Advanced Network Security Report
VerifiedAdded on 2019/09/25
|5
|857
|149
Report
AI Summary
This report provides a comprehensive overview of Distributed Denial of Service (DDoS) attacks, focusing specifically on Ping Flooding attacks. It details the entities involved in a DDoS attack, explaining the roles of victim systems, attackers, master zombies, and slave zombies. The report then delves into the mechanics of Ping Flooding, a common DDoS technique that utilizes ICMP echo requests to overwhelm a target system. It discusses tools like hping3 used to execute such attacks. The report concludes by outlining mitigation strategies for DDoS attacks, including techniques like integrated Intserv, differentiated services, class-based queuing, resource pricing, and throttling. These strategies aim to alleviate the impact of the flood of fake packets by managing resources and limiting traffic flow.

Running Head: Advanced Network Security
Advanced network security
[Document subtitle]
Advanced network security
[Document subtitle]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Advanced Network Security 1
Answer 3
A. Overview of DDoS Attack
Access to a mall is interrupted by multiple illegitimate people which prevents entry to a
genuine customer who is serious buyers. This affects the trade effectively. DDoS also
does the same work that influences the trade ultimately. The DDoS attack is an attack
where a wide range of people or group or preceptor makes the network or server
resources unavailable to their intended users.
In Denial of Service attach, internet or a computer connection utilized to exhaust the
victim resources through flooding a server with packets. In order to fulfill the DoS
purpose, different servers can use a wide range of attack methodologies. These
methodologies will serve as an important source for different server connects to improve
service performance through better processing of available data.
Moreover, it is also considered that DDoS attacks used different internet and computer
connections which are operated internationally to perform an attack. As a result, the
sufferer will be flooded with the packets sent from different sources.
B. Entities in DDoS Attacks:
Answer 3
A. Overview of DDoS Attack
Access to a mall is interrupted by multiple illegitimate people which prevents entry to a
genuine customer who is serious buyers. This affects the trade effectively. DDoS also
does the same work that influences the trade ultimately. The DDoS attack is an attack
where a wide range of people or group or preceptor makes the network or server
resources unavailable to their intended users.
In Denial of Service attach, internet or a computer connection utilized to exhaust the
victim resources through flooding a server with packets. In order to fulfill the DoS
