Blockchain-Based IoT Software Updates: Security and Efficiency
VerifiedAdded on 2022/08/12
|11
|2196
|19
Report
AI Summary
This report investigates the application of blockchain technology to address security vulnerabilities in IoT software updates. The study highlights the centralized nature of current update mechanisms, which are susceptible to threats such as denial-of-service attacks, malicious insiders, and compromised software integrity. The proposed solution leverages blockchain's decentralized, immutable, and transparent properties to establish a trusted system for distributing and verifying software patches. The report details how blockchain can ensure the availability of updates, prevent unauthorized modifications, and enhance the overall security posture of IoT devices. It covers blockchain principles, types, storage methods (on-chain and off-chain), and threat models. The proposed solution involves nodes from a cybersecurity unit in the blockchain to evaluate stored network resources and verify the integrity and resistance of the software code to various known attacks before updating the IoT tools. The report concludes that the blockchain can provide a secure software update platform for IoT devices.

Running head: TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
TRUSTED AND DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
Name of the Student:
Name of the University:
Author’s Note:
TRUSTED AND DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
Name of the Student:
Name of the University:
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
IoT Security:-
Abstract:-
IoT devices are susceptible to software patches or updates due to the integrated model of
immediate software repairing or updating model. There are mostly some categories of dangers,
like a threat to accessibility, the loss of reliability, and malevolent insider. We have applied the
blockchain to deliver a reliable and regionalized IoT software update structure to overwhelmed
those susceptibilities and dangers. This will avoid failure in any distinct node in a network from
carrying the whole network to a halting failure.
Introduction:-
IoT has extended broad acceptance in current time and has become a measure of human
life. The objects of physical IoT like vehicles, home appliances, infrastructure components,
supply chain items. Smart entities in IoT structures are generally assorted and work under
dissimilar organizational domains [1]. Creating belief and preserving safety in the IoT domain is
frequently viewed as one of the most inspiring responsibilities. Such apparatus depends on a
diversity of original network substructure, which is susceptible to outbreaks as evident in some
current cyber-attacks. The safety and confidentiality of the information in IoT networks is also a
considerable concern.
Every IoT tools and apparatus has some category of security susceptibilities to the cyber-
attacks throughout the many factors like resource limitations, power restrictions and
nonexistence of safety mechanism [2]. To avoid the security susceptibilities, mainly newly
originate susceptibilities, IoT constructers usually push safety updates to the end devices. Block
chain is a record that keeps an incessantly rising set of information records. Though, even the
IoT Security:-
Abstract:-
IoT devices are susceptible to software patches or updates due to the integrated model of
immediate software repairing or updating model. There are mostly some categories of dangers,
like a threat to accessibility, the loss of reliability, and malevolent insider. We have applied the
blockchain to deliver a reliable and regionalized IoT software update structure to overwhelmed
those susceptibilities and dangers. This will avoid failure in any distinct node in a network from
carrying the whole network to a halting failure.
Introduction:-
IoT has extended broad acceptance in current time and has become a measure of human
life. The objects of physical IoT like vehicles, home appliances, infrastructure components,
supply chain items. Smart entities in IoT structures are generally assorted and work under
dissimilar organizational domains [1]. Creating belief and preserving safety in the IoT domain is
frequently viewed as one of the most inspiring responsibilities. Such apparatus depends on a
diversity of original network substructure, which is susceptible to outbreaks as evident in some
current cyber-attacks. The safety and confidentiality of the information in IoT networks is also a
considerable concern.
Every IoT tools and apparatus has some category of security susceptibilities to the cyber-
attacks throughout the many factors like resource limitations, power restrictions and
nonexistence of safety mechanism [2]. To avoid the security susceptibilities, mainly newly
originate susceptibilities, IoT constructers usually push safety updates to the end devices. Block
chain is a record that keeps an incessantly rising set of information records. Though, even the

2TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
most significant software update policy falls short if any careful attack is directing for any
specific tools of IoT network.
The Block chain technology has increased attractiveness in different areas because of its
captivating properties like integrity, resiliency, obscurity, delegation and self-governing control
[3]. While crypto-currency is the most extensively used blockchain technology application, the
amount of other applied applications beyond token-values is developing.
