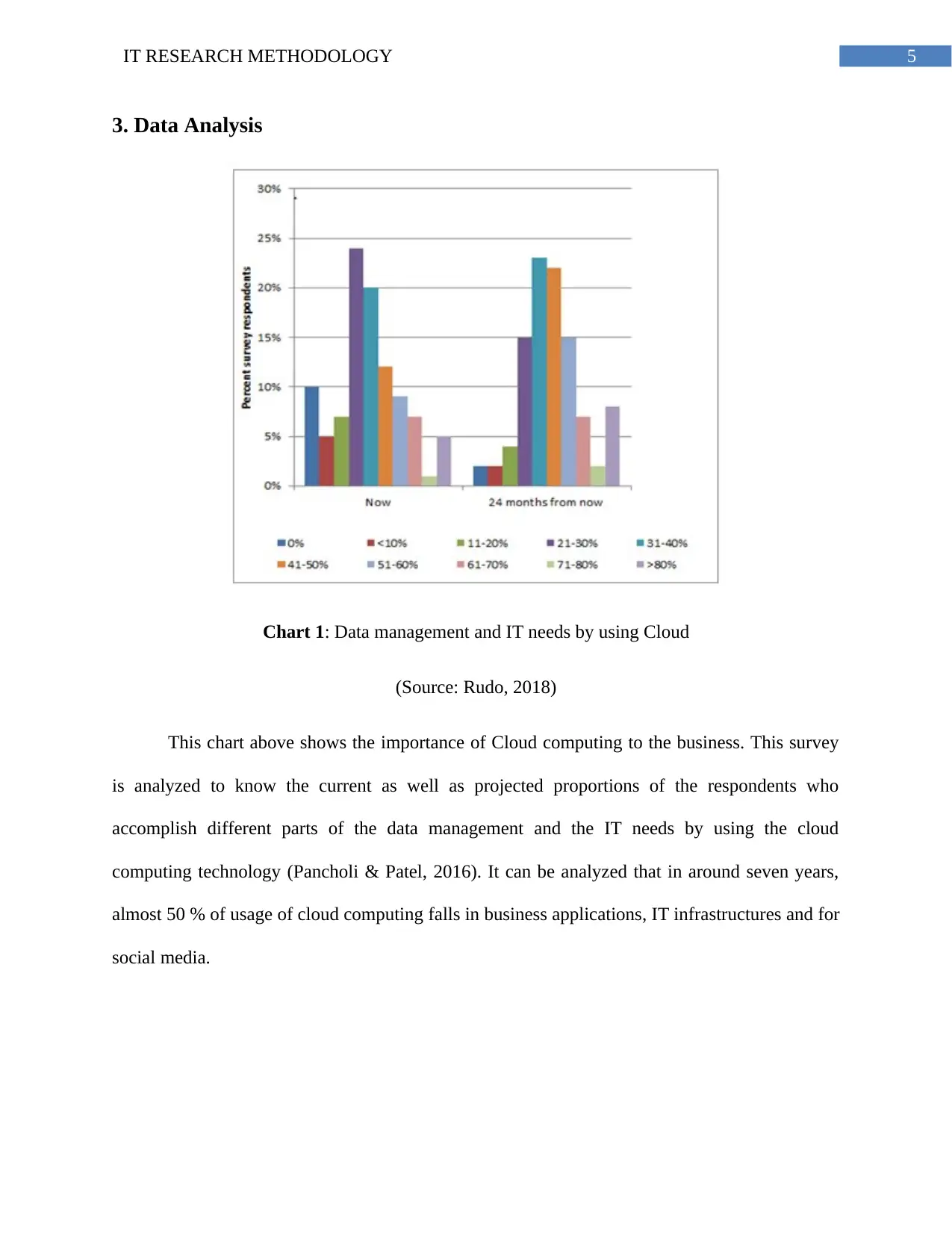
5IT RESEARCH METHODOLOGY
3. Data Analysis
Chart 1: Data management and IT needs by using Cloud
(Source: Rudo, 2018)
This chart above shows the importance of Cloud computing to the business. This survey
is analyzed to know the current as well as projected proportions of the respondents who
accomplish different parts of the data management and the IT needs by using the cloud
computing technology (Pancholi & Patel, 2016). It can be analyzed that in around seven years,
almost 50 % of usage of cloud computing falls in business applications, IT infrastructures and for
social media.
