Comprehensive Report on DDOS Attacks and Mitigation Strategies
VerifiedAdded on 2022/09/30
|13
|2425
|20
Report
AI Summary
This report provides a comprehensive overview of Distributed Denial of Service (DDOS) attacks, a significant threat to information security. It begins with an executive summary and introduction, defining DDOS attacks as attempts to make computing resources unavailable by flooding them with illegitimate traffic. The report delves into the evolution of DDOS attacks, differentiating between traditional and low-rate attacks, including Shrew attacks and those targeting application servers. It explores real-world examples such as the 2016 Dyn attack, the 2015 GitHub attack, and the 2013 Spamhaus attack. The report concludes with key recommendations for mitigating DDOS attacks, emphasizing coding with security in mind, developing cyber incident response plans, keeping patches up to date, avoiding exposure of admin interfaces, and implementing strong authentication and authorization procedures. The report uses several references to support its claims and provide further research opportunities.

Information Security 1
Information Security
My Name
Course Title
Professor name
Date
Information Security
My Name
Course Title
Professor name
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
DDOS attacks are aimed at flooding the target machine with illegitimate traffic to ensure
their availability to legitimate users.The DDOS attacks have evolved from traditional DDOS, to
more low traffic DDOS attacks. All these attacks have been successful in the recent past
including the well executed Github attacks, Spamhaus attacks and Dyn attack. To ensure
companies become prepared for such attacks, the following key recommendations have been
identified,
First ensure the coding is done with security in mind using the SecSDLC.
Second,companies should develop cyber incident response plans and teams
Third,keep the patches up to date to avoid vulnerability exploitations
Fourth,don’t expose the admin interfaces as much as possible
Lastly, keep the computing environment secure using strong authentication and authorisation
procedure
DDOS attacks are aimed at flooding the target machine with illegitimate traffic to ensure
their availability to legitimate users.The DDOS attacks have evolved from traditional DDOS, to
more low traffic DDOS attacks. All these attacks have been successful in the recent past
including the well executed Github attacks, Spamhaus attacks and Dyn attack. To ensure
companies become prepared for such attacks, the following key recommendations have been
identified,
First ensure the coding is done with security in mind using the SecSDLC.
Second,companies should develop cyber incident response plans and teams
Third,keep the patches up to date to avoid vulnerability exploitations
Fourth,don’t expose the admin interfaces as much as possible
Lastly, keep the computing environment secure using strong authentication and authorisation
procedure

Executive Summary 2
Introduction 4
Body 5
Denial Of Service 5
Traditional distributed denial-of-service attack 6
Low Rate DDOS 7
Shrew attack 7
Reduction of Quality DDOS Attack 8
Low Rate DDOS against Application Server 8
Known Attacks 9
The 2016 Dyn attack 9
The 2015 GitHub attack 10
The 2013 Spamhaus attack 10
Conclusion 11
Recommendations 11
References 12
Introduction 4
Body 5
Denial Of Service 5
Traditional distributed denial-of-service attack 6
Low Rate DDOS 7
Shrew attack 7
Reduction of Quality DDOS Attack 8
Low Rate DDOS against Application Server 8
Known Attacks 9
The 2016 Dyn attack 9
The 2015 GitHub attack 10
The 2013 Spamhaus attack 10
Conclusion 11
Recommendations 11
References 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The advent of the Internet and cloud computing infrastructure have brought with it
varying benefits that include reduced costs of computing infrastre since the cloud computing
environments rely on virtualization technology to ensure efficiency in software, platform and
infrastructure deployments. This has made most organizations to move their computing resources
to the cloud to tap the benefits of this emerging technology (Behal, Kumar, & Sachdeva,
2018).Despite the enormous benefits that accrue to this migration, several security risks remains
key challenge to most organizations who employ the use of the Internet and the cloud. Key
among them include the denial of service which involves deliberate move by adversaries to to
make some computing resources unavailable by flooding the servers with useless requests. This
attacks must be dealt with if the various Internet based transactions are to reliable. In this report,
we focus on the details of the denial of service attacks by explaining in details what it is, giving
example of some well known attacks that have occured in the recent past and key
recommendations given in a bid to reduce the impact of such vulnerabilities (Tripathy,
Chamanbaz, & Bouffanais, 2019) .
