MSc Project Report: Managing Data Security Risks with PCI DSS Standard
VerifiedAdded on 2023/04/21
|79
|23010
|344
Report
AI Summary
This report provides an in-depth analysis of managing data security and risks in the context of the Payment Card Industry Data Security Standard (PCI DSS). It begins by highlighting the increasing reliance on card payments and the necessity for businesses to comply with PCI DSS to protect cardholder information. The report outlines the aims and objectives of researching data security and risks, focusing on understanding PCI DSS requirements and utilizing tools like Nmap, Wincap, and Wireshark to assess compliance. It delves into the 12 requirements of PCI DSS, covering building and maintaining a secure network, protecting cardholder data, implementing strong access control measures, frequently monitoring and testing networks, and maintaining an information security policy. The methodology section discusses data security issues and risks, followed by an implementation section that demonstrates the use of Nmap, Win Cap and Wire shark. The report emphasizes the importance of PCI DSS in preventing data breaches, avoiding financial penalties, and maintaining customer trust, ultimately contributing to a more secure payment ecosystem. The report concludes by reiterating the significance of proactive security measures and continuous monitoring to safeguard sensitive cardholder data.

RESEARCH PROPOSAL
TOPIC: MANAGING DATA SECURITY AND RISKS
CONSIDERING PCI DSS
Programme: MSc in Information Security and Digital Forensic
Year: 2018/2019
Term: B
Student ID: U1336039
Author: Michael Akubueze
Supervisor: Dr Shareeful Islam
TOPIC: MANAGING DATA SECURITY AND RISKS
CONSIDERING PCI DSS
Programme: MSc in Information Security and Digital Forensic
Year: 2018/2019
Term: B
Student ID: U1336039
Author: Michael Akubueze
Supervisor: Dr Shareeful Islam
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
A Card Payments have become a very common sight in every Business association and
organisation that a person comes across in day to day life. It becomes very convenient to the business
associations to fulfil their business aims as well easier for the customer to carry the transaction. These
associations permit the client utilizing different bank cards including charge and Visa for this reason.
In any case, such associations need to agree to the payment card industry (PCI) security standard
before incorporating bank card framework into the current business process. This proposition
examines the information security and dangers for the PCI. We consider the PCI standard to
comprehend the Requirements and utilize different instruments, for example, Nmap to assess the
similarity of the requirements. PCI was set up by these Banks’ or the companies of Credit Card
namely MasterCard, Visa, American Express, JCB and Discover. The name given to this association/
Consortium was Payment Card Industry Security Standards Council (PCI). The function of this
association was to set up Data Security Standards (PCI DSS). They expected the industry locals to
meet these conditions and terms. The PCI Security Standards Council issued direction on the most
proficient method to ensure card information when taking installments via phone. Some portion of this
direction was data on the best way to deal with phone brings utilizing voice over IP. The main reason
is that, there exists incredibly ease to eject the data of the cardholder from the VoIP approaches the
remote possibility that you approach the data stream. The most adored device of any person who
works with frameworks is Wire shark, a free and extremely astonishing resource. Wire shark enables
to viably get sort out data and to expel voice calls from that data. So, we choosing wire shark is best
tool to eject the data of the cardholder from the VoIP approaches the remote possibility that you
approach the data stream.
A Card Payments have become a very common sight in every Business association and
organisation that a person comes across in day to day life. It becomes very convenient to the business
associations to fulfil their business aims as well easier for the customer to carry the transaction. These
associations permit the client utilizing different bank cards including charge and Visa for this reason.
In any case, such associations need to agree to the payment card industry (PCI) security standard
before incorporating bank card framework into the current business process. This proposition
examines the information security and dangers for the PCI. We consider the PCI standard to
comprehend the Requirements and utilize different instruments, for example, Nmap to assess the
similarity of the requirements. PCI was set up by these Banks’ or the companies of Credit Card
namely MasterCard, Visa, American Express, JCB and Discover. The name given to this association/
Consortium was Payment Card Industry Security Standards Council (PCI). The function of this
association was to set up Data Security Standards (PCI DSS). They expected the industry locals to
meet these conditions and terms. The PCI Security Standards Council issued direction on the most
proficient method to ensure card information when taking installments via phone. Some portion of this
direction was data on the best way to deal with phone brings utilizing voice over IP. The main reason
is that, there exists incredibly ease to eject the data of the cardholder from the VoIP approaches the
remote possibility that you approach the data stream. The most adored device of any person who
works with frameworks is Wire shark, a free and extremely astonishing resource. Wire shark enables
to viably get sort out data and to expel voice calls from that data. So, we choosing wire shark is best
tool to eject the data of the cardholder from the VoIP approaches the remote possibility that you
approach the data stream.

