Security to Digital Communication: Cryptography and Algorithms
VerifiedAdded on 2022/12/14
|27
|6077
|219
Report
AI Summary
This report delves into the critical aspects of security in digital communication, exploring various cryptographic methods and algorithms. It begins with an introduction to cryptography, differentiating between symmetric, asymmetric, and hashing techniques. The report then examines SHA-3, discussing its advantages such as performance, security, and bitstream capabilities, while also addressing its disadvantages. Furthermore, it investigates Lamport's algorithm, detailing the process of key pair creation and message signing. The report also includes an overview of cryptanalysis, including classical attacks, social engineering, and implementation attacks. The document provides an analysis of the strengths and weaknesses of these security measures, offering a comprehensive understanding of digital communication security. The assignment is based on the ICA from Teesside University for the COM4056 module.

Running head: SECURITY TO DIGITAL COMMUNICATION 1
SECURITY TO DIGITAL COMMUNICATION
Student’s Name:
Institution Affiliation:
Course Name:
Professor’s Name:
Due Date:
SECURITY TO DIGITAL COMMUNICATION
Student’s Name:
Institution Affiliation:
Course Name:
Professor’s Name:
Due Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SECURITY TO DIGITAL COMMUNICATION 4
Question One
Cryptography
Introduction
Cryptography is a significant viewpoint when we manage to arrange security. 'Crypto' signifies
mystery or covered up. Cryptography is the study of mystery composing with the aim of keeping
the information mystery. Cryptanalysis, then again, is the science or once in a while the specialty of
breaking cryptosystems. These two terms are a subset of what is called as Cryptology[1].
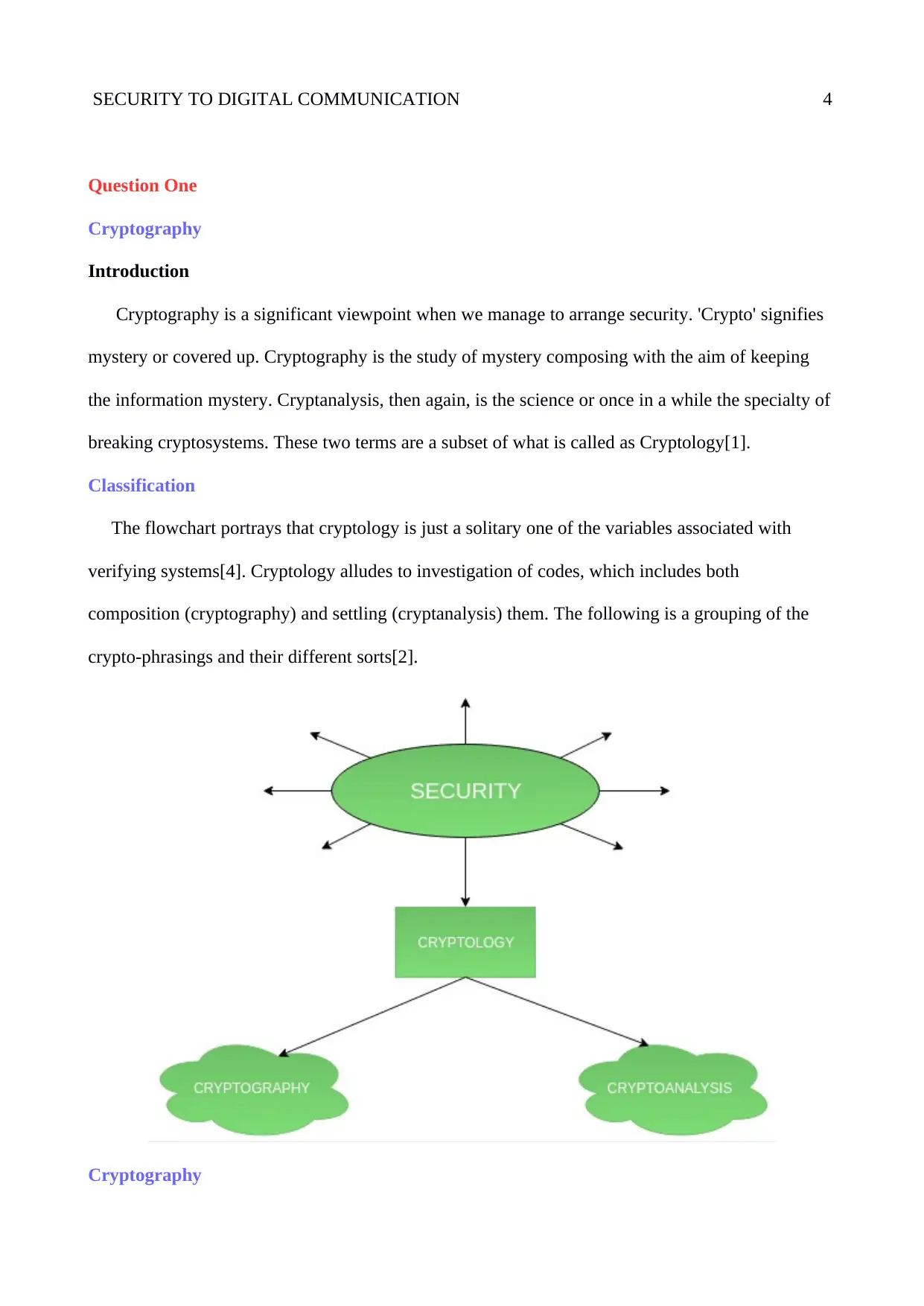
Classification
The flowchart portrays that cryptology is just a solitary one of the variables associated with
verifying systems[4]. Cryptology alludes to investigation of codes, which includes both
composition (cryptography) and settling (cryptanalysis) them. The following is a grouping of the
crypto-phrasings and their different sorts[2].
