A Comprehensive Report on Mobile Device Digital Forensics
VerifiedAdded on 2020/03/28
|11
|2422
|41
Report
AI Summary
This report provides a comprehensive overview of mobile device forensics, encompassing investigative methods, the process of digital evidence handling, and the examination of evidence. It delves into the intelligence aspects of digital forensics, exploring forensic tool capabilities and their applications. The report discusses various investigative methods, including acquiring information and analyzing captured materials. It outlines the process of digital evidence, covering assessment, acquisition, examination, and reporting. The examination section details physical and logical extraction techniques, data analysis, and time frame analysis. The report further discusses the capabilities of forensic tools like Oxygen Forensic Suite and UFED Physical Analyzer, providing insights into their functionalities in recovering data from mobile devices. The conclusion emphasizes the importance of organized procedures and proper guidelines for forensic analysis, especially in managing evidence.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction.......................................................................................................................................2
2. Investigative Methods........................................................................................................................2
3. Process of digital evidence.................................................................................................................3
4. Examining the evidence.....................................................................................................................4
5. Intelligence of Digital Forensic.........................................................................................................6
6. Forensic Tool Capabilities.................................................................................................................7
7. Conclusion..........................................................................................................................................9
References..................................................................................................................................................9
1
1. Introduction.......................................................................................................................................2
2. Investigative Methods........................................................................................................................2
3. Process of digital evidence.................................................................................................................3
4. Examining the evidence.....................................................................................................................4
5. Intelligence of Digital Forensic.........................................................................................................6
6. Forensic Tool Capabilities.................................................................................................................7
7. Conclusion..........................................................................................................................................9
References..................................................................................................................................................9
1

1. Introduction
This study offers the information about forensics tools of mobile device. The procurement,
the examination, the preservation and the reporting, and examination of cellular device digital
evidence. This data is related to enforcement of law and other kind of prosecution. This case
study mainly concentrates on the features of mobile devices which includes smartphones, mobile
phones and tablet etc. This study focus to address the common field which is investigated by
security employee of organization and law prosecution investigators including electronic digital
information residing on cellular phone and connected electronic media. This will engaged to
accomplish available instruction and inquire intensely to problem relevant to cellular phones
with respected analysis and examination. Techniques and process exist in this study are the
combination of best system along with the discipline where reference got from available forensic
rule. Its main function is to advise editor of the different knowledge associated with possible
ways to access it from aspects of forensic.
2. Investigative Methods
Investigation style are practice the examination group can employ, which need no forensic
tools of hardware and software. The common predominant practice are as follows:
Get information from the owner
Assure with mobile admin if a mobile is secured with authentication mechanism such as
PIN, password, or other authentication techniques including authentication of information, the
admin may be inquire about this data during an investigation process.
Analysis captured material
Password may be revealed by written in a slip and put near the mobile, at a desktop
system need to synchronize wit cellular device or with the admin and it will found via visual
examination (Hoog, 2011). Enclosed with substance of UICC and a cellular device is attached as
PUK (PIN unlocking Key) which helps to reset PIN. The vulnerabilities exist in device may
exploited like smudge attacks. This type of attacks includes very careful research of the external
phase on touch screen phones to identify the usage of current gesture lock.
2
This study offers the information about forensics tools of mobile device. The procurement,
the examination, the preservation and the reporting, and examination of cellular device digital
evidence. This data is related to enforcement of law and other kind of prosecution. This case
study mainly concentrates on the features of mobile devices which includes smartphones, mobile
phones and tablet etc. This study focus to address the common field which is investigated by
security employee of organization and law prosecution investigators including electronic digital
information residing on cellular phone and connected electronic media. This will engaged to
accomplish available instruction and inquire intensely to problem relevant to cellular phones
with respected analysis and examination. Techniques and process exist in this study are the
combination of best system along with the discipline where reference got from available forensic
rule. Its main function is to advise editor of the different knowledge associated with possible
ways to access it from aspects of forensic.
2. Investigative Methods
Investigation style are practice the examination group can employ, which need no forensic
tools of hardware and software. The common predominant practice are as follows:
Get information from the owner
Assure with mobile admin if a mobile is secured with authentication mechanism such as
PIN, password, or other authentication techniques including authentication of information, the
admin may be inquire about this data during an investigation process.
