Digital Forensic Investigation: Analyzing Clown-Related Content Case
VerifiedAdded on 2023/06/03
|29
|4729
|316
Case Study
AI Summary
This case study involves a digital forensic investigation into allegations of accessing illegal clown-related content. The investigation uses the Autopsy forensic tool to analyze a forensic image obtained from a computer seized with a warrant. The initial investigation was complicated by a junior investigator's actions, including performing a logical acquisition and wiping the original hard drive. The suspect denies accessing the content, claiming potential malware infection. The report details the process of extracting and analyzing the forensic image files, identifying deleted files, and conducting keyword searches to uncover relevant evidence. The analysis covers multiple data files (182.7z.002 to 182.7z.014), highlighting the presence of deleted files and results from keyword searches, including single regular expressions, literal keyword searches, and email addresses. This investigation aims to determine the extent of the suspect's involvement with the alleged illegal content.
Forensic Research
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Project Description...........................................................................................................2
2 Presentation of content relating to offence.....................................................................2
3 Identification of the Case file...........................................................................................5
4 Intent of the case file.......................................................................................................15
5 Quantity of Files..............................................................................................................21
6 Installed Software...........................................................................................................26
References...............................................................................................................................27
1
1 Project Description...........................................................................................................2
2 Presentation of content relating to offence.....................................................................2
3 Identification of the Case file...........................................................................................5
4 Intent of the case file.......................................................................................................15
5 Quantity of Files..............................................................................................................21
6 Installed Software...........................................................................................................26
References...............................................................................................................................27
1

1 Project Description
This a project which ensures the investigation of the digital forensics images, with the
help of an effective tool. The states present in Western Australia are not allowed to provide
access for the digital content with respect to the clowns. The reason behind this is that it is an
illegal access, which owns and distributes the digital content to the clowns. Malware are used
for accessing the digital content of the clown. Thus, the following investigation is carried on
the digital content related to the clowns. Mostly, the allegation were to construct the law
enforcement where the witness would claim accessing the clown related data inside the
workplace. However, it is possible to access certain content of the clown, without being in the
workplace. Sadly, the junior digital investigator got the forensics image from the computer
which is the content of the clown which performed the logical acquisition. Thus, this specific
circumstance let the junior digital forensics investigator to wipe out the original hard drive
from the computer, as forensically sound logical acquisitions were carried out here. Hence,
with ease the junior investigator was capable of determining the forensic image. The suspect,
Clark demies accessing the clown content, moreover there is no confirmation from Clark that
the computer belongs to him. Clark says, he does not always take the computer home or lock
it. So, senior investigator needs to examine the forensic image of the lap which was seized
with correct warrants. On the other hand, Clark has given a statement that, “The computer
was infected with malware and this led various potential content to appear on the computer.”
It is an investigation carried out with the help of autopsy forensic tool, and this report will
briefly discuss about this investigation.
2 Presentation of content relating to offence
Here, the presentation is required to be on the offence. The given case study states that,
the allegation were to produce law enforcement, where the witness claims accessing the
clown related data inside the workplace. However, it is possible to access certain content of
the clown, without being in the workplace. Unluckily, from the computer the junior digital
investigator got the forensics image, which is clown’s content that performed the logical
acquisition. Hence, from the computer, the original hard drive was wiped by the junior digital
forensics investigator, as the accurate logical acquisition were carried out. The forensic image
was determined easily by the junior investigator and this the reason that the senior
investigator should examine the forensic image that was seized with appropriate warrants.
The autopsy forensics tool is used for the investigation ("Basics of Computer Forensics",
2016).