Cryptography
Question One
Cryptography
Introduction
Cryptography is a significant viewpoint when we manage to arrange security. 'Crypto' signifies
mystery or covered up. Cryptography is the study of mystery composing with the aim of keeping
the information mystery. Cryptanalysis, then again, is the science or once in a while the specialty of
breaking cryptosystems. These two terms are a subset of what is called as Cryptology[1].
Classification
The flowchart portrays that cryptology is just a solitary one of the variables associated with
verifying systems[4]. Cryptology alludes to investigation of codes, which includes both
composition (cryptography) and settling (cryptanalysis) them. The following is a grouping of the
crypto-phrasings and their different sorts[2].
Cryptography
SECURITY TO DIGITAL COMMUNICATION 3
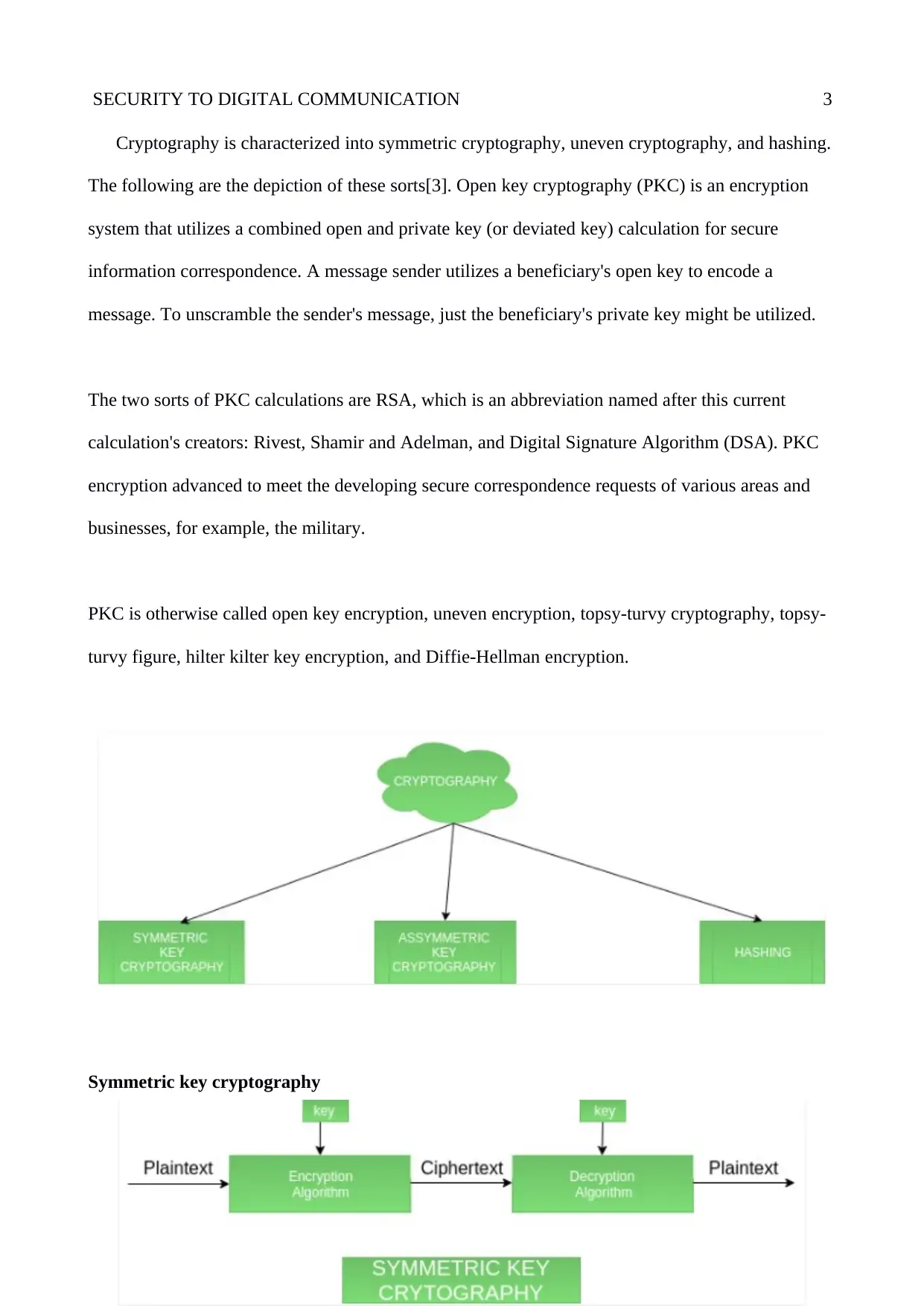
Cryptography is characterized into symmetric cryptography, uneven cryptography, and hashing.
The following are the depiction of these sorts[3]. Open key cryptography (PKC) is an encryption
system that utilizes a combined open and private key (or deviated key) calculation for secure
information correspondence. A message sender utilizes a beneficiary's open key to encode a
message. To unscramble the sender's message, just the beneficiary's private key might be utilized.
The two sorts of PKC calculations are RSA, which is an abbreviation named after this current
calculation's creators: Rivest, Shamir and Adelman, and Digital Signature Algorithm (DSA). PKC
encryption advanced to meet the developing secure correspondence requests of various areas and
businesses, for example, the military.
PKC is otherwise called open key encryption, uneven encryption, topsy-turvy cryptography, topsy-
turvy figure, hilter kilter key encryption, and Diffie-Hellman encryption.
Symmetric key cryptography
Cryptography is characterized into symmetric cryptography, uneven cryptography, and hashing.
The following are the depiction of these sorts[3]. Open key cryptography (PKC) is an encryption
system that utilizes a combined open and private key (or deviated key) calculation for secure
information correspondence. A message sender utilizes a beneficiary's open key to encode a
message. To unscramble the sender's message, just the beneficiary's private key might be utilized.
The two sorts of PKC calculations are RSA, which is an abbreviation named after this current
calculation's creators: Rivest, Shamir and Adelman, and Digital Signature Algorithm (DSA). PKC
encryption advanced to meet the developing secure correspondence requests of various areas and
businesses, for example, the military.
