Debian ISO Verification and Encryption Standards: AES vs DES Analysis
VerifiedAdded on 2024/05/29
|10
|1178
|474
Report
AI Summary
This report details the process of verifying a Debian DVD ISO image using checksums and signatures. It further explores encryption standards, specifically comparing AES (Advanced Encryption Standard) and DES (Data Encryption Standard). The report outlines the advantages and disadvantages of both AES and DES, highlighting AES as a more secure and efficient modern encryption method, recommended as a replacement for DES. The document also touches upon the practical steps involved in key generation and shared secret key creation. Desklib provides students access to this and other solved assignments for learning.

Contents
Task 1: Verification of Debian DVD ISO image............................................................................2
Task B..............................................................................................................................................4
Task D..............................................................................................................................................5
References........................................................................................................................................7
Task 1: Verification of Debian DVD ISO image............................................................................2
Task B..............................................................................................................................................4
Task D..............................................................................................................................................5
References........................................................................................................................................7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 1: Verification of Debian DVD ISO image
A link is given that is https://goo.gl/8CNeyc from where all file can get downloaded. It even
contains a long ISO image along with some of its signature-based files including MD5 for
gaining completeness.
Initially, to bring everything in right place we need to assure that all files must be listed in
the dictionary.
Secondly, by using GNU Privacy Guard (gpg) that is free, the correctness of signature is
checked and this is also done for MD5 that’s why
Thirdly, using ID “6294BE9B” public key can be downloaded which is the key ring
server of Debian.
Both of the checksums files signatures can now be verified.
A link is given that is https://goo.gl/8CNeyc from where all file can get downloaded. It even
contains a long ISO image along with some of its signature-based files including MD5 for
gaining completeness.
Initially, to bring everything in right place we need to assure that all files must be listed in
the dictionary.
Secondly, by using GNU Privacy Guard (gpg) that is free, the correctness of signature is