Analysis captured material
Password may be revealed by written in a slip and put near the mobile, at a desktop
system need to synchronize wit cellular device or with the admin and it will found via visual
examination (Hoog, 2011). Enclosed with substance of UICC and a cellular device is attached as
PUK (PIN unlocking Key) which helps to reset PIN. The vulnerabilities exist in device may
exploited like smudge attacks. This type of attacks includes very careful research of the external
phase on touch screen phones to identify the usage of current gesture lock.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ask the service provider
If a GSM cellular phones is secured with UICC PIN, analyzer therefore the ICCID will
acquire from it and need to inquire the PUK from the service launcher and reset the password.
Some of the service provider promotes capability to extract the PUK by accessing the amount of
cellular phones where the particular subscriber data to universal web sites build for this type of
principle. In future, the data acquired by approaching device manufacturer. Cellular phone users
do prefer poor pin to protect their device in the form of 1-1-1-1, 0-0- 0-0 or 1-2-3-4. This format
is not fully prescribed try to unlock a device applying those compounds for various threat
determinant. This might leads to constant loss of mobile memory, permit advanced security
techniques for example PUK or PIN and initiating destructive operation. Before applying the
attempts to unlocking a cellular phones, it is suggested to consider the time of attempts left over.
Instance has to be considered where an analyzer may prefer to take this risk. This is the only
solution for information extraction.
3. Process of digital evidence
These all are the techniques used to processed the digital evidence, they are
Assessment
Examiners in computer forensic must determine digital evidence entirely with
consideration to the capacity of case to evaluate the sequence of action to be consider
(Gladyshev & Rogers, 2012).
Acquisition
In nature, Digital evidence is very delicate and it may be changed, broken, or destroyed
by incorrect management or analysis. Examination is best management of an imitation of the
original evidence. The original evidence must be seized by a way which secure and preserves the
evidence integrity.
3
If a GSM cellular phones is secured with UICC PIN, analyzer therefore the ICCID will
acquire from it and need to inquire the PUK from the service launcher and reset the password.
Some of the service provider promotes capability to extract the PUK by accessing the amount of
cellular phones where the particular subscriber data to universal web sites build for this type of
principle. In future, the data acquired by approaching device manufacturer. Cellular phone users
do prefer poor pin to protect their device in the form of 1-1-1-1, 0-0- 0-0 or 1-2-3-4. This format
is not fully prescribed try to unlock a device applying those compounds for various threat
determinant. This might leads to constant loss of mobile memory, permit advanced security
techniques for example PUK or PIN and initiating destructive operation. Before applying the
attempts to unlocking a cellular phones, it is suggested to consider the time of attempts left over.
Instance has to be considered where an analyzer may prefer to take this risk. This is the only
solution for information extraction.
3. Process of digital evidence
These all are the techniques used to processed the digital evidence, they are
Assessment
Examiners in computer forensic must determine digital evidence entirely with
consideration to the capacity of case to evaluate the sequence of action to be consider
(Gladyshev & Rogers, 2012).
Acquisition
In nature, Digital evidence is very delicate and it may be changed, broken, or destroyed
by incorrect management or analysis. Examination is best management of an imitation of the
original evidence. The original evidence must be seized by a way which secure and preserves the
evidence integrity.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Examination
The main aim of the examination or analysis process is to refine and examine digital
evidence. The extraction defines to the rehabilitation of information from its media. Analysis
defines to the perception of collected data and storing it into a logical and needful plan.
Documenting and reporting
Deal and examination must be documented throughout the process of forensic evidence. This
will terminate with the development of a written statement of the recommendation.
4. Examining the evidence
The key principle of mobile forensic apply when determining digital evidence. Various kind of
media need various examination model. Individual processing an analysis of digital evidence
must be practiced for this scope (Peterson & Shenoi, 2012).
When executing evidence analysis, consider the following stage:
Stage 1. Preparation
Develop active directories on independent media to which evidence document and
information can be found and refined.
Step 2. Extraction
There is a two-various kind of extraction such as physical extraction and logical
extraction. The physical extraction level discovers and restore the information over the physical
drive without concern of file system. The logical extraction level discovers and restores
resources and information which is depend on the installed OS (operating system), applications
and file system.
Physical extraction
During the level of physical extraction, the resource from the drive appears at the physical
stage unconcerned of file system exist on the drive. This may consider following techniques:
searching keyword, document carving and refinement of the partition table and new space on
physical drive.