3. Data Analysis
Chart 1: Data management and IT needs by using Cloud
(Source: Rudo, 2018)
This chart above shows the importance of Cloud computing to the business. This survey
is analyzed to know the current as well as projected proportions of the respondents who
accomplish different parts of the data management and the IT needs by using the cloud
computing technology (Pancholi & Patel, 2016). It can be analyzed that in around seven years,
almost 50 % of usage of cloud computing falls in business applications, IT infrastructures and for
social media.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RESEARCH METHODOLOGY
Chart 2: Measures taken by professionals for ensuring data privacy of cloud computing
(Source: Rudo, 2018)
From this study, it can be analyzed that there still remains a large difference in the
importance of security that are associated with the cloud computing. About 59 percent of the
total respondents said that the policies of cloud computing has very less significant for their
choice of the cloud provider and 41 % of the respondents do not even care about the privacy
practice of the cloud providers (Manogaran, Thota & Kumar, 2016). From the chart it can also be
analyzed that 60 % of the respondents claims that the data storage of cloud computing is
protecting the sensitive data and the confidential data of their organizations.
4. Literature Review
4.1 Secure Data Storage in Cloud
As stated by Shimbre & Deshpande (2015), there are many ways by which data storage
can be made secured. Mainly include systems, the company stores all the data in data server that
Chart 2: Measures taken by professionals for ensuring data privacy of cloud computing
(Source: Rudo, 2018)
From this study, it can be analyzed that there still remains a large difference in the
importance of security that are associated with the cloud computing. About 59 percent of the
total respondents said that the policies of cloud computing has very less significant for their
choice of the cloud provider and 41 % of the respondents do not even care about the privacy
practice of the cloud providers (Manogaran, Thota & Kumar, 2016). From the chart it can also be
analyzed that 60 % of the respondents claims that the data storage of cloud computing is
protecting the sensitive data and the confidential data of their organizations.
4. Literature Review
4.1 Secure Data Storage in Cloud
As stated by Shimbre & Deshpande (2015), there are many ways by which data storage
can be made secured. Mainly include systems, the company stores all the data in data server that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RESEARCH METHODOLOGY
is remotely stored. So, the data that are to be stored should be correct and should be stored
securely. Even, sometimes some unauthorized person can change or modify the data, there is
need to maintain the correctness of the data (Rittinghouse & Ransome, 2016). The storage
system of cloud gives an effective as well as flexible scheme distribution with dynamic support
of data. The ways of securing the data storage system is described below:
4.1.1Token correctness
Using the pre-computed toke, the assurance of the correctness of data storage and the
error localization of data (Li et al., 2017). Before sharing file using the pre-computes, there are
many number of verification token that are generated and will ensure security for some block of
data in the cloud storage.
4.1.2 Correctness Verification and Error Localization
Error localization is the main requirement for errors that are eradicate in the storage
systems. There are many schemes that explicitly are not considered in the problem of error
localization.
5. Conclusion
With the help of cloud computing technology, the users of cloud uses different types of
devices that includes laptops, personal computers, smart phones as well as PDAs that access the
programs, platforms for application development and storage for accessing the services of cloud
computing (Wei et al., 2014). The cloud computing includes cost savings, easy scalability, and
high availability.
It can be concluded from this research paper is the importance of data storage security
cloud computing in organization. There are many advantages and disadvantages of cloud data
is remotely stored. So, the data that are to be stored should be correct and should be stored
securely. Even, sometimes some unauthorized person can change or modify the data, there is
need to maintain the correctness of the data (Rittinghouse & Ransome, 2016). The storage
system of cloud gives an effective as well as flexible scheme distribution with dynamic support
of data. The ways of securing the data storage system is described below:
4.1.1Token correctness
Using the pre-computed toke, the assurance of the correctness of data storage and the
error localization of data (Li et al., 2017). Before sharing file using the pre-computes, there are
many number of verification token that are generated and will ensure security for some block of
data in the cloud storage.
4.1.2 Correctness Verification and Error Localization
Error localization is the main requirement for errors that are eradicate in the storage
systems. There are many schemes that explicitly are not considered in the problem of error
localization.
5. Conclusion
With the help of cloud computing technology, the users of cloud uses different types of
devices that includes laptops, personal computers, smart phones as well as PDAs that access the
programs, platforms for application development and storage for accessing the services of cloud
computing (Wei et al., 2014). The cloud computing includes cost savings, easy scalability, and
high availability.
