T2 2018 MN603: Secure Enterprise Wireless Network Project
VerifiedAdded on 2023/06/04
|9
|2358
|138
Project
AI Summary
This project details the design and implementation of a secure enterprise wireless network, considering the ethical implications. It explores the importance of secure wireless networks in modern architecture, focusing on supporting mobile devices and providing network connectivity. The project utilizes WPA2 and a RADIUS server to create a secure wireless network. It covers ethical considerations, network design using Boson Netsim, implementation steps, and testing using ping connectivity. The report analyzes authentication and authorization, confidentiality, integrity, and availability of the network. The project also addresses the implications of ethical processes in network security, and provides a comprehensive overview of the design and implementation of the secure enterprise wireless network, including testing and validation.
Network and Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Introduction.......................................................................................................................2
2 Implication of Ethical process.........................................................................................2
3 Secure Enterprise Wireless Network Design..................................................................3
4 Analysis of Secure Enterprise Wireless Network..........................................................5
5 Implementation of Secure Enterprise Wireless Network.............................................6
6 Testing................................................................................................................................7
7 Conclusion.........................................................................................................................7
References.................................................................................................................................8
1
1 Introduction.......................................................................................................................2
2 Implication of Ethical process.........................................................................................2
3 Secure Enterprise Wireless Network Design..................................................................3
4 Analysis of Secure Enterprise Wireless Network..........................................................5
5 Implementation of Secure Enterprise Wireless Network.............................................6
6 Testing................................................................................................................................7
7 Conclusion.........................................................................................................................7
References.................................................................................................................................8
1

1 Introduction
This project is used to create the secure enterprise wireless network by considering the
ethical implications. The secure enterprise wireless network is an important component of
modern network architecture and that networks are needs to support the mobile devices and
provides the network connectivity. Securing the wireless local area network is a not hard
because various industry uses the advances technology to makes the easier to create the
secure enterprise wireless network for an organization. Here, we are using the WPA2 and
RADIUS server to provide the secure wireless network for an organization. The WPA2 that
includes the used for wireless authentication users dials of the enterprise deployment
services. The RADIUS server configuring process of to access point is used for the
encryption information. The user operating system of the configuring process encryption and
settings of IEEE802.1x. Finally, it connected the secure enterprise wireless network. The use
of WPA2 and RADIUS server is used for creating the secure enterprise wireless network.
The implements to ethical design of the wireless network of the secure enterprise process for
mobile devices. After, enterprise wireless design to the secure enterprise by using Boson
Netsim. Then, identify and implement the secure enterprise of wireless network. Finally, test
to the created network by using the ping connectivity on the Boson netsim. These are will be
analysed and demonstrated in detail.
2 Implication of Ethical process
Many ethical issue with identify the represent of the wireless system fruition come to the
everyone to convenience and the ill-advised setup. The wireless network availability of the
numerous issues of ethics and protection of security for the quick expending and most of the
angles to format the fate of eventual wireless system on the world [1].
At the point of the open system association with examine and so on utilizing GPS gadgets
there is no any download by authorised standards is specify to ensure the security hub
anyway checking unauthorised of the US controls the administration are attacking for the
stealing the data. The main issues of the access point to the area of individual filtering data.
Let us issues of the area protection of the client or the area of a passage
All in all breaking to access points is utilized the accompanying things:
To get to the Adult sites or to infuse infection in the system
2
This project is used to create the secure enterprise wireless network by considering the
ethical implications. The secure enterprise wireless network is an important component of
modern network architecture and that networks are needs to support the mobile devices and
provides the network connectivity. Securing the wireless local area network is a not hard
because various industry uses the advances technology to makes the easier to create the
secure enterprise wireless network for an organization. Here, we are using the WPA2 and
RADIUS server to provide the secure wireless network for an organization. The WPA2 that
includes the used for wireless authentication users dials of the enterprise deployment
services. The RADIUS server configuring process of to access point is used for the
encryption information. The user operating system of the configuring process encryption and
settings of IEEE802.1x. Finally, it connected the secure enterprise wireless network. The use
of WPA2 and RADIUS server is used for creating the secure enterprise wireless network.
