Analysis of Wireless LAN Rogue Access Points and Security Report
VerifiedAdded on 2022/03/21
|17
|3558
|34
Report
AI Summary
This report delves into the critical issue of rogue access points within wireless LANs, highlighting their potential to compromise network security. It begins by emphasizing the pervasive nature of internet connectivity and the increasing reliance on wireless networks, making them prime targets for malicious actors. The report defines rogue access points as unauthorized devices that can intercept network traffic, steal sensitive information, and facilitate various attacks. It explores the technical background of rogue APs, including how they exploit vulnerabilities in wireless protocols and DHCP configurations. The report then examines various wireless security standards, such as WEP, WPA, and WPA2, and how they have evolved to address security concerns. Furthermore, it discusses the CAPWAP protocol used in controller-based WiFi solutions to manage and secure access points. The report also covers the concept of "evil-twin" attacks and soft rogue APs. Finally, the report outlines methods for detecting and protecting against rogue access points, emphasizing the importance of a systematic approach and the use of both software-based and hardware-based solutions. The conclusion stresses the need for vigilance and proactive security measures to safeguard wireless networks from these threats.
Wireless LAN Rougue Access Points
1. Abstract
Internet has become an integral part of our lives.Either we are working in an office
environement,waiting at a bus stand or spending holiday at home , we always want to
stay connected to the internet.For internet connectivity, we mostly rely on wireless
networks , hence presence of wireless network infrastructure is now essential at almost
every where and so is the need to enhance security of these wireless networks as
well.To surf internet safely, it is important that we make sure that we are connected to
our intended access point and not the one that has been installed by some hacker ,also
called “Rougue Access Points”.Currently , protocols used for user’s authentication have
improved their encryption schemes however , detection of unauthorized access points
still remains a challenge.This paper is intended to highlight its details and some of the
remedial actions that could be taken for the elemenation of non authorized access
points.
2. Introduction
For the purpose of establishing connectivity , it has become quite common that we
purchase a wireless lan card from the computer shop and plug into our PCs and
establish a network connection.Similarly , because of the fact that prices of wireless
devices i.e. access points have drop to a great extent and users can install access
1. Abstract
Internet has become an integral part of our lives.Either we are working in an office
environement,waiting at a bus stand or spending holiday at home , we always want to
stay connected to the internet.For internet connectivity, we mostly rely on wireless
networks , hence presence of wireless network infrastructure is now essential at almost
every where and so is the need to enhance security of these wireless networks as
well.To surf internet safely, it is important that we make sure that we are connected to
our intended access point and not the one that has been installed by some hacker ,also
called “Rougue Access Points”.Currently , protocols used for user’s authentication have
improved their encryption schemes however , detection of unauthorized access points
still remains a challenge.This paper is intended to highlight its details and some of the
remedial actions that could be taken for the elemenation of non authorized access
points.
2. Introduction
For the purpose of establishing connectivity , it has become quite common that we
purchase a wireless lan card from the computer shop and plug into our PCs and
establish a network connection.Similarly , because of the fact that prices of wireless
devices i.e. access points have drop to a great extent and users can install access
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
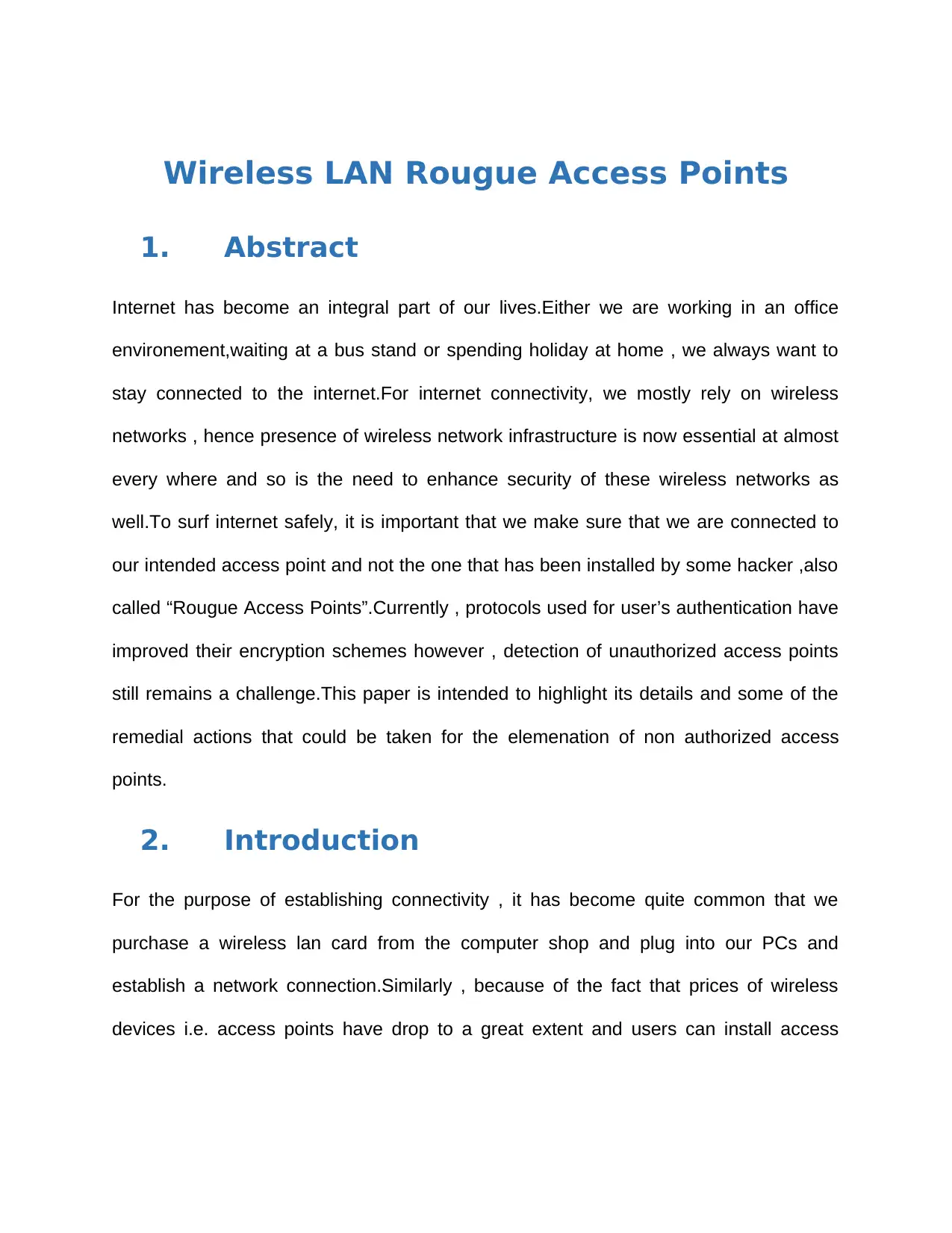
points themselves quite easily , it has become quite a norm to install an access point
whereever there is ethernet drop on the lan networks.
