Comprehensive Report on DB2 Database, Security, and Web Deployment
VerifiedAdded on 2022/10/11
|13
|918
|19
Report
AI Summary
This report provides an overview of the DB2 relational database, highlighting its features and capabilities, including advanced analytics and transactional workload support. It explores the importance of security within the DB2 environment, emphasizing confidentiality, integrity, and availability. The report discusses hardening UNIX/Linux systems and managing database access through authentication. It also examines the deployment of web servers, such as Apache and Internet Information Server (IIS), for tasks like checking project progress within a Navy intelligence context, comparing their strengths and weaknesses. The architecture of the DB2 database is outlined, and the report concludes with a discussion on the use of Apache and IIS for security purposes, considering the underlying operating system and system administration skills. The report includes references to relevant academic and industry sources.
DB2 DATABASE
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INTRODUCTION TO DB2 DATABASE:
• The DB2 is a relational database which can deliver the
analytics capabilities and advanced data for transactional
workloads.
• The Db2 database software includes some of the advanced
features like advanced management, in memory technology,
development tools, workload management, continuous data
availability.
• The DB2 is a relational database which can deliver the
analytics capabilities and advanced data for transactional
workloads.
• The Db2 database software includes some of the advanced
features like advanced management, in memory technology,
development tools, workload management, continuous data
availability.
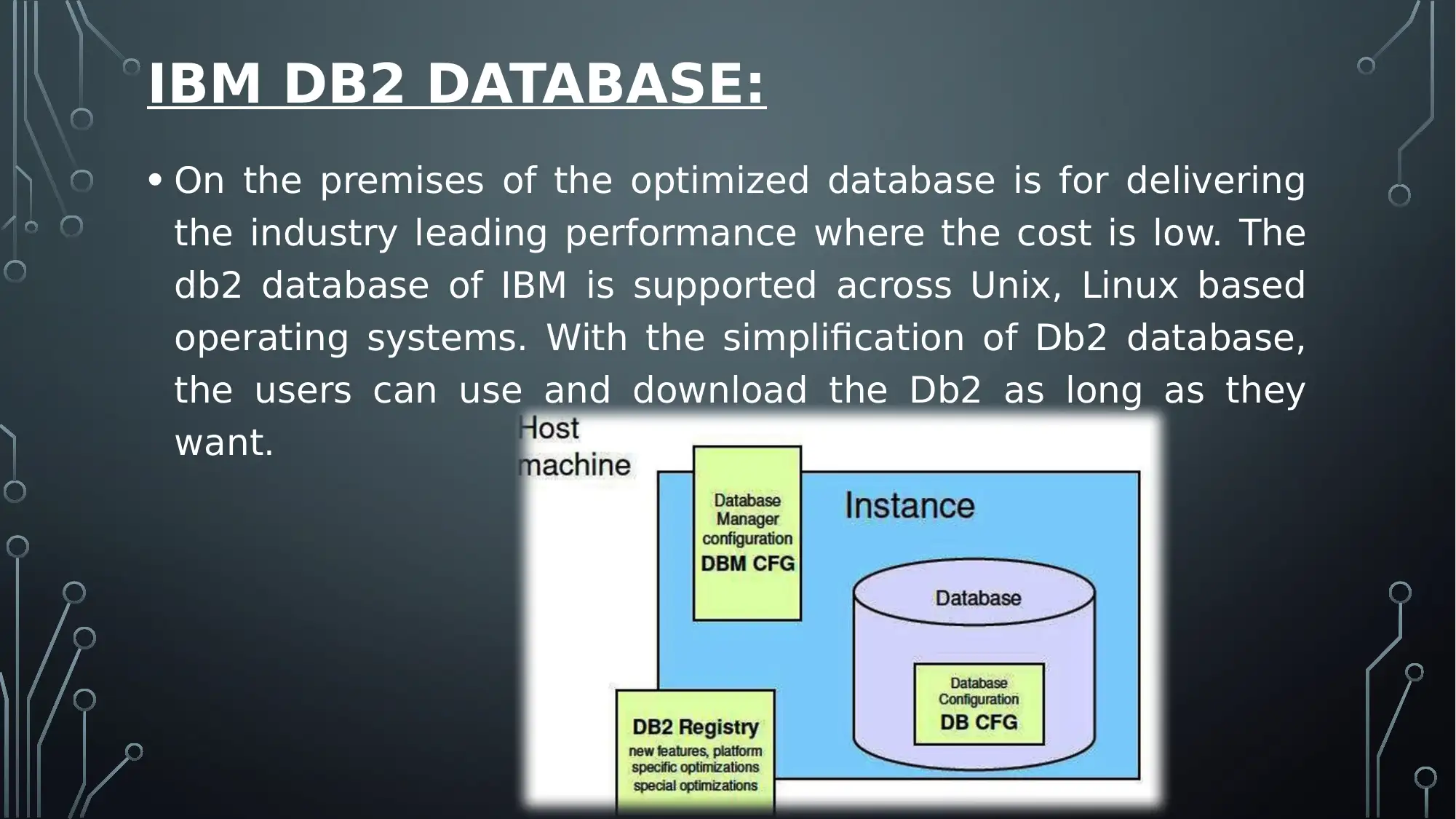
IBM DB2 DATABASE:
• On the premises of the optimized database is for delivering
the industry leading performance where the cost is low. The
db2 database of IBM is supported across Unix, Linux based
operating systems. With the simplification of Db2 database,
the users can use and download the Db2 as long as they
want.
• On the premises of the optimized database is for delivering