2
This a project which ensures the investigation of the digital forensics images, with the
help of an effective tool. The states present in Western Australia are not allowed to provide
access for the digital content with respect to the clowns. The reason behind this is that it is an
illegal access, which owns and distributes the digital content to the clowns. Malware are used
for accessing the digital content of the clown. Thus, the following investigation is carried on
the digital content related to the clowns. Mostly, the allegation were to construct the law
enforcement where the witness would claim accessing the clown related data inside the
workplace. However, it is possible to access certain content of the clown, without being in the
workplace. Sadly, the junior digital investigator got the forensics image from the computer
which is the content of the clown which performed the logical acquisition. Thus, this specific
circumstance let the junior digital forensics investigator to wipe out the original hard drive
from the computer, as forensically sound logical acquisitions were carried out here. Hence,
with ease the junior investigator was capable of determining the forensic image. The suspect,
Clark demies accessing the clown content, moreover there is no confirmation from Clark that
the computer belongs to him. Clark says, he does not always take the computer home or lock
it. So, senior investigator needs to examine the forensic image of the lap which was seized
with correct warrants. On the other hand, Clark has given a statement that, “The computer
was infected with malware and this led various potential content to appear on the computer.”
It is an investigation carried out with the help of autopsy forensic tool, and this report will
briefly discuss about this investigation.
2 Presentation of content relating to offence
Here, the presentation is required to be on the offence. The given case study states that,
the allegation were to produce law enforcement, where the witness claims accessing the
clown related data inside the workplace. However, it is possible to access certain content of
the clown, without being in the workplace. Unluckily, from the computer the junior digital
investigator got the forensics image, which is clown’s content that performed the logical
acquisition. Hence, from the computer, the original hard drive was wiped by the junior digital