This access point which has been installed by the user in network without authorization
from the administration, will act just like another node that is connected to the network
and will obtain all the IP services i.e. ip address from a DHCP server along with default
gateway just like any other PC connected in the network.A typical wireless network
would be as shown below:
Now this access point will be able to connect other clients i.e. desktops and laptops and
will provide ip addresses via DHCP and similarly will assign gateway address as
well.Users connected through this access point can easily access internal resources of
organisation as rogue access point has all the access to the internal network.Quite often
, in case when internal authorized access points or any network device which is working
at default security and encryption could easily be accessed by the unauthorized
whereever there is ethernet drop on the lan networks.
This access point which has been installed by the user in network without authorization
from the administration, will act just like another node that is connected to the network
and will obtain all the IP services i.e. ip address from a DHCP server along with default
gateway just like any other PC connected in the network.A typical wireless network
would be as shown below:
Now this access point will be able to connect other clients i.e. desktops and laptops and
will provide ip addresses via DHCP and similarly will assign gateway address as
well.Users connected through this access point can easily access internal resources of
organisation as rogue access point has all the access to the internal network.Quite often
, in case when internal authorized access points or any network device which is working
at default security and encryption could easily be accessed by the unauthorized

users.At this point , any malicious activity could be done by any user connected to this
rogue access point which could lead security incidents for the organisation.This infact is
a easily exploitable vulnerebility of the network which could provide an entry point for a
malicious attack.One of the major drawbacks of these rogue access points is that the
hacker can launch an attack and can gain access even when he is not present
physically in the organisation premises and can spend time to sniff network traffic and
can steal important information as well.
If deployed in any network ,to secure the infrastructure services or to provide safe
search for the internet surfing , rogue access points should be detected and removed
from the network by using various standard practices used to resolve this specific
issue.This issue can also happen in case when peer-to-peer wirless connections are
established between two end user devices.In this case , most of devices are usually
configured with default encryption and authentication schemes which could easily be
scanned and taken advantage by the hacker to make a peer-to-peer connection with
any trusted computer which is connected to organisations internal network.In this
specific case , it is always recommended to never use default encryption schemes or
default SSID and passwords for peer-to-peer wireless connectivity.
3. Wireless security overview
With the passage of time , wifi security standards have improvide alot and encryption
and authentication schemes got better and better.Various wireless authentication
schemes are used now a days for wireless connectivity for office and home
networks.The well known schemes are WEP , WPA and WPA2 each with its own
rogue access point which could lead security incidents for the organisation.This infact is
a easily exploitable vulnerebility of the network which could provide an entry point for a
malicious attack.One of the major drawbacks of these rogue access points is that the
hacker can launch an attack and can gain access even when he is not present
physically in the organisation premises and can spend time to sniff network traffic and
can steal important information as well.
If deployed in any network ,to secure the infrastructure services or to provide safe
search for the internet surfing , rogue access points should be detected and removed
from the network by using various standard practices used to resolve this specific
issue.This issue can also happen in case when peer-to-peer wirless connections are
established between two end user devices.In this case , most of devices are usually
configured with default encryption and authentication schemes which could easily be
scanned and taken advantage by the hacker to make a peer-to-peer connection with
any trusted computer which is connected to organisations internal network.In this
specific case , it is always recommended to never use default encryption schemes or
default SSID and passwords for peer-to-peer wireless connectivity.
