Computer Security Assignment: DDoS Attack Analysis and Case Study
VerifiedAdded on 2023/06/07
|10
|2318
|138
Report
AI Summary
This report provides a comprehensive analysis of Distributed Denial of Service (DDoS) attacks, a significant threat to computer and network security. It begins by explaining the fundamental concepts of DDoS attacks, including how they operate, the use of botnets, and the different types of attacks such as HTTP flood and SYN flood. The report then delves into the specifics of a real-world incident, the Melbourne IT DDoS attack of April 2017, detailing the attack's impact on Australian websites and the disruption of services. It discusses the outcome of the incident, the financial and operational impact, and which security aims were breached. The report also provides a detailed walkthrough of the attack, graphical depictions of the attack's components, and an examination of the mitigation strategies employed. Finally, the report concludes by summarizing the key aspects of DDoS attacks and the importance of robust security measures.

Running head: COMPUTER SECURITY
Computer Security: Melbourne IT Attack
Name of the Student
Name of the University
Author Note
Computer Security: Melbourne IT Attack
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
COMPUTER SECURITY
Table of Contents
Introduction..........................................................................................................................2
1. DDoS Attack....................................................................................................................2
2. Melbourne IT DDoS attack.............................................................................................5
Conclusion...........................................................................................................................7
References............................................................................................................................8
COMPUTER SECURITY
Table of Contents
Introduction..........................................................................................................................2
1. DDoS Attack....................................................................................................................2
2. Melbourne IT DDoS attack.............................................................................................5
Conclusion...........................................................................................................................7
References............................................................................................................................8

2
COMPUTER SECURITY
Introduction
A distributed denial of service or DDoS attack can be described as a malicious attempt
that aims in disrupting the normal traffic of a particular network, server of its surrounding
infrastructure. A DDoS attack floods the surrounding network infrastructure with a flooded
internet traffic that disrupts the normal operation of that network or server. Effectiveness in
DDos attack is generally achieved by the making use of a number of compromised systems as a
source of attack traffic (Moustis & Kotzanikolaou, 2013). A high level DDoS attack can be
related to a traffic jam that prevents the regular movements of traffic. An attacker will need to
gain a complete control of a network to enforce a DDoS attack. The report will be discussing the
concepts of DDoS attack and will give an overview of the Melbourne IT attack that took place in
April 2017. The outcome and the impact of the Melbourne IT attack will be discussed in the
following sections.
1. DDoS Attack
Distributed denial of service attack is a primary concern associated with the use of
internet. It can be described as a cyber attack that is being attempted with an aim of
compromising the network traffic of an organization (Wang et al., 2015). The distributed denial
of service attack is a subclass of the denial of service attack and it involves a number of multiple
connected and online devices which is collectively known as botnet.
For enforcing a DDoS attack, the attacker needs to gain a complete control of a network
associated with online machines (Wong & Tan, 2014). After establishing the botnet, the attacker
gains a control on the machines associated with the server thus jamming the entire network. The
botnet that is created targets the IP address of the victim computer and sends out continuous
COMPUTER SECURITY
Introduction
A distributed denial of service or DDoS attack can be described as a malicious attempt
that aims in disrupting the normal traffic of a particular network, server of its surrounding
infrastructure. A DDoS attack floods the surrounding network infrastructure with a flooded
internet traffic that disrupts the normal operation of that network or server. Effectiveness in
DDos attack is generally achieved by the making use of a number of compromised systems as a
source of attack traffic (Moustis & Kotzanikolaou, 2013). A high level DDoS attack can be
related to a traffic jam that prevents the regular movements of traffic. An attacker will need to
gain a complete control of a network to enforce a DDoS attack. The report will be discussing the
concepts of DDoS attack and will give an overview of the Melbourne IT attack that took place in
April 2017. The outcome and the impact of the Melbourne IT attack will be discussed in the
following sections.
1. DDoS Attack
Distributed denial of service attack is a primary concern associated with the use of
internet. It can be described as a cyber attack that is being attempted with an aim of
compromising the network traffic of an organization (Wang et al., 2015). The distributed denial
of service attack is a subclass of the denial of service attack and it involves a number of multiple
connected and online devices which is collectively known as botnet.