Keyword search performance in the physical drive is needful to permit the examiner to
refine the information which does not assumed for by the file system or OS.
4
The main aim of the examination or analysis process is to refine and examine digital
evidence. The extraction defines to the rehabilitation of information from its media. Analysis
defines to the perception of collected data and storing it into a logical and needful plan.
Documenting and reporting
Deal and examination must be documented throughout the process of forensic evidence. This
will terminate with the development of a written statement of the recommendation.
4. Examining the evidence
The key principle of mobile forensic apply when determining digital evidence. Various kind of
media need various examination model. Individual processing an analysis of digital evidence
must be practiced for this scope (Peterson & Shenoi, 2012).
When executing evidence analysis, consider the following stage:
Stage 1. Preparation
Develop active directories on independent media to which evidence document and
information can be found and refined.
Step 2. Extraction
There is a two-various kind of extraction such as physical extraction and logical
extraction. The physical extraction level discovers and restore the information over the physical
drive without concern of file system. The logical extraction level discovers and restores
resources and information which is depend on the installed OS (operating system), applications
and file system.
Physical extraction
During the level of physical extraction, the resource from the drive appears at the physical
stage unconcerned of file system exist on the drive. This may consider following techniques:
searching keyword, document carving and refinement of the partition table and new space on
physical drive.
Keyword search performance in the physical drive is needful to permit the examiner to
refine the information which does not assumed for by the file system or OS.
4

File carving functionality of physical drive may help to recover and extracting needful
file and resource which does not assumed for by the file system or OS.
Analyzing the structure of partition can discover the file system exist and examine if the
whole physical size of hard disk is considered for.
Logical extraction
During the level of logical extraction from drive is depends on the file system exist on the
drive and it invokes resources from such fields as operating file, deleted data, slack file and
unallocated memory files. Stage may include the followings.
File system data extraction is to disclose the feature such as structure of directory,
resource attributes, name of the file, date and time of the file, location and size of the file.
Data elimination is the process of discovering and neglecting file through the correlation
of estimated hash values to authenticated values.
Restoration of deleted files
Separation of encrypted, password secured and compressed resource file.
Separation of file slack
Separation of unallocated memory.
Step 3. Analysis of extracted data
Analysis is the sequence of read the refined information to examine the importance for the
case. The example analysis is performed by timeframe, application and file, data hiding and
ownership possession. Analysis may need an inspection of the device request, searching and
finding legal authority for digital evidence, investigate analytical leads.
I. Timeframe analysis
Timeframe analysis is very needful for examining the events placed on a system. Two kind if
methods can be utilized are
Checking the data and time stamps exist in the metadata of file system for example last
modified, current accessed or created to connect the file of interest for the timeframes
related to the inspection.
Checking the exist computer system and application logs. These consist with failure logs,
installation logs, security logs, connection logs, etc.
5
file and resource which does not assumed for by the file system or OS.
Analyzing the structure of partition can discover the file system exist and examine if the
whole physical size of hard disk is considered for.
Logical extraction
During the level of logical extraction from drive is depends on the file system exist on the
drive and it invokes resources from such fields as operating file, deleted data, slack file and
unallocated memory files. Stage may include the followings.
File system data extraction is to disclose the feature such as structure of directory,
resource attributes, name of the file, date and time of the file, location and size of the file.
Data elimination is the process of discovering and neglecting file through the correlation
of estimated hash values to authenticated values.
Restoration of deleted files
Separation of encrypted, password secured and compressed resource file.
Separation of file slack
Separation of unallocated memory.
Step 3. Analysis of extracted data
Analysis is the sequence of read the refined information to examine the importance for the
case. The example analysis is performed by timeframe, application and file, data hiding and
ownership possession. Analysis may need an inspection of the device request, searching and
finding legal authority for digital evidence, investigate analytical leads.
I. Timeframe analysis
Timeframe analysis is very needful for examining the events placed on a system. Two kind if
methods can be utilized are
Checking the data and time stamps exist in the metadata of file system for example last
modified, current accessed or created to connect the file of interest for the timeframes
related to the inspection.
Checking the exist computer system and application logs. These consist with failure logs,
installation logs, security logs, connection logs, etc.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

II. Data hiding analysis
Data will be covered with a system. The examination of data hiding is needful in discovering and
recovering data and indicate information, intent. Techniques involved:
Combining the resource headers to the respective extension of the file to discover
mismatches
Achieving the connection to all password secured, encrypted file and compressed zip file
to indicate the attempt to cover the resource form unauthorized users.