Table of Contents
Chapter 1: Introduction.............................................................................................................................1
1.1 Requirement for Businesses to have a Payment Card...............................................................1
1.2 Understanding the term “PCI DSS”...........................................................................................2
1.3 Why it is Obligatory for the Business Organizations?..............................................................4
1.4 Research Aim and Objectives....................................................................................................5
1.5 Problem Domain and Challenges..............................................................................................6
1.6 Research Question.....................................................................................................................6
Chapter 2: Literature review.....................................................................................................................8
2.1 Payment Card Industry..............................................................................................................8
2.2 Control of Security...................................................................................................................12
2.2.1 Security threat or risks in PCI DSS..................................................................................18
2.3 Tools........................................................................................................................................19
2.3.1 NMAP...............................................................................................................................19
2.3.2 Wincap..............................................................................................................................21
2.3.3 Wireshark.........................................................................................................................22
Chapter 3: PCI DSS................................................................................................................................27
3.1 PCI DSS...................................................................................................................................27
Chapter 1: Introduction.............................................................................................................................1
1.1 Requirement for Businesses to have a Payment Card...............................................................1
1.2 Understanding the term “PCI DSS”...........................................................................................2
1.3 Why it is Obligatory for the Business Organizations?..............................................................4
1.4 Research Aim and Objectives....................................................................................................5
1.5 Problem Domain and Challenges..............................................................................................6
1.6 Research Question.....................................................................................................................6
Chapter 2: Literature review.....................................................................................................................8
2.1 Payment Card Industry..............................................................................................................8
2.2 Control of Security...................................................................................................................12
2.2.1 Security threat or risks in PCI DSS..................................................................................18
2.3 Tools........................................................................................................................................19
2.3.1 NMAP...............................................................................................................................19
2.3.2 Wincap..............................................................................................................................21
2.3.3 Wireshark.........................................................................................................................22
Chapter 3: PCI DSS................................................................................................................................27
3.1 PCI DSS...................................................................................................................................27
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3.1.1 Building and Maintaining a Secure Network...................................................................28
3.1.2 Protecting Cardholder’s Data...........................................................................................30
3.1.3 Implement Strong Access Control Measures...................................................................33
3.1.4 Frequently Monitoring and Testing Networks.................................................................36
3.1.5 Maintaining Information Security Policy.........................................................................38
Chapter 4: Methodology/approach.........................................................................................................41
4.1 PCI DSS Methodology............................................................................................................41
4.1.1 Data security issues..............................................................................................................42
4.1.2 Risks.....................................................................................................................................47
Chapter 5: Implementation.....................................................................................................................50
5.1 NMAP..................................................................................................................................54
5.2 Win Cap...............................................................................................................................60
5.3 Wire shark............................................................................................................................61
Conclusion..............................................................................................................................................64
References..............................................................................................................................................65
3.1.2 Protecting Cardholder’s Data...........................................................................................30
3.1.3 Implement Strong Access Control Measures...................................................................33
3.1.4 Frequently Monitoring and Testing Networks.................................................................36
3.1.5 Maintaining Information Security Policy.........................................................................38
Chapter 4: Methodology/approach.........................................................................................................41
4.1 PCI DSS Methodology............................................................................................................41
4.1.1 Data security issues..............................................................................................................42
4.1.2 Risks.....................................................................................................................................47
Chapter 5: Implementation.....................................................................................................................50
5.1 NMAP..................................................................................................................................54
5.2 Win Cap...............................................................................................................................60
5.3 Wire shark............................................................................................................................61
Conclusion..............................................................................................................................................64
References..............................................................................................................................................65
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Chapter 1: Introduction
1.1 Requirement for Businesses to have a Payment Card
The payment card industry commands to ensure cardholder information and counteract extortion.