For enforcing a DDoS attack, the attacker needs to gain a complete control of a network
associated with online machines (Wong & Tan, 2014). After establishing the botnet, the attacker
gains a control on the machines associated with the server thus jamming the entire network. The
botnet that is created targets the IP address of the victim computer and sends out continuous
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
COMPUTER SECURITY
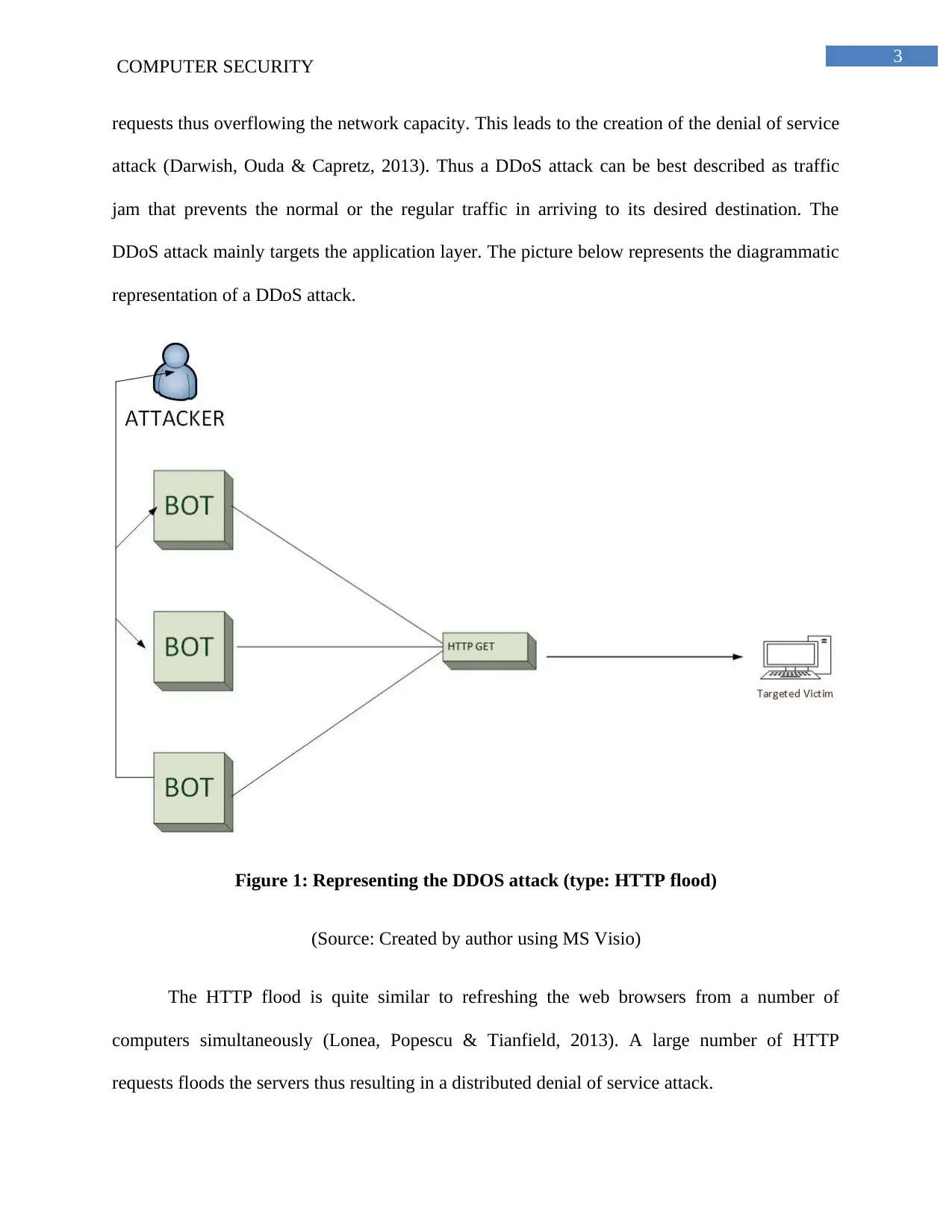
requests thus overflowing the network capacity. This leads to the creation of the denial of service
attack (Darwish, Ouda & Capretz, 2013). Thus a DDoS attack can be best described as traffic
jam that prevents the normal or the regular traffic in arriving to its desired destination. The
DDoS attack mainly targets the application layer. The picture below represents the diagrammatic
representation of a DDoS attack.
