Digital Certificate Technology: Security Risks and Solutions Overview
VerifiedAdded on 2020/01/16
|10
|2598
|295
Report
AI Summary
This report delves into the realm of digital certificate technology, emphasizing its pivotal role in ensuring internet security through the Public Key Infrastructure (PKI). It elucidates how digital certificates authenticate web credentials, enabling secure information exchange. The report explores the various security measures, such as confidentiality, authentication, and access control, that digital certificates provide. However, it also highlights the vulnerabilities and drawbacks associated with this technology, including the risks of fraudulent certificates, malware, and compromised Certificate Authorities (CAs). The report discusses the potential for cybercrimes and the importance of maintaining strong security practices to prevent unauthorized access to sensitive information. It also examines the ways in which digital certificates can be compromised, such as through the use of weak encryption algorithms like MD5 and the exploitation of expired or self-signed certificates. Finally, the report provides recommendations for mitigating these risks, including the use of trusted CAs, regular updates of internet client software, and the implementation of robust PKIs.

Surname 1
Name:
Instructor:
Course:
Date:
Digital Certificate Technology
Introduction
Digital certificates authenticate the web credentials of the person sending a message and
let the recipient of the message to be in a position to know that the message has come from a
trusted source. Thus, digital certificate allows computers, organization as well as people to
exchange information securely using the Public Key Infrastructure (PKI). Digital certificates
technology thus plays a significant role in security to the Internet. Security on the internet is very
important since it provides confidentiality of information, authentication, non-repudiation,
integrity and access control of the information already sent (Henderson et al., 6). However,
digital certificate technology has been faced with several drawbacks. With the development of
networks, antivirus software and firewalls have been standard measures for security. However,
using these measures of security, sometimes it cannot prevent attacks from unauthorized people
using the internet.
Name:
Instructor:
Course:
Date:
Digital Certificate Technology
Introduction
Digital certificates authenticate the web credentials of the person sending a message and
let the recipient of the message to be in a position to know that the message has come from a
trusted source. Thus, digital certificate allows computers, organization as well as people to
exchange information securely using the Public Key Infrastructure (PKI). Digital certificates
technology thus plays a significant role in security to the Internet. Security on the internet is very
important since it provides confidentiality of information, authentication, non-repudiation,
integrity and access control of the information already sent (Henderson et al., 6). However,
digital certificate technology has been faced with several drawbacks. With the development of
networks, antivirus software and firewalls have been standard measures for security. However,
using these measures of security, sometimes it cannot prevent attacks from unauthorized people
using the internet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Surname 2
Digital Certificate Technology
Digital certificate and digital signatures are made to be effective using the Public Key
Infrastructure scheme (PKI) so as to eliminate the risks such as forging of document or sending
irrelevant message to an individual. They provide identification information that prevents any
falsification whereby they provide authentication of the information and in case of any
verification it can be verified easily since the certificate is issued by a trusted agency the
certification authority (CA) .The PKI ensures a safe and secure transaction between two
counterparts in internet network (Le & Eric , 19). This security is ensured by the PKI even when
there are many users in the internet who are transacting a variety of information and data to
various people and organizations.
The browsers and the operating systems can send the already sent public keys and the
encrypted messages back to the sender since it contains symmetric key that is used to encrypt the
attachment that has the identifying data to various recipients simultaneously. A root certificate
authority signs the documents using the public and private keys to provide the evidence that the
certificate is genuine and valid. Public keys are embedded in browsers and client internet
software, and they are currently found on any modern computer. The public key and private key
can be used to sign into any program that is used in an organization to ensure that anyone using it
such as downloading software can be verified.