PKC is otherwise called open key encryption, uneven encryption, topsy-turvy cryptography, topsy-
turvy figure, hilter kilter key encryption, and Diffie-Hellman encryption.
Symmetric key cryptography
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SECURITY TO DIGITAL COMMUNICATION 4
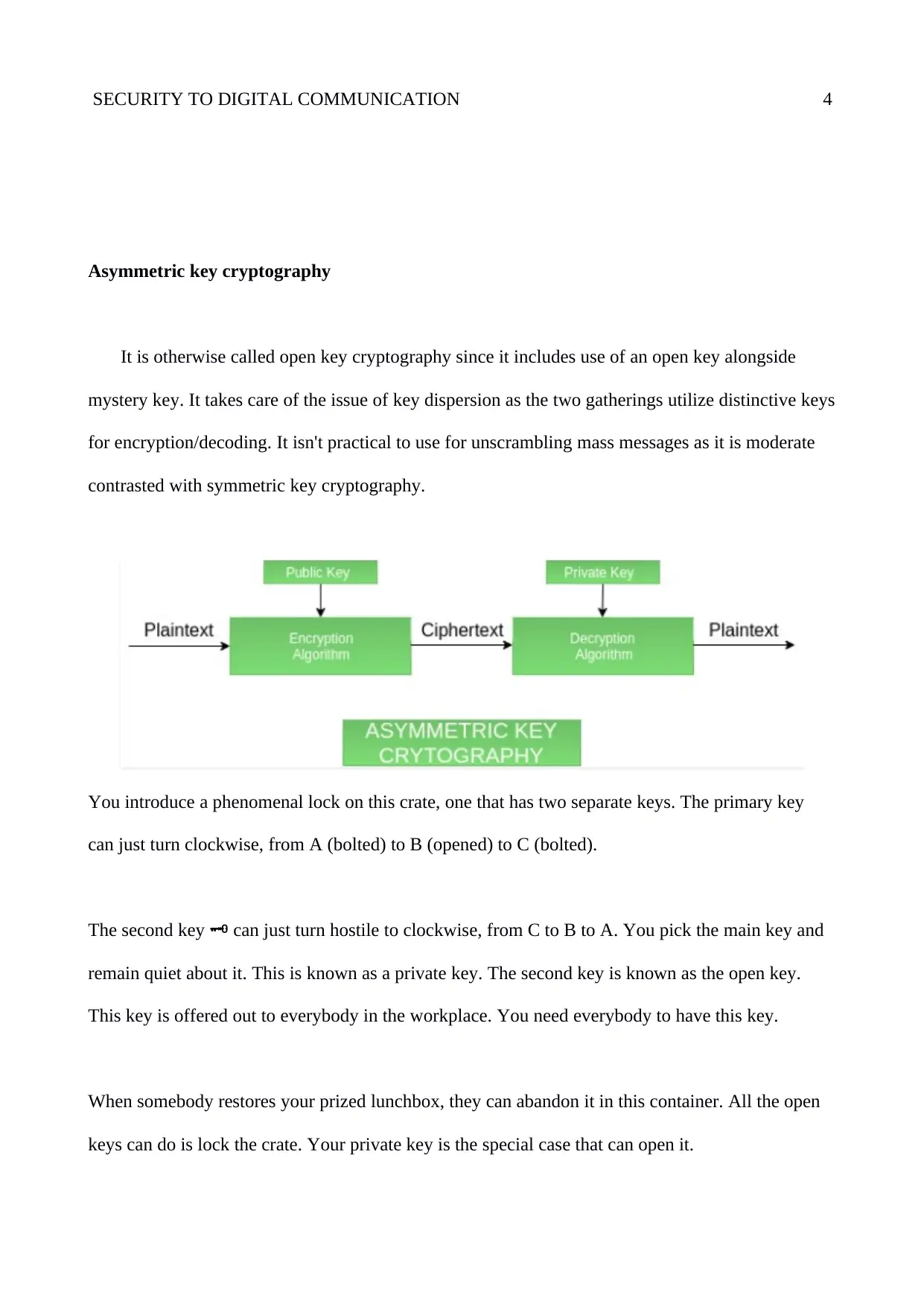
Asymmetric key cryptography
It is otherwise called open key cryptography since it includes use of an open key alongside
mystery key. It takes care of the issue of key dispersion as the two gatherings utilize distinctive keys
for encryption/decoding. It isn't practical to use for unscrambling mass messages as it is moderate
contrasted with symmetric key cryptography.
You introduce a phenomenal lock on this crate, one that has two separate keys. The primary key 🔑
can just turn clockwise, from A (bolted) to B (opened) to C (bolted).
The second key can just turn hostile to clockwise, from C to B to A. You pick the main key and🗝️
remain quiet about it. This is known as a private key. The second key is known as the open key.
This key is offered out to everybody in the workplace. You need everybody to have this key.
When somebody restores your prized lunchbox, they can abandon it in this container. All the open
keys can do is lock the crate. Your private key is the special case that can open it.
Asymmetric key cryptography
It is otherwise called open key cryptography since it includes use of an open key alongside
mystery key. It takes care of the issue of key dispersion as the two gatherings utilize distinctive keys
for encryption/decoding. It isn't practical to use for unscrambling mass messages as it is moderate
contrasted with symmetric key cryptography.
You introduce a phenomenal lock on this crate, one that has two separate keys. The primary key 🔑
can just turn clockwise, from A (bolted) to B (opened) to C (bolted).
The second key can just turn hostile to clockwise, from C to B to A. You pick the main key and🗝️
remain quiet about it. This is known as a private key. The second key is known as the open key.
This key is offered out to everybody in the workplace. You need everybody to have this key.