3. Wireless security overview
With the passage of time , wifi security standards have improvide alot and encryption
and authentication schemes got better and better.Various wireless authentication
schemes are used now a days for wireless connectivity for office and home
networks.The well known schemes are WEP , WPA and WPA2 each with its own
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
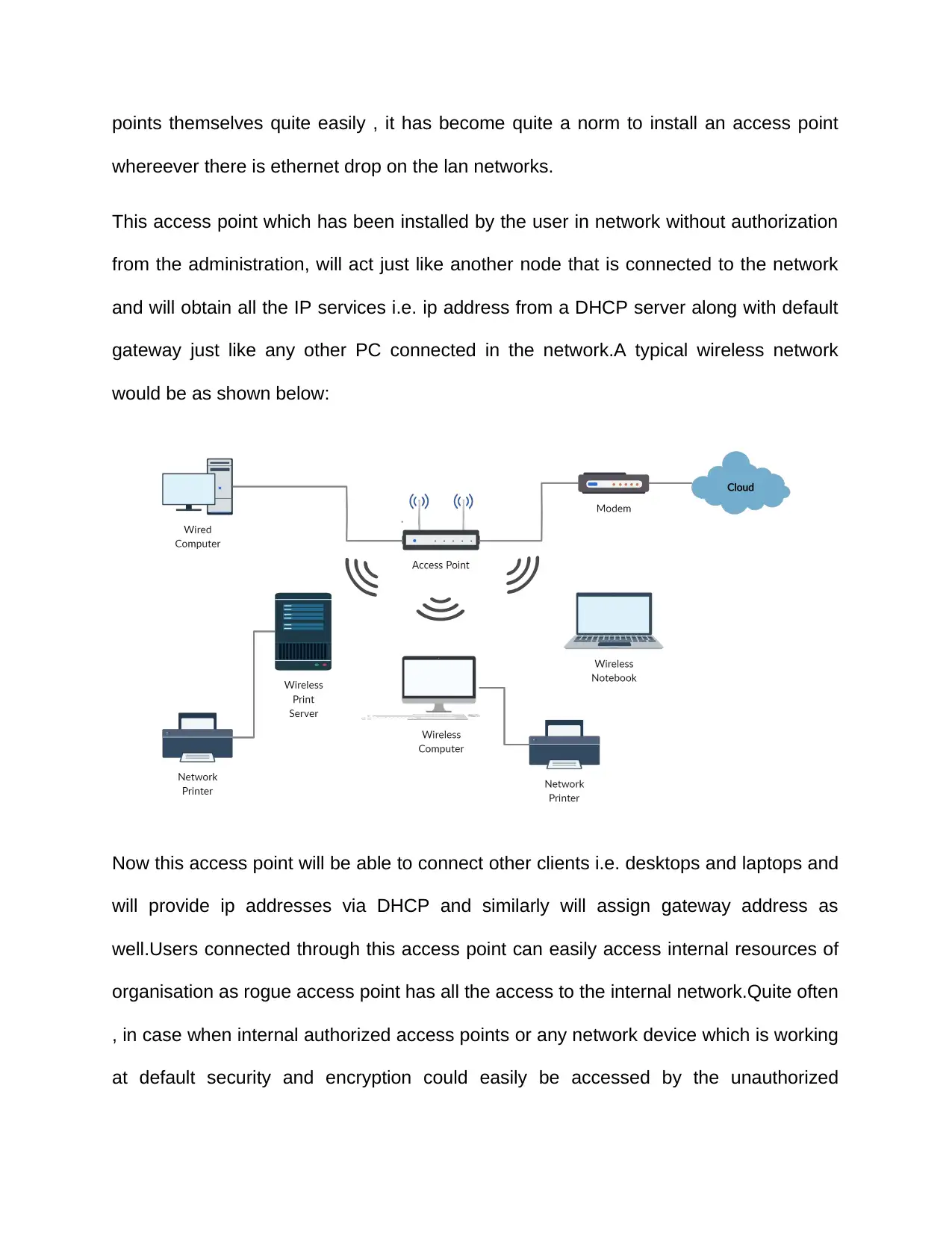
characteristics.These protocols provide authentication mechanism for connecting to the
wireless networks and also provides encryption of the data that is being transfered
through the wireless network.The encryption of the data ensures that it is not decrypted
to ensure integrity and confidentiality of the information.Wireless security is on the
wireless side as shown below in the below figure,
Wired equivalent privacy also called as WEP was introduced at the initail stage and was
meant for providing same level of security as that is offered in wired networks,however it
comes along with alot of deficiencies.As a workaround solution for shortcommings of
WEP , WPA was introduced which stands for WIFI protected access.Most of the
modern devices and softwares uses a preshared key usually called as WPA
personal.But later on WPA was also found to be quite vulnereable for wireless
authentication and encryption.
WPA was further improved and WPA2 was introduced which is actually an enhaced
version of WPA called as WIFI protected access version 2.The major improvement
wireless networks and also provides encryption of the data that is being transfered
through the wireless network.The encryption of the data ensures that it is not decrypted
to ensure integrity and confidentiality of the information.Wireless security is on the
wireless side as shown below in the below figure,
Wired equivalent privacy also called as WEP was introduced at the initail stage and was
meant for providing same level of security as that is offered in wired networks,however it
comes along with alot of deficiencies.As a workaround solution for shortcommings of
WEP , WPA was introduced which stands for WIFI protected access.Most of the
modern devices and softwares uses a preshared key usually called as WPA
personal.But later on WPA was also found to be quite vulnereable for wireless
authentication and encryption.