Among these applications, the conjunction of blockchain and IoT networks grips massive
potentials in the area of IoT device documentation, verification, sensor-data and unified
protected data transfer [4]. The opportunity of this meeting has motivated the eagerness among
the investigators between academia and industry consultants to interrupt some IoT use cases as
well as to state the above-revealed disputes prevailing in IoT structures.
In this report, the writer discovers the process of blockchain structure, which can be used
to deliver software updates to IoT tools fitting to different constructions. The reorganized and
allocated network of the blockchain network can certify the obtainability of the software updates
in the network even in the expression of DoS attack [5]. The blockchain network property can
be applied to construct belief and avoid illegal modifications of the software patch. In the
following part, the report writer will deliver a detail explanation about the blockchain.
Blockchain:-
A blockchain is a record containing successive blocks chained composed subsequent a
strict instructions set. The record is circulated and deposited by the nodes of a P2P network
where every block is made at a predefined intermission in a distributed fashion through a
consensus process. The consensus process promises numerous data integrity connected
most significant software update policy falls short if any careful attack is directing for any
specific tools of IoT network.
The Block chain technology has increased attractiveness in different areas because of its
captivating properties like integrity, resiliency, obscurity, delegation and self-governing control
[3]. While crypto-currency is the most extensively used blockchain technology application, the
amount of other applied applications beyond token-values is developing.
Among these applications, the conjunction of blockchain and IoT networks grips massive
potentials in the area of IoT device documentation, verification, sensor-data and unified
protected data transfer [4]. The opportunity of this meeting has motivated the eagerness among
the investigators between academia and industry consultants to interrupt some IoT use cases as
well as to state the above-revealed disputes prevailing in IoT structures.
In this report, the writer discovers the process of blockchain structure, which can be used
to deliver software updates to IoT tools fitting to different constructions. The reorganized and
allocated network of the blockchain network can certify the obtainability of the software updates
in the network even in the expression of DoS attack [5]. The blockchain network property can
be applied to construct belief and avoid illegal modifications of the software patch. In the
following part, the report writer will deliver a detail explanation about the blockchain.
Blockchain:-
A blockchain is a record containing successive blocks chained composed subsequent a
strict instructions set. The record is circulated and deposited by the nodes of a P2P network
where every block is made at a predefined intermission in a distributed fashion through a
consensus process. The consensus process promises numerous data integrity connected
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
properties in the blockchain. Accepting an identical peer-to-peer communication model to
procedure the hundreds of billions of dealings between devices will expressively decrease the
costs connected with linking. It is also keeping large unified data centres. It will allocate
computation and storage requirements across the billions of devices that form IoT systems.
Principle:-
Blockchain technology can be applied in tracing billions of linked devices, allow the
treating of transactions and direction between devices. It’s also permit for substantial savings to
IoT business constructors. A blockchain shows some properties which build it an appropriate
contender for several application ranges.
Data attribution:
The documents storage procedure in any blockchain is enabled utilizing a mechanism
named the transaction. Each transaction wants to be numerically contracting using public-key
cryptography which confirms the legitimacy of the data resources. Relating this with the
irreversibility and immutability of a blockchain delivers a durable non-repudiation mechanism
for any documents in the blockchain.
Information importunity:
Information in a blockchain is deposited in a circulated fashion certifying its persistency
as long as there are contributing nodes in the P2P network.
Circulated agreement on the chain state:
One of the vital properties of some blockchain is its ability to realize a spread consensus
on the chain state without being dependent on any trustworthy third party. These unlock the
properties in the blockchain. Accepting an identical peer-to-peer communication model to
procedure the hundreds of billions of dealings between devices will expressively decrease the
costs connected with linking. It is also keeping large unified data centres. It will allocate
computation and storage requirements across the billions of devices that form IoT systems.
Principle:-
Blockchain technology can be applied in tracing billions of linked devices, allow the
treating of transactions and direction between devices. It’s also permit for substantial savings to
IoT business constructors. A blockchain shows some properties which build it an appropriate
contender for several application ranges.
Data attribution:
The documents storage procedure in any blockchain is enabled utilizing a mechanism
named the transaction. Each transaction wants to be numerically contracting using public-key
cryptography which confirms the legitimacy of the data resources. Relating this with the
irreversibility and immutability of a blockchain delivers a durable non-repudiation mechanism
for any documents in the blockchain.