forensics investigator, as the accurate logical acquisition were carried out. The forensic image
was determined easily by the junior investigator and this the reason that the senior
investigator should examine the forensic image that was seized with appropriate warrants.
The autopsy forensics tool is used for the investigation ("Basics of Computer Forensics",
2016).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
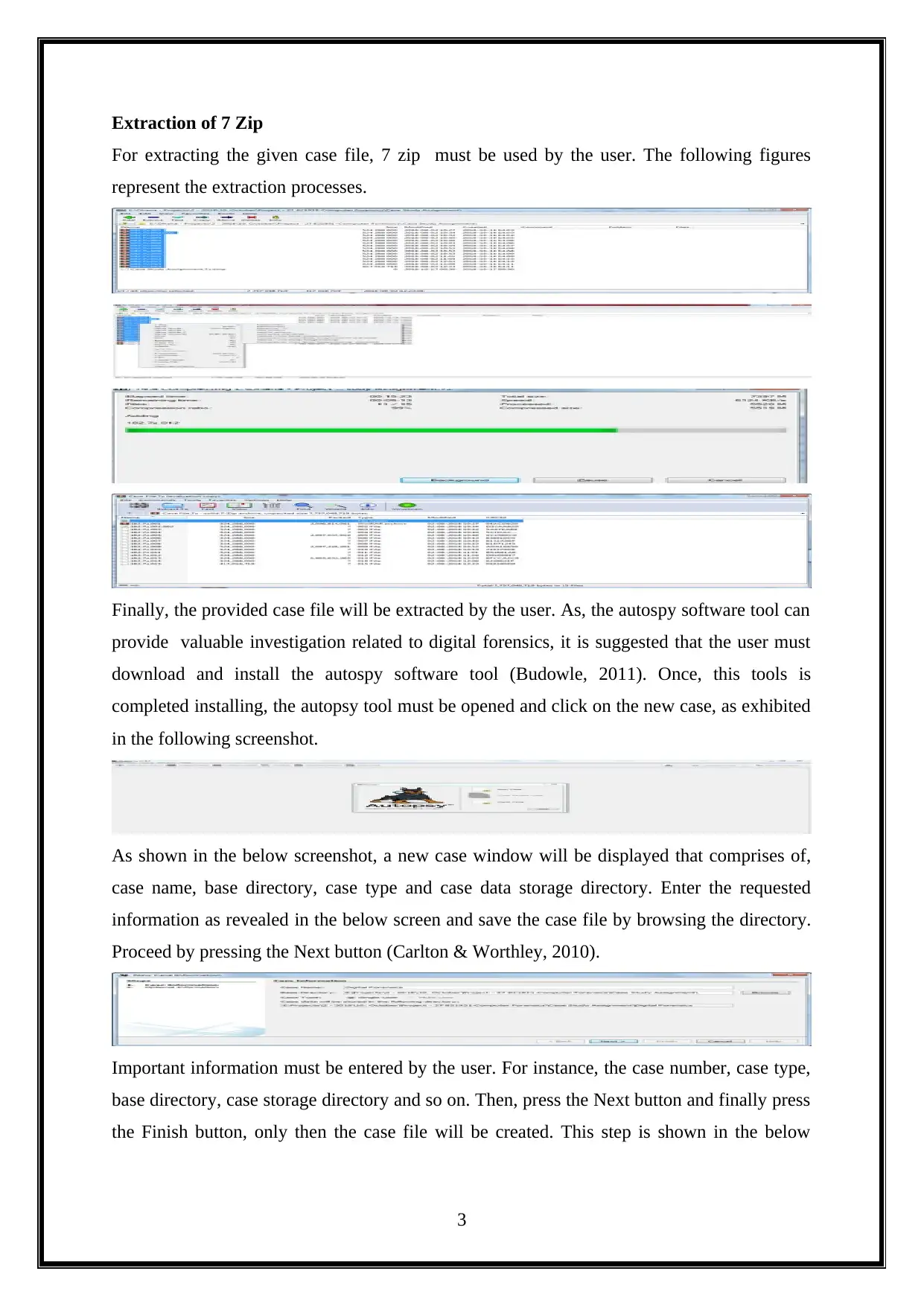
Extraction of 7 Zip
For extracting the given case file, 7 zip must be used by the user. The following figures
represent the extraction processes.
Finally, the provided case file will be extracted by the user. As, the autospy software tool can
provide valuable investigation related to digital forensics, it is suggested that the user must
download and install the autospy software tool (Budowle, 2011). Once, this tools is
completed installing, the autopsy tool must be opened and click on the new case, as exhibited
in the following screenshot.
As shown in the below screenshot, a new case window will be displayed that comprises of,
case name, base directory, case type and case data storage directory. Enter the requested
information as revealed in the below screen and save the case file by browsing the directory.
Proceed by pressing the Next button (Carlton & Worthley, 2010).
Important information must be entered by the user. For instance, the case number, case type,
base directory, case storage directory and so on. Then, press the Next button and finally press
the Finish button, only then the case file will be created. This step is shown in the below
3
For extracting the given case file, 7 zip must be used by the user. The following figures
represent the extraction processes.
Finally, the provided case file will be extracted by the user. As, the autospy software tool can
provide valuable investigation related to digital forensics, it is suggested that the user must
download and install the autospy software tool (Budowle, 2011). Once, this tools is
completed installing, the autopsy tool must be opened and click on the new case, as exhibited
in the following screenshot.
As shown in the below screenshot, a new case window will be displayed that comprises of,
case name, base directory, case type and case data storage directory. Enter the requested
information as revealed in the below screen and save the case file by browsing the directory.
Proceed by pressing the Next button (Carlton & Worthley, 2010).