Steganography
Achieving access to HPA (host-protected area). The existence of user-discovered
information with HPA may reveal try to cover data.
III. Application and file analysis
Enormous file and programs discovered which consist data related to the examination and offer
awareness about the system ability and the user information (Tahiri, 2016). Outcome of the
analysis reveal advance steps that require to be considered in the separation and examination
processes. Some example is considered:
Checking the name of the file for patterns and applicability.
Analyzing the content of the file
Discovering the number and kind of OS
Relating the resources to the already installed application.
Study relationship between the resources or files for example comparing history in the
internet to cache file and mail file for email attachments.
Discovering unknown resources types to evaluate their profit to the examination.
Analyzing the default storage location of the users’ for application and structure of the
file drive to analyses if the resource has been collected in their alternative or default
location.
Analyzing user-configuration settings of application.
5. Intelligence of Digital Forensic
6
Data will be covered with a system. The examination of data hiding is needful in discovering and
recovering data and indicate information, intent. Techniques involved:
Combining the resource headers to the respective extension of the file to discover
mismatches
Achieving the connection to all password secured, encrypted file and compressed zip file
to indicate the attempt to cover the resource form unauthorized users.
Steganography
Achieving access to HPA (host-protected area). The existence of user-discovered
information with HPA may reveal try to cover data.
III. Application and file analysis
Enormous file and programs discovered which consist data related to the examination and offer
awareness about the system ability and the user information (Tahiri, 2016). Outcome of the
analysis reveal advance steps that require to be considered in the separation and examination
processes. Some example is considered:
Checking the name of the file for patterns and applicability.
Analyzing the content of the file
Discovering the number and kind of OS
Relating the resources to the already installed application.
Study relationship between the resources or files for example comparing history in the
internet to cache file and mail file for email attachments.
Discovering unknown resources types to evaluate their profit to the examination.
Analyzing the default storage location of the users’ for application and structure of the
file drive to analyses if the resource has been collected in their alternative or default
location.
Analyzing user-configuration settings of application.
5. Intelligence of Digital Forensic
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

There is some kind of terminology integrated to posit an explanation of digital intelligence which
includes knowledge having the law prosecution and other departments of investigation and this will
combine via forensic examination and operation of digital storage. Intelligence of Digital forensic will
worn from the activities of intelligence and through the regular inspection where the intelligence
restore in databases.
However, more number of examples associated with intelligence database along with this kind of
forensic domain for the object of UK NDNAD (National DNA Database), IDENT1 which is known as
National Fingerprint database of UK and the IAFIS called as USA Integrated Automated Fingerprint
Identification system. The following databases are represents the comparison between evidence and
intelligence. It does not having evidence but it will share effective solution for digital crimes that has not
reveal at the certain period that similar access were combine with the database.
6. Forensic Tool Capabilities
Forensic tools are used to manage the conventional investigation of cases requires by
dispatch a vast number of applicable devices (Peterson & Shenoi, 2014). Complex situation such
as recovery of erased information from the memory of a device will need more advanced tools
and knowledge for the devices. The support extent is offered including cellular devices cables
and driver, pc readers, documentation of the products may differs considerably among goods.
The features provided such as bookmarking, searching and reporting ability may alter
significantly. Tools must be validated to make sure with acceptability and re-practice when
updates or new version of the tool is exist. Validating a tool require discovering a data set where
the following procedures of acquisition to recollect the test data as well as assessing the
outcomes. The significant features of forensic tools having the capability to control the integrity
of original data being accessed and extracted data. Here some of the mobile device tools used for
digital investigation.
I. Oxygen Forensic Suite
Oxygen Forensic Suite discovering the inspection with Oxygen forensic suit discover the
main expensive data such as IMSI, ICCID, IMEI in such cellular device that has been used in
crime scenario. Figure. 1 represents the data that will assist the examiner to discover the primary
7
includes knowledge having the law prosecution and other departments of investigation and this will
combine via forensic examination and operation of digital storage. Intelligence of Digital forensic will
worn from the activities of intelligence and through the regular inspection where the intelligence
restore in databases.