Figure 1: Representing the DDOS attack (type: HTTP flood)
(Source: Created by author using MS Visio)
The HTTP flood is quite similar to refreshing the web browsers from a number of
computers simultaneously (Lonea, Popescu & Tianfield, 2013). A large number of HTTP
requests floods the servers thus resulting in a distributed denial of service attack.
COMPUTER SECURITY
requests thus overflowing the network capacity. This leads to the creation of the denial of service
attack (Darwish, Ouda & Capretz, 2013). Thus a DDoS attack can be best described as traffic
jam that prevents the normal or the regular traffic in arriving to its desired destination. The
DDoS attack mainly targets the application layer. The picture below represents the diagrammatic
representation of a DDoS attack.
Figure 1: Representing the DDOS attack (type: HTTP flood)
(Source: Created by author using MS Visio)
The HTTP flood is quite similar to refreshing the web browsers from a number of
computers simultaneously (Lonea, Popescu & Tianfield, 2013). A large number of HTTP
requests floods the servers thus resulting in a distributed denial of service attack.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
COMPUTER SECURITY
Another type of DDoS attack is SYN flood. In this attack, a worker receives a request and
goes to get the packet followed by which it waits for the confirmation. Similar requests are piled
up in the network until the network becomes overwhelmed and the requests start getting
unanswered.
This attack does not enable the attacker to gain any confidential or private that but surely
makes a particular network or server of a company completely ineffective (Kotenko & Ulanov,
2014). This can however, lead wastage of time and resources (Mousavi & St-Hilaire, 2015). The
main problem behind mitigation of a DDoS attack or eliminate the chances of occurrence of a
DDoS attack is that it is very difficult to differentiate between a normal traffic and a DDoS
attack. A distributed denial of service attack comes in a number of forms such as a single source
attack or a multiple vector attack. In a multiple vector attack, the DDoS attack makes use of
multiple attack pathways in overwhelming a target in a number of ways thus distracting the
mitigation efforts of the network and the servers (Santanna et al., 2015). Therefore, mitigation of
DDoS attack from a multiple vectors requires a variety of strategies. There are a number of
process by which a DDoS attack can be mitigated. These are as follows-
1. One of the approaches for mitigation of the DDoS attack includes blackhole routing. In
this process the network traffic is funneled into a single route (Wang et al., 2014). However, in
this approach, the both legitimate and the malicious network traffic is routed to null route and
dropped from a network in case of traffic overflow.
2. Limiting the number of requests that can be accepted by a network over a certain time
is another approach that is used to mitigate a DDoS attack (Zargar, Joshi & Tipper, 2013).
3. Rate limiting is another approach for limiting the occurrence of DDoS attack.
COMPUTER SECURITY
Another type of DDoS attack is SYN flood. In this attack, a worker receives a request and
goes to get the packet followed by which it waits for the confirmation. Similar requests are piled
up in the network until the network becomes overwhelmed and the requests start getting
unanswered.
This attack does not enable the attacker to gain any confidential or private that but surely
makes a particular network or server of a company completely ineffective (Kotenko & Ulanov,
2014). This can however, lead wastage of time and resources (Mousavi & St-Hilaire, 2015). The
main problem behind mitigation of a DDoS attack or eliminate the chances of occurrence of a
DDoS attack is that it is very difficult to differentiate between a normal traffic and a DDoS
attack. A distributed denial of service attack comes in a number of forms such as a single source
attack or a multiple vector attack. In a multiple vector attack, the DDoS attack makes use of
multiple attack pathways in overwhelming a target in a number of ways thus distracting the
mitigation efforts of the network and the servers (Santanna et al., 2015). Therefore, mitigation of
DDoS attack from a multiple vectors requires a variety of strategies. There are a number of
process by which a DDoS attack can be mitigated. These are as follows-
1. One of the approaches for mitigation of the DDoS attack includes blackhole routing. In
this process the network traffic is funneled into a single route (Wang et al., 2014). However, in
this approach, the both legitimate and the malicious network traffic is routed to null route and
dropped from a network in case of traffic overflow.
2. Limiting the number of requests that can be accepted by a network over a certain time
is another approach that is used to mitigate a DDoS attack (Zargar, Joshi & Tipper, 2013).
