Debian ISO Image Verification and Digital Certificates using OpenSSL
VerifiedAdded on 2024/05/29
|11
|1140
|233
Practical Assignment
AI Summary
This assignment covers two main tasks: verifying a Debian DVD ISO image and generating digital certificates using OpenSSL. The first task involves downloading the ISO image and its checksum files, verifying the checksum using GPG, and confirming the ISO image content. The second task explains digital signatures, their security benefits, and the role of OpenSSL. It details the steps to generate a Certificate Signing Request (CSR), RSA private key, public certificate, secure private key, and verify the digital certificate, including creating and verifying a certificate chain. The process ensures secure communication and data integrity.
1- Debian DVD ISO image verification:
files which are given are downloaded from the link which is provided below:
https://goo.gl/8CNeyc . The ISO picture a long with its mark records both MD5 and
SHA-1 are improved the situation fulfillment.
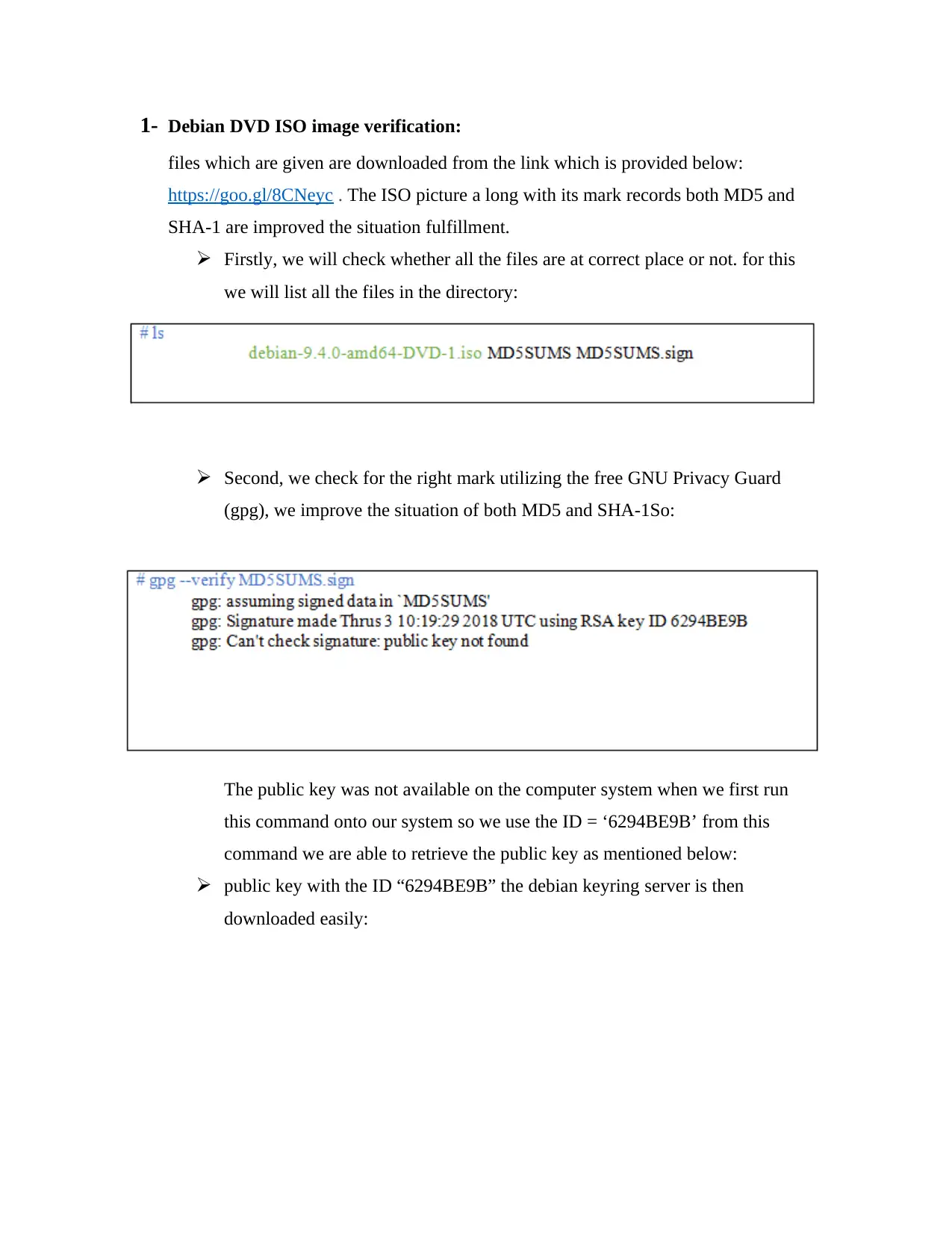
Firstly, we will check whether all the files are at correct place or not. for this
we will list all the files in the directory:
Second, we check for the right mark utilizing the free GNU Privacy Guard
(gpg), we improve the situation of both MD5 and SHA-1So:
The public key was not available on the computer system when we first run
this command onto our system so we use the ID = ‘6294BE9B’ from this
command we are able to retrieve the public key as mentioned below:
public key with the ID “6294BE9B” the debian keyring server is then
downloaded easily:
files which are given are downloaded from the link which is provided below:
https://goo.gl/8CNeyc . The ISO picture a long with its mark records both MD5 and
SHA-1 are improved the situation fulfillment.
