Analysis of MakeBelieve Database Management System Report and Security
VerifiedAdded on 2019/09/20
|15
|2284
|327
Report
AI Summary
This report provides a comprehensive overview of Database Management Systems (DBMS), focusing on the context of the fictional company, MakeBelieve. It begins with an introduction to DBMS, defining its role in managing and creating databases, and highlighting popular systems like PostgreSQL and MySQL. The report then details the components of a DBMS, including data, hardware, software, and users. It explores the importance of data security, outlining various threats such as SQL injection, malware, and DB misconfigurations. The report also discusses security measures, including authentication, authorization, and the CIA triad (confidentiality, integrity, and availability). It further analyzes database vulnerabilities and countermeasures, such as excessive privilege abuse, and presents real-world examples like CVE entries. The report concludes by emphasizing the need for a robust security policy, the significance of data loss prevention, and the importance of understanding database administration within the context of DevOps to safeguard MakeBelieve's data.
Database Management
Introduction
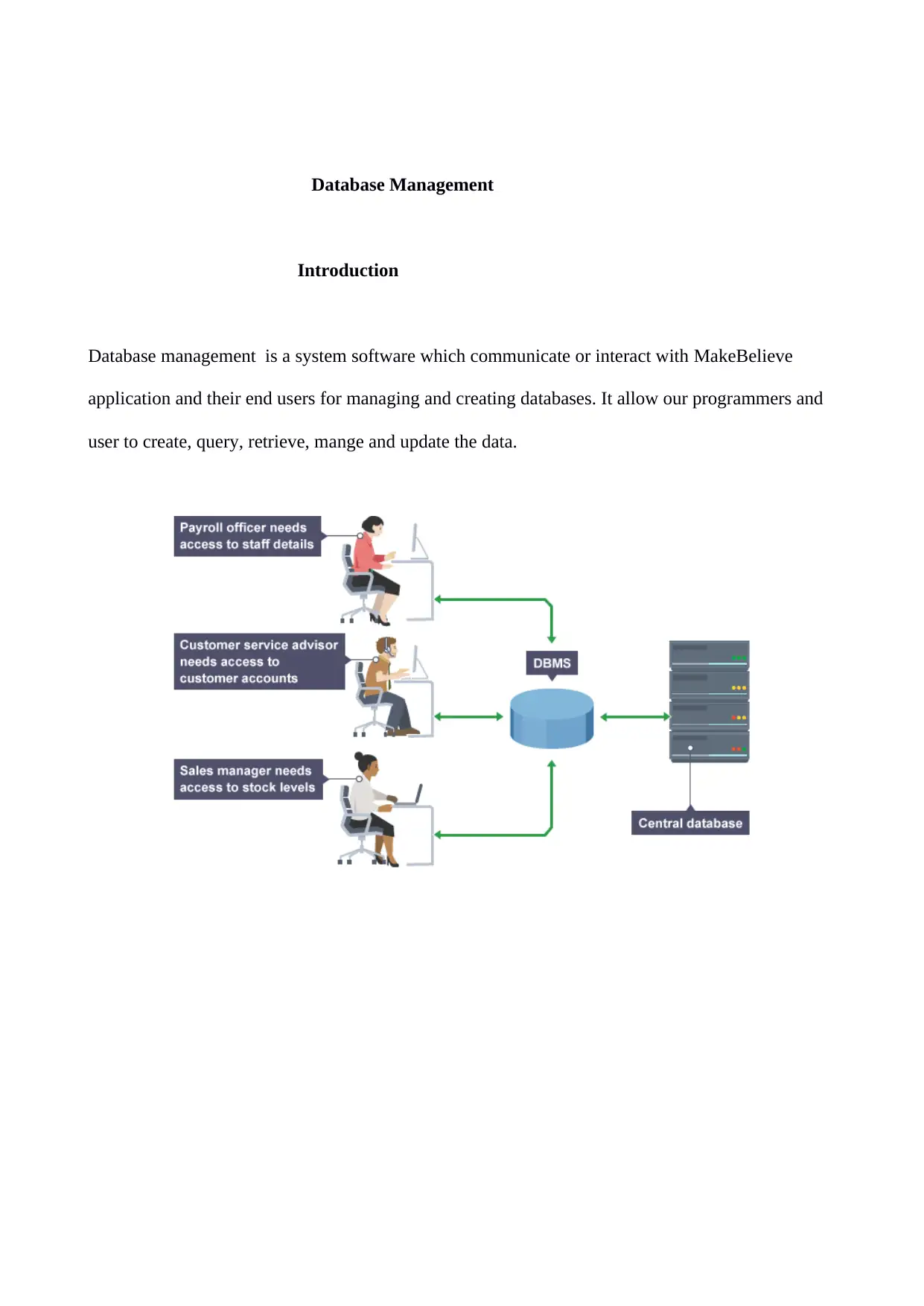
Database management is a system software which communicate or interact with MakeBelieve
application and their end users for managing and creating databases. It allow our programmers and
user to create, query, retrieve, mange and update the data.