However, more number of examples associated with intelligence database along with this kind of
forensic domain for the object of UK NDNAD (National DNA Database), IDENT1 which is known as
National Fingerprint database of UK and the IAFIS called as USA Integrated Automated Fingerprint
Identification system. The following databases are represents the comparison between evidence and
intelligence. It does not having evidence but it will share effective solution for digital crimes that has not
reveal at the certain period that similar access were combine with the database.
6. Forensic Tool Capabilities
Forensic tools are used to manage the conventional investigation of cases requires by
dispatch a vast number of applicable devices (Peterson & Shenoi, 2014). Complex situation such
as recovery of erased information from the memory of a device will need more advanced tools
and knowledge for the devices. The support extent is offered including cellular devices cables
and driver, pc readers, documentation of the products may differs considerably among goods.
The features provided such as bookmarking, searching and reporting ability may alter
significantly. Tools must be validated to make sure with acceptability and re-practice when
updates or new version of the tool is exist. Validating a tool require discovering a data set where
the following procedures of acquisition to recollect the test data as well as assessing the
outcomes. The significant features of forensic tools having the capability to control the integrity
of original data being accessed and extracted data. Here some of the mobile device tools used for
digital investigation.
I. Oxygen Forensic Suite
Oxygen Forensic Suite discovering the inspection with Oxygen forensic suit discover the
main expensive data such as IMSI, ICCID, IMEI in such cellular device that has been used in
crime scenario. Figure. 1 represents the data that will assist the examiner to discover the primary
7
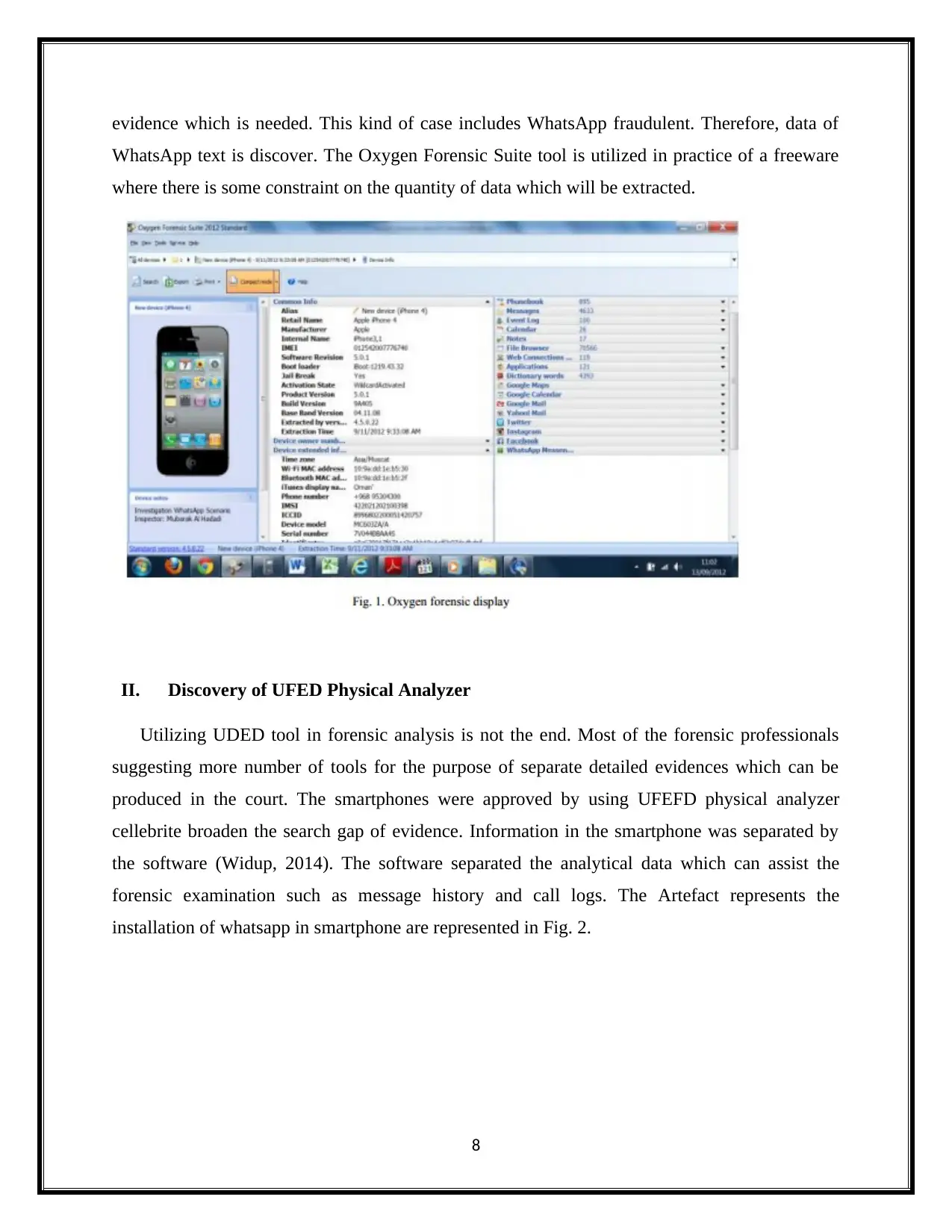
evidence which is needed. This kind of case includes WhatsApp fraudulent. Therefore, data of
WhatsApp text is discover. The Oxygen Forensic Suite tool is utilized in practice of a freeware
where there is some constraint on the quantity of data which will be extracted.