When somebody restores your prized lunchbox, they can abandon it in this container. All the open
keys can do is lock the crate. Your private key is the special case that can open it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SECURITY TO DIGITAL COMMUNICATION 3
This is open key cryptography. Everybody realizes that in the event that they place something in the
container and lock it, no one but you can open it with your private key.
With symmetric cryptography, everybody could open your crate on the off chance that they had the
key. Presently, nobody separated from you can open the container.
Open key cryptography was first planned by Whitfield-Diffie or James (Ellis found first, yet he
didn't distribute it. Whitfield-Diffie distributed first). The two Ellis and Whitfield-Diffie delighted
in that open key cryptography could work in principle, however never figured out how to make
sense of how it would function by and by.
The creation of a working Public Key Encryption framework is credited to Rivest– Shamir–
Adleman (RSA) or Clifford Cocks. Like above, Cocks found first, yet he didn't distribute it. Rivest–
Shamir– Adleman distributed first.
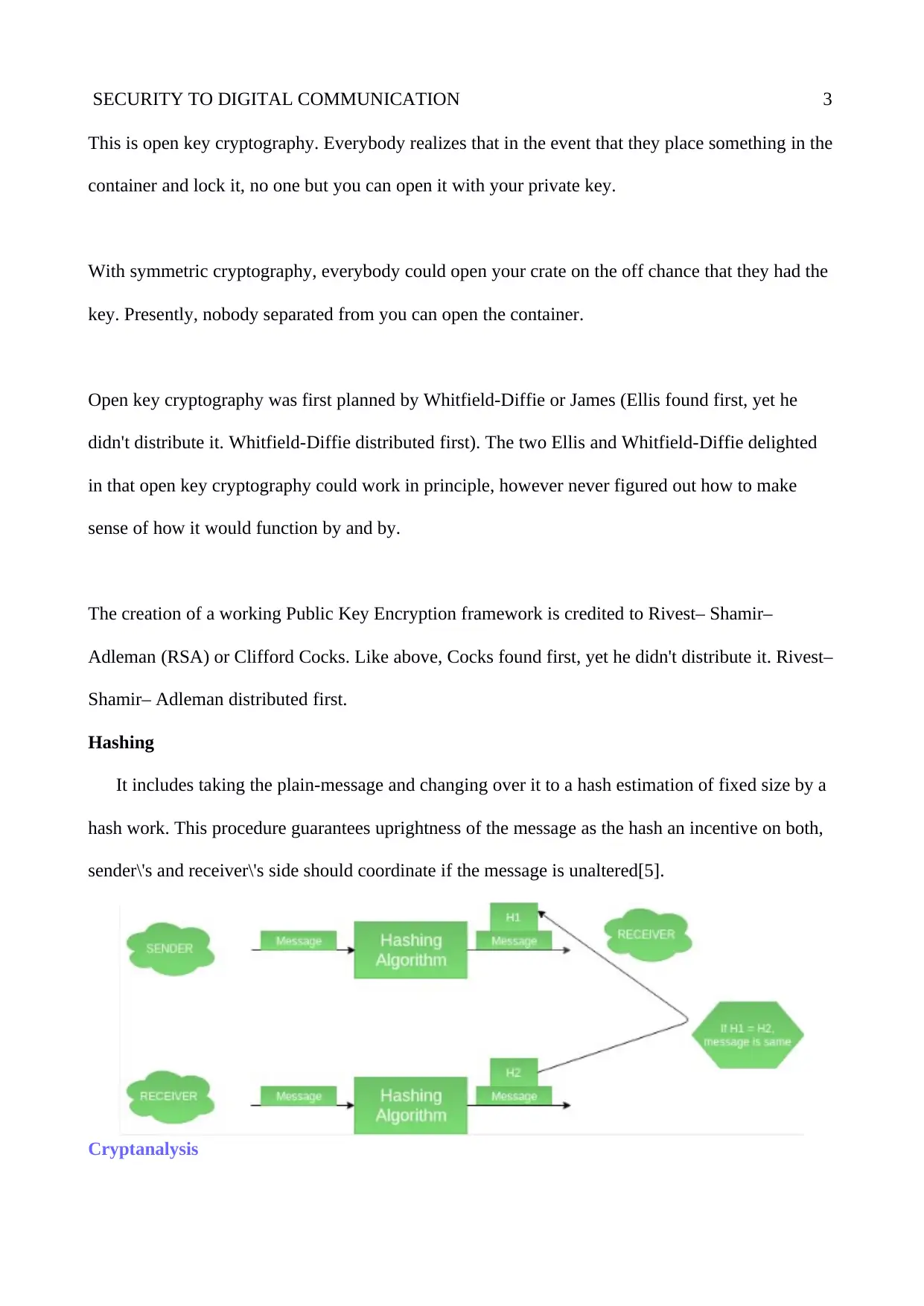
Hashing
It includes taking the plain-message and changing over it to a hash estimation of fixed size by a
hash work. This procedure guarantees uprightness of the message as the hash an incentive on both,
sender\'s and receiver\'s side should coordinate if the message is unaltered[5].
Cryptanalysis
This is open key cryptography. Everybody realizes that in the event that they place something in the
container and lock it, no one but you can open it with your private key.
With symmetric cryptography, everybody could open your crate on the off chance that they had the
key. Presently, nobody separated from you can open the container.
Open key cryptography was first planned by Whitfield-Diffie or James (Ellis found first, yet he
didn't distribute it. Whitfield-Diffie distributed first). The two Ellis and Whitfield-Diffie delighted
in that open key cryptography could work in principle, however never figured out how to make
sense of how it would function by and by.
The creation of a working Public Key Encryption framework is credited to Rivest– Shamir–
Adleman (RSA) or Clifford Cocks. Like above, Cocks found first, yet he didn't distribute it. Rivest–
Shamir– Adleman distributed first.
Hashing
It includes taking the plain-message and changing over it to a hash estimation of fixed size by a
hash work. This procedure guarantees uprightness of the message as the hash an incentive on both,
sender\'s and receiver\'s side should coordinate if the message is unaltered[5].