Firstly, we will check whether all the files are at correct place or not. for this
we will list all the files in the directory:
Second, we check for the right mark utilizing the free GNU Privacy Guard
(gpg), we improve the situation of both MD5 and SHA-1So:
The public key was not available on the computer system when we first run
this command onto our system so we use the ID = ‘6294BE9B’ from this
command we are able to retrieve the public key as mentioned below:
public key with the ID “6294BE9B” the debian keyring server is then
downloaded easily:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

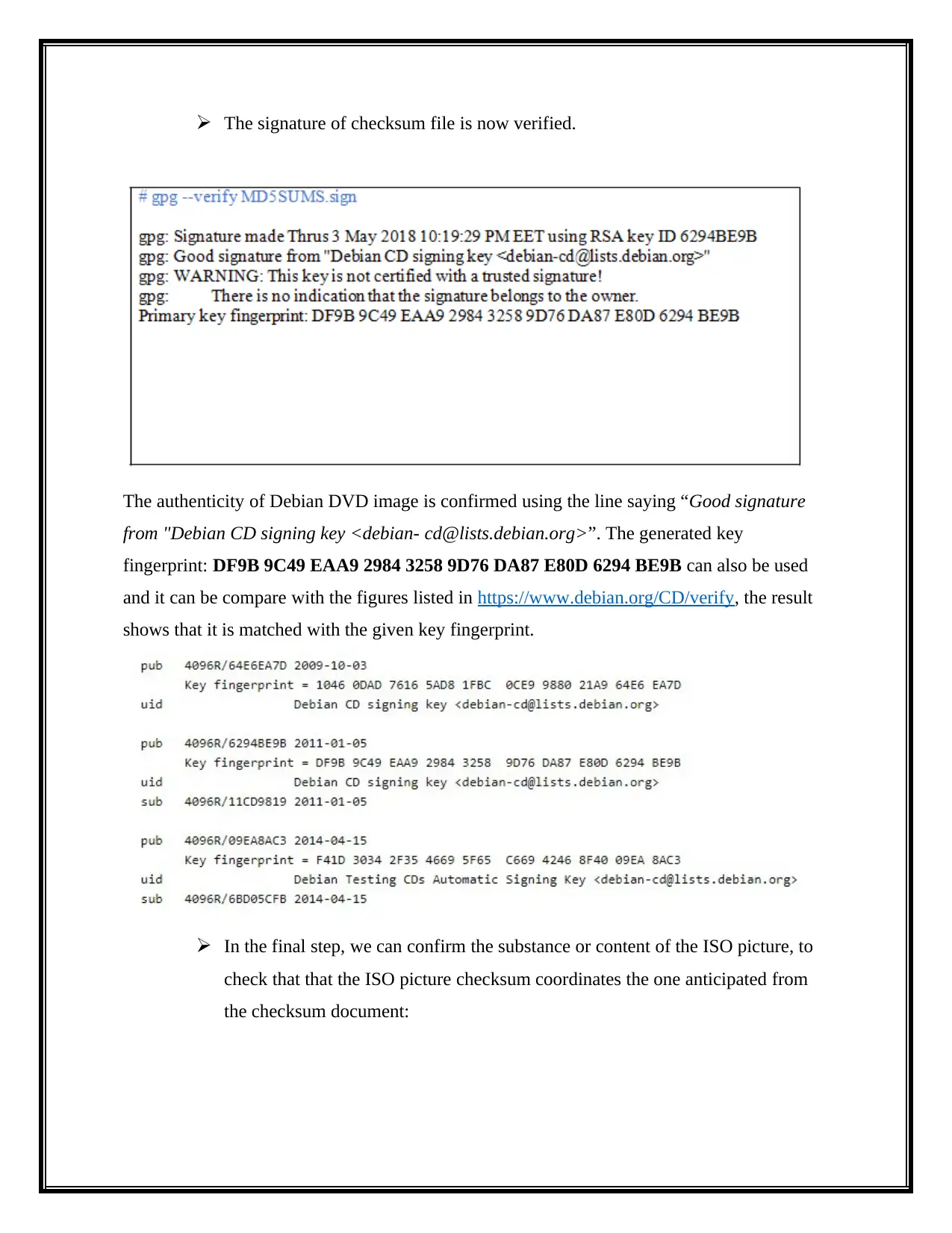
The signature of checksum file is now verified.
The authenticity of Debian DVD image is confirmed using the line saying “Good signature
from "Debian CD signing key <debian- cd@lists.debian.org>”. The generated key
fingerprint: DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B can also be used
and it can be compare with the figures listed in https://www.debian.org/CD/verify, the result
shows that it is matched with the given key fingerprint.
In the final step, we can confirm the substance or content of the ISO picture, to
check that that the ISO picture checksum coordinates the one anticipated from
the checksum document:
The authenticity of Debian DVD image is confirmed using the line saying “Good signature
from "Debian CD signing key <debian- cd@lists.debian.org>”. The generated key