The first section of the report provides the meaning of denial of service and dig deep into
the various types of DOS attacks. The second section details the some well documented DOS
attacks which have occurred in the recent past and the level of destruction such attacks have
caused the various industries which they occurred in. The third section concludes the report and
outlines some key steps that companies and organizations can take to reduce the impact of DOS
attacks in their computing environments.
The advent of the Internet and cloud computing infrastructure have brought with it
varying benefits that include reduced costs of computing infrastre since the cloud computing
environments rely on virtualization technology to ensure efficiency in software, platform and
infrastructure deployments. This has made most organizations to move their computing resources
to the cloud to tap the benefits of this emerging technology (Behal, Kumar, & Sachdeva,
2018).Despite the enormous benefits that accrue to this migration, several security risks remains
key challenge to most organizations who employ the use of the Internet and the cloud. Key
among them include the denial of service which involves deliberate move by adversaries to to
make some computing resources unavailable by flooding the servers with useless requests. This
attacks must be dealt with if the various Internet based transactions are to reliable. In this report,
we focus on the details of the denial of service attacks by explaining in details what it is, giving
example of some well known attacks that have occured in the recent past and key
recommendations given in a bid to reduce the impact of such vulnerabilities (Tripathy,
Chamanbaz, & Bouffanais, 2019) .
The first section of the report provides the meaning of denial of service and dig deep into
the various types of DOS attacks. The second section details the some well documented DOS
attacks which have occurred in the recent past and the level of destruction such attacks have
caused the various industries which they occurred in. The third section concludes the report and
outlines some key steps that companies and organizations can take to reduce the impact of DOS
attacks in their computing environments.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
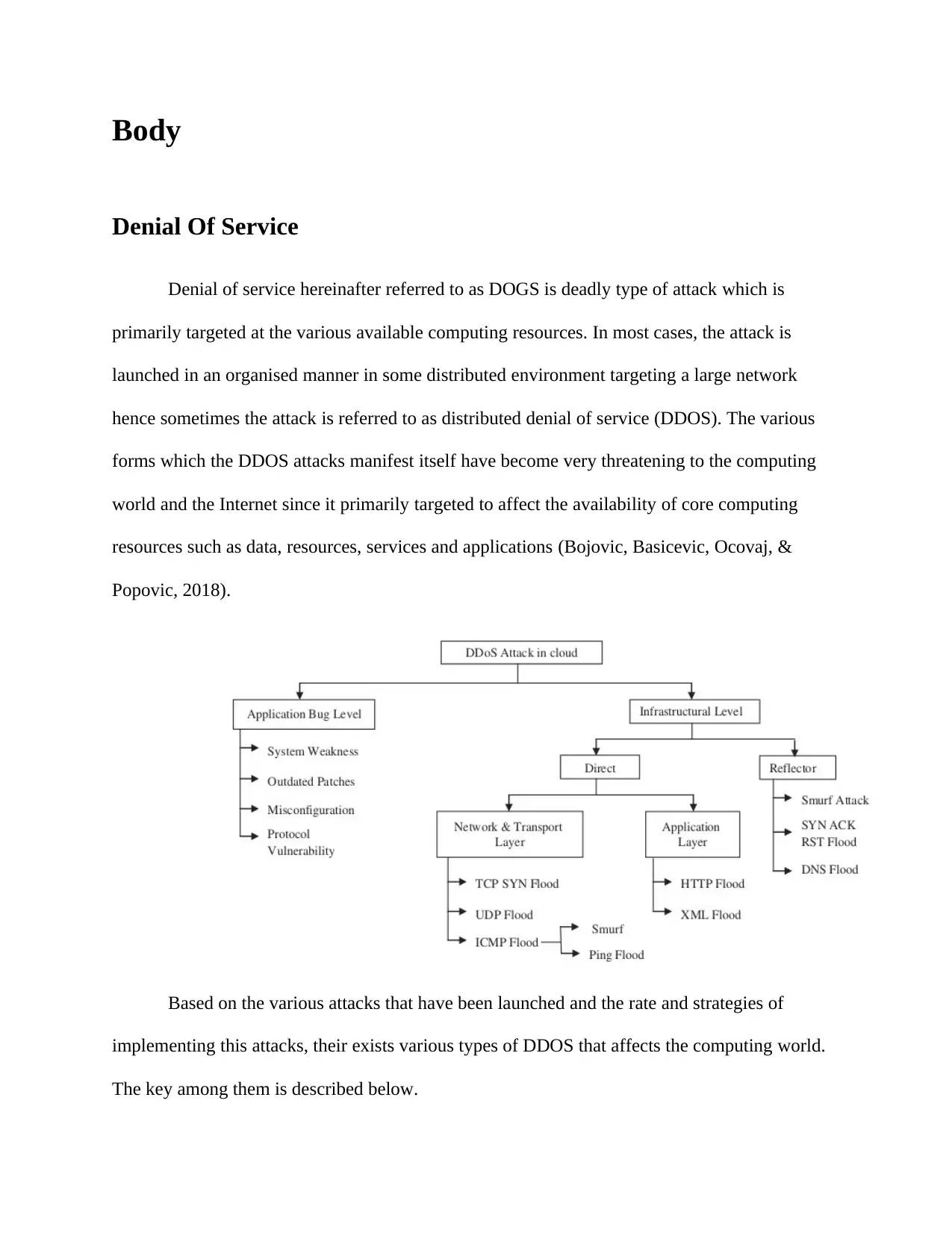
Body
Denial Of Service
Denial of service hereinafter referred to as DOGS is deadly type of attack which is
primarily targeted at the various available computing resources. In most cases, the attack is
launched in an organised manner in some distributed environment targeting a large network
hence sometimes the attack is referred to as distributed denial of service (DDOS). The various
forms which the DDOS attacks manifest itself have become very threatening to the computing
world and the Internet since it primarily targeted to affect the availability of core computing
resources such as data, resources, services and applications (Bojovic, Basicevic, Ocovaj, &
Popovic, 2018).
Based on the various attacks that have been launched and the rate and strategies of
implementing this attacks, their exists various types of DDOS that affects the computing world.
The key among them is described below.
Denial Of Service
Denial of service hereinafter referred to as DOGS is deadly type of attack which is
primarily targeted at the various available computing resources. In most cases, the attack is
launched in an organised manner in some distributed environment targeting a large network