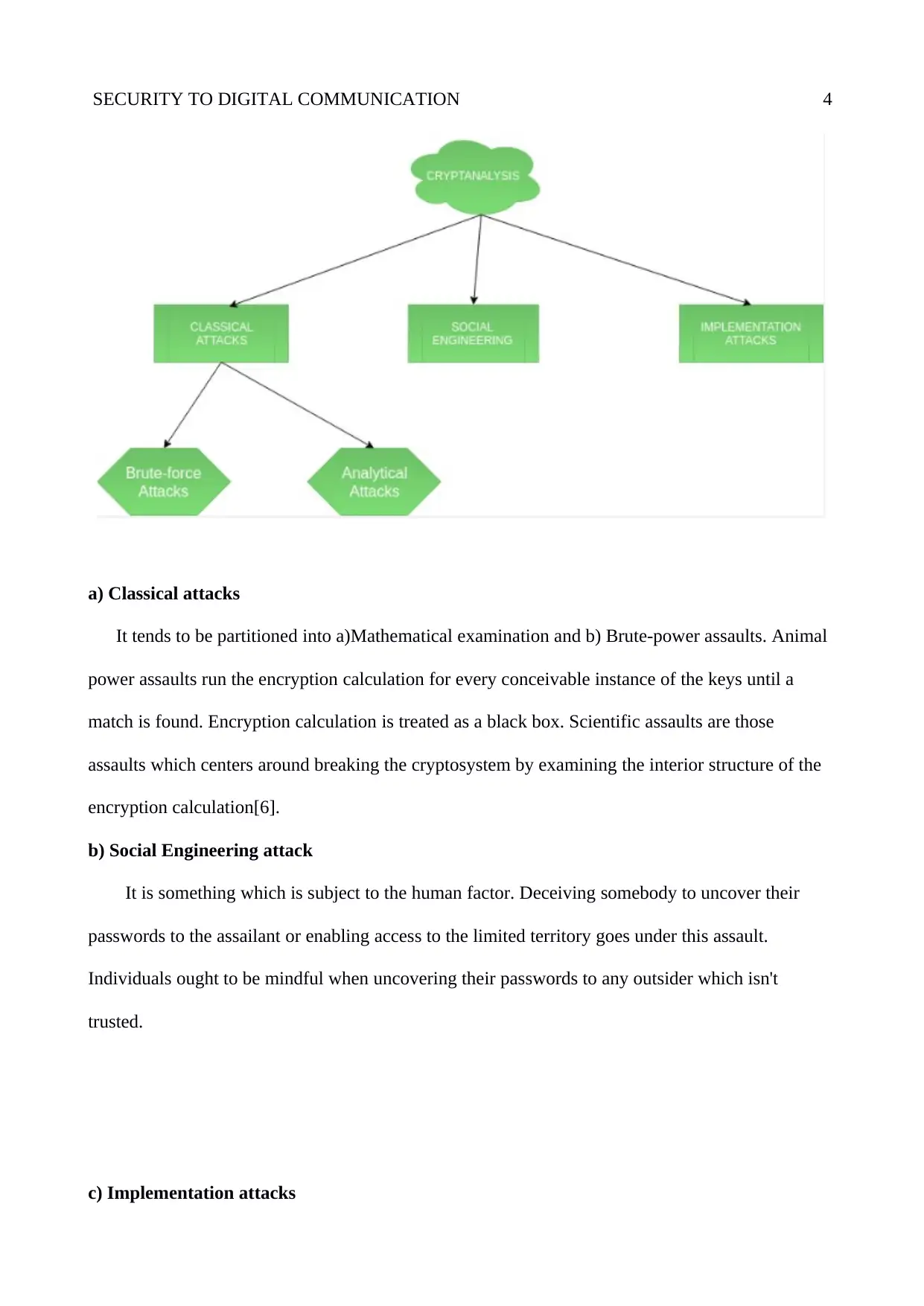
Cryptanalysis
SECURITY TO DIGITAL COMMUNICATION 4
a) Classical attacks
It tends to be partitioned into a)Mathematical examination and b) Brute-power assaults. Animal
power assaults run the encryption calculation for every conceivable instance of the keys until a
match is found. Encryption calculation is treated as a black box. Scientific assaults are those
assaults which centers around breaking the cryptosystem by examining the interior structure of the
encryption calculation[6].
b) Social Engineering attack
It is something which is subject to the human factor. Deceiving somebody to uncover their
passwords to the assailant or enabling access to the limited territory goes under this assault.
Individuals ought to be mindful when uncovering their passwords to any outsider which isn't
trusted.
c) Implementation attacks
a) Classical attacks
It tends to be partitioned into a)Mathematical examination and b) Brute-power assaults. Animal
power assaults run the encryption calculation for every conceivable instance of the keys until a
match is found. Encryption calculation is treated as a black box. Scientific assaults are those
assaults which centers around breaking the cryptosystem by examining the interior structure of the
encryption calculation[6].
b) Social Engineering attack
It is something which is subject to the human factor. Deceiving somebody to uncover their
passwords to the assailant or enabling access to the limited territory goes under this assault.
Individuals ought to be mindful when uncovering their passwords to any outsider which isn't
trusted.
c) Implementation attacks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY TO DIGITAL COMMUNICATION 3
Execution assaults, for example, the side-channel examination can be utilized to acquire a
mystery key. They are pertinent in situations where the assailant can get physical access to the
cryptosystem.