fingerprint: DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B can also be used
and it can be compare with the figures listed in https://www.debian.org/CD/verify, the result
shows that it is matched with the given key fingerprint.
In the final step, we can confirm the substance or content of the ISO picture, to
check that that the ISO picture checksum coordinates the one anticipated from
the checksum document:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 2
1- In first step we confirm that the given global public parameters is in the encoded and
text formats or not:
2- Now using these public parameters we generate the public/private key:
1- In first step we confirm that the given global public parameters is in the encoded and
text formats or not:
2- Now using these public parameters we generate the public/private key:

3- In the next step public key is extracted:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
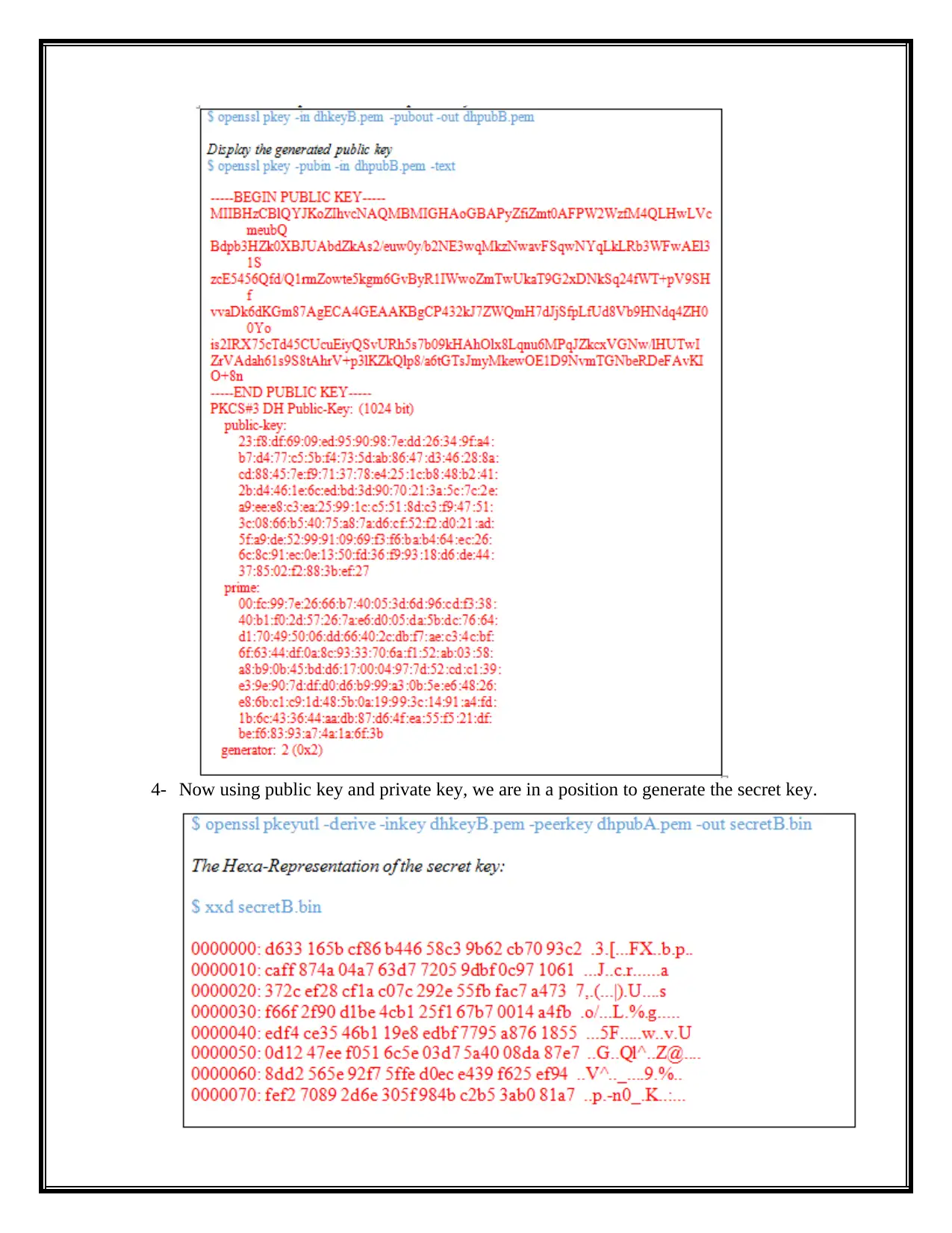
4- Now using public key and private key, we are in a position to generate the secret key.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5- For correct shared secret key generation, the generated shared key in above step and the
key at the instructor side ought to be the same for the generation of shared secret key.
key at the instructor side ought to be the same for the generation of shared secret key.