hence sometimes the attack is referred to as distributed denial of service (DDOS). The various
forms which the DDOS attacks manifest itself have become very threatening to the computing
world and the Internet since it primarily targeted to affect the availability of core computing
resources such as data, resources, services and applications (Bojovic, Basicevic, Ocovaj, &
Popovic, 2018).
Based on the various attacks that have been launched and the rate and strategies of
implementing this attacks, their exists various types of DDOS that affects the computing world.
The key among them is described below.

Traditional distributed denial-of-service attack
This type of DDOS attack is normally orchestrated by means of flooding traffic which
originates from thousands of computing nodes which are normally compromised. This
compromised nodes is referred to as zombies. The zombies get coordinates and channel their
compromised traffic to attack the victim resource. In most of the traditional DDOS attacks, the
main aim of the attacker is to try and make the various target services go down so that the
legitimate users cannot use the service (Suciu, Pacho, Bartoli, & Vilajosana, 2019). Although
this attack has been successfully implemented in the past, the strategy suffers key weaknesses,
first, it is much easier to detect this attack by the various defence mechanisms employed by the
targeted organization due to the sheer amount of traffic spike involved, secondly, the attack's
success depends on the number of zombies involved. Due to this limitations, the attackers have
started migrating to new strategies that uses low amount of traffic. This new strategy is called
low rate DDOS and is described below.
Low Rate DDOS
This new form of DDOS attack is unique way of flooding the computing resources using
low rate traffic hence very much harder to detect using the current defence mechanism. Using
this mechanism, the attacker sends compromised packets at a very low rate making it very much
easier to evade the various defence mechanisms set by the company. Moreover, this strategy
does not require too much zombies hence very easier for the attacker to design and implement
(Hui, Kim, & Wang, 2017).
The main objective of this new DDOS attack to try and reduce the quality of service
which the legitimate users experiences at the organization’s network instead of flooding the
This type of DDOS attack is normally orchestrated by means of flooding traffic which
originates from thousands of computing nodes which are normally compromised. This
compromised nodes is referred to as zombies. The zombies get coordinates and channel their
compromised traffic to attack the victim resource. In most of the traditional DDOS attacks, the
main aim of the attacker is to try and make the various target services go down so that the
legitimate users cannot use the service (Suciu, Pacho, Bartoli, & Vilajosana, 2019). Although
this attack has been successfully implemented in the past, the strategy suffers key weaknesses,
first, it is much easier to detect this attack by the various defence mechanisms employed by the
targeted organization due to the sheer amount of traffic spike involved, secondly, the attack's
success depends on the number of zombies involved. Due to this limitations, the attackers have
started migrating to new strategies that uses low amount of traffic. This new strategy is called
low rate DDOS and is described below.