Important information must be entered by the user. For instance, the case number, case type,
base directory, case storage directory and so on. Then, press the Next button and finally press
the Finish button, only then the case file will be created. This step is shown in the below
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
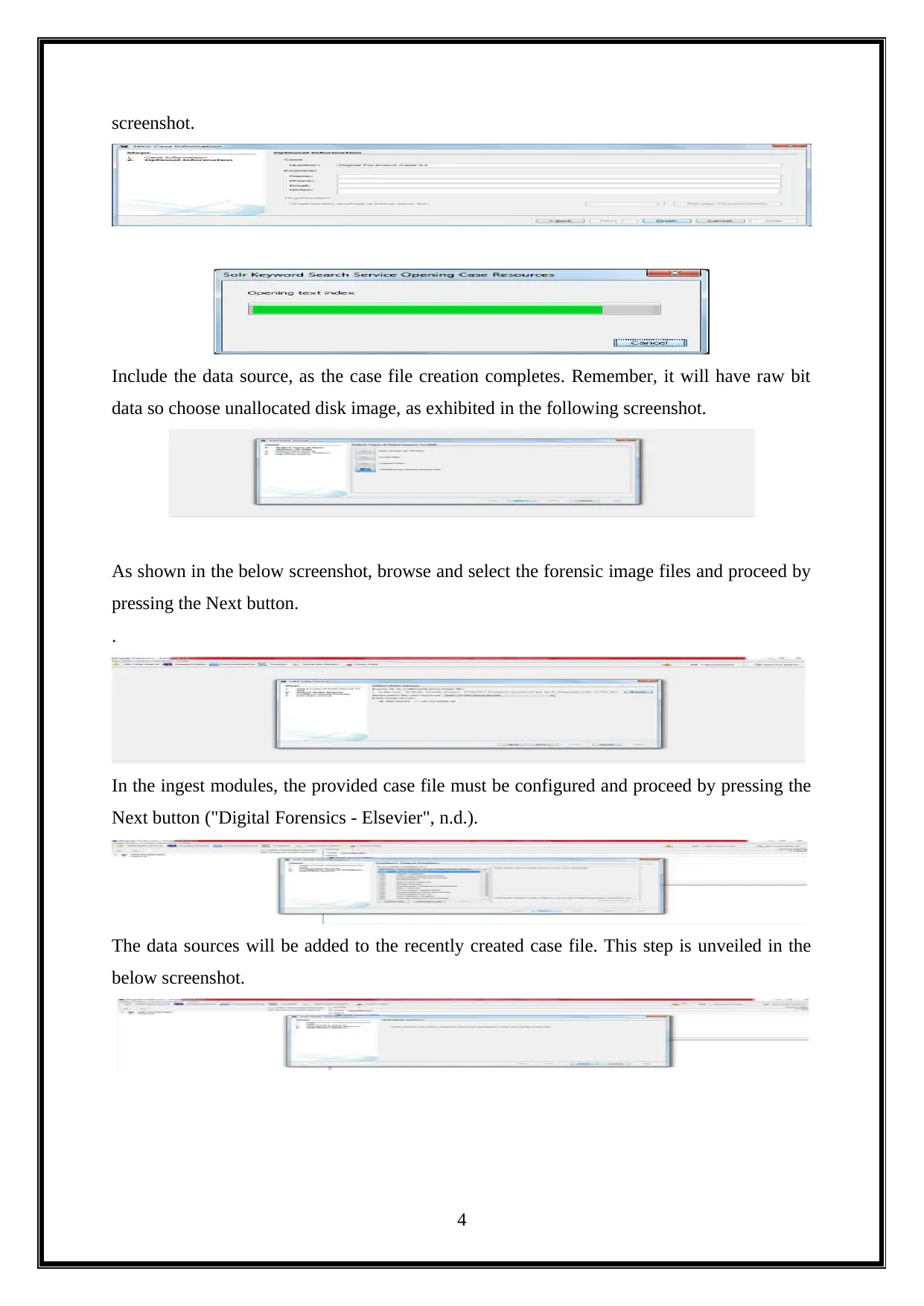
screenshot.
Include the data source, as the case file creation completes. Remember, it will have raw bit
data so choose unallocated disk image, as exhibited in the following screenshot.
As shown in the below screenshot, browse and select the forensic image files and proceed by
pressing the Next button.
.
In the ingest modules, the provided case file must be configured and proceed by pressing the
Next button ("Digital Forensics - Elsevier", n.d.).