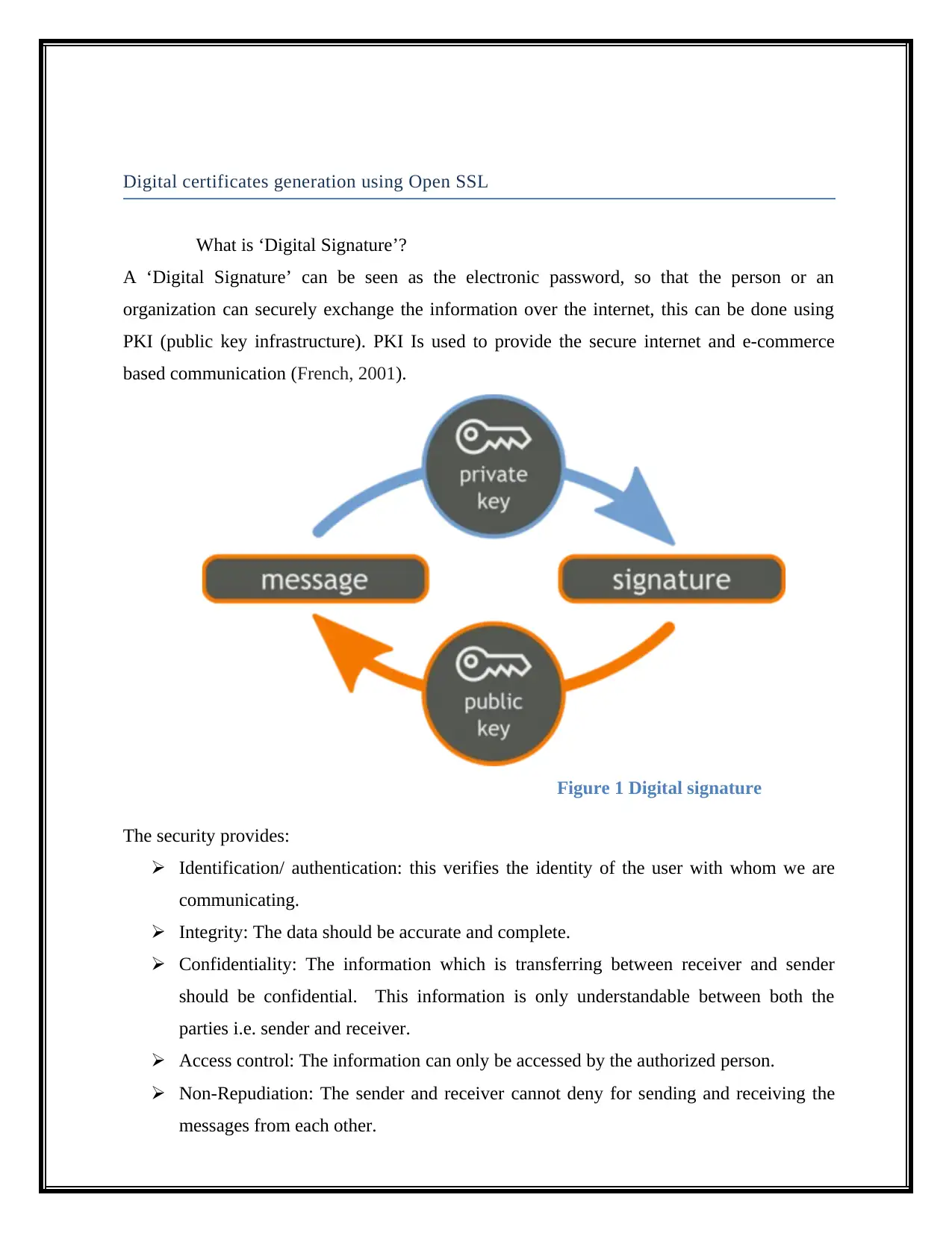
Digital certificates generation using Open SSL
What is ‘Digital Signature’?
A ‘Digital Signature’ can be seen as the electronic password, so that the person or an
organization can securely exchange the information over the internet, this can be done using
PKI (public key infrastructure). PKI Is used to provide the secure internet and e-commerce
based communication (French, 2001).
Figure 1 Digital signature
The security provides:
Identification/ authentication: this verifies the identity of the user with whom we are
communicating.
Integrity: The data should be accurate and complete.
Confidentiality: The information which is transferring between receiver and sender
should be confidential. This information is only understandable between both the
parties i.e. sender and receiver.
Access control: The information can only be accessed by the authorized person.
Non-Repudiation: The sender and receiver cannot deny for sending and receiving the
messages from each other.
What is ‘Digital Signature’?
A ‘Digital Signature’ can be seen as the electronic password, so that the person or an
organization can securely exchange the information over the internet, this can be done using
PKI (public key infrastructure). PKI Is used to provide the secure internet and e-commerce
based communication (French, 2001).
Figure 1 Digital signature
The security provides:
Identification/ authentication: this verifies the identity of the user with whom we are
communicating.
Integrity: The data should be accurate and complete.
Confidentiality: The information which is transferring between receiver and sender
should be confidential. This information is only understandable between both the
parties i.e. sender and receiver.
Access control: The information can only be accessed by the authorized person.
Non-Repudiation: The sender and receiver cannot deny for sending and receiving the
messages from each other.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

What is open SSL?
The secure communication over the internet is secure by the software library which is called
open SSL. The web servers are widely used by the open SSL and servers the majority to all the
web servers. The library of open SSL is written is c language and the SSL and TCL protocol is
open source. Open ssl is a adaptable and flexible command line tool which ensure the
generation of the public key using the PKI (public key infrastructure and HTTP above TLS.
There are basically two keys are available for the cryptography technique: public key and
private key. As the name suggest, public key is made available for the user publically to access
the data and private key is confidential to the owner only, so that the data can only be access
by the authorized person who knows that particular private key.