Yet, numerous associations keep on attempting to accomplish consistence with PCI DSS (Payment
Card Industry Data Security Standard). Five noteworthy payment card organizations have figured the
standard to accommodate their individual projects into a solitary arrangement of Requirements.
Different updates with the latest variant 3.1 w.e.f April 2015 has since been issued by the PCI SSC
(PCI Security Standards Council). The consistence is frequently unquestionably increasingly costly,
mistake inclined and asset escalated, than would normally be appropriate. Despite the fact that, with its
12 Requirements and supporting guidance, the standard is more prescriptive than most government or
industry security orders. The normal expenses can reach past a huge number of dollars every year
relying upon your association's level dimension, given the push to physically gather and break down
log information, aggregate reports, and keep up and approve security controls and strategies through
wasteful work serious procedures. Strategies, for example, get to control, information security and
arrangement the executives are more diligently to keep up and hard to actualize, oversee and authorize
practically speaking. In the present powerful business conditions, consistence and security techniques
are resolute and too moderate to even consider responding. On the off chance that the controls are
physically and inadequately executed, it will be blunder inclined, exorbitant and really obstruct
business productivity without improving security significantly.To "simply complete it", Departments
and even people may evade approach. Because of this, real information ruptures have happened in
associations that were in fact PCI DSS agreeable (Bosworth, Kabay and Whyne, n.d.). An effective,
repeatable and practical security program that fulfils at both the dimensions of cardholder information
protection for which the standard was made and for their technical necessities of their PCI
commitments. Concentrating on the basic, yet tricky zones that contain a significant part of the core of
the necessities, the white paper clarifies the fundamentals of a PCI consistence program:
Protect from unapproved use cardholder information
1
1.1 Requirement for Businesses to have a Payment Card
The payment card industry commands to ensure cardholder information and counteract extortion.
Yet, numerous associations keep on attempting to accomplish consistence with PCI DSS (Payment
Card Industry Data Security Standard). Five noteworthy payment card organizations have figured the
standard to accommodate their individual projects into a solitary arrangement of Requirements.
Different updates with the latest variant 3.1 w.e.f April 2015 has since been issued by the PCI SSC
(PCI Security Standards Council). The consistence is frequently unquestionably increasingly costly,
mistake inclined and asset escalated, than would normally be appropriate. Despite the fact that, with its
12 Requirements and supporting guidance, the standard is more prescriptive than most government or
industry security orders. The normal expenses can reach past a huge number of dollars every year
relying upon your association's level dimension, given the push to physically gather and break down
log information, aggregate reports, and keep up and approve security controls and strategies through
wasteful work serious procedures. Strategies, for example, get to control, information security and
arrangement the executives are more diligently to keep up and hard to actualize, oversee and authorize
practically speaking. In the present powerful business conditions, consistence and security techniques
are resolute and too moderate to even consider responding. On the off chance that the controls are
physically and inadequately executed, it will be blunder inclined, exorbitant and really obstruct
business productivity without improving security significantly.To "simply complete it", Departments
and even people may evade approach. Because of this, real information ruptures have happened in
associations that were in fact PCI DSS agreeable (Bosworth, Kabay and Whyne, n.d.). An effective,
repeatable and practical security program that fulfils at both the dimensions of cardholder information
protection for which the standard was made and for their technical necessities of their PCI
commitments. Concentrating on the basic, yet tricky zones that contain a significant part of the core of
the necessities, the white paper clarifies the fundamentals of a PCI consistence program:
Protect from unapproved use cardholder information
1

Strong controls around advantaged clients and information get to
Centralized, computerized job based access control, approval, and verification to be actualized
Database action observing and framework and database examining to be given
1.2 Understanding the term “PCI DSS”
PCI DSS (Payment Card Industry Data Security Standard) is a standard association that
regulates the data customer’s Credit card data security, which enables the security and breach of trust.
The data has to be confidential and not to be misused by external forces and elements. American
Express, Discover, Visa and MasterCard came together to form this association and set the rules and
guidelines. They started this in 2004 and the industry soon followed these guidelines. The basic
guidelines and the notes for this Association are explained in brief as below (Solarwindsmsp.com,
2019):
Data of Cardholder’s (customers) has to be protected. This was the highest priority in this agenda.