The implements to ethical design of the wireless network of the secure enterprise process for
mobile devices. After, enterprise wireless design to the secure enterprise by using Boson
Netsim. Then, identify and implement the secure enterprise of wireless network. Finally, test
to the created network by using the ping connectivity on the Boson netsim. These are will be
analysed and demonstrated in detail.
2 Implication of Ethical process
Many ethical issue with identify the represent of the wireless system fruition come to the
everyone to convenience and the ill-advised setup. The wireless network availability of the
numerous issues of ethics and protection of security for the quick expending and most of the
angles to format the fate of eventual wireless system on the world [1].
At the point of the open system association with examine and so on utilizing GPS gadgets
there is no any download by authorised standards is specify to ensure the security hub
anyway checking unauthorised of the US controls the administration are attacking for the
stealing the data. The main issues of the access point to the area of individual filtering data.
Let us issues of the area protection of the client or the area of a passage
All in all breaking to access points is utilized the accompanying things:
To get to the Adult sites or to infuse infection in the system
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
To take the financial balances of the cash stealing
Experience of hacking to the get process.
Where this gives the dynamic encryption of the high level security gives to diverse key
encryption. These are [2],
Shared key Authentication: In this methodology verification access is finished by the
reaction to a test by the passage which is known as test and reaction.
Open framework Authentication: In this methodology SSID is utilized for the
Authentication if the SSID is known access can be conceded.
Unified verification: In this technique a server is utilized for the validation if the hub
is confirmed then no one but it can get to the system.
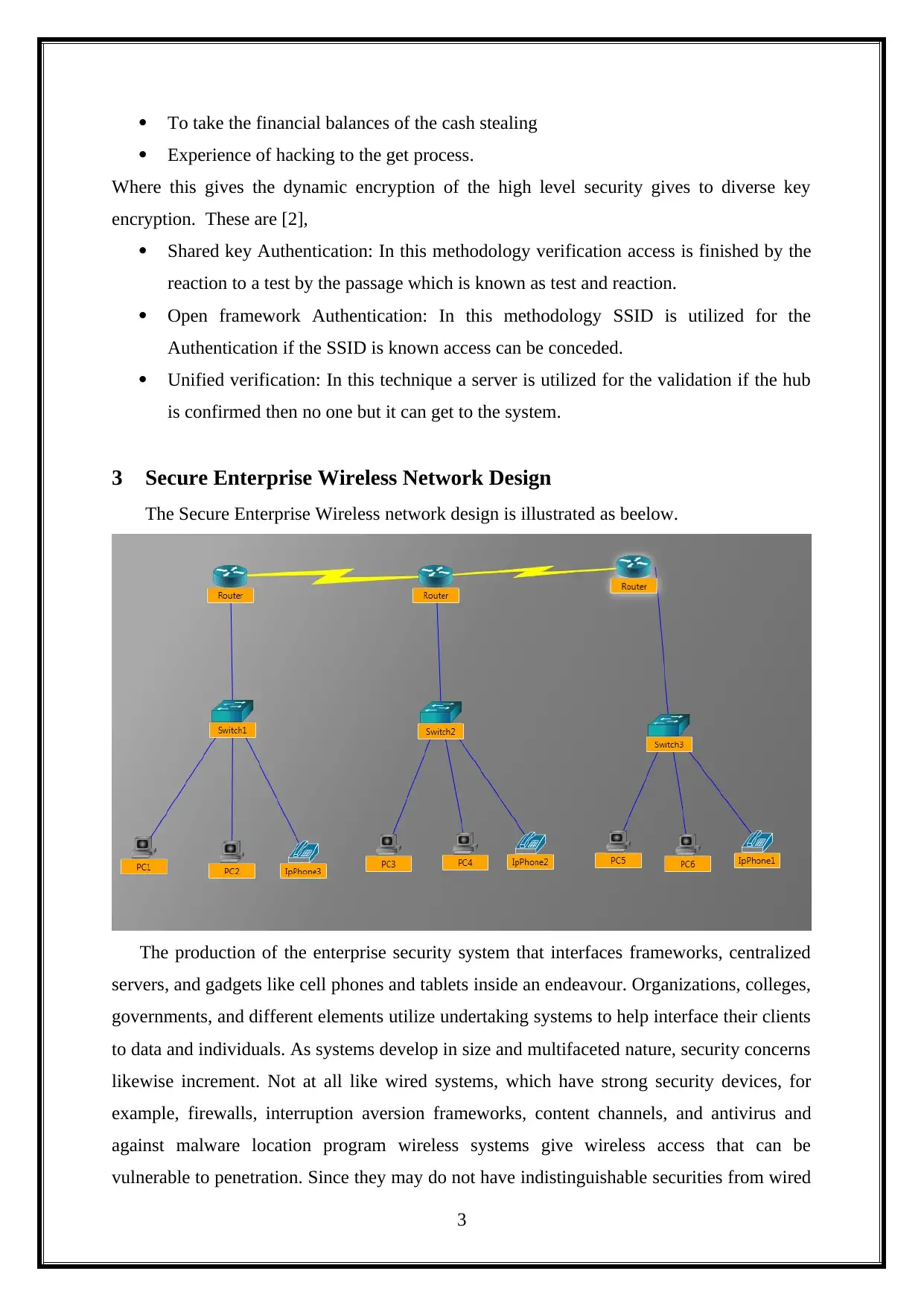
3 Secure Enterprise Wireless Network Design
The Secure Enterprise Wireless network design is illustrated as beelow.
The production of the enterprise security system that interfaces frameworks, centralized
servers, and gadgets like cell phones and tablets inside an endeavour. Organizations, colleges,
governments, and different elements utilize undertaking systems to help interface their clients
to data and individuals. As systems develop in size and multifaceted nature, security concerns
likewise increment. Not at all like wired systems, which have strong security devices, for
example, firewalls, interruption aversion frameworks, content channels, and antivirus and
against malware location program wireless systems give wireless access that can be