WPA was further improved and WPA2 was introduced which is actually an enhaced
version of WPA called as WIFI protected access version 2.The major improvement
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
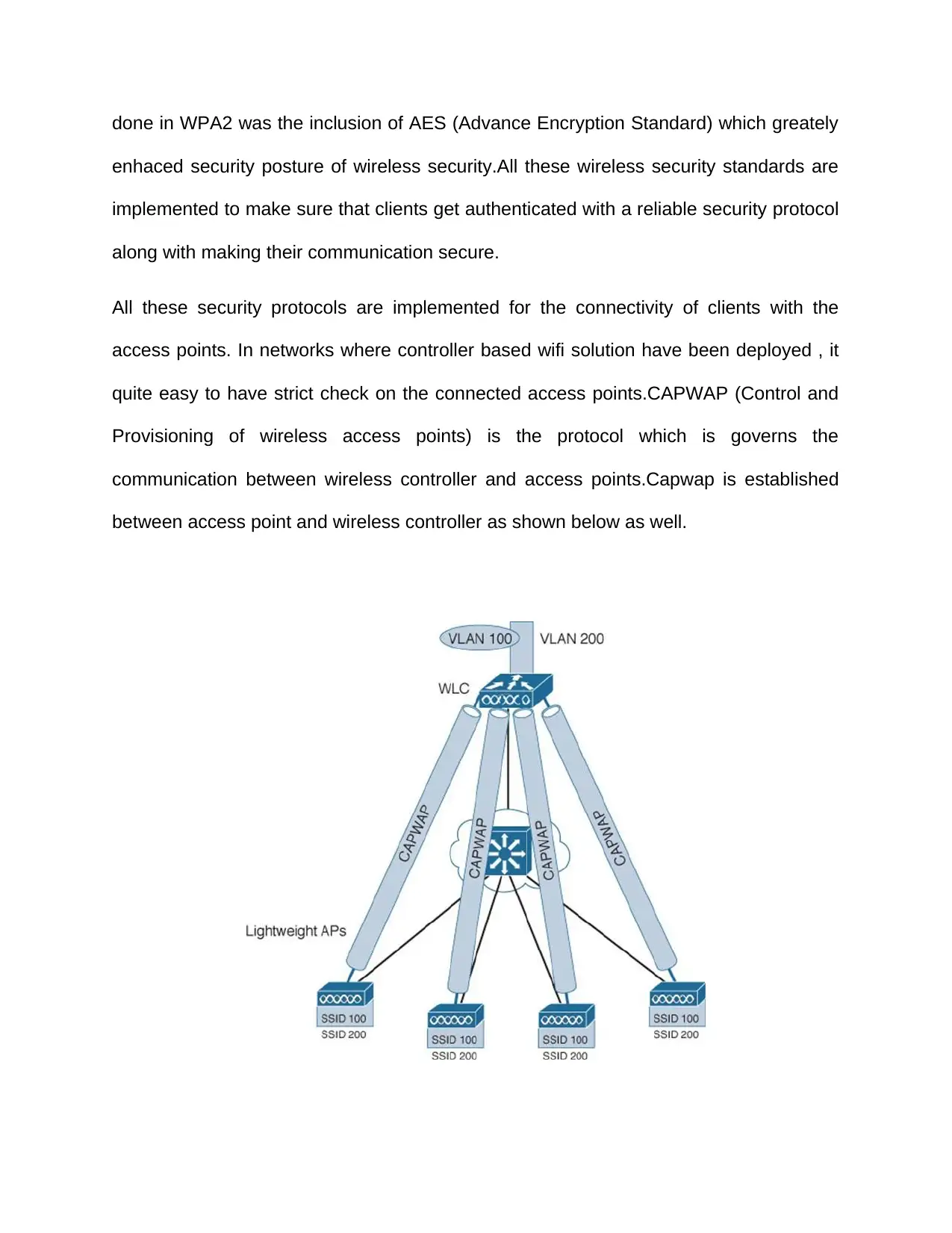
done in WPA2 was the inclusion of AES (Advance Encryption Standard) which greately
enhaced security posture of wireless security.All these wireless security standards are
implemented to make sure that clients get authenticated with a reliable security protocol
along with making their communication secure.
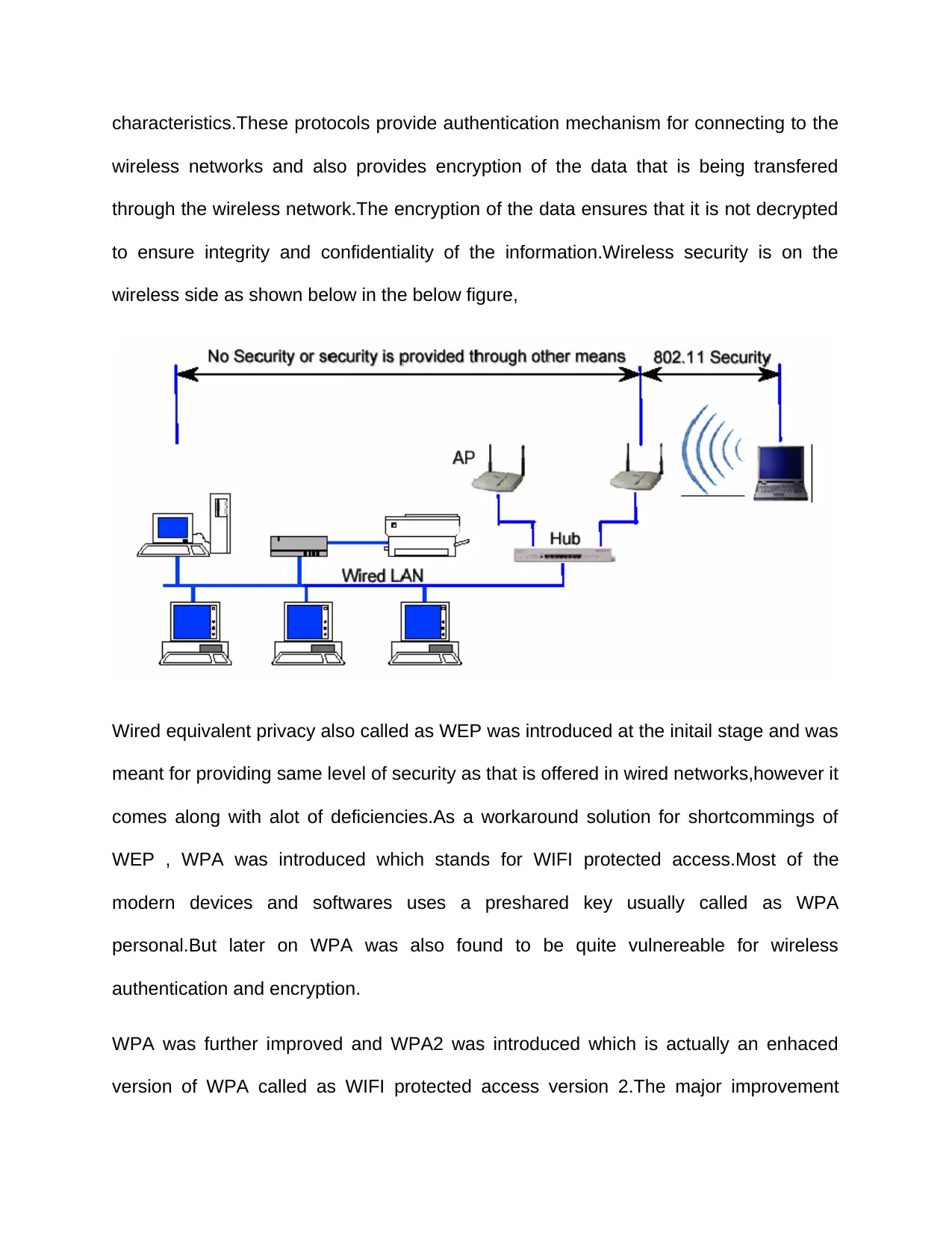
All these security protocols are implemented for the connectivity of clients with the
access points. In networks where controller based wifi solution have been deployed , it
quite easy to have strict check on the connected access points.CAPWAP (Control and
Provisioning of wireless access points) is the protocol which is governs the
communication between wireless controller and access points.Capwap is established
between access point and wireless controller as shown below as well.
enhaced security posture of wireless security.All these wireless security standards are
implemented to make sure that clients get authenticated with a reliable security protocol
along with making their communication secure.
All these security protocols are implemented for the connectivity of clients with the
access points. In networks where controller based wifi solution have been deployed , it
quite easy to have strict check on the connected access points.CAPWAP (Control and
Provisioning of wireless access points) is the protocol which is governs the
communication between wireless controller and access points.Capwap is established
between access point and wireless controller as shown below as well.

CAPWAP relies upon LWAPP (LightWeight Access Point Protocol).The communication
processesing of CAPWAP is same as LWAPP but with only difference of establishment
of a DTLS (Datagram Transport Layer Security).CAPWAP not only performs the
management of the access points but can also push the firware updates.CAPWAP also
doesnot take radio technology used for the providing connectivity to the clients.Wireless
controller can have multiple checks to ensure that only allowed access points are
connected with the controller and provide wireless services.
There is another concept called “evil-twin” which is actually when some access points
out side of the organisation recieves beacon probes from legitimate access points , after
probing the SSIDs it start broadcasting same SSIDs which are undetectable by the
users and wifi network administrator as well.There is also a concept of soft rogue AP.A
soft rogue AP is computer machine (usually a PC or a laptop) which forward network
traffic from its wirless interface to its connected secure network.If exploited by the
hacker , this type of machines can cause a great harm if used as a rogue AP as all the
network.Based on the fact that it is quite easy to setup a soft AP in computer machines ,
it has become a normal pratice by the network or system administrator to provide a