This data should be encrypted and/or coded so that it cannot be breached by outsiders. These becomes
more paramount in today’s world where most of the transactions happen online and are exposed to the
outside world where it can be easily breached by anyone having access to the internet.
Advanced coding is required by the companies to avoid this type of breaching. Exposed
software’s used by the companies may be suspected for external malicious attacks and programs. Bugs
infused in the systems have to be flushed out using advanced and up-to-date software’s. The software
companies have to keep updating their software so that they stay updated with the latest viruses and
bugs that can creep into the system. Spyware, Malware, Phishing are some of the elements that can
affect the system and server (Chan, n.d.).
Client Data has to be kept up-to-date in the sense that passwords and pin numbers for the system
inputs have to be kept changing. This will prevent hackers and abusive programmers to attack the
system by cracking the passwords and pin numbers. Use of strong and layered Firewalls will help to
nullify these outside attacks and hackers from entering the system. Time to time update and thorough
checking including long scanning of the system for malicious viruses and bugs have to be taken
2
Centralized, computerized job based access control, approval, and verification to be actualized
Database action observing and framework and database examining to be given
1.2 Understanding the term “PCI DSS”
PCI DSS (Payment Card Industry Data Security Standard) is a standard association that
regulates the data customer’s Credit card data security, which enables the security and breach of trust.
The data has to be confidential and not to be misused by external forces and elements. American
Express, Discover, Visa and MasterCard came together to form this association and set the rules and
guidelines. They started this in 2004 and the industry soon followed these guidelines. The basic
guidelines and the notes for this Association are explained in brief as below (Solarwindsmsp.com,
2019):
Data of Cardholder’s (customers) has to be protected. This was the highest priority in this agenda.
This data should be encrypted and/or coded so that it cannot be breached by outsiders. These becomes
more paramount in today’s world where most of the transactions happen online and are exposed to the
outside world where it can be easily breached by anyone having access to the internet.
Advanced coding is required by the companies to avoid this type of breaching. Exposed
software’s used by the companies may be suspected for external malicious attacks and programs. Bugs
infused in the systems have to be flushed out using advanced and up-to-date software’s. The software
companies have to keep updating their software so that they stay updated with the latest viruses and
bugs that can creep into the system. Spyware, Malware, Phishing are some of the elements that can
affect the system and server (Chan, n.d.).
Client Data has to be kept up-to-date in the sense that passwords and pin numbers for the system
inputs have to be kept changing. This will prevent hackers and abusive programmers to attack the
system by cracking the passwords and pin numbers. Use of strong and layered Firewalls will help to
nullify these outside attacks and hackers from entering the system. Time to time update and thorough
checking including long scanning of the system for malicious viruses and bugs have to be taken