vulnerable to penetration. Since they may do not have indistinguishable securities from wired
3
Experience of hacking to the get process.
Where this gives the dynamic encryption of the high level security gives to diverse key
encryption. These are [2],
Shared key Authentication: In this methodology verification access is finished by the
reaction to a test by the passage which is known as test and reaction.
Open framework Authentication: In this methodology SSID is utilized for the
Authentication if the SSID is known access can be conceded.
Unified verification: In this technique a server is utilized for the validation if the hub
is confirmed then no one but it can get to the system.
3 Secure Enterprise Wireless Network Design
The Secure Enterprise Wireless network design is illustrated as beelow.
The production of the enterprise security system that interfaces frameworks, centralized
servers, and gadgets like cell phones and tablets inside an endeavour. Organizations, colleges,
governments, and different elements utilize undertaking systems to help interface their clients
to data and individuals. As systems develop in size and multifaceted nature, security concerns
likewise increment. Not at all like wired systems, which have strong security devices, for
example, firewalls, interruption aversion frameworks, content channels, and antivirus and
against malware location program wireless systems give wireless access that can be
vulnerable to penetration. Since they may do not have indistinguishable securities from wired
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

systems, wireless systems and gadgets can yield to a collection of attacks intended to
enterprise access system? An access to the attackers an enterprise system through a wireless
access to direct vindictive exercises including packet sniffing, making rouge access,
password theft, and man-in-the-middle attacks. These attacks could delay the arrange
network, moderate procedures, or even accident the enterprise framework. Consider these
extra accepted procedures to help defend their endeavour Wi-Fi systems [3]:
Send the (WIDS) and a wireless intrusion prevention system (WIPS) on each system.
Guarantee existing hardware is free from known vulnerabilities by refreshing all
product as per designer benefit pack issuance.
Utilize existing gear that can be safely arranged.
Guarantee all gear meets (FIPS) 140-2 to encryption and consistence.
Guarantee consistence with the most current National Institute of Standards and
Technology.
Set up multifaceted confirmation for access to your system. On the off chance that
this isn't conceivable, consider other secure verification implies past a solitary shared
secret word, for example, Active Directory benefit validation or an elective strategy to
make multifaceted confirmation into your system.