Information importunity:
Information in a blockchain is deposited in a circulated fashion certifying its persistency
as long as there are contributing nodes in the P2P network.
Circulated agreement on the chain state:
One of the vital properties of some blockchain is its ability to realize a spread consensus
on the chain state without being dependent on any trustworthy third party. These unlock the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
entrance of prospects to construct and operate a structure where every potential positions and
connection are provable by the lawful entities.
Irreversibility and Immutability of chain state:
Realizing a circulated consensus with the contribution of a considerable number of nodes
confirms that the chain state converts virtually immutable and irreversible after a definite period.
These also relate to smart-contracts and therefore permitting the disposition and implementation
of comprehensive computer programs.
Transparency and Accountability:
Subsequently, the chain state, along with each single connections among contributing
entities, can be proved by any approved entity, it supports responsibility and transparency.
Distributed data control:
A blockchain confirms that data kept in the chain or recovered from the chain can be
accepted in a circulated manner that displays no particular point of disaster.
Types of Blockchain:-
There are many blockchain disposition approaches can be tracked. Based on these plans,
there are mainly two types of blockchains, such as private and public blockchain.
Private Blockchain:
This kind of blockchain also recognized as the authorized blockchain. It has a
constricting notion in judgment to its public complement in the sagacity that only sanctioned,
and responsible entities can contribute to the actions within the blockchain. By permitting only
entrance of prospects to construct and operate a structure where every potential positions and
connection are provable by the lawful entities.
Irreversibility and Immutability of chain state:
Realizing a circulated consensus with the contribution of a considerable number of nodes
confirms that the chain state converts virtually immutable and irreversible after a definite period.
These also relate to smart-contracts and therefore permitting the disposition and implementation
of comprehensive computer programs.
Transparency and Accountability:
Subsequently, the chain state, along with each single connections among contributing
entities, can be proved by any approved entity, it supports responsibility and transparency.
Distributed data control:
A blockchain confirms that data kept in the chain or recovered from the chain can be
accepted in a circulated manner that displays no particular point of disaster.
Types of Blockchain:-
There are many blockchain disposition approaches can be tracked. Based on these plans,
there are mainly two types of blockchains, such as private and public blockchain.
Private Blockchain:
This kind of blockchain also recognized as the authorized blockchain. It has a
constricting notion in judgment to its public complement in the sagacity that only sanctioned,
and responsible entities can contribute to the actions within the blockchain. By permitting only

5TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
authorized objects to contribute in actions within the blockchain, a private blockchain can
confirm the confidentiality of chain information which might be wanted in specific use-cases.
Public blockchain:
It is also identified as the not permission blockchain, permits anyone to contribute in the
blockchain to make and authenticate blocks as well as to adjust the chain state by keeping and
informing documents employing dealings among participating entities. These means that the
blockchain state and its dealings along with the documents kept is transparent and available to
everyone. These increases confidentiality distresses for specific situations where the privacy of
such documents wants to be conserved.
Storage Types:-
On-chain Storage:
On-chain dealings mention to those cryptocurrency dealings which happen on the
blockchain - that is, on the histories of the blockchain. Entire on-chain transactions are measured
to be legal only when the block chain is adapted to imitate these dealings on the public record.
These confirm the ACID activities of the chain. With the blockchain, the rationality of the
system needs a huge group of persons to preserve copies of the whole thing. If information is lost
or degraded in any specific node, then it can directly coordinate with another node in the
network. Consequently, it can deliver any network strength.
Off-chain Storage:
Conversely, the aim for storing documents off-chain is that if everyone supplies all of
their information on the chain. The chain would develop incredibly massive, and it would be
problematic to get persons to keep whole. In the off-chain method, a user will not preserve all the
authorized objects to contribute in actions within the blockchain, a private blockchain can
confirm the confidentiality of chain information which might be wanted in specific use-cases.
Public blockchain:
It is also identified as the not permission blockchain, permits anyone to contribute in the
blockchain to make and authenticate blocks as well as to adjust the chain state by keeping and
informing documents employing dealings among participating entities. These means that the
blockchain state and its dealings along with the documents kept is transparent and available to
everyone. These increases confidentiality distresses for specific situations where the privacy of
such documents wants to be conserved.