In digital certificates technology, if security is not properly maintained its consequences
can be disastrous to the individual or the organization using the internet since its information can
be accessed by an unauthorized person. Criminals can create websites that are fraudulent and
appear to originate from the original user and use it to fraud money to people connected to the
Digital Certificate Technology
Digital certificate and digital signatures are made to be effective using the Public Key
Infrastructure scheme (PKI) so as to eliminate the risks such as forging of document or sending
irrelevant message to an individual. They provide identification information that prevents any
falsification whereby they provide authentication of the information and in case of any
verification it can be verified easily since the certificate is issued by a trusted agency the
certification authority (CA) .The PKI ensures a safe and secure transaction between two
counterparts in internet network (Le & Eric , 19). This security is ensured by the PKI even when
there are many users in the internet who are transacting a variety of information and data to
various people and organizations.
The browsers and the operating systems can send the already sent public keys and the
encrypted messages back to the sender since it contains symmetric key that is used to encrypt the
attachment that has the identifying data to various recipients simultaneously. A root certificate
authority signs the documents using the public and private keys to provide the evidence that the
certificate is genuine and valid. Public keys are embedded in browsers and client internet
software, and they are currently found on any modern computer. The public key and private key
can be used to sign into any program that is used in an organization to ensure that anyone using it
such as downloading software can be verified.
In digital certificates technology, if security is not properly maintained its consequences
can be disastrous to the individual or the organization using the internet since its information can
be accessed by an unauthorized person. Criminals can create websites that are fraudulent and
appear to originate from the original user and use it to fraud money to people connected to the

Surname 3
organization. They can create malware that is addressed to a wrong address, and they can steal
details of credit cards or other information that is vulnerable and crucial whereby the can use it to
steal money.
Ways Digital Certificates has Compromised Security
The risks associated with using digital certificates that are weak have been widely a
matter of discussion. Numerous tools have been released in the digital market to exploit and deal
with these vulnerabilities. There has been malware that has been developed to support the efforts
of ensuring that software developed is genuine and of the right standard. Through the software
vulnerability, there have been many malware authors and advanced hackers who create fake
certificates and encourage the users to communicate and they steal their personal data.
Enterprises and organizations should learn about the dangers that are associated with the use of
insecure digital certificates and ways in which they can use to deal with them.
Digital certificates do not necessarily mean that the identity of the party has been
verified, some documents such as banknotes that have signatures can easily be duplicated
through digital data ( Akehurst-ryan et al., 8). Therefore, identifying the data from the possession
of it does not guarantee that it comes from a trusted source. To determine whether it comes from
a trusted source, one must use the digital certificate and signature that is created using private
keys. The certificate is equivalent to a document that relates an owner to a public key. These
certificates are issued by a Certificate Authority (CA) that is a trusted third party. It is trusted
since it is recognized by both the parties communicating.
organization. They can create malware that is addressed to a wrong address, and they can steal
details of credit cards or other information that is vulnerable and crucial whereby the can use it to
steal money.
Ways Digital Certificates has Compromised Security
The risks associated with using digital certificates that are weak have been widely a
matter of discussion. Numerous tools have been released in the digital market to exploit and deal
with these vulnerabilities. There has been malware that has been developed to support the efforts
of ensuring that software developed is genuine and of the right standard. Through the software
vulnerability, there have been many malware authors and advanced hackers who create fake
certificates and encourage the users to communicate and they steal their personal data.
Enterprises and organizations should learn about the dangers that are associated with the use of
insecure digital certificates and ways in which they can use to deal with them.
Digital certificates do not necessarily mean that the identity of the party has been
verified, some documents such as banknotes that have signatures can easily be duplicated
through digital data ( Akehurst-ryan et al., 8). Therefore, identifying the data from the possession
of it does not guarantee that it comes from a trusted source. To determine whether it comes from
a trusted source, one must use the digital certificate and signature that is created using private
keys. The certificate is equivalent to a document that relates an owner to a public key. These
certificates are issued by a Certificate Authority (CA) that is a trusted third party. It is trusted
since it is recognized by both the parties communicating.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Surname 4
These certificates have a finite life span of about two or three years. After that, they
expire and are no longer valid for use. They expire so that they ensure that the Certificate
Revocation List (CRL) that checks the details of the end users before accepting them. Digital
certificates have been used to secure websites and software, documents and data to encrypt the
data. The digital security problems cause a threat to the safety of an entire network infrastructure
that solely relies on the PKI, and they can be used to attack a system that is insecure.