3. Rate limiting is another approach for limiting the occurrence of DDoS attack.

5
COMPUTER SECURITY
A real life DDoS attack, the Melbourne IT DDoS attack, is discussed in the following
section.
2. Melbourne IT DDoS attack
The Melbourne IT DDoS attack that made thousands of website inaccessible, occurred on
April 1, 2017 at 10am AEST. The attack was not given any specific name and is commonly
known as the Melbourne IT attack. The attack was severe that made almost 500,000 Australian
website almost inaccessible for near about 90 minutes.
The distributed denial of service attack impacted a large number of customers as the
DDoS attack was on the DNS servers that disrupted the web hosting, email and blocked the
access to the administrative portal of a company this impacting a large number of customers
(Coyne & Coyne, 2018). The incident proved that even the most secure systems can be
compromised.
The DNS outage caused by the DDoS attack had a huge impact on the Melbourne IT and
subsidiaries Netregistry. Melbourne IT has experienced this severe denial of service attack on its
DNS servers that mainly disrupted the web hosting, email platform and in accessing the
company’s administration portal. The attack started in around 10 am that affected a number of
business websites.
However, with the identification of the DDoS attack, all the companies started working
on bringing the services back to normal. In the response to the implemented DDoS attack, the
companies implemented the international traffic management measures in controlling the DDoS
attack. There was no such major impact of this DDoS attack as the authorities were quick enough
to bring back the normal operation of the website.
COMPUTER SECURITY
A real life DDoS attack, the Melbourne IT DDoS attack, is discussed in the following
section.
2. Melbourne IT DDoS attack
The Melbourne IT DDoS attack that made thousands of website inaccessible, occurred on
April 1, 2017 at 10am AEST. The attack was not given any specific name and is commonly
known as the Melbourne IT attack. The attack was severe that made almost 500,000 Australian
website almost inaccessible for near about 90 minutes.
The distributed denial of service attack impacted a large number of customers as the
DDoS attack was on the DNS servers that disrupted the web hosting, email and blocked the
access to the administrative portal of a company this impacting a large number of customers
(Coyne & Coyne, 2018). The incident proved that even the most secure systems can be
compromised.
The DNS outage caused by the DDoS attack had a huge impact on the Melbourne IT and
subsidiaries Netregistry. Melbourne IT has experienced this severe denial of service attack on its
DNS servers that mainly disrupted the web hosting, email platform and in accessing the
company’s administration portal. The attack started in around 10 am that affected a number of
business websites.
However, with the identification of the DDoS attack, all the companies started working
on bringing the services back to normal. In the response to the implemented DDoS attack, the
companies implemented the international traffic management measures in controlling the DDoS
attack. There was no such major impact of this DDoS attack as the authorities were quick enough
to bring back the normal operation of the website.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
COMPUTER SECURITY
This attack is a proof that the incident breached the basic security requirements of a
network and the servers affecting a huge number of websites. It has been observed that
Melbourne IT suffers some form of denial of service attack nearly every day but what it observed
in April 13, 2017 is more than a general attack.
In order to control the attack, the organization made use of international traffic
management protocols to take down the attack. Then also, it took 90 minutes to restore the
websites back to normal. It was identified that almost all the attack vectors associated with the
attack was from offshore and therefore the authorities planned to block the international traffics
as a mitigation approach to the problem (Coyne & Coyne, 2018). Thus the domestic visitors to
the website hosted by the Melbourne IT traffic had a little chance of accessing the compromised
websites between 10 am and 10.45 am (Somani et al., 2017). However, after blocking the
international traffic, the access to the website for the domestic visitors improved. This could have
been possible only after the attack vector that was blocking the website fell below 1 gigabyte per
second on around 11.30 am. After the attack was in control and the normal operation of the
website could be regained, the offshore traffic of the website, which was earlier blocked, was
unblocked as well. After the issues were resolved, the companies officially declared that the
issues have been resolved at around 12.30 pm. The magnitude of the DDoS attack had
considerably increased over the years and specially in 2016, its magnitude have increased.
