Analysis of Data as a Service (DaaS) Cloud Offering Research Report
VerifiedAdded on 2023/01/05
|13
|633
|60
Report
AI Summary
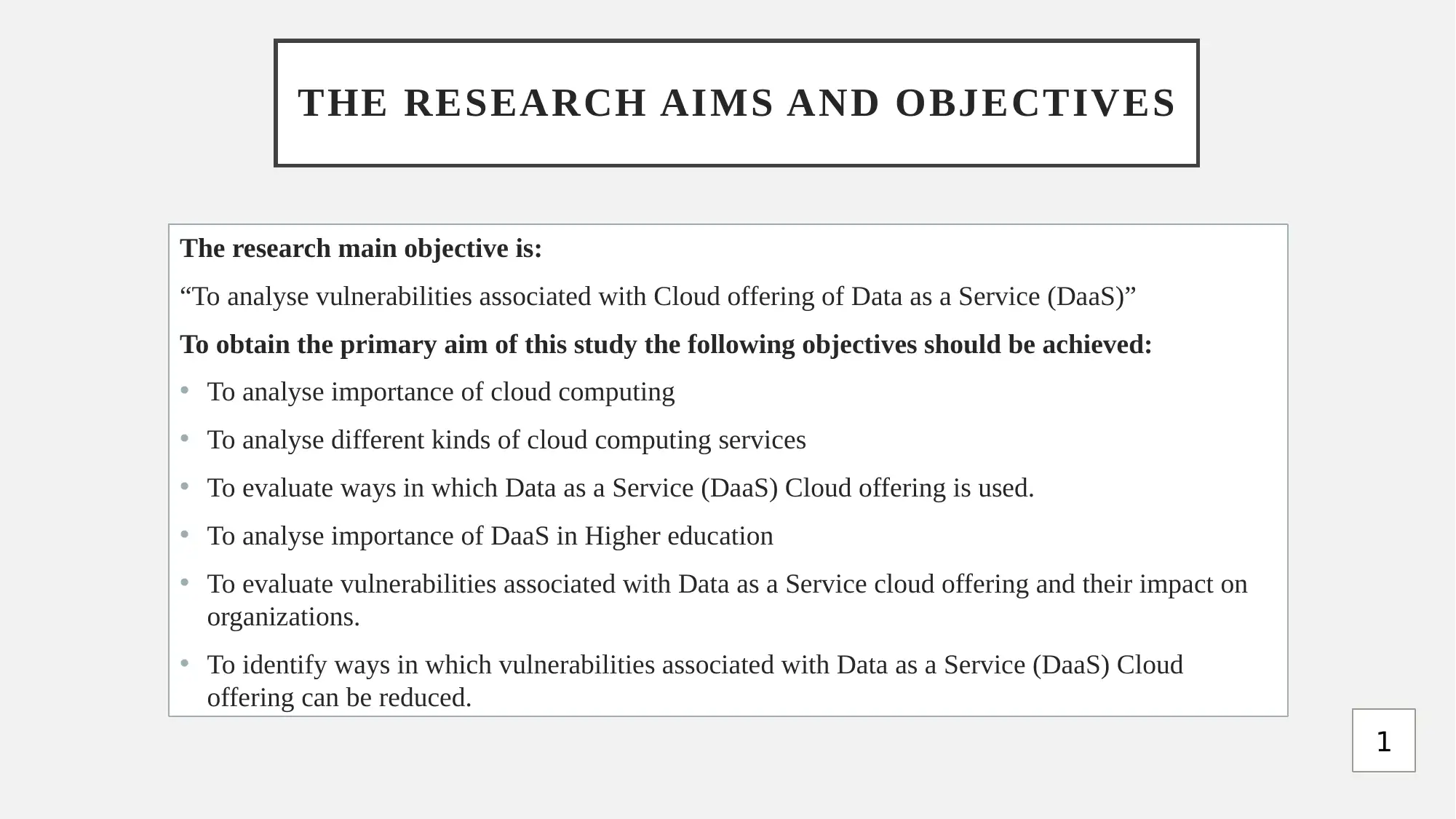
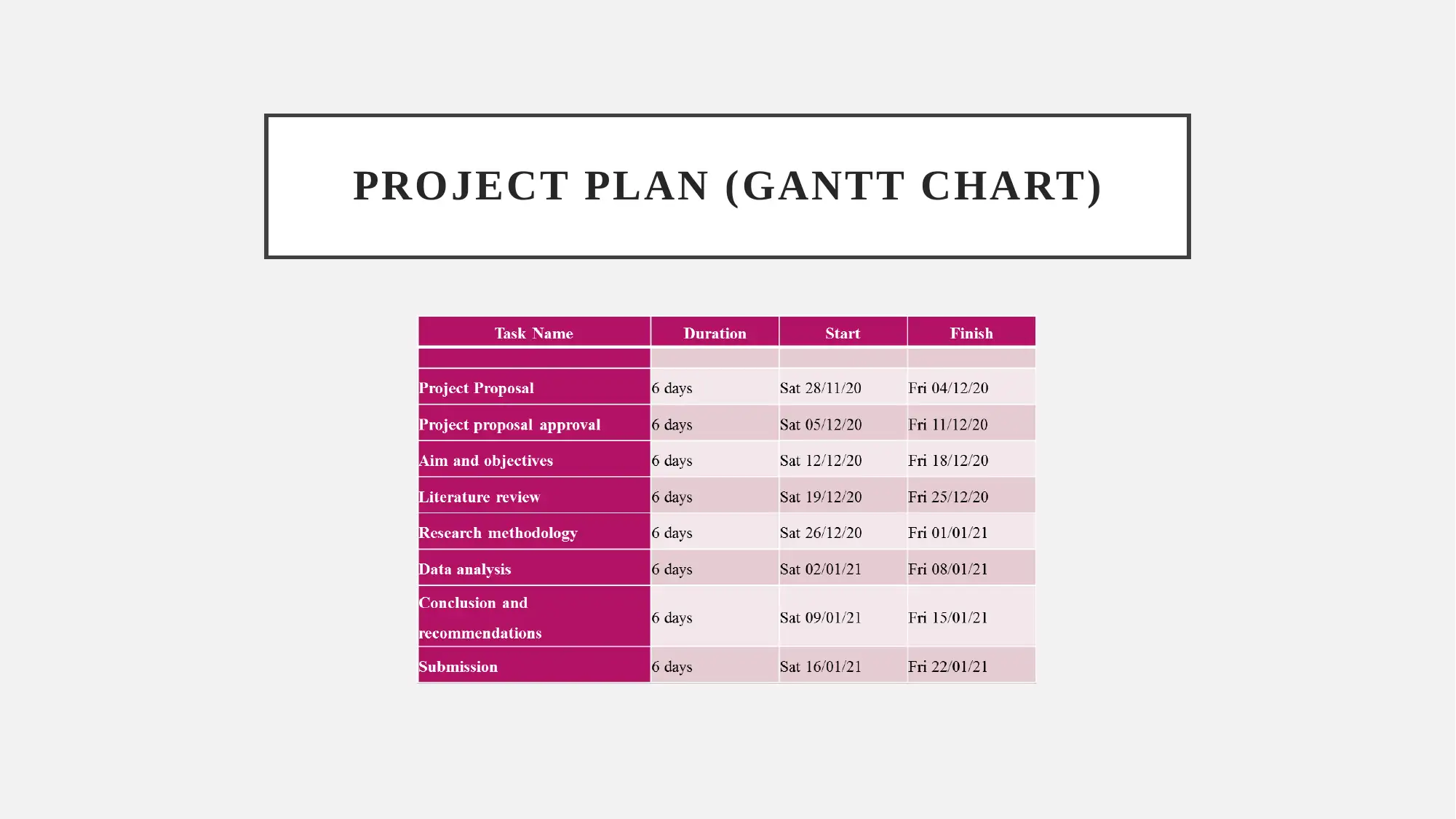
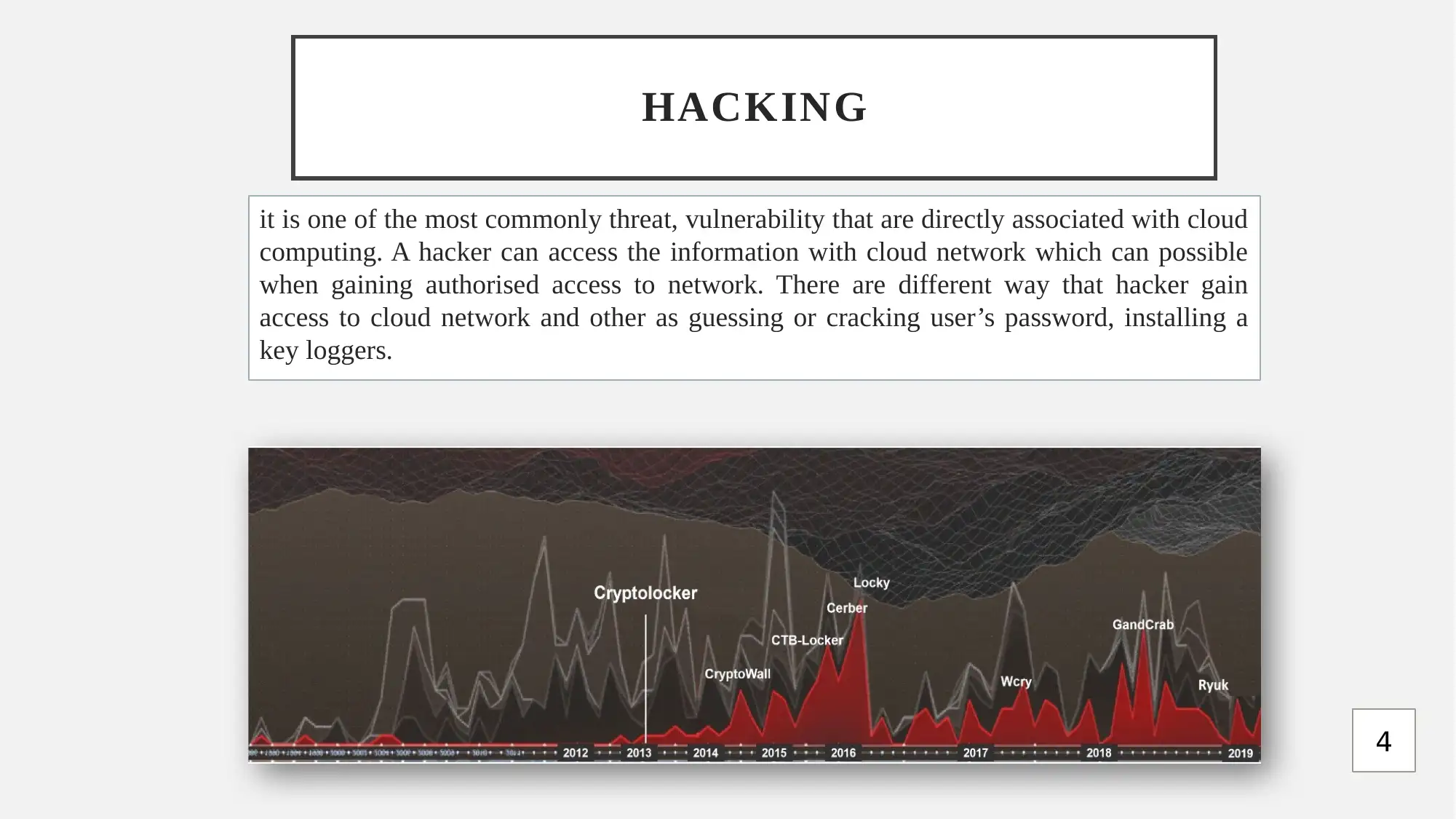
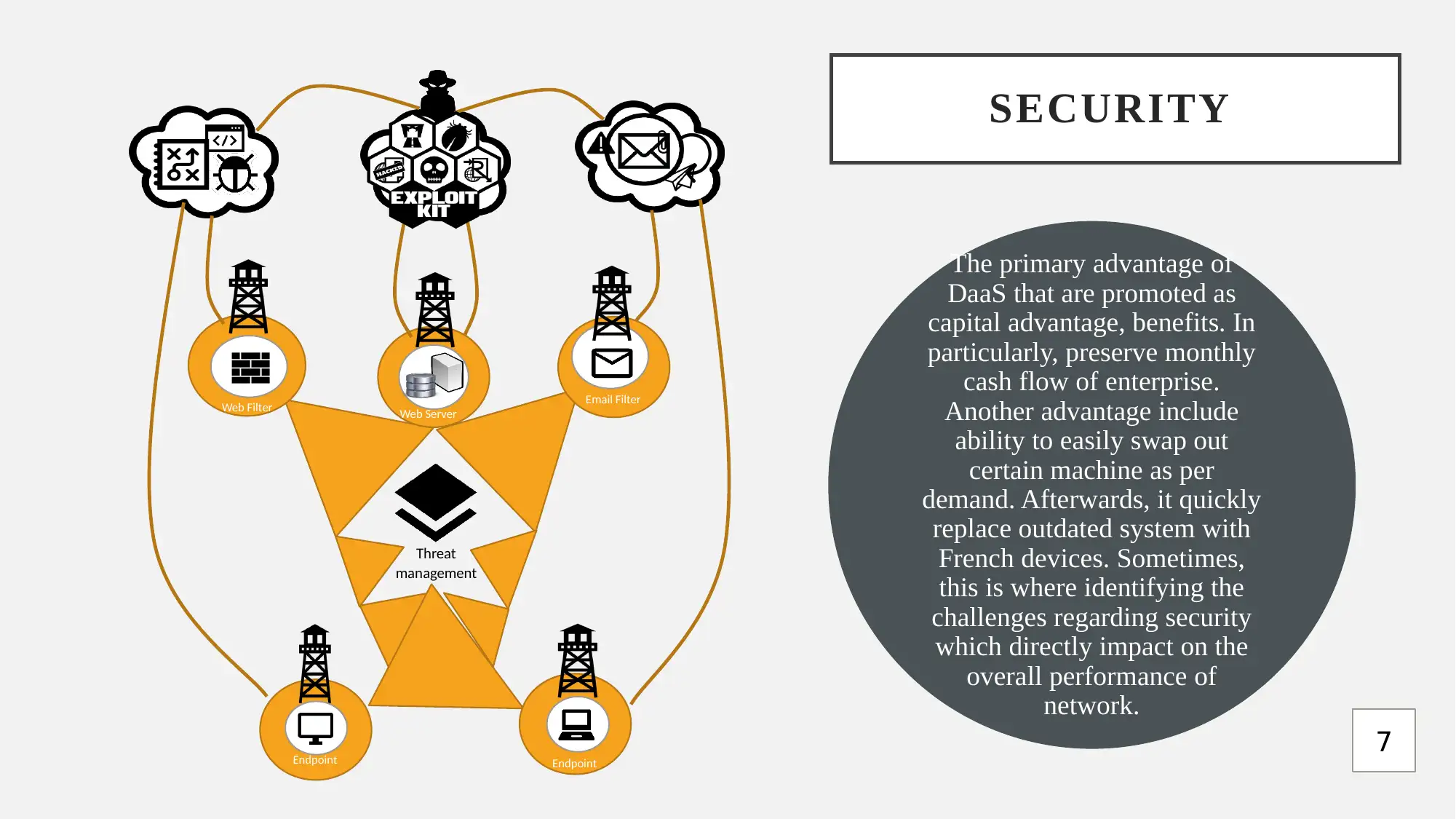