The problems of using digital certificates may lead to disastrous consequences in
different ways. These problems may arise when the system of Certificate Authorities (CA) has
been interfered with mostly by the internet hackers. If this case happens there is a risk of hackers
being able to issue counterfeit and malicious certificates to other users, and they pretend to be the
certificate authority hence allowing them to communicate exposing their personal data details
(Aucsmith & David, 36). Such a case happened to DigiNotar, a Dutch Certificate Authority where
the Certificate authority website was hacked and the hackers issued fake certificates. These
certificates could be used to show that a particular website belongs to a bank or another vital
organization and the users could use it even to transact money. It can also be used to show that a
particular sign into software comes from a software company that is not true thus leading to
malware.
Enterprises that use the certificates that are issued by Certificate Authorities that are
trusted may also be victims of such circumstances of their system being hacked. This is because
the hackers can access vital information about the company using the fake certificates. They can
use this vital information that they have obtained from the company’s website to create a website
that is similar to the company’s website. They can be posting some misleading information about
These certificates have a finite life span of about two or three years. After that, they
expire and are no longer valid for use. They expire so that they ensure that the Certificate
Revocation List (CRL) that checks the details of the end users before accepting them. Digital
certificates have been used to secure websites and software, documents and data to encrypt the
data. The digital security problems cause a threat to the safety of an entire network infrastructure
that solely relies on the PKI, and they can be used to attack a system that is insecure.
The problems of using digital certificates may lead to disastrous consequences in
different ways. These problems may arise when the system of Certificate Authorities (CA) has
been interfered with mostly by the internet hackers. If this case happens there is a risk of hackers
being able to issue counterfeit and malicious certificates to other users, and they pretend to be the
certificate authority hence allowing them to communicate exposing their personal data details
(Aucsmith & David, 36). Such a case happened to DigiNotar, a Dutch Certificate Authority where
the Certificate authority website was hacked and the hackers issued fake certificates. These
certificates could be used to show that a particular website belongs to a bank or another vital
organization and the users could use it even to transact money. It can also be used to show that a
particular sign into software comes from a software company that is not true thus leading to
malware.
Enterprises that use the certificates that are issued by Certificate Authorities that are
trusted may also be victims of such circumstances of their system being hacked. This is because
the hackers can access vital information about the company using the fake certificates. They can
use this vital information that they have obtained from the company’s website to create a website
that is similar to the company’s website. They can be posting some misleading information about
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Surname 5
the company in that company. They can also be in a position to create malware software which
has the signature illustrating that it has been authorized by the respective company.
The use of false certificates issued by the hackers in pretext to of being the Certificate
Authority (CA) can be used to conduct cybercrimes. DigiNotar, a Dutch Certificate Authority
when its system was once hacked, the hackers sold a digital certificate to a company that did not
exist. The document was later used to carry out cybercrimes through the use of malware.