Storage Types:-
On-chain Storage:
On-chain dealings mention to those cryptocurrency dealings which happen on the
blockchain - that is, on the histories of the blockchain. Entire on-chain transactions are measured
to be legal only when the block chain is adapted to imitate these dealings on the public record.
These confirm the ACID activities of the chain. With the blockchain, the rationality of the
system needs a huge group of persons to preserve copies of the whole thing. If information is lost
or degraded in any specific node, then it can directly coordinate with another node in the
network. Consequently, it can deliver any network strength.
Off-chain Storage:
Conversely, the aim for storing documents off-chain is that if everyone supplies all of
their information on the chain. The chain would develop incredibly massive, and it would be
problematic to get persons to keep whole. In the off-chain method, a user will not preserve all the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
records in the blockchain, he will save it off-chain and just stock a URL directing to the
documents and data hashing on the chain. This tactic is known as a Distributed Hash Table. In
blockchain-based cryptocurrencies, off-chain dealings denote to those who happen external of
the blockchain itself and can be compared with on-chain dealings.
Threat models of Software update:-
IoT industrialists make different categories of IoT devices and specify the software to
activate them. These devices are positioned to sense the atmosphere and recover data from the
system. Generally, when these devices are arranged, the constructors usually deliver the latest
cyber safety safe protector. Though, this safe protector is continually checked by the limited
dispensation power. Besides, throughout the period, new susceptibilities are revealed and can be
exploited by the malevolent performers. Therefore, constructors generally push the software
patch from timely. Conversely, there are some dangers in the present software covering
mechanism,
Risk to Availability
In the present mechanism, the constructors upload the patches in their webpages. The IoT
devices download the coverings and modernize the software. Conversely, these websites can be
under attack by mischievous inspired actors. Cyber attackers can promote DoS to create the
website unreachable. The DoS attack can be stretching by using more amount of attack machine,
which is classier and named as DDoS attack.
Mischievous IoT Constructors
Several IoT devices are used in a network, like the smart city or smart home. Any
malevolent constructor may push mischievous code to its devices. By using this mischievous
records in the blockchain, he will save it off-chain and just stock a URL directing to the
documents and data hashing on the chain. This tactic is known as a Distributed Hash Table. In
blockchain-based cryptocurrencies, off-chain dealings denote to those who happen external of
the blockchain itself and can be compared with on-chain dealings.
Threat models of Software update:-
IoT industrialists make different categories of IoT devices and specify the software to
activate them. These devices are positioned to sense the atmosphere and recover data from the
system. Generally, when these devices are arranged, the constructors usually deliver the latest
cyber safety safe protector. Though, this safe protector is continually checked by the limited
dispensation power. Besides, throughout the period, new susceptibilities are revealed and can be
exploited by the malevolent performers. Therefore, constructors generally push the software
patch from timely. Conversely, there are some dangers in the present software covering
mechanism,
Risk to Availability
In the present mechanism, the constructors upload the patches in their webpages. The IoT
devices download the coverings and modernize the software. Conversely, these websites can be
under attack by mischievous inspired actors. Cyber attackers can promote DoS to create the
website unreachable. The DoS attack can be stretching by using more amount of attack machine,
which is classier and named as DDoS attack.
Mischievous IoT Constructors
Several IoT devices are used in a network, like the smart city or smart home. Any
malevolent constructor may push mischievous code to its devices. By using this mischievous
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
code, the malicious constructor may negotiation other devices in the network like smart city,
smart home.
The integrity of Software Patch
The reliability of the software patch is very significant. The constructors generally, create
Hash of the source code and broadcast it with the software covers. The IoT possessors can use
that Hash to confirm the reliability of the software covering. If the website has cooperated then
the Hashes can be reformed.