temporary wireless access for some reason (i.e. some file sharing to wireless device)
and later forget to disable it.
But unfortunately there are ways in which all these security mechanism are by passed
and a wireless router (either hardware based or software based) is deployed in the
network which broadcasts SSID (most probably with no authentication) so that users
may connect to it and start accessing their network resources.There are multiple
techniques which can ensure that no rogue access points are deployed in the network
processesing of CAPWAP is same as LWAPP but with only difference of establishment
of a DTLS (Datagram Transport Layer Security).CAPWAP not only performs the
management of the access points but can also push the firware updates.CAPWAP also
doesnot take radio technology used for the providing connectivity to the clients.Wireless
controller can have multiple checks to ensure that only allowed access points are
connected with the controller and provide wireless services.
There is another concept called “evil-twin” which is actually when some access points
out side of the organisation recieves beacon probes from legitimate access points , after
probing the SSIDs it start broadcasting same SSIDs which are undetectable by the
users and wifi network administrator as well.There is also a concept of soft rogue AP.A
soft rogue AP is computer machine (usually a PC or a laptop) which forward network
traffic from its wirless interface to its connected secure network.If exploited by the
hacker , this type of machines can cause a great harm if used as a rogue AP as all the
network.Based on the fact that it is quite easy to setup a soft AP in computer machines ,
it has become a normal pratice by the network or system administrator to provide a
temporary wireless access for some reason (i.e. some file sharing to wireless device)
and later forget to disable it.
But unfortunately there are ways in which all these security mechanism are by passed
and a wireless router (either hardware based or software based) is deployed in the
network which broadcasts SSID (most probably with no authentication) so that users
may connect to it and start accessing their network resources.There are multiple
techniques which can ensure that no rogue access points are deployed in the network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

but no specific protocol has been designed to get rid of this type of attack.All these
techniques are based on security best practices and recommendation regarding
wireless security.
4. Technical Background of rogue access
points
Technically , a rogue AP is a man in the middle attack for 802.11 wireless network.In
this attack , attacker try to gain the access of organisations internal resources and steal
important information. Even though , 802.11 protocol has very explicit rules that how a
client can join extended service set , but the selection of the access points purely
depends upon the end user device who can roam freely between multiple basic service
set identifiers that share the same ESSID.802.11 also doesnot consider the selction of
these access points within an ESSID.