Introduction
Database management is a system software which communicate or interact with MakeBelieve
application and their end users for managing and creating databases. It allow our programmers and
user to create, query, retrieve, mange and update the data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
https://goo.gl/images/sU3AWa
As we know that data is a collection of facts and information which is totally unorganized.
Nowadays very popular DBMS which used by many companies are postgreSQL, MongoDB,
MYSQL and Microsoft Sql Server. User data and information are processed through our
application programs by different users. MakeBelieve Database management system provides
condition which is very efficient and convenient in retrieving and storing the data. In this we
converting the facts in to a meaningful conversations. (Ramakrishnan & Gehrke, 2000)
As we know that data is a collection of facts and information which is totally unorganized.
Nowadays very popular DBMS which used by many companies are postgreSQL, MongoDB,
MYSQL and Microsoft Sql Server. User data and information are processed through our
application programs by different users. MakeBelieve Database management system provides
condition which is very efficient and convenient in retrieving and storing the data. In this we
converting the facts in to a meaningful conversations. (Ramakrishnan & Gehrke, 2000)

In MakeBelieve, database administrator controlled and manage the databases throughout our system
by updating, creating and modifying while ensuring the integrity of the data. Our Database mainly
contains the data of customers and services. The main purpose of MakeBelieve business process
mapping is to help in compare and measure our whole organization objective to make sure that
every functions are match with MakeBelieve capabilities and values. The major steps consists in
mapping MakeBelieve business functions are identification process, gathering of information,
covert facts in to process map, work using map(analysis) and manage process. To know the
information requirements of our organisation it is very important to study the business function.
(Dunn & Kelbie, 1997)
Components Of Database
MakeBelieve DBMS have many components, every one of them performing their specific task in
the database management. But it is mainly consist of four components :
a) Data b) Hardware c) Software d) users
Each one of these components make an effective database system.
by updating, creating and modifying while ensuring the integrity of the data. Our Database mainly
contains the data of customers and services. The main purpose of MakeBelieve business process
mapping is to help in compare and measure our whole organization objective to make sure that
every functions are match with MakeBelieve capabilities and values. The major steps consists in
mapping MakeBelieve business functions are identification process, gathering of information,
covert facts in to process map, work using map(analysis) and manage process. To know the
information requirements of our organisation it is very important to study the business function.
(Dunn & Kelbie, 1997)
Components Of Database
MakeBelieve DBMS have many components, every one of them performing their specific task in
the database management. But it is mainly consist of four components :
a) Data b) Hardware c) Software d) users
Each one of these components make an effective database system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Fig. Data Base System
Data :
It is very major component of MakeBelieve database system. Our organization store, generate,
and process the huge amount of data. It act as a bridge between software,hardware and users which
can be directly or indirectly access by using MakeBelieve application programs. Our database is
both shared and integreted. Each of those users can access our similar data for the different
purposes. Data may be of different types like user data, Metadata and Application metadata.