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
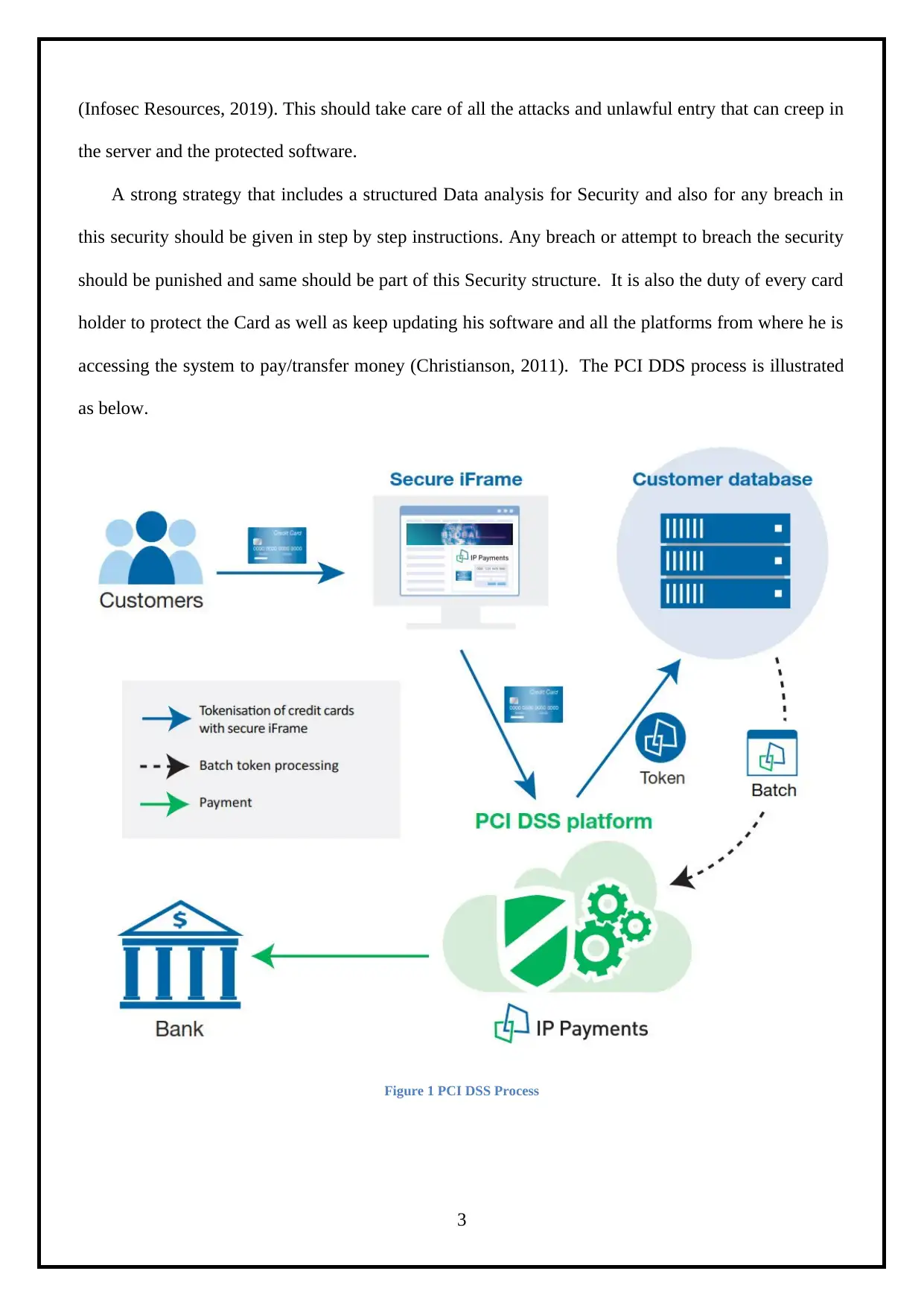
(Infosec Resources, 2019). This should take care of all the attacks and unlawful entry that can creep in
the server and the protected software.
A strong strategy that includes a structured Data analysis for Security and also for any breach in
this security should be given in step by step instructions. Any breach or attempt to breach the security
should be punished and same should be part of this Security structure. It is also the duty of every card
holder to protect the Card as well as keep updating his software and all the platforms from where he is
accessing the system to pay/transfer money (Christianson, 2011). The PCI DDS process is illustrated
as below.
Figure 1 PCI DSS Process
3
the server and the protected software.
A strong strategy that includes a structured Data analysis for Security and also for any breach in
this security should be given in step by step instructions. Any breach or attempt to breach the security
should be punished and same should be part of this Security structure. It is also the duty of every card
holder to protect the Card as well as keep updating his software and all the platforms from where he is
accessing the system to pay/transfer money (Christianson, 2011). The PCI DDS process is illustrated
as below.
Figure 1 PCI DSS Process
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards
designed which is used to ensure that ALL companies that accept process, store or transmit credit card
information maintain a secure environment.
1.3 Why it is Obligatory for the Business Organizations?
As Internet and data access become more and more easy in today’s wired world, people from
any part of the world can access the system and misuse the information that can be accessed by these
types of people. There is a vast increase in the number f transactions that take place on the internet and
it becomes difficult to track for the company to make sure that the system is maintained perfectly. But,
it has to. It is the responsibility and the duty of the company to make sure that the System is breach-
proof. As per, WPR (World Payments Report) 2018, the online transactions identifies that, the global
e-wallet market has been growing drastically, with the transaction volume estimated as a total of 41.8
billion, and it is nearly 8.6% of the global non-cash transactions. Here, the PCI DSS role becomes
very important and crucial. It is an umbrella body that sets the standards and rules for the companies
as to how the data by the customer should be used. It includes the privacy policy and the terms and
conditions as to how a customer’s Name, Address, Account information, Security ID etc. has to be
taken care of (Conti, 2007). They have set a guideline for the industry and the banking sector to follow
that is these confidential and high value data should not fall in the wrong hands. The organisation also
places responsibility and requires that the Card holders, Business firms, Customers, Online Traders,
Small Industries etc. and anyone using online network for monetary transactions should be aware of
all the possible ways in which there Data and information can be breached. They have time and again
emphasised the importance of these vital functions. And the serious results when they have been not
followed. The recursions for not following the advice may lead to losses and theft in unimaginable
ways (ComputerWeekly.com, 2019).