Malware helps the cyber criminals to steal digital certificates and private keys associated with
particular users. Some malware is even capable of stealing private keys and the digital
certificates from windows stores. These codes can be used to destroy the operating systems'
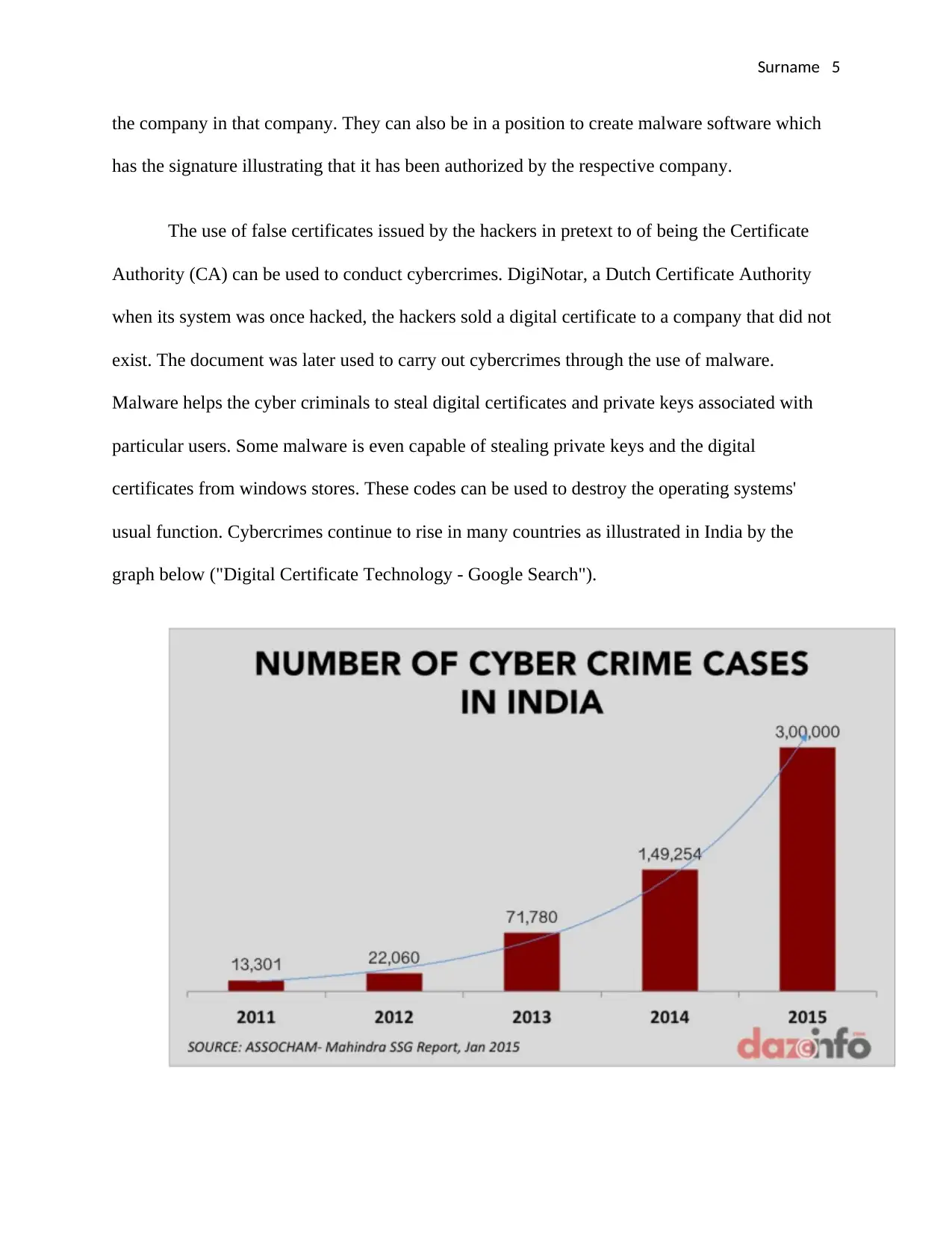
usual function. Cybercrimes continue to rise in many countries as illustrated in India by the
graph below ("Digital Certificate Technology - Google Search").
the company in that company. They can also be in a position to create malware software which
has the signature illustrating that it has been authorized by the respective company.
The use of false certificates issued by the hackers in pretext to of being the Certificate
Authority (CA) can be used to conduct cybercrimes. DigiNotar, a Dutch Certificate Authority
when its system was once hacked, the hackers sold a digital certificate to a company that did not
exist. The document was later used to carry out cybercrimes through the use of malware.
Malware helps the cyber criminals to steal digital certificates and private keys associated with
particular users. Some malware is even capable of stealing private keys and the digital
certificates from windows stores. These codes can be used to destroy the operating systems'
usual function. Cybercrimes continue to rise in many countries as illustrated in India by the
graph below ("Digital Certificate Technology - Google Search").