(Gouhar, 2017)
Hardware :
In MakeBelieve hardware mainly consists of secondary storage volume such as hard disks and
magnetic tapes etc. It is mainly used to storing and retrieving data in efficient and fast manner. It
provides the interface between real world systems and our computers. Due to huge amount of data
and so many their users it is very necessary to choose appropriate hardware devices for the required
databases. (Stonebraker, Brown, Zhang, & Becla)
Data :
It is very major component of MakeBelieve database system. Our organization store, generate,
and process the huge amount of data. It act as a bridge between software,hardware and users which
can be directly or indirectly access by using MakeBelieve application programs. Our database is
both shared and integreted. Each of those users can access our similar data for the different
purposes. Data may be of different types like user data, Metadata and Application metadata.
(Gouhar, 2017)
Hardware :
In MakeBelieve hardware mainly consists of secondary storage volume such as hard disks and
magnetic tapes etc. It is mainly used to storing and retrieving data in efficient and fast manner. It
provides the interface between real world systems and our computers. Due to huge amount of data
and so many their users it is very necessary to choose appropriate hardware devices for the required
databases. (Stonebraker, Brown, Zhang, & Becla)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Software :
It act as a bridge between MakeBelieve hardware and the user. It is mainly used to interact with
MakeBelieve application programs and database to delete, update and insert the data. It consists of
set of programs which is mainly used to manage and control the overall database. It includes
network software and operating system to share and access the data in our DBMS. (CHAPLOT,
2017)
Users :
MakeBelieve users are basically those persons which need the information from our database to
carry out their work responsibilities.
There are three types of users in MakeBelieve DBMS : a) Application programmer b) End users
and c) database administrator
The application programmer work on the data in all the usual ways to retrieve, create and delete of
existing information. Whereas end user access the database using terminal. They are not much
bothered about structure or detail about the structure of lanugauage of the database system. At the
same time database administrator responsible for the whole control of the database. They have both
managerial and technical skills.
It act as a bridge between MakeBelieve hardware and the user. It is mainly used to interact with
MakeBelieve application programs and database to delete, update and insert the data. It consists of
set of programs which is mainly used to manage and control the overall database. It includes
network software and operating system to share and access the data in our DBMS. (CHAPLOT,
2017)
Users :
MakeBelieve users are basically those persons which need the information from our database to
carry out their work responsibilities.
There are three types of users in MakeBelieve DBMS : a) Application programmer b) End users
and c) database administrator
The application programmer work on the data in all the usual ways to retrieve, create and delete of
existing information. Whereas end user access the database using terminal. They are not much
bothered about structure or detail about the structure of lanugauage of the database system. At the
same time database administrator responsible for the whole control of the database. They have both
managerial and technical skills.