The data sources will be added to the recently created case file. This step is unveiled in the
below screenshot.
4
Include the data source, as the case file creation completes. Remember, it will have raw bit
data so choose unallocated disk image, as exhibited in the following screenshot.
As shown in the below screenshot, browse and select the forensic image files and proceed by
pressing the Next button.
.
In the ingest modules, the provided case file must be configured and proceed by pressing the
Next button ("Digital Forensics - Elsevier", n.d.).
The data sources will be added to the recently created case file. This step is unveiled in the
below screenshot.
4
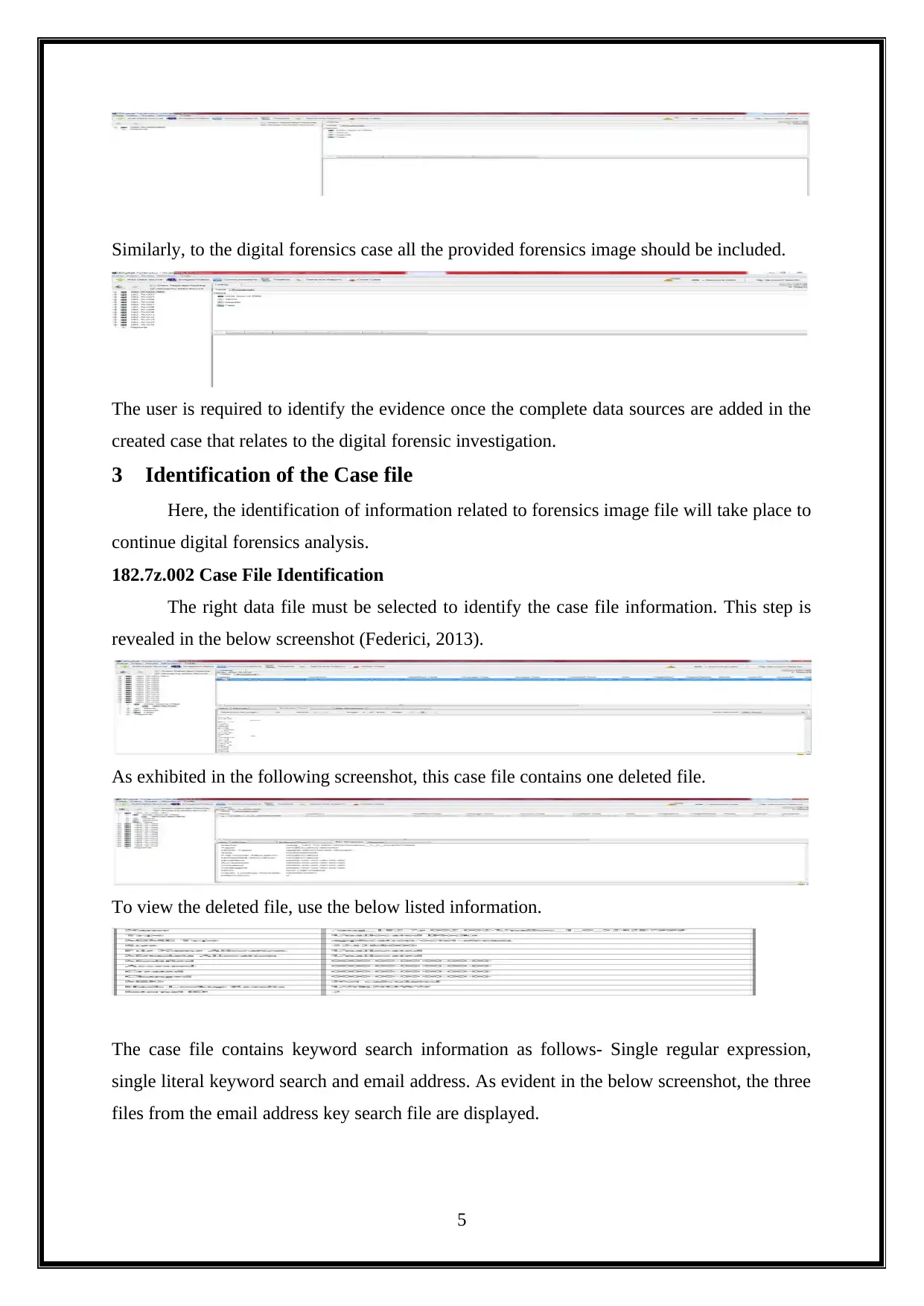
Similarly, to the digital forensics case all the provided forensics image should be included.