Low Rate DDOS
This new form of DDOS attack is unique way of flooding the computing resources using
low rate traffic hence very much harder to detect using the current defence mechanism. Using
this mechanism, the attacker sends compromised packets at a very low rate making it very much
easier to evade the various defence mechanisms set by the company. Moreover, this strategy
does not require too much zombies hence very easier for the attacker to design and implement
(Hui, Kim, & Wang, 2017).
The main objective of this new DDOS attack to try and reduce the quality of service
which the legitimate users experiences at the organization’s network instead of flooding the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

entire network with the aim of bringing the server down. Based on the various launching
strategies, their are different attack models that can be launched using the low rate traffic,namely
shrew attacks, reduction of quality attack, low rate DDOS designed against the application
server.
Shrew attack
The shrew attack is a special kind of low rate DDOS attacks in which the attacker
normally exploits the various vulnerabilities that exist in the TCP packet retransmission using
time out mechanisms. The main aim of the shrew attack is to ensure the various legitimateTCP
packets get blocked hence affecting the various applications that uses the TCP protocol. The
design involves ensures that anytime the TCP sender tries to make the recovery attempts from
any time out, the attacking machine immediately ensure that it sends low rate traffic to ensure the
link that sends the retransmission request is congested hence will be timed out again. Through
this approach, it makes it very difficult for any legitimate TCP packets to pass through (Feng,
Cetinkaya, Ishii, Tesi, & De Persis, 2018).
Reduction of Quality DDOS Attack
In order to ensure there is high availability, performance, reliability and efficiency, the
current system is set up to achieve this based on the various adaptations made. The key
adaptation procedure currently utilised by network designers is load balancing and admission
controls. Although such adaptation mechanism have yielded significant results, attackers have
successfully exploited vulnerabilities in this mechanism using the reduction of quality attacks .
The admission control is used to limit the number of requested that a given server can process at
strategies, their are different attack models that can be launched using the low rate traffic,namely
shrew attacks, reduction of quality attack, low rate DDOS designed against the application
server.
Shrew attack
The shrew attack is a special kind of low rate DDOS attacks in which the attacker
normally exploits the various vulnerabilities that exist in the TCP packet retransmission using
time out mechanisms. The main aim of the shrew attack is to ensure the various legitimateTCP
packets get blocked hence affecting the various applications that uses the TCP protocol. The
design involves ensures that anytime the TCP sender tries to make the recovery attempts from
any time out, the attacking machine immediately ensure that it sends low rate traffic to ensure the
link that sends the retransmission request is congested hence will be timed out again. Through
this approach, it makes it very difficult for any legitimate TCP packets to pass through (Feng,
Cetinkaya, Ishii, Tesi, & De Persis, 2018).
Reduction of Quality DDOS Attack
In order to ensure there is high availability, performance, reliability and efficiency, the
current system is set up to achieve this based on the various adaptations made. The key
adaptation procedure currently utilised by network designers is load balancing and admission
controls. Although such adaptation mechanism have yielded significant results, attackers have
successfully exploited vulnerabilities in this mechanism using the reduction of quality attacks .
The admission control is used to limit the number of requested that a given server can process at
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

a given time. The attacker can send illegitimate requests that is aimed at passing the limit set by
the server hence preventing legitimate requests from being processed. The load balancing
adaptation mechanism have been exploited by sending burst amount of traffic which are
normally unbalanced in a very short period of time. The impact of this normally leads to RoQ
attacks (Jamal, Haider, Butt, & Chohan, 2018).
Low Rate DDOS against Application Server
LoRDAS is a special type of DDOS that aims at exhausting the target resources by means of
sending low rate traffic. The only fundamental difference between LoRDAS and the shrew attack is the
protocol being targeted. Whereas the shrew attack targets the TCP protocol layer, the LoRDAS targets the
application layer of the TCP/IP. The RoQ normally is used due to the limitations of the adaptation
behaviours of the computing resources whereas the LoRDAS is targeted at service time patterns used by
the application server (Zhang, Wilkinson, Ganesan, & Oates, 2019)
Analysis
While DDOS attacks occures worldwide, the following data set map shows most attacks
the server hence preventing legitimate requests from being processed. The load balancing
adaptation mechanism have been exploited by sending burst amount of traffic which are
normally unbalanced in a very short period of time. The impact of this normally leads to RoQ
attacks (Jamal, Haider, Butt, & Chohan, 2018).