While organizations bear the weight of gathering multi-layered PCI DSS conventions, the
expense of consistence is far not exactly the option. Ramifications for resistance include:
4
designed which is used to ensure that ALL companies that accept process, store or transmit credit card
information maintain a secure environment.
1.3 Why it is Obligatory for the Business Organizations?
As Internet and data access become more and more easy in today’s wired world, people from
any part of the world can access the system and misuse the information that can be accessed by these
types of people. There is a vast increase in the number f transactions that take place on the internet and
it becomes difficult to track for the company to make sure that the system is maintained perfectly. But,
it has to. It is the responsibility and the duty of the company to make sure that the System is breach-
proof. As per, WPR (World Payments Report) 2018, the online transactions identifies that, the global
e-wallet market has been growing drastically, with the transaction volume estimated as a total of 41.8
billion, and it is nearly 8.6% of the global non-cash transactions. Here, the PCI DSS role becomes
very important and crucial. It is an umbrella body that sets the standards and rules for the companies
as to how the data by the customer should be used. It includes the privacy policy and the terms and
conditions as to how a customer’s Name, Address, Account information, Security ID etc. has to be
taken care of (Conti, 2007). They have set a guideline for the industry and the banking sector to follow
that is these confidential and high value data should not fall in the wrong hands. The organisation also
places responsibility and requires that the Card holders, Business firms, Customers, Online Traders,
Small Industries etc. and anyone using online network for monetary transactions should be aware of
all the possible ways in which there Data and information can be breached. They have time and again
emphasised the importance of these vital functions. And the serious results when they have been not
followed. The recursions for not following the advice may lead to losses and theft in unimaginable
ways (ComputerWeekly.com, 2019).
While organizations bear the weight of gathering multi-layered PCI DSS conventions, the
expense of consistence is far not exactly the option. Ramifications for resistance include:
4

Suspension of Merchant Accounts: Card suppliers, for example, Visa and MasterCard can
deny to work with associations who don't meet consistence Requirements and dealers,
decreasing your capacity to execute down to a money just premise.
Fines: Fine culpable traders up to $500,000 per security episode, and up to $50,000 every
day for consistently a business is working disregarding security measures by Banks and
MasterCard establishments may, at their watchfulness (Cole, Krutz and Conley, 2009).
Loss of Reputation, Customers and Business: When shoppers lose certainty, they change to
different administrations or brands, bringing about benefit loss.It takes a very long time to
construct a tenable notoriety however just a couple of minutes to demolish one, and lost
validity makes an interpretation of legitimately to an association's main concern.
Public Notification: Currently 38 states have laws necessitating that information ruptures
uncovering client data (counting cardholder information) be accounted for to clients
influenced.
Litigation: because of cardholder information being uncovered without approval,
association that neglect to verify cardholder data may confront common suits, harms and
other expensive legitimate procedures. 31 percent of respondents ended their association
with an association subsequent to accepting warning of a rupture of information security
according to an ongoing report by the Ponemon Institute.
1.4 Research Aim and Objectives
Main objective of this project is to research the managing data security and risks considering
PCI DSS. A Card Payments have become a very common sight in every Business association and
organisation that a person comes across in day to day life. It becomes very convenient to the business
associations to fulfil their business aims as well easier for the customer to carry the transaction. These
associations permit the client utilizing different bank cards including charge and Visa for this reason.
In any case, such associations need to agree to the payment card industry (PCI) security standard
before incorporating bank card framework into the current business process. This proposition
5
deny to work with associations who don't meet consistence Requirements and dealers,
decreasing your capacity to execute down to a money just premise.