Utilize Extensible Authentication Protocol-Transport Layer Security endorsement
based strategies to anchor the whole confirmation exchange and correspondence.
Utilize Counter Mode Cipher Block Chaining Message Authentication Code Protocol,
a type of AES encryption utilized by Wireless Application Protocol 2 endeavour
organizes sparingly. On the off chance that conceivable, utilize more mind boggling
encryption advancements that comply with FIPS 140-2 as they are produced and
endorsed.
Actualize a visitor Wi-Fi arrange that is separate from the principle organize. Utilize
switches with different SSIDs or draw in different wireless disconnection highlights
to guarantee that authoritative data isn't open to visitor arrange movement or by
connecting with different wireless disengagement highlights [4].
4 Analysis of Secure Enterprise Wireless Network
Authentication and Authorization
The enterprise business wireless system is intended of WPA enterprise standard, is
otherwise called WAP-802.IX, use to utilizing a authenticator of the supplicant and the server
4
enterprise access system? An access to the attackers an enterprise system through a wireless
access to direct vindictive exercises including packet sniffing, making rouge access,
password theft, and man-in-the-middle attacks. These attacks could delay the arrange
network, moderate procedures, or even accident the enterprise framework. Consider these
extra accepted procedures to help defend their endeavour Wi-Fi systems [3]:
Send the (WIDS) and a wireless intrusion prevention system (WIPS) on each system.
Guarantee existing hardware is free from known vulnerabilities by refreshing all
product as per designer benefit pack issuance.
Utilize existing gear that can be safely arranged.
Guarantee all gear meets (FIPS) 140-2 to encryption and consistence.
Guarantee consistence with the most current National Institute of Standards and
Technology.
Set up multifaceted confirmation for access to your system. On the off chance that
this isn't conceivable, consider other secure verification implies past a solitary shared
secret word, for example, Active Directory benefit validation or an elective strategy to
make multifaceted confirmation into your system.
Utilize Extensible Authentication Protocol-Transport Layer Security endorsement
based strategies to anchor the whole confirmation exchange and correspondence.
Utilize Counter Mode Cipher Block Chaining Message Authentication Code Protocol,
a type of AES encryption utilized by Wireless Application Protocol 2 endeavour
organizes sparingly. On the off chance that conceivable, utilize more mind boggling
encryption advancements that comply with FIPS 140-2 as they are produced and
endorsed.
Actualize a visitor Wi-Fi arrange that is separate from the principle organize. Utilize
switches with different SSIDs or draw in different wireless disconnection highlights
to guarantee that authoritative data isn't open to visitor arrange movement or by
connecting with different wireless disengagement highlights [4].
4 Analysis of Secure Enterprise Wireless Network
Authentication and Authorization
The enterprise business wireless system is intended of WPA enterprise standard, is
otherwise called WAP-802.IX, use to utilizing a authenticator of the supplicant and the server
4

validation. The supplicant is a customer gadget that is in charge of making solicitations to the
WLAN, giving accreditations to the authenticator. The enterprise access to the authenticator
is normally interface with the server verification, through RADIUS or IAS actualized
convention to approve the validate of the client customer. The innovation depends on the
EAP to sending the message confirmation of the supplicant server. enabling numerous of
enterprises to exemplify the packets are EAP-TLS, EAP-TTLS/MSCHAPv2, PEAP/EAP-
MSCHAPv2, PEAP/EAP=GTC, PEAP-TLS, EAP-SIM, EAP-AKA, EAP-FAST and
LEAP[5].
The methodological method utilized is made out of an initial step of readiness of the
system framework, trailed by a list of wireless gadgets lastly the attack stage to the associated
customers with a specific end goal to get the accreditations. The attack comprises of mocking
the objective system and give a superior flag to the customer than authentic passage, with a
specific end goal to play out a Man-In-The-Middle attack among customers and system
foundation, in light of the fact that presently the TLS burrow is sufficient secure and not
effortlessly attackable. To make this sort of attack you should be physically closeness to the
objective, particularly remaining inside the activity scope of enterprise business access.