The user is required to identify the evidence once the complete data sources are added in the
created case that relates to the digital forensic investigation.
3 Identification of the Case file
Here, the identification of information related to forensics image file will take place to
continue digital forensics analysis.
182.7z.002 Case File Identification
The right data file must be selected to identify the case file information. This step is
revealed in the below screenshot (Federici, 2013).
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted file, use the below listed information.
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed.
5
The user is required to identify the evidence once the complete data sources are added in the
created case that relates to the digital forensic investigation.
3 Identification of the Case file
Here, the identification of information related to forensics image file will take place to
continue digital forensics analysis.
182.7z.002 Case File Identification
The right data file must be selected to identify the case file information. This step is
revealed in the below screenshot (Federici, 2013).
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted file, use the below listed information.
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

To view the results of the case file, use the below listed information.
182.7z.003 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot ("Forensic Examination of Digital Evidence: A Guide for Law ...",
n.d.).
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information (Hannay, 2011).
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed.
To view the results of the case file, use the below listed information (HU, LIU & HE, 2010).
6
182.7z.003 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot ("Forensic Examination of Digital Evidence: A Guide for Law ...",
n.d.).
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information (Hannay, 2011).
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed.
To view the results of the case file, use the below listed information (HU, LIU & HE, 2010).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

182.7z.004 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As shown in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information.