Low Rate DDOS against Application Server
LoRDAS is a special type of DDOS that aims at exhausting the target resources by means of
sending low rate traffic. The only fundamental difference between LoRDAS and the shrew attack is the
protocol being targeted. Whereas the shrew attack targets the TCP protocol layer, the LoRDAS targets the
application layer of the TCP/IP. The RoQ normally is used due to the limitations of the adaptation
behaviours of the computing resources whereas the LoRDAS is targeted at service time patterns used by
the application server (Zhang, Wilkinson, Ganesan, & Oates, 2019)
Analysis
While DDOS attacks occures worldwide, the following data set map shows most attacks
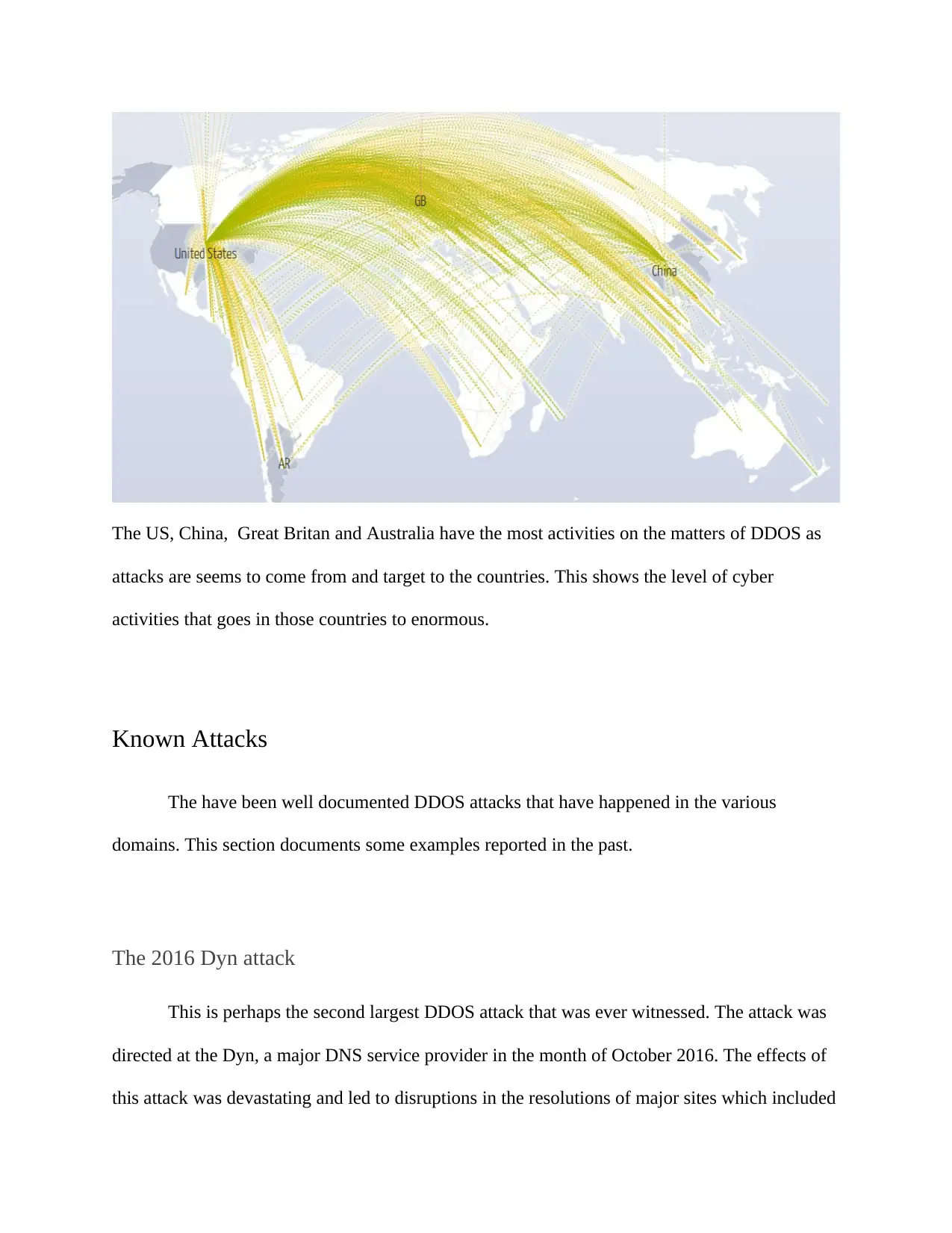
The US, China, Great Britan and Australia have the most activities on the matters of DDOS as
attacks are seems to come from and target to the countries. This shows the level of cyber
activities that goes in those countries to enormous.