checked and this is also done for MD5 that’s why
Thirdly, using ID “6294BE9B” public key can be downloaded which is the key ring
server of Debian.
Both of the checksums files signatures can now be verified.

A line states that “Good signature from "Debian CD signing key<debian-cd@lists.debian.org>“
approves Debian DVD image authenticity. We can even use some key fingerprints generated that
is: DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B and is finally compared with
the listed once in the provided link https://www.debian.org/CD/verify, this comparison
determines whether the key fingerprints matches with it.
Lastly, the content provided in the image of ISO can be verified so as to check the
checksum matches of ISO images with those expected in files of checksums.
approves Debian DVD image authenticity. We can even use some key fingerprints generated that
is: DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B and is finally compared with
the listed once in the provided link https://www.debian.org/CD/verify, this comparison
determines whether the key fingerprints matches with it.
Lastly, the content provided in the image of ISO can be verified so as to check the
checksum matches of ISO images with those expected in files of checksums.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
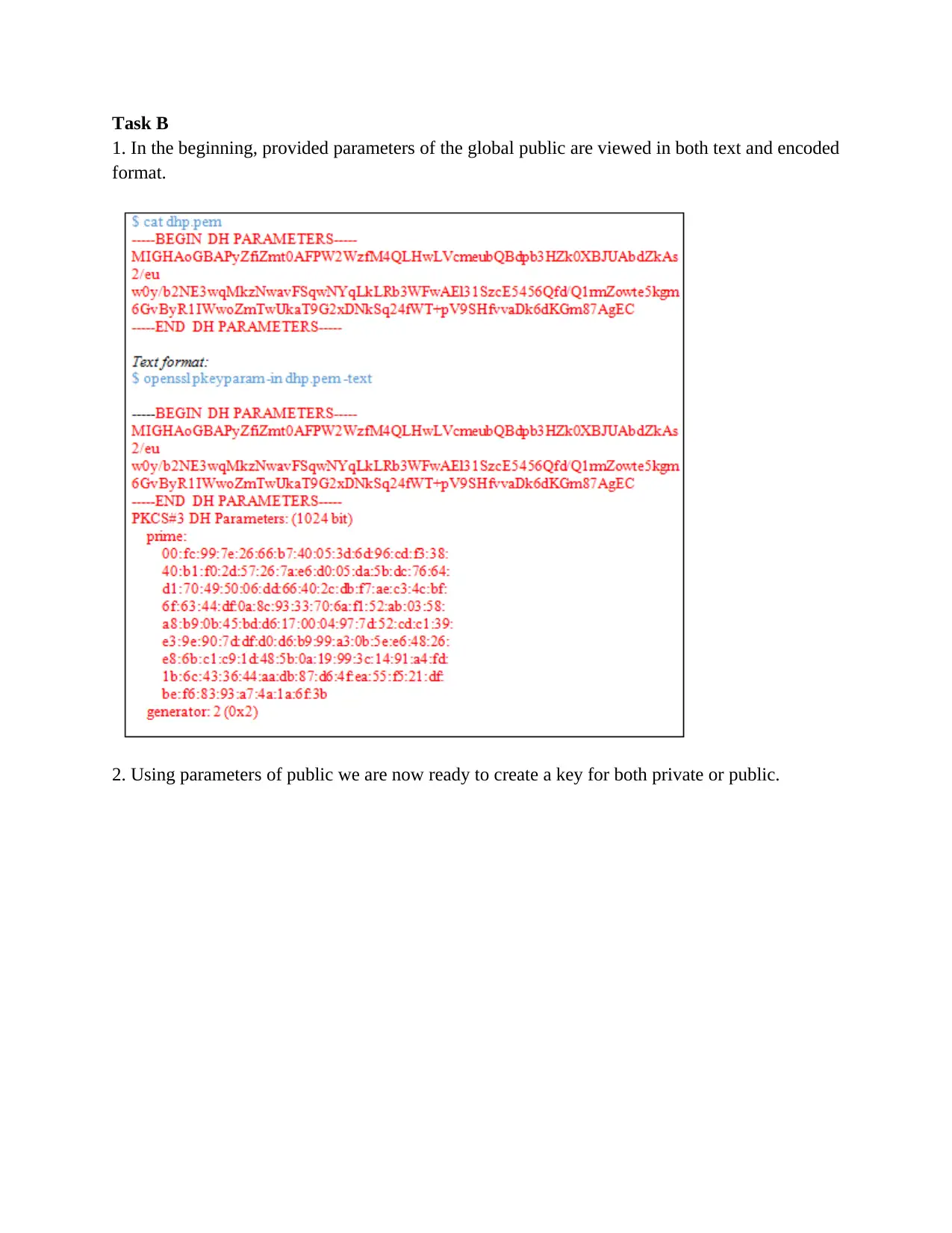
Task B
1. In the beginning, provided parameters of the global public are viewed in both text and encoded
format.
2. Using parameters of public we are now ready to create a key for both private or public.
1. In the beginning, provided parameters of the global public are viewed in both text and encoded
format.
2. Using parameters of public we are now ready to create a key for both private or public.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. The further step is extracting the key for the public.
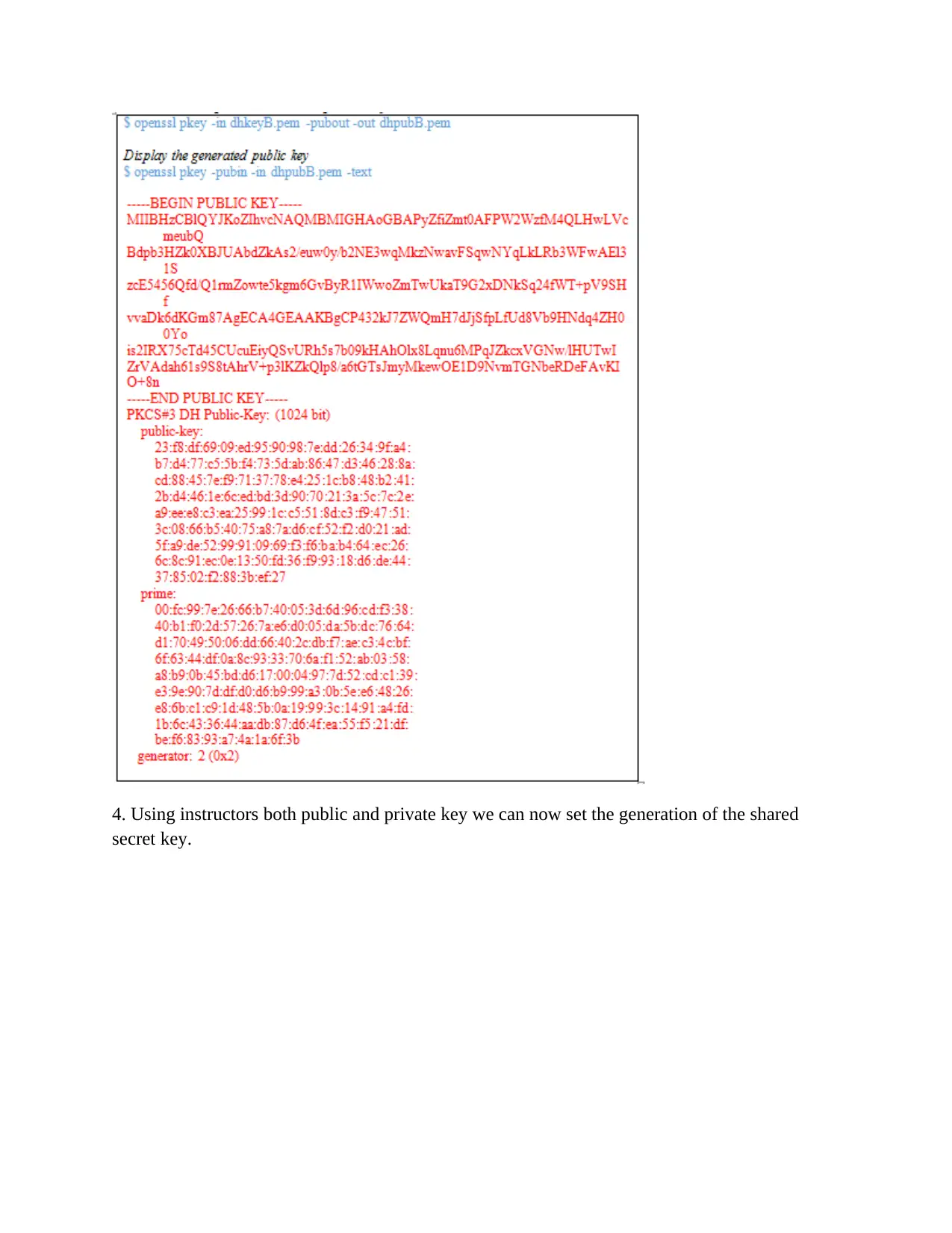
4. Using instructors both public and private key we can now set the generation of the shared
secret key.
secret key.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5. Here both generated a shared key and the side for instructor must be same for the generation
of the shared secret key.
of the shared secret key.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task D
DES (Data Encryption Standard) and AES (Advanced Encryption Standard)
Abstract
Both AES and DES are generally called as block cipher which is symmetric and AES was
introduced to conquer all shortcoming of DES. Though DES are of key size that is smaller and
permits less security to beat these triple introduced DES but instead of that it turned out to be
slow. Later, AES was announced along with its difference with DES. The fundamental
difference among them is that AES processes the entire block to accomplish cipher text. On the
other hand DES segregates the plain text block into two different halves depending on the