( Ullman, Jeffrey; Widom, Jennifer (1997) A First Course in Database Systems. )
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

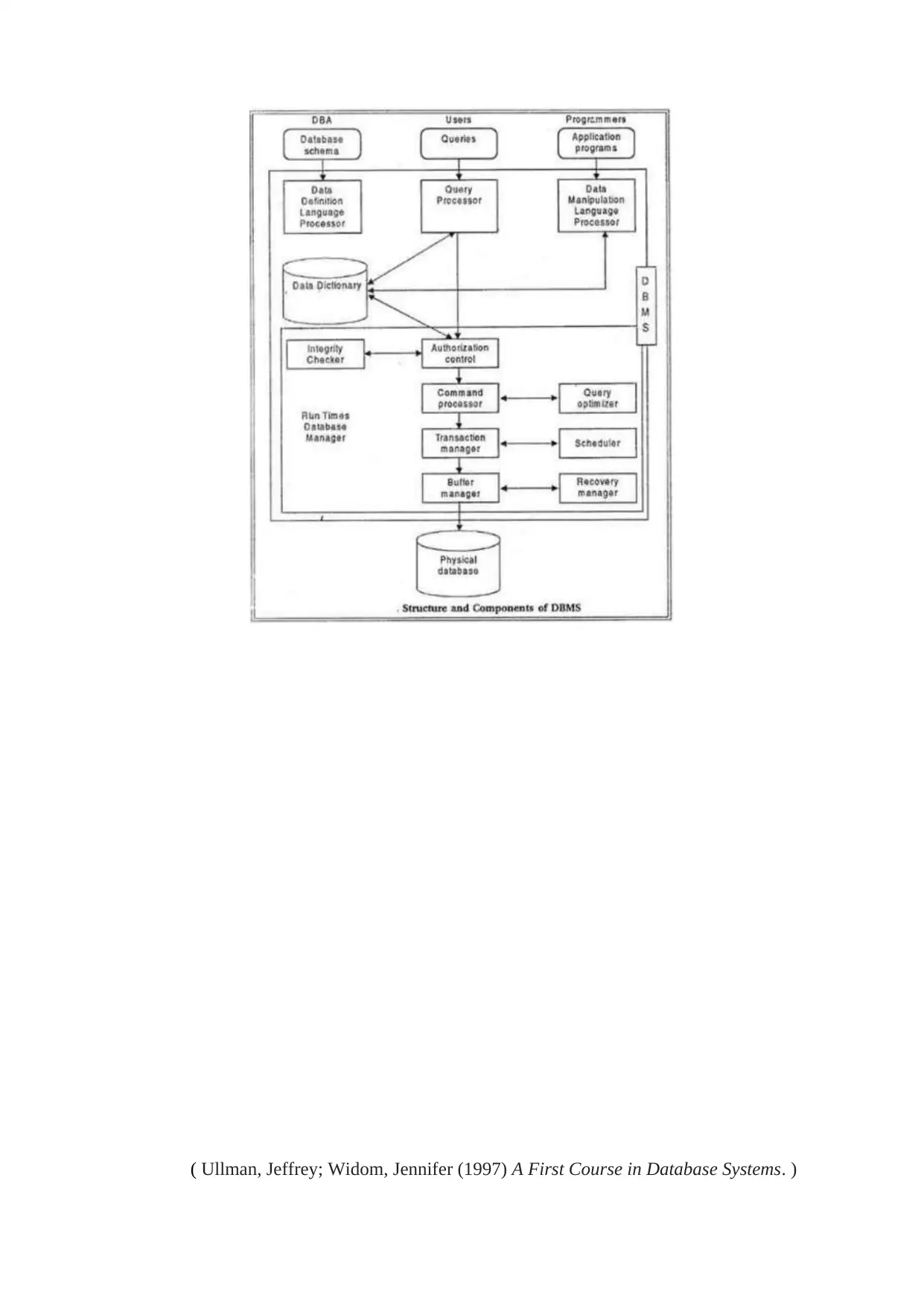
MakeBelieve database management system only accepts the SQL command created from our
different user interface , execute the plan against the database and return the query results. The
query processor mainly uses the data storage to find the structure of the related portion of the
database and then use that information in preparing the query and modifying and good plan to
access the database.The data manager is mainly responsible for the real-time handling of data in the
database. It allows recovery option so that system should be able to recover the data after few
failure.
As we know that an organization performance is hugely affected by how they manages their data.
And one of the most basic idea of data management is the effective management and Understanding
the different layers of the DBMS like how it works and relates to each other is the first step to
employing an effective DBMS. (Stonebraker, Brown, Zhang, & Becla, A database management
system for applications with complex analytics, 2013)
Requirements For Security In Database
In today world security is one of the major challenging and more important work that all people are
facing across the globe in every corner of their life. Makebelieve database management security is a
mjor issue because data and information stored in database is very sensitive and valuable. In today
time database facing so many kinds of attacks. The requirements of database security arise to
protect the data from hackers ,accidential loss and also from unauthorized access of data, undue
delay in using data. Due to evolution in the world technological environments are changed and its
put risk on both of existing solutions and in development of new one.
different user interface , execute the plan against the database and return the query results. The
query processor mainly uses the data storage to find the structure of the related portion of the
database and then use that information in preparing the query and modifying and good plan to
access the database.The data manager is mainly responsible for the real-time handling of data in the
database. It allows recovery option so that system should be able to recover the data after few
failure.