Known Attacks
The have been well documented DDOS attacks that have happened in the various
domains. This section documents some examples reported in the past.
The 2016 Dyn attack
This is perhaps the second largest DDOS attack that was ever witnessed. The attack was
directed at the Dyn, a major DNS service provider in the month of October 2016. The effects of
this attack was devastating and led to disruptions in the resolutions of major sites which included
attacks are seems to come from and target to the countries. This shows the level of cyber
activities that goes in those countries to enormous.
Known Attacks
The have been well documented DDOS attacks that have happened in the various
domains. This section documents some examples reported in the past.
The 2016 Dyn attack
This is perhaps the second largest DDOS attack that was ever witnessed. The attack was
directed at the Dyn, a major DNS service provider in the month of October 2016. The effects of
this attack was devastating and led to disruptions in the resolutions of major sites which included
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the AirBnB, PayPal, Amazon, Visa and Netflix. The attack was achieved by the help of a
malware called Mirai. The Mirai malware creates zombies from IoT devices including camera,
radio, printers and smart TV. The zombies were programmed to send compromised traffic to the
single target. Dyn took one day to resolve the issues and the Hacktivist group claimed
responsibility although they claimed was not verifiable (Shah & Nagaraja, 2018).
The 2015 GitHub attack
This is perhaps the largest DDOS attack that was ever witnessed and was targeted to the
Github. This attack took several days to resolve and majority of the traffic originated from China
and their are links to suggest the Chinese government was behind the attack. The attack was
motivated by need to circumvent some two projects on the Github server which was aimed at
reducing chinese censorship. The attack was a means of blackmailing Github to eliminate those
projects. The Great Firewall of China might have been used to compromise traffic going to
Github (Tiloca, Gehrmann, & Seitz, 2017).
The 2013 Spamhaus attack
Another DDOS attack that was highly reported was the 2013 attack targeted at the
Spamhaus, a spam fighting organization. The spamhaus infrastructure is responsible for filtering
of oiver 80% of the spam traffic which makes them very ideal target for scammers. The traffic
race 300gbps and forced spamhaus to sign up for cloudflare. Cloudflare DDOS protection
programmes was able to mitigate the attack. This attack turns out to have been initiated by a
malware called Mirai. The Mirai malware creates zombies from IoT devices including camera,
radio, printers and smart TV. The zombies were programmed to send compromised traffic to the
single target. Dyn took one day to resolve the issues and the Hacktivist group claimed
responsibility although they claimed was not verifiable (Shah & Nagaraja, 2018).
The 2015 GitHub attack
This is perhaps the largest DDOS attack that was ever witnessed and was targeted to the
Github. This attack took several days to resolve and majority of the traffic originated from China
and their are links to suggest the Chinese government was behind the attack. The attack was
motivated by need to circumvent some two projects on the Github server which was aimed at
reducing chinese censorship. The attack was a means of blackmailing Github to eliminate those
projects. The Great Firewall of China might have been used to compromise traffic going to
Github (Tiloca, Gehrmann, & Seitz, 2017).
The 2013 Spamhaus attack
Another DDOS attack that was highly reported was the 2013 attack targeted at the
Spamhaus, a spam fighting organization. The spamhaus infrastructure is responsible for filtering
of oiver 80% of the spam traffic which makes them very ideal target for scammers. The traffic
race 300gbps and forced spamhaus to sign up for cloudflare. Cloudflare DDOS protection
programmes was able to mitigate the attack. This attack turns out to have been initiated by a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

British teenage hacker who was sort after and paid to launch a DDOS attack (Rajeev Singh & T.
P. Sharma, 2019)
Conclusion
In conclusion, DDOS attacks are very serious security breaches which companies must put in the
necessary resources to thwart. The various DDOS attack mechanisms have mutated over time
and current rely on slow stealth mode to ensure non detection by current defence mechanism.
The following are some key strategies which can be deployed to reduce the impacts of DDOS.