the industry leading performance where the cost is low. The
db2 database of IBM is supported across Unix, Linux based
operating systems. With the simplification of Db2 database,
the users can use and download the Db2 as long as they
want.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IMPORTANCE OF SECURITY
Db2 databases can hold the backbone of an entire organisation.
The triad of integrity, confidentiality and availability are the
actual foundation of the database security and information
security. Confidentiality is one of the important most aspect for
the security of Db2.
This is so much important to maintain the defences and security
practices for combatting the attacks on to the database.
Db2 databases can hold the backbone of an entire organisation.
The triad of integrity, confidentiality and availability are the
actual foundation of the database security and information
security. Confidentiality is one of the important most aspect for
the security of Db2.
This is so much important to maintain the defences and security
practices for combatting the attacks on to the database.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
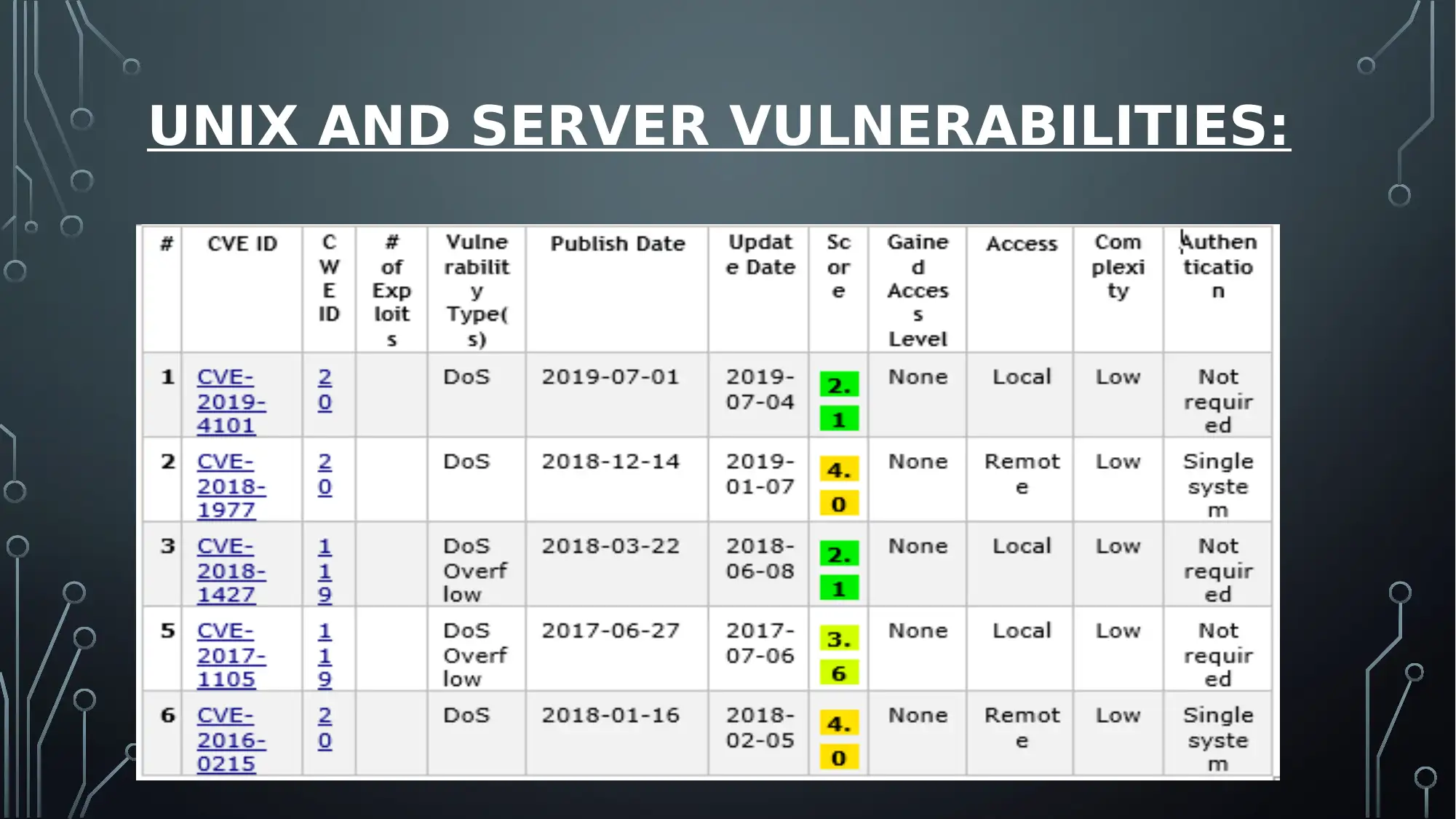
UNIX AND SERVER VULNERABILITIES:
HARDENING THE UNIX/LINUX SYSTEM
• Two of the models for the security
control for accessing Db2 database
functions and system data. Access to
the database (Db2) system can be
managed through the facilities.
• After the account of the user is
authenticated, it id determined by
the database manager that the user
has been allowed for accessing the
DB2 resources and data.
• Two of the models for the security
control for accessing Db2 database
functions and system data. Access to
the database (Db2) system can be
managed through the facilities.
• After the account of the user is
authenticated, it id determined by
the database manager that the user
has been allowed for accessing the
DB2 resources and data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
DEPLOYMENT OF A WEB SERVER TO BE
USED BY NAVY INTELLIGENCE FOR
CHECKING ON PROJECT PROGRESS:
• Before the deployment of data web services to one of the