Surname 6
However, there are various measures you can take to prevent being a victim of the
fraudulent certificates. Though it is not possible to protect the organization directly from
fraudulent certificates, one can ensure that the company’s website has digital certificate from the
certificate authorities such that it can be trusted by the users. This digital certificate will continue
to be trusted by the end users until the security breach has occurred and added to a Certificate
Revocation List. The browsers are then updated, or are said to have expired. This can help to
ensure that the Internet client software is updated and installed as soon as they are available.
Ones the digital certificates expire, they become worthless. This is because the browsers
would warn the users when the documents are being presented that it has expired. When the
company does not renew them, some users find it easy to trust the expired certificates because
they still believe that they are still valid ( Aday et al., 22).This creates an opportunity for hackers
and fraudsters. Trusting the expired certificates is like ignoring certificates that have been
revoked previously by the Certificate Authority. This is because they do not appear in the
Certificate Revocation List. Ignoring the certificates that have expired even for a few hours or
minutes also creates a high vulnerability to risks for an organization.
If the hackers in case infiltrate the company’s website due to the expiration of the
certificates, they are most likely to target a group that has the least define assets. Most companies
are not aware of the vulnerability and the risks that their expired certificates can have. They
therefore, fail to provide full protection adequately and efficiently their websites.
The use of self-signed certificates that are downloaded also keeps organizations at a high
risk of its website being hacked. There are many in-house software developers that instead of
buying certificates from the Certificate Authorities, they develop and test the software. This turns
However, there are various measures you can take to prevent being a victim of the
fraudulent certificates. Though it is not possible to protect the organization directly from
fraudulent certificates, one can ensure that the company’s website has digital certificate from the
certificate authorities such that it can be trusted by the users. This digital certificate will continue
to be trusted by the end users until the security breach has occurred and added to a Certificate
Revocation List. The browsers are then updated, or are said to have expired. This can help to
ensure that the Internet client software is updated and installed as soon as they are available.
Ones the digital certificates expire, they become worthless. This is because the browsers
would warn the users when the documents are being presented that it has expired. When the
company does not renew them, some users find it easy to trust the expired certificates because
they still believe that they are still valid ( Aday et al., 22).This creates an opportunity for hackers
and fraudsters. Trusting the expired certificates is like ignoring certificates that have been
revoked previously by the Certificate Authority. This is because they do not appear in the
Certificate Revocation List. Ignoring the certificates that have expired even for a few hours or
minutes also creates a high vulnerability to risks for an organization.
If the hackers in case infiltrate the company’s website due to the expiration of the
certificates, they are most likely to target a group that has the least define assets. Most companies
are not aware of the vulnerability and the risks that their expired certificates can have. They
therefore, fail to provide full protection adequately and efficiently their websites.
The use of self-signed certificates that are downloaded also keeps organizations at a high
risk of its website being hacked. There are many in-house software developers that instead of
buying certificates from the Certificate Authorities, they develop and test the software. This turns
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Surname 7
to be a major problem when these self-signed certificates end up being in a produced version of
software. These certificates may be stored in a software developer’s personal computer,
unprotected by any security tools and mechanisms.
Certificates that use the MD5 hashing algorithm allow hackers to generate their own data
that gives them the authority to produce code that is used to sign in digital certificates. Many
organizations still use such algorithm unwittingly (Schwabach & Aaron, 18). Many digital
certificates attacks do not necessarily lead to the execution of codes, but they show the weak
vulnerabilities that receive little or no attention than any other threats on the internet.
Digital certificate crime should be put into keen attention. The MD5 algorithm has been
targeted by many hackers, and there have been many collision attacks by attackers that are
determined to use them to generate some codes to create some fake certificates. Compared to the
SHA-1 and the SHA-2 certificates, the MD5 certificates are more risky to use.