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed (Kearns, 2010).
7
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As shown in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information.
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed (Kearns, 2010).
7

To view the results of the case file, use the below listed information.
182.7z.005 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file (Kessler,
2012).
To view the deleted files, use the below listed information.
To view the results of the case file, use the below listed information.
182.7z.006 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
8
182.7z.005 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file (Kessler,
2012).
To view the deleted files, use the below listed information.
To view the results of the case file, use the below listed information.
182.7z.006 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
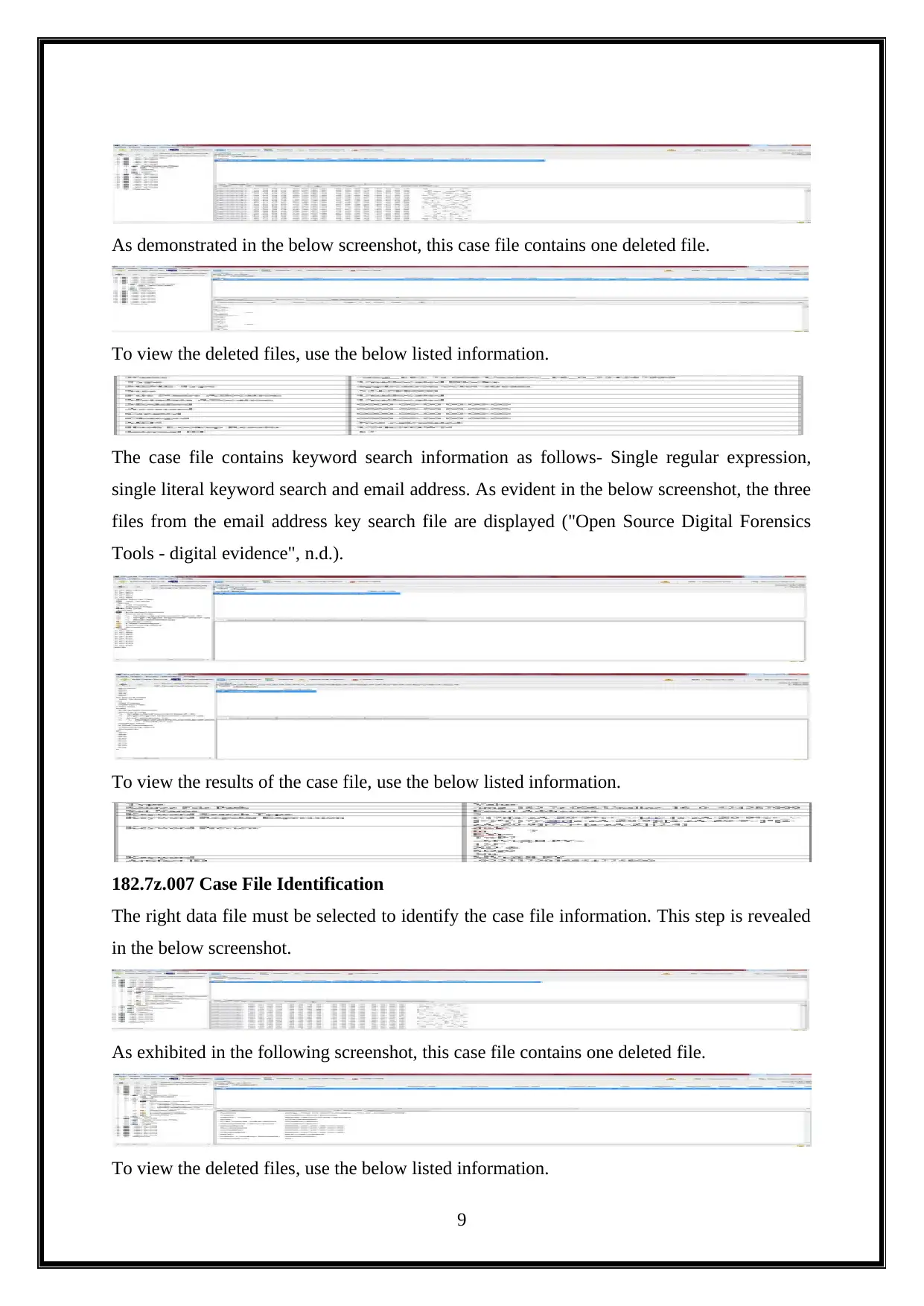
As demonstrated in the below screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information.
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed ("Open Source Digital Forensics
Tools - digital evidence", n.d.).
To view the results of the case file, use the below listed information.
182.7z.007 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information.
9
To view the deleted files, use the below listed information.
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed ("Open Source Digital Forensics
Tools - digital evidence", n.d.).
To view the results of the case file, use the below listed information.
182.7z.007 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed (Science needs for microbial
forensics, n.d.).
To view the results of the case file, use the below listed information.
182.7z.008 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file (Wright,
2012).
To view the deleted files, use the below listed information.
10
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed (Science needs for microbial
forensics, n.d.).
To view the results of the case file, use the below listed information.
182.7z.008 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file (Wright,
2012).
To view the deleted files, use the below listed information.