purpose, different servers can use a wide range of attack methodologies. These
methodologies will serve as an important source for different server connects to improve
service performance through better processing of available data.
Moreover, it is also considered that DDoS attacks used different internet and computer
connections which are operated internationally to perform an attack. As a result, the
sufferer will be flooded with the packets sent from different sources.
B. Entities in DDoS Attacks:
Advanced Network Security 2
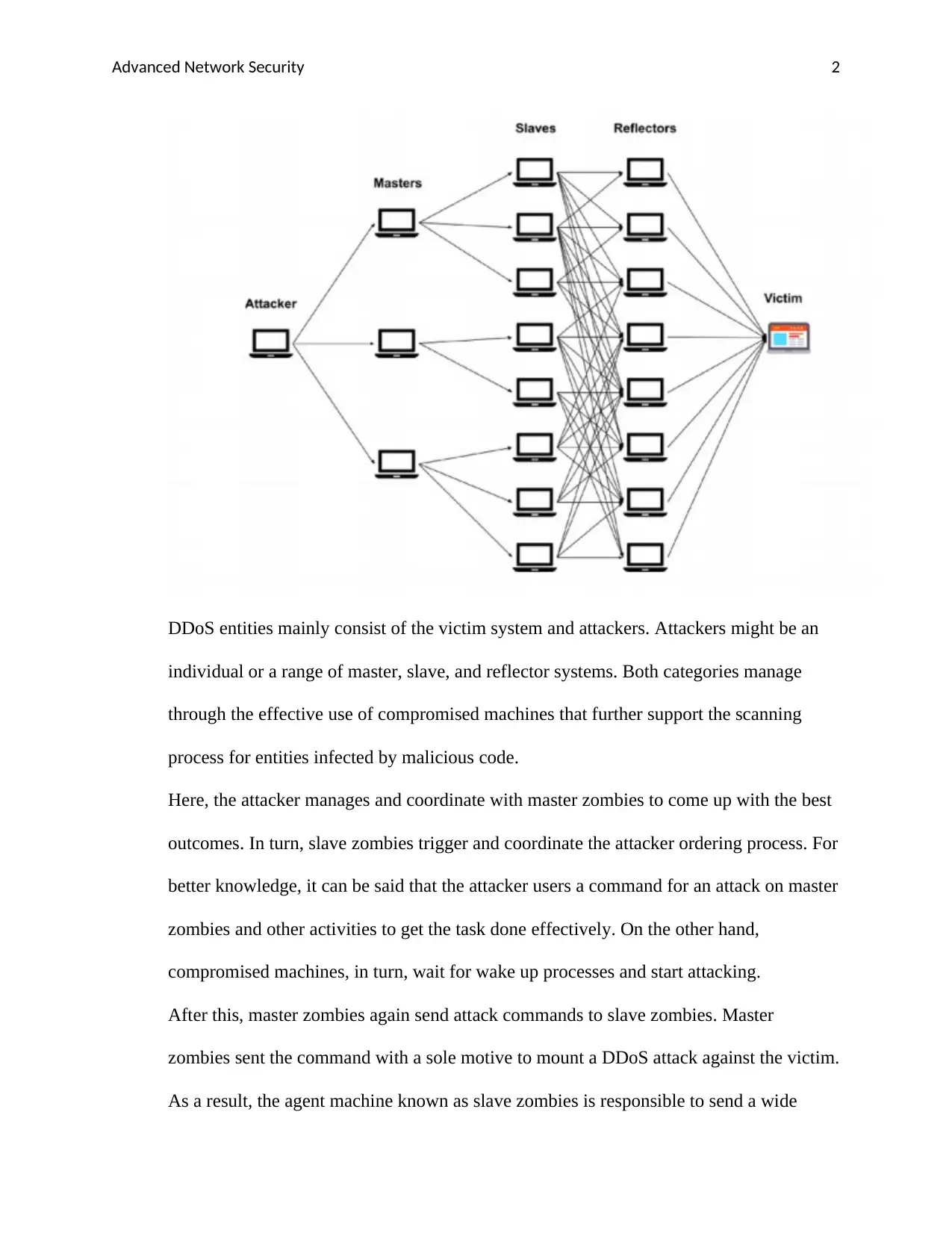
DDoS entities mainly consist of the victim system and attackers. Attackers might be an
individual or a range of master, slave, and reflector systems. Both categories manage
through the effective use of compromised machines that further support the scanning
process for entities infected by malicious code.
Here, the attacker manages and coordinate with master zombies to come up with the best
outcomes. In turn, slave zombies trigger and coordinate the attacker ordering process. For
better knowledge, it can be said that the attacker users a command for an attack on master
zombies and other activities to get the task done effectively. On the other hand,
compromised machines, in turn, wait for wake up processes and start attacking.
After this, master zombies again send attack commands to slave zombies. Master
zombies sent the command with a sole motive to mount a DDoS attack against the victim.
As a result, the agent machine known as slave zombies is responsible to send a wide
DDoS entities mainly consist of the victim system and attackers. Attackers might be an
individual or a range of master, slave, and reflector systems. Both categories manage
through the effective use of compromised machines that further support the scanning
process for entities infected by malicious code.
Here, the attacker manages and coordinate with master zombies to come up with the best
outcomes. In turn, slave zombies trigger and coordinate the attacker ordering process. For
better knowledge, it can be said that the attacker users a command for an attack on master
zombies and other activities to get the task done effectively. On the other hand,
compromised machines, in turn, wait for wake up processes and start attacking.
After this, master zombies again send attack commands to slave zombies. Master
zombies sent the command with a sole motive to mount a DDoS attack against the victim.
As a result, the agent machine known as slave zombies is responsible to send a wide
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Advanced Network Security 3
range of packets to the victim. After receiving the packets, victims will further
responsible to flood the system with useless load and reduce its burden.