Confidentiality
The fundamental methods of the information and the guarantee to revealed to client of the
unapproved encrypting it amount transmit to the simply indistinguishable among the transmit
wired system of the route information of the encryption is negligible of without validation
since could be an unapproved client onto the system themselves is giving the key of the
decode is information [6].
Integrity
The wireless system though the air packets of the information is captured the effectively by
pernicious of altered the clients. The system are more defenceless of the against assaults of
the information. But that the way to utilized wired systems present techniques of the packets.
For models the checksums to handle the impeccably guaranteeing of satisfactory the
respectability of the no original arrangements of the bundles in wireless system embraced.
Availability
The especially of the wireless system that helpless to the assaults. The wired system required
of the assailant associated of the system somehow before dispatch such an assault of the
physically associated with wireless systems an aggressor inside the scope of the specific
system to the capacity of dispatch such as assault.
5
WLAN, giving accreditations to the authenticator. The enterprise access to the authenticator
is normally interface with the server verification, through RADIUS or IAS actualized
convention to approve the validate of the client customer. The innovation depends on the
EAP to sending the message confirmation of the supplicant server. enabling numerous of
enterprises to exemplify the packets are EAP-TLS, EAP-TTLS/MSCHAPv2, PEAP/EAP-
MSCHAPv2, PEAP/EAP=GTC, PEAP-TLS, EAP-SIM, EAP-AKA, EAP-FAST and
LEAP[5].
The methodological method utilized is made out of an initial step of readiness of the
system framework, trailed by a list of wireless gadgets lastly the attack stage to the associated
customers with a specific end goal to get the accreditations. The attack comprises of mocking
the objective system and give a superior flag to the customer than authentic passage, with a
specific end goal to play out a Man-In-The-Middle attack among customers and system
foundation, in light of the fact that presently the TLS burrow is sufficient secure and not
effortlessly attackable. To make this sort of attack you should be physically closeness to the
objective, particularly remaining inside the activity scope of enterprise business access.
Confidentiality
The fundamental methods of the information and the guarantee to revealed to client of the
unapproved encrypting it amount transmit to the simply indistinguishable among the transmit
wired system of the route information of the encryption is negligible of without validation
since could be an unapproved client onto the system themselves is giving the key of the
decode is information [6].
Integrity
The wireless system though the air packets of the information is captured the effectively by
pernicious of altered the clients. The system are more defenceless of the against assaults of
the information. But that the way to utilized wired systems present techniques of the packets.
For models the checksums to handle the impeccably guaranteeing of satisfactory the
respectability of the no original arrangements of the bundles in wireless system embraced.
Availability
The especially of the wireless system that helpless to the assaults. The wired system required
of the assailant associated of the system somehow before dispatch such an assault of the
physically associated with wireless systems an aggressor inside the scope of the specific
system to the capacity of dispatch such as assault.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5 Implementation of Secure Enterprise Wireless Network
The wireless security of conventions used to actualize of the secure enterprise system.As
of late, there has been a brisk of WPA convention of substitution essentially numerous usage
of the vulnerabilities TKIP, the fundamental system that can be utilized the keep up
uprightness of the association.
A portion of the key issues that were featured were:
• The encryption of WPA/TKIP bolstered on helpless potential assaults of
the safe systems is malevolent movement, the TKIP convention is openly
accessible and being effectively used in the adventures of the wireless
system.
• The hostage visitor entry way to organized to auto associate had client
gadgets of the interacting empowered with it about bringing the genuinely
IP asset is fast weariness of corruption in framework assets. The general
involvement for the real clients.
• Users arranged to utilize their home site i.e. Loughborough, were at times
unfit to get to the visiting other instructive systems because of wrong
arrangement [7].
The steps relocation process was done in three distinct stages:
• Stage 1 The IP address arranging included planning of existing framework
that is range of arrangement and foundation of access points so they could
expend deals with the number of clients.
• Stage2 The change of the clients included the testing of new changes and
the various of gadgets obtaining an apparatus to setting up customer of the
new setup its customisation of required setting should the pushed out of
the customers i.e. customer testament, 802.IX profile settings.