As we know that an organization performance is hugely affected by how they manages their data.
And one of the most basic idea of data management is the effective management and Understanding
the different layers of the DBMS like how it works and relates to each other is the first step to
employing an effective DBMS. (Stonebraker, Brown, Zhang, & Becla, A database management
system for applications with complex analytics, 2013)
Requirements For Security In Database
In today world security is one of the major challenging and more important work that all people are
facing across the globe in every corner of their life. Makebelieve database management security is a
mjor issue because data and information stored in database is very sensitive and valuable. In today
time database facing so many kinds of attacks. The requirements of database security arise to
protect the data from hackers ,accidential loss and also from unauthorized access of data, undue
delay in using data. Due to evolution in the world technological environments are changed and its
put risk on both of existing solutions and in development of new one.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Database Threats
(International Journal of Information Sciences and Techniques (IJIST) Vol.6, No.1/2, March 2016
DOI : 10.5121/ijist.2016.6218 175 DATABASE SECURITY - ATTACKS AND CONTROL
METHODS )
As we see that database security is the major concern for each and every organization. So it became
very important for MakeBelieve to find out all the weak elements and risk factors in their database .
(International Journal of Information Sciences and Techniques (IJIST) Vol.6, No.1/2, March 2016
DOI : 10.5121/ijist.2016.6218 175 DATABASE SECURITY - ATTACKS AND CONTROL
METHODS )
As we see that database security is the major concern for each and every organization. So it became
very important for MakeBelieve to find out all the weak elements and risk factors in their database .

And after that find solution to face or neutralize all threat. Data threat mainly consists of data theft,
data tamper,falsifying the identity of users,unauthorized access to table and columns, password
related threats and lack of accountability etc. To save MakeBelieve database we have to take
security action at so many levels like physical level, human, operating system and at network level.
Due to weakness at low level security allow the access to high level security. We should always use
new technology to provide a secure computing environment for our organization. The major basic
security standard through which technology can ensure are availability, integrity and
confidentiality. A secure system always ensure the confidentiality of data. Authentication process
is one of the most basic concept in database security. In this process system verifies the users
identity. After the verfication process authenticated user have face the second layer of security
authorization. In this process system get the information about the authenticated user and get few
more privileges that user may access. The end user have so many form of authorization on parts of
the database. A secure system always ensure that data contain is valid and easily available to
authorized users.
data tamper,falsifying the identity of users,unauthorized access to table and columns, password
related threats and lack of accountability etc. To save MakeBelieve database we have to take
security action at so many levels like physical level, human, operating system and at network level.
