CSC8419 - Cryptography and Security: Digital Certificates with OpenSSL
VerifiedAdded on 2024/05/29
|14
|1389
|406
Practical Assignment
AI Summary
This assignment solution for CSC8419 - Cryptography and Security, addresses several key tasks. First, it details the process of verifying a Debian DVD ISO image by comparing signatures, using tools like GNU Privacy Guard. Second, it outlines the steps for generating a shared secret key using encoded text formats and public parameters. Third, it focuses on generating digital certificates using OpenSSL, explaining the purpose, benefits, and limitations of digital certificates, as well as the steps involved in their creation. The assignment emphasizes the importance of trusted authorities in certificate validation and the role of OpenSSL in securing web communications.

CSC8419 - CRYPTOGRAPHY AND SECURITY - ASSIGNMENT 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................5
Task 3.........................................................................................................................................9
Task 4.......................................................................................................................................10
References................................................................................................................................13
1
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................5
Task 3.........................................................................................................................................9
Task 4.......................................................................................................................................10
References................................................................................................................................13
1

Task 1
Debian DVD ISO image’s verification process
From the link https://goo.gl/8CNeyc, the required data has been downloaded and ISO image
has been checked for their completeness by comparing the signatures as follows.
List and save all the file in the directory at the correct place
For the MD5, correct signature must be verified using the free tool named as GNU
Privacy Guard
ID= 6294BE9B has been extracted from running the above command where public
key is not available. The reason for non-availability is that the command runs for the
first time. To retrieve the public keys, following steps are done.
Now from the server of Debian Key, the public key can be downloaded using the ID
“6294BE9B”
2
Debian DVD ISO image’s verification process
From the link https://goo.gl/8CNeyc, the required data has been downloaded and ISO image
has been checked for their completeness by comparing the signatures as follows.
List and save all the file in the directory at the correct place
For the MD5, correct signature must be verified using the free tool named as GNU
Privacy Guard
ID= 6294BE9B has been extracted from running the above command where public
key is not available. The reason for non-availability is that the command runs for the
first time. To retrieve the public keys, following steps are done.
Now from the server of Debian Key, the public key can be downloaded using the ID
“6294BE9B”
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

For the checksum files, there will be verification of their signatures
The confirmation of the authenticity is stated by the appearance of the statement as
“Good signature from "Debian CD signing key <debian-cd@lists.debian.org>”. The