• Stage 3 the real arrangement of the single SSID which included i.e. for all
client and upholding the endeavour wireless association settings security to
be WPA2 with AES encryption of the network security. The permitted
clients of the relocate and the old SSID's were step by step resigned [8].
6
The wireless security of conventions used to actualize of the secure enterprise system.As
of late, there has been a brisk of WPA convention of substitution essentially numerous usage
of the vulnerabilities TKIP, the fundamental system that can be utilized the keep up
uprightness of the association.
A portion of the key issues that were featured were:
• The encryption of WPA/TKIP bolstered on helpless potential assaults of
the safe systems is malevolent movement, the TKIP convention is openly
accessible and being effectively used in the adventures of the wireless
system.
• The hostage visitor entry way to organized to auto associate had client
gadgets of the interacting empowered with it about bringing the genuinely
IP asset is fast weariness of corruption in framework assets. The general
involvement for the real clients.
• Users arranged to utilize their home site i.e. Loughborough, were at times
unfit to get to the visiting other instructive systems because of wrong
arrangement [7].
The steps relocation process was done in three distinct stages:
• Stage 1 The IP address arranging included planning of existing framework
that is range of arrangement and foundation of access points so they could
expend deals with the number of clients.
• Stage2 The change of the clients included the testing of new changes and
the various of gadgets obtaining an apparatus to setting up customer of the
new setup its customisation of required setting should the pushed out of
the customers i.e. customer testament, 802.IX profile settings.
• Stage 3 the real arrangement of the single SSID which included i.e. for all
client and upholding the endeavour wireless association settings security to
be WPA2 with AES encryption of the network security. The permitted
clients of the relocate and the old SSID's were step by step resigned [8].
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6 Testing
Ping configuration is shown below [9], [10].
7 Conclusion
This project successfully created the secure enterprise wireless network by considering
the ethical implications. The secure enterprise wireless network is an important component of
modern network architecture and that networks are needs to support the mobile devices and
provides the network connectivity. Here, we are uses the WPA2 and RADIUS server to
provide the secure wireless network for an organization by created the secure enterprise
wireless network. And, user explores the ethical implication and design ofa secure enterprise
wireless network. After, designed the wireless network of secure enterprise by using Boson
Netsim. Analysis and implement of the secure enterprise wireless network is successfully
completed. Finally, tested the created network by using the ping connectivity on the Boson
netsim. These are analysed and demonstrated in detail.
References
[1]"Wireless Networks Security Privacy and Ethical Issues Computer Science
Essay", Ukases, 2018. [Online]. Available: https://www.ukessays.com/essays/computer-
science/wireless-networks-security-privacy-and-ethical-issues-computer-science-
essay.php. [Accessed: 24- Sep- 2018].
7
Ping configuration is shown below [9], [10].
7 Conclusion
This project successfully created the secure enterprise wireless network by considering
the ethical implications. The secure enterprise wireless network is an important component of
modern network architecture and that networks are needs to support the mobile devices and
provides the network connectivity. Here, we are uses the WPA2 and RADIUS server to
provide the secure wireless network for an organization by created the secure enterprise
wireless network. And, user explores the ethical implication and design ofa secure enterprise
wireless network. After, designed the wireless network of secure enterprise by using Boson
Netsim. Analysis and implement of the secure enterprise wireless network is successfully
completed. Finally, tested the created network by using the ping connectivity on the Boson
netsim. These are analysed and demonstrated in detail.
References
[1]"Wireless Networks Security Privacy and Ethical Issues Computer Science
Essay", Ukases, 2018. [Online]. Available: https://www.ukessays.com/essays/computer-
science/wireless-networks-security-privacy-and-ethical-issues-computer-science-
essay.php. [Accessed: 24- Sep- 2018].
7

[2]"Wireless", Ethics.csc.ncsu.edu, 2018. [Online]. Available:
https://ethics.csc.ncsu.edu/risks/security/wireless/study.php. [Accessed: 24- Sep- 2018].
[3]"Wireless Networking Security", Cs.bham.ac.uk, 2018. [Online]. Available:
https://www.cs.bham.ac.uk/~mdr/teaching/modules03/security/students/SS7/Wireless
%20Networking%20Security.htm. [Accessed: 24- Sep- 2018].