Due to weakness at low level security allow the access to high level security. We should always use
new technology to provide a secure computing environment for our organization. The major basic
security standard through which technology can ensure are availability, integrity and
confidentiality. A secure system always ensure the confidentiality of data. Authentication process
is one of the most basic concept in database security. In this process system verifies the users
identity. After the verfication process authenticated user have face the second layer of security
authorization. In this process system get the information about the authenticated user and get few
more privileges that user may access. The end user have so many form of authorization on parts of
the database. A secure system always ensure that data contain is valid and easily available to
authorized users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Database Vulnerabilities & Countermeasures
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

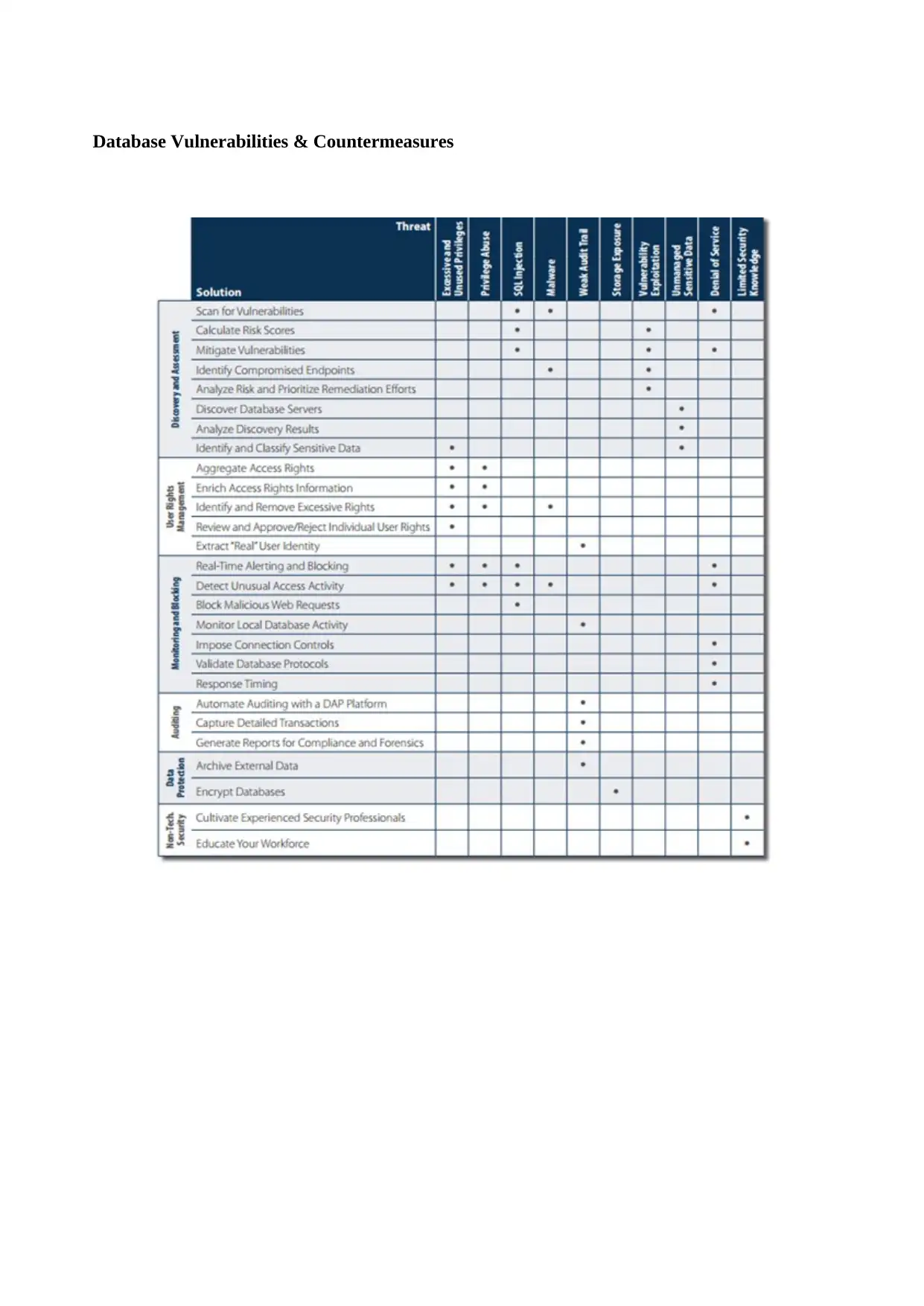
Matrix Threat – Solution (Imperva)
Following are the major attacks and vulnerabilities on MakeBelieve databases :
a) Excessive privilege abuse
Database privileges can be abused in so many ways. This type of abuse come in different forms like
legitimate privileges abuse,unused, and excessive privileges abuse. It is very dangerous because
authorized users can misuse the data.