comparison with the list given in https://www.debian.org/CD/verify is done with the
help of generated fingerprint key as DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D
6294 BE9B.
3
The confirmation of the authenticity is stated by the appearance of the statement as
“Good signature from "Debian CD signing key <debian-cd@lists.debian.org>”. The
comparison with the list given in https://www.debian.org/CD/verify is done with the
help of generated fingerprint key as DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D
6294 BE9B.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
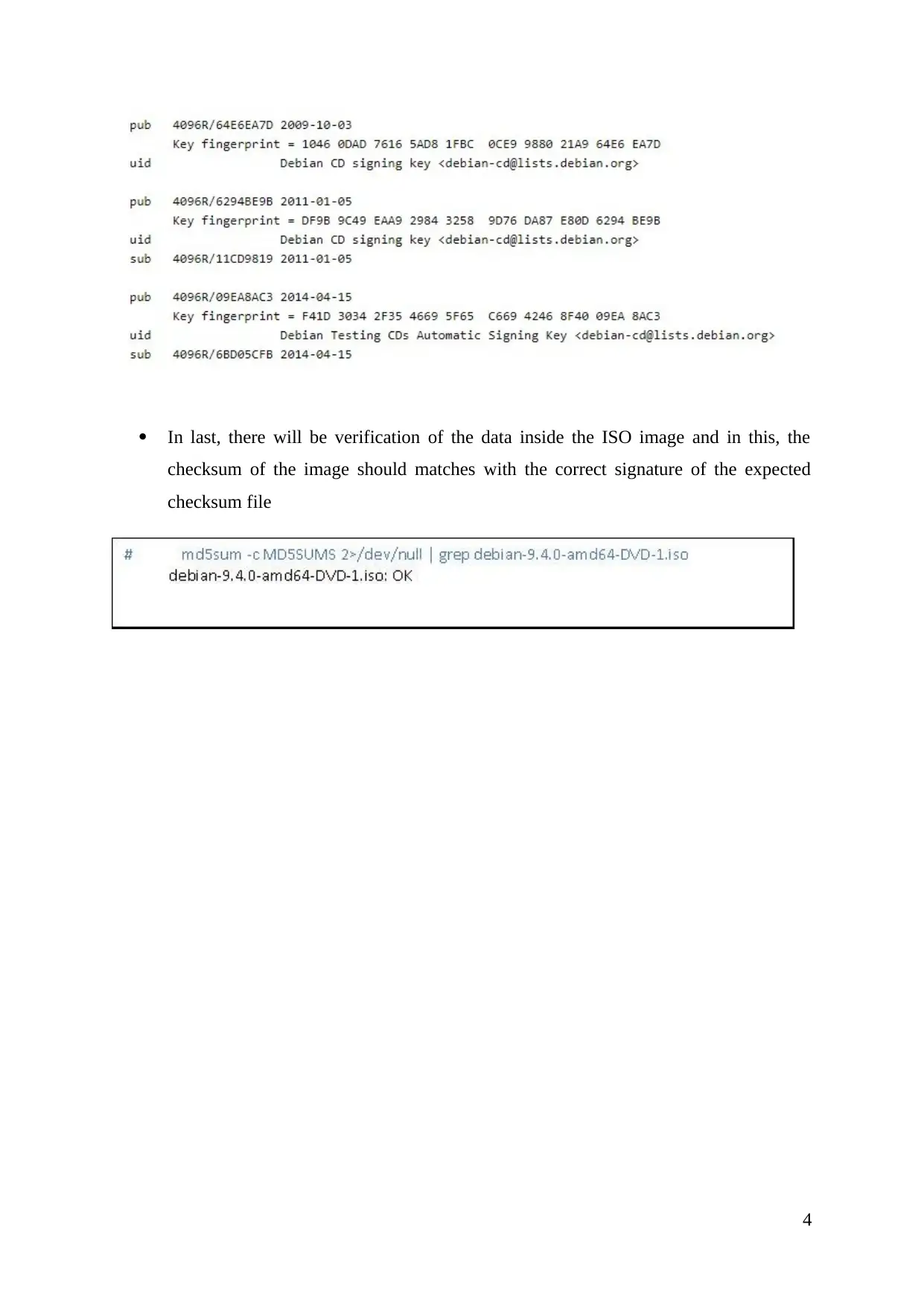
In last, there will be verification of the data inside the ISO image and in this, the
checksum of the image should matches with the correct signature of the expected
checksum file
4
checksum of the image should matches with the correct signature of the expected
checksum file
4
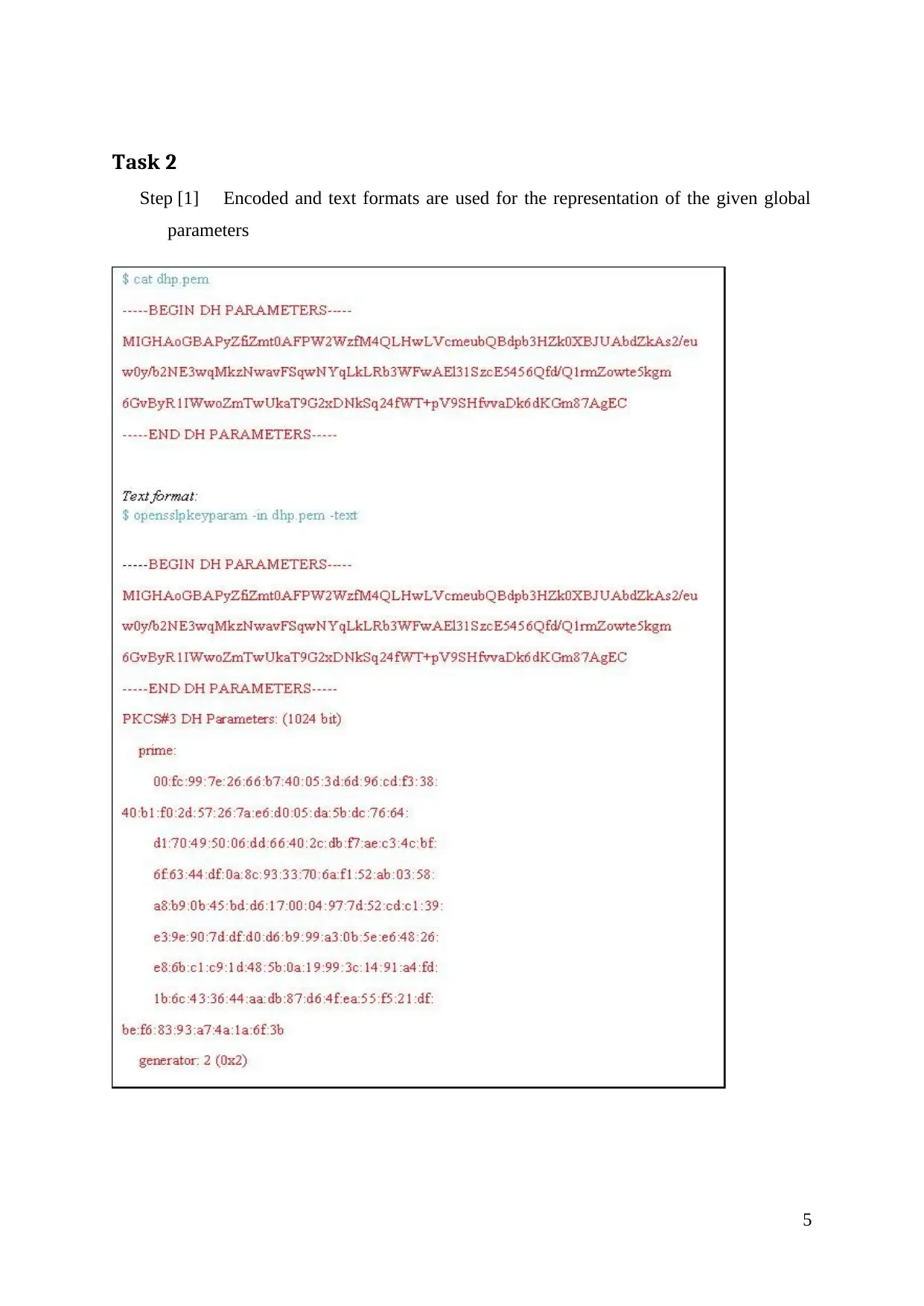
Task 2
Step [1] Encoded and text formats are used for the representation of the given global
parameters
5
Step [1] Encoded and text formats are used for the representation of the given global
parameters
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
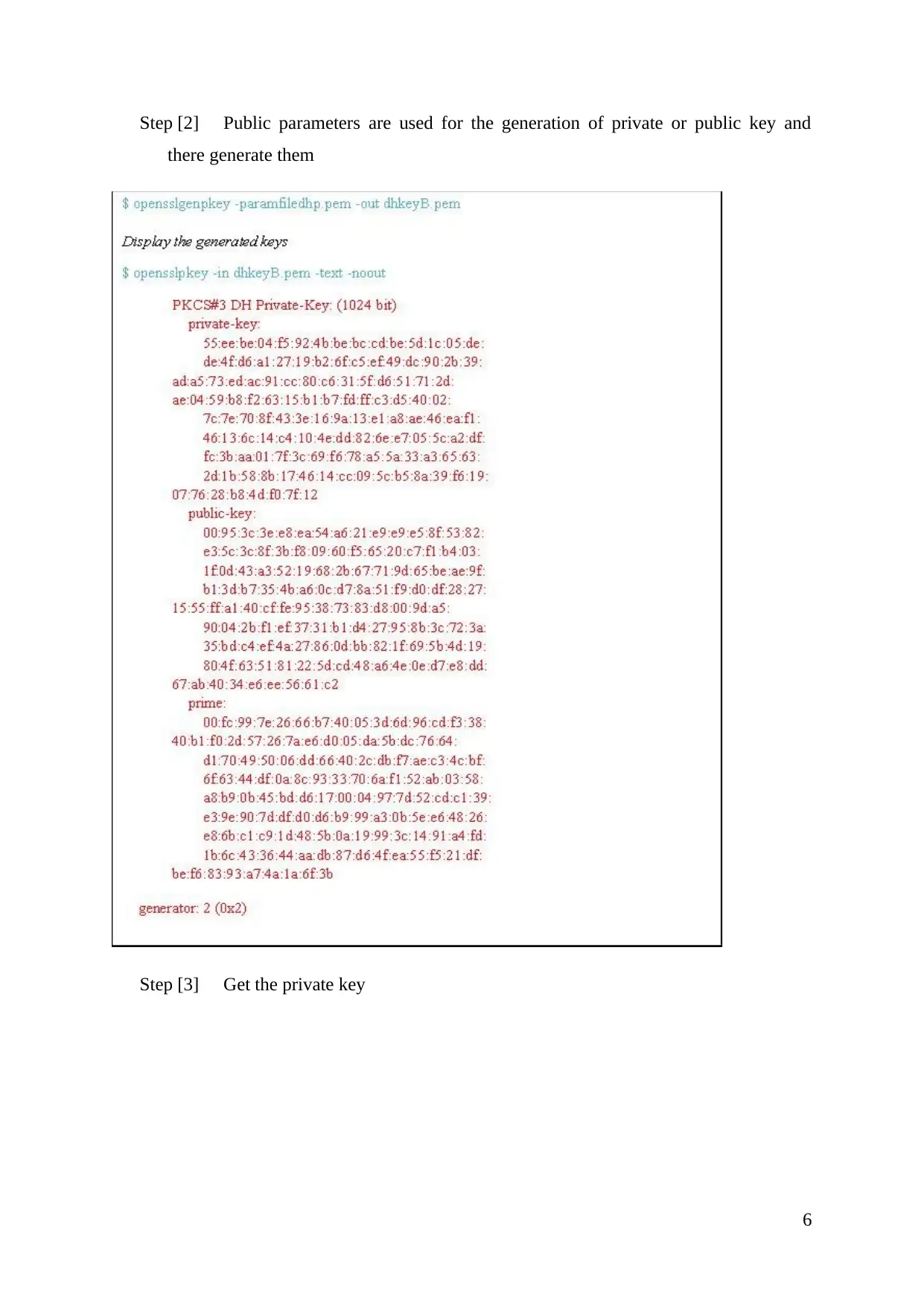
Step [2] Public parameters are used for the generation of private or public key and
there generate them
Step [3] Get the private key
6
there generate them
Step [3] Get the private key
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Step [4] All parameters are now set for the generation of the shared secret key. This
generation is occurred with the help of instructor’s private and public key
7
generation is occurred with the help of instructor’s private and public key
7

Step [5] Finally, the generated shared key should be equivalent and matches the key
generated at the side of the instructor and it must be correct secret key
8
generated at the side of the instructor and it must be correct secret key
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 3
9
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 4
‘Using OpenSSL to generate the Digital certificates’
Abstract
Digital Certificates are digital form of recognition and identification just like driver license.
With the help of digital certificates, it is easy to gather the information regarding the entity
whose certificate is this. The verification and validation of the certificates from the trusted
authority guarantees the validation of the information supported by the certificates. The
owner of the certificate and the private must have to protect the associated private key.
Website runs using the internet connection and they are configured with HTTP using the
digital certificates. OpenSSL tool helps in developing such certificates for several systems
(Zhu and Lin, 2016).
Introduction
Digital Certificates are important for the identification of any person or business so that they
must have identity for identification. Here the research has been done on the digital
certificates and how it can be developed using the OpenSSL Tool.
Digital certificates
Digital certificates are the public key certificates and are actually electronic documents which
are used to verify the identity of a person or business in the market. Every certificate is
created using specific content and format. The information included in the certificate are
regarding the issued person or business, certifying authority, valid date and any restriction on
the use (Bort, 2014).