local server, at least one of the web server connection. The
use of the options that are advanced for configuring the
connections of the web server.
• The designer of the data web services have to be opened. If a
web server connection has not been configured for opening
the designer for the very first time.
• With the add ins of the database for the visual studio, the
web services can be created d which can expose the
operations of the database to the client related applications.
USED BY NAVY INTELLIGENCE FOR
CHECKING ON PROJECT PROGRESS:
• Before the deployment of data web services to one of the
local server, at least one of the web server connection. The
use of the options that are advanced for configuring the
connections of the web server.
• The designer of the data web services have to be opened. If a
web server connection has not been configured for opening
the designer for the very first time.
• With the add ins of the database for the visual studio, the
web services can be created d which can expose the
operations of the database to the client related applications.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
APACHE AND INTERNET
INFORMATION SERVER
In the Db2 database, both the internet information server and
apache server can be connected. Apache is one of the most
widely used web based servers, it runs on linux, unix, windows
and Mac OS. On the other side the Internet information servers
runs on windows only. Both the IIS and Apache is having their
own weaknesses and own strong points. The obvious most
advantages of the of IIS id the tight integration with the
technologies related to windows and for Apache is the cross
platform.
INFORMATION SERVER
In the Db2 database, both the internet information server and
apache server can be connected. Apache is one of the most
widely used web based servers, it runs on linux, unix, windows
and Mac OS. On the other side the Internet information servers
runs on windows only. Both the IIS and Apache is having their
own weaknesses and own strong points. The obvious most
advantages of the of IIS id the tight integration with the
technologies related to windows and for Apache is the cross
platform.