II. Discovery of UFED Physical Analyzer
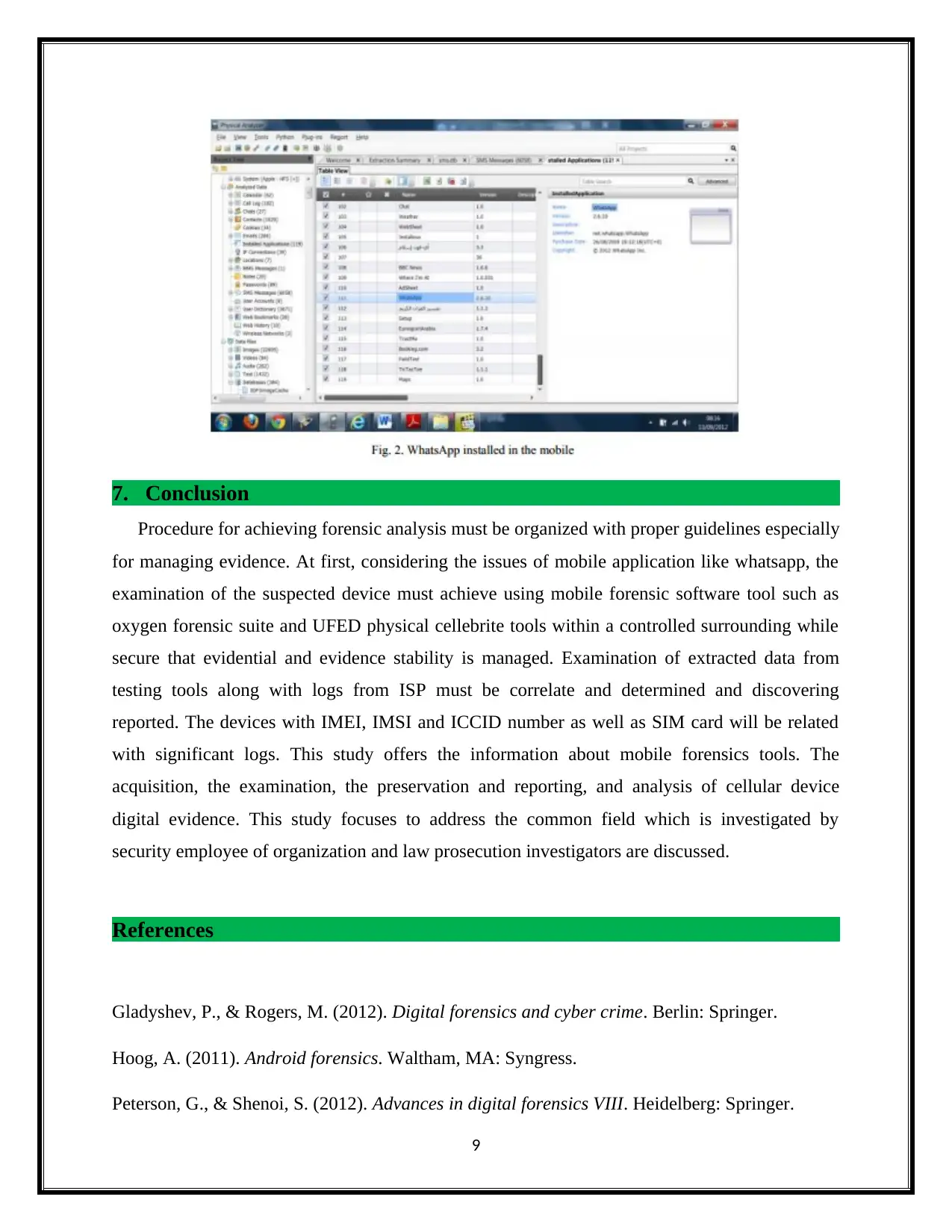
Utilizing UDED tool in forensic analysis is not the end. Most of the forensic professionals
suggesting more number of tools for the purpose of separate detailed evidences which can be
produced in the court. The smartphones were approved by using UFEFD physical analyzer
cellebrite broaden the search gap of evidence. Information in the smartphone was separated by
the software (Widup, 2014). The software separated the analytical data which can assist the
forensic examination such as message history and call logs. The Artefact represents the
installation of whatsapp in smartphone are represented in Fig. 2.