As an effect of the attack, as many as 500,000 Australian websites were made
inaccessible for about 90 minutes. Melbourne IT DDoS attack is considered to be serious outage
as it surpassed the average waiting time of a particular traffic (Coyne & Coyne, 2018). The
authorities although directed all the network engineers to work on the problem as a priority, the
issue could be solved only after one and half hour. The mitigation services that have been
COMPUTER SECURITY
This attack is a proof that the incident breached the basic security requirements of a
network and the servers affecting a huge number of websites. It has been observed that
Melbourne IT suffers some form of denial of service attack nearly every day but what it observed
in April 13, 2017 is more than a general attack.
In order to control the attack, the organization made use of international traffic
management protocols to take down the attack. Then also, it took 90 minutes to restore the
websites back to normal. It was identified that almost all the attack vectors associated with the
attack was from offshore and therefore the authorities planned to block the international traffics
as a mitigation approach to the problem (Coyne & Coyne, 2018). Thus the domestic visitors to
the website hosted by the Melbourne IT traffic had a little chance of accessing the compromised
websites between 10 am and 10.45 am (Somani et al., 2017). However, after blocking the
international traffic, the access to the website for the domestic visitors improved. This could have
been possible only after the attack vector that was blocking the website fell below 1 gigabyte per
second on around 11.30 am. After the attack was in control and the normal operation of the
website could be regained, the offshore traffic of the website, which was earlier blocked, was
unblocked as well. After the issues were resolved, the companies officially declared that the
issues have been resolved at around 12.30 pm. The magnitude of the DDoS attack had
considerably increased over the years and specially in 2016, its magnitude have increased.
As an effect of the attack, as many as 500,000 Australian websites were made
inaccessible for about 90 minutes. Melbourne IT DDoS attack is considered to be serious outage
as it surpassed the average waiting time of a particular traffic (Coyne & Coyne, 2018). The
authorities although directed all the network engineers to work on the problem as a priority, the
issue could be solved only after one and half hour. The mitigation services that have been
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COMPUTER SECURITY
implemented tracked down the operation and the origin of the attack, on which the international
traffic management measures were implemented to eliminate the problem.
Conclusion
The report discusses the concept of distributed denial of service attack and illustrates its
working principle. The DDoS attacks are implemented with an aim of making the network
resources or network servers of company inaccessible for the legitimate users. The DDoS attack
although does not incorporate any malicious agent compromising any confidential data of the
company, it surely leads to the wastage of resources and time. It is a bit difficult to control a
DDoS attack mainly because it is very difficult to identify a legitimate request or a spam request.
The report discusses three most commonly methods of mitigation of DDoS attack. The report
further discusses a real example of DDoS attack that took place in April 13, 2016 and is known
as Melbourne IT attack. This attack compromised a number of systems and suspended the
number of Australian website for good 90 minutes. The attack was however mitigated by the
enforcing an international traffic management plan. The report discusses the issues associated
with the Melbourne IT attack.
COMPUTER SECURITY
implemented tracked down the operation and the origin of the attack, on which the international
traffic management measures were implemented to eliminate the problem.
Conclusion
The report discusses the concept of distributed denial of service attack and illustrates its
working principle. The DDoS attacks are implemented with an aim of making the network
resources or network servers of company inaccessible for the legitimate users. The DDoS attack
although does not incorporate any malicious agent compromising any confidential data of the
company, it surely leads to the wastage of resources and time. It is a bit difficult to control a
DDoS attack mainly because it is very difficult to identify a legitimate request or a spam request.
The report discusses three most commonly methods of mitigation of DDoS attack. The report
further discusses a real example of DDoS attack that took place in April 13, 2016 and is known
as Melbourne IT attack. This attack compromised a number of systems and suspended the
number of Australian website for good 90 minutes. The attack was however mitigated by the
enforcing an international traffic management plan. The report discusses the issues associated
with the Melbourne IT attack.

8
COMPUTER SECURITY
References
Coyne, A., & Coyne, A. (2018). Melbourne IT's DNS falls over in 'major outage'. Retrieved from
https://www.itnews.com.au/news/melbourne-its-dns-falls-over-in-major-outage-458235
Darwish, M., Ouda, A., & Capretz, L. F. (2013, June). Cloud-based DDoS attacks and defenses.
In Information Society (i-Society), 2013 International Conference on (pp. 67-71). IEEE.
Kotenko, I., & Ulanov, A. (2014). Agent-based simulation of DDOS attacks and defense
mechanisms. International Journal of Computing, 4(2), 113-123.