Question Two
Introduction
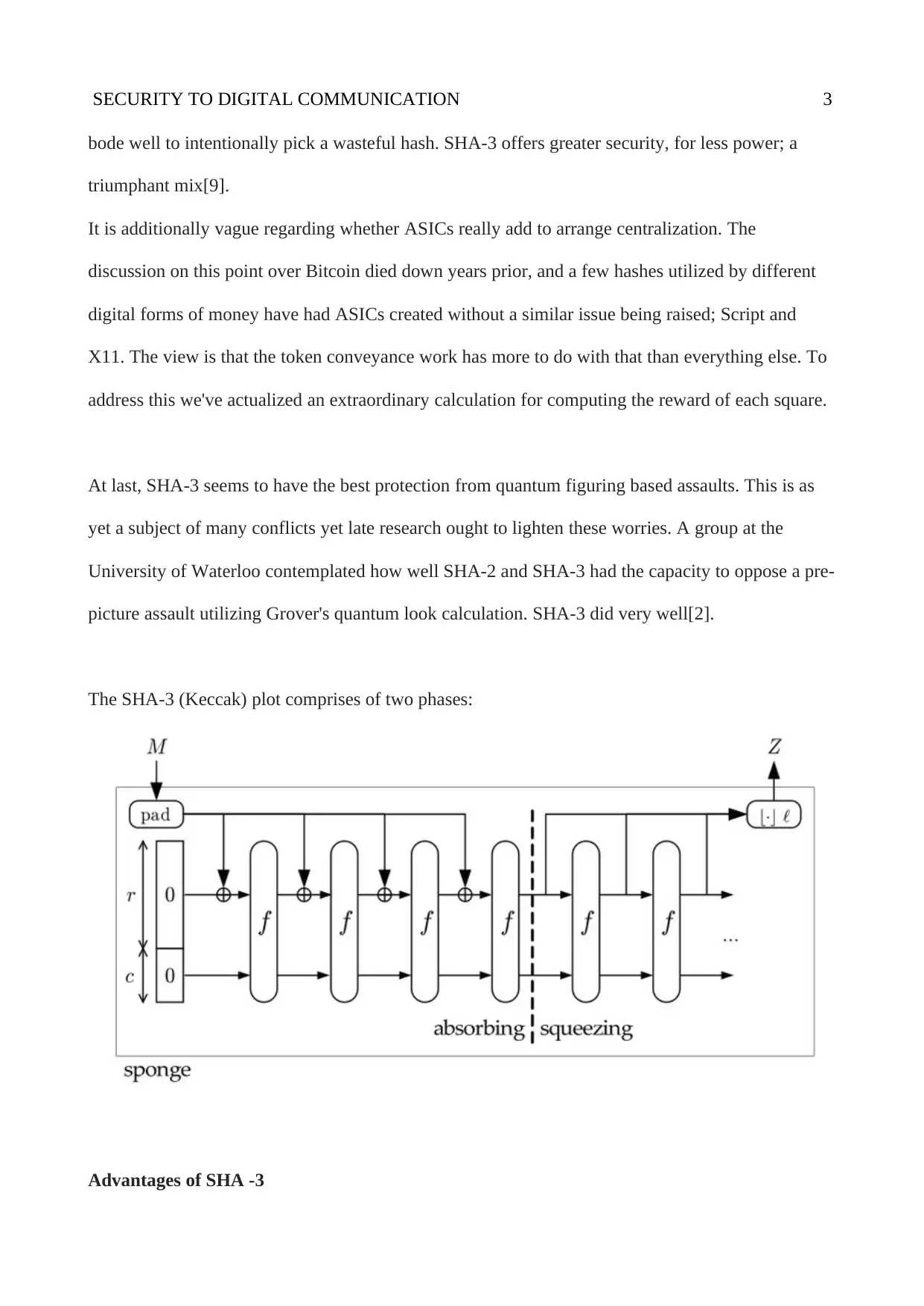
SHA-3 calculation Keccak
SHA-3 (Secure Hash Algorithm Version 3), likewise called Keccak, is a unidirectional capacity for
producing advanced prints of the chose length (the standard acknowledges 224, 256, 384 or 512
bits) from info information of any size, created by a gathering of creators driven by Yoan Dimen in
2008 and received in 2015 as the new FIPS standard. The calculation works by methods for the
blending capacity with pressure to the chose size "cryptographic wipe"[7].
The first Keccak calculation has numerous configurable parameters (information square size,
calculation state estimate, number of rounds in the f word, and so on.) so as to give an ideal
proportion of cryptographic security and execution for application on the chose stage. The
adaptation of SHA-3 calculation has a few contracts from the first keccak calculation:
moderate modes c=768 and c=1024 are disposed of
disentangled calculation of filling
Execution assaults, for example, the side-channel examination can be utilized to acquire a
mystery key. They are pertinent in situations where the assailant can get physical access to the
cryptosystem.
Question Two
Introduction
SHA-3 calculation Keccak
SHA-3 (Secure Hash Algorithm Version 3), likewise called Keccak, is a unidirectional capacity for
producing advanced prints of the chose length (the standard acknowledges 224, 256, 384 or 512
bits) from info information of any size, created by a gathering of creators driven by Yoan Dimen in
2008 and received in 2015 as the new FIPS standard. The calculation works by methods for the
blending capacity with pressure to the chose size "cryptographic wipe"[7].
The first Keccak calculation has numerous configurable parameters (information square size,
calculation state estimate, number of rounds in the f word, and so on.) so as to give an ideal
proportion of cryptographic security and execution for application on the chose stage. The
adaptation of SHA-3 calculation has a few contracts from the first keccak calculation:
moderate modes c=768 and c=1024 are disposed of
disentangled calculation of filling
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY TO DIGITAL COMMUNICATION 4
presented" capacities with an all-inclusive outcome "(XOF, Extendable-Output Functions)
SHAKE128 and SHAKE256, for which the hash message was important to Supplement the"
addition " of 2 or 4 bits, contingent upon the sort of capacity.
The reference usage source code was devoted to open area by means of CC0 waiver. Albeit part of
a similar arrangement of principles, SHA-3 is inside very not the same as the MD5-like structure of
SHA-1 and SHA-2[8].
