MN624 Digital Evidence Report: Acquisition Methods, Data Preservation
VerifiedAdded on 2022/09/15
|4
|582
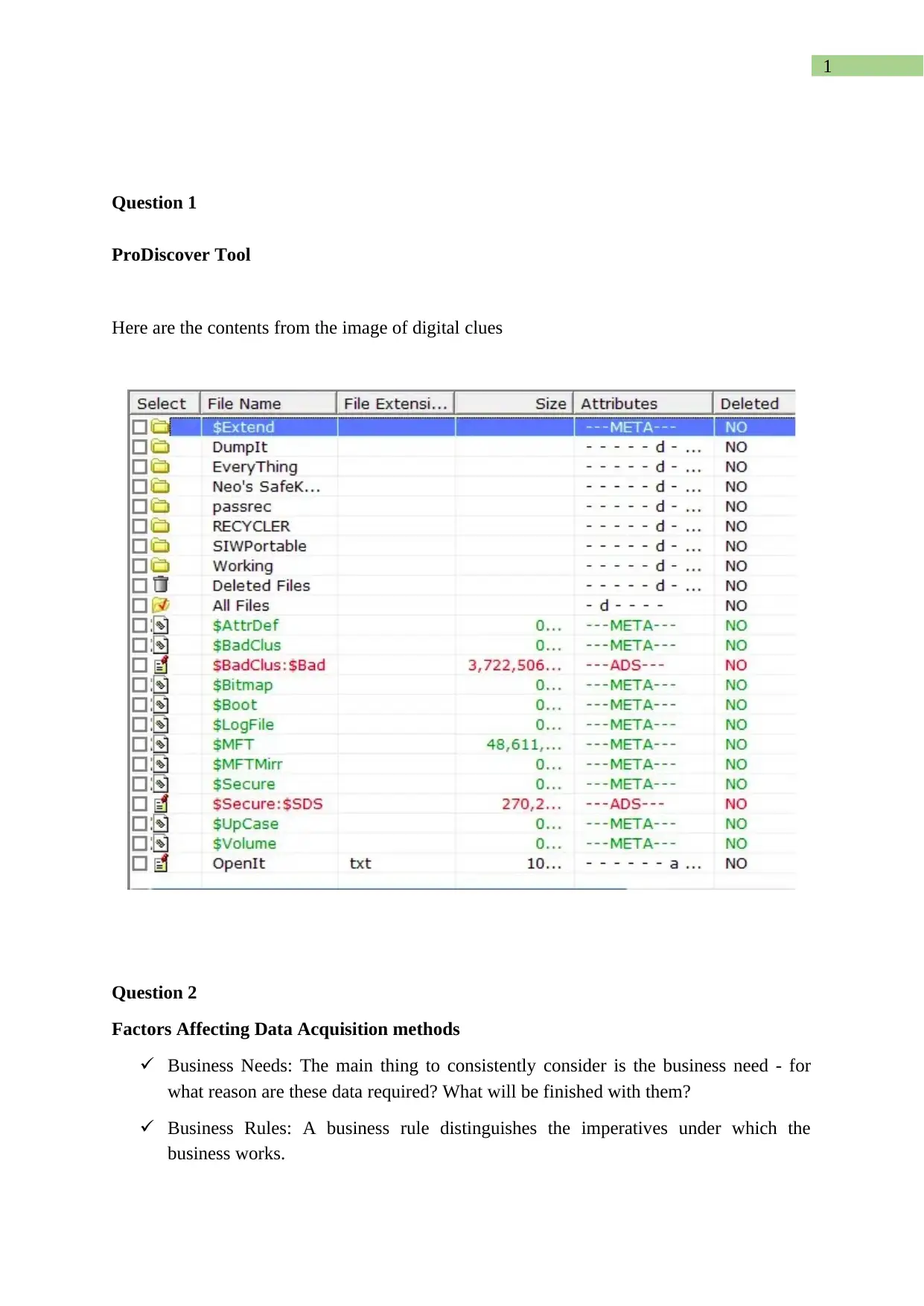
|22
Report
AI Summary
This report, prepared for the MN624 Digital Evidence module, provides a detailed overview of digital forensic concepts. It begins with an examination of the ProDiscover tool, analyzing its role in digital evidence. The report then explores factors affecting data acquisition methods, emphasizing the importance of business needs, rules, data standards, cost, time constraints, and format considerations. It delves into data preservation techniques, including drive imaging and the critical concept of chain of custody to maintain evidence integrity. Furthermore, the report contrasts two acquisition methods: live acquisition, utilizing tools like the DD command, and offline acquisition, highlighting their respective advantages and disadvantages. The report underscores the significance of each step in the digital forensic process, from initial acquisition to final preservation, to ensure the admissibility and reliability of digital evidence.
1 out of 4






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)