OpenSSL
OpenSSL is the tool for the Transport Layer Security and Secure Sockets Layer (SSL)
Protocols which is highly robust and commercially upgraded. This tool is a licensed under
Apache-style License. For simple license condition, it can be used in free for the commercial
and non-commercial purpose (Chandrasekar, et-al, 2017).
Purpose of Digital Certificates
10
‘Using OpenSSL to generate the Digital certificates’
Abstract
Digital Certificates are digital form of recognition and identification just like driver license.
With the help of digital certificates, it is easy to gather the information regarding the entity
whose certificate is this. The verification and validation of the certificates from the trusted
authority guarantees the validation of the information supported by the certificates. The
owner of the certificate and the private must have to protect the associated private key.
Website runs using the internet connection and they are configured with HTTP using the
digital certificates. OpenSSL tool helps in developing such certificates for several systems
(Zhu and Lin, 2016).
Introduction
Digital Certificates are important for the identification of any person or business so that they
must have identity for identification. Here the research has been done on the digital
certificates and how it can be developed using the OpenSSL Tool.
Digital certificates
Digital certificates are the public key certificates and are actually electronic documents which
are used to verify the identity of a person or business in the market. Every certificate is
created using specific content and format. The information included in the certificate are
regarding the issued person or business, certifying authority, valid date and any restriction on
the use (Bort, 2014).
OpenSSL
OpenSSL is the tool for the Transport Layer Security and Secure Sockets Layer (SSL)
Protocols which is highly robust and commercially upgraded. This tool is a licensed under
Apache-style License. For simple license condition, it can be used in free for the commercial
and non-commercial purpose (Chandrasekar, et-al, 2017).
Purpose of Digital Certificates
10

The purpose of the digital certificate includes:
Creation of owners identity
Makes the availability of the owner’s public key
A trusted authority is always involved in the certification of the digital certificates. Every
certificate has its limited range of time. Replacement of the digital certificates is required
after the expiry of the existing digital certificate.
Process of generation
For generation of the digital certificates following steps are followed:
Step [1] Create certificate signing request or CSR from the certified authority in
addition to it entries must be filled
Step [2] For the generation of the password, set the commands for password for
security
Step [3] In order to save the private key, create the key file for storage
Step [4] After request command and generation of private key, generate the X.509
digital certificates using the OPENSSL
Step [5] Now, generate the certificate for the person in addition to password and the
private key using OPENSSL
Step [6] Generate the encoded public key which only contains the public key which
requires no password
Step [7] Verify the certificates from trusted authority using OPENSSL (SAS, 2018)
Benefits
End users have minimum involvement in the digital certificates
There is no requirement of extra hardware
No requirement of backup plan
Easy accessibility of multiple devices
Scalability can be analysed to accommodate the business growth
Supported by multiple company’s applications and networks
Provides global level security (García, et-al, 2015)
Limitations
11
Creation of owners identity
Makes the availability of the owner’s public key
A trusted authority is always involved in the certification of the digital certificates. Every
certificate has its limited range of time. Replacement of the digital certificates is required
after the expiry of the existing digital certificate.
Process of generation
For generation of the digital certificates following steps are followed:
Step [1] Create certificate signing request or CSR from the certified authority in
addition to it entries must be filled
Step [2] For the generation of the password, set the commands for password for
security
Step [3] In order to save the private key, create the key file for storage
Step [4] After request command and generation of private key, generate the X.509
digital certificates using the OPENSSL
Step [5] Now, generate the certificate for the person in addition to password and the
private key using OPENSSL
Step [6] Generate the encoded public key which only contains the public key which
requires no password
Step [7] Verify the certificates from trusted authority using OPENSSL (SAS, 2018)
Benefits
End users have minimum involvement in the digital certificates
There is no requirement of extra hardware
No requirement of backup plan
Easy accessibility of multiple devices
Scalability can be analysed to accommodate the business growth
Supported by multiple company’s applications and networks
Provides global level security (García, et-al, 2015)
Limitations
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