10
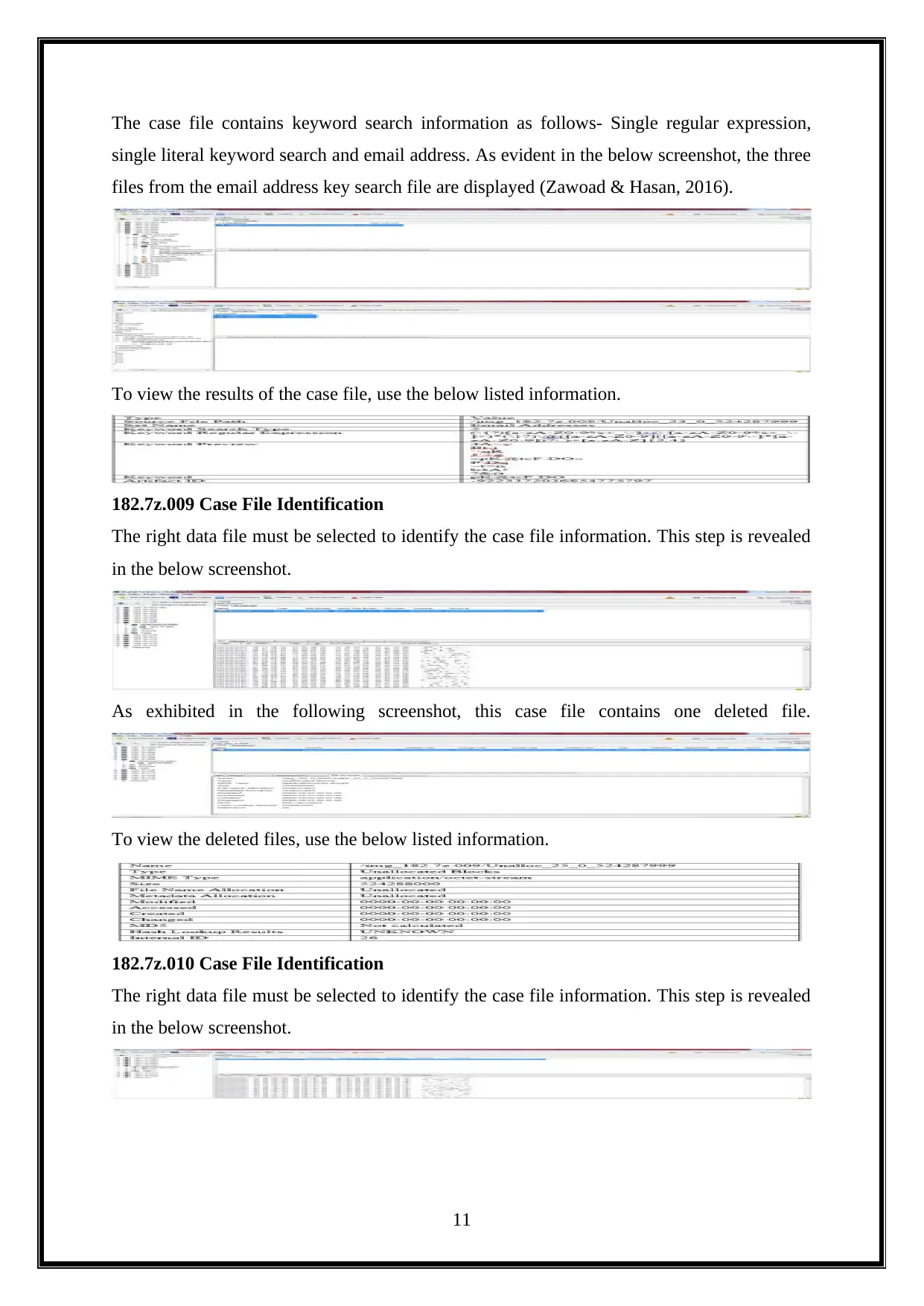
The case file contains keyword search information as follows- Single regular expression,
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed (Zawoad & Hasan, 2016).
To view the results of the case file, use the below listed information.
182.7z.009 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information.
182.7z.010 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
11
single literal keyword search and email address. As evident in the below screenshot, the three
files from the email address key search file are displayed (Zawoad & Hasan, 2016).
To view the results of the case file, use the below listed information.
182.7z.009 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
As exhibited in the following screenshot, this case file contains one deleted file.
To view the deleted files, use the below listed information.
182.7z.010 Case File Identification
The right data file must be selected to identify the case file information. This step is revealed
in the below screenshot.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 29
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