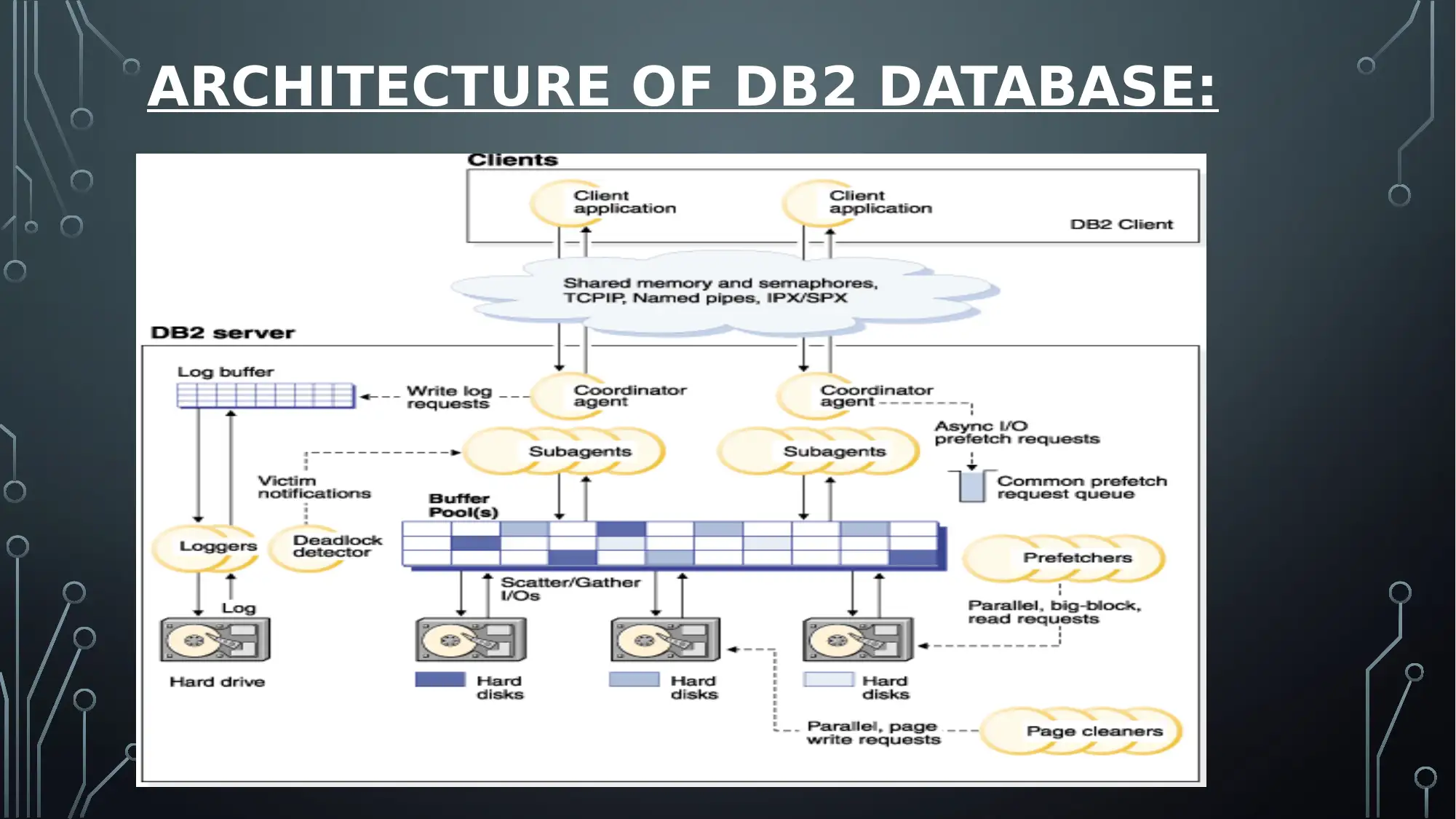
ARCHITECTURE OF DB2 DATABASE:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
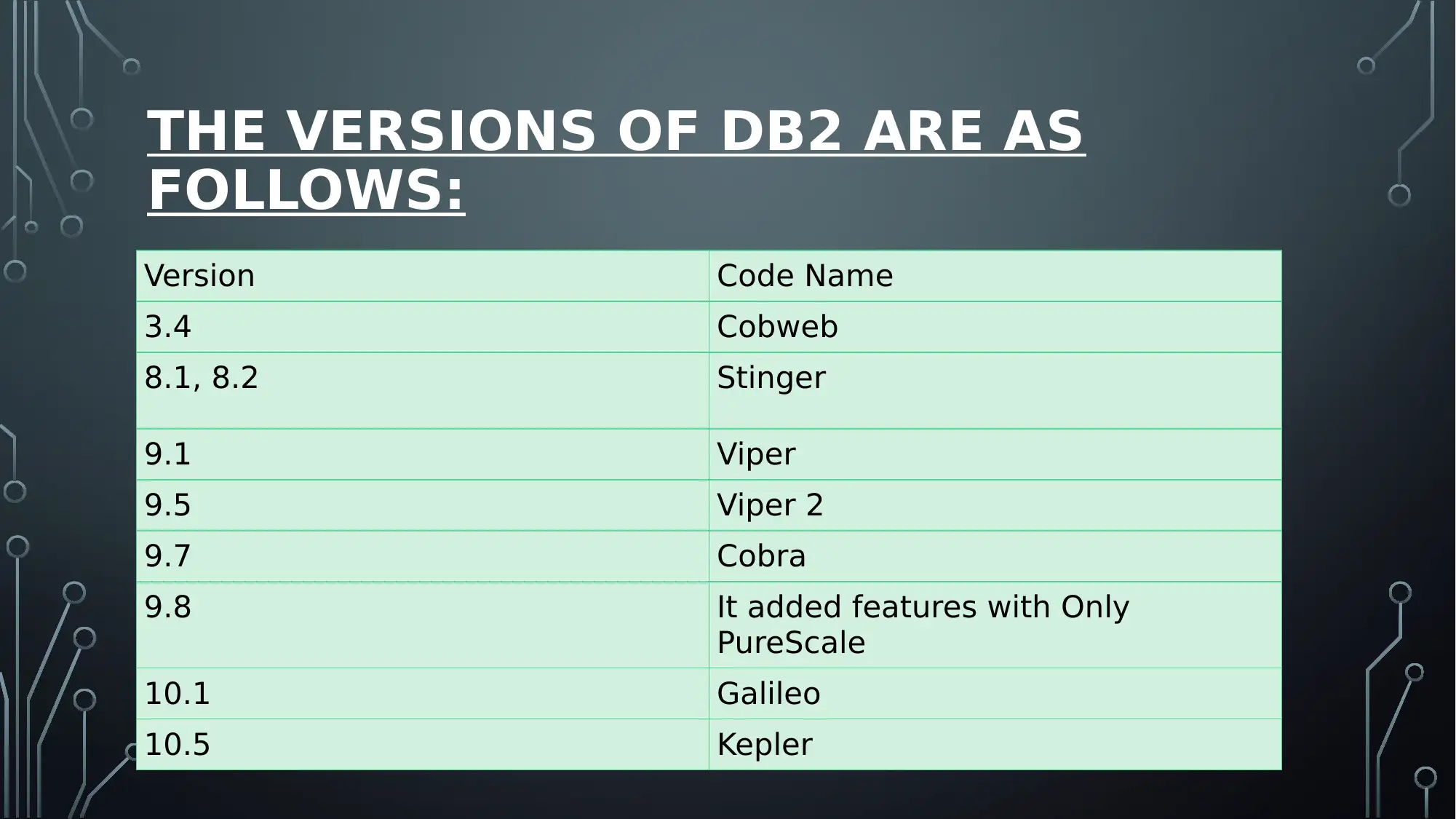
THE VERSIONS OF DB2 ARE AS
FOLLOWS:
Version Code Name
3.4 Cobweb
8.1, 8.2 Stinger
9.1 Viper
9.5 Viper 2
9.7 Cobra
9.8 It added features with Only
PureScale
10.1 Galileo
10.5 Kepler
FOLLOWS:
Version Code Name
3.4 Cobweb
8.1, 8.2 Stinger
9.1 Viper
9.5 Viper 2
9.7 Cobra
9.8 It added features with Only
PureScale
10.1 Galileo
10.5 Kepler
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
USE OF APACHE AND IIS FOR
SECURITY:
• For the perspective of security, the choice between Apache
and IIS is debatable. The security of web server, is as good as
the operating system that is underlying. The consideration of
the skills of the system admin rights to the operating system.