We can generate the digital signature using the open SSL. Following are the steps of
generating digital certificates using the open SSL:
Step 1: The CSR (Certificate signing Request) and RSA private key is generated: The client
and server should be same when we request for the CSR and RSA private key. Only the value
differs.
Step 2: From the existing certification the public certification is generated
Step 3: Then we will secure the file of private key: The security to the private key can be given
while generating the private key or afterwards. To provide the security we give the password to
restrict the access of the file of private key.
Step 4: Digital certificate is than checked using open SSL: In the digital certificate the digital
signature timestamps, signature itself and other information is stored. Since It is in encoded
form, hence it is unreadable (Brubaker, 2014).
Step 5: In PEM format the certificate chain is created: you should distinguish for the Open SSL
client application. There should be at least one CAs that are to be trusted. This rundown is
known as a chain of trust. There can be one or more than one trusted CAs. The content of the
more than one CAs is stored in the file in which all the digital signatures of CAs are stored.
Step 6: This chain of trust is verified: All the certificates need to be verified on both client and
server side. All the CAs side certificates must be available for the validation at the server side.
Step 7: Open SSL is finally end: type ‘QUIT’ to end the open SSL.
The secure communication over the internet is secure by the software library which is called
open SSL. The web servers are widely used by the open SSL and servers the majority to all the
web servers. The library of open SSL is written is c language and the SSL and TCL protocol is
open source. Open ssl is a adaptable and flexible command line tool which ensure the
generation of the public key using the PKI (public key infrastructure and HTTP above TLS.
There are basically two keys are available for the cryptography technique: public key and
private key. As the name suggest, public key is made available for the user publically to access
the data and private key is confidential to the owner only, so that the data can only be access
by the authorized person who knows that particular private key.
We can generate the digital signature using the open SSL. Following are the steps of
generating digital certificates using the open SSL:
Step 1: The CSR (Certificate signing Request) and RSA private key is generated: The client
and server should be same when we request for the CSR and RSA private key. Only the value
differs.
Step 2: From the existing certification the public certification is generated
Step 3: Then we will secure the file of private key: The security to the private key can be given
while generating the private key or afterwards. To provide the security we give the password to
restrict the access of the file of private key.
Step 4: Digital certificate is than checked using open SSL: In the digital certificate the digital
signature timestamps, signature itself and other information is stored. Since It is in encoded
form, hence it is unreadable (Brubaker, 2014).
Step 5: In PEM format the certificate chain is created: you should distinguish for the Open SSL
client application. There should be at least one CAs that are to be trusted. This rundown is
known as a chain of trust. There can be one or more than one trusted CAs. The content of the
more than one CAs is stored in the file in which all the digital signatures of CAs are stored.
Step 6: This chain of trust is verified: All the certificates need to be verified on both client and
server side. All the CAs side certificates must be available for the validation at the server side.
Step 7: Open SSL is finally end: type ‘QUIT’ to end the open SSL.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References:
French, J. and Wilder, J., Equifax Inc, 2001. System and method for authentication of
network users and issuing a digital certificate. U.S. Patent 6,321,339.
Brubaker, C., Jana, S., Ray, B., Khurshid, S. and Shmatikov, V., 2014, May. Using
frankencerts for automated adversarial testing of certificate validation in SSL/TLS
implementations. In Security and Privacy (SP), 2014 IEEE Symposium on (pp. 114-
129).
Tycksen Jr, F.A. and Jennings, C.W., Preview Systems Inc, 2001. Digital Certificate.
U.S. Patent 6,189,097.
French, J. and Wilder, J., Equifax Inc, 2001. System and method for authentication of
network users and issuing a digital certificate. U.S. Patent 6,321,339.
Brubaker, C., Jana, S., Ray, B., Khurshid, S. and Shmatikov, V., 2014, May. Using
frankencerts for automated adversarial testing of certificate validation in SSL/TLS
implementations. In Security and Privacy (SP), 2014 IEEE Symposium on (pp. 114-
129).
Tycksen Jr, F.A. and Jennings, C.W., Preview Systems Inc, 2001. Digital Certificate.
U.S. Patent 6,189,097.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