Normally whenever an end user device is connected to an ESSID , this wirless network
information gets stored in a prefered network list usually called as PNL.This PNL is
basically a list all those wireless networks to which end user’s device connected in the
past and also contains this connection’s specific settings as well.
At first the end user device perform a passive scanning for the wireless access points to
which it has to connect with.The client device looks for beacon frames from surrounding
access points.IF ESSIDs in the beacon frames matches to that of in PNL list , the client
automatically connects to that ESSID and start using network services as provided by
this specific access point. The wireless communication security offered by 802.11 are
effective just for 802.11 protocol itself which only takes effect only after the client has
techniques are based on security best practices and recommendation regarding
wireless security.
4. Technical Background of rogue access
points
Technically , a rogue AP is a man in the middle attack for 802.11 wireless network.In
this attack , attacker try to gain the access of organisations internal resources and steal
important information. Even though , 802.11 protocol has very explicit rules that how a
client can join extended service set , but the selection of the access points purely
depends upon the end user device who can roam freely between multiple basic service
set identifiers that share the same ESSID.802.11 also doesnot consider the selction of
these access points within an ESSID.
Normally whenever an end user device is connected to an ESSID , this wirless network
information gets stored in a prefered network list usually called as PNL.This PNL is
basically a list all those wireless networks to which end user’s device connected in the
past and also contains this connection’s specific settings as well.
At first the end user device perform a passive scanning for the wireless access points to
which it has to connect with.The client device looks for beacon frames from surrounding
access points.IF ESSIDs in the beacon frames matches to that of in PNL list , the client
automatically connects to that ESSID and start using network services as provided by
this specific access point. The wireless communication security offered by 802.11 are
effective just for 802.11 protocol itself which only takes effect only after the client has
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

joined the access points himself.This mechanism leaves a vulnerebility that if there is
any access points which has got ESSID information stored in the clients PNL list , this
rogue AP will send probes to the client device , which automatically will join the ESSID
and will be directed to a hacker’s network.
Another technical aspect of this type of attack is also that in our wireless networks IP
addresses are assigned through DHCP (Dynamic host configuration protocol). DHCP is
for assigning IP addresses automatically as we dont want users to assign IP addresses
manually in case where the user are in a large number. So , in case of rogue AP which
gets IP address authomatically is routable device in our internal network, as it also
assigns gateway information as well. With the features that DHCP offers , rougue
access point provide network services to its clients for the connectivity which could be
misused by the attacker for sniffing sensitive information as well.
In terms of technical aspect , rogue APs can be deployed in multiple ways.One of the
ways is that the wireless device is connected through the trusted interface of the
network.In this case , wireless router will reside inside DMZ zone in the firewall and will
also provide the DHCP services as well , if not planned accordingly, its dhcp services
may cause interuption with the trusted DHCP services of the network.Wireless device
can also de deployed outside of the trusted network i.e untrusted network , in this case
AP will provide ip addresses which are not internal to the network , but still can be used
to access the network resources which are allowed through the firewall.
An attacker could also somehow install a wireless card in to the trusted network.This will
ease the job of attacker as functionality of the wireless device will be taken from
computer itself which will provide services because the chipset supports this feature as
any access points which has got ESSID information stored in the clients PNL list , this
rogue AP will send probes to the client device , which automatically will join the ESSID
and will be directed to a hacker’s network.
Another technical aspect of this type of attack is also that in our wireless networks IP
addresses are assigned through DHCP (Dynamic host configuration protocol). DHCP is
for assigning IP addresses automatically as we dont want users to assign IP addresses
manually in case where the user are in a large number. So , in case of rogue AP which
gets IP address authomatically is routable device in our internal network, as it also
assigns gateway information as well. With the features that DHCP offers , rougue
access point provide network services to its clients for the connectivity which could be
misused by the attacker for sniffing sensitive information as well.
In terms of technical aspect , rogue APs can be deployed in multiple ways.One of the
ways is that the wireless device is connected through the trusted interface of the
network.In this case , wireless router will reside inside DMZ zone in the firewall and will
also provide the DHCP services as well , if not planned accordingly, its dhcp services
may cause interuption with the trusted DHCP services of the network.Wireless device
can also de deployed outside of the trusted network i.e untrusted network , in this case
AP will provide ip addresses which are not internal to the network , but still can be used
to access the network resources which are allowed through the firewall.
An attacker could also somehow install a wireless card in to the trusted network.This will
ease the job of attacker as functionality of the wireless device will be taken from
computer itself which will provide services because the chipset supports this feature as

well.Fourth scanario comes into play when hacker try to get access of the existing
wireless device and can sniff all the user data for malicious activites.In this case
attacker can redirect the traffic or perform various filters on the traffic as per his
requirement.
5. Methods to protect against rogue APs
Whether at home or in office , people are connected to network via multiple devices i.e.
mobile phones , tablets , desktop PCs and laptop etc. Often a rouge AP is also
connected to the network and usually goes undetected untill some one physicall
observes that a new unseen device has been added to the network.There are multiple
ways that a rogue AP can be detected in a network and can be done with a systemic
approach.One of the ways to identify a rogue AP is software based in which a software
is used to scan the network and via some authentication protocols it is identified that
some devices are not being authenticated , while the other approach is physically
identify with the help of physical survey in which it can identified that some unknown
physical devices has been installed in the network.