Fines: Fine culpable traders up to $500,000 per security episode, and up to $50,000 every
day for consistently a business is working disregarding security measures by Banks and
MasterCard establishments may, at their watchfulness (Cole, Krutz and Conley, 2009).
Loss of Reputation, Customers and Business: When shoppers lose certainty, they change to
different administrations or brands, bringing about benefit loss.It takes a very long time to
construct a tenable notoriety however just a couple of minutes to demolish one, and lost
validity makes an interpretation of legitimately to an association's main concern.
Public Notification: Currently 38 states have laws necessitating that information ruptures
uncovering client data (counting cardholder information) be accounted for to clients
influenced.
Litigation: because of cardholder information being uncovered without approval,
association that neglect to verify cardholder data may confront common suits, harms and
other expensive legitimate procedures. 31 percent of respondents ended their association
with an association subsequent to accepting warning of a rupture of information security
according to an ongoing report by the Ponemon Institute.
1.4 Research Aim and Objectives
Main objective of this project is to research the managing data security and risks considering
PCI DSS. A Card Payments have become a very common sight in every Business association and
organisation that a person comes across in day to day life. It becomes very convenient to the business
associations to fulfil their business aims as well easier for the customer to carry the transaction. These
associations permit the client utilizing different bank cards including charge and Visa for this reason.
In any case, such associations need to agree to the payment card industry (PCI) security standard
before incorporating bank card framework into the current business process. This proposition
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

examines the information security and dangers for the PCI. We consider the PCI standard to
comprehend the Requirements and utilize different instruments, for example, Nmap to assess the
similarity of the requirements. The name given to this association/ Consortium was Payment Card
Industry Security Standards Council (PCI). The function of this association was to set up Data
Security Standards (PCI DSS). Data of Cardholder’s has to be protected. This was the highest priority
in this agenda. This data should be encrypted and/or coded so that it cannot be breached by outsiders.
These becomes more paramount in today’s world where most of the transactions happen online and
are exposed to the outside world where it can be easily breached by anyone having access to the
internet.
1.5 Problem Domain and Challenges
The intentions of each were roughly similar: to create an additional level of protection for card
issuers by ensuring that merchants meet minimum levels of security when they store, process, and
transmit cardholder data. To cater out the interoperability problems among the existing standards, the
combined effort made by the principal credit card organizations resulted in the release of version 1.0
of PCI DSS in December 2004. PCI DSS has been implemented and followed across the globe. All
companies that process transmit, or store payment card data are required to maintain compliance with
the PCI DSS security standard to ensure the protection of cardholder data and avoid fraud. Achieving
PCI DSS compliance should not be viewed as an insurmountable challenge, but dedicated attention is
needed to the processes involved in its validation.
Challenges
All requirements are Mandatory
Competency Gap
Correct Scope Definition
There is a lot of organizational pressure involved in certification
6
comprehend the Requirements and utilize different instruments, for example, Nmap to assess the
similarity of the requirements. The name given to this association/ Consortium was Payment Card
Industry Security Standards Council (PCI). The function of this association was to set up Data
Security Standards (PCI DSS). Data of Cardholder’s has to be protected. This was the highest priority
in this agenda. This data should be encrypted and/or coded so that it cannot be breached by outsiders.
These becomes more paramount in today’s world where most of the transactions happen online and
are exposed to the outside world where it can be easily breached by anyone having access to the
internet.
1.5 Problem Domain and Challenges
The intentions of each were roughly similar: to create an additional level of protection for card
issuers by ensuring that merchants meet minimum levels of security when they store, process, and
transmit cardholder data. To cater out the interoperability problems among the existing standards, the
combined effort made by the principal credit card organizations resulted in the release of version 1.0
of PCI DSS in December 2004. PCI DSS has been implemented and followed across the globe. All
companies that process transmit, or store payment card data are required to maintain compliance with
the PCI DSS security standard to ensure the protection of cardholder data and avoid fraud. Achieving
PCI DSS compliance should not be viewed as an insurmountable challenge, but dedicated attention is
needed to the processes involved in its validation.