Sha -3 ASIC
SHA-3 runs well on ASICs and excavators consider this to be a key preferred standpoint. The
Keccak group states "Its throughput for a given circuit region is a request of size higher than SHA-2
or any of the SHA-3 finalists. What's more, on the off chance that you care past plain speed, note
that it additionally devours considerably less vitality per bit. In this sense, Keccak is a green
cryptographic crude." as far as they could possibly know ASICs for SHA-3 are not yet generally
accessible. Security is the top concern and more noteworthy system hash rate implies a lot harder
focus for criminals. Hashes that are memory-escalated, or utilize different intends to decrease the
benefit of particular equipment, make for systems that are simpler to topple. Consequently, it didn't
presented" capacities with an all-inclusive outcome "(XOF, Extendable-Output Functions)
SHAKE128 and SHAKE256, for which the hash message was important to Supplement the"
addition " of 2 or 4 bits, contingent upon the sort of capacity.
The reference usage source code was devoted to open area by means of CC0 waiver. Albeit part of
a similar arrangement of principles, SHA-3 is inside very not the same as the MD5-like structure of
SHA-1 and SHA-2[8].
Sha -3 ASIC
SHA-3 runs well on ASICs and excavators consider this to be a key preferred standpoint. The
Keccak group states "Its throughput for a given circuit region is a request of size higher than SHA-2
or any of the SHA-3 finalists. What's more, on the off chance that you care past plain speed, note
that it additionally devours considerably less vitality per bit. In this sense, Keccak is a green
cryptographic crude." as far as they could possibly know ASICs for SHA-3 are not yet generally
accessible. Security is the top concern and more noteworthy system hash rate implies a lot harder
focus for criminals. Hashes that are memory-escalated, or utilize different intends to decrease the
benefit of particular equipment, make for systems that are simpler to topple. Consequently, it didn't
SECURITY TO DIGITAL COMMUNICATION 3
bode well to intentionally pick a wasteful hash. SHA-3 offers greater security, for less power; a
triumphant mix[9].
It is additionally vague regarding whether ASICs really add to arrange centralization. The
discussion on this point over Bitcoin died down years prior, and a few hashes utilized by different
digital forms of money have had ASICs created without a similar issue being raised; Script and
X11. The view is that the token conveyance work has more to do with that than everything else. To
address this we've actualized an extraordinary calculation for computing the reward of each square.
At last, SHA-3 seems to have the best protection from quantum figuring based assaults. This is as
yet a subject of many conflicts yet late research ought to lighten these worries. A group at the
University of Waterloo contemplated how well SHA-2 and SHA-3 had the capacity to oppose a pre-
picture assault utilizing Grover's quantum look calculation. SHA-3 did very well[2].
The SHA-3 (Keccak) plot comprises of two phases:
Advantages of SHA -3
bode well to intentionally pick a wasteful hash. SHA-3 offers greater security, for less power; a
triumphant mix[9].
It is additionally vague regarding whether ASICs really add to arrange centralization. The
discussion on this point over Bitcoin died down years prior, and a few hashes utilized by different
digital forms of money have had ASICs created without a similar issue being raised; Script and
X11. The view is that the token conveyance work has more to do with that than everything else. To
address this we've actualized an extraordinary calculation for computing the reward of each square.
At last, SHA-3 seems to have the best protection from quantum figuring based assaults. This is as
yet a subject of many conflicts yet late research ought to lighten these worries. A group at the
University of Waterloo contemplated how well SHA-2 and SHA-3 had the capacity to oppose a pre-
picture assault utilizing Grover's quantum look calculation. SHA-3 did very well[2].
The SHA-3 (Keccak) plot comprises of two phases:
Advantages of SHA -3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SECURITY TO DIGITAL COMMUNICATION 4
a) Performance
A product act correlation between the two SHA-3 finalists demonstrates that Blake is around
multiple times quicker than Keccak on a cutting edge CPU for a 512-piece hash, and just 1.26
occasions quicker for a 256-piece hash. Execution recorded in cycles per byte.
b) Security
Keccak has a round tally that is sufficiently high to give it a gigantic security edge, and the
wipe development it utilizes gives generally amazing security proofs, which have just been
demonstrated better with time[9].
Blake likewise has a high-security edge, which permitted Blake-2 to have a lower round tally and
still hold the normal security from a hash capacity of a given size. The development utilized by
Blake was likewise changed for Blake-2, so as to rearrange cushioning and memory access in
programming stages, yet additionally bolted it to byte preparing as it were. Blake and Keccak can
process bitstreams[10].
c) Bitstreams
As a feature of the institutionalization procedure, the adaptable wipe development of Keccak
brought about the SHAKE XOFs which can create self-assertive length bitstreams for different
applications. There was additionally discuss confirmed encryption dependent on the Keccak
change, Kayak is a second round CAESAR applicant dependent on the Keccak stage utilized in
SHA-3[11].
Disadvantages of SHA -3
a) Randomness validity
When needed, the yield of the capacity is put away into a document which is utilized to re-seed
the capacity, etc. Presently we can test the consistency of the yields of the capacity.
a) Performance
A product act correlation between the two SHA-3 finalists demonstrates that Blake is around
multiple times quicker than Keccak on a cutting edge CPU for a 512-piece hash, and just 1.26
occasions quicker for a 256-piece hash. Execution recorded in cycles per byte.
b) Security
Keccak has a round tally that is sufficiently high to give it a gigantic security edge, and the
wipe development it utilizes gives generally amazing security proofs, which have just been
demonstrated better with time[9].
Blake likewise has a high-security edge, which permitted Blake-2 to have a lower round tally and
still hold the normal security from a hash capacity of a given size. The development utilized by
Blake was likewise changed for Blake-2, so as to rearrange cushioning and memory access in
programming stages, yet additionally bolted it to byte preparing as it were. Blake and Keccak can
process bitstreams[10].
c) Bitstreams
As a feature of the institutionalization procedure, the adaptable wipe development of Keccak
brought about the SHAKE XOFs which can create self-assertive length bitstreams for different
applications. There was additionally discuss confirmed encryption dependent on the Keccak
change, Kayak is a second round CAESAR applicant dependent on the Keccak stage utilized in
SHA-3[11].