Lonea, A. M., Popescu, D. E., & Tianfield, H. (2013). Detecting DDoS attacks in cloud
computing environment. International Journal of Computers Communications &
Control, 8(1), 70-78.
Mousavi, S. M., & St-Hilaire, M. (2015, February). Early detection of DDoS attacks against
SDN controllers. In Computing, Networking and Communications (ICNC), 2015
International Conference on (pp. 77-81). IEEE.
Moustis, D., & Kotzanikolaou, P. (2013, July). Evaluating security controls against HTTP-based
DDoS attacks. In Information, intelligence, systems and applications (IISA), 2013 fourth
international conference on (pp. 1-6). IEEE.
Santanna, J. J., van Rijswijk-Deij, R., Hofstede, R., Sperotto, A., Wierbosch, M., Granville, L.
Z., & Pras, A. (2015, May). Booters—An analysis of DDoS-as-a-service attacks.
In Integrated Network Management (IM), 2015 IFIP/IEEE International Symposium
on (pp. 243-251). IEEE.
COMPUTER SECURITY
References
Coyne, A., & Coyne, A. (2018). Melbourne IT's DNS falls over in 'major outage'. Retrieved from
https://www.itnews.com.au/news/melbourne-its-dns-falls-over-in-major-outage-458235
Darwish, M., Ouda, A., & Capretz, L. F. (2013, June). Cloud-based DDoS attacks and defenses.
In Information Society (i-Society), 2013 International Conference on (pp. 67-71). IEEE.
Kotenko, I., & Ulanov, A. (2014). Agent-based simulation of DDOS attacks and defense
mechanisms. International Journal of Computing, 4(2), 113-123.
Lonea, A. M., Popescu, D. E., & Tianfield, H. (2013). Detecting DDoS attacks in cloud
computing environment. International Journal of Computers Communications &
Control, 8(1), 70-78.
Mousavi, S. M., & St-Hilaire, M. (2015, February). Early detection of DDoS attacks against
SDN controllers. In Computing, Networking and Communications (ICNC), 2015
International Conference on (pp. 77-81). IEEE.
Moustis, D., & Kotzanikolaou, P. (2013, July). Evaluating security controls against HTTP-based
DDoS attacks. In Information, intelligence, systems and applications (IISA), 2013 fourth
international conference on (pp. 1-6). IEEE.
Santanna, J. J., van Rijswijk-Deij, R., Hofstede, R., Sperotto, A., Wierbosch, M., Granville, L.
Z., & Pras, A. (2015, May). Booters—An analysis of DDoS-as-a-service attacks.
In Integrated Network Management (IM), 2015 IFIP/IEEE International Symposium
on (pp. 243-251). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
COMPUTER SECURITY
Somani, G., Gaur, M. S., Sanghi, D., Conti, M., Rajarajan, M., & Buyya, R. (2017). Combating
DDoS attacks in the cloud: requirements, trends, and future directions. IEEE Cloud
Computing, 4(1), 22-32.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Wang, H., Jia, Q., Fleck, D., Powell, W., Li, F., & Stavrou, A. (2014). A moving target DDoS
defense mechanism. Computer Communications, 46, 10-21.
Wong, F., & Tan, C. X. (2014). A survey of trends in massive DDoS attacks and cloud-based
mitigations. International Journal of Network Security & Its Applications, 6(3), 57.
Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed
denial of service (DDoS) flooding attacks. IEEE communications surveys &
tutorials, 15(4), 2046-2069.
COMPUTER SECURITY
Somani, G., Gaur, M. S., Sanghi, D., Conti, M., Rajarajan, M., & Buyya, R. (2017). Combating
DDoS attacks in the cloud: requirements, trends, and future directions. IEEE Cloud
Computing, 4(1), 22-32.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Wang, H., Jia, Q., Fleck, D., Powell, W., Li, F., & Stavrou, A. (2014). A moving target DDoS
defense mechanism. Computer Communications, 46, 10-21.
Wong, F., & Tan, C. X. (2014). A survey of trends in massive DDoS attacks and cloud-based
mitigations. International Journal of Network Security & Its Applications, 6(3), 57.
Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed
denial of service (DDoS) flooding attacks. IEEE communications surveys &
tutorials, 15(4), 2046-2069.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