8
WhatsApp text is discover. The Oxygen Forensic Suite tool is utilized in practice of a freeware
where there is some constraint on the quantity of data which will be extracted.
II. Discovery of UFED Physical Analyzer
Utilizing UDED tool in forensic analysis is not the end. Most of the forensic professionals
suggesting more number of tools for the purpose of separate detailed evidences which can be
produced in the court. The smartphones were approved by using UFEFD physical analyzer
cellebrite broaden the search gap of evidence. Information in the smartphone was separated by
the software (Widup, 2014). The software separated the analytical data which can assist the
forensic examination such as message history and call logs. The Artefact represents the
installation of whatsapp in smartphone are represented in Fig. 2.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7. Conclusion
Procedure for achieving forensic analysis must be organized with proper guidelines especially
for managing evidence. At first, considering the issues of mobile application like whatsapp, the
examination of the suspected device must achieve using mobile forensic software tool such as
oxygen forensic suite and UFED physical cellebrite tools within a controlled surrounding while
secure that evidential and evidence stability is managed. Examination of extracted data from
testing tools along with logs from ISP must be correlate and determined and discovering
reported. The devices with IMEI, IMSI and ICCID number as well as SIM card will be related
with significant logs. This study offers the information about mobile forensics tools. The
acquisition, the examination, the preservation and reporting, and analysis of cellular device
digital evidence. This study focuses to address the common field which is investigated by
security employee of organization and law prosecution investigators are discussed.
References
Gladyshev, P., & Rogers, M. (2012). Digital forensics and cyber crime. Berlin: Springer.
Hoog, A. (2011). Android forensics. Waltham, MA: Syngress.
Peterson, G., & Shenoi, S. (2012). Advances in digital forensics VIII. Heidelberg: Springer.
9
Procedure for achieving forensic analysis must be organized with proper guidelines especially
for managing evidence. At first, considering the issues of mobile application like whatsapp, the
examination of the suspected device must achieve using mobile forensic software tool such as
oxygen forensic suite and UFED physical cellebrite tools within a controlled surrounding while
secure that evidential and evidence stability is managed. Examination of extracted data from
testing tools along with logs from ISP must be correlate and determined and discovering
reported. The devices with IMEI, IMSI and ICCID number as well as SIM card will be related
with significant logs. This study offers the information about mobile forensics tools. The
acquisition, the examination, the preservation and reporting, and analysis of cellular device
digital evidence. This study focuses to address the common field which is investigated by
security employee of organization and law prosecution investigators are discussed.
References
Gladyshev, P., & Rogers, M. (2012). Digital forensics and cyber crime. Berlin: Springer.
Hoog, A. (2011). Android forensics. Waltham, MA: Syngress.
Peterson, G., & Shenoi, S. (2012). Advances in digital forensics VIII. Heidelberg: Springer.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Peterson, G., & Shenoi, S. (2014). Advances in Digital Forensics X. Berlin, Heidelberg: Springer
Berlin Heidelberg.
Tahiri, S. (2016). Mastering Mobile Forensics. Packt Publishing.
Widup, S. (2014). Computer forensics and digital investigation with EnCase Forensic v7. New
York: McGraw-Hill Education.
10
Berlin Heidelberg.
Tahiri, S. (2016). Mastering Mobile Forensics. Packt Publishing.
Widup, S. (2014). Computer forensics and digital investigation with EnCase Forensic v7. New
York: McGraw-Hill Education.
10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