Disadvantages of SHA -3
a) Randomness validity
When needed, the yield of the capacity is put away into a document which is utilized to re-seed
the capacity, etc. Presently we can test the consistency of the yields of the capacity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY TO DIGITAL COMMUNICATION 3
b) Pre-image attack
Given y an overview, how might we discover ax, for example, SHA3(x) = y? The clearest
technique to do it is beast power. I produce a great deal of x and I trust that I will discover one, for
example, SHA3(x) = y. Regardless of whether the technique is very basic, we should get some
information about its possibility[12].
Question Three
Lamport’s Algorithm
Despite the fact that the potential advancement of quantum PCs compromises the security of
numerous normal types of cryptography, for example, RSA, it is trusted that Lamport marks with
huge hash capacities would, in any case, be secure in that occasion. Tragically, each Lamport key
must be utilized to sign a solitary message. Be that as it may, joined with hash trees, a solitary key
could be utilized for some, messages, making this a genuinely proficient computerized signature
conspire.
Making the key pair
To make the private key Alice utilizes the irregular number generator to deliver 256 sets of arbitrary
numbers (2×256 numbers altogether), each number being 256 bits in size, that is, an aggregate of
2×256×256 bits = 128 Kibit altogether. This is her private key and she will store it away in a safe
spot for later use.
To make the open key she hashes every one of the 512 irregular numbers in the private key, along
these lines making 512 hashes, every 256 bits in size. (Likewise 128 Kbits altogether.) These 512
numbers structure her open key, which she will impart to the world.
b) Pre-image attack
Given y an overview, how might we discover ax, for example, SHA3(x) = y? The clearest
technique to do it is beast power. I produce a great deal of x and I trust that I will discover one, for
example, SHA3(x) = y. Regardless of whether the technique is very basic, we should get some
information about its possibility[12].
Question Three
Lamport’s Algorithm
Despite the fact that the potential advancement of quantum PCs compromises the security of
numerous normal types of cryptography, for example, RSA, it is trusted that Lamport marks with
huge hash capacities would, in any case, be secure in that occasion. Tragically, each Lamport key
must be utilized to sign a solitary message. Be that as it may, joined with hash trees, a solitary key
could be utilized for some, messages, making this a genuinely proficient computerized signature
conspire.
Making the key pair
To make the private key Alice utilizes the irregular number generator to deliver 256 sets of arbitrary
numbers (2×256 numbers altogether), each number being 256 bits in size, that is, an aggregate of
2×256×256 bits = 128 Kibit altogether. This is her private key and she will store it away in a safe
spot for later use.
To make the open key she hashes every one of the 512 irregular numbers in the private key, along
these lines making 512 hashes, every 256 bits in size. (Likewise 128 Kbits altogether.) These 512
numbers structure her open key, which she will impart to the world.

SECURITY TO DIGITAL COMMUNICATION 4
Signing the message
Later Alice needs to sign a message. First, she hashes the message to a 256-piece hash whole. At
that point, for each piece in the hash, in light of the estimation of the bit, she picks one number from
the relating sets of numbers that make up her private key (i.e., if the bit is 0, the main number is
picked, and if the bit is 1, the second is picked). This delivers a succession of 256 arbitrary
numbers. As each number is itself 256 bits in length the absolute size of her mark will be 256×256
bits = 8 KiB. These irregular numbers are her mark and she distributes them alongside the message.
Note that since Alice's private key is utilized, it ought to never be utilized again. She should crush
the other 256 arbitrary numbers that she didn't use for the mark. Something else, each extra
signature reusing the private key diminishes the security level[1] against enemies that may later
make false marks from them.
Verifying the signature
At that point, Bob needs to confirm Alice's mark of the message. He likewise hashes the message to
get a 256-piece hash whole. At that point, he utilizes the bits in the work entirety to choose 256 of
the hashes in Alice's open key. He picks the hashes in a similar way that Alice picked the irregular
numbers for the mark. That is, if the principal bit of the message hash is a 0, he picks the primary
hash in the main pair, etc.
At that point, Bob hashes every one of the 256 arbitrary numbers in Alice's mark. This gives him
256 hashes. On the off chance that these 256 hashes precisely coordinate the 256 hashes he just
picked from Alice's open key then the mark is alright. In the event that not, at that point the mark
Signing the message
Later Alice needs to sign a message. First, she hashes the message to a 256-piece hash whole. At
that point, for each piece in the hash, in light of the estimation of the bit, she picks one number from
the relating sets of numbers that make up her private key (i.e., if the bit is 0, the main number is
picked, and if the bit is 1, the second is picked). This delivers a succession of 256 arbitrary
numbers. As each number is itself 256 bits in length the absolute size of her mark will be 256×256
bits = 8 KiB. These irregular numbers are her mark and she distributes them alongside the message.
Note that since Alice's private key is utilized, it ought to never be utilized again. She should crush
the other 256 arbitrary numbers that she didn't use for the mark. Something else, each extra
signature reusing the private key diminishes the security level[1] against enemies that may later
make false marks from them.
Verifying the signature
At that point, Bob needs to confirm Alice's mark of the message. He likewise hashes the message to
get a 256-piece hash whole. At that point, he utilizes the bits in the work entirety to choose 256 of
the hashes in Alice's open key. He picks the hashes in a similar way that Alice picked the irregular
numbers for the mark. That is, if the principal bit of the message hash is a 0, he picks the primary
hash in the main pair, etc.
At that point, Bob hashes every one of the 256 arbitrary numbers in Alice's mark. This gives him
256 hashes. On the off chance that these 256 hashes precisely coordinate the 256 hashes he just
picked from Alice's open key then the mark is alright. In the event that not, at that point the mark
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