Challenges
All requirements are Mandatory
Competency Gap
Correct Scope Definition
There is a lot of organizational pressure involved in certification
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.6 Research Question
The payment card industry commands to ensure cardholder information and counteract
extortion. Yet, numerous associations keep on attempting to accomplish consistence with PCI DSS
(Payment Card Industry Data Security Standard). Five noteworthy payment card organizations have
figured the standard to accommodate their individual projects into a solitary arrangement of
Requirements. Despite the ongoing advances in point-of-sale systems and technologies, data breaches
remain a very real threat to the average small and medium sized business (SMB). That’s because SMB
owners often place their full trust in the technology solution to protect them. In reality, all businesses
must understand and adhere to the PCI Data Security Standard in order to be fully secure.
The Procedure for storing Data of Customers and how it is kept Secured?
How to maintain the PCI DSS?
How to Build and Maintaining Secure Network and Systems?
How to Build and Maintain a Secure Network?
What are the risks in PCI DSS?
What are the privacy concerns for PCI DSS?
7
The payment card industry commands to ensure cardholder information and counteract
extortion. Yet, numerous associations keep on attempting to accomplish consistence with PCI DSS
(Payment Card Industry Data Security Standard). Five noteworthy payment card organizations have
figured the standard to accommodate their individual projects into a solitary arrangement of
Requirements. Despite the ongoing advances in point-of-sale systems and technologies, data breaches
remain a very real threat to the average small and medium sized business (SMB). That’s because SMB
owners often place their full trust in the technology solution to protect them. In reality, all businesses
must understand and adhere to the PCI Data Security Standard in order to be fully secure.
The Procedure for storing Data of Customers and how it is kept Secured?
How to maintain the PCI DSS?
How to Build and Maintaining Secure Network and Systems?
How to Build and Maintain a Secure Network?
What are the risks in PCI DSS?
What are the privacy concerns for PCI DSS?
7

Chapter 2: Literature review
2.1 Payment Card Industry
One of the most important tools in the hands of the Customers, Banks, Organisations and
Industries in general is the use of update software’s and Anti-Malwares. Use of highly layered and
highly secured Firewall will be the first barrier against the viruses, bugs, and crack codes for
protecting the vital and confidential reports and data (Marsella, 2019). Hence for all these security
related issues, PCI DSS has come up with standard procedures and guidelines which help in protecting
the online system, servers and all the platforms that are exposed to the internet. WPA/WPA2 is one
such example where wired protection keys are used to detect any activity in the framework which is
susceptible in nature (Baxter, 2014).
Twelve necessities for consistence indicated by The PCI Data Security Standard, composed into
six intelligently related gatherings called "control targets". The six gatherings are
(Entrustdatacard.com, 2019),
Maintaining the Information Security Policy.
Maintaining the Program related to Vulnerability Management.
Building and Maintaining Secure Network and Systems
Implementing measures that are strong for controlling the access.
Protect Cardholder Data
Regularly Monitor and Test Networks
The “12 Abnormal” state Requirements have not changed since the commencement of the standard but
rather every variant of PCI DSS has isolated these 6 necessities into various sub-necessities in an
unexpected way. Every Requirement/sub-Requirement is moreover expounded into three areas.
8
2.1 Payment Card Industry
One of the most important tools in the hands of the Customers, Banks, Organisations and
Industries in general is the use of update software’s and Anti-Malwares. Use of highly layered and
highly secured Firewall will be the first barrier against the viruses, bugs, and crack codes for
protecting the vital and confidential reports and data (Marsella, 2019). Hence for all these security
related issues, PCI DSS has come up with standard procedures and guidelines which help in protecting
the online system, servers and all the platforms that are exposed to the internet. WPA/WPA2 is one
such example where wired protection keys are used to detect any activity in the framework which is
susceptible in nature (Baxter, 2014).
Twelve necessities for consistence indicated by The PCI Data Security Standard, composed into
six intelligently related gatherings called "control targets". The six gatherings are
(Entrustdatacard.com, 2019),
Maintaining the Information Security Policy.
Maintaining the Program related to Vulnerability Management.
Building and Maintaining Secure Network and Systems
Implementing measures that are strong for controlling the access.
Protect Cardholder Data
Regularly Monitor and Test Networks
The “12 Abnormal” state Requirements have not changed since the commencement of the standard but
rather every variant of PCI DSS has isolated these 6 necessities into various sub-necessities in an
unexpected way. Every Requirement/sub-Requirement is moreover expounded into three areas.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 79
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