C. Ping Flooding Attack
Ping Flooding attack is a common service denial attack. In Ping flooding attack, an
attacker destroys a computer by hacking it with ICMP echo requests. This requires also
known as the pings with a wide range of resources. Ping Flooding attack is a combination
of different processes which involves influencing the system network of other corporate
houses through request packets or unknown networks. Apart from this, ping flooding
attack also uses other attack methods to hack a network. These mainly include; customer
codes and tools like scapy and hping.
These hacking tools enable the network to strains both the outgoing and incoming
channels and consume significant bandwidth that further results denial of service. The
more overwhelming and severe attack also bring down the whole server very easily.
One of the tools for ping flooding attack is hping. HPing is considered as a free packer
generator and evaluates for the IP and TCP protocol. Apart from this, Hping is also
known as the de-factor tool for testing of networks and firewalls or security auditing.
Moreover, it is also utilized to exploit the Idle Scan. It is a scanning methodology that
implemented with the sole motive of the port scanner.
$hping3-c 10000 –d 120 –S –w 64 –p 21—flood –rand-source www.google.com
D. Mitigating Ping Flooding Attack
DDoS In simple words it can be said that relieving victims resources from the high
volume of fake packets to the disseminated locations sent through the attackers. DDoS
distributed nature makes difficult to combat. In a way to conceal the true identity
range of packets to the victim. After receiving the packets, victims will further
responsible to flood the system with useless load and reduce its burden.
C. Ping Flooding Attack
Ping Flooding attack is a common service denial attack. In Ping flooding attack, an
attacker destroys a computer by hacking it with ICMP echo requests. This requires also
known as the pings with a wide range of resources. Ping Flooding attack is a combination
of different processes which involves influencing the system network of other corporate
houses through request packets or unknown networks. Apart from this, ping flooding
attack also uses other attack methods to hack a network. These mainly include; customer
codes and tools like scapy and hping.
These hacking tools enable the network to strains both the outgoing and incoming
channels and consume significant bandwidth that further results denial of service. The
more overwhelming and severe attack also bring down the whole server very easily.
One of the tools for ping flooding attack is hping. HPing is considered as a free packer
generator and evaluates for the IP and TCP protocol. Apart from this, Hping is also
known as the de-factor tool for testing of networks and firewalls or security auditing.
Moreover, it is also utilized to exploit the Idle Scan. It is a scanning methodology that
implemented with the sole motive of the port scanner.
$hping3-c 10000 –d 120 –S –w 64 –p 21—flood –rand-source www.google.com
D. Mitigating Ping Flooding Attack
DDoS In simple words it can be said that relieving victims resources from the high
volume of fake packets to the disseminated locations sent through the attackers. DDoS
distributed nature makes difficult to combat. In a way to conceal the true identity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Advanced Network Security 4
attackers may use IP spoofing. In regards to security breaches on the internet, there is no
satisfactory security measures are available. The defense mechanism of DDoS includes
detection, prevention, Mitigation, tolerance, and responses.
A) Integrated Intserv: Resource Reservation Protocols may be used to manage the
allocation of the resources along the path through which particular traffic passes.
B) Differentiated Services: differentiated services should be based on the Type of
services that is byte in the IP header.
C) Class Based Queuing: Different type of queues should be made based on the
different packets and types and then accordingly bandwidth should be assigned.
D) Resource Pricing: Payment protocol and distributed gateway architecture need to be
proposed that should impose the dynamically changing prices on both the network,
information resources, and server.
E) Throttling: the passage of the traffic through the router to the ultimate source is rate
limited with regards to throttle rate.
attackers may use IP spoofing. In regards to security breaches on the internet, there is no
satisfactory security measures are available. The defense mechanism of DDoS includes
detection, prevention, Mitigation, tolerance, and responses.
A) Integrated Intserv: Resource Reservation Protocols may be used to manage the
allocation of the resources along the path through which particular traffic passes.
B) Differentiated Services: differentiated services should be based on the Type of
services that is byte in the IP header.
C) Class Based Queuing: Different type of queues should be made based on the
different packets and types and then accordingly bandwidth should be assigned.
D) Resource Pricing: Payment protocol and distributed gateway architecture need to be
proposed that should impose the dynamically changing prices on both the network,
information resources, and server.
E) Throttling: the passage of the traffic through the router to the ultimate source is rate
limited with regards to throttle rate.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