beginning of algorithm (Luken, Ouyang and Desoky, 2009).
Introduction
It properly describes both AES and DES along with their advantages as well as disadvantages.
The major issues arise while making a choice whether to encrypt the network data for both AES
and DES encryption algorithm as it is a matter of security.
DES
DES is defined as symmetric block cipher also called as shared secret key that have a key length
of 56 bits. DES encryption was originally developed by the federal government with respect to
extend communications of government using cryptographic security. To describe the DES
inadequacy and reasons why in important systems is must not be able to utilise it. It is funded
with many challenges to visualise the taken time to decrypt the message.
DES work has a principle of Feistel cipher structure along with plaintext having size as 64 bits.
DES when compare to AES has key size smaller and is slower comparatively, containing small
key that behaves to be less safe and secure (Sivakumar, Balakumar and Pandeeswaran, 2018).
DES Advantages
It encounters during interfacing with commercial products and the legacy services.
It acts as predecessor that encrypts using key of 56-bit having blocks of 64-bit.
Its key length can be extended using operations of 3 that applies 0 and 2 key encryption
along with 1 key decryption.
DES Disadvantages
Encryption creates vulnerability in security.
A relation may exist between three keys.
The entire key length of it is only 56 bits.
DES (Data Encryption Standard) and AES (Advanced Encryption Standard)
Abstract
Both AES and DES are generally called as block cipher which is symmetric and AES was
introduced to conquer all shortcoming of DES. Though DES are of key size that is smaller and
permits less security to beat these triple introduced DES but instead of that it turned out to be
slow. Later, AES was announced along with its difference with DES. The fundamental
difference among them is that AES processes the entire block to accomplish cipher text. On the
other hand DES segregates the plain text block into two different halves depending on the
beginning of algorithm (Luken, Ouyang and Desoky, 2009).
Introduction
It properly describes both AES and DES along with their advantages as well as disadvantages.
The major issues arise while making a choice whether to encrypt the network data for both AES
and DES encryption algorithm as it is a matter of security.
DES
DES is defined as symmetric block cipher also called as shared secret key that have a key length
of 56 bits. DES encryption was originally developed by the federal government with respect to
extend communications of government using cryptographic security. To describe the DES
inadequacy and reasons why in important systems is must not be able to utilise it. It is funded
with many challenges to visualise the taken time to decrypt the message.
DES work has a principle of Feistel cipher structure along with plaintext having size as 64 bits.