It can be concluded from this research paper is the importance of data storage security
cloud computing in organization. There are many advantages and disadvantages of cloud data
8IT RESEARCH METHODOLOGY
storage security. All such security issues of data storage of cloud computing is explained in this
research paper and the mitigation technique for solving the security issue of the data storage is
also explained in this research paper.
storage security. All such security issues of data storage of cloud computing is explained in this
research paper and the mitigation technique for solving the security issue of the data storage is
also explained in this research paper.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RESEARCH METHODOLOGY
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities and
challenges. Information sciences, 305, 357-383.
Feng, B., Ma, X., Guo, C., Shi, H., Fu, Z., & Qiu, T. (2016). An efficient protocol with
bidirectional verification for storage security in cloud computing. IEEE Access, 4, 7899-
7911.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015). The
rise of “big data” on cloud computing: Review and open research issues. Information
Systems, 47, 98-115.
Li, Y., Gai, K., Qiu, L., Qiu, M., & Zhao, H. (2017). Intelligent cryptography approach for
secure distributed big data storage in cloud computing. Information Sciences, 387, 103-
115.
Manogaran, G., Thota, C., & Kumar, M. V. (2016). MetaCloudDataStorage architecture for big
data security in cloud computing. Procedia Computer Science, 87, 128-133.
Pancholi, V. R., & Patel, B. P. (2016). Enhancement of cloud computing security with secure
data storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), 18-21.
Rao, R. V., & Selvamani, K. (2015). Data security challenges and its solutions in cloud
computing. Procedia Computer Science, 48, 204-209.
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation, management,
and security. CRC press.
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities and
challenges. Information sciences, 305, 357-383.
Feng, B., Ma, X., Guo, C., Shi, H., Fu, Z., & Qiu, T. (2016). An efficient protocol with
bidirectional verification for storage security in cloud computing. IEEE Access, 4, 7899-
7911.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015). The
rise of “big data” on cloud computing: Review and open research issues. Information
Systems, 47, 98-115.
Li, Y., Gai, K., Qiu, L., Qiu, M., & Zhao, H. (2017). Intelligent cryptography approach for
secure distributed big data storage in cloud computing. Information Sciences, 387, 103-
115.
Manogaran, G., Thota, C., & Kumar, M. V. (2016). MetaCloudDataStorage architecture for big
data security in cloud computing. Procedia Computer Science, 87, 128-133.
Pancholi, V. R., & Patel, B. P. (2016). Enhancement of cloud computing security with secure
data storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), 18-21.
Rao, R. V., & Selvamani, K. (2015). Data security challenges and its solutions in cloud
computing. Procedia Computer Science, 48, 204-209.
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation, management,
and security. CRC press.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RESEARCH METHODOLOGY
Rudo, P. (2018). Privacy and Data Security In The Cloud (Statistics) - Enterprise Features.
Retrieved from http://www.enterprisefeatures.com/privacy-and-data-security-in-the-
cloud-statistics/
Shimbre, N., & Deshpande, P. (2015, February). Enhancing distributed data storage security for
cloud computing using TPA and AES algorithm. In Computing Communication Control
and Automation (ICCUBEA), 2015 International Conference on (pp. 35-39). IEEE.
Sookhak, M., Gani, A., Khan, M. K., & Buyya, R. (2017). Dynamic remote data auditing for
securing big data storage in cloud computing. Information Sciences, 380, 101-116.
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security and
privacy for storage and computation in cloud computing. Information Sciences, 258, 371-
386.
Rudo, P. (2018). Privacy and Data Security In The Cloud (Statistics) - Enterprise Features.
Retrieved from http://www.enterprisefeatures.com/privacy-and-data-security-in-the-
cloud-statistics/
Shimbre, N., & Deshpande, P. (2015, February). Enhancing distributed data storage security for
cloud computing using TPA and AES algorithm. In Computing Communication Control
and Automation (ICCUBEA), 2015 International Conference on (pp. 35-39). IEEE.
Sookhak, M., Gani, A., Khan, M. K., & Buyya, R. (2017). Dynamic remote data auditing for
securing big data storage in cloud computing. Information Sciences, 380, 101-116.
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security and
privacy for storage and computation in cloud computing. Information Sciences, 258, 371-
386.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