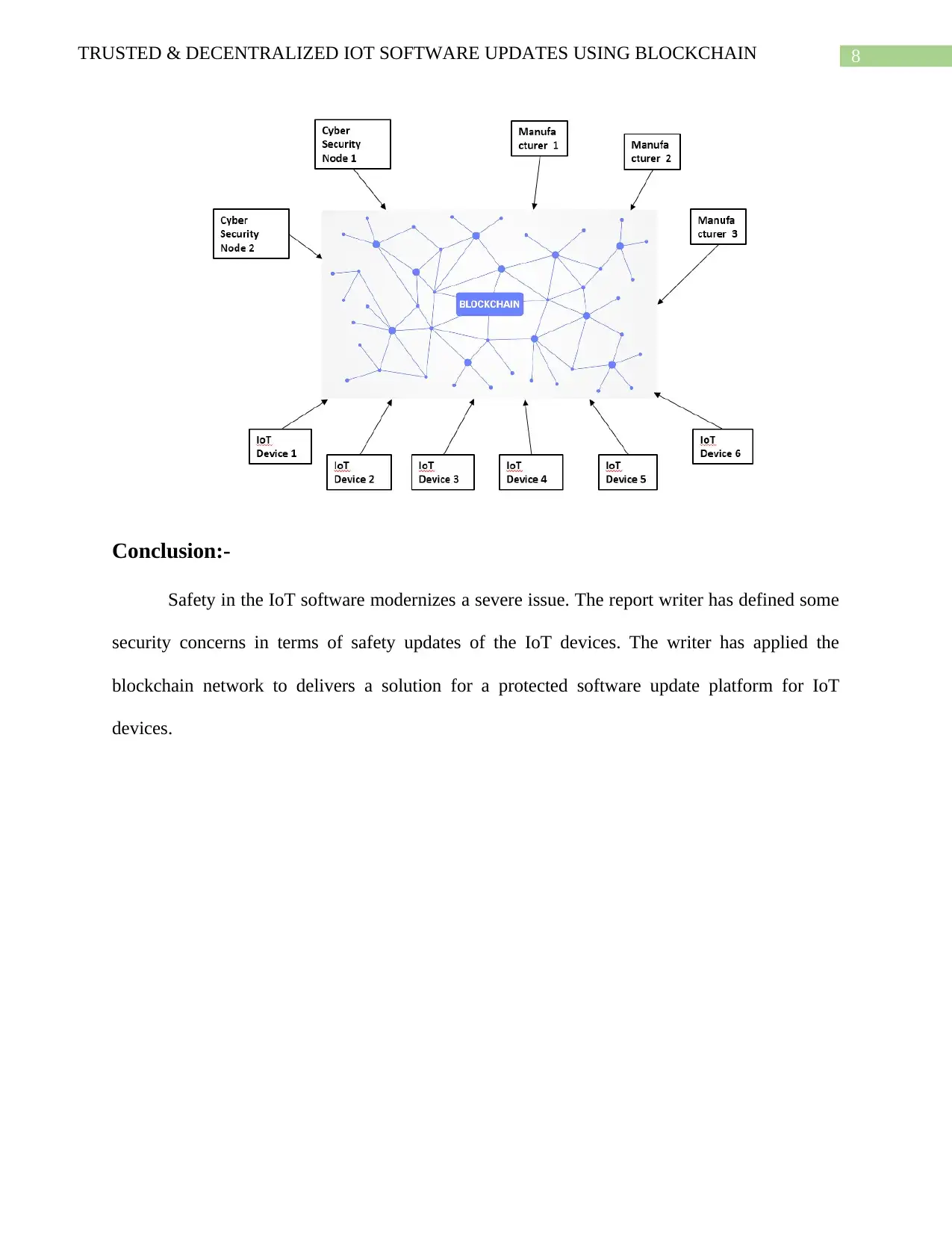
Proposed Solution
The report writer has already mentioned the essential properties of the blockchain.
Consequently, it can deliver the integrity facilities to the source code. Furthermore, if the track
is keeping in the blockchain, then the information will be introduced among several nodes due to
the distributed properties of the blockchain. Then the report writer also suggests that there will be
node from the administration cyber safety unit in the blockchain, which will estimate the stored
network source.
These nodes will check the bugs, evaluating their susceptibilities and challenging its
resistance to a set of recognized attacks. Only, if cybersecurity node confirms the code, then only
the IoT tools will update the software. Occasionally IoT devices may not be openly linked with
the blockchain network; instead, it may be linked through the gateway, which has more
computational control. In this below diagram displays the proposed objects in the blockchain
network.
code, the malicious constructor may negotiation other devices in the network like smart city,
smart home.