Recommendations
Key recommendation to thwart DDOS includes;
i. Coding with security at the back of the mind
ii. Development of cyber incident response plans and teams
iii. Ensure patches are up to date
iv. Avoid exposing the admin interfaces to the outside world
v. Limit access to the internal network by strong authentication and authorisation
procedures
P. Sharma, 2019)
Conclusion
In conclusion, DDOS attacks are very serious security breaches which companies must put in the
necessary resources to thwart. The various DDOS attack mechanisms have mutated over time
and current rely on slow stealth mode to ensure non detection by current defence mechanism.
The following are some key strategies which can be deployed to reduce the impacts of DDOS.
Recommendations
Key recommendation to thwart DDOS includes;
i. Coding with security at the back of the mind
ii. Development of cyber incident response plans and teams
iii. Ensure patches are up to date
iv. Avoid exposing the admin interfaces to the outside world
v. Limit access to the internal network by strong authentication and authorisation
procedures

References
Behal, S., Kumar, K., & Sachdeva, M. (2018). A generalized detection system to detect
distributed denial of service attacks and flash events for information theory metrics.
Turkish Journal of Electrical Engineering & Computer Sciences, 26(4), 1759–1770.
Bojovic, P. D., Basicevic, I., Ocovaj, S., & Popovic, M. (2018). A practical approach to detection
of distributed denial-of-service attacks using a hybrid detection method.
Feng, S., Cetinkaya, A., Ishii, H., Tesi, P., & De Persis, C. (2018). Data Rates for Stabilizing
Control under Denial-of-Service Attacks.
Hui, K.-L., Kim, S. H., & Wang, Q.-H. (2017). Cybercrime Deterrence and International
Legislation: Evidence from Distributed Denial of Service Attacks. MIS Quarterly, 41(2),
497-A11.
Jamal, T., Haider, Z., Butt, S. A., & Chohan, A. (2018). Denial of Service Attack in Cooperative
Networks.
Rajeev Singh, & T. P. Sharma. (2019). Present Status of Distributed Denial of Service (DDoS)
Attacks in Internet World. International Journal of Mathematical, Engineering and
Management Sciences, (4), 1008.
Shah, R., & Nagaraja, S. (2018). Do we have the time for IRM?: Service denial attacks and
SDN-based defences.
Suciu, I., Pacho, J. C., Bartoli, A., & Vilajosana, X. (2019). Authenticated Preambles for Denial
of Service Mitigation in LPWANs.
Tiloca, M., Gehrmann, C., & Seitz, L. (2017). On improving resistance to Denial of Service and
key provisioning scalability of the DTLS handshake. International Journal of Information
Security, 16(2), 173–193.
Behal, S., Kumar, K., & Sachdeva, M. (2018). A generalized detection system to detect
distributed denial of service attacks and flash events for information theory metrics.
Turkish Journal of Electrical Engineering & Computer Sciences, 26(4), 1759–1770.
Bojovic, P. D., Basicevic, I., Ocovaj, S., & Popovic, M. (2018). A practical approach to detection
of distributed denial-of-service attacks using a hybrid detection method.
Feng, S., Cetinkaya, A., Ishii, H., Tesi, P., & De Persis, C. (2018). Data Rates for Stabilizing
Control under Denial-of-Service Attacks.
Hui, K.-L., Kim, S. H., & Wang, Q.-H. (2017). Cybercrime Deterrence and International
Legislation: Evidence from Distributed Denial of Service Attacks. MIS Quarterly, 41(2),
497-A11.
Jamal, T., Haider, Z., Butt, S. A., & Chohan, A. (2018). Denial of Service Attack in Cooperative
Networks.
Rajeev Singh, & T. P. Sharma. (2019). Present Status of Distributed Denial of Service (DDoS)
Attacks in Internet World. International Journal of Mathematical, Engineering and
Management Sciences, (4), 1008.
Shah, R., & Nagaraja, S. (2018). Do we have the time for IRM?: Service denial attacks and
SDN-based defences.
Suciu, I., Pacho, J. C., Bartoli, A., & Vilajosana, X. (2019). Authenticated Preambles for Denial
of Service Mitigation in LPWANs.
Tiloca, M., Gehrmann, C., & Seitz, L. (2017). On improving resistance to Denial of Service and
key provisioning scalability of the DTLS handshake. International Journal of Information
Security, 16(2), 173–193.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