DES when compare to AES has key size smaller and is slower comparatively, containing small
key that behaves to be less safe and secure (Sivakumar, Balakumar and Pandeeswaran, 2018).
DES Advantages
It encounters during interfacing with commercial products and the legacy services.
It acts as predecessor that encrypts using key of 56-bit having blocks of 64-bit.
Its key length can be extended using operations of 3 that applies 0 and 2 key encryption
along with 1 key decryption.
DES Disadvantages
Encryption creates vulnerability in security.
A relation may exist between three keys.
The entire key length of it is only 56 bits.

64 bits is the size of the block (Eichlseder, 2007).
AES
AES is defined as symmetric block cipher that was published by National Institute of standards
and technology in 2001. It was also announced to replace DES as it was slower and have smaller
cipher key.
It has secret key of 128-bit and plaintext of 128-bit which cumulatively forms 128-bit block
represented as a matrix of 4*4 that undergoes transformation.
Advantages of AES
It is a cryptographic algorithm that is effective and mathematically more elegant.
It provides choices to user like 256-bit key, 192-bit or 128-bit key.
It is safe and secure.
Disadvantages of AES
It uses algebraic structure that is simple.
Software is difficult to be executed.
In similar way every block used to be encrypted (Daemen and Rijmen, 2013).
Recommendation
AES is introduced as replacement of DES as an algorithm with standard symmetric encryption
for organisation of US federal. AES uses blocks of 128-bit and can even accept bits of 256, 192
or 128 range. AES is effective for both software and hardware. Basically, out of both AES is
best.
Conclusion
DES is defined as algorithm that is older whereas AES is defined as algorithm that is advanced.
AES is more secure and faster as compared to DES. AES is unbreakable and strong using
substitution-permutation and on the other hand DES is breakable and using structure which is
balanced Feistel. Overall AES gets is entirely better in comparison to two (Penchalaiah and
Seshadri, 2010).
AES
AES is defined as symmetric block cipher that was published by National Institute of standards
and technology in 2001. It was also announced to replace DES as it was slower and have smaller
cipher key.
It has secret key of 128-bit and plaintext of 128-bit which cumulatively forms 128-bit block
represented as a matrix of 4*4 that undergoes transformation.
Advantages of AES
It is a cryptographic algorithm that is effective and mathematically more elegant.
It provides choices to user like 256-bit key, 192-bit or 128-bit key.
It is safe and secure.
Disadvantages of AES
It uses algebraic structure that is simple.
Software is difficult to be executed.
In similar way every block used to be encrypted (Daemen and Rijmen, 2013).
Recommendation
AES is introduced as replacement of DES as an algorithm with standard symmetric encryption
for organisation of US federal. AES uses blocks of 128-bit and can even accept bits of 256, 192
or 128 range. AES is effective for both software and hardware. Basically, out of both AES is
best.
Conclusion
DES is defined as algorithm that is older whereas AES is defined as algorithm that is advanced.
AES is more secure and faster as compared to DES. AES is unbreakable and strong using
substitution-permutation and on the other hand DES is breakable and using structure which is
balanced Feistel. Overall AES gets is entirely better in comparison to two (Penchalaiah and
Seshadri, 2010).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Luken, B.P., Ouyang, M. and Desoky, A.H., 2009, September. AES and DES Encryption with
GPU. In ISCA PDCCS (pp. 67-70).
Sivakumar, R., Balakumar, B. and Pandeeswaran, V.A., 2018. A Study of Encryption
Algorithms (DES, 3DES and AES) for Information Security.
Eichlseder, M., 2007. AES und DES.
Daemen, J. and Rijmen, V., 2013. The design of Rijndael: AES-the advanced encryption
standard. Springer Science & Business Media.
Penchalaiah, N. and Seshadri, R., 2010. Effective Comparison and evaluation of DES and
Rijndael Algorithm (AES). International journal of computer science and engineering, 2(05),
pp.1641-1645.
Luken, B.P., Ouyang, M. and Desoky, A.H., 2009, September. AES and DES Encryption with
GPU. In ISCA PDCCS (pp. 67-70).
Sivakumar, R., Balakumar, B. and Pandeeswaran, V.A., 2018. A Study of Encryption
Algorithms (DES, 3DES and AES) for Information Security.
Eichlseder, M., 2007. AES und DES.
Daemen, J. and Rijmen, V., 2013. The design of Rijndael: AES-the advanced encryption
standard. Springer Science & Business Media.
Penchalaiah, N. and Seshadri, R., 2010. Effective Comparison and evaluation of DES and
Rijndael Algorithm (AES). International journal of computer science and engineering, 2(05),
pp.1641-1645.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