Countermeasures – always use access control policy and provide good audit trail
b) SQL injection
In MakeBelieve database backend functionality user input the data which main aim is to affect the
database directly. In this hacker inject the unauthorized database statement in to a vulnerable SQL
data. There are two type of injection 1) sql injection and 2) Nosql injection. These attack can give
attacker unrestricted access to the whole database.
Countermeasures – Always try to use MVC architecture and use stored procedure instead of using
direct queries. (Shar & Tan, 2013)
c) Malware
It is one of the most classic cyber threat. In this attacker use phishing emails and malware to eneter
in the organization database and steal their sensitive data. Using this technique they can control the
sensitive data and networks.
Following are the major attacks and vulnerabilities on MakeBelieve databases :
a) Excessive privilege abuse
Database privileges can be abused in so many ways. This type of abuse come in different forms like
legitimate privileges abuse,unused, and excessive privileges abuse. It is very dangerous because
authorized users can misuse the data.
Countermeasures – always use access control policy and provide good audit trail
b) SQL injection
In MakeBelieve database backend functionality user input the data which main aim is to affect the
database directly. In this hacker inject the unauthorized database statement in to a vulnerable SQL
data. There are two type of injection 1) sql injection and 2) Nosql injection. These attack can give
attacker unrestricted access to the whole database.
Countermeasures – Always try to use MVC architecture and use stored procedure instead of using
direct queries. (Shar & Tan, 2013)
c) Malware
It is one of the most classic cyber threat. In this attacker use phishing emails and malware to eneter
in the organization database and steal their sensitive data. Using this technique they can control the
sensitive data and networks.

Countermeasures – always use antivirus and enable the firewall protection
d) DB misconfiguration and vulnerabilities
It is very easy to find the database which have default accounts and configuration parameters. Due
to this attackers easily knows how to launch attack against your organization.
Countermeasures – passwords and accounts must be updated regularly and no default account
should be persent.
(Development of an object-oriented DBMS; Portland, Oregon, United States; Pages: 472–482;
1986)
CVE is a collection of information security vulnerabilities which main aim to give common names
to known cyber security issues. Its main aim is to share data across many vulnerabilities
capabilities. The process of making a CVE Entry starts with the finding of a potential security
vulnerability. Following is CVE example :
CVSS Score 4.3
Confidentiality
Impact
None(There is no impact to the confidentiality of the system.)
Integrity Impact
Partial(Modification of some system files or information is possible, but the
attacker does not have control over what can be modified, or the scope of what
the attacker can affect is limited.)
Availability Impact None(There is no impact to the availability of the system.)
Access Complexity
Medium(The access conditions are somewhat specialized. Some preconditions
must be satistified to exploit)
Authentication Not required(Authentication is not required to exploit the vulnerability.)
d) DB misconfiguration and vulnerabilities
It is very easy to find the database which have default accounts and configuration parameters. Due
to this attackers easily knows how to launch attack against your organization.
Countermeasures – passwords and accounts must be updated regularly and no default account
should be persent.
(Development of an object-oriented DBMS; Portland, Oregon, United States; Pages: 472–482;
1986)
CVE is a collection of information security vulnerabilities which main aim to give common names
to known cyber security issues. Its main aim is to share data across many vulnerabilities
capabilities. The process of making a CVE Entry starts with the finding of a potential security
vulnerability. Following is CVE example :
CVSS Score 4.3
Confidentiality
Impact
None(There is no impact to the confidentiality of the system.)
Integrity Impact
Partial(Modification of some system files or information is possible, but the
attacker does not have control over what can be modified, or the scope of what
the attacker can affect is limited.)
Availability Impact None(There is no impact to the availability of the system.)
Access Complexity
Medium(The access conditions are somewhat specialized. Some preconditions
must be satistified to exploit)
Authentication Not required(Authentication is not required to exploit the vulnerability.)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