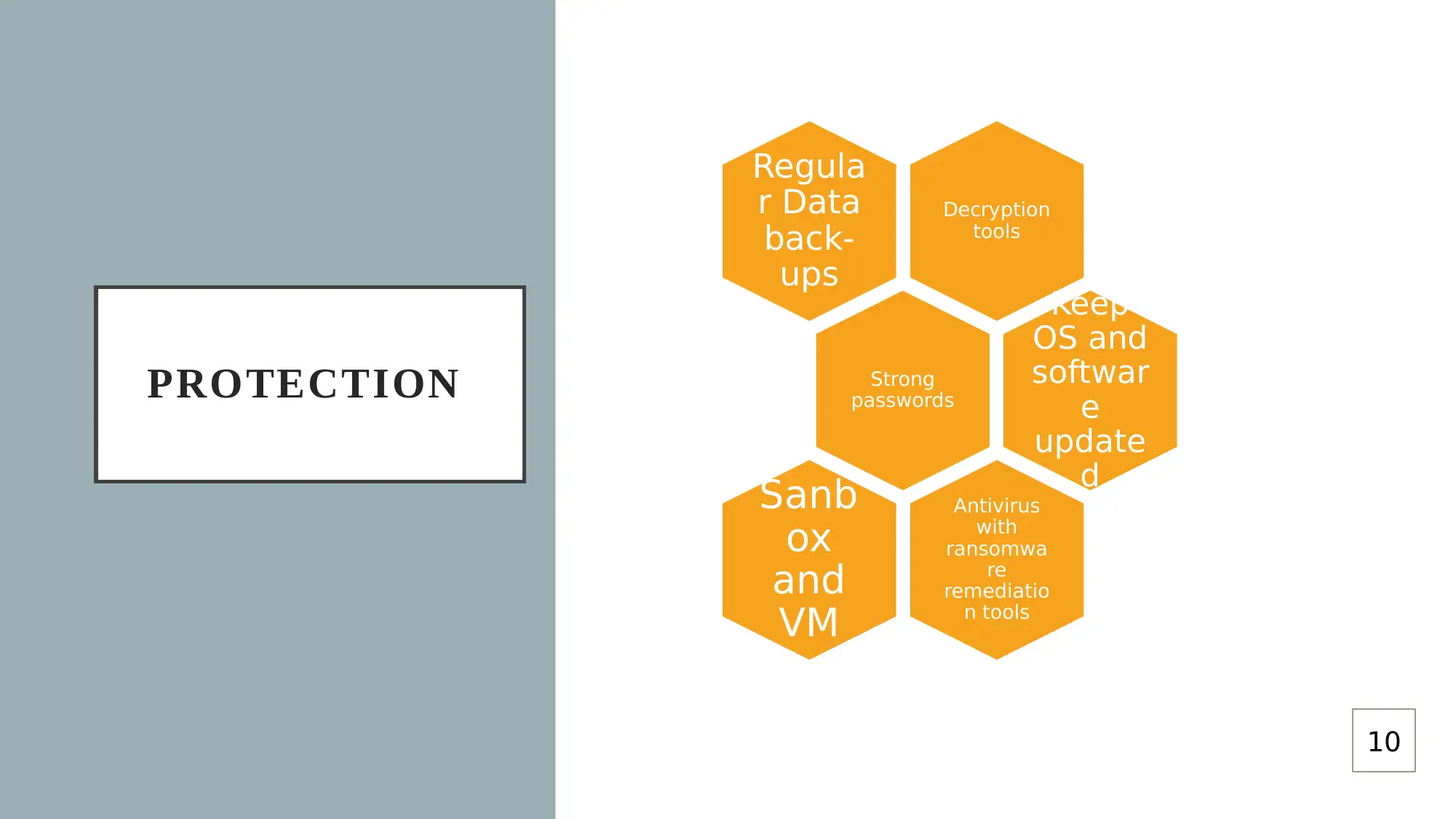
This report provides a comprehensive analysis of Data as a Service (DaaS) cloud offerings, focusing on research aims, objectives, and associated vulnerabilities. It begins by outlining the research's primary objective: to analyze vulnerabilities in DaaS cloud offerings. The report details the research methodology, including ethical considerations related to data protection and the use of secondary data. A Gantt chart outlines the project plan, and the report identifies hacking as a primary threat and vulnerability in cloud computing. The report also proposes a framework for managing DaaS applications, including steps for data finding, storing, processing, and moving. It highlights the advantages of DaaS, such as cost savings and scalability, while addressing security challenges. The report also recommends measures for data protection, including regular backups, strong passwords, and up-to-date software. The report concludes with a list of references.
1 out of 13











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)