SECURITY:
• For the perspective of security, the choice between Apache
and IIS is debatable. The security of web server, is as good as
the operating system that is underlying. The consideration of
the skills of the system admin rights to the operating system.

REFERENCES:
• Barber, R., Lohman, G., Raman, V., Sidle, R., Lightstone, S., & Schiefer, B. (2015, April). In-memory BLU acceleration
in IBM's DB2 and dashDB: Optimized for modern workloads and hardware architectures. In 2015 IEEE 31st
International Conference on Data Engineering (pp. 1246-1252). IEEE.
• Chan, Y., Ivanov, N., & Mueller, O. (2014). Oracle to DB2 Conversion Guide: Compatibility Made Easy. IBM Redbooks.
• Deenadayalan, E., Hanirex, D., & Kaliyamurthie, K. (2014). Association rule mining in distributed database
system. International Journal of Computer Science and Mobile Computing, 3(4), 727-732.
• Deenadayalan, E., Hanirex, D., & Kaliyamurthie, K. (2014). Association rule mining in distributed database
system. International Journal of Computer Science and Mobile Computing, 3(4), 727-732.
• Drzymala, P., & Welfle, H. (2014). DB2 pureXML-advanced of data storage in the relational hierarchical
structures. Przegląd Elektrotechniczny, 90(3), 165-168.
• Ebbers, M., Bosch, W., Ebert, H. J., Hellner, H., Johnston, J., Kroll, M., ... & Schmidbauer, J. (2016). Introduction to the
New Mainframe: IBM Z/VSE Basics. IBM Redbooks.
• Francis-Lothai, F. L. O. R. E. N. C. E., & Bong, D. B. (2015). Fingerdos: a fingerprint database based on optical
sensor. Wseas Transactions On Information Science And Applications, 12(29), 297-304.
• Halvorsen, H. P. (2016). Introduction to Database Systems. Notodden, Norway: University College of Southeast
Norway.
• Petkovic, D. (2016). Temporal data in relational database systems: a comparison. In New Advances in Information
Systems and Technologies (pp. 13-23). Springer, Cham.
• Barber, R., Lohman, G., Raman, V., Sidle, R., Lightstone, S., & Schiefer, B. (2015, April). In-memory BLU acceleration
in IBM's DB2 and dashDB: Optimized for modern workloads and hardware architectures. In 2015 IEEE 31st
International Conference on Data Engineering (pp. 1246-1252). IEEE.
• Chan, Y., Ivanov, N., & Mueller, O. (2014). Oracle to DB2 Conversion Guide: Compatibility Made Easy. IBM Redbooks.
• Deenadayalan, E., Hanirex, D., & Kaliyamurthie, K. (2014). Association rule mining in distributed database
system. International Journal of Computer Science and Mobile Computing, 3(4), 727-732.
• Deenadayalan, E., Hanirex, D., & Kaliyamurthie, K. (2014). Association rule mining in distributed database
system. International Journal of Computer Science and Mobile Computing, 3(4), 727-732.
• Drzymala, P., & Welfle, H. (2014). DB2 pureXML-advanced of data storage in the relational hierarchical
structures. Przegląd Elektrotechniczny, 90(3), 165-168.
• Ebbers, M., Bosch, W., Ebert, H. J., Hellner, H., Johnston, J., Kroll, M., ... & Schmidbauer, J. (2016). Introduction to the
New Mainframe: IBM Z/VSE Basics. IBM Redbooks.
• Francis-Lothai, F. L. O. R. E. N. C. E., & Bong, D. B. (2015). Fingerdos: a fingerprint database based on optical
sensor. Wseas Transactions On Information Science And Applications, 12(29), 297-304.
• Halvorsen, H. P. (2016). Introduction to Database Systems. Notodden, Norway: University College of Southeast
Norway.
• Petkovic, D. (2016). Temporal data in relational database systems: a comparison. In New Advances in Information
Systems and Technologies (pp. 13-23). Springer, Cham.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