The integrity of Software Patch
The reliability of the software patch is very significant. The constructors generally, create
Hash of the source code and broadcast it with the software covers. The IoT possessors can use
that Hash to confirm the reliability of the software covering. If the website has cooperated then
the Hashes can be reformed.
Proposed Solution
The report writer has already mentioned the essential properties of the blockchain.
Consequently, it can deliver the integrity facilities to the source code. Furthermore, if the track
is keeping in the blockchain, then the information will be introduced among several nodes due to
the distributed properties of the blockchain. Then the report writer also suggests that there will be
node from the administration cyber safety unit in the blockchain, which will estimate the stored
network source.
These nodes will check the bugs, evaluating their susceptibilities and challenging its
resistance to a set of recognized attacks. Only, if cybersecurity node confirms the code, then only
the IoT tools will update the software. Occasionally IoT devices may not be openly linked with
the blockchain network; instead, it may be linked through the gateway, which has more
computational control. In this below diagram displays the proposed objects in the blockchain
network.
8TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
Conclusion:-
Safety in the IoT software modernizes a severe issue. The report writer has defined some
security concerns in terms of safety updates of the IoT devices. The writer has applied the
blockchain network to delivers a solution for a protected software update platform for IoT
devices.
Conclusion:-
Safety in the IoT software modernizes a severe issue. The report writer has defined some
security concerns in terms of safety updates of the IoT devices. The writer has applied the
blockchain network to delivers a solution for a protected software update platform for IoT
devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
References:-
[1] C.M. Medaglia and A. Serbanati An overview of privacy and security issues in the internet of
things, In The Internet of Things 2010, (pp. 389-395), Springer, New York, NY.
[2] S. Sicari, A. Rizzardi ,L.A. Grieco, A. Coen-Porisini ,Security, privacy and trust in Internet
of Things: The road ahead. Computer networks, 2015 Jan 15, 76:146-64.
[3] M. Swan, Blockchain: Blueprint for a new economy, " O'Reilly Media, Inc."; 2015 Jan 24.
[4] M. Conoscenti, A. Vetro , JC. De Martin , Blockchain for the Internet of Things: A
systematic literature review, InComputer Systems and Applications (AICCSA), 2016 IEEE/ACS
13th International Conference of 2016 Nov 29 , (pp. 1-6), IEEE.
[5] A. Boudguiga, N. Bouzerna, L. Granboulan , A. Olivereau , F. Quesnel , A. Roger, R.
Sirdey ,Towards better availability and accountability for iot updates by means of a blockchain,
InSecurity and Privacy Workshops (EuroS&PW), 2017 IEEE European Symposium on 2017 Apr
26 , (pp. 50-58), IEEE.
References:-
[1] C.M. Medaglia and A. Serbanati An overview of privacy and security issues in the internet of
things, In The Internet of Things 2010, (pp. 389-395), Springer, New York, NY.
[2] S. Sicari, A. Rizzardi ,L.A. Grieco, A. Coen-Porisini ,Security, privacy and trust in Internet
of Things: The road ahead. Computer networks, 2015 Jan 15, 76:146-64.
[3] M. Swan, Blockchain: Blueprint for a new economy, " O'Reilly Media, Inc."; 2015 Jan 24.
[4] M. Conoscenti, A. Vetro , JC. De Martin , Blockchain for the Internet of Things: A
systematic literature review, InComputer Systems and Applications (AICCSA), 2016 IEEE/ACS
13th International Conference of 2016 Nov 29 , (pp. 1-6), IEEE.
[5] A. Boudguiga, N. Bouzerna, L. Granboulan , A. Olivereau , F. Quesnel , A. Roger, R.
Sirdey ,Towards better availability and accountability for iot updates by means of a blockchain,
InSecurity and Privacy Workshops (EuroS&PW), 2017 IEEE European Symposium on 2017 Apr
26 , (pp. 50-58), IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10TRUSTED & DECENTRALIZED IOT SOFTWARE UPDATES USING BLOCKCHAIN
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