While considering the software approcah there are alot of mechanisms used to detect
and block rogue APs.One of the most widely technique which is to apply restrictions on
the controller.The solution is applicable where all the APs are connected to the network
via a controller.Controller based solution makes it easy to manage all the access
points , this management involves management of the APs and also routing the APs
traffic as well.So , if we apply authentication mechanism for the APs to be connected
with the network i.e. only white listed APs either based on their mac address or their IP
wireless device and can sniff all the user data for malicious activites.In this case
attacker can redirect the traffic or perform various filters on the traffic as per his
requirement.
5. Methods to protect against rogue APs
Whether at home or in office , people are connected to network via multiple devices i.e.
mobile phones , tablets , desktop PCs and laptop etc. Often a rouge AP is also
connected to the network and usually goes undetected untill some one physicall
observes that a new unseen device has been added to the network.There are multiple
ways that a rogue AP can be detected in a network and can be done with a systemic
approach.One of the ways to identify a rogue AP is software based in which a software
is used to scan the network and via some authentication protocols it is identified that
some devices are not being authenticated , while the other approach is physically
identify with the help of physical survey in which it can identified that some unknown
physical devices has been installed in the network.
While considering the software approcah there are alot of mechanisms used to detect
and block rogue APs.One of the most widely technique which is to apply restrictions on
the controller.The solution is applicable where all the APs are connected to the network
via a controller.Controller based solution makes it easy to manage all the access
points , this management involves management of the APs and also routing the APs
traffic as well.So , if we apply authentication mechanism for the APs to be connected
with the network i.e. only white listed APs either based on their mac address or their IP
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

address could get connected to the network , it can resolve issue of rogue APs.Another
software based mechanism could be that an approval mechanism is followed at the
contoller according to which whenever an AP is installed into the network a request
would be sent from AP to the controller , if the controllers approves only then AP is
authorized to broadcast the allowed SSIDs otherwise AP cannot forward the user traffic
or even get user connected to itself.
Another software approach is to scan the network for the authorized APs , if an AP is
unauthorized and also connected into network it would be considered as rogue
AP.Another way of detecting a rogue AP is that if some AP is interfering with planned
radio frequency schemes adjust by the organisation , this AP must have an rogue AP as
while planning , the wireless network administrator adjusts all the frequencies so that
there is no interefence regarding the radio frequencies.Hence upon finding this
interefence , scanning can be done in the network using available software to identify
the AP.
Another very useful technique is to use Intrusion Detection Systems which not only are
used to scan network traffic but also are used to scan the network for unauthorized
APs.Several vendors provide this functionality specially Aruba network and the most
renowned brand for wireless connectivity i.e. Ruckus wireless networks.Below is the
snapshot showing how we can perform our settings in Ruckus controller to detect and
block rogue APs.
software based mechanism could be that an approval mechanism is followed at the
contoller according to which whenever an AP is installed into the network a request
would be sent from AP to the controller , if the controllers approves only then AP is
authorized to broadcast the allowed SSIDs otherwise AP cannot forward the user traffic
or even get user connected to itself.
Another software approach is to scan the network for the authorized APs , if an AP is
unauthorized and also connected into network it would be considered as rogue
AP.Another way of detecting a rogue AP is that if some AP is interfering with planned
radio frequency schemes adjust by the organisation , this AP must have an rogue AP as
while planning , the wireless network administrator adjusts all the frequencies so that
there is no interefence regarding the radio frequencies.Hence upon finding this
interefence , scanning can be done in the network using available software to identify
the AP.
Another very useful technique is to use Intrusion Detection Systems which not only are
used to scan network traffic but also are used to scan the network for unauthorized
APs.Several vendors provide this functionality specially Aruba network and the most