[4]"Attacking WPA2 Enterprise", InfoSec Resources, 2018. [Online]. Available:
https://resources.infosecinstitute.com/attacking-wpa2-enterprise/#gref. [Accessed: 24-
Sep- 2018].
[5]"WPA2 Enterprise Wireless Security with Synology RADIUS Server and DD-WRT -
Bukovac.si", Bukovac.si, 2018. [Online]. Available: https://www.bukovac.si/wpa2-
enterprise-wireless-security-with-synology-radius-server-and-dd-wrt/. [Accessed: 24-
Sep- 2018].
[6]"Wireless Security: How to Deploy WPA2-Enterprise", business.com, 2018. [Online].
Available: https://www.business.com/articles/deploying-wpa2-enterprise-encryption/.
[Accessed: 24- Sep- 2018].
[7]"RADIUS Server Security for Wife Networks", Interlinknetworks.com, 2018. [Online].
Available: https://www.interlinknetworks.com/whitepapers/Link_Layer_Security.htm.
[Accessed: 24- Sep- 2018].
[8]"WPA/WPA2 Enterprise Authentication with RADIUS", Watchguard.com, 2018.
[Online]. Available:
https://www.watchguard.com/help/docs/fireware/12/en-US/Content/en-US/
authentication/wpa_wpa2_enterprise_auth_c.html. [Accessed: 24- Sep- 2018].
[9]"Securing Enterprise Wireless Networks | US-CERT", Us-cert.gov, 2018. [Online].
Available: https://www.us-cert.gov/ncas/tips/ST18-247. [Accessed: 24- Sep- 2018].
[10]"How to secure a wireless network for small business", Search Networking, 2018.
[Online]. Available: https://searchnetworking.techtarget.com/answer/How-to-secure-a-
wireless-network-for-small-business. [Accessed: 24- Sep- 2018].
8
https://ethics.csc.ncsu.edu/risks/security/wireless/study.php. [Accessed: 24- Sep- 2018].
[3]"Wireless Networking Security", Cs.bham.ac.uk, 2018. [Online]. Available:
https://www.cs.bham.ac.uk/~mdr/teaching/modules03/security/students/SS7/Wireless
%20Networking%20Security.htm. [Accessed: 24- Sep- 2018].
[4]"Attacking WPA2 Enterprise", InfoSec Resources, 2018. [Online]. Available:
https://resources.infosecinstitute.com/attacking-wpa2-enterprise/#gref. [Accessed: 24-
Sep- 2018].
[5]"WPA2 Enterprise Wireless Security with Synology RADIUS Server and DD-WRT -
Bukovac.si", Bukovac.si, 2018. [Online]. Available: https://www.bukovac.si/wpa2-
enterprise-wireless-security-with-synology-radius-server-and-dd-wrt/. [Accessed: 24-
Sep- 2018].
[6]"Wireless Security: How to Deploy WPA2-Enterprise", business.com, 2018. [Online].
Available: https://www.business.com/articles/deploying-wpa2-enterprise-encryption/.
[Accessed: 24- Sep- 2018].
[7]"RADIUS Server Security for Wife Networks", Interlinknetworks.com, 2018. [Online].
Available: https://www.interlinknetworks.com/whitepapers/Link_Layer_Security.htm.
[Accessed: 24- Sep- 2018].
[8]"WPA/WPA2 Enterprise Authentication with RADIUS", Watchguard.com, 2018.
[Online]. Available:
https://www.watchguard.com/help/docs/fireware/12/en-US/Content/en-US/
authentication/wpa_wpa2_enterprise_auth_c.html. [Accessed: 24- Sep- 2018].
[9]"Securing Enterprise Wireless Networks | US-CERT", Us-cert.gov, 2018. [Online].
Available: https://www.us-cert.gov/ncas/tips/ST18-247. [Accessed: 24- Sep- 2018].
[10]"How to secure a wireless network for small business", Search Networking, 2018.
[Online]. Available: https://searchnetworking.techtarget.com/answer/How-to-secure-a-
wireless-network-for-small-business. [Accessed: 24- Sep- 2018].
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