Malware can issue certificates that are illegitimate that appears to be official. A good
example is whereby in 2011, there was an attack on Microsoft’s software via a malware that
attacked the Windows update and issued illegal certificates that were invalid. This gave a chance
the hackers to obtain some vital details and issue some illegal certificates.
Conclusion
To ensure that certificates are fully secure, organizations have to make sure that they take
a more active stance on the way they handle digital certificates in use along with other system
configurations within the organization. Organizations may use digital certificates that are issued
by Certificate Authorities that are trusted, while they can take an additional step in implementing
to be a major problem when these self-signed certificates end up being in a produced version of
software. These certificates may be stored in a software developer’s personal computer,
unprotected by any security tools and mechanisms.
Certificates that use the MD5 hashing algorithm allow hackers to generate their own data
that gives them the authority to produce code that is used to sign in digital certificates. Many
organizations still use such algorithm unwittingly (Schwabach & Aaron, 18). Many digital
certificates attacks do not necessarily lead to the execution of codes, but they show the weak
vulnerabilities that receive little or no attention than any other threats on the internet.
Digital certificate crime should be put into keen attention. The MD5 algorithm has been
targeted by many hackers, and there have been many collision attacks by attackers that are
determined to use them to generate some codes to create some fake certificates. Compared to the
SHA-1 and the SHA-2 certificates, the MD5 certificates are more risky to use.
Malware can issue certificates that are illegitimate that appears to be official. A good
example is whereby in 2011, there was an attack on Microsoft’s software via a malware that
attacked the Windows update and issued illegal certificates that were invalid. This gave a chance
the hackers to obtain some vital details and issue some illegal certificates.
Conclusion
To ensure that certificates are fully secure, organizations have to make sure that they take
a more active stance on the way they handle digital certificates in use along with other system
configurations within the organization. Organizations may use digital certificates that are issued
by Certificate Authorities that are trusted, while they can take an additional step in implementing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Surname 8
their PKIs that could be outsourced. The PKI found in their Certificate Authorities are the ones
that they should be used in their system. This ensures that there is maximum control of the
certificates being used and organizations should only trust their internal Certificate Authorities.
Such a configuration helps in avoiding digital certificates at high risk that rely on the MD5
algorithms and other encryption keys that are weak.
Depending on the total number of users who use insecure certificates, the user
administrators and organizations can replace their certificates manually or update their
configuration settings (Nedeltchev et al., 16). To change any digital certificate or update it, the
team needs to understand that all the changes they need have to be backed up. The efforts used in
changing these digital certificates should meet the long-term goals of securing data and
eliminating any potential threats that may arise in the future. Providing such services depends on
the certificates used for encryption and should help to evaluate the documents so as to determine
whether the certificate is secure or not.
Hackers and attackers have not been able to exploit the vulnerable certificates fully to
perform malicious software verification and signing in. Enterprises need to understand that these
certificates are essential elements that can prevent any digital security certificate problems.
Addressing these vulnerabilities as fast as possible will ensure that companies and their
customers are not at risk of losing their trusted data (Sheridan et al., 41).The high operational cost
of PKI has to be given attention so as to optimize the assessment of certificates which has a
majority of its accounts issuing licenses. In cases where a new system may be built,
administration of IDs and PKI can be linked to users using a Single Sign-on (SSO) procedure or
their PKIs that could be outsourced. The PKI found in their Certificate Authorities are the ones
that they should be used in their system. This ensures that there is maximum control of the
certificates being used and organizations should only trust their internal Certificate Authorities.
Such a configuration helps in avoiding digital certificates at high risk that rely on the MD5
algorithms and other encryption keys that are weak.
Depending on the total number of users who use insecure certificates, the user
administrators and organizations can replace their certificates manually or update their
configuration settings (Nedeltchev et al., 16). To change any digital certificate or update it, the
team needs to understand that all the changes they need have to be backed up. The efforts used in
changing these digital certificates should meet the long-term goals of securing data and
eliminating any potential threats that may arise in the future. Providing such services depends on
the certificates used for encryption and should help to evaluate the documents so as to determine
whether the certificate is secure or not.