renowned brand for wireless connectivity i.e. Ruckus wireless networks.Below is the
snapshot showing how we can perform our settings in Ruckus controller to detect and
block rogue APs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
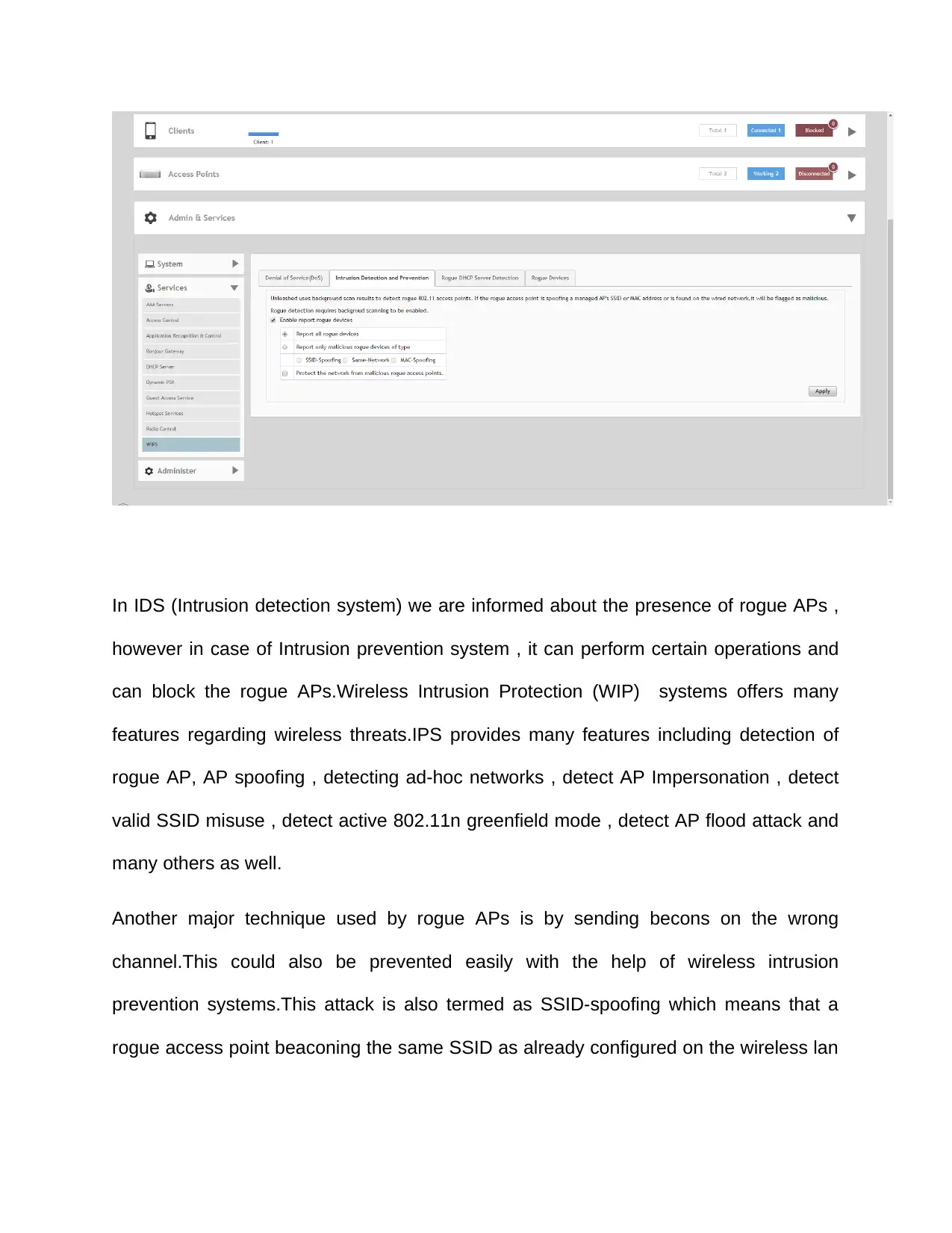
In IDS (Intrusion detection system) we are informed about the presence of rogue APs ,
however in case of Intrusion prevention system , it can perform certain operations and
can block the rogue APs.Wireless Intrusion Protection (WIP) systems offers many
features regarding wireless threats.IPS provides many features including detection of
rogue AP, AP spoofing , detecting ad-hoc networks , detect AP Impersonation , detect
valid SSID misuse , detect active 802.11n greenfield mode , detect AP flood attack and
many others as well.
Another major technique used by rogue APs is by sending becons on the wrong
channel.This could also be prevented easily with the help of wireless intrusion
prevention systems.This attack is also termed as SSID-spoofing which means that a
rogue access point beaconing the same SSID as already configured on the wireless lan
however in case of Intrusion prevention system , it can perform certain operations and
can block the rogue APs.Wireless Intrusion Protection (WIP) systems offers many
features regarding wireless threats.IPS provides many features including detection of
rogue AP, AP spoofing , detecting ad-hoc networks , detect AP Impersonation , detect
valid SSID misuse , detect active 802.11n greenfield mode , detect AP flood attack and
many others as well.
Another major technique used by rogue APs is by sending becons on the wrong
channel.This could also be prevented easily with the help of wireless intrusion
prevention systems.This attack is also termed as SSID-spoofing which means that a
rogue access point beaconing the same SSID as already configured on the wireless lan

controller and acts as a man in the middle attack to sniff users data.This could be easily
blocked by enabling checks for SSID-spoofing.
Some rogue access points can also be detected with the help of other access points by
sending network traffic on our internal network.When the packet arrive with a simiilar
mac-address to one of those identified from an over the air rogue AP.This could be also
be done by beaconing the same mac-addresses as that of authorized access points and
could use the rogue access points as honey pots, which could be prevented at the
wirless controllers by blocking the mac-spoofing attacks , and there the issue of the
rogue APs will be resolved.
The other approach is to physically inspect the network for the presence of unseen
network devices which has been not been installed the network administrator himself
and is also not authorized from the management as well.This could only be ensured by
keeping strict operation and procedures for the network operations so that if anyone
wants to install any device , he/she may have to seek approval from the management
regarding the same otherwise its not allowed to intall personal devices into the network.
6. Recommendation of a suitable
solution
A recommened solution for detecting and blocking a rogue AP would be software based
i.e. configuration on the controller so that only authenticated access points can
broadcast allowed network SSIDs.This could be done either by white listing APs on the
controller or by enforcing a approval mechanism on the controller so that each AP while
blocked by enabling checks for SSID-spoofing.
Some rogue access points can also be detected with the help of other access points by
sending network traffic on our internal network.When the packet arrive with a simiilar
mac-address to one of those identified from an over the air rogue AP.This could be also
be done by beaconing the same mac-addresses as that of authorized access points and
could use the rogue access points as honey pots, which could be prevented at the
wirless controllers by blocking the mac-spoofing attacks , and there the issue of the
rogue APs will be resolved.
The other approach is to physically inspect the network for the presence of unseen
network devices which has been not been installed the network administrator himself
and is also not authorized from the management as well.This could only be ensured by
keeping strict operation and procedures for the network operations so that if anyone
wants to install any device , he/she may have to seek approval from the management
regarding the same otherwise its not allowed to intall personal devices into the network.
6. Recommendation of a suitable
solution
A recommened solution for detecting and blocking a rogue AP would be software based
i.e. configuration on the controller so that only authenticated access points can
broadcast allowed network SSIDs.This could be done either by white listing APs on the
controller or by enforcing a approval mechanism on the controller so that each AP while
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