Hackers and attackers have not been able to exploit the vulnerable certificates fully to
perform malicious software verification and signing in. Enterprises need to understand that these
certificates are essential elements that can prevent any digital security certificate problems.
Addressing these vulnerabilities as fast as possible will ensure that companies and their
customers are not at risk of losing their trusted data (Sheridan et al., 41).The high operational cost
of PKI has to be given attention so as to optimize the assessment of certificates which has a
majority of its accounts issuing licenses. In cases where a new system may be built,
administration of IDs and PKI can be linked to users using a Single Sign-on (SSO) procedure or

Surname 9
an IC card for data storage and distribution. This will ensure that there is a reliable way of
authenticating PKI and SSO.
an IC card for data storage and distribution. This will ensure that there is a reliable way of
authenticating PKI and SSO.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Surname 10
Work Cited
Aday, Michael A., and Bryan M. Willman. "System and method for assigning quality to cryptographaic
identities used in a digital transaction." U.S. Patent No. 9,313,197. 12 Apr. 2016.
Akehurst-ryan, Andrew D., David J. Mckechan, and Stuart J. Reece. "EMBEDDED EXTRINSIC SOURCE
FOR DIGITAL CERTIFICATE VALIDATION." U.S. Patent No. 20,160,127,355. 5 May 2016.
Aucsmith, David W. "Method of caching digital certificate revocation lists." U.S. Patent No. 6,134,551. 17
Oct. 2000.
"Digital Certificate Technology - Google Search". Google.com. N.p., 2016. Web. 1 July 2016.
Henderson, Michael, Glenn Finger, and Neil Selwyn. "What’s used and what’s useful? Exploring digital
technology use (s) among taught postgraduate students." Active Learning in Higher
Education (2016): 1469787416654798.
Le Saint, Eric F. "Trusted and unsupervised digital certificate generation using a security token." U.S.
Patent No. 9,331,990. 3 May 2016.
Nedeltchev, Plamen, Robert T. Bell, and Max Pritikin. "Secure network deployment." U.S. Patent No.
9,264,422. 16 Feb. 2016.
Schwabach, Aaron. Internet And The Law. Print.
Sheridan, Denis M., Weimin Tsai, and Neil Edward Bergman. "Dynamic digital certificate updating." U.S.
Patent Application No. 14/843,551.
Work Cited
Aday, Michael A., and Bryan M. Willman. "System and method for assigning quality to cryptographaic
identities used in a digital transaction." U.S. Patent No. 9,313,197. 12 Apr. 2016.
Akehurst-ryan, Andrew D., David J. Mckechan, and Stuart J. Reece. "EMBEDDED EXTRINSIC SOURCE
FOR DIGITAL CERTIFICATE VALIDATION." U.S. Patent No. 20,160,127,355. 5 May 2016.
Aucsmith, David W. "Method of caching digital certificate revocation lists." U.S. Patent No. 6,134,551. 17
Oct. 2000.
"Digital Certificate Technology - Google Search". Google.com. N.p., 2016. Web. 1 July 2016.
Henderson, Michael, Glenn Finger, and Neil Selwyn. "What’s used and what’s useful? Exploring digital
technology use (s) among taught postgraduate students." Active Learning in Higher
Education (2016): 1469787416654798.
Le Saint, Eric F. "Trusted and unsupervised digital certificate generation using a security token." U.S.
Patent No. 9,331,990. 3 May 2016.
Nedeltchev, Plamen, Robert T. Bell, and Max Pritikin. "Secure network deployment." U.S. Patent No.
9,264,422. 16 Feb. 2016.
Schwabach, Aaron. Internet And The Law. Print.
Sheridan, Denis M., Weimin Tsai, and Neil Edward Bergman. "Dynamic digital certificate updating." U.S.
Patent Application No. 14/843,551.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





